Configure Credential Types
Credentials A credential is a stored value (or values) that are used for user verification during authentication. are stored in devices and contain information used to authenticate users, and are linked to a credential type which defines the credential parameters leveraged during user authentication.
Credential types are provided in ActivID Appliance for all the different types of supported authentication tokens, as well PKI certificates.
Credential type parameters include adapter settings, customizable fields and validity settings.
You configure credential types using the ActivID Management Console.
Create a Credential Type
-
Log on to the ActivID Management Console as a Configuration Manager.
- Select the Configuration tab and, under Policies, select Authentication and then Credential Types.
- Code – the unique code identifying the credential type
- Name – the name of the credential type
- Credential Adapter – the credential adapter associated with the credential type
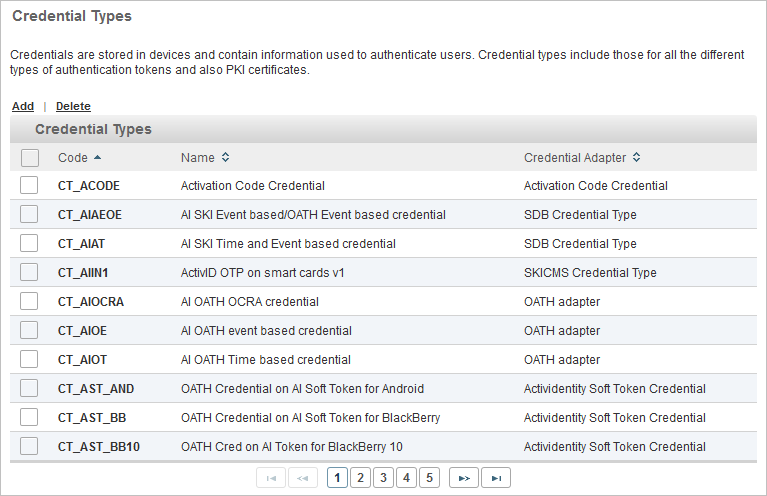
All existing credential types are listed in a paged table. The total number of credential types is given in the lower left corner.
Each row corresponds to a credential type. It provides the following information in the different columns:
Launch the Credential Type Creation Wizard
-
Click Add.
- Enter the main information for the Credential type:
- Name – should be unique for ease of administration.
- Code – a value is automatically generated but it can be changed. The code must be unique, a minimum of three characters, and a maximum of 10 characters. It cannot be changed once the credential type is created.
- Description – (optional) content is free-format.
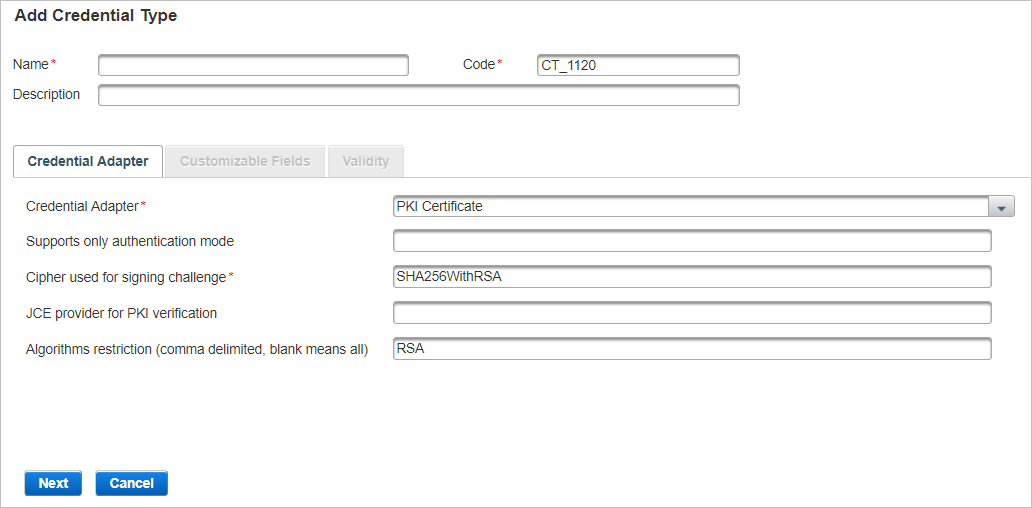
- Proceed to Define the Credential Adapter Settings.
Define the Credential Adapter Settings
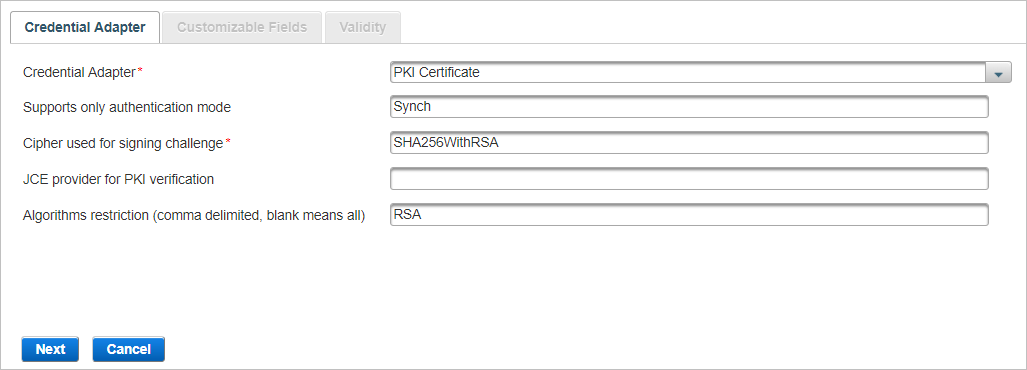
- From the drop-down list, select the type of Credential Adapter that you want to create and define the corresponding parameters.
