HID RMS Scenarios
End users authenticate successfully if the detected threat is sufficiently low. However, as soon as one of the risk score thresholds is reached, access to the resources will be protected by one of the methods defined in the HID RMS configuration.
The end user is either prompted to use another authentication method as a step-up (typically a stronger authentication method, such as a multi-factor authentication), or be prevented from accessing the resources.
The HID RMS Demo Sample is used to illustrate the cases. It provides a quick demonstration of the HID RMS concepts and Threat Detection details.
By default, the sample is mapped to the Customer Banking Portal Channel (an existing Channel from the ActivID Appliance pre-defined dataset).
Using the ActivID Management Console, you can add an RMS source to the Customer Banking Portal Channel and define its Risk Management settings. This will immediately impact the result of the authentication process on the HID RMS sample.
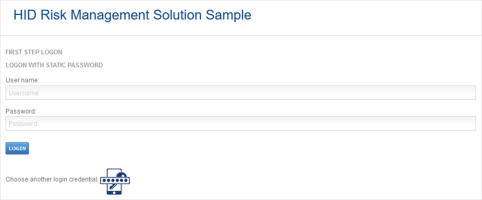
By simulating the login page for a relying party application, the Risk Management Login page allows you to test the solution.
The sample uses the ActivID OAuth/OpenID Connect API (RESTful) and ActivID SCIM API (RESTful) to send the login requests to ActivID Appliance and then waits for the result of the logon.
If necessary, when the step-up threshold is exceeded, the sample asks for an OTP or sends a Mobile Push Logon Validation request to the HID Approve mobile application and waits for the result of the Logon request on the RMS callback servlet using the HTTP Callback method.
The sample allows to perform a first authentication using either a static password or an OTP. The following examples are illustrated with the spl-consumer account using a static password for first authentication, and a step-up configured allowing Push Mobile login.
One: No Thresholds Exceeded – Successful Logon
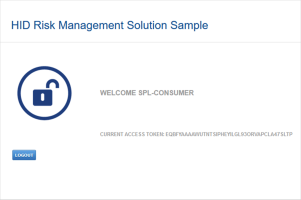
When the user logs on and the retrieved score is lower than any of the thresholds, they access the HID RMS Sample Welcome page.
| Parameter | Value |
|---|---|
| Step 1 reject score threshold | 900 |
| Step 1 block score threshold | 950 |
| Risk score obtained for Step 1 | 205 |
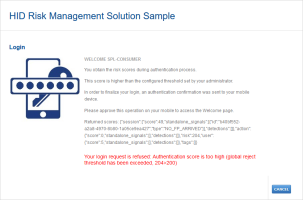
As the risk score (205) is lower than the Step 1 Reject score threshold (900), the request is authorized, and the user is logged on.
Two: First Authentication Step-up Threshold is Exceeded
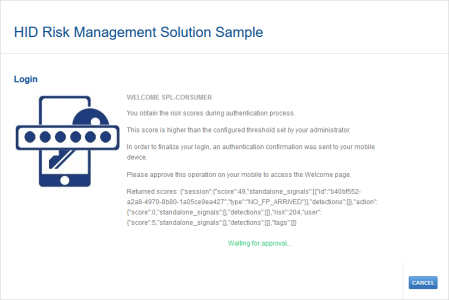
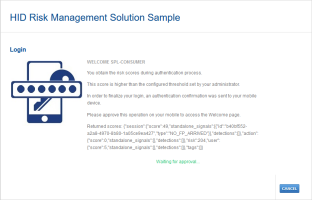
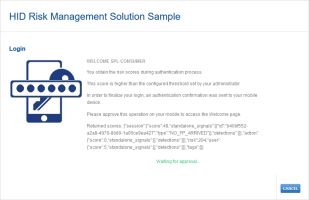
If a Step-up Threshold has been set, when the user logs on and the retrieved score exceeds the step-up threshold, they are prompted to use another authentication policy (defined by the HID RMS configuration).
| Parameter | Value |
|---|---|
| Step 1 reject score threshold | 900 |
| Step 1 block score threshold | 950 |
| Step-up Aggregate Risk Score threshold | 200 |
| Step 2 reject score threshold | Not set |
| Step 2 block score threshold | Not set |
| Risk score obtained for Step 1 | 204 |
-
As the Step 1 Risk score (204) exceeds the Step-up Aggregate Risk Score threshold (200), the user is prompted to approve a push-based validation.
