Configuring PIN
PINs provide a secure and more convenient alternative to passwords for authentication, enabling quicker logins without the usual complexity requirements. The Administration Portal allows an administrator to configure and manage the settings of PIN profiles for authentication.
This explains how an OpenID application can specify a PIN to be used for enrollment and end-user authentication. You need to enable the PIN before enrolling them for users.
In order to enable and configure the PIN profiles, follow the below steps:
-
Click Settings
in the left navigation bar to open the Settings page.
-
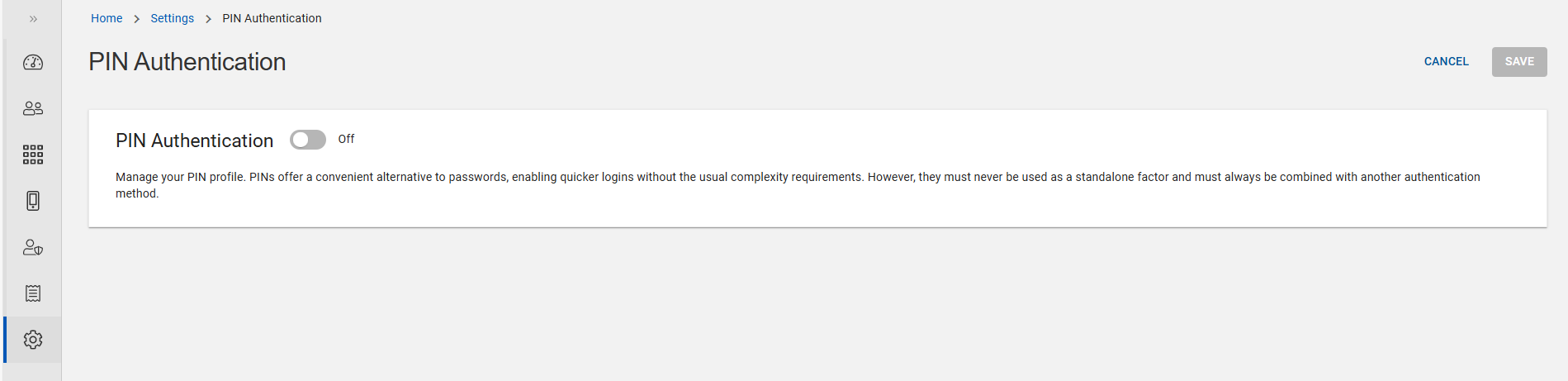
Click PIN on the Settings page, then PIN Authentication page opens.
-
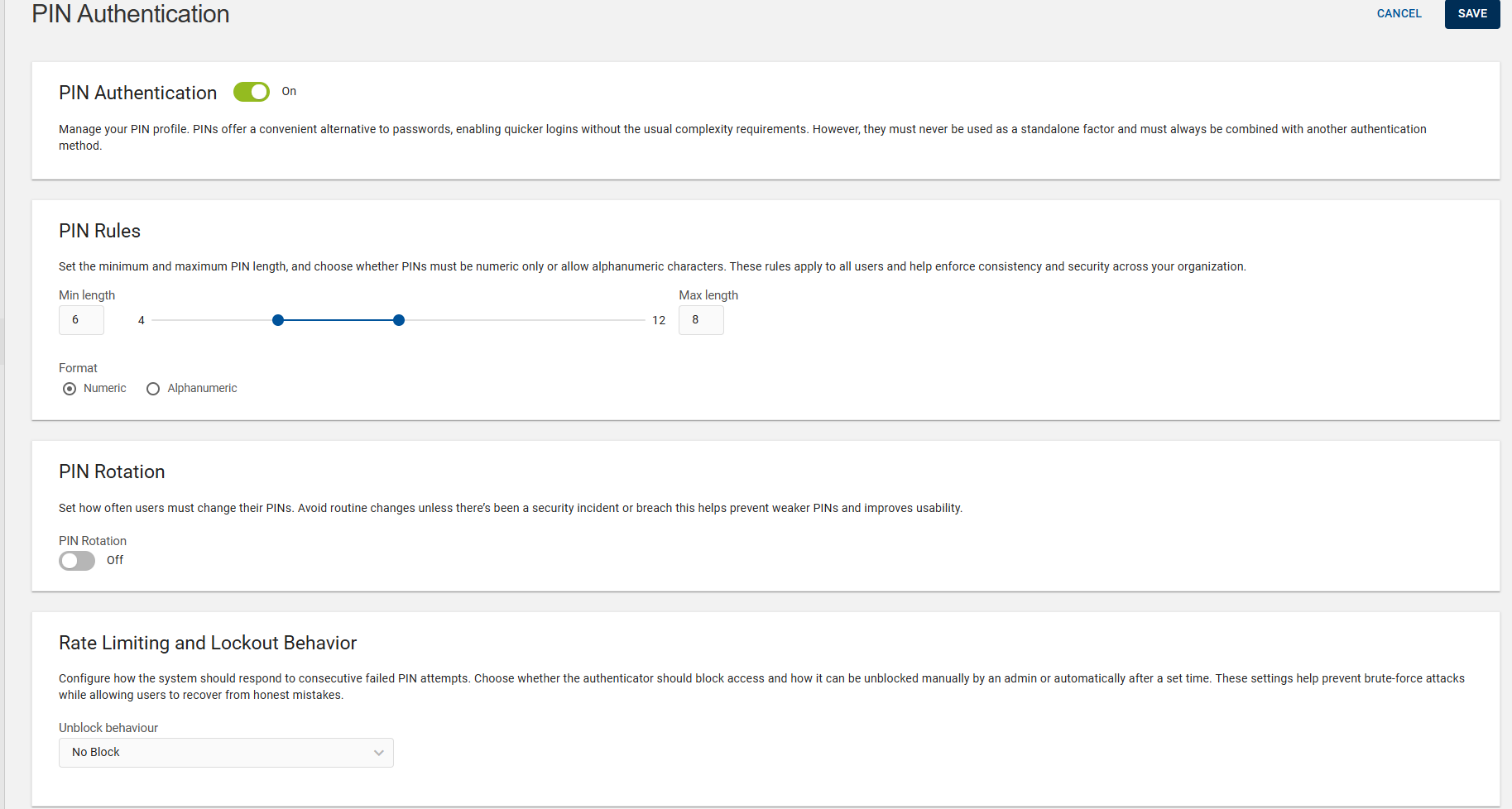
Click the toggle button to On and enable it to allow users to enroll a PIN through the Self-Service/Administration Portal. Enabling PIN will apply a global PIN profile to all applications and user types where PIN is used as one of the factors within Multi-Factor Authentication.
Important: If you click the toggle button to Off, it prevents users from signing in with a PIN across all applications. It also prevents users from authenticating with any previously enrolled PINs. -
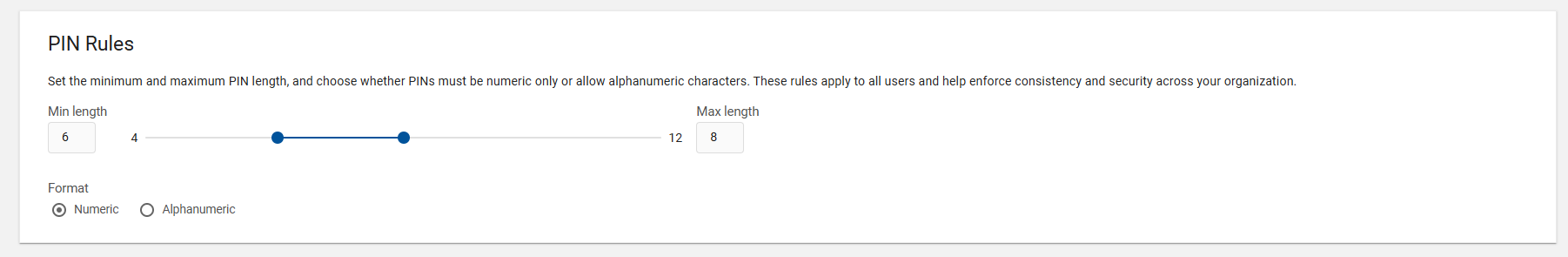
To ensure security and usability, you can set the PIN rules such as minimum/maximum PIN length and formats of PIN as mentioned the constraints below:
-
Min length: The minimum number of the characters required for the PIN (default is 6). You can also set the minimum value to 4.
-
Max length: The maximum number of the characters allowed for the PIN (default is 12).
-
Format: The allowed format of the PIN (Numeric or Alphanumeric). The default format is Numeric.
-
-
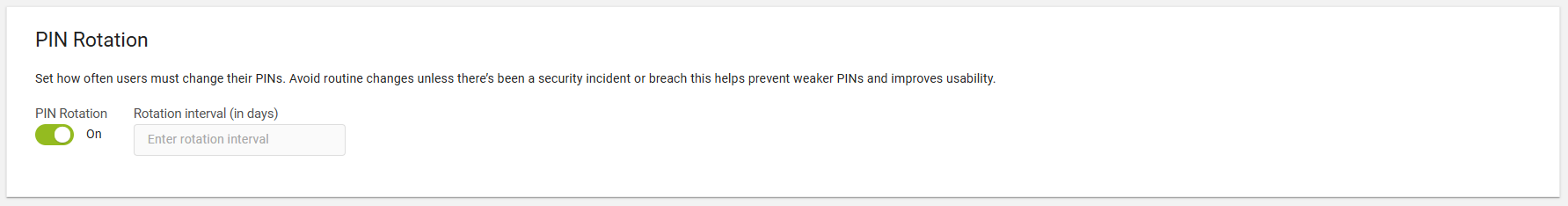
To enhance security, users must change their PIN after a defined period (e.g., every 1825 days). PIN rotation reduces the risk of unauthorized access by ensuring that PINs are regularly updated.
Note: Avoid enforcing routine changes of PIN unless a security incident or breach occurs, as this approach helps prevent the selection of weaker PINs and enhances usability.Click the toggle button to On to define the PIN rotation interval (in days).
-
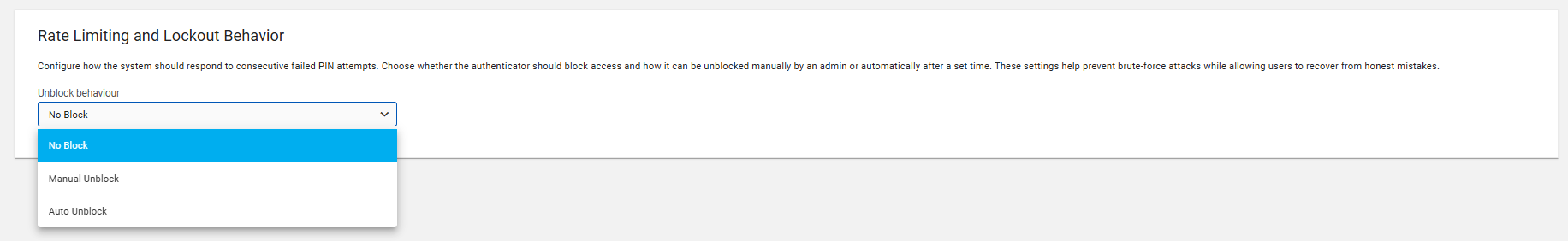
Configure how the system should react if someone enters consecutive incorrect PIN entries too many times. You can choose:
No Block: The system does not block access, no matter how many incorrect PIN attempts are made.
Manual Unblock: After too many wrong attempts, access is blocked, and an administrator must manually unblock the user’s account.
Auto Unblock: After a set number of failed attempts, access is temporarily blocked. The system will automatically unblock the account after a defined period (e.g., 15 minutes), allowing the user to try again.
-
Click SAVE and a message will appear confirming that the PIN authentication configuration has been successfully completed.