PKI Certificate
Parameter Description Supports only authentication mode
Optional
The supported authentication mode.
Possible values:
- <empty> - both modes are supported
- Synch
- Asynch
Cipher used for signing challenge
Required
The cipher to be used when signing challenges.
The default value is SHA256WithRSA.
For further information about signature algorithms, see https://docs.oracle.com/javase/8/docs/technotes/guides/security/StandardNames.html#Signature.
JCE provider for PKI verification
Optional
The JCE provider to be used for PKI verification.
Algorithms restriction...
Optional
A comma-delimited list of crypto algorithms supported for signature. Leave the field blank to allow all algorithms.
The default value is RSA.
For further information about the algorithms, see https://docs.oracle.com/javase/8/docs/technotes/guides/security/StandardNames.html#KeyPairGenerator.
Activation Code Credential
Parameter Description Validity period of Activation Code (seconds)
Required
The number of seconds for which the Activation Code is valid.
The default value is 31536000 seconds.
Length of PIN
Required
The length of the credential's PIN
The default value is 4.
Number of times a requester can use the activation code
Required
The number of times the Activation Code can be used to request an OTP via SMS or Email.
The default value is -1, meaning that the code use is unlimited.
OOB Credential Code
Required
The OOB credential type that should be used for the Activation Code.
By default, this is CT_OOB when using Activation Code credential type CT_ATCODE.
ActivIdentity™ Soft Token Credential
Parameter Field Password service name
Required
The name for the password service.
The default value is PASSWORD.
Small OTPWindow Time Start From [0..-3]
Required
The Time Start for the small OTP synchronization window.
The default value is -3.
Small OTPWindow Time End To [0..3]
Required
The Time End for the small OTP synchronization window.
The default value is 3.
Large OTPWindow Time Start From [-5..-100]
Required
The Time Start for the large OTP synchronization window.
The default value is -5.
Large OTPWindow Time End To [4..100]
Required
The Time End for the large OTP synchronization window.
The default value is 4.
Time Increment By
Required
The number of seconds by which the time should be incremented.
The default value is 128.
Important: For soft tokens, this setting should be set to 30 seconds.Small OTPWindow Event End To [1..10]
Required
The Event End for the small OTP synchronization window.
The default value is 2.
Large OTPWindow Event End To [1..100]
Required
The Event End for the large OTP synchronization window.
The default value is 10.
Event counter manual entry maximum difference with previous value
Optional
The maximum difference allowed between a manual event counter entry and the previous counter value.
Possible values:
- 0 = allow any value
- 1 = any value only forward (default)
- Other values = maximum difference
Event counter resynchronization window (OCRA)
Optional
The resynchronization window for the event counter.
This only applies to OCRA if the OCRA suite specifies the use of the counter.
The default value is usually 30 depending on the credential type.
Time resynchronization window, in +/- time steps (OCRA)
Optional
The +/- time steps for the time resynchronization window.
This only applies to OCRA if the OCRA suite specifies the use of the timestamp.
The default value is 20.
OCRASuite with counter
Required
The OCRA suite for the event counter.
The default value is OCRA-1:HOTP-SHA1-8:C-QA06
OCRASuite with timestamp
Required
The OCRA suite for the timestamp.
The default value is OCRA-1:HOTP-SHA1-8:QA06-T30S
OCRASuite with counter (plain signature mode)
Required
The OCRA suite for the event counter in plain signature mode.
The default value is OCRA-1:HOTP-SHA1-8:C-QA06
OCRASuite with timestamp (plain signature mode)
Required
The OCRA suite for the timestamp in plain signature mode.
The default value is OCRA-1:HOTP-SHA1-8:QA06-T30S
Version authentication black list
Optional
List of token versions to blacklist for authentication.
- To exclude specific versions of a given platform from authentication, enter the token version code.
This code corresponds to the third and fourth digits of the serial number (only for 16 digit serial numbers). For example, if the version authentication blacklist is set to “12, 13, 14”, then authentication will fail for the devices with the version codes 12, 13, and 14 (that is, users will not be able to authenticate with devices with sn = 01125878523663, sn =01135647854526, sn= 01140277854500, etc.).
- To exclude all versions of a given platform from authentication, remove the credential type corresponding to this platform (for example, CT_AST_PC) from the Authentication Policy’s list of approved credential types (for example, AT_CUSTOTP). This prevents authentication using any method other than the approved credential type.
About OTP Synchronization Windows
The small OTP Window is applied first, and if, and only if, it fails the large OTP Window is then tried.
So the small window is just a means to optimize the process by restricting the number of synchronization tests to perform if it works with the small window range.
For time, the OTP Windows are expressed in number of time steps. Most time-based OATH devices are initialized with a time step of 30 seconds. In this case, if the Large OTP Window Time Start From is equal to -10 and the Large OTP Window Time End to is equal to +10, this gives an OTP validity of +- 30*10 seconds (that is, +- 5 minutes).
