Configuring the ActivID CMS User Portal
The User Portal Configuration page enables you to set parameters for:
-
Device issuance,
-
Help Desk operations,
-
Automatic update operations,
-
Initial password distribution, and
-
Escrowed certificate download.
In addition, you can configure the ActivID CMS User Portal Start page. For details, see Configure the Start Page.
Configure the ActivID CMS User Portal
-
Select the Configuration tab, and then click the User Portal sub-tab:
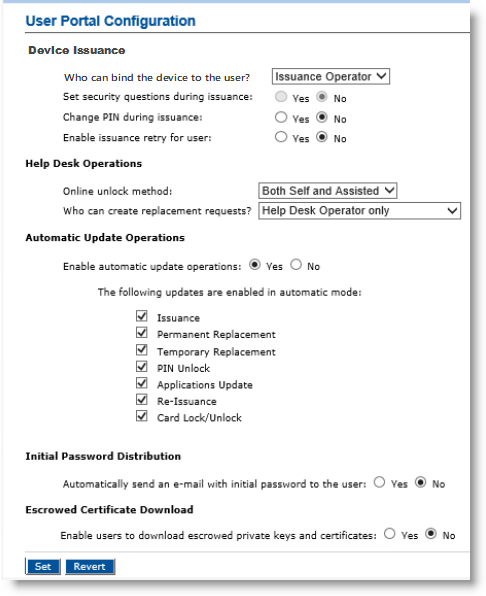
-
From the Who can bind the device to the user? drop-down list, select one of the following options:
-
Issuance Operator—An Issuance operator binds a device to a user before it is given to the user.
- User—The user can bind the device during self-enrollment.
Giving the user the rights to bind devices reduces the operator’s workload, but it also reduces the control over the devices distributed. For more information, see Binding a Device.
Important: When working with virtual smart cards, you must select User from the Who can bind the device to the user? drop-down list as the binding operation is done automatically during self-issuance. Operators cannot bind a virtual smart card in advance. For more information, see Prerequisites for Using Virtual Smart Cards. -
-
For the Set security questions during issuance option, select Yes if you want the user to initialize the security questions at the end of the self-enrollment process.
-
For the Change PIN during issuance option, select Yes if you want the operator to request the user to enter their final PIN at the end of the local issuance.
-
For the Enable issuance retry for user option, select Yes if you want to users to be able to retry issuance or update operations from the User Portal. For details, refer to the ActivID CMS User online documentation.
-
From the Online unlock method drop-down list, select one of the following options:
-
Self Online Only—The user can unlock the device without the help of a Help Desk operator.
-
Assisted Online Only—A Help Desk operator must create an unlock request before the device can be unlocked using the ActivID CMS User Portal. In this case, the end user will have to contact the Help Desk to unlock the device. Select this method if you want ActivID CMS operators to have increased control over device unlock processes.
- Both Self and Assisted—Enable both of the above methods.
-
This setting also applies to reset PIN feature.
-
When working with virtual smart cards, select Both Self and Assisted.
Note: -
-
From the Who can create replacement requests? drop-down list, select the person who can create replacement device requests:
-
Help Desk Operator only—A user must declare a device incident through the ActivID CMS User Portal, and a Help Desk operator must create a device replacement request. The issuance then takes place locally or using self-enrollment.
-
User only—A user can create the replacement device request. Once this request is approved by an ActivID CMS operator, the issuance can take place locally or using self-enrollment. A device replacement request is automatically created.
- Both Help Desk Operator and User—Both the Help Desk operator and a user can create a replacement request.
Note: When working with virtual smart cards, select Both Help Desk Operator and User.For details on the replacement processes, see Issuing a Replacement Device.
-
-
For the Enable automatic update operations option, select Yes if you want to enable device automatic update operations. Then, select the updates you want to enable. For detailed information about automatic updates, refer to ActivID ActivClient Smart Card Auto Update.
-
For the Automatically send an email with initial password to the user option, select Yes or No for the automatic sending of the Initial password by email.
