Configure the Push-Based Validation Credential Type
For easy configuration/usage purposes, you can use the pre-configured Credential Types:
| Credential Type | Description |
|---|---|
|
CT_TDSOOB |
Mobile Registration Credential |
|
CT_PASAV4 |
Mobile Logon Validation Credential Optional, used for logon operations with push |
|
CT_TDSV4 |
Mobile Action Validation Credential Optional, used for other operations with push (except logon) |
|
CT_TDSOE |
Mobile OATH event-based Credential Optional, used for Secure Code offline operations using mobile counter synchronization |
|
CT_TDSOT |
Mobile OATH time-based Credential Optional, used for Secure Code offline operations using mobile time synchronization |
|
CT_TDSOAECR |
Mobile OATH OCRA event-based Credential C/R Optional, used for challenge/response offline operations using mobile counter synchronization |
|
CT_TDSOAESIGN |
Mobile OATH OCRA event-based Credential SIGN Optional, used for transaction signature offline operations using mobile counter synchronization |
|
CT_TDSOATCR |
Mobile OATH OCRA time-based Credential C/R Optional, used for challenge/response offline operations using mobile time synchronization |
|
CT_TDSOATSIGN |
Mobile OATH OCRA time-based Credential SIGN Optional, used for transaction signature offline operations using mobile time synchronization |
|
CT_SMK4 |
Transport Key for Mobile Service communications |
In this case, you only need update the credential types for your deployment if necessary.
Configure the Pre-Configured Credential Types
-
Log on to the ActivID Management Console as a Configuration Manager.
-
Select the Configuration tab.
-
Under Polices, expand Authentication and click Credential Types.
-
Select the Mobile Logon Validation Credential (CT_PASAV4) credential type (or another credential type).
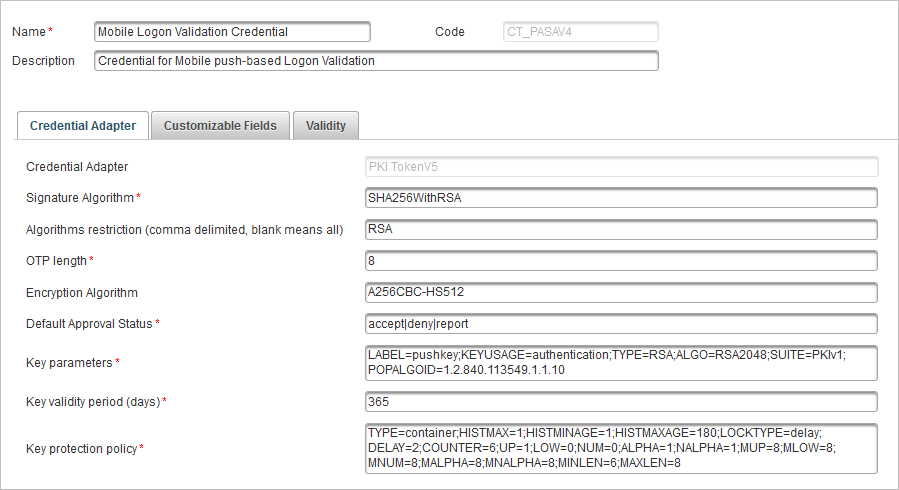
-
In Credential Adapter tab, edit the values as required.
In the Customizable Fields tab, the Search Field 1 Type field must contain the value SEARCH_PUSHID.
Do not change the Key protection policy TYPE parameter value.
When the container policy is used, the key protection policy corresponds to the Device Type's Container Keys protection policy parameter. All keys with the container policy will have the same protection method.
The following table specifies the policies supported by HID Approve for each key.
Credential Type Credential Key Name Type CT_SMK4 Transport Key for Mobile Service communications device CT_PASAV4 Mobile Logon Validation Credential container CT_TDSV4 Mobile Action Validation Credential container CT_TDSOAECR Mobile OATH OCRA event-based Credential C/R container CT_TDSOAESIGN Mobile OATH OCRA event-based Credential SIGN container CT_TDSOATSIGN Mobile OATH OCRA time-based Credential SIGN container CT_TDSOATCR Mobile OATH OCRA time-based Credential C/R container CT_TDSOE Mobile OATH event-based Credential container CT_TDSOT Mobile OATH event-based Credential container
ActivID Appliance uses this value to define the attribute to store the device Push ID. This value must not be changed or removed.
If necessary, edit the Device Type settings.
-
In the Validity tab, accept the default values for the Start Date (dd/MM/yyyy), Expiry Date (dd/MM/yyyy), and Status fields.
-
Click Save.
Configure a Mobile Operation Protection Credential Type
To use the HID Approve Silent Lock policy, you need to create a new Mobile operation protection credential type and add it to your push solution.
-
Log on to the ActivID Management Console as a Configuration Manager.
-
Select the Configuration tab and, under Polices, expand Authentication and click Credential Types.
- Click Add and create the credential type with the following settings:
- Name - Mobile operation protection
- Code - CT_OPPRO
- Description - Credential for Mobile operation protection
- Credential Adapter - TDS OATH adapter
- Password service name - PASSWORD
OTP Key Parameters - LABEL=OAUTH_OPPRO;SUPPORTEDALGS=totp;KEYUSAGE=OPPRO;RESYNCWIN=20;TYPE=OCT;OTPLEN=6;ADDCHECKSUM=0;OFFSET=16;TIMESTEP=30;STARTTIME=0;SERVEROCRASUITE=N/A
- Key Protection Policy - TYPE=container
- Add the new credential type to the existing Mobile push-based Logon validation Authentication policy (AT_PASA):
- Select the Configuration tab and, under Polices, expand Authentication and click Authentication Policies.
- Select the Mobile push-based Logon validation Authentication policy (AT_PASA) and then the Constraints tab.
- Move Mobile Operation Protection to the list of Selected Credential Types and click Save.
- Repeat the above step to add the new credential type to the existing Mobile push-based Action validation Authentication policy (AT_TDS).
- Add the new credential type to the Mobile push based validation Device type (DT_TDSV4) container profile:
- Select the Configuration tab and, under Polices, expand Authentication and click Device Types.
- Select the Mobile push based validation Device type (DT_TDSV4) and then the Device Adapter tab.
- In the Container Profile field, enter:
SMK:KEY1:CT_SMKV4:AT_SMK:CH_SMK|OTP:KEY2:CT_TDSOT:AT_CUSTOTP:CH_PASA|OTP:KEY3:CT_TDSOATCR:AT_CUSTOTP:CH_PASA|OTP:KEY4:CT_TDSOATSIGN:AT_CUSTOTP:CH_PASA|RSA:KEY5:CT_PASAV4:AT_PASA:CH_PASA|RSA:KEY6:CT_TDSV4:AT_TDS:CH_TDS|OTP:KEY7:CT_OPPRO:AT_PASA:CH_PASA
- In the Container keys protection policy field, enter:
TYPE=biometricorpassword;HISTMAX=1;HISTMINAGE=1;HISTMAXAGE=0;LOCKTYPE=silent;DELAY=2;COUNTER=6;UP=1;LOW=0;NUM=0;ALPHA=1;NALPHA=1;MUP=8;MLOW=8;MNUM=8;MALPHA=8;MNALPHA=8;MINLEN=6;MAXLEN=8;CACHE_ENABLED=0
- Click Save.