For the event counter, the value is the number of event counters that will be tested ahead of the last know counter value stored in the server database.
For further information, see Configure OTP Device Synchronization.
About Soft Token Black Listing
You can control your deployment of soft tokens by:
- Configuring a blacklist, and forbidding activation or authentication by using a specific version or a specific platform of Soft Token. For example, an administrator can blacklist the iOS token version 4.0.0.2.
- Configuring a blacklist of all the versions for a given platform. For example, any version of J2ME Soft Token will fail for activation and/or authentication.
- Defining a maximum number of Soft Tokens per user. This is enforced for users reaching the maximum number of Soft Tokens. Despite the state of the Soft Tokens being assigned, activation of any additional Soft Token fails.
- Defining the Soft Token activation settings at the group level (the Device Type and Authentication Policy per Soft Token type).
New Soft Tokens display a 16-digit Serial Number to enable the enforcement of the blacklist where the first four digits are used as platform and version identifiers:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 P1 P2 V1 V2 X X X X X X X X X X X X Where:
- P1 is the first digit of the platform identifier, and P2 is the second digit of the platform identifier
- V1 is the first digit of the version identifier, and V2 is the second digit of the version identifier
For example, a Soft Token with the serial number "0301425395368453" corresponds to the iOS Soft Token Platform (Platform Code 03) and Version 4.0.0.2 (Version Code 01) of the iOS Token.
Soft Token Platform Platform Code P1P2 Digits Platform Code Decimal ActivID Token for PC 02 2 ActivID Token for iOS 03 3 ActivID Token for Android 04 4 ActivID Token for BlackBerry 05 5 ActivID Token for J2ME 06 6 Rebranded Soft Token for PC 08 8 Rebranded Soft Token for iOS 09 9 Rebranded Soft Token for Android 0A 10 Rebranded Soft Token for BlackBerry 0B 11 Rebranded Soft Token for J2ME 0C 12 Legacy Soft Token (only used on the server side) 00 0 ActivID Token SDK for iOS 80 128 ActivID Token SDK for Android 81 129 ActivID Token SDK for BlackBerry 82 130 ActivID Token SDK for Windows Phone 83 131 To black list soft tokens at Activation:
- Configure the Platform and version activation black list parameter for the Device Type.
To black list soft tokens at Authentication:
- Configure the Version authentication black list parameter for the Credential Type.
- Remove the credential type corresponding to this platform (for example, CT_AST_PC) from the Authentication Policy’s list of approved credential types (for example, AT_CUSTOTP).
FIDO™ token key
Parameter Description Algorithms restriction...
Optional
A comma-delimited list of crypto algorithms supported for signature. Leave the field blank to allow all algorithms.
The default value is SHA256withECDSA.
For further information about the algorithms, see https://docs.oracle.com/javase/8/docs/technotes/guides/security/StandardNames.html#KeyPairGenerator.
OOB Credential
Parameter Description Validity period of OTP (seconds)
Required
The number of seconds for which the OTP is valid.
By default, ActivID Appliance will generate an OOB OTP valid for 1200 seconds.
Number of times a requester can ask for OTP via OOB
Required
The number of time an OOB OTP can be requested using the Activation Code without the OTP being used for authentication.
The default value is 3 times.
Length of OTP
Required
The length of the OTP.
The default value is 8.
Format of OTP (0:Digit, 1:Hex)
Required
The format of the OTP.
Possible values:
- 0 = OTP will consist of digits
- 1 = OTP will consist of hexadecimal characters
PKI Certificate Matching
Instead of importing and binding a PKI certificate to a user at registration, you can define attribute matching rules to be checked when the user provides their certificate for authentication.
At authentication, attributes of the certificate provided by the user will be matched against reference values which can either be static text, templates containing user attribute values or regular expressions (only with the Matches operator).
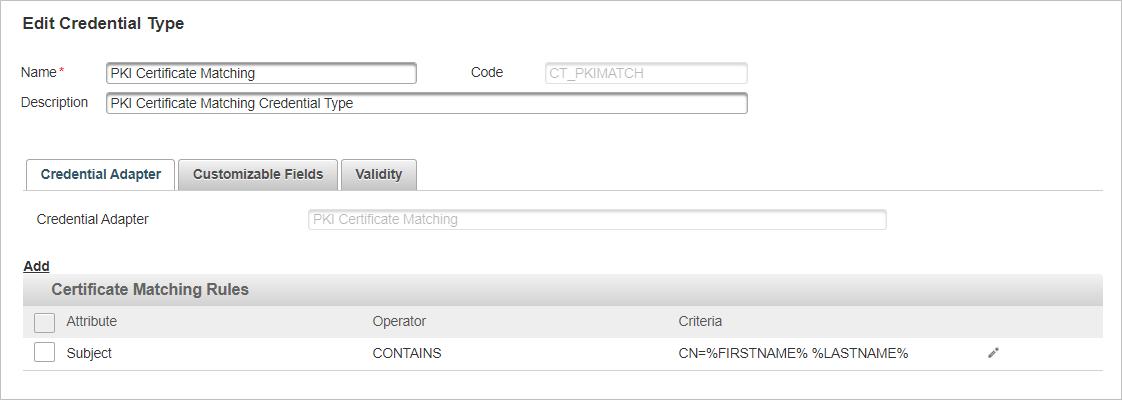 Important: Each rule is an AND condition so all must be met for a successful authentication. If you want to deploy rules with multiple definitions (for example, for multiple certificate issuers), you must create a PKI certificate matching Credential Type per definition.
Important: Each rule is an AND condition so all must be met for a successful authentication. If you want to deploy rules with multiple definitions (for example, for multiple certificate issuers), you must create a PKI certificate matching Credential Type per definition.You can add and edit the Certificate Matching Rules as required for your deployment:
- If required, click Add to create another rule.
- Click the edit icon
for the rule and configure the settings:
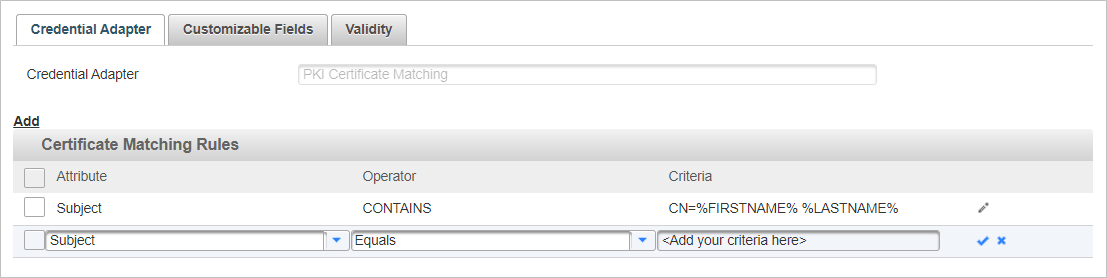
Attribute:
- Subject
- Issuer
- SubjectAlternativeName - match one or more items in the Subject Alternative Name.
You need to define a separate rule for each item with the Contains or Matches operator.
- IssuerAlternativeName - match one or more items in the Issue Alternative Name.
You need to define a separate rule for each item with the Contains or Matches operator.
- Object Identifier (OID) - match one or more items based on the identifiers for the certificate fields.
Operator:
- Equals
- Begins with
- Ends with
- Contains
- Matches
Criteria:
An eligible Criteria can be either :
- A 'static' plain text value, such as CN=TrustID Server CA O1, OU=TrustID Server, O=IdenTrust, C=US
- A text template with placeholders for user attribute values (that will be resolved dynamically at authentication) in the %USER_ATTRIBUTE_NAME% format, such as CN = %FIRSTNAME% %LASTNAME%
- A regular expression (which can also contain placeholders for user attribute values between ‘%’) if the associated operator is Matches
Note: The content of criteria is case-sensitive must match exactly the expected format of the certificate value, including spaces.- Click the check mark icon
to apply the rule settings.
Otherwise, click the cancel icon
to discard the settings.
- Click Save.
To delete a rule:
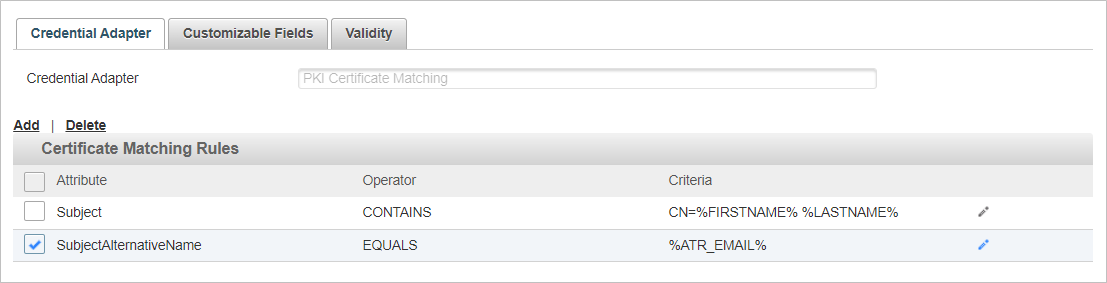
Select the check box for the rule you want to delete, click Delete and then Yes to confirm.
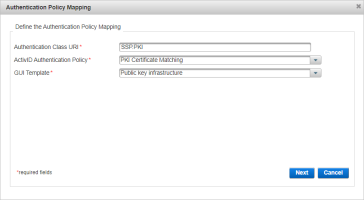
Important: To enable PKI Certificate Matching as an authentication method for a service provider (for example, the ActivID Self-Service Portal), you must add an Authentication Policy Mapping.The mapping configuration is:
- Authentication Class URI - the SAML 2.0 authentication class for your service provider (for example, urn:oasis:names:tc:SAML:2.0:ac:classes:SmartcardPKI)
For the ActivID Self-Service Portal, the URI is SSP.PKI. For the ActivID Management Console, it is MC.PKI.
- ActivID Authentication Policy - PKI Certificate Matching
- GUI Template - Public key infrastructure
PKI Token V5
Parameter Description Signature Algorithm
Required
The crypto algorithm for message signature.
The default value is SHA256WithRSA.
Algorithms restriction ...
Optional
A comma-delimited list of crypto algorithms supported for signature. Leave the field blank to allow all algorithms.
The default value is RSA.
For further information about the algorithms, see https://docs.oracle.com/javase/8/docs/technotes/guides/security/StandardNames.html#KeyPairGenerator.
OTP length
Required
The length of the OTP used to verify the device’s identity.
The default value is 8.
