Configure the ActivID IdP Authentication Policies Mappings
Authentication policies mappings enable you to define the authentication methods used to authenticate a specific SP through the ActivID Authentication Portal. Authentication Policies Mappings establish a link between:
-
Authentication Class URI:
- Information on which Authentication Class to be used for authentication.
- It is optionally contained in the SP’s Authentication Request and/or in its metadata file.
-
Authentication Policy
-
GUI(s) template(s) to be displayed by the ActivID Authentication Portal for this authentication process.
For information on the association between the Authentication Policy and the GUI Template, see Supported Authentication Policies.
Add a New Authentication Policies Mapping
-
Log on as a configuration manager or administrator.
-
Navigate to Configuration, Identity Providers and then ActivID Identity Provider.
-
Go to the Login Pages section and click Add to create new authentication policies mapping.
-
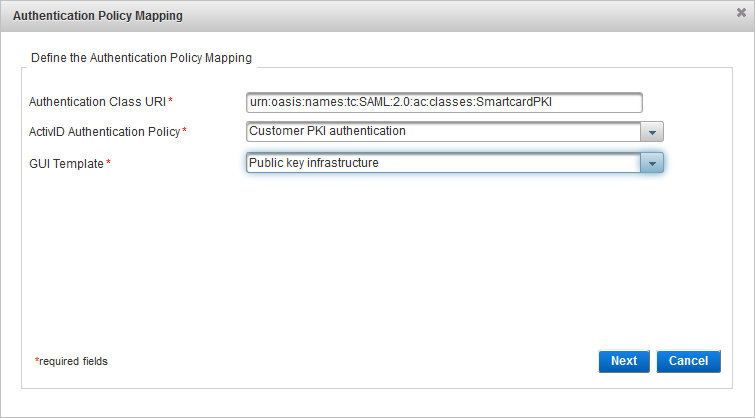
Enter the Authentication Class URI.
-
From the ActivID Authentication Policy drop-down list, select the authentication policy you want to map.
-
From the GUI Template drop-down list, select the template you want to map.
-
Click Next.
-
Review the new authentication policies mapping, and then click Ok to validate the configuration.
-
Click Save. It might take a few seconds for the changes to take effect.
To configure tiered authentication policy mappings, you are prompted to add more mappings. For more information on how to configure tiered authentication policy mappings, see Configure Tiered Authentication Policies Mapping.
Edit an Existing Authentication Policies Mapping
-
Log on as a configuration manager or administrator.
-
Navigate to Configuration, Identity Providers and then ActivID Identity Provider.
-
Go to the Login Pages section and click the Authentication Policy Mapping that you want to edit.

-
Click the Authentication Policy link (in bold) below the Authentication Class field.
-
Modify the ActivID Authentication Policy or GUI Template as required.
-
Click Next.
-
View the new mapping summary, and then click Ok to validate it.
-
Click Save. It will take a few seconds for the changes to take effect.

The list of Authentication Policies mappings is displayed with your changes.
Configure Tiered Authentication Policies Mapping
-
Log on as a configuration manager or administrator.
-
Navigate to Configuration, Identity Providers and then ActivID Identity Provider.
-
Go to the Login Pages section and click Add to create new authentication policies mapping.
-
Enter the Authentication Class URI.
-
From the ActivID Authentication Policy drop-down list, select the required policy.
-
From the GUI Template drop-down list, select the required template.
-
Click Next. You will be prompted to map the base Authentication Policy to a GUI template.
-
Select the required Authentication Policy and GUI Template, and then click Next.
-
To validate the tiered Authentication Policy mapping, click Ok.
-
Click Save. It will take a few seconds for the configuration changes to take effect.



The authentication policies mapping is created.
Configure Authentication Policies Mappings for the ActivID Management Console
Users can log on to the ActivID Management Console using their Username and password, Question and Answers (Q&A), PKI certificate, their One-time-Password (OTP) or Push Authentication.
This authentication policy mapping is available by default and is displayed as follows in the Authentication Policies mapping table in the ActivID Identity Provider details page:

By default, the Static Login GUI Template is the first one displayed on the ActivID Management Console login page.