-
The user approves the push logon request.
-
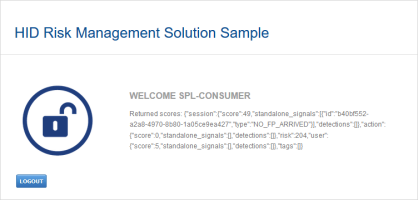
As there are no Step 2 thresholds defined, the request is authorized, and the user is logged on.
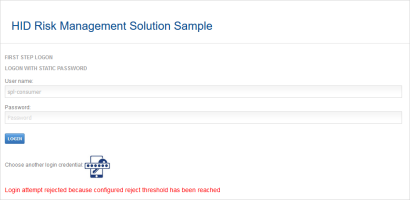
Three: First Authentication Reject Threshold is Exceeded
When the user logs on and the retrieved score reaches the reject threshold, he cannot access the HID RMS Sample Welcome page, and a warning is displayed.
| Parameter | Value |
|---|---|
| Step 1 reject score threshold | 200 |
| Step 1 block score threshold | 950 |
| Risk score obtained for Step 1 | 204 |
As the risk score (204) exceeds the Step 1 Reject score threshold (200), the request is rejected, and the user is not logged on.
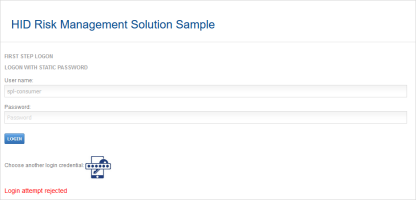
Four: First Authentication Block Threshold is Exceeded
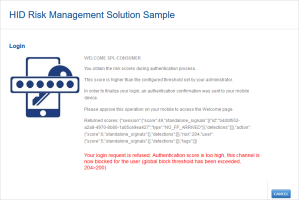
When the user logs on and the retrieved score exceeds the block threshold, he cannot access the HID RMS Sample Welcome page, and a warning is displayed.
In addition, he is blocked from further logon attempts to the portal.
| Parameter | Value |
|---|---|
| Step 1 reject score threshold | 100 |
| Step 1 block score threshold | 200 |
| Risk score obtained for Step 1 | 204 |
As the risk score (204) exceeds the Step 1 Block score threshold (200), the request is rejected, and the user is not logged on.
The user is also blocked on the channel.
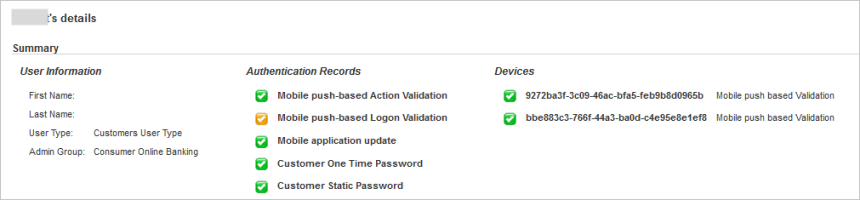
In the ActivID Management Console, view the status of the user’s authenticator.
The blocked status is indicated by the orange checkmark  .
.
All subsequent log on attempts by the user will fail until an ActivID Appliance operator unblocks the channel.
To unblock the channel for the user, see Block/Unblock a Channel for a User.
Five: Second Authentication Reject Threshold is Exceeded
If the user is required to perform a step-up authentication (because the risk score exceeded the step-up threshold for the first authentication), it is possible to calculate a separate risk score evaluation for the second step authentication (that is, the step-up authentication) as well.
When the user logs on using the step-up authentication method and the score exceeds the reject threshold, he cannot access the Risk Management Solution Sample Welcome page, and a warning message is displayed.
| Parameter | Value |
|---|---|
| Step 1 reject score threshold | 900 |
| Step 1 block score threshold | 950 |
| Step-up Aggregate Risk Score threshold | 100 |
| Step 2 reject score threshold | 200 |
| Step 2 block score threshold | 950 |
| Risk score obtained for Step 1 | 690 |
| Risk score obtained for Step 2 | 700 |
-
As the Step 1 Risk score (690) exceeds the Step-up threshold (100), the user is prompted to approve a push-based validation.