Encryption Algorithm
Optional
The algorithm used for encryption.
The default value is A256CBC-HS512.
Default Approval Status
Required
The approval status to be sent to the device.
Any string items are separated by |.
The default value is accept|deny|report.
Important: Do NOT modify the default value for deployments with the HID Approve application.Key parameters
Required
The parameters for the credential key.
The default value is LABEL=signkey;KEYUSAGE=signature;TYPE=RSA;ALGO=RSA2048;SUITE=PKIv1;POPALGOID=1.2.840.113549.1.1.10
Key validity period (days)
Required
The number of days for which the credential is valid.
The default value is 365.
Key protection policy
Required
The parameters of the key protection policy.
The default value is TYPE=password;HISTMAX=1;HISTMINAGE=1;HISTMAXAGE=180;LOCKTYPE=delay;DELAY=2;COUNTER=6;UP=1;LOW=0;NUM=0;ALPHA=1;NALPHA=1;MUP=8;MLOW=8;MNUM=8;MALPHA=8;MNALPHA=8;MINLEN=6;MAXLEN=8
OATH Adapter
Parameter Description Password service name
Required
The name for the password service.
The default value is PASSWORD.
Small OTPWindow Time Start From [0..-3]
Required
The Time Start for the small OTP synchronization window.
The default value is -3.
Small OTPWindow Time End To [0..3]
Required
The Time End for the small OTP synchronization window.
The default value is 3.
Large OTPWindow Time Start From [-5..-100]
Required
The Time Start for the large OTP synchronization window.
The default value is usually -10 depending on the credential type.
Large OTPWindow Time End To [4..100]
Required
The Time End for the large OTP synchronization window.
The default value is usually 10 depending on the credential type.
Time Increment By
Required
The number of seconds by which the time should be incremented.
The default value is usually 30 depending on the credential type.
Important: This setting should be set to the value used to initialize the corresponding device (usually 30 seconds).Small OTPWindow Event End To [1..10]
Required
The Event End for the small OTP synchronization window.
The default value is 2.
Large OTPWindow Event End To [1..100]
Required
The Event End for the large OTP synchronization window.
The default value is 10.
Event counter manual entry maximum difference with previous value
Optional
The maximum difference allowed between a manual event counter entry and the previous counter value.
Possible values:
- 0 = allow any value
- 1 = any value only forward (default)
- Other values = maximum difference
Event counter resynchronization window (OCRA)
Optional
The resynchronization window for the event counter.
This only applies to OCRA if the OCRA suite specifies the use of the counter.
The default value is usually 30 depending on the credential type.
Time resynchronization window, in +/- time steps (OCRA)
Optional
The +/- time steps for the time resynchronization window.
This only applies to OCRA if the OCRA suite specifies the use of the timestamp.
The default value is 20.
OCRASuite with counter
Required
The OCRA suite for the event counter.
The default value is OCRA-1:HOTP-SHA1-8:C-QA06
OCRASuite with timestamp
Required
The OCRA suite for the timestamp.
The default value is OCRA-1:HOTP-SHA1-8:QA06-T30S
OCRASuite with counter (plain signature mode)
Required
The OCRA suite for the event counter in plain signature mode.
The default value is OCRA-1:HOTP-SHA1-8:C-QA06
OCRASuite with timestamp (plain signature mode)
Required
The OCRA suite for the timestamp in plain signature mode.
The default value is OCRA-1:HOTP-SHA1-8:QA06-T30S
About OTP Synchronization Windows
The small OTP Window is applied first, and if, and only if, it fails the large OTP Window is then tried.
So the small window is just a means to optimize the process by restricting the number of synchronization tests to perform if it works with the small window range.
For time, the OTP Windows are expressed in number of time steps. Most time-based OATH devices are initialized with a time step of 30 seconds. In this case, if the Large OTP Window Time Start From is equal to -10 and the Large OTP Window Time End to is equal to +10, this gives an OTP validity of +- 30*10 seconds (that is, +- 5 minutes).
For the event counter, the value is the number of event counters that will be tested ahead of the last know counter value stored in the server database.
For further information, see Configure OTP Device Synchronization.
PKI Token
Note: This credential type is deprecated and only provided for legacy support. Use PKI Token V5 instead.
Parameter Description Signature Algorithm
Required
The crypto algorithm for message signature.
The default value is SHA256WithRSA.
Algorithms restriction ...
Optional
A comma-delimited list of crypto algorithms supported for signature. Leave the field blank to allow all algorithms.
The default value is RSA.
For further information about the algorithms, see https://docs.oracle.com/javase/8/docs/technotes/guides/security/StandardNames.html#KeyPairGenerator.
OTP length
Required
The length of the OTP used to verify the device’s identity.
The default value is 8.
Encryption Algorithm
Optional
The algorithm used for encryption.
The default value is A256CBC-HS512.
Default Approval Status
Required
The approval status to be sent to the device.
Any string items are separated by |.
The default value is accept|deny|report.
Important: Do NOT modify the default value for deployments with the HID Approve application.
TDS Symmetric Encryption key
Parameter Description Key parameters
Required
The parameters for the credential key.
LABEL=CDFEncKey;KEYUSAGE=encryption;TYPE=oct;EXTRACTABLE=0;SCOPE=singledomain;DERIVEDKEYLENGTH=32
Key validity period (days)
Required
The number of days for which the credential is valid.