If you select Yes, then the following mandatory fields appear:
Enter the SMTP Host hostname or IP address.
Enter the name of the Sender who will appear in the email.
Enter the Subject of the email containing the initial password.
- Enter the Body of the email and use the keyword INITIAL_PASSWORD. The system will automatically replace this password with the user’s real initial password just before sending the email.
-
For the Escrowed Certificate Download option, select Yes to enable end users to download escrowed private keys and certificates using the ActivID CMS User Portal.
-
Optionally, click Revert to go back to the previously saved settings.
-
Click Set.
Configure the Start Page
The Welcome page appears automatically in a separate window:
You can configure the default start page by changing the configuration parameters.
If the configuration parameter (ForceStartPage) is set to true, any user trying to access the /user URL is redirected to a custom ActivID CMS User Portal start page at the URL /myDigitalIDCard. This URL requires SSL server authentication and is directed to a dedicated HTML page named: System_Use_Notification.html.
Location of Sample Start Page
The sample start page is located here:
cms_install_dir\aims.war\html\MDIDC\System_Use_Notification.html
For more information, refer to the ActivID CMS User online documentation.
ActivID CMS User Portal Services
When a user connects to the ActivID CMS User Portal, the choice of services displayed depends on the state of the device and the User Portal configuration. The following table lists all the ActivID CMS User Portal services.
|
Device State and ActivID CMS User Portal Configuration |
Service Provided by the ActivID CMS User Portal |
|---|---|
|
Device has not been bound and not assigned to a user |
|
|
Blank device is inserted into the reader, but device binding has not been authorized for the user. |
Not available – an error message appears. |
|
Blank device is inserted into the reader and device binding has been authorized for the user. |
The User Portal executes a device issuance request or device replacement request. This service is LDAP Lightweight Directory Access Protocol password- protected; no other authentication method is allowed. |
|
Device is bound but device has not been issued |
|
|
Blank device is inserted into the reader. Configurable authentication methods are:
|
The User Portal executes a device issuance request or device replacement request. |
|
Device is bound and issued, but is in LOST, STOLEN or DAMAGED state, or has been terminated |
|
|
Device is inserted into the reader. |
Not available – an error message appears. |
|
Device is locked |
|
|
Device is inserted into the reader. Device unlock process can be configured in Assisted online or Self online mode. Configurable authentication methods are:
|
The User Portal executes a device unlock request. When a device update request is pending, the unlock request is not executed; instead, you must delete the pending Device Update request.
|
|
Device is operational (bound, issued, in valid state) and user wants to reset a forgotten PIN |
|
|
Device is inserted into the reader. Device reset process can be configured in Assisted online or Self online mode or both. Configurable authentication methods are:
|
The User Portal executes a Device Reset PIN request. User can change the PIN even if the device is not locked. |
|
Device is operational (bound, issued, in valid state), no device is inserted into the reader |
|
|
Configurable authentication methods are:
|
The User Portal allows user to enter a device incident. When the device incident report functionality is not configured, this service is not available. |
|
Device is operational (bound, issued, in valid state), FIPS-196-based authentication is available |
|
|
Device is inserted into the reader. The authentication method is device PIN and FIPS-196 authentication. The FIPS-196-based authentication requires the device to contain at least one ActivID CMS-managed certificate and PIN-protected PKI key pair. |
The User Portal executes any pending device update requests. Portal executes any pending device re-issuance requests. Users can:
|
|
Device is operational (bound, issued, in valid state), FIPS-196-based authentication is NOT available |
|
|
Device is inserted into the reader. The authentication method is a device PIN. If FIPS-196-based authentication is not available, then the services of device re-issuance and security question answer changes are not available. |
The User Portal executes any pending device update requests. Users can change their PIN code and download escrowed certificates. |
Virtual smart cards are considered as always present/detected in the card reader and can only be self-issued by the user.
YubiKey devices inserted in the client machine appear as a card reader with a card inserted.
For more details, see Managing Virtual Smart Cards or Managing YubiKeys.