To use Questions & Answers, PKI, One-Time-Password or Push Authentication to log on, the user can select the relevant icon at the bottom of the login page. Placing the cursor over the icon displays the icon name.
Upon subsequent logins, the last used template is displayed on the login page so that user will not have to select the icon again.
To add additional mappings corresponding to all authentication policies supported by the ActivID Management Console:
-
Log on as a configuration manager or administrator.
-
Navigate to Configuration, Identity Providers and then ActivID Identity Provider.
-
Add the mappings as required.
-
Save the changes. It might take a few seconds for the changes to take effect.
-
Log off and, if necessary, go to the login page again.
Configure Authentication Policies Mappings for the ActivID Self-Service Portal
Users can log on to the ActivID Self-Service Portal using their user names and passwords, Question and Answers (Q&A), PKI certificates, LDAP usernames and passwords, OOB One-Time Passwords, regular One-Time Passwords (OTP) or Push Authentication.
These authentication policies mappings are available by default and are displayed as follows in the Authentication Policies mapping table:
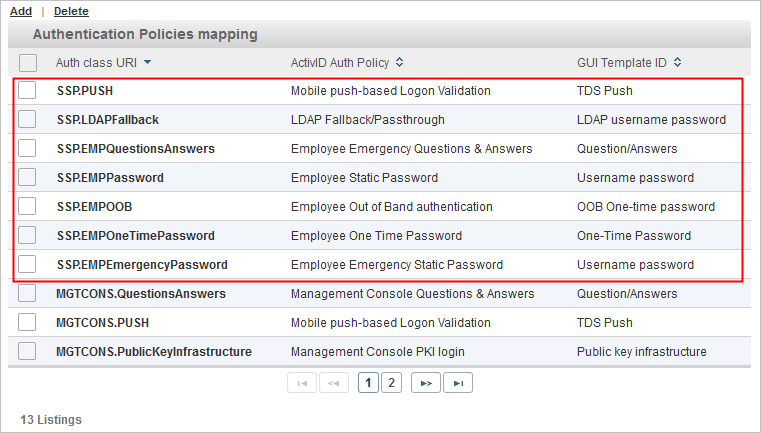
You can add additional mappings if required.
Configure Authentication Policies Mappings for Other Service Providers
Each Service Provider might support an Authentication Context with particular SAML Authentication classes. You must identify them, verify that they are enabled for the Service Provider, and create the mappings accordingly.
The following table lists several examples (for an OPENSSO Implementation) of mappings that can be used.
| SAML Authentication Classes | Authentication Policy | GUI Template | Device Used |
|---|---|---|---|
|
Password Identified when a user authenticates to an IdP by using a password over an unprotected HTTP session |
Static Password |
Seeded Username Password |
none |
|
PasswordProtectedTransport Identified when a user authenticates to an IdP by using a password over an SSL-protected session |
Static Password |
Username Password |
none |
|
SmartCardPKI Identified when a user uses a smart card with an enclosed private key and a PIN to authenticate to an IdP |
PKI |
Public key infrastructure |
SmartCard |
|
MobileOneFactorContract*Identified when a mobile user has an identity for which the IdP has vouched |
One Time Password |
One Time Password |
Mobile Soft token without PIN |
|
HID Approve™ container on Smartphone |
|||
|
MobileTwoFactorContract Identified when a mobile user has an identity for which the IdP has vouched |
One Time Password |
Challenge Response |
Mobile Soft token with PIN |
|
One Time Password |
HID Approve container on Smartphone (password protected) |
||
|
Mobile push-based Logon Validation |
TDS Push |
HID Approve container on Smartphone (password protected) |
|
|
Push-Based Authentication |
HID Approve container on Smartphone (password protected) |
For example, if your SP supports an Authentication Context with the Authentication Classes Password and SmartCardPKI, you can map the ActivID IdP Authentication Policies as follows:
-
Auth Class URI: urn:oasis:names:tc:SAML:2.0:ac:classes:Password
- Authentication Policy: Customer Static Password
- GUI Template: Username password
-
Auth Class URI: urn:oasis:names:tc:SAML:2.0:ac:classes:SmartCardPKI
- Authentication Policy: Customer PKI authentication
- GUI Template: Public key infrastructure
See also:





