Configuring Object Request Support
You can configure support for OpenID request objects using either the ActivID Management Console or OpenID dynamic client registration API.
Using the ActivID Management Console
-
Log on to the ActivID Management Console as an ActivID Administrator (for example, ftadmin).
-
Select the Configuration tab and, under Environment, select Adapters.
-
Create an OpenID adapter or edit an existing one (for example, OpenID_admin) where:
-
Name – mandatory and should be unique for ease of administration.
-
Description – a user-friendly description of the adapter (optional).
-
Adapter Type – select Process to send notifications of operational events (such as user validations).
- Adapter Category – select OpenID client (organization) configuration as the definition of the adapter.
-
-
Configure the main parameters (channels, authentication policies, …) as described in Create the OpenID Administrator for Dynamic Registration.
-
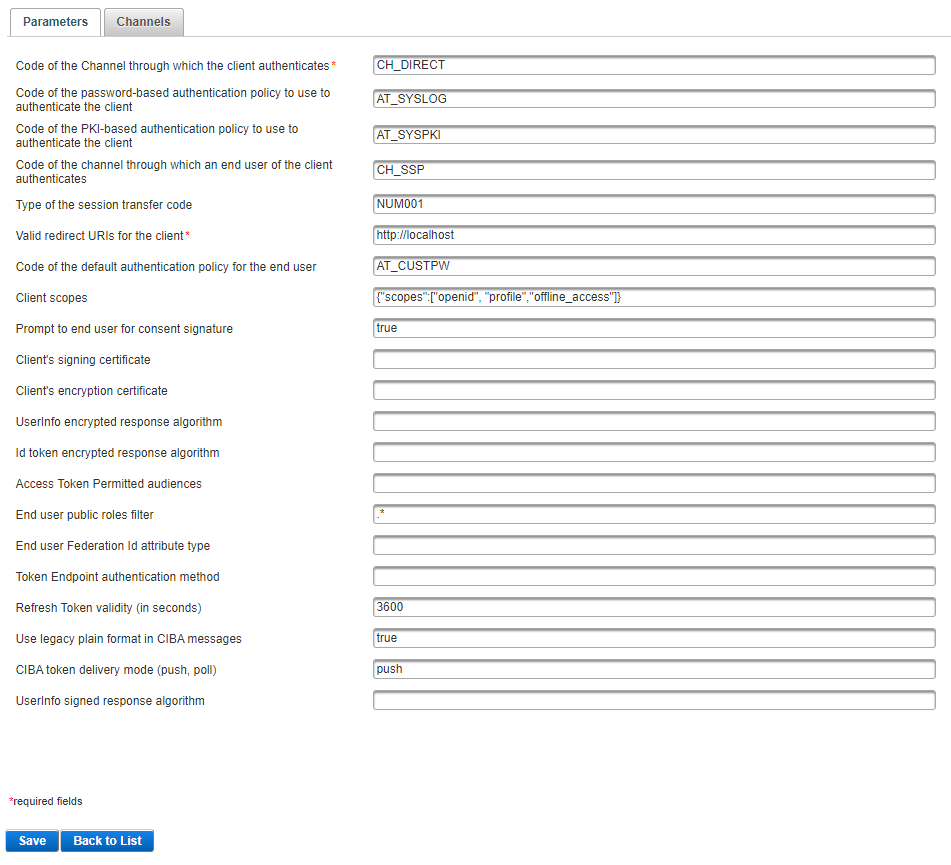
Enter the values for the following parameters:
-
Client's signing certificate - the client’s signature certificate used to verify a signed request object
-
Client's encryption certificate - the client’s encryption certificate used to encrypt the ID Token in the token endpoint response or the UserInfo response. If empty, the response is not encrypted.
-
UserInfo encrypted response algorithm - the algorithm to encrypt the UserInfo response. The recommended algorithm is RSA-OAEP-256.
If this field is empty, the response is not encrypted.
- UserInfo signed response algorithm – the algorithm to sign the UserInfo response:
If empty, the JWT response is not signed.
If set to RS256, the JWT response is signed by the Identity Provider’s signature key (that is advertised in the JWKS endpoint) with RS256 algorithm.
-
Id token encrypted response algorithm - the algorithm to encrypt id_token in the token endpoint response. The recommended algorithm is RSA-OAEP-256.
If this field is empty, id_token is not encrypted.
-
-
Click Save.
Using OpenID Dynamic Client Registration API
The Client's signing or/and encryption certificate can be registered via dynamic client registration API. The jwks parameter can contain a list of keys (X.509 certificates).
The following parameters are taken into account and saved during dynamic registration to OpenID client's configuration:
-
userinfo_encrypted_response_alg – the JWE algorithm [JWA] required for encrypting the UserInfo response.
If both signing and encryption are requested, the response will be signed then encrypted, with the result being a Nested JWT, as defined in [JWT]. If not present, the response is not encrypted.
-
id_token_encrypted_response_alg – the JWE algorithm [JWA] required for encrypting the ID Token issued to this client.
If this is requested, the response will be signed then encrypted, with the result being a Nested JWT, as defined in [JWT]. If not present, the ID Token is not encrypted.
- userinfo_signed_response_alg – algorithm to sign the UserInfo response:
If not present, the JWT response is not signed.
If set to RS256, the JWT response is signed by the Identity Provider’s signature key (that is advertised in the JWKS endpoint) with RS256 algorithm.
Optional certificates:
-
Certificate to be used for PKI authentication if required (jwk "use" attribute value should be null, (that is, no “use” attribute)).
-
The signing certificate used to verify the signature of request object (jwk “use” attribute value should be sig).
-
The encryption certificate used to encrypt the response for the token endpoint (if an id_token is included in the response) or userInfo endpoint response to the client (jwk "use" attribute value should be enc).
For example:
{
"client_id": "client9",
"id_token_encrypted_response_alg": "RSA-OAEP-256",
"userinfo_encrypted_response_alg": "",
"jwks" : {"keys":[{"kty":"RSA","x5t#S256":"ZFgZlr5qYFHyWtKzsHk1rja2chRcshc4NrWkYFrvoio","e":"AQAB","use":"sig","kid":"379112668518902081505018885217414831543418907","x5c":.......}
...
}