The default value is 365.
Key protection policy
Required
The parameters for the key protection policy.
TYPE=device;HISTMAX=1;HISTMINAGE=1;HISTMAXAGE=180;LOCKTYPE=delay;DELAY=2;COUNTER=6;UP=1;LOW=0;NUM=0;ALPHA=1;NALPHA=1;MUP=8;MLOW=8;MNUM=8;MALPHA=8;MNALPHA=8;MINLEN=6;MAXLEN=8
TDS OATH Adapter
Parameter Description Password service name
Required
The name of the password service.
The default value is PASSWORD.
Small OTPWindow Time Start From [0..-3]
Required
The Time Start for the small OTP synchronization window.
The default value is -3.
Small OTPWindow Time End To [0..3]
Required
The Time End for the small OTP synchronization window.
The default value is 3.
Large OTPWindow Time Start From [-5..-100]
Required
The Time Start for the large OTP synchronization window.
The default value is usually -10 depending on the credential type.
Large OTPWindow Time End To [4..100]
Required
The Time End for the large OTP synchronization window.
The default value is usually 10 depending on the credential type.
Time Increment By
Required
The number of seconds by which the time should be incremented.
The default value is usually 30 depending on the credential type.
Important: This setting should be set to the value used to initialize the corresponding device (usually 30 seconds).Small OTPWindow Event End To [1..10]
Required
The Event End for the small OTP synchronization window.
The default value is 2.
Large OTPWindow Event End To [1..100]
Required
The Event End for the large OTP synchronization window.
The default value is 10.
Event counter manual entry maximum difference with previous value
Optional
The maximum difference allowed between a manual event counter entry and the previous counter value.
Possible values:
- 0 = allow any value
- 1 = any value only forward (default)
- Other values = maximum difference
Event counter resynchronization window (OCRA)
Optional
The resynchronization window for the event counter.
This only applies to OCRA if the OCRA suite specifies the use of the counter.
The default value is usually 30 depending on the credential type.
Time resynchronization window, in +/- time steps (OCRA)
Optional
The +/- time steps for the time resynchronization window.
This only applies to OCRA if the OCRA suite specifies the use of the timestamp.
The default value is 20.
OCRASuite with counter
Required
The OCRA suite for the event counter.
The default value is OCRA-1:HOTP-SHA1-8:C-QA06
OCRASuite with timestamp
Required
The OCRA suite for the timestamp.
The default value is OCRA-1:HOTP-SHA1-8:QA06-T30S
OCRASuite with counter (plain signature mode)
Required
The OCRA suite for the event counter in plain signature mode.
The default value is OCRA-1:HOTP-SHA1-8:C-QA06
OCRASuite with timestamp (plain signature mode)
Required
The OCRA suite for the timestamp in plain signature mode.
The default value is OCRA-1:HOTP-SHA1-8:QA06-T30S
OTP key parameters
Required
The parameters for the credential OTP key.
The default value is LABEL=OTP;SUPPORTEDALGS=hotp|ocra;KEYUSAGE=otp;MODES=CHALLENGE_RESPONSE|SIGNATURE;TYPE=OCT;RESYNCWIN=20;OTPLEN=6;ADDCHECKSUM=0;OFFSET=16;TIMESTEP=30;STARTTIME=0;CLIENTOCRASUITE=OCRA-1:HOTP-SHA1-8:C-QA06;SERVEROCRASUITE=OCRA-1:HOTP-SHA1-8:C-QA06
Key validity period (days)
Required
The number of days for which the credential key is valid.
The default is 365.
Key protection policy
Required
The parameters for the key protection policy.
The default value is TYPE=password;HISTMAX=1;HISTMINAGE=1;HISTMAXAGE=180;LOCKTYPE=delay;DELAY=2;COUNTER=6;UP=1;LOW=0;NUM=0;ALPHA=1;NALPHA=1;MUP=8;MLOW=8;MNUM=8;MALPHA=8;MNALPHA=8;MINLEN=6;MAXLEN=8
About OTP Synchronization Windows
The small OTP Window is applied first, and if, and only if, it fails the large OTP Window is then tried.
So the small window is just a means to optimize the process by restricting the number of synchronization tests to perform if it works with the small window range.
For time, the OTP Windows are expressed in number of time steps. Most time-based OATH devices are initialized with a time step of 30 seconds. In this case, if the Large OTP Window Time Start From is equal to -10 and the Large OTP Window Time End to is equal to +10, this gives an OTP validity of +- 30*10 seconds (that is, +- 5 minutes).
For the event counter, the value is the number of event counters that will be tested ahead of the last know counter value stored in the server database.
For further information, see Configure OTP Device Synchronization.
TDS OOB Credential
Parameter Description Validity period of password (seconds)
Required
The number of seconds for which the password is valid.
The default value is 1200.
Length of password
Required
The length of the password.
The default value is 8.
Format of password (0:Digit, 1:Hex)
Required
The format of the password.
Possible values:
- 0 = password will consist of digits
- 1 = password will consist of hexadecimal characters
SDB Credential Type
Parameter Description Password service name
Required
The name for the password service.
The default value is PASSWORD.
Small OTPWindow Time Start From [0..-3]
Required
The Time Start for the small OTP synchronization window.
The default value is -3.