-
The user approves the push logon request.
-
As the Step 2 Risk score (700) exceeds the Step 2 Reject score threshold (200), the logon request is rejected.
Six: Second Authentication Block Threshold is Exceeded
If the user is required to perform a step-up authentication (because the risk score exceeded the step-up threshold for the first authentication), it possible to calculate a separate risk score evaluation for the second step authentication (that is, the step-up authentication) as well.
When the user logs on using the step-up authentication method and the score exceeds the block threshold, he cannot access the Risk Management System Sample Welcome page, and a warning message is displayed.
| Parameter | Value |
|---|---|
| Step 1 reject score threshold | 900 |
| Step 1 block score threshold | 950 |
| Step-up Aggregate Risk Score threshold | 100 |
| Step 2 reject score threshold | 150 |
| Step 2 block score threshold | 200 |
| Risk score obtained for Step 1 | 204 |
| Risk score obtained for Step 2 | 204 |
-
As the Step 1 Risk score (204) exceeds the Step-up threshold (100), the user is prompted to approve a push-based validation.
-
The user approves the push logon request.
-
As the Step 2 Risk score (204) exceeds the Step 2 Block score threshold (200), the logon request is rejected and blocked.
To unblock the channel for the user, see Block/Unblock a Channel for a User.
Seven: Continuous Authentication using Refresh Token
In a scenario with continuous authentication, users can renew their access token using a refresh token.
Refresh tokens are credentials used to obtain access tokens. Refresh tokens are issued to the client by the authorization server and are used to obtain a new access token when the current access token becomes invalid or expires (allowing access tokens have a shorter lifetime).
In the context of an HID RMS deployment, the risk score of the renewal request is evaluated against the defined thresholds for user authentication.
If the request’s score exceeds the thresholds, the renewal will be rejected.
Refer to one of the previous scenarios for the possible parameters and values.
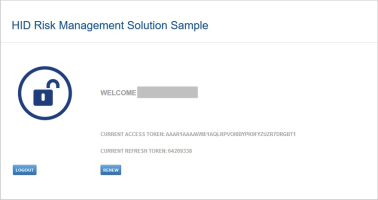
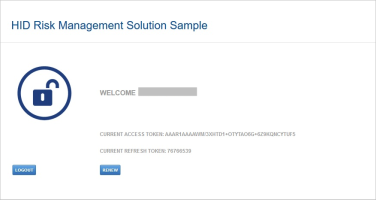
In the Welcome page, the current token value is displayed, as well as a Renew button to allow the user to renew their access_token.
The user clicks Renew.
HID RMS will then re-evaluate the risk score:
-
If the risk score does not exceed one of the reject or reject and block thresholds, the user is granted a new access_token and a new refresh_token:
-
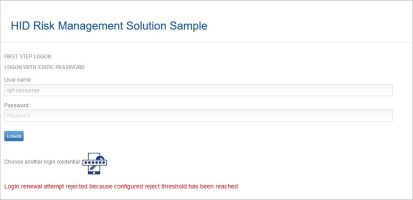
If the risk score exceeds one of the reject or reject and block thresholds, the renewal request will be rejected.
The user will be logged out and the login page will be displayed with an error message:
Eight: HID RMS Server Unreachable or Invalid Configuration for the Channel
When the user logs on via a channel where the HID RMS server cannot be reached, if the response cannot be read correctly, or if the RMS source is incorrectly configured, the response depends on the status of the Enable RMS fail-open… setting (see Bind the RMS Source to a Channel):
-
If the setting is enabled (default) for the channel, then the failure is ignored and the user is either prompted for a step-up authentication (if configured), or the authentication is accepted
-
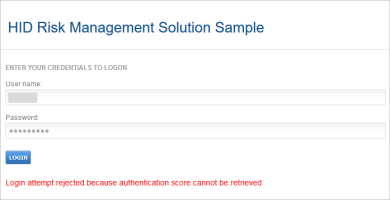
If the setting is disabled for the channel, a warning message is displayed
As the risk score cannot be retrieved, the logon request is rejected.