Procedure 8: Configure File Logging and Email Logging
The Configure Logging page enables you to specify the minimum severity level of events that are recorded in the log file, the maximum size that the current log file can become, and the maximum number of past log files that the Validation Responder Appliance will retain, as well as the parameters for sending email messages to specified recipients when events of a particular severity occur.
-
In the Responder Software section of the navigation bar, click Logging. File Logging appears at the top of the Configure Logging page.
-
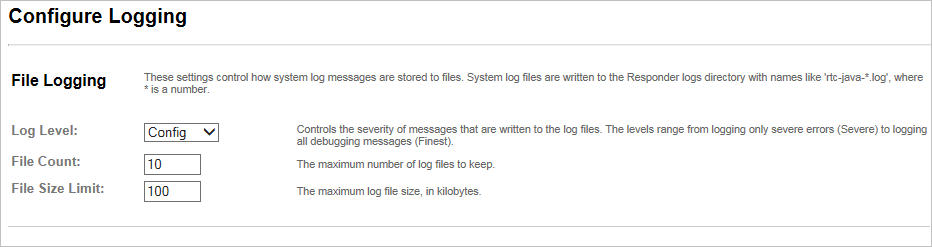
Specify the following File Logging information:
-
Log Level specifies the minimum level of log events that will be written to the responder log files. Log messages at a level lower than this value will not be written. The default setting is Config.
Important:Be very careful when you enable debug logging (that is, logging at levels FINE, FINER, and FINEST). Logging impacts overall responder performance. You should only enable debug logging when advised to do so by support personnel.
If you enabled debug logging, then to disable it, select Severe, Warning, Info, or Config from the Log Level drop-down list, and then click Update Configuration at the bottom of the page.
-
File Count specifies the number of system log files that should be kept. As additional log files are created, older log files are discarded. In the default configuration, the 10 most recent log files are available. The default setting is 10.
-
File Size Limit specifies the maximum size, in kilobytes, of system log files. Once a log file reaches the maximum size, it is closed and a new log file is created. In the default configuration, log files are rolled over when they reach the File Size Limit. The default setting is 100000 (100kb).
Email Logging appears at the bottom of the page, as illustrated next.
-
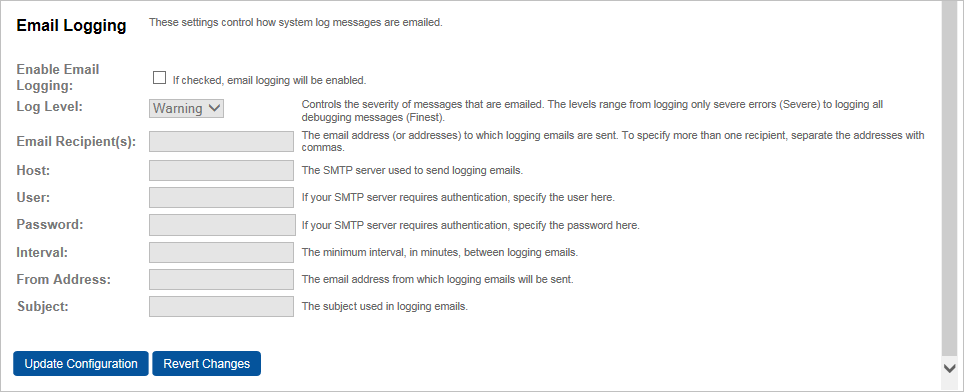
Select the option to Enable Email Logging, and then specify the following:
-
Log Level specifies the minimum level of system log events that are sent. To avoid a large number of unnecessary emails, set this level to Warning or higher.
-
Email Recipient(s) specifies a comma-delimited list of email addresses to which log messages should be sent.
-
Host specifies the mail server through which the email should be sent.
-
User specifies the user name used, if necessary, to authenticate to the mail server when sending email. Many mail servers do not require authentication.
-
Password specifies the password used, if necessary, to authenticate to the mail server when sending email. Many mail servers do not require authentication.
-
Interval specifies the minimum interval, in seconds, between emails sent. Log events are aggregated and sent in a single email at the frequency specified by this property. This prevents recipients from receiving too many emails.
-
From Address specifies the address from which logging event emails will appear to come.
-
Subject specifies the email subject line used in logging event emails. Use this to identify the originating system in the event that your site includes multiple Validation Responder Appliances.
-
Click Update Configuration.
-
In the Responder Software section of the navigation bar, click Restart.
Basic configuration procedures are completed at this point. After you restart the appliance, click View Responder Status to check/confirm the configuration parameters. For details, see section View Responder Status Page.