Small OTPWindow Time End To [0..3]
Required
The Time End for the small OTP synchronization window.
The default value is 3.
Large OTPWindow Time Start From [-5..-100]
Required
The Time Start for the large OTP synchronization window.
The default value is -5.
Large OTPWindow Time End To [4..100]
Required
The Time End for the large OTP synchronization window.
The default value is 4.
Time Increment By
Required
The number of seconds by which the time should be incremented.
The default value is 128.
Small OTPWindow Event End To [1..10]
Required
The Event End for the small OTP synchronization window.
The default value is 2.
Large OTPWindow Event End To [1..100]
Required
The Event End for the large OTP synchronization window.
The default value is 10.
About OTP Synchronization Windows
The small OTP Window is applied first, and if, and only if, it fails the large OTP Window is then tried.
So the small window is just a means to optimize the process by restricting the number of synchronization tests to perform if it works with the small window range.
For time, the OTP Windows are expressed in number of time steps. Most time-based OATH devices are initialized with a time step of 30 seconds. In this case, if the Large OTP Window Time Start From is equal to -10 and the Large OTP Window Time End to is equal to +10, this gives an OTP validity of +- 30*10 seconds (that is, +- 5 minutes).
For the event counter, the value is the number of event counters that will be tested ahead of the last know counter value stored in the server database.
For further information, see Configure OTP Device Synchronization.
SKICMS Credential Type
Parameter Description Password service name
Required
The name of the password service.
No default value.
Note: This service name is to identify the SKI slot to be used in case of multi-slots devices. The most common slot used is “PASSWORD”.
SMS OOB Transaction Validation Credential
Parameter Description Validity period (seconds)
Required
The number of seconds for which the password is valid.
The default value is 1200.
Length of password
Required
The length of the password.
The default value is 8.
Format of password (0:Digit, 1:Hex)
Required
The format of the password.
Possible values:
- 0 = password will consist of digits
- 1 = password will consist of hexadecimal characters
OIDC ADFS Credential Type
No parameters to configure
JWT Bearer
Parameter Description Algorithms restriction ...
Optional
A comma-delimited list of crypto algorithms supported for signature. Leave the field blank to allow all algorithms.
The default value is RSA.
For further information about the algorithms, see https://docs.oracle.com/javase/8/docs/technotes/guides/security/StandardNames.html#KeyPairGenerator.
CMS OATH Credential Type
Parameter Description Password service name
Required
The name of the password service.
The default value is PASSWORD.
Small OTPWindow Time Start From [0..-3]
Required
The Time Start for the small OTP synchronization window.
The default value is -3.
Small OTPWindow Time End To [0..3]
Required
The Time End for the small OTP synchronization window.
The default value is 3.
Large OTPWindow Time Start From [-5..-100]
Required
The Time Start for the large OTP synchronization window.
The default value is usually -10 depending on the credential type.
Large OTPWindow Time End To [4..100]
Required
The Time End for the large OTP synchronization window.
The default value is usually 10 depending on the credential type.
Time Increment By
Required
The number of seconds by which the time should be incremented.
The default value is usually 30 depending on the credential type.
Important: This setting should be set to the value used to initialize the corresponding device (usually 30 seconds).Small OTPWindow Event End To [1..10]
Required
The Event End for the small OTP synchronization window.
The default value is 2.
Large OTPWindow Event End To [1..100]
Required
The Event End for the large OTP synchronization window.
The default value is 10.
Event counter manual entry maximum difference with previous value
Optional
The maximum difference allowed between a manual event counter entry and the previous counter value.
Possible values:
- 0 = allow any value
- 1 = any value only forward (default)
- Other values = maximum difference
Event counter resynchronization window (OCRA)
Optional
The resynchronization window for the event counter.
This only applies to OCRA if the OCRA suite specifies the use of the counter.
The default value is usually 30 depending on the credential type.
Time resynchronization window, in +/- time steps (OCRA)
Optional
The +/- time steps for the time resynchronization window.
This only applies to OCRA if the OCRA suite specifies the use of the timestamp.
The default value is 20.
OCRASuite with counter
Required
The OCRA suite for the event counter.
The default value is OCRA-1:HOTP-SHA1-8:C-QA06
OCRASuite with timestamp
Required
The OCRA suite for the timestamp.
The default value is OCRA-1:HOTP-SHA1-8:QA06-T30S
OCRASuite with counter (plain signature mode)
Required
The OCRA suite for the event counter in plain signature mode.
The default value is OCRA-1:HOTP-SHA1-8:C-QA06
OCRASuite with timestamp (plain signature mode)
Required
The OCRA suite for the timestamp in plain signature mode.
The default value is OCRA-1:HOTP-SHA1-8:QA06-T30S
Event counter resynchronization window
Required
The resynchronization window for the event counter .
The default value is 30.
Time resynchronization window
Required
The +/- time steps for the time resynchronization window.
The default value is 10.
About OTP Synchronization Windows
The small OTP Window is applied first, and if, and only if, it fails the large OTP Window is then tried.
So the small window is just a means to optimize the process by restricting the number of synchronization tests to perform if it works with the small window range.
For time, the OTP Windows are expressed in number of time steps. Most time-based OATH devices are initialized with a time step of 30 seconds. In this case, if the Large OTP Window Time Start From is equal to -10 and the Large OTP Window Time End to is equal to +10, this gives an OTP validity of +- 30*10 seconds (that is, +- 5 minutes).
For the event counter, the value is the number of event counters that will be tested ahead of the last know counter value stored in the server database.
For further information, see Configure OTP Device Synchronization.
- Click Next and Define the Customizable Fields.
Define the Customizable Fields
- If required, enter the search or data field content as required
- Click Next and Define the Validity Settings.
Define the Validity Settings
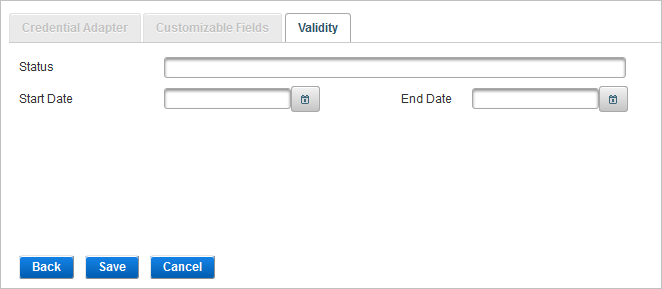
-
In the Status field, enter/edit the status category.
-
In the Start Date (dd/mm/yyyy) field, enter/edit the valid start date of the credential type.
-
In the End Date (dd/mm/yyyy) field, enter/edit the expiry date of the credential type.
-
Click Save.
Edit a Credential Type
-
Log on to the ActivID Management Console as a Configuration Manager.
- Select the Configuration tab and, under Policies, select Authentication and then Credential Types.

-
Click the Code of the credential type that you want to edit.
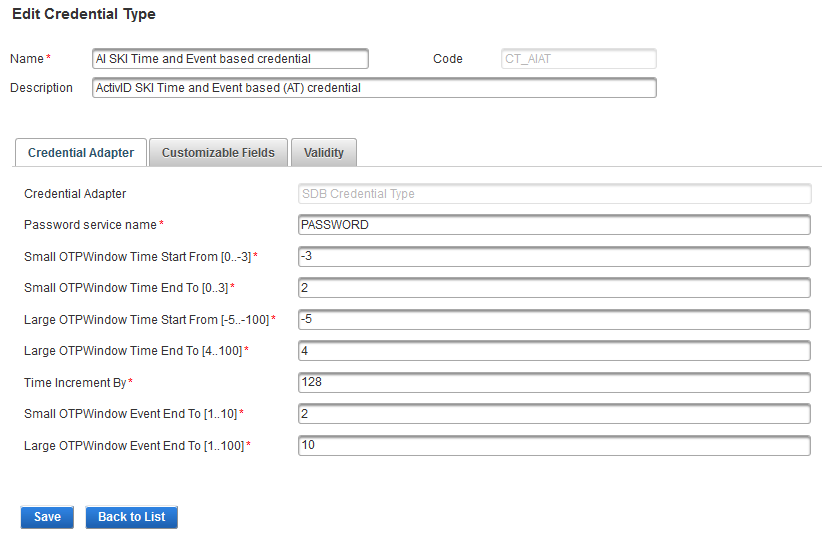
-
Edit the credential type settings as required in each tab.
All the tabs are accessible and all settings can be modified except the:
- Code
- Credential Adapter
- Click Save to apply your changes.
If you want to cancel the operation, click Back to List.
Delete a Credential Type
- To delete a credential type, you must be assigned the Delete credential type permission.
- Make sure the credential type is not used by any instances of credentials in the ActivID Appliance database. You will not be able delete the credential type if it is still in use.
-
Log on to the ActivID Management Console as a Configuration Manager.
- Select the Configuration tab and, under Policies, select Authentication and then Credential Types.
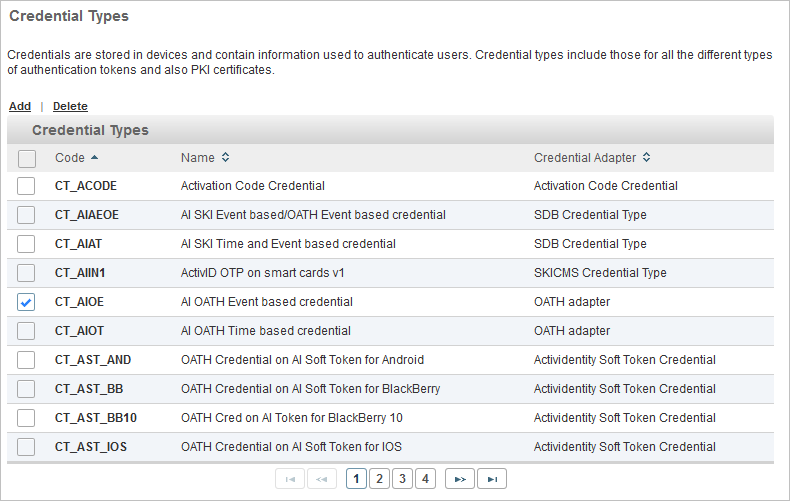
-
To delete one or more credential types, select the checkboxes to the left of the names and click Delete.
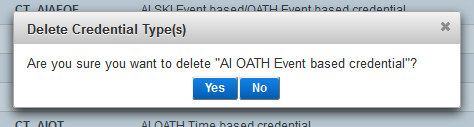
-
Click Yes to delete the types, or No to cancel the operation.
See also: