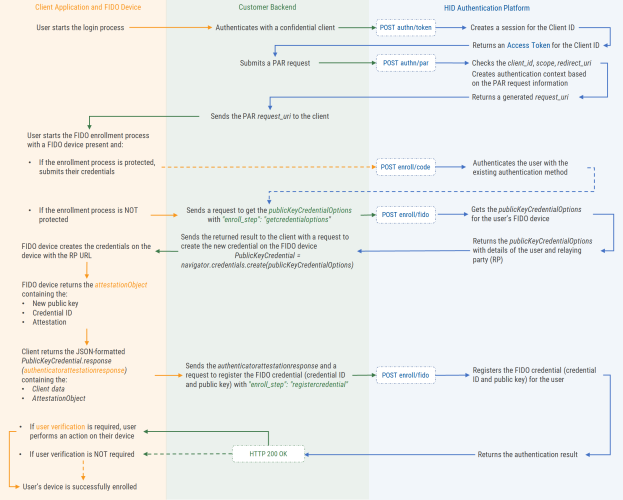
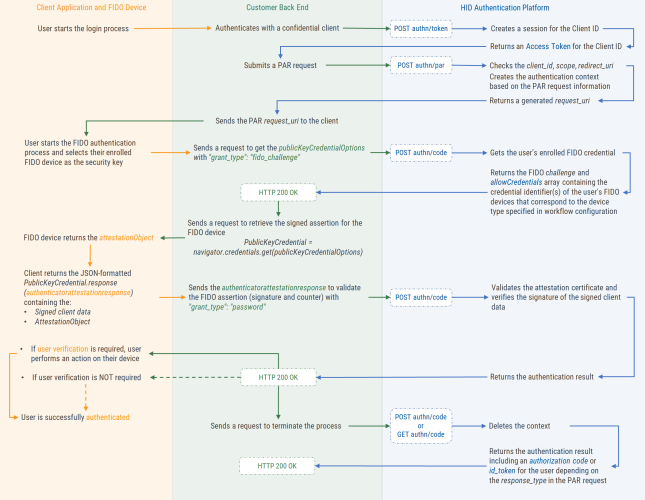
API Integration Flows
The following sections illustrate the authentication flows with client applications by integrating the various HID Authentication Service API endpoints.
In these flows, the client application calls the APIs via the customer back end with an authenticated client. This client submits a PAR request based on which the HID Authentication Service generates the request_uri for the end user authentication process.
Enable the Authentication Flow
As an integrator, you can enable the APIs to deploy authentication workflows for a custom front-end application, leveraging the various elements of the HID Authentication Service workflows.
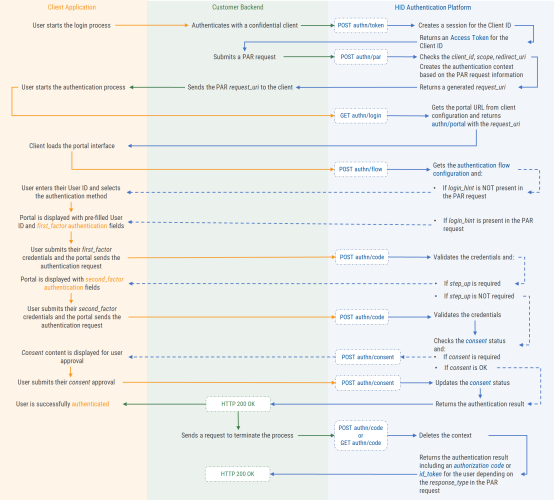
Push Authentication Request
The Service Provider (SP) creates the authorization request and sends users to the authentication portal using the par endpoint.
Create authorization request
POST https://[base-server-url]/tenant/authn/par HTTP/1.1
Content-Type: application/x-www-form-urlencoded
Authorization: Bearer RTp7HwAAAXyStuhFZfZf2g4BQmVj1yf84hUvta3j
scope=openid accounts payments
&response_type=code id_token
&login_hint=5619630280
&nonce=n-0S6_WzA2Mj
&client_id=spl-pisp
&redirect_uri=https://<localhost>
&request=CJleHAiOjE0OTUxOTk1ODd...JjVqsDuushgpwp0E.5leGFtcGxlIiwianRpIjoiM...JleHAiOjE0.olnx_YKAm2J1rbpOP8wGhi1BDNHJjVqsDuushgpwp0EPAR Response
HTTP/1.1 200 OK
Cache-Control: no-cache, no-store
Content-Type: application/json
{
"request_uri": "urn:hid:43d5b009-7b52-4d6f-a8a9-0d8de27968f9",
"expires_in": 300
}Authentication Request
The Service Provider (SP) delegates the authentication to the HID Authentication Service using the login endpoint.
HID Authentication Service supports two modes:
-
Using the par endpoint request_uri parameter where the SP must be pre-authenticated to the HID Authentication Service and the parameters are hidden (POST request)
CopyInitiate Authentication by PAR request
GET https://[base-server-url]/tenant/authn/login?request_uri=urn:hid:43d5b009-7b52-4d6f-a8a9-0d8de27968f9&client_id=spl-pisp -
Using the login endpoint for 'standard' mode where all the required parameters are sent in the query and visible in the GET query string
For example, the boostrap URL for standard flow will be:
CopyGET https://[base-server-url]/tenant/authn/login?
state=VzRP4nD6iKCKPuRi
&nonce=rgu1VjOl2J0HHItd
&response_type=code,id_token
&scope=openid
&redirect_uri=https://<localhost>
&client_id=spl-api
&login_hint=myuseridNote: The above URL contains only required parameters for illustration, the other optional parameters are also supported.
The response from HID Authentication Service sends the user to the authentication portal as defined in the URL configured for the OpenID client application, including the theme identifier for the required interface design.
Sample response to authorization request
HTTP/1.1 302 Found
Location: https://[base-server-url]/authn/portal?theme_id=ID_THEME1&request_uri=urn:hid:43d5b009-7b52-4d6f-a8a9-0d8de27968f9
Set-Cookie: server-csrf-token= urn:hid:256ab6ef-12c4-47e3-b220-0e96c161d283; Domain=<svcaddress>; Path=/; Expires=Sun, 14 Nov 2021 22:23:01 GMT; Secure; SameSite=StrictClient gets the portal design (theme)
GET https://<portaladdress>/<tenant>/authn/portal?theme_id=ID_THEME1?request_uri=urn:hid:43d5b009-7b52-4d6f-a8a9-0d8de27968f9Response
HTTP/1.1 200 OK
{
"localization": {
"extensions": {},
"hid_portal": {
"en": {
"userid.error.required": "Username is required.",
"OOB.methods.sms": "Receive OTP by SMS",
"OTP.input.otp.label": "One-Time Password",
"PUSH.error.defaultmessage": "Push logon request failed.",
"ENROLL_FIDO.error.not_supported": "This client does not support the Web Authentication API!",
"PKI.error.defaultmessage": "Invalid certificate.",
"CHANGE_PWD.title": "Change Password",
"LOGIN.input.password.tooltip": "Enter your password",
"CODE.error.defaultmessage": "Invalid Username or Activation Code.",
"FORGOT_PWD.input.new_password.error.short": "New password is too short.",
"FORGOT_PWD.input.confirm_password.error.required": "Confirm password is required.",
"pwd_constraints.notOldPassword": "Cannot be a previous password",
"FORGOT_PWD.methods.input.sms.error.too_long": "Phone number is too long.",
"OTP.input.otp.error.required": "One-Time Password is required.",
"login.error.password.expired.title": "Password expired!",
"LOGIN.tooltip": "Authenticate using your password",
"PUSH.tooltip": "Authentication using a push logon request on your device",
"OOB.methods.email.otp.message.2": "Check your email and enter your OTP.",
"OOB.methods.email.otp.message.1": "We emailed you the OTP.",
"PKI.instructions": "Click Next to connect using a certificate.",
"pwd_constraints.notUserAttribute": "Cannot contain a user attribute",
"FORGOT_PWD.input.new_password.label": "New password",
"LDAP.error.defaultmessage": "Invalid Username or Password.",
"FIDO.tooltip": "Authenticate using FIDO",
"notification.error": "Error!",
"FORGOT_PWD.methods.email": "Receive by email",
"userid.placeholder": "Enter your username",
"pwd_constraints.numAndAlpha": "Numbers AND letters",
"login.error.password.expired.message": "Your password must be changed.",
"FIDO.enroll_action.separator": "OR",
"FORGOT_PWD.input.temp_password.error.required": "Temporary password is required.",
"cancel_button": "Cancel",
"pwd_constraints.atLeastOneUp": "At least one uppercase character",
"FORGOT_PWD.input.new_password.error.required": "New password is required.",
"ENROLL_FIDO.instructions": "Connect your FIDO key, click Next, and follow the instructions given by your browser.",
"login.error.invalidurl": "Invalid access request.",
"CHANGE_PWD.input.old_password.error.required": "Password is required.",
"notification.success": "Success!",
"FIDO.instructions": "Connect your FIDO key, click Next, and follow the instructions given by your browser.",
"submit_button": "Submit",
"OOB.name": "Out Of Band",
"FIDO.error.not_supported": "This client does not support the Web Authentication API!",
"LDAP.expiry.warning": "Your password will expire soon.",
"CHANGE_PWD.input.old_password.placeholder": "Enter your current password",
"pwd_constraints.numOrAlpha": "Numbers OR letters",
"PUSH.deviceitem.unnamed": "Unnamed device",
"consent.confirm.button": "Accept",
"login.error.emptyfactor": "No authentication option available.",
"LOGIN.input.error.required": "Password is required.",
"copycut.warning": "The copy and cut actions are not allowed from this field.",
"CHANGE_PWD.tooltip": "Click to change password",
"consent.title": "Consent",
"pwd_constraints.atLeastOneSpecial": "At least one special character",
"ENROLL_FIDO.success.message": "Your FIDO device has been successfully registered.",
"service_name": "HID Authentication Service",
"CHANGE_PWD.input.new_password.label": "New password",
"OTP.error.defaultmessage": "Invalid Username or One-Time Password.",
"LOGIN.input.password.label": "Password",
"OTP.tooltip": "Authenticate using an OTP generated on your device",
"PUSH.confirmationsent.notice": "To finalize your login, an authentication confirmation was sent to your device.",
"FIDO.submit.button": "Next",
"LOGIN.action.change_password.separator": "OR",
"FORGOT_PWD.reset.title": "Password Reset",
"LDAP.tooltip": "Authenticate using your corporate password",
"OOB.input.otp.tooltip": "Enter the received OTP",
"CHANGE_PWD.input.confirm_password.placeholder": "Enter your new password",
"service_tagline": "Rapidly build and deliver trusted identity solutions",
"PKI.tooltip": "Authenticate using PKI",
"FORGOT_PWD.methods.input.sms.tooltip": "Enter your mobile phone number",
"OOB.error.nomethod.message": "No Out Of Band method has been found to deliver the OTP.",
"OTP.name": "One-Time Password",
"LOGIN.input.error.short": "Password is too short.",
"CHANGE_PWD.input.confirm_password.error.required": "Confirm password is required.",
"login_title": "Sign in",
"LOGIN.submit.button": "Next",
"FORGOT_PWD.methods.input.email.placeholder": "Enter your email address",
"CHANGE_PWD.input.old_password.label": "Current password",
"CODE.input.error.required": "Activation code is required.",
"FIDO.error.defaultmessage": "Invalid FIDO credential.",
"CODE.methods.email": "Receive OTP by email",
"PUSH.submit.button": "Next",
"FORGOT_PWD.methods.input.sms.error.invalid": "Phone number is invalid.",
"FORGOT_PWD.input.temp_password.placeholder": "Enter the received temporary password",
"OOB.input.otp.placeholder": "Enter the received OTP",
"PUSH.sendtodevice.notice": "Click next to receive a push logon request on your device.",
"CHANGE_PWD.input.confirm_password.label": "Confirm your new password",
"FORGOT_PWD.methods.input.sms.error.not_mobile": "Not a mobile phone number.",
"redirect.message": "You will be securely redirected to your service provider.",
"FORGOT_PWD.methods.input.email.tooltip": "Enter your email address",
"pwd_constraints.onlyNum": "Only numbers",
"LDAP.expiry.warning.notice": "You can change your password now or click Next to continue.",
"LOGIN.expiry.warning.notice": "You can change your password now or click Next to continue.",
"pwd_constraints.minDiffChars": "Minimum number of different characters",
"FIDO.enroll_action.tooltip": "Click to enroll your FIDO device",
"PKI.submit.button": "Next",
"FIDO.enroll_action.link": "Enroll your FIDO device",
"copyright": "HID Global Corporation/ASSA ABLOY AB. All rights reserved.",
"LOGIN.action.change_password.link": "Change your password",
"CODE.submit.button": "Next",
"LDAP.input.password.tooltip": "Enter your corporate password",
"CHANGE_PWD.input.old_password.tooltip": "Enter your current password",
"pwd_constraints.minLength": "Minimum length",
"CODE.input.code.label": "Activation code",
"OOB.tooltip": "Authenticate using an OTP sent Out Of Band",
"login.error.badconfiguration": "Unable to proceed. Please contact your administrator.",
"CHANGE_PWD.input.new_password.tooltip": "Enter your new password",
"login.error.maxretry": "Maximum retries reached.",
"LDAP.input.error.short": "Password is too short.",
"LOGIN.input.password.placeholder": "Enter your password",
"CHANGE_PWD.success.message": "Password is changed.",
"select_factor.label": "Select an authentication method",
"pwd_constraints.notSequence": "Cannot contain sequences",
"FORGOT_PWD.input.temp_password.label": "Temporary password",
"OOB.input.otp.error.required": "One-Time Password is required.",
"PUSH.approve.prompt": "Please approve this operation.",
"CHANGE_PWD.input.new_password.placeholder": "Enter your new password",
"OOB.submit.button": "Next",
"FORGOT_PWD.methods.input.sms.error.required": "Phone number is required.",
"FORGOT_PWD.input.temp_password.tooltip": "Enter the received temporary password",
"CHANGE_PWD.input.new_password.error.short": "New password is too short.",
"FORGOT_PWD.methods.label": "Select how you want to receive a temporary password",
"CODE.error.nomethod.message": "No Out Of Band method has been found to deliver the OTP.",
"OTP.input.otp.placeholder": "Enter OTP displayed on your device",
"login.error.unexpected": "Unexpected error!",
"FORGOT_PWD.request.title": "Forgot Password?",
"CHANGE_PWD.input.confirm_password.tooltip": "Enter your new password",
"next_button": "Next",
"PUSH.error.timeout": "The approval for your authentication could not be received. Please retry.",
"CHANGE_PWD.input.new_password.error.required": "New password is required.",
"FORGOT_PWD.input.temp_password.error.short": "Temporary password is too short.",
"OOB.methods.email": "Receive OTP by email",
"OOB.error.failotp": "Failed to send OTP.",
"notification.warning": "Warning!",
"FORGOT_PWD.reset.tooltip": "Click to set the new password",
"LOGIN.action.forgot_password.link": "Forgot your password?",
"CODE.methods.sms": "Receive OTP by SMS",
"OTP.input.otp.tooltip": "Enter OTP displayed on your device",
"FORGOT_PWD.input.confirm_password.error.nomatch": "Passwords do not match.",
"userid.label": "Username",
"CODE.input.code.tooltip": "Enter your activation code",
"LDAP.input.password.label": "Corporate Password",
"CODE.input.code.placeholder": "Enter your activation code",
"FIDO.name": "FIDO",
"CHANGE_PWD.input.old_password.error.short": "Current password is too short.",
"pwd_constraints.atLeastOneNum": "At least one number",
"FORGOT_PWD.input.confirm_password.tooltip": "Enter your new password again",
"LOGIN.expiry.warning": "Your password will expire soon.",
"PKI.error.badconf": "PKI authentication cannot work properly due to bad configuration.",
"pwd_constraints.atLeastOneLow": "At least one lowercase character",
"CODE.tooltip": "Authenticate using an activation code",
"CHANGE_PWD.error.defaultmessage": "Failed to change password.",
"OOB.input.otp.label": "One-Time Password",
"FORGOT_PWD.request.tooltip": "Click to receive a temporary password allowing to set a new password on next screen",
"FORGOT_PWD.input.new_password.tooltip": "Enter your new password",
"ENROLL_FIDO.submit.button": "Next",
"FORGOT_PWD.methods.input.sms.label": "Mobile phone number",
"OOB.input.oob.label": "Select how you want to receive your OTP",
"FORGOT_PWD.methods.sms": "Receive by SMS",
"OOB.methods.sms.otp.message.2": "Check your mobile phone and click Next to enter your OTP.",
"OOB.methods.sms.otp.message.1": "The OTP was sent to your mobile number.",
"pwd_constraints.notBlackListed": "Cannot be a blacklisted word",
"pwd_constraints.onlyAlpha": "Only letters",
"LDAP.name": "Corporate Password",
"LDAP.input.error.required": "Password is required.",
"login.error.unsupportedconfiguration": "Unsupported configuration.",
"pwd_constraints.maxLength": "Maximum length",
"CHANGE_PWD.input.confirm_password.error.nomatch": "Passwords do not match.",
"consent.deny.button": "Deny",
"userid.tooltip": "Enter your username",
"LOGIN.action.change_password.tooltip": "Click to change your password",
"PUSH.name": "Push-based authentication",
"consent.prompt": "Please confirm that you agree to share the following content with:",
"application_title": "Authentication Service",
"login.error.maxfailure": "You are blocked due to too many unsuccessful authentications.",
"OOB.error.defaultmessage": "Invalid Username or One-Time Password.",
"LDAP.input.password.placeholder": "Enter your corporate password",
"OTP.submit.button": "Next",
"LOGIN.name": "Static Password",
"LOGIN.error.defaultmessage": "Invalid Username or Password.",
"FORGOT_PWD.success.message": "Password is reset.",
"ENROLL_FIDO.title": "Enroll your FIDO device",
"FORGOT_PWD.input.confirm_password.label": "Confirm your new password",
"ENROLL_FIDO.tooltip": "Click to enroll your FIDO device",
"FORGOT_PWD.input.new_password.placeholder": "Enter your new password",
"PUSH.selectdevice.label": "Select a device",
"PKI.name": "Public Key Infrastructure",
"FORGOT_PWD.methods.input.email.error.required": "Email is required.",
"CODE.input.method.label": "Select how you want to receive your OTP",
"LDAP.submit.button": "Next",
"FORGOT_PWD.methods.input.sms.error.too_short": "Phone number is too short.",
"FORGOT_PWD.input.confirm_password.placeholder": "Enter your new password again",
"FORGOT_PWD.methods.input.sms.placeholder": "Enter your mobile phone number",
"FORGOT_PWD.error.defaultmessage": "Failed to reset password.",
"consent.datalist.label": "Data requested:",
"CODE.name": "Activation code",
"OOB.error.maxunused": "Failed to send OTP due to too many unused generated OTPs.",
"ENROLL_FIDO.error.register": "Failed to register your FIDO device!",
"FORGOT_PWD.methods.email.reset.message.1": "We emailed a temporary password to",
"LOGIN.action.forgot_password.tooltip": "Click to set a new password",
"FORGOT_PWD.methods.input.email.label": "Email address",
"FORGOT_PWD.methods.sms.reset.message.1": "The temporary password was sent to your mobile number"
},
"fr": {
"userid.error.required": "Identifiant requis.",
"OOB.methods.sms": "Recevoir OTP par SMS",
"OTP.input.otp.label": "Mot de passe à usage unique",
"PUSH.error.defaultmessage": "Echec de l'authentification par requête.",
"ENROLL_FIDO.error.not_supported": "Ce client ne prend pas en charge l'API Web Authentification !",
"PKI.error.defaultmessage": "Certificat invalide.",
"CHANGE_PWD.title": "Changer le mot de passe",
"LOGIN.input.password.tooltip": "Entrez votre mot de passe",
"CODE.error.defaultmessage": "Utilisateur ou code d'activation invalide.",
"FORGOT_PWD.input.new_password.error.short": "Nouveau mot de passe trop court.",
"FORGOT_PWD.input.confirm_password.error.required": "Mot de passe requis.",
"pwd_constraints.notOldPassword": "Différent des mots de passe précédents",
"FORGOT_PWD.methods.input.sms.error.too_long": "Numéro de téléphone trop long.",
"OTP.input.otp.error.required": "Jeton requis.",
"login.error.password.expired.title": "Mot de passe expiré !",
"LOGIN.tooltip": "Authentifiez-vous avec votre mot de passe",
"PUSH.tooltip": "Authentification utilisant une requête envoyée sur votre appareil",
"OOB.methods.email.otp.message.2": "Vérifiez votre courriel et cliquez sur Suivant pour entrer votre OTP.",
"OOB.methods.email.otp.message.1": "Nous vous avons envoyé un OTP par courriel.",
"PKI.instructions": "Cliquez sur Suivant pour vous connecter en utilisant un certificat.",
"pwd_constraints.notUserAttribute": "Ne peut pas contenir un attribut utilisateur",
"FORGOT_PWD.input.new_password.label": "Nouveau mot de passe",
"LDAP.error.defaultmessage": "Utilisateur ou mot de passe invalide.",
"FIDO.tooltip": "Authentifiez-vous en utilisant FIDO",
"notification.error": "Erreur !",
"FORGOT_PWD.methods.email": "Recevoir par courrier électronique",
"userid.placeholder": "Entrez votre nom d'utilisateur",
"pwd_constraints.numAndAlpha": "Des chiffres ET des lettres",
"login.error.password.expired.message": "Votre mot de passe doit être changé.",
"FIDO.enroll_action.separator": "OU",
"FORGOT_PWD.input.temp_password.error.required": "Mot de passe temporaire requis.",
"cancel_button": "Annuler",
"pwd_constraints.atLeastOneUp": "Au moins une majuscule",
"FORGOT_PWD.input.new_password.error.required": "Nouveau mot de passe requis.",
"ENROLL_FIDO.instructions": "Connectez votre clé FIDO, cliquez sur Suivant, et suivez les instructions données par votre navigateur.",
"login.error.invalidurl": "Requête d'accès invalide.",
"CHANGE_PWD.input.old_password.error.required": "Mot de passe requis.",
"notification.success": "Succès !",
"FIDO.instructions": "Connectez votre clef FIDO, cliquez sur Suivant, et suivez les intructions de votre navigateur.",
"submit_button": "Valider",
"OOB.name": "Hors Bande",
"FIDO.error.not_supported": "Ce client ne prend pas en charge l'API Web Authentification !",
"LDAP.expiry.warning": "Votre mot de passe expirera bientôt.",
"CHANGE_PWD.input.old_password.placeholder": "Entrez votre mot de passe actuel",
"pwd_constraints.numOrAlpha": "Des chiffres OU des lettres",
"PUSH.deviceitem.unnamed": "Appareil sans nom",
"consent.confirm.button": "Accepter",
"login.error.emptyfactor": "Aucune option d'authentification disponible.",
"LOGIN.input.error.required": "Mot de passe requis.",
"copycut.warning": "Les actions copier / couper ne sont pas autorisées à partir de ce champ.",
"CHANGE_PWD.tooltip": "Cliquez pour changer le mot de passe",
"consent.title": "Consentement",
"pwd_constraints.atLeastOneSpecial": "Au moins un caractère spécial",
"ENROLL_FIDO.success.message": "Votre clé FIDO a été enregistrée avec succès.",
"service_name": "HID Authentication Service",
"CHANGE_PWD.input.new_password.label": "Nouveau mot de passe",
"OTP.error.defaultmessage": "Utilisateur ou mot de passe à usage unique invalide.",
"LOGIN.input.password.label": "Mot de passe",
"OTP.tooltip": "S'authentifier avec un mot de passe à usage unique généré sur votre dispositif",
"PUSH.confirmationsent.notice": "Pour confirmer votre authentification, une requête de confirmation a été envoyée sur votre appareil.",
"FIDO.submit.button": "Suivant",
"LOGIN.action.change_password.separator": "ou",
"FORGOT_PWD.reset.title": "Réinitialisation du mot de passe",
"LDAP.tooltip": "Authentifiez-vous avec votre mot de passe d'entreprise",
"OOB.input.otp.tooltip": "Entrez le jeton reçu",
"CHANGE_PWD.input.confirm_password.placeholder": "Entrez votre nouveau mot de passe",
"service_tagline": "Construisez et délivrez rapidement des solutions d'identité de confiance",
"PKI.tooltip": "Authentifiez-vous en utilisant PKI",
"FORGOT_PWD.methods.input.sms.tooltip": "Entrez votre numéro de téléphone",
"OOB.error.nomethod.message": "Aucun canal hors bande trouvé pour envoyer l'OTP.",
"OTP.name": "Mot de passe à usage unique",
"LOGIN.input.error.short": "Mot de passe trop court.",
"CHANGE_PWD.input.confirm_password.error.required": "Mot de passe requis.",
"login_title": "Connexion",
"LOGIN.submit.button": "Suivant",
"FORGOT_PWD.methods.input.email.placeholder": "Entrez votre adresse Email",
"CHANGE_PWD.input.old_password.label": "Mot de passe",
"CODE.input.error.required": "Code d'activation requis.",
"FIDO.error.defaultmessage": "Données FIDO invalides.",
"CODE.methods.email": "Recevoir OTP par courrier électronique",
"PUSH.submit.button": "Suivant",
"FORGOT_PWD.methods.input.sms.error.invalid": "Numéro de téléphone invalide.",
"FORGOT_PWD.input.temp_password.placeholder": "Entrez le mot de passe temporaire",
"OOB.input.otp.placeholder": "Entrez le jeton reçu",
"PUSH.sendtodevice.notice": "Cliquez sur Suivant pour recevoir une requête d'authentification sur votre appareil.",
"CHANGE_PWD.input.confirm_password.label": "Confirmez votre nouveau mot de passe",
"FORGOT_PWD.methods.input.sms.error.not_mobile": "Entrez un numéro de téléphone portable.",
"redirect.message": "Vous allez être redirigé de manière sécurisée vers votre application.",
"FORGOT_PWD.methods.input.email.tooltip": "Entrez votre adresse Email",
"pwd_constraints.onlyNum": "Seulement des chiffres",
"LDAP.expiry.warning.notice": "Vous pouvez changer votre mot de passe maintenant, ou cliquer sur Suivant pour continuer.",
"LOGIN.expiry.warning.notice": "Vous pouvez changer votre mot de passe maintenant, ou cliquer sur Suivant pour continuer.",
"pwd_constraints.minDiffChars": "Nombre minimal de caractères différents",
"FIDO.enroll_action.tooltip": "Cliquez pour enregistrer votre clé FIDO",
"PKI.submit.button": "Suivant",
"FIDO.enroll_action.link": "Enregistrez votre clé FIDO",
"copyright": "HID Global Corporation/ASSA ABLOY AB. Tous droits réservés.",
"LOGIN.action.change_password.link": "Changez votre mot de passe",
"CODE.submit.button": "Suivant",
"LDAP.input.password.tooltip": "Entrez votre mot de passe d'entreprise",
"CHANGE_PWD.input.old_password.tooltip": "Entrez votre mot de passe actuel",
"pwd_constraints.minLength": "Longueur minimale",
"CODE.input.code.label": "Code d'activation",
"OOB.tooltip": "Authentifiez-vous avec un OTP envoyé hors bande",
"login.error.badconfiguration": "Impossible de procéder. Veuillez contacter votre administrateur.",
"CHANGE_PWD.input.new_password.tooltip": "Entrez votre nouveau mot de passe",
"login.error.maxretry": "Nombre d'essais maximal atteint.",
"LDAP.input.error.short": "Mot de passe trop court.",
"LOGIN.input.password.placeholder": "Entrez votre mot de passe",
"CHANGE_PWD.success.message": "Le mot de passe est modifié.",
"select_factor.label": "Choisissez une option d'authentification",
"pwd_constraints.notSequence": "Ne peut pas contenir de séquences",
"FORGOT_PWD.input.temp_password.label": "Mot de passe temporaire",
"OOB.input.otp.error.required": "Jeton requis.",
"PUSH.approve.prompt": "Approuvez cette opération.",
"CHANGE_PWD.input.new_password.placeholder": "Entrez votre nouveau mot de passe",
"OOB.submit.button": "Suivant",
"FORGOT_PWD.methods.input.sms.error.required": "Numéro de téléphone requis.",
"FORGOT_PWD.input.temp_password.tooltip": "Entrez le mot de passe temporaire reçu",
"CHANGE_PWD.input.new_password.error.short": "Mot de passe trop court.",
"FORGOT_PWD.methods.label": "Comment recevoir le mot de passe temporaire ?",
"CODE.error.nomethod.message": "Aucun canal hors bande trouvé pour envoyer l'OTP.",
"OTP.input.otp.placeholder": "Jeton affiché sur votre dispositif",
"login.error.unexpected": "Erreur inattendue !",
"FORGOT_PWD.request.title": "Mot de passe oublié ?",
"CHANGE_PWD.input.confirm_password.tooltip": "Entrez votre nouveau mot de passe (confirmation)",
"next_button": "Suivant",
"PUSH.error.timeout": "Votre confirmation d'authentification n'a pu être reçue. Veuillez réessayer.",
"CHANGE_PWD.input.new_password.error.required": "Mot de passe requis.",
"FORGOT_PWD.input.temp_password.error.short": "Mot de passe temporaire trop court.",
"OOB.methods.email": "Recevoir OTP par courrier électronique",
"OOB.error.failotp": "Echec de l'envoi d'OTP.",
"notification.warning": "Avertissement !",
"FORGOT_PWD.reset.tooltip": "Cliquez pour appliquer le nouveau mot de passe",
"LOGIN.action.forgot_password.link": "Mot de passe oublié ?",
"CODE.methods.sms": "Recevoir OTP par SMS",
"OTP.input.otp.tooltip": "Entrez le jeton affiché sur votre dispositif",
"FORGOT_PWD.input.confirm_password.error.nomatch": "Mots de passe non identiques.",
"userid.label": "Identifiant",
"CODE.input.code.tooltip": "Entrez votre code d'activation",
"LDAP.input.password.label": "Mot de passe d'entreprise",
"CODE.input.code.placeholder": "Entrez votre code d'activation",
"FIDO.name": "FIDO",
"CHANGE_PWD.input.old_password.error.short": "Mot de passe trop court.",
"pwd_constraints.atLeastOneNum": "Au moins un chiffre",
"FORGOT_PWD.input.confirm_password.tooltip": "Confirmez votre nouveau mot de passe",
"LOGIN.expiry.warning": "Votre mot de passe expirera bientôt.",
"PKI.error.badconf": "L'authentification par PKI ne peut pas fonctionner correctement suite à une mauvaise configuration.",
"pwd_constraints.atLeastOneLow": "Au moins une minuscule",
"CODE.tooltip": "Authentifiez-vous avec votre code d'activation",
"CHANGE_PWD.error.defaultmessage": "Echec du changement de mot de passe.",
"OOB.input.otp.label": "Mot de passe à usage unique",
"FORGOT_PWD.request.tooltip": "Cliquez pour recevoir un mot de passe temporaire vous permettant de choisir un nouveau mot de passe à l'écran suivant",
"FORGOT_PWD.input.new_password.tooltip": "Entrez votre nouveau mot de passe",
"ENROLL_FIDO.submit.button": "Suivant",
"FORGOT_PWD.methods.input.sms.label": "Numéro de téléphone",
"OOB.input.oob.label": "Sélectionnez comment vous souhaitez recevoir votre OTP",
"FORGOT_PWD.methods.sms": "Recevoir par SMS",
"OOB.methods.sms.otp.message.2": "Vérifiez vos SMS et cliquez sur Suivant pour entrer votre OTP.",
"OOB.methods.sms.otp.message.1": "L'OTP a été envoyé sur votre mobile.",
"pwd_constraints.notBlackListed": "Ne peut pas être un mot interdit",
"pwd_constraints.onlyAlpha": "Seulement des lettres",
"LDAP.name": "Mot de passe d'entreprise",
"LDAP.input.error.required": "Mot de passe requis.",
"login.error.unsupportedconfiguration": "Configuration non supportée.",
"pwd_constraints.maxLength": "Longueur maximale",
"CHANGE_PWD.input.confirm_password.error.nomatch": "Mots de passe non identiques.",
"consent.deny.button": "Refuser",
"userid.tooltip": "Entrez votre nom d'utilisateur",
"LOGIN.action.change_password.tooltip": "Cliquez pour changer votre mot de passe",
"PUSH.name": "Authentification par requête",
"consent.prompt": "Acceptez-vous de partager le contenu suivant avec:",
"application_title": "Authentication Service",
"login.error.maxfailure": "Vous êtes bloqué suite à trop d'authentifications infructueuses.",
"OOB.error.defaultmessage": "Utilisateur ou mot de passe invalide.",
"LDAP.input.password.placeholder": "Entrez votre mot de passe d'entreprise",
"OTP.submit.button": "Suivant",
"LOGIN.name": "Mot de passe",
"LOGIN.error.defaultmessage": "Utilisateur ou mot de passe invalide.",
"FORGOT_PWD.success.message": "Le mot de passe est modifié.",
"ENROLL_FIDO.title": "Enregistrez votre clé FIDO",
"FORGOT_PWD.input.confirm_password.label": "Nouveau mot de passe (confirmation)",
"ENROLL_FIDO.tooltip": "Cliquez pour enregistrer votre dispositif FIDO",
"FORGOT_PWD.input.new_password.placeholder": "Entrez votre nouveau mot de passe",
"PUSH.selectdevice.label": "Sélectionnez un appareil",
"PKI.name": "Infrastructure à Clés Publiques",
"FORGOT_PWD.methods.input.email.error.required": "Adresse Email requise.",
"CODE.input.method.label": "Sélectionnez comment vous souhaitez recevoir votre OTP",
"LDAP.submit.button": "Suivant",
"FORGOT_PWD.methods.input.sms.error.too_short": "Numéro de téléphone trop court.",
"FORGOT_PWD.input.confirm_password.placeholder": "Entrez votre nouveau mot de passe",
"FORGOT_PWD.methods.input.sms.placeholder": "Entrez votre numéro de téléphone",
"FORGOT_PWD.error.defaultmessage": "Echec de la réinitialisation du mot de passe.",
"consent.datalist.label": "Données requises:",
"CODE.name": "Code d'activation",
"OOB.error.maxunused": "Echec de l'envoi d'OTP suite à un trop grand nombre d'OTPs générés et non utilisés.",
"ENROLL_FIDO.error.register": "Echec de l'enregistrement de votre clé FIDO !",
"FORGOT_PWD.methods.email.reset.message.1": "Nous avons envoyé un mot de passe temporaire à",
"LOGIN.action.forgot_password.tooltip": "Cliquez pour savoir comment réinitialiser votre mot de passe",
"FORGOT_PWD.methods.input.email.label": "Adresse Email",
"FORGOT_PWD.methods.sms.reset.message.1": "Le mot de passe temporaire a été envoyé sur votre mobile"
}
}
},
"ui": {
"extensions": {},
"hid_portal": {
"gradient-end": "#00539B",
"login-side-panel-bottom-right-radius": "100px",
"login-side-panel-bottom-left-radius": "0",
"login-background": "data:image/jpeg;base64,/9j/4AAQSkZJRgABAQEASABIAAD/4QBWRXhpZgAATU0AKgAAAAgABAEaAAUAAAABAAAAPgEbAAUAAAABAAAARgEoAAMAAAABAAIAAAITAAMAAAABAAEAAAAAAAAAAABIAAAAAQAAAEgAAAAB/+EJUGh0dHA6Ly9ucy5hZG9iZS5jb20veGFwLzEuMC8APD94cGFja2V0IGJlZ2luPSLvu78iIGlkPSJXNU0wTXBDZWhpSHpyZVN6TlRjemtjOWQiPz4gPHg6eG1wbWV0YSB4bWxuczp4PSJhZG9iZTpuczptZXRhLyIgeDp4bXB0az0iQWRvYmUgWE1QIENvcmUgNS42LWMxNDAgNzkuMTYwNDUxLCAyMDE3LzA1LzA2LTAxOjA4OjIxICAgICAgICAiPiA8cmRmOlJERiB4bWxuczpyZGY9Imh0dHA6Ly93d3cudzMub3JnLzE5OTkvMDIvMjItcmRmLXN5bnRheC1ucyMiPiA8cmRmOkRlc2NyaXB0aW9uIHJkZjphYm91dD0iIi8+IDwvcmRmOlJERj4gPC94OnhtcG1ldGE+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPD94cGFja2V0IGVuZD0idyI/Pv/bAEMABQMEBAQDBQQEBAUFBQYHDAgHBwcHDwsLCQwRDxISEQ8RERMWHBcTFBoVEREYIRgaHR0fHx8TFyIkIh4kHB4fHv/bAEMBBQUFBwYHDggIDh4UERQeHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHv/AABEIA44FVQMBIgACEQEDEQH/xAAdAAABBQEBAQEAAAAAAAAAAAAFAAMEBgcCAQgJ/8QAVBAAAgEDAgQEAgcGBAQFAAITAQIDBAURACEGEjFBEyJRYTJxBxRCUoGRoRUjYrHB0TNy4fAkQ1OCFjRjkvElRKKywghz0hdU4iY1g5PDNmR0o7P/xAAbAQACAwEBAQAAAAAAAAAAAAAEBQACAwEGB//EADwRAAICAQQABQIFAwQBBAIBBQECAAMRBBIhMQUTIkFRMmEUcYGhsSOR8ELB0eEGFTNS8SRicqI0Q1OC/9oADAMBAAIRAxEAPwD5ovFQ9TUGgWXxuWXxKqUdJZv/AMVeg/HUOcFitLFjlX427fj7DXUcYoYOXDeK2wB6j1OnaOkDN9XII+1Oe49F/voiuvALGYHCgASXY7RLcKiNYAysxAh9v4jrWeBaZI0hiucLw26lYsamGJnjkPTmOASpPQZ20O4OsMxEdLHGfrdUq847xxHovzbqfb56KfSJeaezW82a3urLG2XZf+ZJ0/IdB76M8P0q6hzdb9C/vAtbqTSorTlm6lc+lbixrlXPDEfChjHIiA7RoOi/Puff5azMfv5zI4OAcYHf0Gna6oaqqm3yxO57E+uiFAsVuov2nMgYqeWkjb/mSd2PsP7aMXOsuNr8KP2EHSv8PWEHJP7mc1vNb6T9nR71tUAagj7CnpGPQnvru52yGhttPRgu1xm/eyKG2jjI2BHqevy1IskC0lPLxDcwZXLHwEfrNKd9/budGeCLLV3m5NX1Ub1MskwCqRvPKTso9u59tTxC9Vr9Q5PQ+B/yZrp1YvtB4HZ+T8fkJYPoa4YSvrhTEtFVsvNUcww0EPcgdy2wBG2+tD44ulPMqWKgVUt9IAhVejFe2e4H6nJ0r3Q0NhsUNtaKnqbjIfFacoCyMerKeoG2Bj56rgGNP/8AxfwTYv4q4cnofaeb/wDI/FyT+HqPXcYSkgXdVx8teSUUTjDGQj0JH9tSNLXsTpqj2onkhrb16cyAbPRtsY4z/mQHTZsVJn4Yx8owP5aKqO+vdZnRUH/SJdfEtSvTQT+xIVGY2YH2lcfyOolxpxQUsk71k6qg+zMd/YZ0emfkXOQANyT21mfGd9arqTHCxEKHEY9T3b+2kXjNlGgq9I9R65jrwf8AEa231Y2jvgRu511mrJyJ5Lm0pGCSUbGhF1tlHTpTyxyzo9QOaINs3KDjJA6e3y1ItNNDFDJcq8H6tERle8z9ox/XRO1R+WXii8ospZ+WlgxtLJjZQPuKMfht315E6YOm60+o8/kPn/iexrv8rhB6Rx+Z+IKtlTPbjLBRHmrJvI0wGSqHqQezHf8Auda59FfB9PHTS1l1kFNR08fi19Q5wI068mfU9/wHrqu8CcLXS7XlLgipNcKqQycsg8p65f2wem2NjtqX9K/FsMlHHwbYg8FDStmuckEzzAkHJUkFQem+50prRtS4UnKCF2utIyB6jBX0r3et4wvoehrKJbdTqYqGkjmDckY7kD7R6nVJpkqzAtDPJFHQmcNI64wTgfEfQdvnom0c1GiWqjVmudWoWTl3MKN0T/M3f21Nq7JAzw8P28JJUQtz1tSPh8QYyg7cqgbn1z6aY6qo0guG67+Pyg2nsV8IR+X/ADCFmp24krqempYJYLLQYWKNR5nYnc+7ufyHyOtd4mrv/wAnXCwttHTytf7jCBUPTLk0VPjaNT2Y9M9dyeuofAiW/gzhpbxcKN4rgqE2yknQhJHI81QWxhlHtuNhgEjOYcZ3maprZpnneSvqWaSSZjhhucucfiAOmRtsgJA3MxN9nftNWCg+TX+sGcR3gVMPIEeOHH7wFSpbsEAPY4H4YHYk8WunlmP1OAc1bVDFS67CCPc+ED2Pdj2G3rqFNb5KujSokll8ec4pEJyWUHDSMT27D1Py1qX0T2GzUFDWXbiCcUtHbl8WvWRsSSHO0Sjq3MR1HXp2OoGtqYr/AKm/aXCVFeOhDNoW2fRzwYOLblCstS2UtFIwwaiXGPFI+4vb+51j0l9q7rXVFyeoes4guUzAtg5hB6sPc5wAOgGrJxvxnceI7hU3y5qsdG2YLbQKowoGwUHrgdWPrtqq11vq6L6kD4YuFUheRETzQxt05uwyN/Yb7Z0wSqzQJuH6/PMGLV6k4P6f5/ML0dCCF4ctkgbo9zq13BI+wD3Ufqdbhw3b6bgXh+GUokd5q4f+GjYjNJCert/6jfoNCPos4VoeHrHHf7jEkyZBo4j/APW5h9s/+mv6nTF2tVTdblUXKsudQ9TO/O7BiBn5A4A9hph4ToX1134m1fQOhFvierTS1mhG9Z7MmLMGy3iBt8kk5J1y8pcEA4+Wg72GojUlLjL+LH+udQLqstqoXqqi5yqq7BQiksewGRr2dmoFKF3XAH5TyC6ZrWCIwJP5xzi2+w2WkBJDVEgPhL2z6n2/nrMKXNwnnudymdaSHzyydWYnOFH8Tb4/PtojWzUXENXIzT13OFJd3CCNFUdT5tgNBaNBAlPNKZ6i3/WHMEToQkkmFyff7Oe+CPXXi9Zr2u1AutHoHX2+89j4f4cuno8tT6j3/wASy27xIXivdVTg186iO00Q3ECdA+D+OPU5OtJ4NtVHwlw+3Fl+VKiqnYmigmP/AJmVdzIx/wCknUnufwyP+jvh1Z/rPF3FTOtHCVD4GGdiPJTxj7xAGw6DVF484suPFV9qqm41FPHaw6wpT03SKJM8kKnuM7nHUnO/ZY1n4iwWWD0Dr7n5MYJUa1Kr9R/YfAku43KXiO41HFF8klqKBJyYYnPK9wqMfooGP8q4HU73XgmzU9LSVnHPGUgFPF1j+HxWA8tPGOwAG+NlUY650O+j3h9uIKr9u3fltlktsIKA7pSwA7f5nY5x3JJPYDVf+kjjUcRXWnpYwtvstJ5KKnVg4jj685xszt19z8hrPUX/AIhsZ9P8/wDU0pp8tfv/AB/3GOLL/W8XX2e+XRmSkjIiigj8oUYPJDGOxI/9oyTuTm2cB8O0kFHVcX8VulPa6JQHUeXOBlaePvn19AcndtQPo64bF6na61zChtFvjMheQZEEWd3P3pHI2Hc+wwR3GvGdNxLXQxNSy0XDlr8lvtufPUuTszEdz1JPv3xq6bbW2Z9I/f8A6EqwZRuxz/H/AGZ5xNxFX8R3uLiCvpQXk/c2K1gYSNBsHK9lH6n5HWi/R5w7FwnahxHeOWtvNcfFpll352z/AIzD7in4R9o79AMB/o+4ep6Knk434yKfvH8OngPlErAbQoOyKMcx/DrnJu4cQ0lyrJKuquFO00h3/eKAo7KBnYAbAac+H6Ma+wO/FS9D5MUeIattIhSvmw/sIqqeWeeWpqJDJI7F5JGO5Pck6zLjHiCa+Vy2S0N+4VuZn6BsZy7HsoGcZ9z6ak/SVxYI4ntdvkVo38ssqj4jv5Qe69PmR6ar1BHRQ26UeN4lGMfXZ4z56uQ7injPp3Y+2TsBkvxLxFLmNSnCL+//AFBfDPDXpAtcZduvtH6SOkioomELT28S4pYCMNc6gfbPcRJ/vcnF/sVGOFKBOIrtHFceJbqS1tpZQArcvWaQfZgjA2HRiMDYai8L26mt1CeNOKaXxWYiltdriGDO4+GCMdkGcu3v6k5jUNJeOOOJqiBpUnqql/8A6SqkIESovSnjPRYUA3PfGew5vKX3+cd7dewnpKa/LXaO57wxZKniy6VVTV1/Pb0c1l0uVTsJ3X4pXPURr0Vfy3OzPGXEEnEtdSWCwQPDZ6Qn6lAV3djsamUDqxGyr2Gw2zzPcc8RUs1NDwbwp57VEwMkiDH7QmXbnPpCn2R369TkHeHLenBNvWYvGeI6qL6wZpQCLfCR/wCYkB25yNo0PpzHYDVKwXP3/iWO1Bk9SRR0lNwRaZbbSzFLwyZudYDl6FHH+Eh3zUyA790B+82i3B1jhpoIOI71RxqiqUtVuI8uB9ph3XI8x+0dh9omLwbZoa2NL7dY5ltFNIxpaeRj4tXMd2didyxzlmPwg+pGGfpD4welkwkkbXKcBIkXHLToBgYHbA6D8fm00unRl8x//bH92MXajUMG2J9Z/YRjj7iipFVLR087zXWpOJpOpiB+yP4jkdOmcdelHtlALi8kKORQRsBVzruZ3P8Ayk9Rldz0Yj7q517R0c1ZWz0STMvLlrlVnP7oHYxg9ec5wcbjPKPMxBvkTW7hKyQXasgVJVT/AOiqFlDEZ2Ezr0JJUhV74P2UYmms1Ts+B9R/soltNplVft/JndXVw8GW5Kh4Qb7OgShpE3NGjDKnH/UPUEjYeYj4F17YqGPhG2ycTX4tNfKoDwY1HM0PNuiqDnzncqDnAzI2fKGb4Ztpo46jjri9+erceJBFL+88NWY4dh9sswIC9ZGB6IjkWPhi1tXTDjniyFzCGZbXb3YMzs25JJ+Jjylmc7HlPRExpS7ADYp49zGCIezFwzbXtKDi/iOJJrzVL/8ARlCSeWFB5uY5yQo5uYsckluY5ZlzYqCmlt0huVeTV3ysbMaN5Sm3xH7uFJ/yKT9piR3TCXx/29dFM9dUsq0kCrnJzlOVTuFGcqD13dt+UCqcS3a4V10/8NWErV3quGKidd44Y9yRk7CNdySfiIJPlHnpWM/b/b7n7/EpY3sI1e66uvd2bhnh+YPO48S43A+VIkXfmJ+yijBUfJupQaeudwpeFbXQ8PcN0zVVwqSHoadky875x9cnX7o/5cZ+Z9+ayptvBfDsVttkYuNXWvmFWBL3OcH/ABX7inRskA7u3XvqLR0F1tl0e3UkxruPbwPEr61jkWyJgc79Fk5eg+wu/wA7DBA+PYfP3Mirt9I7jNFb6ykqqrhax1nj8Q1gaTiG9vJkUaHd4w/ZsfE3YHlG51YrZb6CG3QWy3RPHZKd8qvwSXCZRnnYn4VA332RfMfMV15ZLVQUdqFntRd7asimqqVGZblP1AGeq53AOx3dtuUNDv1zq6+u/YFhaL62Y81NQG/c0UA8xPMeijIbJ3ZiHOcoGzZi5xNB6RgRq8V1ZeLjJYrLNHE6IDX1yqVipIlIwFHVQMjlXrkgnzleRmukp6Cnk4ZsE/7NprenPc7i/wD9SU+U5I61L5CgDJQEIvmJI6qpo7RAeGeHJ1pZoV+s3G4zjH1NcbzyntKQ3kTcpzZ3dhrvhSyUtTTUk8tFJHY6dzLbqGUYkrZcHNVPk+zYB2A5t8c7a0UADcepOo9wvZKd4aO41VB9VtVKC1otcpAycZNTP25ioJ32Vf4Qeav8b8RyXOtNBbiKlpiH5iu0u+RIwPSIdVQ/EfO222nOPOK5q+drbbnFSZ8BmHwz77f/ALkEZAOPEK5PlXy+2S3rYYZ3eo5bpyrLW1rrzfUw2CMD7U77cidshiBhdXAJO49/xK/VwI3bbWtjSdkq5obgpBuFeMs1OX3ESA/HUud1HVMcxwRlbRQ2VOHbZHervULbZqOMCngCq37OibfG/wAVVKBucZHXYAYn2G3UvD9vjv8AeY1oTSx+LRUsxDigV/8Any/9SpkxsP5KpIAIH4qqFv8AfElgsMD5t9C2XeqdmxzuBu5Zh06uwwMBSUxducLNlGBBsdJWX640nEd0pjFZ1lCUNvbmkkkDE8hCfbdm6AnLnmJ8qsVsNHC1zeW43UmOgQSJKwkwpXH7yFJAPh2HjTj4to02wDPpaZ7rUS11xf6vRwc8csiSABRjzwRONubAAmmGyqPDXbbUKVouJUSrqYvq/DFOypSUsaFTcGU8qKqjcQg7Ko3djj4iSt87PznPbEZWsTimpNVWxPHw7SMi0lEkRU17AkR+QbiIHIVBuxz352BKaphmgkvN5kVaJV5EjXzCUHyiNAvxK3KFPLjxSvIuIlYlupWCpglvF5dI6GJeVVXdWX4fDTl6qcchK/H/AIaYQOxkGimM8dwukUi3EOHoKJWOaLfAdguOaY4C4HwjyLjBKQDH5yKI8rVMNal0uSE3dsijo/i+ohvLk8uOac4wcYxjlXl5WaMNeLlUw1Ys9oZZr1OpM0xIKUcZAJYn4eblA/hAA2CBFdu7V9ZT1ptVo5Km8zoTJIxBjpEK7sx+HPKPlygf8sASSrbRUXCVlM9a8s0kkmJZhkzVkxJPKud/iBO5yCCSeYEx6KuBmSS7La6Sw29QEmqJZ5MHGfHrZskkDO+xBYk/DgscEEoYSGK3wS3S6TwrNGn76UA+HTRgjEce2eoXtlmxtkKFjW2YUlE95vLJRTmL96X2WjiyMQoOxyADjdmA7hQvdspGvDw3e6Rmlt0JWSipJB8PZZZB3c5wqds46kkwHPck5obU1+niuV2p2hoKdllo6GQdD0WWVR8TnOFTfr7kmfW8PipqhcK1nNJSkSUtFEnPzSjfxHHR3+6BsOvvqw0sWVEsqso+wmQTkgjJ7FiO/YZA2yTzdK/6kUihiFVXz5FPThsZAxl2P2UXbLfIDJIGqqxJ4lsYEqVQlXT3CC43WlWsu8ysLZbo5MrTDGHdj2OD55d8Z5VyThklMIjWrFcVWqUBrzeCvKKcDpDED8JGdl35M8zZcgEskbJJWolwKTrj9sXjlx4GOkEI3w4zgAZ5M5OXIGnxbIWWBRRRUiUsfiUVJLlUpEBJ+s1Bz8WckKTnOd+bmZdsiTErMtoimURfVBQjwCaWHZWgiByaioY7jv5Sc/F1bmKRZI6mkXE6NPSlS6S8vKwjzgOy9VB7Zxq3LQlUZkDTwsfrB+tDlM5HSefGMIMeSLAzgdMeVz6llyGMyTNJzMZceI0mMhm7GTG4X4YlGT0ABem1T09HiDW6dbBK3a61opBDI4eBzhH+63ofno1qLX8PKgJg5Ym5dwCShGOhzv0xud8EscbAs2+aphl+o18TpMBmJz0lUeh7kd//AJ16LT6tLhweYnv0zVnPtCGlpaWi4LFrw9Ne687akkQ3GvdeAYGvdSSeAY0iM690tSSeAY7690tLUki0tLS1JIvlpaWvQMjUknmlpa9IxqSTzS0l217jOpJPNLXWNsaWNsarmSc6WugNsaQGBjUzJOdLXvLrrUzJOQM6QG+NegY17qZknPL76XL7660tTMk55ffS5ffXWlrmZJ4BjXulpakgGYtLS0tSdxFpaWlqTgEWlpaWpO4i1zy++utDb5eKW10rSyc0sg+GKMZYn3x0GpgnqcOB3H7pcKS2UbVVbMsUS9z3PoPXWR8T3+9XytlSCYig5sxw+CG5fnsc6icQXCuuVxlq6i5SwKx2h+tFFT5AttoQ8VNJkTXKOb15qoSD+Z1sqbefeZbs9x2anr1/xqqSH8BEB+WNMfVIZ2/f3OOT156pX2/EnXVJQ2l5PLMgBIXKhuvpsNW36vw3w7TLV3e3yVZJzFGHBXP3n836dvc5Ous+37mcUbjx/EAx8O2qKmNXXTKlEME+C4Lyfgu4Hy1FlrrRUlqWikMMCD4WJIA6fabc6lXPiSjvvNMXP1eM8q0ylVyPQbnT/DMC3+4/U6K1TU9OikNJCicsQHqTgfMk63Vgi7nwIO6l2wATBVJUWySeOjoLPl+5CoZPmzYJ/DVvmjNgpIZLdCJ7lNlZY3UO6nsqhT06Z7djqTItbb68WXhmiFa7gedPPIzb5LFSQB7/ADxtvovXQw8KW2SpWohgv7qMfvPGCE+gMRAPpv36+q+/WbsBD/YQurS7eW/cyNb7OaalW6cXU0MVURzxxPO5ZfQlANvxO3ftmNYrbxJe6t6uarp6azQOxepmXCkbnCrsT0+e2du73D9tvlxEnEHF3gQ2/HNH9Z+OTvsEYf79caCXur4h4pu62/hqWVaFV5EgLMsUe+SSGZ/59t9DBnY7Qx/2E2GxVzj/AJMlcW3NLm8No4Z8UcnkDQJ4ay++ATkDHU7bnHrohw9Z5eDoDcL3dqiorm+Clp5HHLkdCQc5z+WuxPScJ2c0VdUxXG6SRkMEhhIQkfeaMtsR+PpjGYHBn0e3G4zG/wB6uMtttfMZAMlZJdsnG4Cj3xgfrrhZQhHO35+Z0KzEE43fHxGqugqePL39ZutelspEGDLU1DMVT0HiMTvsfwH4mbjeeEuErUtu4Tp7dX1hXBq5zExJ9fN/Ibduuwjcd8YPV0R4a4ehuE9N8DyvVTOGG+QBzYwQSD6gnpqiQcJRQI1ZV1VTJOxJ5YQpAPXHwk9f667RozeMsu1B95W7Uio7Q2W/KKqgo62ta58T1kbySSM/KuQpbGSSV27Z/DUWsexSSrBb3oKdGGDyxvzHfbcjHUdc/luTz+xa641S06084UkYWQjJAzucfj/vGr1w9YuDOGENVfKqOSu3IgldgWPpg4AG2B0z6gaYWMKlwi8fvA60aw5Zuf2kSw8M2q1Un7TuFbbpREAwXxCVUZAz5VYbEjfoNs9tQuIPpHjuNGLTbaSqt9K55WWMrzyZ23P4gHbfcdNtdcSXq78WVJihqqeCgU4SmiqAVA3A5gux6nboMnHU5I2Sl4N4WP1y/CKoqm5SMBXLk5xnBJUbHtk4P4BsLGXfcBj2EKGwHbX37mSOBeDqOppBd5oLksYBbmenjZExuclpFG2ASSMDqex0J4k4+ucDva7WgWhwBzNHySs/2scjHJycA52Bz5QfNxxZxxFxJMKWC4x0tCMBKeNGXI+yG2AA7gDp8yWLnC9dw9YM3CupnuMkeCic6qo/DfPrjoNz6nVPK1Fql3+n4nVelDtAyfnqSeCuGrlcYBca6zR09IcvztK0QwMjOXRtsdDjoTjrqL9IHFVdQPHbrBcZ4BCrRypFUsyoRjrzKoGN/L7jPL354x+lWS9RvDCKuipD5QkKqWOO4bPUjfI6L0xnJq1v/ZZYSOlRyIR5ZHCe+dl9/Xbf567RRbcfUwx9p226ukZxn85zbTxZdatWjkqhEGUPKWVMjpjsdh+O/YbautJZpaOkNRdLuqxIPMzLzlz2ChgSWI7D57DcCa/i6ktdEsdtpeeYLh05VWOPts2TnqOoG+3XA1WbhxWlZVqlVTRSHPL552winf17nJI/P01sxx/TrfmYKpcb3XiFOJ62s4luCCDnEaFfAjITYAcpbCqFA27eUH7x1cuAfojnq2iuF3n8GnAPhxRhgzKewyenfJ3J1UuHuJqSlcSQwxiUkM3ICTkepYNnH6DU3if6SeIqtWgt1RVQxEcsnNKZOfGeYY5V2xj2GfNgHcS7TGtQA37wiq/zCciXvi1eCOE6XwEoILlXtHmNJAGPL052Y/Cn8R69BnqMvr46jiC4uXggEjBUEcEQjSFRny+qjB6fG3ViBoVLxDfq2taVBNO7SCSaYUysWJ6ebGSRv5u+dsddE6CuvZiWP6rcJPMcHw+UHf05hv021tptCpGXJP3OZS7UlThB/aaRwX9GVBDyV99Znc8vLC0nLsOgIHQD7o0d4ju9nsNL/wDRVvWoqHyqClXdu3xDZF9XP/bncjG7pfLxVQGjpzBGoblZ0p1DMcHK8wy3vsfngaBQQXqrxS0Ynq5MsCfF5gFPVidwT2B6Dtk76wbRrbZyM/lNU1BRMn95a7694u9WtTcYpWOSIY90SPPXlz8I9WOXb26kzwXw3a5q1WuM6eXcQQRFz8lCg4H6+pOqjZ+EuKpJoY4LaZZjlVDMSWz0GMZzohX0V+tEccdfJ4U0ynwYYppCWH3vi+H3Ox7ZwcHiqqpMDg+wgRsssbI5E2Kp4v4V4bpxRlvqjDASGSBoh16nIB/rrN+N+MDeHqITdIYqHPI4UtzTHOQrkDyr35B17knfVDuNKSTU1FVzSyNzBs83MfvLnrjHxHb0zpuLhysuOZJKhaeLGyeEMnPVjnfPv11hptEWbO3JhF2rVEwzYEJyNSTxssFwJUYSQLA2cfd7BV/hH46m0lRaqKFVi8RnOOYsUUk/i2oEXDkkR5v2myAKFJWNVGOw2Go8lG7M8UFfVMoGHkeTCqM/pn89OgTQORzFOE1HRyP1hWfi2hiEiR0lQzqeQhWUkE9MDfOmbhfqScK0tHP4UY51DS5jL9DjbzP7n+m0aOxwB1JWdn5MKnPhiDjzH7g6dd+mrlwJ9EcnExSWrjent8Xwtynlz6KDgn5/n6aV3ahxlrCMCMKNPWOEHcq9DebfNRufqU0OSA7MSTI2cEE7e/ttqx2njGG2cn1NZoHT/oyQpj5ZJI21pVs+gjhenDvNUSrEi8zMyhQAOpJPTQLji08AcKgUlJRT19eRhacMAxyNmc4/dr0O/mPoAebQg11Vp2D1EwltLYg3Z2iCa/6Tp47dORS3N5jCwhY3Vsc/TJCAbDc9dUK/8ZX+43LxKmSeOBvKtOXaRjvjALAkjIyc6dSkmmmeZ4/EkPVxH5E9lGN/5anW6y1VfUJSwRCnST7UrBM+7Meg9uvy1r+CFZ8zOJl+K3rsxmVSqv105WpUraiWQNnnRThR6dtP0NyuoiTlNU7kjnzFn8snW88JcI8FWmk8OsrLfcKlsF35wVB9ABq5W1uA7bSyTSR21TGvOVFPzNj5Y79ND2a6tTjkzVNK7/YT5yobpxF/ynuEIP2ljVP6aeqOJL7RzxH9rXT6yjK6jxsEb7dv9++ta4++kGIUwpuGKa385wwlZUEcB6g4PxuOv3QcfEemQ1NPLUVctTV3KmeombmlmecF3YnfRFJOpXNg2j9M/wAQe1BQRt9R/aV2ppa+vkZKmonqpGYyMJGJy5bfPpkfjpr9m1pT6uix1FVzBY+UEiP2HqdXK3WWaumNJQESgdRAC7N65x0GtY+jHhRrdCKpOFq2srV28SUJFHH/AJQx/XWFz6fTJ6D+82qW68+qYhH9E3GFXGs0lBNzNvkx4Jzpa+tVi4gYcxs9NGT2evTP6aWlg8U//Qf3/wC4wGhYf6j/AGn5/qsFcq1MfI0yg+GzdM+jD26/6dLFwVZQua2qjMkcUmEVv/rEx3A9wOp1WK2lkoZjU0gLIfjj7H/frqy8AcTxW2509XUQmso4288BbDDP8jt8jjSvUaW2pxVYcfeOabksTzE5mn1dRHwjw09ZUSYulahcsesaHq/zPQawriK7S107O5wW6L9wasP0l8T1N5uUksrnkYhjkYDHsAPQDVLoopKmcEKZZHbCKPtHTG9lfbpdP9I/cxZQjZOpu7PX2El2WiFQ58Z/DhReeokP2FHb5nU6hha/3bxjiC30y+UN0iiX19+599NXDJaPh+hPiEODUuN/Ek9PcD+ep9zUUkKcPUHmIYGsddyz9o/w7+/y0U5rpTn6V/dvj8hLDcxyPqPX2HzHaaKXiS+RQUy+FRwqVhDbCKIdXb3O5Ot44MtlHw1w6t9qYuTMPJQQtswRvtn0d+vsv4ar/wBFHBsMUbNXIop6fleuZtg7DdYM+g6t+WiHF16e8XEsrH6tESIRjGfVsds/oMay8F8PfxXVG+36R+8H8X8QXw7T+Wn1GDK6qmrauSqqX5pZDlj29gPYaY0tegZ19ORQqgCfNXcuST3EBnXoGDpAga91aZxa5c4GddZGd9BOKbwltoiUYePICIwe38X4aG1mqr0tRsfoQjS6Z9TYK0HJgbjm+LEj0EL7/wDOYHp6KP66pdqpJLjWZZgigF2kOyxoOrH5DTTtLX1XIA0hZsAd2J0ZlppZpo+GrYvizSOPrjp0ZvuD+Fe/v8tfPTY+suOquHHsP4E+iUadNJUKa/1MVFTx32vGCaax25Sedh0Xux9WY9vkNHbLSPxJd0qmp3jt1NyxUsA6gfZUfxN1J+Z1HWkWtli4atLq1FTtzVU+fLNIPiYn7i74/PvrUKOS28A8IpxHWRAykGO0Usgw0j95WHpsD7DA7aWa69rn8hD/APyP+ewjDTIqL5zDgdD/AH/MyHx9e04D4dNioWUcQ3GIfWXj2NJCRsi+hI2+WskpgttoxcplWSZzy0kbdHYbc5/hX9Tp2Saa73Csvt6qJHTm8WplPxMT0QfxN2HYakWsCVn4nu8AaFGEVDSfZkYfCg/hHVj/AH0w01K6eoHo+32HzA7GNrkt1/nEcoIZ7JSCcsZL/clLIx3aCNush/ib7P5+mtM+jHhGgoKCa7XseFbKLDVTdTNJnywL6nOM46k47aEfRhwpcb/exXVcmaqpzPJO3SCPvIfTYYUe2ew1L+k/jCCRI7RaKd0sFtX/AIchlAmOPNM24JJyMezDG7qdKLX/ABD5/wBC/vDEzSP/AN2/aCvpE4smudfLcagBScRU9OhwEUfDGpHYDckd8t9zVDpIFnearrsvTxuPG5NvHkx5YU9BsPkB7aX7+7XIt4ngryFi79KaEdXb3Pt7AbADVn4Rsj3utpkp6SQ0cTCGipj8UjHqT/E3Vj2GB6a6HCjznH5D5lkUgeWOz2YY+jjhauvt3+szGOOWRfFeXGI6WFdub2UAYX8/nH+kriSh4gq0tVrP1bhOxg8snL5p2Oxk/wAzHZR6b6PfSTeVtVGfo74dmSSrmIa+VsZwpIH+CCOiKOv5eus3pYKa4li0jRcP21uaSQbNUyeoz3OMAdh+OmGg0pX/APIu+o/5/Ye8F1FwP9NOAP8AP/qd0jgIOIrhAiouYbVRHocdz/CDuT3J1on0VcHyVtTU3u/Susafva+c/FvuIl/ibv6DQX6P+G7jxfxHDWyQpAnL/wANGw/d0sK/bPsP1bPvrVrvU0op4LTaQUtlIT4efimkPxSt7k9PQa10+nbxW/YP/bXs/Mw1GoGgq3n6z0PiRa2ZJ52MECU1OpxDBGMJEvoB0HqcdTk6jOwRCW6/z10MKuTjUGplGc56dBr3lVa1JtXgCeJvudyWPJMj1tUsFNJPM6oiAl2PQDWS8TXaq4gvAgp1cpzckMY67n/7Y/p+GiHHvEZrpzQ0b5gQ7sOjt6/IdvXrobb6CpScWeiwtyqELVUzHApIiMtk9mI3PoMDqdeX1+sOut2A/wBNf3M9F4ZofwieY/1n9hOqKiiqhJb4pfDtdJiS51ijIkYHaNPUA7Adzk9Bq38HcOtxVc1qalFt9po4eZOYkJR06nJcn7xO+epbOonDdkbiKvo7DZIGNsgkxECOU1Uv2pX9ABv7D3O5/wCkG/x26jp+CuET9aklcc8sa71cwOPEx/01OyDoSOboBlLYfxlnlpwg7P8AsI8QeUu89nof7mDuOuIKviKug4RsUhgoKGNxzyAIKeHq8kpG3iMN2PYbdScx+FeHBxTW0tntULJZaNmMJfyeM4HnqZD2AGPkMDqTqNZrO1W68MWhmqleZf2lVxnmNZNnIiQ90Bzv3ILHYDVl4/vtNwvaX4G4akWW4zcsdzqafzYP2aeM9wD/AO45Pzz1FvmHyK/pHf8AxNKk2+tuT/nMF/SHxKa5IeCOHZEe10jt4s6r4f1uQDzSPvsAB8gOmMkANwpwq/FF1p6S3xfuYSWWdkA8Q4HPK+ekYAGB6Y7nTHD9jqLlWrZKBDPLK6pVPGebxGztCh7qDuT3IPZdXTjK4x2CgfgDhiojFdJHm+3JD5IIxuYlbso3z6kk+muLRvPkp+p+PsJPM2jef0/5gzjriGC40DcKWuVaXhy2EPdauI5+tzdNiQM5xhV7dOx0vo04OF1uD8UV9KKW1UxQ+CDhkj2CqpPWVgM/iTttqJwDwseK6+CCmH1Xh6gBlEkuyvjZqiT16YA+Q+9rT7rVwPFFb7fGYbZS/wCAh+KRj1lf1dv0G2mWj0I19gpQYrXs/P2i7V646Os2E+s9D/cxu8137SqlZoI4qeFPCpoFHkhjHRR/MnudUP6QeIoLVSm30PKa18BivWP2H8R/Qe50S414hisVEQpU1bj92v3R94j+Q/trOLbT1j1iVTlWulSplh8U+Wki6mokPb1Gep39MtfEdVWq/hqeFXsj+Is8N01jn8RdyT0P95KjNwkpp6W4XGQOqiWvnk3WijzsgHeVthjt06k4O8E8P2+Lx+LeIVnpLDSN+5jGGk5m+CJRtmVwBuOnU4217wTw7TXnmqJpxR8L2wGqmqqgf4xGQ1RIOpJJ5UTqScd21Ov14qb5daKG10zU8cQIs1E25pY2xzVc3rM+3KOwxj7OfHai0XPnpRPVVBqlweSZB4iW+cacVU1PFEyVajwUoaYZW3wH4adPWQ5Jc+vyOJ/GV2pbFw+/BXCcqs0gEVyq485nk6/V4z90Hd27n2ABm8RVlL9H9jk4dtcv/wBP1CYuVUDl6RX6xKe8z9z9kbepDHAnDUNBRJxHfaUylnMNvoFbDVMmM+GD2UDzSP2HuQBmFLddzTftHMe4BtFPw9QJeK6GCqvtUD9TopBhIwvWaUdoU2x99thkZ07wBZ7lxHc7jcuI7g7W6Oo+sTt9qrcnKsCfiJ2wOigAnAAyTtdvq+KrxVLUVK/V8h7pXBcR8qnlWGMdok3UKOp2+9g3xZfKG02tFhiMdHDlKOmz5pGOMscdSTgk/IDsNMdJo1syWPoH1H5+wi/U6srgKPUeh/vBPHN+raKSOUVcaKf3dFQRwgiOME7ZJ6Z3JPVsn1xmFypaye9GtoampnuCRPPOeVWMSkZznsxGSO4wDttopUSXG5XVTyipu1bvEmMpEnQMR05RjYdyPQHmuHDlqtlps8tdWzFrXA/NUTl8PcZ/iKhvuD4i3b4jnyDV9bqiQEUY/wDiPgfMppKNpJb9T8yBw4lNw7wVFfrzRKKaNTJR0AbzVco253PXlXIB9yQN2OHLbDXVtHVfSLxVSy1qQoZaSjVdn3VS7Y+GMZQEjYDlRd8YfsdBJxZc34nv6rTWWnbNPT7RLJyqSMZ2VVXJyfgXLHLHzH6cjigtVTq1HwnRyAqioUNfKueQBeoReY8q9uYscu+lJ4O1eT7n/PaMlIxubgQTRVdVX0cXF3GEE0lEKgLb7bGnmqp2HKCcbAAAL2CqAi7knVwq7xLHDDxDxDTtJEf3dFRR8vKq56nJA5cqP85UfYTXckVJ9Se43iKKG3wIYoacDKqo28JfQdmI9eRTnnOs34z4gqbtWqxR5C7eHTUwO7kYB6dgMczDpsq79NaKVfluv5+/5Qe28jgf/X/ckXz6Q7zVXeURU+ZqyMpTFpFIQM3Kd89Ccgnq3TYZ1YTVWfgrhsh3/aVbcGImZD+8uk43MSHqtOhxzNtzEADbGK/bbHQ2S1TX3ibM/M4Tw12eomx5YIgOhAxkjZB03OrLZKN7dV0fF/FFILjxJWqsdhsifDFGNlLAfDEPzYn131lcVJJX6f5/6mlAPWOf4g601NdbeITNIi3fj+4oDHHygw2qPHlLDoCo3VOwGTjsbs/7Mt1lq4KavE1LIfEvN5bzGsdjnwoyfiUnP+cjfyBs2E2WkttJdVr5oKq+3cM97q+UeHToxw0Sgdz8JA3OOUb8zLQOK734sdPZ7XAGiXy0tMVHnOeUySY2I8uOwbl5R5VbGKMLW5695s39MYEnni172Vs/DlOPrk3NEodhy00XVmYnbcZZmPxY3wi8rOzypYaccPcOTJLdJl+tVlfUnCwqMsaqYt0AyTGjeviNuVBD2eiqrNURpRt9d4juMZbllOYooieYzzZ2CArzAHZuXJ8i7kbBw9Hdqd/389RYVqxLV1cgbxr5Vc3f7XhAkYHc8p68oHQg79pAMfnO+GrVS1sEB8Od7Gs/i08cgInvNSCf38gO/IDnlB9yd+YrA444wNUz261utQZv3ckkZ8k2DjkUjH7lSoBIxzlQowq7SOML8KRpbdREVNVVEwlUx8PT6vHjpGNgzL1+AHclhVksAstQ1bJLStc5IPHcyRgU9FFn/wAxIBsR0Cp9o4AyMh9gOcn9JTljgSVYbaLMktTU1EYurxioqamZMpRRHGJHUdXPlEceNzynGOVWuFhoKO0UqXy9AUqU/wDxFDTVZ5zAXzmrqN/PO+/Knz7BmI+y2af6it2rm+rwrmspFrfMxJOHr6r1Y5IjQ53bAB8xIa8wS8YCS6PUyUXDtGxaB6klpK5+YB5GAO+chc77lEUEnByewfSDNQNoxCLVDcXzm9XnxYOG6aQyUtNIxMldIW5fFkxuwLYG27HCJjHlOUsE12q3qquQ0lJSlo5GV1UwYXzQxkeUS8oxJIPLCg5V3ydRqSmqq+RpH8ShpKE8hcuqmmwh8inoKgqCGI8tOnNjzcx1W6u/HiitgtVupfC4Xoigm8NjGtRGGACLgFvD5+UADzSMR9oqBK69n5yFvaWSaaHieNXeP6twlR4ighiVl/aBVsKiAeYQhiBt5nY43YjlnTSwSQyXa7MlPbqdSiquyld08NOTt9glev8AhRnBkcsu4kpZLhcAtHbaReTbyqijKGNOU7HfkJXpzGJDzNI+uqX61Jckud0o3ikhCm1ULL/5bPkEkirnEu6qqj4eYKo5jkdxt/OQDMmwpUfW4rtdIClcuP2bQEf+TB8od1X/AJx2UKPh2Rd91GXy6TwVX7KtfJUXypXmdyVZKWMru7fZzy9vh5f/AE/8V28VVyihqYrZAKm58qmWRyvh0quCOZiTylivNgDI5Q3/ACwxl4tsNu4XtclbWTTTTyPzTS4Zp6qbmzyrnzc3MD7ggk4ZSYrLj9Z3PtJNtordwlZ5Kurllklkk/eyEkz1UxJPKudyeYE5PQgk4YExSbbQMJZOJuI2hppoI/3UX/LoI9gFUY3kOw6ZzgDcAK3YqOoq61OIL4FhqUULTUoGVoUOAFVR1kOw2Gc4AGQAhGgi/aTfti7IaW30n7yjo3GSvYTSKOsh+yo6Zx65vmcxgTu222W71EV2usLU9DTsGoqJxupOwkkA+KQ9FXtnA7k2VLbBIBLUwKuGDRx4BIbsfdtuvYdNskqnkiCx1VQeUFgsKEgkFsgbd3PT5ZA2yS5cLiaVo6WniFTcpwTBT82AADgux+ygJGW6k4UbkAZEljgTRRjmMXFzRyxR0yvVXOdGWnpmcleXIy7/AHUBxlup+EbkACo450krY4bh+8VsXe845TGQceBBjOGHNygDPJnu7afXC/XUjr3QK3LeLwFw/MDy/V4AM4cE8o5c8nNgZkO0yJVhjiRYIKJaSLxKalkwIrfFg/v5t8eIRzYXPrv8bjUDbJGKaP6sKeP6klJFSp4tJSuR4VFHg/8AEznPxnfC5yN988zrKVRIhMivHAGE3LUqVaRsjE84wO4HJFjOQNhgBJdHTIYjUVPOtOjidUqAS8j5GJ5h1LE45I+owuwIASXI55syZVgzEKWHMrD4mLdOfHVukYOBvqAZnD1GE8rFvMGDliWI5+cDOSenOBv92Mb9cacip+ZeVlUKRgjGwGc9D2yQd+pIZskqpcp6OP7gVugCjlxvkADqBnBwcnJBOWwNTI4ERBh2OcYPXJPTHXPX369873AxOCRkoVjUsh5fY5YHf8853+Z7nQS+JHDUGOWGFqgDpjmWLtnH3sflonebm9vdqeCRHqcYLD/k/wD6X8tVkksxYnJJySe+nHh+jYnzH6ivWaoAbFnHtpaQG+vQPXT3MUTzS10RtpAbb67mSc6WvSPTSwdTMk9UY1yBnXeljXMyTkjGkF11pamZJ4RhdeKO+utLUBki0tLS1ySeDB15ynXWlqSTxRjrr3S0tSQDMWlpaWpIBFpaWlqTuItLS0tSTEWlpaWpIBFpaWlqTpEWlpY3xr3B1JAMTzS16BnS5TqTs80tdEbba85Trkk817jbOvQNteEHf01JJ5paQGqNxnx3Bbpp7ZQrI1SuxnVQ6Ln0wevz10DMqzYhPivjG22ZZaVKiB69djE78vITvk5/prI7rNR3Oulrq2op5aiVsswUtk/gp03NW080zzVAq5ZWPmZolJP5trkVdDnC0tST/wDgk/8Ax9aqAOpn95wptCA4kGfRYZBv/wC0aS1dlWVRNI2XIAHJg9fc/rpyGuojU+ElFVGTHmIiBCfPGcamG7w24GGmtc9RPIQDKgLO/XYDl2x7aIRBjJg7uScDMJUHEvD3D6fWEtUNZWcuI58oyw57KvqfXQqqvMVyn/aVXA9USf8AAYhce52O3tr2G4mnkFV+zqiWY7Yk5h4J9hy7nVptdnee1Ld73Sz0nMWaKCrcDxiOhIODj9NVZqaCWPc4i23DGOJWaC4i5SGSehuEcA351RvMvovlAA6d+mdFk4ovs8ItFusLpQxnDiljc4B6czAEE+3qdGuHIrtxRNI1XQvS2qDZ6kSGKPbrylhv+H6DT9ZdbsKwcL8JUcdTRtgZp1Ic+pdgB/Lp7HcO7VqzbRzCqtOUyYHHFF7s0Jo+HrcY5JvLKzKJJZG9AcDHb8fy1F+s3ahf6/fLK0dXktG077E/Ik59dWK81K8I0oNulpTfSB4y+J4/IDn4f3Yx7b99s94/D9rvvEBe98WUkdPRDdZJ5jGWAOdgA22/p3HfWIuRSXPR/wA4l2qYgAf5+cACq+kLimVpPq7XCkRscxROQdgANvbtpi5XS9wQi2WkR0coYiT6ozAucjy5BIOMdh+ejN5vV+uF1Fi4SjNTQY8OOBF2PqxJCnByB+HoRoxW09u4LtPiXKooIL86FovqyuXRh7hsbdCcYBz1O2p+JVV2476HvOCgls5/X2ldgsHGlnozd75LSwREBz40is2/TYqck4PzwfQ4q10q77xDcCKSrKBdgVURIvuQgAz/AL30/WXPjPiSpaWZ2qadGYhqgxkLnrjm9Mdfl6DUesr7nTqtLTFaeQHJ8JlwD03xt/8AH5mVpld139oO7bTiqcT01bbYjFVV8FVKeisrO36np/vrryy8I3HiCoxTuI1ZhzPyEqM74A/3t7Y0Z4U4a4svNUkjMqwN9p+XLDscAdO2rbxjdqGx2Y2SlqoKi5kBXkgpk/dZBB8+eYtvke477gY6jVoMLgk/E00+nYksSAPmV658KJwfQo1TxCstTKMrSwph226k9hgfj27kBrPwhXcTVxbnljR2w02Mnfsue+/6592JcM8N8V3SoFTU3Genp2JIzMWYg98Ht269B366tt/ult4UtEtuSoWtusnUtSwN4JBz5iUJzkYK5+e/l0NZftwHBZvYTWtMk7cAe5g67fR/YuE7Ws8t5qqmtbIWlgRScgnYlRsM5BPzAyQQKnBYay83ALJH4IJI55jyIoz6nb/fftBt3D9/us/jU9QYqcnZpXfLb9MAen55/AW6hqKjhCnH1qup5ZWXMcVMgEsm+PjKkhe2TkZ2AY5AttZU3W8n2Em8McVYHyZOX6PeDbbQ+JPe3qpuTmbwaotzNnJ2Uknft1/AEilXe2iedoqK2ypToSEEreZvUsc/39BnrqPXU1x4nvDywE87dWdi6p5iRv3xk9c+5PQXDhXgKno4vFrK6QcmWaVJTGoXbOc57989x7a6pYJutBx+k43eE5MHWLgy2+AK26wx1AHfrHH+IyP99zvp27R8K0UGLTQWp6gDId5EAXfAOCRk+3T1J3GnuMr7bore1ktMlbLAGHiTy1MnM5wfKq5wBhumAxG7FRqtWHgiouPhy1Mzw0+RyoFBZ/Q59hnHpnb1Mqua5SFTC/2kKCvlmyf7zugsNZdK3woPCcsTzNC3iMfkFyfb13xsNjc4uHbdw1SeNeqGeipVXnaaamZebGw3IAG+2TsM6JR8PcMcK0ArL/EJZHY+DR452kfuOX17kbAZyxGQDnXFVxjvVQqpbaKljC8tPT00Y8oJyGLfaOR8RHL2RT1FF1TZ2UL+Z/4kOnBG68w7xffrVWn6na5bfRUikKXAbxJDj4RgZAx1x5mz9kbAHbbRHcJljFfTmnO2BlOYDpksAuOuB0HuSTr2zcDtWOktbNMG2CRKo2377dSce579dXz9jcP8LU4q7pEPrLEiKnQFmZ+4Cknmb1HRftH7J1Lfhhudcn+8zB870oeJHipbbYaKOesmpfqoVnxBVwvI4UZYgBiSfw0H4l4+oK+3LS0NVJb6IRZkWKL946tsF5sggHv9phnoNgH4qvcl5lVqiOCKmVi0NLCiEenMTjDnp5yOUYwoONoNr4WNYUkrHnSMEskayMNz1O++fnufbGuouo1Ry4nGbT6Yek8ziOS11fLDBVzCPkAciNFyM9B5vh/hHfc5OrjwzbbXPEqpWRU4ZsASLK5J7fAhznoB+GurRwHa0pPrld49PRxrvJJUMFCjvknZe2fXAGSQDHv3EsC0gtXDiPQ29UIabmKyzIdicn/DjPTmPmbp08o0s1LofKpHq+fiUShbf6lv0/B953Jx5SWaRqC10sFTI0R56qNW6nYJhhnP8OMNkZyMjVNruIaeorSZqSrqaqc807SzlmZ+yv5e2Ph6DvplohcXjhgQyJFnEjE4TPZQfhH/ANkfUamUfDdpiTzUccr5yzNvk/01pptHcx3tjPzM9RrKKhsGcfAnFLV0LsKtqRWkY5bxp2OCD32HTT9bxAkFOTFT0zMThEDkliOoG/XTdZSWil/dpQwPMTgIFz/s+3/wY0VBToWnnih5lHKQFyqe2B8R/hG3r6aMd2rG1O4PXXXad7g4+85i4oM7CNrdRcp8qHnJ53+78Q/E+nzxriHiMrPBFHTUZ5G/eckYIRj6Hm3776l0dskuEgWnpfChHlZ2Tc+xP/3I2/rpf0f/AEdrXkBIKeKBT+8mmUDf/fYaAsFiJusfAhiGtm8utIN+j6lrbjXu1Xw3W1MTnYQKsKuexLlTtg60PimaLhexJU3K0S0sAHLHG3EMvMTvhVUJ/oO+n+Kr3w79HFtajsVJFcL20eQUAIjzndsdPXHXG523GJXmovnEFxNyvP1ieZz5E5CAo9vuj/fXcqq6LtY+7OF/X/mMWtTSpg8mQ77xpc6mSqhpPrNMHmDQs9U8vJGM5DZGN8rufujA3yRovt2zHNLV1hLAgx4IaX+PO2B/fRc0dZzqkFJIz4xzCIhE9lH57/mdXj6P+CaCaUVt9uVNTxhuYxtOodj8j/M/hoz8OumBO6C+c1zY2yr8CcP8YcQyztASUXB5plOBnfG7DW0cK8NX210cSSvYqVlABkNtWRy3zLHJ0fobrwxQQpR0lzt0UajIVZlx8+vXVb4k43pqGFp6J2uNSSViWE46eh+wv8W7H7IHxBHY+o1DFU6/KMkrrqGTLPeblXcOW5qu48WRwomA3JQRxqhIyAcKSW2yEGWPyyRh/wBI3G1x4m+vUcfEFYLXViMMslKBJIUVmA2AwvPjyg4y2STjQ7iav4h4irEqLr+8KDEMCELFCuegGe+B6k43J66CVFHXqSkMQLsN3Z1GPlvpnpvB1C77m9X2xArvEmJKVLx8mVaWnmjj8OSJhyNmFRIOfPqcDpo3w/wpdrjVRV1bzUsWc+VjkjtgbatnC3DUEXLU1IarqichVQsFP5b/AD1oFls0k1QrVVHco4AMkx0UjnHsANE3ipF5Y8SlAdj9MqfCnB1wWslFrud0p0kx4hjqDGMDucNrWLJwXQUVNHLdZq2r5hgCSpkZ5G9FGdR6zi3hOwRxrTiWNieVfrERjUYOGY5wWwew77az3jn6QLhfIZaOhuVLSUcuVkZ5wJZ19Djov8A2+8W0ieq3VPhCQPkxmDXQu5uTDfFPFHAdtuRpUt7zlR5vqrxsqn0Lvsx/y7D1OlrIzTxFiUu1EmevnBJ+elpkvhWnAw1pz+cXHxHUE+mviUSSMEHI30FrqB4Xaqozh/toRsw9NWeaAHJ1FkTfcYOnOr0NeqTa0x0mraptywGjU9zpTHLlSnc/FGT/ADB/3vr0H9jUTSqUNfPmOnC7+EnQv8z213cbeyy/WqPyzDORjY+3y11b6ymrFVKqDJiYFoj1XHcH0/l323HlGps8PsKt0feelV69Ym4dj2jlrRbFaRXEZuNUMUq90HQyfh29/lq2/Rbw3JLVUtWxUVVRJy0hkOy/emPsO3qfx0Fttpnvd/nrK8gUcQDMY+gjGyxr7npjWy2mIcPWgXaeJUuNUoSihxtDGOh+QH5nWRqs8S1A09PCj/P7mUe1dHS2otPP+cSZxhW0ttt0XDFpJEEI/fyfacnc838RO5/AdtVHXTMzuXdizMckk5JPcnXmDr6foNHXo6BUg6nzHX619ZcbHiAzroDGkAB00tGQExYGlr0a4lcIhJIGBnc9tcLBQSZ1QWOBI10rIaKkkqJmwqjt1J7DWUcQXKa4V0jyPln7dlHponxrfvrtSYYCTBGcIPvHoW/tobaKeGGCS6V680EJACd5pOyD27nXz7xLWt4nqDWpxWv+Zn0DwjQDQU+Y4y7f5iPQr+x6COSMH9pVS4p1PWJDsZD7nt+ei0FO1htyW6n3vNwQGZhu1PE32f8AM2fyPvpmzg00cvFV1RZqmWQrRQMNpJPXH3FGP0Grn9F/C9dc7mKud2euqyZGlk/5Sb80p9D1x+J9NLNdq/KQLX9R4A+B8/mY1opFhO48Ds/J+PyEOfR7w1b7Va57hdnENtoFEldMSPOw3EK+u/XHU7dhrPeMeIK/jvi01boIadf3dLDnCQQr6/Ibk+ujn0vcWQXSoh4S4ebFjt7cvMn/ANZl6F/cZyB+eqhJTTmVOG7bGXraghatlPw+kQPoOrf6aroNItalm5/3PxOai02ttX/6HzHaOCC9V/gJI1PYraDJLOR8frIfVm6KPlqxcOW2fie9wTLRMKSNhT0FGvpnIX5n4mP+mh9NSJWyR8P2yUfsykfxKmpA2nkHV/dR0Udz89a/EYPo+4ZiqQgiv9dBy0UTYLUcB6ysPvsenqfYbYa29rnNKn8z/t+QmtKrWnmEce3/AD+sj8dXKDhqzPwlbJllq5cG8VEY2d9sQLj7K5AI91XvtiN4rZblWrDTgzKZAsaA58eTJ/MAk/MknuAJnE91eVpKdZWJI555OYkhTk4z3LcxOeuGJ2LkBm20c0TLBFG37SqkC4HWmhboPZ2H5L89ZKqN3wiy6gr/AFDyx6ky02z6zIbbC4eFHD11SBkSyA9B6ovQDu34a069XOP6OOGYUpYuXie5wclHD8TUMDbGQ/8AqMf19hjTfDNLauCeEv8AxVdokkhiPLb6boa2oA2P/wCDXf8AU6zO83W6112e8VTvVcQ3duaEY3hVtgwHbbZR2G+idHQdU/n2cKOhKXv5S+Wp5PcYSkmqaprDSSg1EuXulUzZCDqULeg6se520Ystt/8AEVxpbVa4JDaaSTw4UUYaqlP2j7n/AOxXUKCg8JDwvbXUuSHutWuSCQfgB7gHr6trb+ErRDwbYoZDEEu1TDinjI81JC32z/6jfpou42au38LT2e/sPj/PeDKUor8+zodfc/P/ABJRp4OHLQ3D9EyPUyY/aVQnRmHSFf4F2/HQ8hQMk40lJyfz1Hq5Psg+Xvr2mg0VekqFSDqeQ1usa+w2POaiUE4zhc6z36QuJVgR7bRuTK+0zKdxn7A9/XRXjjiJLVSeDBIDUyDyn7g+9/YazSijTwpLxcwzwq3LFFnzTyHfkH82PYe50p8V1xtY6Wk8f6j/ALQ7wvRdai0fkI/b4JqJIahIvHulWcUMGM98eIR6D7I7nfto9b7c4zw5b3aeeZw1zq0yzSuTtEp7gE/ifkNNUUFXRSvI7BuIrgmWI2FDARsB90le3Zfc60SiSg+jThVLpU8qXmoh8SlR1y9NG23jsD/zHwQinoMnsdefvsLH8NR+v2H/ACZ6KpRg2v1/J/4Ea4sudJ9HfDD2SkCPeKpBFWeE28YO4pkI+YMjD1A77UmhoqyjmlpA/NxDXpmunHShhO3hjHRyMAgfCpCjc7N0bVZqY+IKyPxbxWZ/ZNIx5vAQk5nfPU5yRn4myx2Gr5ZkoPo94ZTiW6EVV4rcyW2nkPM0z5P/ABDg78oJPLnqct06ZXWClRRT/n3/ADmqIbG8x/8APtPbtWU30Y8MJQUfIOJq2HYHrQQkDJb0kYYz6DAHY6zW30dS1X4Sc5uVSOaSQ9adG6/KRgR/lUgdTt09RXXC5G61zmruddIZIA/mycn962fsKc8o7nJ6Z1oVrSh+jnhiPiK4Iau+VpJtdM+7yyHP/EP7Ak8vzLemMUrKAIn1H9h8/nNGIOSev5+06r5k+jixwWO0RLJxjc4uREAyaCJupPo57+gwOx1TuFOHZ+IbitgtfNU05m5q+rBwaybqV5v+mu5J/H7umqakut4vdTQiaWqvlwYG6VS+YwKx/wABP4j0OPl662KkoKThKyCwW4J9cZOStmQ55F6+Ap7+rnudug0fTp2tb8JR/wD9H4gV2oWlDfb+g+f+p5UtR262Jw/Z2RqOIgzzqMfWZBsCPRF6KPx1W+JbzS2S2vU1BUuQRFGT8TDufYd9SrvcKW1296ypOI0GAB1c9lHvrIrnXyX+vmu1yLi3xMESOPrM32Yk/v23J7Z9Bqbk0NQ0mn4Pufj7mItLQ+ttOov+n4+fsJwrVVzuC3athaqnqZStBSkf+YfpzEdkXv8AID1xY+FeHqniO4va6eZZ6cv4lzri2EqXXcrzfZhj7nocD+HUax2m43W8G1U0ZNyqQsVW8Q2pIjstLF6MR8R7DOftatHE9wttrsz8K2U89shcQXOop23uE43FHC3eJTu7DOSfkD4/U3+YfLrPpHZnqqagg3t37Rniq901ZBS2iyQ+LY4Zf+BhKcv7VqF2NTIvaBOiqdj+eCLzR/R7Z/rcsqz8W3GMzo0m/wBUjP8A9Yf0b7i/j90abtccHCdp/wDFvEEENTeKwclroCAEIXYEjtCn/wBkRjsToLwraKvi27Vl/v1aRQRsauurajdWxsXb+HOFVR1OAPYTvHH5Tf8AWPcB8PJU+LxPxCZ47bTvzDbmlnlc+VVB+KVz0HYZJ2BJtIFy4m4g+p06xwzeF4Mnht+5t1MPN4CN678zv1JOfu68q5qu83ajttopJIpEylvpDgtSI/xTSDp47477KBjorasbi28MWOShpqgCGMBq6rzkzNnPKD1Iz0+8ST6YYaXSmximf/5H4HxAdTqAihv7D5M8vFdarBYBSUpMVtpsbgcr1MmMA/kDgdhn31lN1r6y5XBKyaEzVU5MdFSDOw3HTqFGdz1J2G5PK7xBe3u0/wBfqEcU0bclHTK3mdjvge52JbsMH7oNh4NsE6yz1FZMkVX4YNdVcpCUMPQRoPvHOABvkgDLMeUnV6pUUIg9I+kfP3MH09DFiz/Uez8faO8K2GGkpauauqf3WxutdtzSMelPH2ycEHtgEbKrc3lPFLx3dBW1EZo+GLceSKKPfn3JCJnHMSQTv8RDO2Avl4cvxpXi1W//AIDha2nErnuMgHPL8TMcA4zk8qLsNySp/wCKKn9g2k/UOHLehFXUZ8oTIDLkbMWwAxHXARfKpLJ2LAkdse4yUDHwo/zMeQji+oeMSCg4StwHjSofJMFJYRoT8S5Utn7bDnOyqFtEPg1EX1+pX6jaKAFYIQeXkAGcZ/6hByT1QN99hiNQRU9ZHH4SfULDbhzRLgAscZEjZ2LtjKg7ADnOwUapXHXFYuchhpg0FqpSEjSPqxOcAZ6sTkjP8TN7Wpp38e38/wDQmdlv+fE5424na4z8/IYqOI+HS06YUsQNlUdBsdz0RT6sOZ7hm1U9ooKniPiGbwOQBXZB5lznkgiU9XPYfZBLHc6i8K2iIJNxDe5kpKWljDM58yU8eSVCg/E7HPKOrNljsNiqzR1C0/FnElG6WyJ2h4esfN56mTuzepzgu/bYD01e6wMCo+n+f+pytCOT3HqVnjkpeL+JreJayYGHhzh9SSoXPxMPuAkFm6sdu+rhaaWrtNVVXK5ViVXFdWnPX1rnyW6LH+GuPhIBA2+HIA8zDUSz0FwoK2S+XiSOfiyuj5snCxWuADO3ZMKdvug5OWIBqvFvEsIp/qVvMr0viFQd1krJh1J7hRzf9obu7jILbrmwsKUitcx7i/iUFEt1tjZ43flhiOzVD/CXbHRR026fAu5ZhFtFA9qaJjTrdOIbmf8AhoGAKsBsXfGOWFeXHYNy8owqsQxZ6NrYI6+rpjcLxXsIqGiTYzMPLygD4Ylzgkf5BuWOjdgtEt2qa+n+vh4W24hvS4CuAP8AykBGwjGApI2OOUeUebRQgGB9P8yAHs9zvhyyrePrcRrZJrQZQ96u/wDzLpKCP3MR/wCiDgbfEeXbHIpkcf8AFMVFEtrtkeJFBpooID/hbEGJMfbwfO4zyhuUZZjzc8d8WU9np1s1rj+rtAPCihi2an2PlH/rEdT/AMsE587YFf4ctTUPJc6+KGoulSjfVKZzyxRRrnmdj9iFNyzZyTkDfmK9A3Hc36CVzk4EfsNt/ZKitrRTz3mohMiJJtBSwrkGV/uxLuMfbOVGRzk2nhmzR1EC3m65ag5zV08VX5Wr5F2NbU+kS5wie4UDJ0zw3aaeqhN4vEnjWx5PHX6x+6N1lTA8aXbyUsewVf8AKMFioVi63JuNKmoZ6l6fhimfnrKpv3TV7oPgX7kag/JFPdmAalthHA7myqFHE9r6scYSz1dXPLDwtSymWaSRuR7lKuxZiPhjXIG3wghFyzDmJ0VLUXau8Ry1vpKHlDFVCfUwFPKqr0FQV5uVc4hQsxPMWbXFFHPdatEjX9n0dHycoWPAo1wSh5TsZyCTHGf8MFpH8xzqq8RXwcTS/wDhXhorR8P0oIqqhXOJFyObz9SpbBZ+rtgDPlGu117Rn3nGYz3iK7NxdMOHrAEouGaJeSWVCQkqhtwD1Kc3Lk/FI2NieVdWWy2qioLY9RUOaG1UXMZZGbkYsvlIBHR/NysRnk5vDTMjMR5ZrbRW6gdpGNFbaIF5pG8jBl2O4zhxzcpIz4QbkXMrEiVFK1a9LdKun8Cmg5TarcUwIgMBJpFAPm8wCIM8nONmd1D6FgvA7nFX3kpA801Pc7hTCnEPL+y7aUwKcDCrLIoB/eeZQqAHk5gAC7DL/wC++tPBA0ZriviTzSAMlEjBvOwzhnK8wVc4xzb8niO8Vp5Vr1popYzdJUMjPJhkpI8EGRhnBYgsFXODlt+XxXdyvrrfZbRLLI8sdJC5ZiSWmqZidyTsWkJX2xy7cvLmLPBPAmgAjtZU2+z21pHMqUschKjmJnqpidyTsWclck7Y5fs8uYlZLVNUVn7cvKBKmMAU8CjK0SEgBVAG8hIUbDOQAACByR+H7fPU1K32+csEyqBS02PLRoTgKABvISAMAZyAAAQAlloT44WecGnRf8KJxvGD5QWA6u3QAdjyjYktb6RgTo+8k01KGYTToIxH/hrkN4QI5c7dXOeXbseUbZLFKakTyyyR8pU/u0Jzy56n3Y+vpkDbOWLXzSKs0scke7COJhkjqMkjYkgdfQ46Zz3VV1RGsdNTUfi3SZC0dOzeWMdC7sOijue52G52qMnidx8xyumWB1paWnWor51PhRdFVc4LufsoO57nAG52FeBBHFWKlYUiVgt1uwXDs4PKIIMb82TyjlzyZwuXOyVvBhq/Dq5BCr8t1u2MSSyZ5RBAFz5snkAX4c8q5ckiRDBKnhSyQ01B9Tj5qanfDQ2uMjAkkA2aZhkBR0yQNuZm0UbZIoqWGIRtJBT0CUUfiU1LJgQ22LBHjS42MpGcLnbJwfiYy6WiRsSMksUKOJ0jnBLs5PlnnHVpCQOSPscHAIHK5T0TcgeRXijjYSxRSgu4kPwzzD7cxOCsf2dtsgcswoydGwysxA591PRiX382+Gk+znlXc66JycLCOYEtIGVmK5m3VujMW6c+D5n6IDyrvqTT0aL0LA7DYEYwdgB2weg7Hc5fGOqenZT1OdhhV5cY6DHbHYfZ923EwQxxIuTknChRjf0AH+/55sJAI1FTogwS+DgBQc5z2A7k5/n1yeYXfbp9UdqelmL1O4dgQRFnOwPdt9z27d8+X+6RwO0FG/NUHIklVyVjznKr6n1bVa040Gh3f1LOviK9XrMZRIickknJPXS0tLT0cRPgmLGlpaWpJiLS0tLUkxOSd/bXWvMDXuu5nMRaWlpa5O4i0tLS1JAItLSxr0dd9Sdnmlr3HppYPpqSYnmlr3B9NLB9NSSea9Xrr0AY16ABrmZ2c4Odegbb690tSSc4z00sHXQ20tTMk5wdLB11pamZJzg6QG++utLUzJFgemvMb690tckixpaWlqSRYxpaWlqSRaWlpakkWvHZERmdgqqMkk4AGma+spqGkepq5kiiQZLMdZLxhxZcLtVyRUMyx284HhOPiI7nGDv6asq7pUnHAhHjTjiolnmoLTFz0pHKZ43KO3qNwdtUn6xITk2+X3zUD/8AE16ZK5RslER7K3/42lG1ybm/dUWAM55W/wDxtEKPaYlsTxaic9La/wD/AB//ANDTlLU1MkjctqqlhHledGLqp9B5d9P0lNd2hNRUW+nSiP2lcqz+4BbOP541w1de6rMdPbIXooDgsjhAo9PjAJ+Wt0QLyZg7FjPJLtWxo1vt9okkT4m8Lm5iPvPsdKGuqaaUxUVrlnmnGA3m8Q/wjbp+WnaaS7yubdbLMkqs3OwVjzH3c8x/DVhqS3D8MJoKSKpusrclRCXMjrtsq+UDr2ycd/TVbdQF4zzOV1b/AGnVugNooo7rUUEX7UGGipKjLKq/ewBnPpnqfXR2ktlwvcBvfFsT0ED+aJZZQvOOo8mMgbdPn1665jgmsVpbiC8Q00d25fEhpKyXnBb1YbYPz9Mewr68R3Hiqokrr/S1VHSLukrIRE3sA2OuPvdtKCz2sWVuPn/iMQqVrgj9P+YZgr+I+K6j9lU9tVLVTgjxKYmKBEztvuCcY/HpnfUG68T19hnksnDNLT1MUo5ZJoULSs3TkDDPffp33321z/4wvV1SLhi0WVo6ZsACiQqzgjcsTnrv33HpotM8PAlCldFRxVlzcAcszx88K43I5ZDgds8vXWG4Jwx/If8AM1Cluh+v/Ej22xJaKL9tcQ0v1Wpx4iwzzh2Z+vmUrksdtjvvvjQ6huPFXHdz+ozW0yUkQy7xMYYUAz1JBGw6fp311bRU8Z3Bqy6GsgjG4D8gQjrhQWU+vvvv305xP9JMVkp5OGbTRJSRg8gqKZwWkPdhknJz3yem3Ua6WYkDcC37CVCgKcjA/czriHiF+BS1s4aFNLUvtVMcSOm3TIAIz6de+2Rmu2u3196d7vdrHVqsnm8R3lXn22x5SAMZGBsMbaO8HWugSmm4hr4XqEhBcxVCSYznOSVQg9z11Fu/FdRxXUJQQ09ZR8wwYI4S+V7A8u4G3pvjPprVbBW5G4FvcyhrFqZxgewldut9nM5pLbbA9OPKnIzEk+3IB0JG+MDr6aunBvA0jW1LxerKKGPHiKJqzwjjuxV0b1HX29dEbXQW3gS2G+XOh+uzqFEaSxTRkMRsAGiAJxv1HfpnercR8ePxjcPq/j1dPTkj9ysORnO3MQffptjPuSavqbrjtqb8zLrTVUu51xHOI+M7tDVT2ywQfWKFmMQdfPJJjYkFADy7jcgdx3wZvCXC7vTNc7xZlpZEHiHx6l4u2Sf3kbD3JPpk+urFZ1s3A9le71tIlVKAOVyzqebGyqGjAzgbYOcA42GqJxbxl/4qq2p6evmpaaTBEJiPm32yQemcED5Hcnm1lU1jNtrIJ9zLuqBQzDA+I5xfx3WUFS1PYCHp+VlLhxKzNncqVVSNsDoCMt2IyI4eoLpdKhZJbFCHZtlLOCTnHRj8sbd8al26mtNjjSsrahZpSwUHK5UeuM//ABn5kkKj6QLb9QFNaqkUjzDlaaWNid+y4G2x3OcnONh8RpRqBlSGYwXeLjyMCR+Kr7X2mdaG2pTtKFHjqZFkEeCeZThVx2yDsNw2OmmeGLDf+Ja+ZzYFqOYc0k7GSPJOBnLA4GMgA74HQDbRTgW1WqeojqqudZoi/MCs8KZI6Hzuu/p2XOwzubjxH9KlktFEbLYQlHUKuCWIbBJ5dmj5hkkHzbnsN9wDbbqN20EFoQiVbckYEqPENNW8I0kkMsFLSy48saS855sZAxyZJx27DGcDGqdWcacQVatSqiyxO4McXhEk5+Enl7AZ36bnl6k66qqg3utapku1PUSMWBISQhVznYFfXse+55j0vnCFitdohW43imrxTggmTwCPEJ36sQcbfM/horbaU3XNiDh6w22scwLwNwxeLpAla1gpRGo2kZxGFxuRuremf10T4xvEvDaCChaOO8LzcwSu8TwcgcrMPCXBO+FzzHsNTOMfpNpqu3Ch4br6Wjp/D/xDJylFzgcuARzZHxHZewZhkZzDQS1kjYrqcRZPO4ZmYk/F2zv3OcnuQNtZ1rqbzgnAmjGmkZ7MhV3FN7udVzS00dbUFFQs9Lz8qA/D3wM746euTo/aqS7ySeL9SpBNz8zPGYlJ9z5SRtt66NWykobVbvG5jHAPjqDGQpx2z09Nu2uq7iMx04hsFZTiR15mqlmXnQekY7N/GRt9kdyawbTj+mQTBQfP+sED85H4pvNx4fEMFK6wXQIwmCVBZoScchccg5SfN5PiOO3esSXa/wBdIPHpo6qseMRYkpAzRqPvnlyAdsJ2zk6sFosM7zqufVmljy5UnryYyeYjq53PbHUabwnS8NWSkEkv1gOo3Y0MwVPxK9ff/wCdAO7r6mOTDUVD6VXiUCxWS8zss1TaKQO2Dl6WQEn8EzoteqmjslDIa2htEkxRhEq1FSGaQHHKFyOY5G/YdznAJri/6RaWOlamsM0M7s3IGeURgD1Y5BA9hucblRs2UXBq2pmkq554aqoccrE1Ma+XsMA+RPRF6gb4G2uVDVXHBOB+8q5oq+5kS/cUXsz1MctVik5g8Uan6xHGF2ChiMM2CRkbDf1xoRDxBfalpJAtQI2wyqaYHm9ieXfbv76P0NpaaQVFdNTu3RU8ZMADtgHGPYbaNRU3hoZJRlR8KqQC3y3xpxRpBWuWeK7tazttSvP3laivVz8FmCV4RereCQB+ONQq6+Xhpg9NPVKIwVby7nO2d+m/c+mrDchcaycKVEcKDyosin/25PX3OP5jUeS310XKlPSZYHbzDlQ/ifM3uenbXbGZuM4E0RUU5IyYCa/XyCIePVVbMh3RVwZc9AO4Az176kWmr4qlU5etwG5lVkIB9Qd9uv6astlsHhyeNUkSzk5PmBAPr8/fWl8DWvhpB9fvt4o41iO1KJR4rn0I7D3OPwG+hrimnr3s+f3m1Ja59qp+pgz6LLBxBUTyXSvp6BbfFGed7lC7x+ucGQb4GnvpN4gFuma1W6m4XjqwUw62Uhx5lJJDc2Fwe+5HbGCSf0icd1EuLbwtTsscflFSq/uocf8ASX7bfxnofhHRjk81HXYkmajqpmkOX2JeUk7lz2B327750rp092sc22nA9hDmvr0q+XXyf2leqKy8LPI0lbO8cg3kiyI4ts7dAT18oG2Pnrmhk4hulTEtI9asSMFeWR2ww7k77dtWO2WGrrpxNcw0MI6RdDjsMdh/v53W10VHBGiNJBBEowq8wGmR061rjfARa7t9MA8LWa+wV3jvUW+pVfhNRHI4/EbfhrU+HuGrkIluVTPZqeMZZGjsqmRiBnK87du7EYHU4Go1NUWi1Uf1l5oauVFDiGE+IF64yF3Zv4B/3FRvqjcXcVcS36KalWGspLbJgPGE/eT46ByMAKOyjCj3PmKt6rtS+ys8fJhyMlC7n7+IV+kH6Qa9/CpbPxGkz04mEs6UarGvMvKOVguGOCwD7DzEgHZtY1W09RBPURfWZ6imLH/imUqX325A3m3Hr66sVRSVkMfMaCZiPhVYzyqd9ycbnf8AX85tj4carlFVeJAkfaLmAJ+foNMKfD66OVbmCPrbL+14lStlovl6eM0sEsEKHlMjYwwzuTgdflrQ+EuAr9UXAQ0Ne+Cvnbwvh9yzJtq8cL2i1Txk1NyoqGjh65lUMfZVz+utAluHC9toIoKK40rQk8vgwTqWmb+Js7DrknAGlmtvNbbaySYfp6Q4ywwIEsPCF0pYz4nGt8jhhGZJEqQsS49NgNBOPeJ04fjemXi3iKoncD9z4+JDnoW2zGuNwPjbsAN9QOO/pCukytQ2GCRQMgVCxkIn/wCCBHX/ANRhn7qj4tZM1Ncp5HkenqGYklnKkkknJx8z1J6++qaPw27UnfccD9JNTrq9MNtQyYJvT3C6gJW1NZViAcsSyvuEZmZh1OMsQfc5znQpoapSpkTmqhtEFkbIH8R/pqyNbrrLL4ENFNEpO7upA/M/z1aOGeG6OnljM0sUlUxwGdgApPff+Z03GkqpUhTgRf8AibbGyw5lAi4Rv9Yn1h1WJm3OXIz+Glr6Vs1g4ThowK68UU0x3PJOAq+w30tLTqdODjkxmiajHtPmTweYHfTEtLkdcakspHfXBBU9Tg+mvRYsHvPPK6D2g6SBuYqdmHTQe624u4qKdjFUJuGG2TqxShjkcxz89Q5Ygc8xOfXOstRpTqE2PiGafU+W2VMgcNXuSjr425EWphIZoWHlcD0Hp7Dcdtai3ES8SzNXsVjkwB4AO0S9gvqvvrKblbVnAZDyTqQVcbHPbfXtkutRT1qxuTDVqduwkHsPX279u+Umle3wXUZYZQxrrKa/F9PsBwwmrgba9AxofYrpBcoPKQs6jzp2PuPbRHXv9NqK9RWHrOQZ851Oms01hrsGCItLGugMa8bpreYTnOATqnceXxYo2t8D+Yj98Qe3ZdFuKrylqoyVb/iJNoh6fxfLWWO81xrOQB5Sz4GNy7Ht+OvIf+QeJMx/CUHk9z1n/j/hYP8A+TcOB1H7VRyXKtzIwijALvI2yxoOrH+mi1BDFe64zyk0titqZGRuE9cd3Y4/PHbTT00tRNHwza8SyM4NZKnR3H2c/dX+fy0U8CK5VMFhtTD9mUh5p5x8M0g2Zz/COgH99eesevSVY9h+5+PyE9Qoa6zjs/sPn8z7SdYKOo4mvi10tNiljKw0lKv3c7IP5sfmfTV0+k/iBOELA/CVskVr1XIDdJ0/5KEbRDHTb8hqc1XRfR3wjHfJ4l/alQhjtNK4+Ed5mH5H8hrGoXaqmqr5epZJlDl5Sx808jHIQH1PUnsNBaSh7rDbZ2efyE2vda08pOh+5ntOf2TRR1IANfUgikTG6DoZT/JdFKaiktVMLTShnvNco+tODloY238PP326n0Bx3OmrZ4lKp4nuaJLX1BIt9ORsCuwfH3E2AHc7eur99FPCBrZqi53eoMUEamouNXKceHGck5P32H5D56I1mp2AJX2eh8D5/MzOikHJbr3P+35CHfo9sNt4b4dPEt3iWWkp3ApYdh9dqB0A/gXffp1Os7+kG/VN1uVRX1lTJNXVbEYWRlQYBHw52VQcAfIdS+rJ9J/F6XKp50Q0ttpE8GhpQP8ADTpjHTnYjfPfY7K+czpozcKieqrWZKeMA1LJuQpzyxLnqx/qSe+l6V7cVL37mbhw58w/SOp3a4hHEtxmAn5pD9VjlOfHlzlpG9UXOfc7a076OOGYBBWXq/VBhoqZTPcqtzvg78g/jbpj0wPUaEfR/wAOVvEV4hmECRs4xChH7uniXvv9lf8A7Jsn1079JPElHd5V4YslSYeFrQfEqakdaqUHDSn72Tso7nf01tXV+KsFafQv7yO/lKXb6j+0EcdcVNxNdX4grqfwbVSH6tabcPhwOi4/Isfw9NDqRK2gH1l8zcSXXBQd6aNtgfZiOnoN/TTNHJGQvEVfTKtLD+5tVC3RiO5HcA7se52760X6KuD5K+oqr9xDI4iX97Xzn4t+kK/xt3x0G2mWpv8AKVaaRlj1/wA/8faBVVh8s54Hf/H/ADDn0VcKUdhsycQXGJZlD/8ACxMP/Nzj7Z/9ND09TozVzz1dTJU1EheaRizse517dbnJcarxQixQRqI4IF+GKMdFH+9zqIHYjrnXpvCPCho6ufqPZnnfEvEfxVmF+kdTiok5FIB3P6arvFN5htNvaeQ5Y5EadOc/29dFLxXwUNLLVVEgVUGf7Ae51i1/utTxBfUjlZYy7ciozYVBnpnsO5Ou+K+JDTL5NZ9bftMfDfDzqnLv9AnPNJeq+aurp+Smj/ezzMOg7YHcnoo0Wt/l8C91FLvjwrLbyM43/wARh3Gd/dvYajUkdFUwl5Gb9hW9wSV2avnxtj29PRd+p1euCrRDMKzjDiyb6pbqSNTNyjAjTHkgjH322AA6D3OvLX3DTJsQ5Y/5n/ieqpq8xueAP2Hx+cJ8FWik4ds0nF/EfJVTSuzU8Uzf+bmG5LE/8pOrHufXbNKuNyk4lus/FV+eWpoEnP1aFsq1fUYHbsoGM/dUKOp3f4t4lHHN3kkeoSisFHEomMfwpCPgp4geu/8A7m3OwGD3BFkiu0z8RXrltVktsIKKd1pIM+UL6yOScdySW+7rDcmkq2qcsff/AD2E2ANr/AH7f9yfwpbaa20FZxxxi4eMNymP4frEgA5adB2QADmx0GF9dUXiS913FV8nv95ZnRn8OGmXYMcbRKB0UDHMR0GB1OpHH3FR4uvKqB+z7DblEdNTj/lIM4wPtO36nJ6DY3wLYIJ4puJL4HorRb4gSqgkxRnJWNPWVz+O5Y/Z0KmK139sf3Pz+Qm559I4H8f9mEeELVb7BZKrjbi0q8KNhISMGqlAwsKDsi7A4/y+uqpdbneb5xGbzWHnv1wXNHCfgoIN8SH0OOn5+mlxPxZLxVe4ayWgKU1IBBZbKN1B7M4HYZyfX8zrQeBLEnCtqHE92ha5XiufxKePAJkYH/FOSP3Sn4R9oj0AwbTlQEq9Vj+/x94LYRy1gwg9v9v+YV4SsVNwPZEVFJvlSnPzt8dOrdZGz/zGGcD7K+5Oo1ZUQUlO89TKI4kBLMx/3k6jT3W4TTS1M1tq2kYl5JJWUZO5JJJ1n/GV1n4jlFBR1NNEkSmTw+ZiRgEl2IHKAB6nAGfXXpE8vwvT7K+XP7meeIs8Tv3Pwg/YQZxNdpuKblIDMaa2UikyuTkRpnH4sxwNupwNd2+GeSqpY6GHw650xQwDcUEJO8z+sr7YHXofu6EWZauJKOlNOtUjs09JCYyEmfPL4r5+JVwcduo7nWmU6NwJZnnVvrHFtfA1WJJMH6nFg5qpM7A9o1Pzx0GvKajVlxtU8nsz0tGmFZGeh1PbhJScF2ebhu21DU9yaLN5r13eijf/AJCnvUSd9/KNvUhnhi30Fvt3/i7iOn+r26lAp7bbkbeRuoiTuWPV37A+pAA7gO0rdaA3+/zNSWC2sZ3Zhl5pWO7tn45XOyg9APQHMO51l3+kDjOChpqc0tNGFgoqaNsimj7oPWVsgsevc7DYD04wOv5hQBJye5IoKe8fSLxZLV1jKY22lbPJDDEgz4a52WJB1PT+tsuFdDLHR2ewxF6NZA9FHyHNXKML9bkXryDOI06756sND+LS1r4Xj4a4Y8J4XlWKqlTJ+uspJZEx1hjI3P22BxsuNXHhazLYbY1ZU1TTXyui5mqAcNTJjqD9lsZx90ZPUnB+moex9qj1fwIJfcqJuY8fzJduoqfha1Tw+Or3GZC9xq2YHkB6oD67eYj0CjYayXijimO+3N6fxGgoKPzFDgvI3QeX7THOAO2d8Dm1M4pukE1RNTUdRIbdTjM09RK0ivg9QCemSABjJJHcjAyzcKVV9qEmpYFpp5mApolRQyxjqzkdCwB36Df0OC9TqK6KRXV9I/8A6jBNNU1tpezv2+0O8HWepq69amVI4azw+aPnb93QQAFizE7ZxliT33P2Q0+vqTxHV/8AhfhqXwLNSc0lfXMeUPgHmkdux5S3X4FJHxM2vLsjXOKPgThR5S0pR7hWBt3I8wy2fh2yATvu525cOzUCyUcHAXCysHYo9ZVQuRkqQ4ctt5duZQe2ZG+xhUzNuLN9R/b7RiiJjA6/mTqqKGsih4S4Ykjp7dTR+NX1meVYUxuzsOj8p3H2Fbl+N2wcoYaGS3R2+2/8Pw9RqsskpjyZz0EjKPiz0RO/ToGJ5o+HaMWFeE6FE+rEc9ZNuPHZT8ZJ3CAke5JxuW2Cca8Rx01EOHbRMkcEKk1dRjlBxgEnGcdlIHsi988ppZiR7e//AAP95W20f5/MG/SdxfJUwC3WWKaO2QMBKceZyx+I5xliR3xzEDoANC+D7dFczLdq10o7XQKXaSU5SCPI5mYj4mJwDjdjhRsANdcL2GS+1geQeDQwBpSZiFCqB55ZD226/dGFG5ObDTU9tu9DLUzPJQcCWuZWwEw9yqN+XlXuTvyJ0UEnuc73OOVQ4Hv/AMCUqXIyw5jTVtHcYaXiC+wVlJwnSVPJa7eF/f3Goxku2NucgZydlGAOo1ZbEKo8SrdrvS+NxFNT81vouXEFqph8Gc+UEDLY7YLt21zbLfNWz0l+vVCqzlBDYbKvmSliJyrEdycZz9ojPQaE8X36LwqqkhrOdGb/AOka9PMZmY/4MR+0CV/7yuThEzoIg2Hav/1CeEGTIvHfERltdbb7XUZjaQeNXHJerm3IRR3XcsM/52xsAH4epmo4zerzRtLUM4goKCFSslQ4GyRjcqg5ss3Ucx6uw1OtFvip6YX6+xSJEreFRUUW7s53ESZG8jbMzEbDc/YXVlsNnutz4gmpopIor4YuWuq02gsdKMnwYyekuCct1XJJ8xJXQhcYXgD95WsE8tItis9yu15qqFauNaySH/6bu0flhoIVB/4OA5wuFyGIP3l++dEOIuI4uHeH4LbSRLQtBhYqeHcwH7Lb/FMwGVzsoy5xhQpDi/iG08J2CKy2FVhpYgrKCuWdjuszr3Y4zGh6452wqjVL4ftc088N8vEMtTPPIy2+gDZeaQ4Y7nv0Z3I2GD15F1Ud5P6S5JJ2iQ+EuH6qmqYbjcIGqKioDigomlPMWzzOzsfgjXPM77fmRi4WOyz3dHr6tlmopvM0jDk/aUkfwgDbko4sZxsDgE74w9Zbb+1TJV1jLPQSERTSRHkFwKb/AFeE/YpY9yzfa3JJ6s3c7nPxbXT2i11IgstPhLncIsIHCgkQQg7BAFJxsAAXbGPLSyzbwO5dFwIzdZZeNJpaBKrksFGR+0a8AIKl0BIiiB2WNBkjsi5Y7nU2y2qqrzS26lkMFHQxpyu8OfAXrHKyd5STmKLGcnxHAOBqTQU61zQW21wxUtupUVokaMtHGnMCs0ikZclsGOI7yNh2GAoAXie9yXiobg/hV2ht8RkNxr2lyWJBMpMnQsRkySZxjKjy5Ldqrxy3f8SM2BmQ+Irib5O/DHC8xgs9OGFbWGXIbvJiTvzHeST7R2GRjJuw2WjtVDK0TtQUFO5lnnZjGwdRuxO5VxkevhBhjMrgK7Z7dQ2ugMSMKKgowHmmb92QUweY53VhkEAj93kMQZWjVXrfLFeFhuNTTiK0wEfs2gZcCVl6Tyqc4Uc2UQ5xz8zczOqyaE7RKqCOTOqenNb9Xr62kEVHFytbLa6co8o8k8q74wGHImDy84JDO6q89ad45hSUyRtcHQO7uuY6OLzDncZ6+Zwq53ywzgyuYt1vH1SsipoiKm8VpzGjgkRL5syuM9Bl8DO5LDOTI+p01XQWCzzT1MzpBG3iTzvgyzynbJxjmc4wAMAAbYC5WmDnA7M0jlY1tslpeSVpBTJJlmbzTVMzbZPQs5wfTAH2QuU4sVoknqhxBfUWCSID6rTYytIpIAwAMmRiFGwyTgAZA5ItmgM7txRxOI6BKdS1NTSv5aKPOOZh/wBQ4HvkADBA5CdorZ7hz325xm3WinXmooZlw3KRjx5B2ZgeVUG+DjuQdQNowJwHJh2np48Crq1EMcQzFEdxGD5QTj4nYHlAHY8q7EliUMSBVqqvyLzYijJyeYg/mxGc+gyBtkkHaoLjX1q3i6QzU1Kpxb6An96zEH95IO8hGcL0Rc574mNDWQXdaifw6q9zqVoaRCfBoYc4ZyffbmfGWOFXHTVNstC9bVtT1MVFTIk90nUmGHmPLEgOC7Hsg2yepOAN+gtpoI4KyOKtkSkjlC3O6qP3tRLnlFPBy75yeTy/DnkXzklVDRQwUlarXCp5JHC3S5plZaiQHlEEPLuPuAL8OeVfOSQ9FBHBIh8CnojQxhYo+UNDaoyOUeUZDzsDgAZwGwMgnngwJ2cQlo54meKno3o4gYIMBoLTERgM2NmnYHAUdASBtzF50MFTzQ8tNNGFbxY1lXmaMk/40g/5k7fZTouxOplsooYVSaeJ4kjfngpm88gdv+bJ9+Zuw3x+Z0QmldH5UTLYyCW6Z2PTf2JG+/KuT0qT8S3tIPhzR45sK3mKr4mSudmPMOrHPmf35E3OdPw05THO+GwM8o5cY6YA6Y3AA+Hf7WWHcED5Mjv5j1PQ7Z9OmBnAGw3AOeZhMSKNAAFaVuiqN8n+Xb2xjsBtcSs4hVIwM5JPlVFG57YAH+x7DOgnEF1iQyU9FyNKQVkmG/KO6p/U99K+3nlV6OicAnKyyoe33U9vU99V7G2nGh0GcWWf2ivV6z/Qk47aWvcb6RGnoimeaWuuUa8Az11JJ5pa6Axpco1MyTnXoA5c695Rr0DbGpmSca9A2317yjXuN9TMk4wfTXXKNe6WpJOQN9dAAaWlqSRYGc68I6nXulrkk8Xpr3S0tSSLS0tLUki0tLS1JItLS0tSSLS0tLUki0tLS1JItLS16BnXMyTzS10V20guRqZknONe4PprobaWpmScaWvSMa81MyRaHXq80FpiLVU6+Ly8yQg5dx7D+uoHF3Fdv4eAjqGJqHQlFAJXP8WMkflrJb1ckvtWai4V1JKc4UNMqhR6AMRga1RM8yhbHEIcTXC83u4GqIrqWPHKqQ86rjtnHU++gxiuCZDV1SCD/wAzfH56ZW20Ln9xFExPeF1Y/oTqTBaalWEcb3JGc4REkZcnRCqepizqJxHBcG2+vrjO3NAjb+nTfRZbfcbfF9Zuc1CVYZSnMaiQehbC4/Dt+GvJaWSyAvLfZp6ojJi3KxH0Dc2c6hPTX0yeNXVsEwbJWCojBk5fvMcbfLWgT35mTOBkcT2eq4griKqcUstCSQnieVnH8O3Qeun7Wl/uMqwU9BStQwnBk5uRYx+Dbn5DR6x8N3iromu1/qaWK1KuPFeMh5T0Coo5fl/rtqVZ6K/3mV7Xb6Kma0RPlpD+6WNfRjvk57YO/vsBrNbWAQCeJoumY4LAQfRVl4iqTauGrZHUrOASUz4oPcl9ttjvjp+J0YuFQvA0QrYEo6u7ts8LMZGi/wAhGMnPoPU++o954km4ULWfhymguMlQv76aBXabPcc2Nx741DqeXhqnj4gvFDJU1k/mFPLNGHjz35Qc49yBoMnzDktgH+5hGNvCjkf2E8QVV1pX4j4jpqiBlb93TVUqIspHoGKk9DsAc41AivI4tvVPRrQT0kceI0WPzRp6n37b66tbzcaV61M8lc8YzhDTnlx91eXmwMD0+ejEPE9CIVslhDUUoyjvIpVjvjynGwP3j7+hzo1mwYDDPx8SiqXycfr8whXcS0vBcMtmorcy1MiDxK1cuWY78uCAc4weUeu/Q66tlDDR0snE18pK6thUeIweCVCe2SWTlO56Z77d89Wq7cJcH8z3SVZ7xy80Skq0YznGCrHuOh+Z9dVyvquI+PLi1Q03i0QOy0xMqxgeyjJOO+AN9sDQSJZYTgj7mFvYlYHH6Tri3jqLiaT9n22ra30/KEaIoyk+2RsB7d9s9sOW2Lh/hSKKa51Ucs0wPI8MqSluowArHl3GN8fpjU2lj4a4coGagpaauuI2MaKOcNnfnPUb9uu22Opg2mz1nGt1L3+5Q09PjBSacIFT7qrkYG3Qf6AgFq1IQAAdn/iYEByGY5PsPidxVE/GFWix1EX1GNvJFBlgvbmIx5mPrj09uW6DiXg/gqgkpKHl/apTLmdPCkcnPdugOOu/4nOB3Ed+4b4Jtxs3DVugnqSMNK6eIMkn4ic56ny79d+41QrTwfX8WXF6+5hx4zmR+QBC/uTjpsOvp366DWk6jJ24QfvCfOFIxuy0mV0fEfG1zNRUM8tOpyopiZVjXOcAJnf575367myWuDhLhWiaVIaeqr49vq6oBIG6+bIz+Yx7HpqFcZ+F+CKcUVvoqevuij45FDCI9N/f29eu/lNTsnA9y40uT1C5pImP7yULnbt1Jx0AwPugdsDVcMhVFwg95lyDuZst8QpdrhfuLLgkdZVJSUwPkR5hHDED3OTjPqd/+49LMnDHCXDfD09VFHRXK5NGT4oYvlj2HKSe3bc4ye+JFXScNcDWlYfr1dWVJAIRap1Lt64U7KSD2OegzuRlFVT3LiC8TVFud6fnYnm8QlYxk9D8ie5+bY2pTts9FSHEswKeqxuZxXrW3KqCPBMxbCrEQ3TORnf8cfzxzCzcNcC0niJNWQmep25Vy2Fyc4wOpJ7fzO5J8K8I3Cmh+tV16kEMQ5pZHRXQDOM5fPsOh39SdB+OLwampjgsNTKnhkI0iwRxGVhzBtowvQEbEHsWK9CS19SNs25P8TBa7GGd2B/MP32/2/hunNNbPqsldynmkVE5Yd+oIGCffcDtzNjFCjtFTxFWSVdQ0gWQt4s52eQsTn3JPqd/UgYXVr4M4Q40urfWKmdYqQAcrTkPzEHbpgk/kATto9xDBScLW1vr9fbpqgxt4EEcUwkYj/LLyhQerEYGCNztoettNU+X5b8ps63uuE4EA2jhSzWyjepq1WGli8zyzucLnYe++NgNyRgA40C4pvlNVwmjobdBR28MBymFTNOQftnqAPuA4H2znGRVy4l4gnqDTvGtaUlJgj+rlwpYfFuMjyjqQCw7ADchaaO7zCOee0USScqldkVlx2K9Rj5aI8uu5tznAg4Z6VwvJg208GvcgJKmWWnhyWCKBlsjA6j0/wBAO9jbh6zWukM1XIqIuAS6ZJOMDbuT6Dr+Z05cL3V26gAeFBcGBMcZkUAIASXKlRgbdSw67Z1WpOIXrZIpKu3pJOUxEqSsp3+Jhk+UH73VtbPbpwNqHGPeVSq58NZzJFbAlcfBipkp6aNmQc0eZGJ7MV+Jjj/DXp9r3s3BX0Y1V6ADs8FJgeJzKCX9Ocjrjso2G3XrpzhyKkabx3pDT8i8sQ5UlVR6KBJsPX1751crt9Ic3Dduj8N6dgDyGNrc6BTykjLCQ5zj36jO2+lt5THpPJ+8OqDng9SxU3A3DfDlE07zVKeXfkqGj58Dc7EBQOpJOB31l3H3FFNXqaKwtVGIOH+stWzEEoc5hDNsB3lbA7ADoQnFX0jT8RQZucVYkYGZYUbCu4JKqwxud8hM4HXGSSQUdVbbgoH/AB6KwDHKr+8wcdcb47AbD013ReHFzm1s/bMpqNWK1xWuP0gn9n1c8rw22QcxfnVyWIQnPMwPcnpk+mw0QoeFLlT8vh1NKWByMeID6Y69NXGx01qFteaGtpacKd4p5eV2x+GO/c6irxLZI5ViacF3iLqU8y7Z6lTkdDkbN03HXTtV0tIwDkiKmbVXc4wpgaS23CijM9XV0yIpwArSczN91Rnc9PlkZxkZhXwXO6qXuFbNKIQuI56h3WMhQAMk7HC/CN9h0GikdTQ1tWsr3iMzSpzIzRmLC52CdkXruPfGNG7JwRdbzPin8OoWIHlhpiPLv2Gdu2T10NYEtO61sY+/UJTdUMIv/coUFmu1wJipY05WwZZCSCzDYYHbG22tp+jn6MeKI7fBUXCpqqFcfu0hrTG5Bxudsj5atnB/D1LwnQftG5cPXh54U5jJ9UBihA7rv233/lpcV/SlbaenqaC2SeFVJs0c7iGQMeoOT5ANsn4jnbHxBNrbmsOzTZP3h+npAG6/j7Ri/wAsvBsUs8nFl9EsW2Hr1mRWI6EMDzNg55QM9zyjzDJ+OuI7txTFNDUXe7ywMUligl8MOWVeXmLDHICObbGOvU7lq6tXXWuFVXXCiml/5fLOvJCCc4Rc4znfJ7nJySdRktNdPL4OYYYGPmbx1Yv7sQck+3+yVpvDBgNc2WmFutYHbUvplXSK6zyiKmR5Z5F5H5ZRyIPbbr6n31fPo/8Ao64kujhkrXgKN+8Z8MqjsD5SCfz1beAeGbHDma4V8UMQO43LyfiBgDWmwcR8OUlG9LR1cUccQCRpEQpJPpnGPdjgdydZ66zZ6aiSZppqy43WDAg+ycJ3WiQRS8ZVURRcvy0tOVQepJj2GhHHfFZ4cpKy0niarq66WFljiaih8TmIyC3LGDGp6YPmIbPkHm1XeNuM7vLOaGx088Socmq8NsIRnzR5GS3X942/3QueY5/HQ1szyzTpVKpOZJHRjJIT6Drknt19cb6y03h1t433tgfpmXu1y0+ioZMHcTVd8uN7avW5VFyqZyRIkMZhjjwSOhwAOUAgADA6750zbqDiCtZaS3yV1QSc+Puxb2QHqM/aO2OmtG4T4PN0ZYqjwKamGCYWkXA95D9o/wAI8o9+utZs9ktdppitI0JYr+8lLDmP9h7a0utWkeWhM7VW1h3uBmYrZ+E+KYIkMktUzEgt4lGsnbtk6vNjtt5tMBr7hc7bTU8fxGsssXJ+J2P66tstdb6GimqamshhpYcsZXYAYz/fWGfSjxu3FNzFLaDUrb4MqjyDl5j3IXt/P1I6axoqu1Llc8flL3NXSNwHMNfSZxYtPNV2gXTh+vmqYiGajtbK8JHQBg2AxO3sOpGstrbzeKuniieVqWSIEO0EbJz8zcxOQfMR0HYDYDvqTTQJCDy4aToWboP7/Lt7a8epYz+BTK00rbZAyflt/LTVfDFUAlouPiRYkBYMkutxCJUS1FYoAK+ESx5/f4v9++pPD9NxHc52eKepp4CCw8STlGewBLAat/DnCbF1qroDJIdxF1x8/wC2tDtNnZiodCq7YUDUur2LkvL0tvP0zP7HY+KHynj0Mi52d5Axx7+fWscDcKcQVlKo+ocMoiDBnkt7uzH1yXwdWS2WWitdE9yvk0VHSQqGYSHAA9WP9NU+8f8A3wCUl7jo+G7PHV22AlJGmJQy7EDHXlHfGMnHbSS1tRflKuQIyrSmn1WHE0sm40qLAK+31DJ5XMFnDBSOxIbGfbS18tcU36v4iubV12qFdukUXKOSFfuoucKPl16nJ0tXXwS4jJYTM+MUg4AJH5Sr9iNchcKQemu0xvtnS5R317AETy3MYePsRph4sg5Gp3JkEE7jTbJ9rqdQGWViIMkiwDn8NDbnb1qVIOFkG6vo9JF18uosseM8wyNVuqS9CrjMMovZDkQJabpVUdasVS7R1KHyS5xz/M/e/Q998HWmcP3qG5R+HLypUr1XoG9x/Uf7Gf19DDVQlHAzjyt6agUFbPQVawVbEFceHMT27An+R/A7a8+j6jwW3cvNZji+ijxera/DjozYS6nuPz1DuldT0VJJUTuBGgyd+p9BoDZ6qOtLRz19TFKM7eIFB/Tr+P57E1ziG90LTPB4M1bGj/u2kqGw3vjTrU/+RVjTb6+z1PP0f+OONRssPA7lf4lu81bVyyySAsx8oz8A9Ne2i4Q0tvdqU81zkYxR4G0Knq4PdjnA9NTPBt72+avqaCKCFPLGqHLSyHooz2HUnTDUE9FbKW5vDDFJPKRAncgdW5T9nP668a34jTsbTySOfkZntFFDqKxwBwPv9oXghNroVs9EOe6VygVLruYkPRB/E3f2+etM4CsNssVhnvt6YJa6Ac0xA3qJR8Ma+u+3uc+2gf0T8HS1Uyux5ZJV8SadztDEerZ9SM49t9MfSPxvNdrzDYuGMJZaA+FThY1Pjv0MmCDue3trBCdZYGxhRwBLORplIz6j2ZSOP+LLhxRxLNd61XALcsMXL5Yox8KD5fz305SVFBcqqOWt8Sls9Cp8OEbvI3X5F2I69vw1NqYqu510Vipp0kkjJetqsAKpHxLkbBVHU9zrm22qCvvrmOSZrVHIAszJy+J2BI6AnfGe2t7nt0uSTkE/v/wJRFruwBwZZ+BbFceLuIYax6ZeeVglJBjyRIvT5Ig/M/jq2/SdxNHaadOELHTVU1uo25qqqjXH1uoGcnJ6hSNu3Nv9ncxe6yHgjhtrPQvGL1XQKaySJtqSAjKxKR0YjcnsMnqRnEL7VrVVZpYY+aON8ScqjLvnZB+PX323C5IY3DLty7TQBXPlqPSJAvNfNWXFVOIhnljVzgL2LN+WAPQAdc5sfClsN6qKemo4ZXoYXHhLjDzyt1Y/xN2+6o+ehv8A4fWedKGMI1ZE3PWSljyIf+kMfdHU+u3bWpx3Gn+jrhaOoFJJHxNVxmO3U0kR/cI3WcnoxPbHsNsa6tdm40L2ez/tLF69vmew6jf0j10nDlgk4J4dqaY3mrT/AOl545AGiQLkQIBuAB19BrFqIyimWmqp0NtSbxHWLq7Y26bn0HYZOrD9WrKyukssExkr6kmS6VbvkRrnmZC36ufXbRC3WuPiKvpbVaYZDaqJ+WnKp+8qZm6v8zj8FGmF9S6SsFDjHGPn/PeC1Wm5sMO/2+//ABDH0c8OV/F3ENPVyxJAiriljP8Ah00K9XOew/VjrSeKDXSrT2Xh/wAGmstEP3ZkyXqJD8UrYPU9vbRCgpRw9Z3scQgNUxH16ohJw+OkS5HlVemMnJ76Y7E+mnvg3hjD/wDJv+s9RJ4prhjyKvpHcrRtd93L3GFfcIT/AFOmp7dXRo0k94KgAknw0wAN+40enm645vlrMvpG4lLlrZSvlAeWU5+Nh9kHuB30412pXSVbicsehmKNHSdTbsUDA7ME8RXuOuqRQqtTXqJMRc0oUNnYHlVfy0Oaw0dZcHpKaGGNaWIyXCd3JihI+yCOp6D3Ow05bKKrp5YqSjTxL3XDKH/81jP2z6MRnHoN9WKxWQ3eopuG7JGZqGOUeLImc1s/r/kXfGe2T1OvI6llWsvfyx/zA/3nq9MCCEp4H+cxv6LeGqniOsjM7LBSUSmRvFOEp4x1mft/c/LRj6Q7snEVdTcIWGNYrdR/vCZthEuDzTzfxsMk5+FdupOiHHV0p7NSU3CPDkUdbcJJAGmRATNLnHl7+Eh2A+0wzuBvXbLZZKyY8MWovVmWZf2pVRnmarmzkQo3dQdye5BPRRoZKV01Zst5Y/5iEM5tbbX0P5+ZH4K4VivPEoEb/wD0LG5anmnXkjIGA0sg+yvf32HU6MfSLxOt0qoeFOGZGhs1C7PJOW5PrEoHnmkO2AP0GAMHI0S4/u8FgoP/AAPw06y1khVLlVU++Wz5aeM/dBOPc5J96vwvYZrvXpZaCMTq0gWoeLcTuOkSn7i4JJ6EgsdgNC11gZsf/PsP95qzE4Vf8+854E4RF6v4qoklNujXmZ5N+VF+Kdl+7/D13A330V494kob8f2bQeLBwdaJceU4kuNQc7+5JHXsPYDRDjm6U1PTTcC8O1iRUcCiS/3RNlbl/wCUp+6OgHcn1J0z9HHCv/iGsiulbG1BYbcmaeMjeJCfjI7yuRt/YDRddYoG8jLt0Ji9nmekH0jsyZ9FvCkcc8/Fd8o4RAz8q0q+TftCh9APiPptnJOrncKyeurHqqhgztsAB5VUbKqjsANgNOXCqFSyLDCKekgXw6aAHaNP6k9Se51QvpE4o/ZsLW2ifNXIOVyvVc/ZHue/oPc69LpNPX4VQbbebG/zAnndVfZ4lcK6+EH+Zg36QeJpqmcWGzhpJZG5W5Ny7fd+Q7+p9hqu0dNTU1FIsnNUUiy8lQ0Z81xqO0EZH/LU4LEfP7uvLfRfVlqhU1BhdUBuVUo3pkPSCP1lbpjt0+9i6cL2ulpaL/xfxFStDQUvLTW23RfGzNukCesj/E7dhv3GPP63VPuOTl2/b7R3otKAoVfpH7/ee2q2fsW3pxFe6dKu+V7eHaqJfKCyDAx9yCIfEehxj1JY4ftNVxVdKqerr/FoVk+t3W6T+Val16uT2hTYKo67YG45eoaa8cacUzU5IernAirXhbENLCucUkR6LGoyXbpnOe/N5xrfKeaGLg/hZVktcbjnlTYV8q/bPcQoc8o7nJ6nZRjAIH6mMO+ZD4our8TXiCz8PQSQWyBv+Fjxux+E1MijYyN0UdhgDYb2majoOFrJJY4PNUkiO4zKcuHO/wBVjPeVtjIw+EEKNydKz0EXBNqYtMEvk8YmnqSvmoY3GFfH/WcZEafZXzHG2i/B1hQRpxBeaUJTR5jt1CxJ5tzktnrucu3UklepbRenqZmAA9R6H+5mN1oVSM8DsyVwjZhbYo79dIYmuEyKKGlVfJDGMcpx90YGB9ojPQLqq8ecSyVk8tqoagMCC1XUF9sDdhzfdHUnv+G876Q+KpzVNbKKQzXOoPLKy9UB+yPQ46+g9N8Ue3UP7RcU8X72h5gHdf8A624OQF/9NSP+4jPQDDO1q9PUawf/AOR+T8CLq1a5w5H5D4+8kcO2qS7VUBEEklIJB9Up8ENUydBIw6432HYH7zb2281M1BIOEuHwKy813krKhBzBR08NcfYBGDj4iAoyqnm7utX/AOFqcWu3qs3EtYPDYIf/ACiEfAMbq2D5j1UHA8zMV8gSHhKnktsHNW8U168szIMmInbw8j4dtmxuowi7liqRrGY7279h8RkqDofrPXhWx00fCnDqCuvVf/5qoHn5yTv81yDn77DHwKee12KyxWShFsoGFTX1bE1dSW3mb4mHP/0x1Z+5HcADT3B/D6cO2+WerRqy71reFI6EB3lIx4MYHTCjDkYCqAoxvkJx1xStija0251q73W4WR4uiDqFT0QdR645jty6lVTOxUfqf9h9zK2Px/n+YjPHXEkdsp3sFlmD1Um9XUg8oGAe/wBlVGcD7IyT5icUjhmz1HEFwjpaZGNOHD8zeTxSAf3jZ+FQMkA/CMk7nZmzWypvtyWhow1Qsrr4jruahs5GPVARkfePmOwXVtqFpXpKvh+2VsdLZaNea/3fOVcA/wCBGepXmwDjd2wBsBoqxhWPLT/6+0yRSx3GORx0N6gnt9LVpQ8G20rJdbljArnXPKiDumchE6sdz7HaCJbm9HfblbzT2qmPhcPWUrkuSceK6j4mY9fX4RsCdV6keCsgo7vcbe8FhppDFYLINnq5dgZXx36czdAMKu+neN+Kau1t9Xmq4UvtWDFLOv8AhW6PGDFGBuGxscbj4B5i2A2RiQFhaEKOZI4z4kaKSso4q1Wq2Ui6VynmWFCcGCPHUk4Bx8R8owoJ1X7FRQPTniG8B6a3UxApoAAzlm6ADo8z8vyAXJwqDQzhughrg9dWu1HYLa3NJLKvM0shyPh+3K3QKNh8I2DnVqE1bNc4GWGOmuMcJko6eVg0VkpiATUzHoZ3GCM+xxgIGuVCDYvXuZVVLncYStFDd7lxFHBAkcd/aLlQA5hsFKTkksf+e2QSTuCeY78oBXifiGy8H2CPh6w8jx8omkkccxqTn/HkHVkLbIn/ADG3PlHmDx18Fi4fknhDJRSDngiqCRJXMSQ1VUfaKZJwnVieXcl9UezW2rv1wmu17nrJre1UWZygM1VO2QIkUdWYDA7KAwBChjquzPJ6lw3sO4Y4foJbnVC/3sT1ETzYpKYMHmqZmOcD7ztjJY7AAHoAGs9MouFSTORLHNmnmamfAmVd2pIGPwwLnMsp+Ik5Pm86t9qrro8hFOUjiP1Sb6s2RGp/+pUzY3dv+bL1O49te3Wgqrg9Rw5Y5YhMFVLnXwg+DSRZ8lJFjrv2G7tudgTrhYKeZdQEWA+I+Jqzie7rw5YGCUpxDJNTjkUxruUjz8MS4zv8R8zfZ5bDSCnjt1Pa7ekQooY1ZByFklBYASuvVkLgcidZ3APwKAINosdBRwNR24RvDNGPrE8hJWoQNjnYjfwQ2wC7zPhVyoJLta1RW3CSx2R3+shjJca+UjNOeUhiSNvHK5G20SgquPMRzaq+oy2445kTii+XCfn4U4bdhM8jNcKky7xkg85eQbF8Z53GyDKrgcxJXh+2xWu1LR07FYKfzSzECMFl8/McjC42ZQwIQcsj5fwk0Qs1qooKdaWgSOloqeMGWblALADnDMTsT9sBtgAJH2EakhHFT1tNFWVEISzx+ajpXJzWEHm8aTm38LJLANu587Z2GrB+OZzGPzlYuFsreIFp/rKtQWCMrNHFuklWASwYg5KJuWHNk+bnPM7DNkWjqlnSjpFiWq8MMiOpEdJECRzyb5A6gLnmLEjJYuyTpJKlrh4aqst0kHihZMhaZM48aTuMHIC9S2w8/MY3Q1Jbrc48WUwc4aeXlzNVy4wNh1YgYVRsqjbA61YzuB1B1osFDbZZ655KmqqqhwklS4zNO32Y0A2GcbKNgB2AGDLW2gpk/aV38BXpB4nMzZiox0wp7v2LdWIwuANu4JY6OKW4V0sUEkURLNzZSjiJAKqR1YnHMw3Y7DAGQPpo3u+b3e4xRWKkxNS08+3NtgTzD1OwSP3HyNlGeZOMRykiS4kXy9IKKz0g8ampphgYxgTSgdSRsqe+B7m6aI100F2u8MkVOkoNBQMMuZDnDuO8pAOB0QZPqQxS0lRcZ4LvdY5YqeF+agt7AFjIc4lkHeTGcDogyeuTorUM9PPDTxRJW3qdSaeJslKdDsZHI3C9s9XOw9uk+wlwI5WV0lJNHTU0S1d5qVPgwjPJBHnd3I3CA4yernAG+OWJEop4qgLUyvE74uVywfGqZs8oghA75yvl+H4V8xJHNP8AVKSlquSrmkhaTFxuSLmeum+HwYAvvlfL8PwrvzMJqrNCBO6xUUtMoRFVeaO2xt5QiKBiSocELgA4zgbHElcYnQIvDdJfElaKjalQBUVQ0VsRhgAAZElQ4YAAZxzYGxxITtlvgpI4qisjZFSTNLSM3O4kbPnf78zZJzvgE79SVb6IU6w1NUjI0b/8LSA87I7ZJZifjnbJJJJ5QTvjmJ7TlkPMOV+ZcKFJdQpJGAepUkYJG8h2Hlzqnc7iSPrLySlwqsSDykEkAE4OCOo7cw3Y7LtrqGJiS8jYHc7ehHbbpkbbAZA25m11TQEnnkI336jLbEfLptttjYbZJlhGTBVMsenMcDb+QHr8vYC2PiQmcRRbgLGSTso6fP0xjA/IdMDlA369FlekopAUI5ZJV6MPur/D799cX68GRpKWklLRHaSUDHP/AAj0X+egOnWg0HVln6CKdZrP9CRaWlpadiKotLS0tSSLS0tLUki0tLS1JItLS0tSSLS0tLUki0tLS1JItLXpG2kvXXMyTzS11y768xtqZknmlr0ddekb51MyTnS13pa5mSckbZ0gM660tTMk85dIDGvdLUzJFpEZ0tLXJIgMaWlpakkWlpaWpJFpaWlqSRaWlpEgAsdgBkk9BqSYi1S+N+M0s7/U6BBVVOCJOQ/4XofQn20N4740lLfUrDMuVJEsxGVbtyjG/wCIOs9M84YtLQK5J6xTkZ/9wOfz1vWnzKlvid1dwiq6p566StDu2S0sOc/kx0341tl/+sU3p5wyY/8AcANe/XYB8cNXCfV4cgfiDn9NTrTDaq5udq6k8EHEszqfJj2I6/PYaIUTHPxI9LZaauIWOOmmJOOYTAqnucH9O+p//hyChdaW2z18s83lYLjDN6KMbfntqebVQVcy0VltsYjlGGl59pfUsc4/rr36na7NG1rtMlTcK+byOwkPIp+7GBjGPXtqFyOAJQqDnJkO42W48Pqn1q/vJUuufqpzJ4PpvnrpmOi4mpVFXW1FEwk3SKVVExx3I5fxOdh30Yp7PWWWMvdbo1ZcJV5ol8IM1OT0JYnJP8/T0N2ewXKKlN34umpYUbBiUgiV8dOZQCMd8Y/vod9WqLzmXXTM54gA3Lje5xxVF4oWq7ZAOVJoyIFA/hxtjfHTXty47vr0n7CpbK0NCg60SEsF9X2O/wCWi73DiLiuoMNRb2ht1MOX6zTeSnAHTHNj8PxxqJLxVSx044ds9tekmLlWmiAn8fqOYFe3vggdtxoVbazjIHHtNjW/sYKtfF9n4YEkjWueoqpP/rc+Mq3upxv7abp7rZ6+ra+Xy5SVSlh5BGc57ZHtq0Wym4a4WX6xxKfEucqs1NDJyiPH57Hr8WMb6HJaBxJdPrdf9UtNsJwJMgR49FPQk/P+mtxeCzMv9/8AiZtSyqAf7Tyuv9PfpP2ZaKmnp6HPK4JIkf8AzLjP/aP172KC78J8LWcrw6Ke63hl5ZJFUCRTgeuGA6e/8xW+KrDw1RSJb+GqCQz9GqF+D8MYDH9B3Po9H9EEH7P/AGtfK5rbheZUzvj7zZ+ff198aFs8lgN3A/mEIbFJA5MgWnh+4ca3Yz8QVbEb8wmlweXPwqM5Vd+g6n1J0Xv904b4Zp/2JwzbaSqq84epkiWXlb+Hmzk+/wCp2IqlRaq+6yra7VW19ZCGxES7Zf3AGMA9tskfjgxUcIcX8KUJrbneIDCMZSUhypPQDJPvjv19DizrUzAHhfj5lKvMVSez/EmcIfRfDVAcRcTTyUNGvnEa8qGTufkMDrsBv030xx9xZRV9N/4f4diqTS5Cl/rMrc4z0ClsYPrjc4x71O533jC8TvSUs0lbCcD6q4DIoBznByB22+X4v2ypuVpJqK2yCBx5S6qg8x6YxzfoPXXF0iu2+w4Ue3Uj6hkGE5J7MLcGcDXlmNXXXqWmpl3YZJCgDODzHB23Pb12Gu+M76g5KDhutmDx/HVxxRxl2HQKUCnHufbp1IW8fSBc7nTpQV9DIlKGHlpm5PLsRzbY+6fxz6HRjhGp4ao4f2nJJI7ouSKiJmCEbnBQMNs9wOvvrhXzDuLYUewkB2cAeowdbrJxUEjrLpSxNA+68yRFsdNycHof1Opl842u9ojNBaanEYyJomAKg5G2wGPQjJx0PXl0zxNx3TXlFhgrXo4CeXlaFt/xB9O+M7gDGd4XDdqt1RP41RWR1Cr5ljiVsYHfoPX/AOBsd1ra4Y3cCUZ0qbOOZCoKu5X2qaStsUs3OfNNmVS/UH4jg+nyGO2NXmcTcN8PpXy2owJnywyBOaUhSdsOWOMDJIwM7kalU9/tFupQ9tNPcKoeVIlkAVcDuM529Bv8uuqZd14h4iuxkq45Aznd2UBVHYL227Y2HbJ82s2N2/y6uvnE7/Txvs/tOL59ISXoxUVStVTQghlhp2GOnxHvk7jPXHTAwdWDgKOyxzJWSQrVkgBUklEWd9huNhnoB/M7uWLhu3W6MTOkIdfM0zgAjGSSCenrnPqSdRL/AMWhFeksMzRLjEtaCQ5B7Rk7qD05sczbhQBknlyNT6VAJMlbC07jkASz3n6WKBo5LdbkSkqwFiUSZZFJ7eTrsPh29yBkHOHhqr3WyVMV1graiVuZ5QWLHBwMALjbG3ZceUZ30U4Q4GqOJKk5jkjpeXkkkckeUnJB32B+6Nz9ok61hODeB+G7MxraWnl8NDI71LDJHdjnZVyMdOu25wCJ5i6ZssuTCtpuXCniZ5ZbHS2alWWeKWMt8U8sLqu+SRkjA6fM6V6vEyU/hWdUl51z43OrBf8Atz5m9vhHcnsJ4uuVtusrU1ktNFb6RCHknSHw3fqAdt0QgnA+N89hjEbhH6O7heX8OmJhgOzOylCV+yNj5FG5AGST1PbRb6t7E9S4EHTTqh9DZM5pLRX1dWVdXaV3DSzTNzAN2JJ+Nt+vwrnygnOdZ4E4Jtlvh+s1k1NNOcucyBgPUk9/959uY+BrVwxapK+6X94qZABI0kaSAn7qiRWyT2HX8NZjx1d6Wt8A8PGaSXLq0jUkMIAIwAPDVS7r8WRsu2566D/EecNtYP8AaECo1nLkZmh/SXxRZ7bH9RoI4J6wrzEqq/Dj4ieiL7ncjpsQ2sdrqhTOaiciSdt0CrykZ+6PsL7/ABNnt1Iv9rcRtyw00tXUy4wOV/ECgHr1wSe/YdtFbZPxDJOoqKGd5SQVZqRc575OD+ejdLpq6xlv3EF1Oosf6f2nFv4ahr2WWupowucpCF5R+Q6fL89XGz8CcNw0/wC0rxFDQUSdCzkNIRuVQE7nH5Dc4Gnr/KbBY2NTHRpeY4Vl8JbgnMmSCPEjaMEZHYMT0PTfVJreLqm9TiS7UUNVJGg8Ms7IEiB3OMgKPQYGd/XW76ql12VAD7zGvTXKd9hJ+0tM/GNcIfqVipltVtRuWnRBztnuwz8Unv0TBxynJNMlt0ctUVi8SaoeTmIV8qDtsSPiPQ4GFGiVoudvucrUyW+dCyheeByxZM7BVzkD2GtN4R4PpKdIapoqiLBBeKst1WvMPQskZAHyOhd+jpyTCF/EWcLKxwB9ENZxFVCsnqKhIw+ZJ3wVX2Hqeuw21s104b+j7gnh9ay72y3tHGOUNPTRtJO+MkDbr16bD5ahcRfSOvDlpKEWSNEQpEtM0wKkYyoRowOYBg2M5xk6wi43ij4guBrbjxFVVLygyoskLbjI6YJ5RkenYd99LFpPiDli21R7Aw3cNKnIy0tXG3E/D9wSSnsfD1sgiZGjeUQFI4+YEYAG7v79B9kdHOa3CiWOpklVuTxfihZi7su+FY9hv8/z0dpfqVSqrQXamaXonNG68o/gGDj59f6HeE+FWkqebw3uFV1VY4mbl98Yz+Om9Gh01Iznr3zFtmrvsbr9JT7PwndLhNFVXCUQwqcKi8wbk32Az037/wB9aJwdwNULUxNDcriiq2UAAyPYZY/y1abfaFpHR7lT1dPlgAZaaQD5Z5dTOJ+KIqKhEfDdtkncqUUrkEjccztkED0VcMe5QbETUuB6aSSTC6amIzdxDV1rouGLAJqnjC+QmI8gX6xGy8w6qq8o5mHcAgL9oqOuK/SDxFdOJp6hzerutM0v1inpmVedmwinJXGMjmA25RjAAJ1xcKe+3Gt+sXCGaWoIChmTEcS74VV6ADsAABvtucy+HrHVVdYsNOkkTu2DMwxI5/gB+EfxHf0wN9cr8NSpfMtb1faVbXPa2ytcL95VaCk4gaYcgqWqiAppxL5Ih2aQjoe/L1I9BrQuFOAuOWo/rc00ILNzRpVRZLD3HMCAfz1p/BfBlBZ6eNnSKaddwq+ZEPf/ADN7n/XVugaOSSREcc6DLHqF+Z0u1Wpcn0GHUUKB6hM4pOG+IYWU1Fu4XBY4USUUjE/lKdRuM6xeFEjW7UvA4qJl8lOIZEcDfzkl/KPTPU7DJ20c4r45tvD8TMlR49U6ZWRcc8i5IzGDsqZ/5hGD0UOdhgF6rHul2nr6oMZp3LBeZmI7dWJPzJOT7Dy610Wmv1R5PHzMtVqa9Mv3gWu4n4hjr5lhqY4csTGkUYZIx6knp646+uNdpxheeRZ2rUEMZ5ZS8QwT/CeTf5akTSRxHcLJJjZRgBf9+v5emivD/CdXeJ43qon5WOEhVfM3sB2/npwNL5IwGi1dUbeSsB0PF17q6wjwqWSLqC0OO/Q4X5nWj8JtUV7GdeFYZ1z5StekJYf+w60DhT6OqK3wRTXOkgwpBFOFGB/m9flrTbFaKHLs1LTqiDOfDUAD+mkWt8Qas4rbP9/+Y2o0e/kjEy63WsysofgG4AkgZjvCHH/2I0bu1vt9mttXWyWi/wBHLS0bVIdbnGApH2S2fJnfBI37b6NfSDx3Z+EqD93IEldMxJFjxZRnqgOyp/6jbegY6+duMONb/wATVCtXVTwUySFoaWFiFUnIz6uxBPmbfrgAappk1Wt64H5mXvuo0g9XJ+IN4n47hrGSCKzzVK5zJ9cqGkMr7+cLtyjHTO++hMPENJG6JFw7SeGRjyAjl+YGuJ0jWndZH5Yy3My85wDjH54229dQbfaHuLmloKcxwuf3jDv8z/TTunSXUjbmKLNXXcckYEIy8W2unkZDY4cg4JjdiP5aWjlBwVa4acRzR+Kw75xpa55Wo/8Al+8sG03x+0qIGdepv5W10Bge+vCM4A20766iAMRxOuTqdcmPqdex7nlzrv8Avrs1UZGRI/ICM+umJI13HfU7y9PXTUqbdNzqwl84gqaLB/h1ArqSKpiMci7dj6aOSRDHTOoksYXJXpqPWlilWE3pvKHI7lZpaie1zrT1LEwjaOU/ZHYH2/l8ttTHtUNTVLOs6QR9ZQTsi4J5lx126D8vaZWUsc8RjkGUP6aEQSz2io8OV2elJ/duMkx53/L2/EYOvH63w5tDYLUGVnqNLrF1SbHOGhC3xQXeoe41avTWK2rhF7kZ2A9XY/720c4at1XxLeluFRTZ5yIqSmUeVVHwoPYDcn++oCKtzShonqY4KOJzKVRfK5P28jqew/puNaZeLhT/AEdcJx1IRV4guEPLQQHc00X/AFD/ABH9SdAX3NqmFa9dk/P+e03SoUZdx1wB/nuYB+k28w8MWxuCrFUstVKv/wBLyxuOTP8A0l9Md8YHbVCjWS208cdMrPdq1cQgDzQxttzezN29BrylCwRS3y5AzsZD4aOcmol64+Q6k6JW5am1QftactJf7mC1NzDeBDsZcdj2Ufj2GmiImmryeD/A/wCTAgxubJ5/3P8AwPeOx280kQ4VtxVqmQg3OoU7ZG/gg/dXqx9RjtrW+GqKi4H4Wi4gqIkaslBFpp3GC7Y81Q468o2wPkBudCvos4UoqC2VF9vvMlso8NVN1eeTI5YF+8ScZ9Tgaqn0j8W3K7XWe5VDQqZCI6WmUEiNAByxgg9AMkkdebmHVdJnt8xvNbodCHkFB5a/UezA3FF4laaSNJcTzEySSZA5ATkucbAk9MemRsqag2mmkpYoJIIyK6oTFHHjenjO3ikffb7P5+mo9rgEnPca4fWIhJgJnH1ufGeQfwLsT2AGPTWmfRrwua6oqbxe6kQU0SGpuNWw5RFHjoPQkbKB0XHrroLVjd/rbr7fed2Kf6Y6HZk3g6z2nhTheTiu+oGoqVuWnhzvW1A6IPVQep9QT0A1nfEF6ulzvT3ytJqL/dG/4SEDanQ7BgO3oo/HRX6ROLV4muf7TkpmgsFu/wCGtNBjHiEdMj1OxY9hgaGUcdZbFFbJzS8TXUDwVC70sR2D+xI2Udhv6abaaldHUWY89n/Pn4gN1hvbA69h/n7xRUBpx/4Yt0gad8NdqvqAQcmMH0B6+p27a27hCxQ8IWWKbweS6VEX7iM9aWJvtN/6jfoNCvom4RpLJZkvtxiWZecmlRxn61MPtn/01PT1OrFUyS1U0k9Q7SSyNzMx7nRHhmkOtt/EWjCjoQbXar8NX5SH1HsyIB+uo9VJtyqQADvp2pcxggD8fTVV4yv8dmoWIZTUPkRL/Nj7DXrbbU09Rsc8CeXCNa/lqMkwT9IXEgt9O1DTuRUuPOQN4wf6nt7az2jjFPGlzqohPPK/JQ0x38V+mSPujv6nb10k/wCOmnulzkk+qRNzSN9qVz0Rf4m/Qb6OW2Oqp5I7lNGv7brUAoIMeWigwQHwehx8P4t3GfJX6k2MdTdx8D4H/M9NptKtKCpOfn7mO0tvqadprRDI012rPNd6oeYxhv8AkqR3O2cd8L65vl8rKL6NuFmoIk/+nKmMRTqh81OjDIgUj7bDBdh8K4Hca7sVNQ/R9wuvEFeUNymjM1EsgzyDJBqXB675Eanqd/XFDinq6quj4krommuVYzCz0cvnKgseaokz182Tk/E2eynS+obj+Ju4HsP94cwx/SXv3/4ntHR1tPUNEHB4ir0DVUqjAt1ORgIPuuVIGPsqQOrbXe81lN9GfDC2ygCpxHWQ4670ELDctjpIwwT3A5R769tCUX0fcMrxJdGFZeK0mS3xSHLzyknNQwPVQc8uepy3TpncUtfXXM3aqc1d1rn8SDn82+TmZs/ZBzy56tljsDocub3NjcAf5n85uoFQ2+/+cTq1W2oE4oYQ/wC0Z1/4iTB5qZGx5dv+a+RkD4QQo3O18v8AVHgm2RcIcPKn/im4Q8tVICMW6A7lSegYgZY9sAdF11TvT/Rzw3BcmjNXxLct7ZTN5n5m61Dg79zy59c9TtUbPaLhd7rLZKd5ay41koN4rEPMzuTn6uh/A8x6bHspzumNvnWDAHQ/z3MzdiTsXs9/58STwNwyeJK+G027eyU0hkmnkyBWSr8czn/prnb5+rba3cTTQ0kVstoK0FOcrkYM8mADK3uegHYYGuoKOjsFoWx24oQAoq5oukjDoin7inPzOSdVrjHiClsVtaeTBmYYiT7x9T7DT3w/TCgHW6nv2HwIk1+oNrfhaevc/Jg3jfiSGxUBSOQGskB5B15B05j/AEH9tZvbKeqerFXI6pcpozMjzHyUUG5M7+/3e+d/u58gNVda9brWRNV1FTKVoaZ/+e46u3pGu2e3b1xZOFbE1+rJKZahXt8bGouVwlPKlU6DLOx7QxjGPXb1GF3iHiDMfMf6j0Pj/uHaLRBF8tf1Pz/1JHB1loq2A3a4SNb+GLSDP4koy0hJwZ2H2pHOyLv+hy/cK+58U8RU9PQ00lPMF8GhpFyxtlO56nHWplJBJ6jI9secR3z9rTUlvs8J/Z8L89rp5Ex4z9DXTr6YGI0OwA+eZ15roPo7sslqoZ2fiWsXmrajrJSK/UZ/67gn3RT6knSI7s8/Ue/tGw+B0IxxhdaPhm0twRw4RJO4EVzqITnnb/8ANoyO2R527nboADM4VtMHCdsS93FaeW71UfPSRSrmKKNTjxnH/SU7KPtvsM4JI/gfh+ntVAvFHEECyO5MdDRs3L4rgZKk/ZRR5pH7DbqQAQssEnF1zqr3eqzw7JC6y1FU0fKKlx5UCoeiDHLHH7En7WiaagQGxx7D5MztfGcHn+BCnCNpe9Ttfrw0/wCzIZjKnit+9rJ2wS5Pd265+wuP4defSVxobai01KR+0ZlEcEMS7QL0UKOx9B+J93uLuM6Olt3Lb4vD5E5KSGUFERSTliWxzEnJJGcnWOTS3OlutTUVcgeqbCGRWLywl98KegkYZG+4G+3ZvgaNOfqPZ+PsIrRTqn4+kdD5+8IQRvzNTSO0tROxjq3Q5Lk9YEPoOrt+HrnQ1mi4JtUVTJGsl/qkH1OmTrTqRlWA7MRgr6Dzn7AIayUMfCPD3/ie50sUtykjC2u3ndVySFJHdcg/52B7Kx0SsVLPbrdLxxxPUCpu1QCaKKRRJyOxbBK7czFgcKccxVicIjZT6i8OcnodD/eMqqtvHv7xp5Z+D6cVcw+s8X3QAwr1FEh3Db9GwcgdRnnbcrkjZqWThNY1CfXuMLljlXBLUaHuR1DnOw6jPqSVb4ZoJuH6F+L+I1at4kuLH6jTuSSW6mU5+yMg59Tk9VBJ2unj4DtM9wujGq4kryZGkkJZ0z1Ldw2+/pnHUtiVIWOZLWVRj2kriXiT9iWz6ok31y+SRCmBQDkp1/6UefKd/ix8TbdAc5DRftW7XWWkNOai41kjLJIH5+dM4K5HReb4sE8xwo75sNQtbdrtJEXZquUnx5T/AMlcYZQezY2Yj4R5BvnFjt9mmtlZFwtw5H4/FNUAaipAx+zo8Y6/Zk5SdvsKTncnGruKhsr4I7/z5g9YLnLRmkpJ6eqm4MsFTHHW+Ez367u4C00QH7yJG6AgfGw6DCjvn2gp7fcacTSxzUnBVmlApacKRLdqjB5Xwe5GcA7RrknckktaLBQ3GmksFrmMXCltkVrpcUGWuc4OyJ95M55R9o5Y7DV5tlqheWK8V0cVHRUEOaGA48OkiO/iHOzO2MgnrjmPlC6XveF4jAJgZgGw2mrpIKjiXiWWOmrxFyDl8sVugxlY4gejld991GWPmIxV5OH6e4073m4pHarEoM8SMCrzJ8PivjcLk8qj4mLYXzMSLjUSxcQAXy7AQcL0ZeSjppnKisZDlppCdxEpwSerNgDJICgLlX1l/udNW1FI9UZ5OazWuReU1LrlfrU6j4YkGQqdAMqN/EbVa2dsjPff/EgTPJkCioqmrqLbDT0Oarl5rFa5EAFOnQ1tSo2yQNlOxwQPKGLWK+UVj4UtJFTUG4VjO01VLI5zW1AbJZz18NDnJ9TgDm3SdPUUXBNmqqqqqzW3euYmtrC4V55AM+Gh+yigDmYbKAMb8gXOqRZ+JbhNerzMIbXByk+QgEA4RVT0+yqDcn3yV0GT11KufYdx+2QTXysl4gvXMtuidWVXiBMz9FAToSccqRjYAEdA51cLJaKm63BwxNBBSDwqmWHzfUVY/wDlocfHUyEAOw6Y5RjHkbstDU3W4eHExt0dCAJJRuLarYHKvL8dXIABt8Awo3HlY4j4whSspuC+EFjpOQ+AkiHxBTc2zEcueeZuhb35V2zzR2ODjv8AiaIvl9yxXOrkqKleEuFBFRmniEdVUR+eO2QN5SikfHM+wJG5J5RtnQ/lo0oEstkhVbYiu7GRv/MjPLJLKw38LOzMN5DiKPy8xMOM01JbRY7So+pIzPUSPJg1TDaR3cbiMZ5Xcdc+FHklyYdyuVeax+H7EXW4uyGqqTEAabAwhKjYTY8scQ2iH8eSvK68Dc04Tzz3ObjX1M10ewWSZ/2hzc9ZVtgfVduXmONhNy+VVG0K+UeYsQaslBRU1AtvoMQUEKiSWZwD4m3N4jc2xyBzKrbYHiNhFUPC4X4epKSmemom5aZuWSoqJG5wRjm5iSeVlIUsF6Pgs2Il87jrHxORFGZIeGYHZizMea4SZLsSzYPJlSxY45ivMcBByd2+rJlwD7yZb6+mvTO5ppf2BTEmCNwcXCQEsWctuYwRznm+M+Z9lwsviG61VHVRAQmrvdYf+GpiDmPfaRx1VQQcDY5H3gTD3dLgtmFPHDTePdpxyUFCoI5QD8bDYqoIGBsSw7MB4PNktqW1Z7hXzGqrajH1moVed5SQAsMSgb5GAANiMY8uA/QAOTIM8x3h+hlt9ukavrZKh55w9Q6IC9RMRyrHGAN9sBR0A6YU+Y1Twx0kclxuM0MDwxHmYvmKiiOxAPdjjDMN2Ow2301FJHFCbnWukTpCSMn93RxEHIB7s3durHIG2SYsVK14Vb3enNDw9R4ngpp1wZm7TzDv2Cp7j2B4Bn8p3idU6RXWI3q9YoeH6MCenp5xgOR0nmHcnYIny29STSpP4V6vUMsdLHIDbbaVzK8h+GR1+1Kfsr0QbnuR7JySRR3m/RSpSxyD9nW9lzI8p+F2X7Up3wvRBk+pEmEzxXGJ5YYai/1KH6rTA5hoIScF2I9+p6uw5V2BxrJgSUKiuE0MaUiSXmpj5o4GfKUqHqzkfZB223cjA6bQaeOCOlqitdUPRPNyXC4r/j3KbPKIIeXtkcuV6fCu/My+80LUM6pUztbnm5K6vXP1i5z/AA+BDjt1UlemOVcYZlKUkIhk+uVpjgmpUEKRQgNFbUYALDGo2edgQuw2yANiA9DgdS2JzSxLSuJp4o6SSlRY4ooUDR21GHKsUagYeoYEDYHGQAMECQrSUphWOpqomilViKSlBEjRM2cnJyHmYZyxOFBbfHMWYhgqI5oJnpzEUJWnhBDGEkHIXOzzsOYs52QE77ktJCiViXKyPIgXABKhGPwjuVJHzkIycIDqh5nZzGDUuXcCTmBUcuWXkJ+EdypI3PWQjso0QpYGJLynykkjfJY4x/LHTbGw8uebqmhLDLDY7kfFnPr67YHywB5cBpmRGudhtzeY9B6k9h7/AM+/fyk67iQLCudgxBOWP6k9gPX5e2qxxBePrBalpXLQn/El6GX2Hovt+J1xfruarmpqZm8DPnc/FKR/JR2Gg2nWg0GP6lncUazWbhsScaWveU6XKdOhFc80tegb766wPTUzJONe8p11gaWuZknPKdLlOutLUzJOeU69xtjXulqZknGvQCddY0tTMk55Tr3lOvdeHOdTMk91xrvSwPTUzJENLS0tcki0tLS1JItLS0tSSLS0tegZ1JMTzS17ynS5TqS2J5pa6A330iN9ScInOlroDbXnKdSdAnmuuXSUeuutSTEb16vXXpGkoIOpJieHqdea97nUC+XSmtFvlrKl1AUeVScFz2A10DMhx3H66spaGnaorJ0ghTHNI5wBnpvrMuPuJ6m5g0lKs1LSBgVkwVeQjuD6fLQriviluIZ+Q1MdPTA+Smm/dH8S2FJ/HQIULUx54GqKPn6NE7IG/LZtbpXt5mBfM9ArlyRPFN/+FhXJ/wC4Yb9dcmpqguJKBWC9Wgmx+jZ/npAXFST4tPUJnpNHhj+KYJ/HOidO/wCzwk17slTGg8yxK6up9CR/Q6IAxMic/TGbTV2w8s9caukpurCSnKu/yI+z7jR6mFHf50jp3t0NEvk8QFOVQOxPdvY6j0U9Df5o6y4XSOktTHlVuVlLkfYXI6+/5aKUnD0fEcz0FFQQ2uz0y80jsgUIvXm92OPkPXvrO2wASVqcwbV26hmmksfDtuK85/eztzczn75J3HsO/wDPpKGqszrQUF2r6y4PssniZZG22XY7e3QfPUm7GiRV4e4N+uB4TvWyTsWB7k9gpz077fiqSuuPCURlgqqWtvTHlGKRcsO6+oPy986GyQn0kf7zT/URnMLR0ldw1RPdeJLlQPezmSBTHz8rH7+x3J7gZz8toFHXXniXxr1f7dNBTQeYCSZY4pR6LzH9N+u/XTH75AnEfFtvqTNz5+pNOmW6eZehO2/y1JW6pxjUrJ9bFFZ6dt1EZHhDf/3HruP00NwPVu5/YflNl3Z64/mMzcRycWVQtdv56KiiXBouTlC9cl26E+xIz39NWeivfDvDVukpbE4rrz8ExfAdDjoPbttnp7DXNw4hobZbIbTwWglSTl5quMZLE+/r+g+eNOR8JWazUJ4m428OtrSC0UMrlgCR338zf76DYax2xyOPj3MIrUZyDz/ED2+1Ut6SS+cb3aIUCSYFM045nYdsA+Qfl/XQLie8w36b9hcNWalgt7HkHhwDxH9w2OYD9T7AnUW6/tfja+q9rje3CMeHGYGfyrk4B3wTv0G2/fc6tLwxcDWdnrr1JU3pkzDyp51ONixDDbod89fx1qVSvDWJz7CZAs4wjcfM64c4KtnBVtN24kuc5kdcJRgKQCe3KRgnptjbYnGdAvB4n4uvz01gDCkZh/w04UwxqO5AUDOS3YdfXOmbTLxRxXeInu9qnrIT5Vq0PLyqDueUnAG+527576uFz45j4Np34eobZHCVX95UxorcrdMOA532O2eu2OoI7tsOSfUfb2E1QbhjHp/mSrksnAFrMsNyo/2zIDyxQxj962fQoxxnOSCOmO21IkfiXju5K9ba6+QKM89Kf3S9NwGxnO24O56E9dFeHKKkvVw/at5r5Kjxd2JAEjDA25Cc46DAGNt84AFw4g4zobdajQ8JxCocZR+VfgIJBLjrnbp+f3TkDajZB3NLHa67ehKjL+zuCIII62imVpjgKIn8TO4ycrg77bEjJ0BqJ6jjC5KTdKeohjyI6eEsSg74Qgkn1O/QddsWDhHg+5cXXB6+6tI0TH968i5J7Y5T2xtj0xn7ou/E1fwbwRw+bfS0VI8zDyQqgZnPYt+W3rjYdxpbq7FYbxuaZpShBC8CCbNScEWC2GKZVqq47uk9O6yZ9ArAHvn3zkkddZrxvX1N6u/h2+xS2+n6JEqMAxyfMxPX8MYxtj4iFrqGq4qvEk8EUcAO3PFGFRB7Abdhv7D4iMi1cOcFtbaM1D3mohhiILyuoIAzt5Tn323zjYHRVaFB5t+cTJmDf06pDsn0f0VWFa4U5nqW6FNuXvtj5dsY/MkXxHarJRSGgtE8tSRjxpTMxjTfAC5JB325sYJ2Xm1N4jutwqbn4Viqaj6owaOSN4Y8zdOY8owvUbjGFyMtnA1ZeDuCuJa6JK+sslLChcvHhhGxJAHMBjB9ObbbpsdSzXIR/wDFfyna9Mw//Yyn8PfRfduIlkaiD08KjzOwC59t+mdjjOdhk7AAjdeEeIOEqUzVlzMcSsqj95zEk9FADHLHrjGe+MauvE/H904Lp4qJqWldOTIjjSMNEuQOfKSHAOdmYDODjO2s2unEEPEt2eWurqkVAUhY5YQY4QTuuzbdckHds+YnpqunuZj/AE8AfvO21DHrzmBqytvclV9ZSvnUydEjIXI6ZGBy9R16Anqx2D1HLxVzB62iecZLKDGjlcjHc5zjGtF4Es9gpWe4XRp64IA5anCyg4GMvyMSAB7DuNhtq1cWce0At7U1hghrJ8mII2FCYHVh8QH8KjmP8PffzzW2EBYzMV+YPVhZnFNx9f7NQrTxx1EMg2iiyAM538hQ/oe2q1e+O6i6Ist8haUlywxPjmkz8WDkMVB2JyF6DRqG1XG517TVEJepqPiLRhUC9gQNgNto122HMdaHw59F1I9Oai8xvNNIARk4bPr+W2P5d+MwDb34/SRBxtTn9ZlVju1leojlaGZlQ5CM/OEJ3J8oO57k5OtPpvpZ4esFHDAaCMK8ZIMcjdQPtBkB0G454f4Es0QijjaprHB8ONERi5Gemw2B6sfKMHqQQMympKRI+aoUHnwyLGcAgdOX+H+I7fdB66u2zUrhBmUTdQ2WMs3F3FcnFdw+tXC+UzQRY8GDDxonNv6bZG/qcDfbOhBo5Kt/ChraEU7DlZ1qFyVH2cdl/hG3c50PpeEZrrHzySzQRLnlTm65OSfN/wDPy1Ik4YuFFGWjr/DjB+1CuOnblI9P66Po05rXlcCC26hHbAbJ/WW2xWqmgdIIHiy5ALtINz7nONXGruVo4WsjtRmStu88ZELw9I+o5+b7AHqcE/Zxs2sNmo7hUY8KSMiNuVHHNl3+6OpPyHpk9jrj6xeaEmGmnqJpxlVEdRnr1J9SPQHA76H1bteQnIX7e8vpaxRluCfvLDIf+INXUSNJNKS3OB5nO5PID06nzn1OOudGeFuFaziGsjgjpWcOfJAi9fUnP6sf9dVGjvPEsGBWLWuN+fMIfvsc750fsn0j360NJJRXGWi8o8RhGU2HTI5cH5as9ZCHaMH7zisWfk5/KfSnAX0b2XhyNa6sp6SStReYPyAJDgdQT1P8R/TUX6S/pCoeH4/qdE5kq5FykEDFZX9yesae/wAR7YHm1g4+m7iuoVIbhOtQkTEszcq8q9pDt19M9yCN8HQKbie0u5eto60SzuWkKz+I75OxYkZIOfXfJzrzNfhpuuNmobj7R0+r8qvbUvP3hniHiC5XmVqq61MMiLkIjQo0EQLAlY1YHJyAc/MknLZrNvsFReWeCjepgp2fMkrOST2x/oPx6aKQNw7XVqyVNwqYFQgGKpCxge3sP9+udC4fFvnaKmt1VbqgEqkcNPWwlmPYBebJPtr0K1aapeBgRUrX2N9WYB4f+ju1CEQPTGpJfnMrkq2fTbb9NX6z8CcLWWIXG5xyU6BC6x/Wih5Qd3yOUIo2BYnAzjqQDKpOLLPw5HIqhI7k/Og+sGPycpIblHNu3N5eoAOcnbBzTiOs4i4jmeWrkWSAuHEMVQpDMMgM7Z3IBIzjbcKFBIKopZqWK1navzmMc10Lufk/EncfcV01Uxo+G6m6pBTyZSrNymCqcMpWMOSdwccx8xzsF6HLqmhkpZJFjZ1p2POMuvik9hgDAG35fjqzVlDdICFS3TySdFKxZRB02/uf/ixcIcFtUVUVTcv+IqXI5KdTzb52z6n20wTQ00LnP6wE6y61uRx8Sl8OW7iyuqFq4RUQU++BzZU+4Gtd4F4c4qqaFGqqC3yRZPLNU0UrmQZ6+WQfy1oth4Jgt8Uc1zUNO2PDplGQvu2P5dNBfph+kb/wvTLbLRURftWRcMkfmkhHyxhTjp3xuBjfSW2xr7fLoP6mM60Fab7OPyjF6slRb6IS1Vv4ZjLnkj5UqYZZHxsqDmOW2PY9CTsDrD77xrd6Gtr6OCSnWJn5Y/CqBNG3XmXYYfsvNnGx6k40xd7jd+IZI6riC5VNasa8kSzSFwoJ6DOc5/LbvjZibwYYw0mFXPlTqzH3/tplT4XYq5d4Db4mhbaq5nDcY3apmL1UFuqqoHnqC8YLYxjmySN8YG526e2uIuL4pqswpZbbMjZ88a8obHvzak2mx1F7cAQrDRZyzcow2P5/y+fbVOAeAQ8qi103gBRh6rJUgfMd/Ya2uL0LncABKV7bz1kymcIfsS43Bf8A6Lq4CH88kFFJUcp9cAnOtbsTWu0uZaO+TRSvtmp4fqeYD5ldhq30FpobHTtFGAWVeaasqTnHyzqlccfTZR8Oh6Cx08VzqcFRNKeZQxG2AOp9vzxpN+J1OqO1Bx+f/UaLTTp/U55kXjL6SorLJHML9ZrtGvMCkSOjRkDoyEjc9BnufbQG5fTeomlojPCjgeHFJCiyQc46yZ5ismO2cqDvgnWf8R8T37iigeG9PSiF5fGcRQKhkI+EMR1A7KML65Oq2bYBEeabzAbO6DyrnP6Y2z07Y0Qnhlh5ZBiYWeI1AlUbmWevudlutwqKmqv9dNWOwaV54Gdid9ye5/l2xqNFFYpDiDiGJnIweaFweuqzTW+prJY6a3BpZvtztGObB9D2H8/fVu4c+j+iiDvcXlllcDHhcu35jTAXXUrhV4/SAmmq0licmN03DkFTOktRdoZovshFZfyz01cKGnpKWnWKn8JEGPhI15aPo4t/JmOtuUKk5AJ6fLDDV04N+jCqr0eCG63OMgZ5xM/LjPqT19tCv4oEX1ZH6TavQlmwBAlIaBYsMC59dLWirwtw7w+gpLrcL1WVJJLOKpUUew5iP66WgT4sM8QwaAjifKAYld8Z10pBTsDrkD06a9XH9teznkCIsDsN9eoR0PY6WCclRuO2lgEc2uYnEYqZ3gEdO2uSMgDuNdKQRsdesp5Cw6jUzCAAYxIoGSOnfTMsYIOBtqYi7EkbHqNctGBnHT31YGQKYHmhKk4XI1EqKdJI2Vlyp66NTIeuNQpYepX8tW2LYuD1Na7WQyqkT2eX7ctExz5eqE9SP6jvozKVvVRT1FTWyvyIqB+YyZjXYBR2x0A7dPm7NCHQqygqfiXQKaGW0zGWLMtIzZdAd1PqPQ/z768pr/C30b+fSMj4np9Hrl1KeVaefmG7esVZK/ENzpmS2UJ8CiojsZX6rH+OMsf9NXf6MeGLlxNxC1xrHH1ic+NJM2yU8Y6v6AAbKPbVMtVXS3KWiasneSnh5vDBby4O7bfZOcZ7/PrrVeNOILZw9w+vCdlqlq5KlElulZTqXWYkZWFSNigGMjvkL3OE9151Jwfp7P3MMFX4cZ7PQg76UOLKKoijtlpPgWC2KVp1x/inGDM3qWzt3ww7vtlcKSXSvknncwRpHzyyHf6vDn26uxPbqTt213WVc14r44aQGQO+IUJ/xX3y5z2GTufUnbOxrh61i4Tx0FGXmo45Q0kirlqqfccw9RnIUfNtRduPNf6R0PkyKpHA+o/tDHAnDtXxFeqWOnpDGgHhUdO26wxjqzf/AGzHudtE/pP4io6lDwVYavw+H7Y3i3OvB/8ANzA+ZvcA7KO5+Q0Z42uh4Lsw4MsbIeJ7nGFuMsbf+ThI2hU9iQck+mT3GsspaWmuDPSpMUsVu/eVlSv/ANZk3A5fXfyqPmdH6HTnJvt7PUH1FoA8tOh2f8/aPWwU7oOJLjTgUdN+5tVA3/MYdz6gfEx7nbWhfRXwhJcqyqv/ABE7rED4ldKRg4PSFf4mHYdBtoTwHw9W8X8QwVJiWnpo1xSRt/h0sKH4z7Df/M2datcamljp4bVagUt1Jnw8/FM5+KVvUn+WtaKG8Tv2j6B2fmDXagaGrefqPQ+I5c7n9cn8TwvDjRQkMKjCxIOijUI1HooHzOmGY8vXUK41cNNTPLLIqRoMlmOABr2qVJUmBwBPKPdZY2TyTGeJb1T223yVNTgKo2AO7HsBrFK6sqeI7xK8sqpEBzSSN8EUa/0H6n56f4uvlXxFelpaQOyc3JDGPfv8z+g15SUdLPFLRGfktFEQ9yqkGfrEgO0SeozkAdzlunTzOr1P4uzcf/bXr7meg0el/DLlvrP7SVbo6eWCO71VOxtVM5jtdG3xVc3eR/boSewwo1ovA1khoqWp4t4nAnVpCBGxCmrmAz4Q9EUDLnoAMdjoVwNZReaqTiG9stutVBCG2HlpIB8KqO8jdu5JLemofHF9fiy7SW2Blt1itkXJUlN0pYAdoVx8TsccxHxOcdF0oz+Ls3N9A/c/8RnjyE4+o/sJBv8AdpOLLpU8S3t3mtEE+Io18hrpwPKiD7KAdPurv1be28JWunoKCs434vx4KnlEIHKJWA8tNGOyAY5sdB5evNofwTZY71VG+3TltVhtcPNEG3FLBn4v4pXPT1Y56BdV/wCkDixeKb0kMPNb+H7coSmgUE8kedjju7Hpnq252A0Pff8AiHA/0j9/+pvVX5a59/8AP3kfiC91nFF8n4gvAMis/hQU67BvSFfRQMFiOgwOp3uXDFvoeGrHUcb8VgTczcsEBGDVzDZYlH/TXABx6BexzA4EsdNNDPxPfv8AgLNb4ebAO8Ue5WNSesj9c+5b7uq5xFxRdeI+JqatnoomVE5bJblUiGnjyQrEH4sY69CQemDroKuct9A/czpR8cfV/H/cm1NXervxDLcKyUycS3Nck/ZttO3TAHRyDsOoB9SNa1w7ZabgqyrboFC3OWPE7HHNTqeqZ/6jbcx7DC9tDeAeHRwvZxd6uTx77XAywySAMyk9ahgfTJ5Af83oBHrKCCGCWquNzuEiKC8jvUFQfchcb/zzp74foze34m4YQdD/AHibXaryR5FZ9R7/AOJMvd0prXb5KqpcKibBR1Zj0A99YZf7xU3a/GrukFVNSBt1jTGQM4QE9B7/ADPXRW63MXG6T/UCLdbqcZnmA5mVc4xnqWb0B67djp2Ojqa+rhpEp3+uzRhIYWy/1KBvtN6zPn8MjHVcYeKa03KHzgDofP3mnh2kFJIYZJ7+094eoKviS5C20cZlqqnljqpIhhYYx8NNF6DG7N8/4sm+ML5S01PTcJcPQLWWwPy1DxZC3GeM7RqevgIT2+Jsk9QdSLk8HCdrqOFqBx4iqIrnWQn94vNv9TjI2Mrbc7DoNux09arXRWCzLxTxHTRSVUq+Farep5R5M4A7rEmSWbO5OPvaQFnZt7fUf2joBR6R1JMcsfAVl/bFa8NTxXc4/FpVdRy0yDYTsOyrjEa9yAegUaCfR5Yv2lLJxPxG8pp4JASo809TO5JVQD8UjnOPQZY7DJ54etlXxjeaviC/Vp+oxH6xWVkoJD4OAcen2UQdTgAelorY6ziG9Q2O1UrU/IphWLIzRxN8fM3TxnG8jfZAC9Ac3rrByT1/JnGfaMDuC5rZW8f8YRjm/wDo2kTwp0hP/DwRq2fDjP2kUkczdXYnHUavnFN6tnDtkipaWILTQ+Wlh6NNJjBc4/Dp0GFGnKuWz8IcM/UqblWliA8R1HK1TIBsB/CN8D0yTuTrJ7tcam63H6/VRiWWYlaSmPwcoPUj/pr3+8dhvzYc01/hhuP1n/8ApH/MUWWHUHaD6R+5katmrK24NXVD+LcZx4kfOPLBH0ErDp7IvfGegHNYOHbFb7XbX4j4hUNRR8wpqeXJNRJ9tm7nJI5m67qo3IxK4WslKlJNeLxO31GJ+eeZjh6qTGeUHoNh8lUZ6Y5jXC9pm45vIv8AeUWjsNGMU0DHw4+VATk5+FVDZyfhDZOWccyq3Ubs/wDxH7w6mnHXf8SHY6A1zycccXkilhBNFTzAkYGF5mAO4+FcDr5UXuQestua4ynjPiinkamDFbXbnI5pmxuzdskKOY9AECjCJjVgprRBxhcf2rUrLFwlaSDCpTlNXIuQG5eoGDyov2QT9p2Ovb1c6dIW4hu6ItNGvJQUq4KlR8IA6FcqD6OVz8CDISs1r8cn+PuYSwFSQXWVMdoMnFV9dZ7pOo+pwdBEo3BAPwgZyM+vMdyo1nNdW192vO7M9fIebPT6uuMg+zYOR90eY+YjXvEN4uF6vHjlvFrZ/NCh8wiQkkOQevcqD8Ryx2xzHLZTrwvR0iU8AuHENz81BTOC5bJ/x5B1Kc3wg7u252AywLeSu1e/85MC2m1snqSqCmk4d+q2OxwCq4orgpgUJn6oh+GVx2O/kQ9PjPbVot/Cooaep4Os9YDK6+JxVe+Yt4YJyadW6lic83cnC+oASxSrZlrKOz3VJ75UBpeIOIWfmWiUnDRxv3lOcEr0yFXJ6WKtvVutPDlPb7ZTOtsDZpoHBEtwl+EyyY35Adsdz5RvzYW2Fs7F7h9SKgyYet9HbPq9JTxRRUlnpFJpIZAD4g6NM475/wDsj5R5QeYFX1acYytUzyyRcI0cjEAycjXSVfMxLdolwGd+gAGOi6odbcb9xjeDTfW2lpF/d1aQkRxSnvEpHUBRuc8oAP2Rkkrvcf21FThlaWwROtNT0tOChusqYKwQjqtOhIJP2ieZskoNUTTsHIbv5/z3kyG5jl6vLcRVdPUyUpqLc8ipabZEhQ3ORNlYqN0po87D3++3lsdtSKx26ru1XWJWXWrUCqrI2AXZcrTwdlVVA3HlVRzHbl5vLXZ1sX1q93uaNrtUxLHP4SAx0seDyU8KnYbZGOmMk7c3PTpZJuMKuRvEFHw9RAiSTn8hQHmKKx+zkglurEg75QHbgjA6EozH27gt4rhxVdqm6VlUsdjiKq8vKRGkanZUByxXmYbdWZlY+YjVjnWRXMcQehFGFMK8vOaLnGFYqPjq3Bwif8tTnbdi/USrEqJEq0UdKiywo6ZFGhyEnkTfmnfmIii3xzFjux565xbfHtBSz2tHF2yyqgfneiL7Plh8dU/2m+z8IOeYruq5PMsMKuT3FxRxDUW9V4bsgZa9gYmigfnWk5tiit9uZt+eTr1UYAOCHCHDcVkpWUiOWvmV1qJvE5VUL/iRK/2UUf4s3YeRfMdmeDuG1sSZlHNdZOaOVhIFMOAC8SP0VguDLL0jXAHmICzeJr8bQI7TaEWe91AiWNUgOIlz+6Ph9gM5iiO+T4j+YjGpwuQJzknLR+619RFXLY7Iea7v4bSy+FgUijyo5QdHGcRRfYzk+cjlJcP2ikoKGOioeVo3800rYfxubOWbfDBuVu+H5W3ESSM8bhaxfVqU00IEjygy1NRKefxCxIZmOcsCQw6+c8yKQglcs1lQ/E1TNbLVK62RGxV1ZIZqsnBKg7AqeTJOwYJ9mKMax5J5lwMHJ7jr18fE0ktDTTMOH6aQ/WZg/mrpT5ivMcZTycxJxzcnMeVEHLaaYyxSwQU1MrVjpmlpzlUiRSP3j91RSF7AluXbm5BE1bqGG2xU1JRUqSVUmfqlLkgDBUmaQ4yFB5CSRknk25vCVJzSUlrt9VJNV/ujh66tdcGY7AADfy+YBEGRhh15sS1OSeJccyHSWekoq6quMlVPVT1BVZaqRAzyZAAjiQbANkBUGdio3XAkORRx0Mb1tZJHFLHGSSz5SkQ55vN3dt+ZupyQNuZmj22ohei/a0+IAIjInjZC0kbA5ZiesjAnmPXcgHBZni09Kl8QXq9MaSw0h+sQQTbfWCOk0w7r91O+xPYairmTqPUcMV1jN7vBFJYqT9/BBOMeL6TSjvnblT5ewM41DVKx3280s8NJHKBbLaV/eSSnIV2XvK32V+wDk75IRaORI+IL9FPHRxSj9mW4rzSzStsrsv2pW+yvRRknoSJsRuH7RiqJqaKo4jqIj9VpSxaC3wk4LMRjIz1YbyMOVcAEi44lcTxaatFzjqqlEqb/AFMRFLSgkw0EJOGYkevQsN3Ycq4AJHKik+qTxx1M8lvebkrKyPee6VHw+BDjfl25SVwAAVXADMrcaU5pZ1NbUz0Ek/JXVyf492qMFfAhx9nYqSuAFBVcAOwsNsop0mjq54qeGeJRDGkYBit8RGBFEAMNKRygtj2G2Aas00VZzRW2oA+t1rx0dTEgigipwGS3RkYEcQxgykYHNj2A5QAxClp4KHwlSmkMkZKU0KnmKM2S2CfikIyXc/CC2+5JkloYTGyoXkjLJEitnlb7QBO3N15nPwjO+5yxCJGk5+dTKwA8o25TkhQD9nbIHVsczHlA1kMmWxPZY15WEpjnqZF5SFGURSc8ijuDjod3IycKNpNHTYXmcks5JI65z1JPftv32GMcqlymgXOTlieozk74zk++2T327YGpbBIldmKgKuSzfCg9Sfz+eT6nPR8Ccz8zjCxo3Mw28zZOFA7lj6b/ADP55q19vBrOampyVps5ZuhlI7n29Brm+3d6wmngZlpgcnOxkPqf6DtoQP56e6HQbf6lncTazWbvQnUWlpaWm0WxaWlpakkWBpaWlqSRaWlpakkWlpaWpJFpaWvdSSeaWvcHSwdSSeaWvcaWD6ak7ieaWuiPTSUeupJjmc69AzrrA0gANSdxOcb40gN9dYGc6WBnOpOjieEb6RHprrS1JzE5Ueuvdhr3S1J2eZ17rzGvdSSLS0tLUki0tLS1JItLS0tSSLXnz17rl+bkblxzYOM+upJA3E/ENDY6QyTMJJ2H7uJTu3bPsNY9eb9W3WpE1zjkn5dlaFhsP8h2z8iNWq829LrWSyfXStUGInUgTQ842PlPmTf7vL01XLlaamljeeWnJgT/AJ9O3jRj5j4h+ujkoKjiCNcpJzBQkpKk+Es8Zc7eHJ5HPsA3X8M6UNraOfw6Nqqknk/5cLlS5916Y+e2pEdD+0cQwpT1QY4LcwKqPUjqvyIB1OpLc1FLFR8PXSuepY45FYSRls9EQ9B+ONalNgyRMvM3HCmLw7lYnWWZ7dcKpRkARlGjJ7bbFvfGfbUqmqKKKqFfxXT11Oo3+rSoM56gsR9jpvjGicBl4ZnFRc6aguVzQY8CnMjmFjnDAHZm9RkH01Oof2dFUm58TvUPWzfvKWjqIWi8c+uGGDj7o6e/cN9TnhTNhT8iNUkEfFHjVN4uFPBZ1TIpoJc+MmdlRR1HTJ659NKlsMl/i+p2SI2a10ZylSjNmJe4znDk+hzjUv8AYUvFMRu3EDtQWeBiYvCAjfPTEe2VG2PfbTSU98vlV+zeFJpoaKMBZkqpS0RUH4mOMhtvX576Dd+8jr+w/wC4XWuJEEdwopVt/CwFwqTlJCYVQzZ+0CPhO3XHyzjOpSNQ8EFbreaFauucAeGZ1dqZuxK9WXPcD886kVPFK8Fma00VLTV1ROvJLWUqPI8T7Agg9R8vkfTS4fprLQ1n7U4wqpDWyZkpqaaJl8U9e/U9NjjrrI2sc+rj9zOhBn6f+BIVrjouJLml64ou8cNE/wDhkqw5t9l3HlHz/XU7iHiK6XOpThvhCinpaUjkDRoVLr0Jz6fz11WLxB9INbJReG9JZ4yPEVxiNQOh92Hb0ztjQ29Dh7gymnstkNTVVhHxmYkwPg+Ydge+MZG+cbjUJJIDrk+w+PznD6VO04HuZ3U8N2L6P6f6/UytU3ydT+5ExCbj0B2Hv09M74rdrtfEl+q/rENYkFC7kiGaPxUGT0QNk43x1z+OjnD/AArxJd45LzxE1FJTDzJNVOyStj7xA3xjckbZ66g3rj2mpFlssOKMliq1kQ51kQbbDOUHbpnfG241asp1nL/sJRt4GTwv8wjW8SVHBkEdFa0oqyqKkVCQx45M9OTAPmx23Gw99QeGrcL5cZLpdaK75AMsi1ERI23J5gMbbnfA/XM/gm32CPw66uutPJJJkrKdxnc8q/xHHff+eiN1q7pxDViz2ilnpqLmAIKkPL7sfTboD2z/ABGtjNWTtOW+fiRBvX1DA+I7duMKKstqWvg7khDjEkjOEmOOoAz7jcHbtj7RDgLhG0xhq+61VLM8Z5jCsgYrt1bfbYHc429BtojbuC+G+HqD6/fKeGpqgBnxRlV64GPzwMeuO50MSKfi67Qw0lPJR0sbARGJ2UgeuM4APYD9fi0rfU4BGM/Jhgq5BJ/SO8T8VVlSTa+HIhFTv+7LxKADgdFG2cA9dsZ+yN2g8N/RS06C61NVJbynmjaHyEt0GMAE+mdvYDprarVwPR260RyTzCepji80xTlJ7/Lv6axz6VePK+nae1MtQ9Nkr4sLJzN2xjA98g49D1wQ6dQjtsTgn3MIelqxusPHxIfHfEdtttIKChqJKmtVcNUSKk3h4OOsgYkncbNjt5jtrOqKHiq91LTVdBSVsEmf3kyKrNnGdxvjtvnpvopZKC21tWaueeaVR5xHUKI9+m5Y4Y/I79Om2rfJxJbLZSYssaV9eBgqMDwth9nIJ6/6gdXlVCULlTlosLvacEYWC7mJuFLNHUVdvgicDIplmRmI3y25BABG5Ixk9c6qt14ypeIahaZquakjTzLTun7tc46kNkbYznBO24G2vKmK+8SXiSSqEysWBeSUFcY2GNh22GAMfZAG5ulFwTwxw/ao7lxJDTRRkZjSRQJZffPVV9/7777bNu68g/AlQVJK1DHyZL+j6n4RtUaVt4naRiQqyGLngGPhBZcr64XYDsOup/0gfSLPJSyUPDdNNMrgA1SrzIg/kT7Hyjvk4AzrjO8pxD/wdHTLS2+PCIzRc0nqAuQWXYDAB5j1PKuAI3DX0c3i48tTSVRoadDnmYfEfTK+g2wBge/XQ3kiw77VOPzmwfyxtrPM4s9lufENy8OGOaWWWQtJM4Jd2PU5O+cfaODjpyjrtXB3APDvCtLHXXGCkar5TjKrgbZOPU4GSegG/qdUoQz8K0JmrrqQyADxBI+fN0GUZGyewwxPoRkij37ja+VnPDduetomAUiVpOchSTyMe5zg8mSB9rcDUvK2jy6+B+U7SrV+p+T+cuX0k8c0t0E1vtNLRmn5WDVbRK4CbgmMsPwMh2HRQTuctprDU3Wq8K2sYwzBS3hncnrgdcnb3O3QYGj9moqe+iJ/qFziXmyUUGUE+p5VZs/PoOmNaTwxeuF+DacS1lNG1SAwVhUxZTAzjwyQ6+5I1vVVp9OmQcmZWvfc2OhGeBPotuNstrVl9u0EC4ULH9XSQjOwzzg+Y7DlXf8AE6A/SFdBaX/Z1huaPVqxjnMcUirHkbI3K5VnJHwKuw6+0/jbju6cRAQWqeBaXHxQzqsjBhuFycouNi27MD2BwKAttuVRN9WhpJaaJRytNJGUAU9QvoD8+Zu51TT6XUXvudsD2E5bqKqVwoz94GquKqs1BNZbYKueQjxS0TcxC7eYrse2x2A676mUF0tElS1VUUJWYnf/AIktk+u+Tqz262Q0CLHTr58YZu7e23T5ahXeejH7haaKqnbfBQN299vx6fPfD9KPw67i0R/jPxDlFU/nPRxXaqXlWWOaFWQlfISMD9f9nUGsuFLc5WkN4pvDABWN+aPOemTjyjvjvtvtnQiot9v8MzVKIfEIbMewbHZB3A7sdvTJ31Gj4dkue/jTU9PksMnmLE99+vz/AC0OPPuOAMwz+hSvJxDctFWTuIaKWlkQjlaVKhCeX0AByq+w69z10Tt1kkpAAsEhdtjIV2/0HtquQ8N1sAK0tdG4OPK8ZQbd/Kf11xJ+2Yf+Hp51ExOFeCQjl7+mSdx3xjfpvohbG0wyy8wV611XCNxLXcpaG1R8tRyTVDDIjG2Pmew/37gH4U1ZLz1Gd/MsKbYH/wByPf223GdRYL5xNTRuZ6mV42OzTRrKqYPrvkn0GcalWq/XO6STIvDsdXF8TmOmZXbHry4GdC26/d/7kMq0IRf6c6aH61MKakp46iZjjIQFV/yj+bH+2rhw59DDXulNZVeHGz7+JIh5W/y4OT88aLfR1DSvPzC1T07qeZ4nts067dObw+Y49u3prSq7jBqKnWaqlsojj2dXaekdVwSCVlQYHlIHqcAbnGlOr8Q2HFeMxjptCXXLE4meS/8A3v8AVUdK1Ulyp4IlAywqHQegG6nJPTA+WqHxHZP2LXm2K0dVWD4/N4jRnPRt9myOnUd8HynQuMPpT/8AElHHDarxTW4nyO7llaMkEcseRhdti3xHcZAypoaWmZo3+qtS1a9khnUs/pzZI/Lp/TTRedeM3kAfbiZ6ha6TikEn5Mq9RZY8NNFJEnKeYOfgDb77AFjvt0A37ZAHTUFyn5lokXk5ud5SzKWf13O3y/PtrQLTwvXXKtVriRTxBgFTmA5vkeg+Z/TW48EcFW+2UkbF4p2A8sUTBo0+ePiOtL302nGT/YStA1Fp+/3ny9bf/ElIVMa1RAGG5ZQ+T64xtqwW/iHiCHaSniYAZJqKUDb5hhr6guFt4aooGnudroJWKsyxmBOZgvVsnACjuxIA7nWG/SDxFZKyolpLDbKOH71REpWOMA58nqen7xhn7qqPOcKdcl58utD+00t0j1DfY4larfpEvNI6rRUVIkyc3iywzToAOU8u3OdwRnHU49N9Av8AxbVTSP8AXrTbZ6l2PhiWPld8nJzk5BJ39/fUlYYxE5JCx488jDqOpxnp8z+vXXVHaprnUeBRUoHMMM5TBIPqe2fzPt10QNIaju3QddX5np28SO3FlsaqVJLEju2ATBMcjP2cDOOmplLU8MT1AlqKWuhdQCyyMzAZ7HbVxoPoKmqKJJpHpopH3McqMG/TONEU/wDvfLvy81M0OCMjw6nl/wDthqo1Sp9VoP6/9SxpJ+ms/wBpFsF/4YSaItc7e8aHeCSYw5HpkjV0/wDywWOkWGI0cdPSJsqQTgL+JIG3+ms64k+jS9cNxSyV8q+FDF40oeoVgiZwCxzhcnYZ3J2AJ21ndZSTXKViBHDS5BAEYVmx0yQNs577/LOh76l1XXq/Wb0WNR9fpE1b6TeNJeLGkht9/oaalXASmeoCnPfmxv8Ah/LGqJScNzLmaOekq5Mbss6k4/oPb+eq3HZ6mJTJGYy4GIghKqozv33/AN5J1Eq4qqNjDTReNNL8fK55Qe5Ge/v/AC1vQ1lChNnUzuZLyTulzltF0QM/1Kablwf3eG/LUeh4fulyqeWriekpwejjBP8Ac+//AM6rFELzSxv5a5X35eRsgD3GjdFxHfKdVVqiYMAMiSIkf/baL85z9S4/vA/JrX6TNLsFmpqSFYKOMD1PcnVrt9sjh80ihn641lFFxpdfiltlsq8DGWjlT/7U6NTfSFQUljqnruHniuGQKb6vXMsR9S4bfbY4HXQGpvKjP8Rhpa0Y4E1230IeNJ6p2pqZm5UKqS8rfdjUbsflqVB9K1k4cqVtlLAs2CVdInDCI7/G4yGfbHKuQO5zrA7j9J9fOVL0NV4T0/gSLPWM8hTq3QDlU7eXqffQ/wD8T2pJVElkeHI5VMcrDl9gMbH20r8hdScu3ENNxo+gcy78ecXrxHfpLjKGBIwIypfkHpt00tUSqv8AwnHMVmoKtH7qXBx+Z0tGrVpFGMfsYK1mqY5gVDykgjbXRAwMY20h30lG+/TXpgcxAOBie5IHOBk6XReZRjPUDXp8uw6a5JIJAGddnCueYlAztsDpzuBkY9tNj07a6UYxjVJE9InW4Ow6687dOuulOcg7ZGvcco2J13M2Az1GXXIxsNRZIyWwo1OUb76bZQGOBuddVyJUgEQXNCfi6e2ocsQbOw9we+jcsYYe+oFRCT07a1B3DBllYoZVqilmt0zVVGpaFiPEiyRn5Y6EdiNE4apbnbTAlQyo+2cYI9Ub0z7dicbEjUuWMknPX00Eq6SWjqGraEDHSSLsw/3+WvK+K+DFM20j8xPS6DxIOAlv6GGbbQuT9Qh5TV1Kf8VIp2hiO/hA+43Y+m3rrU4aqi+jTg+G9yQq98rUK2alkXdARg1Dr+WB8h66zz6P+JKOkudNWVdH9epUceNTM3Kzb5Ck46Z39D8+oXi7iLia9ccTcQXAQ/XJGP1aPmDJFGAQoQZxheo999I67EewGzoe3xGT1EKdpyT7x+RLhV10ttWcy3auLS3OqkbeFDlmUt2J6sfw0W4ftZ4huNJZ7TBI9qppAkSqMNWTHqx+fb7q++gVhSauiNnt5bNRh7lWNkswznk6Zxnr6nA19A8O2NeEOG1jpv8Ahb3VQcsZwGahhbvjp4rdc9ttM2dta4oo9+/sPj/mAbV0ym27ofufmTZUpOHbR/4foZYmlODcahCAJHHSJf4F6aDPWU6Elplx651Di4bSTepudfN6hZPDB/8Abr39g2WJuY0aykfalYuT+evZaLTLpahWizymsuOosNjtOJ7/AGuM8prIifRW5j+Q1QvpAu9dcgaSjiKUq7lpW8MSN+O+Bqd9InENPbYXtltjiimIxI0SgFAfsjHc/oNUe2wVERhqTCai51bctDBjm748Qj0B6DufYaU+Iaw6gmhT6R2R/EY6DRrUBc3fsD/MFxxXO2VFXCZY4pGj5agg8zRocZwexIPzwdXfgOw1XFVVRUcNOtPa6XLQq4wrY+OeU+mPyGANMWm0NXz/APhy3GWr8SUG5VSHLVc+c+Grd1B79yCegGrhxXcl4Tsn/hCzNHXVdSyxTmNcmaRTjwAR1hQ/Ft5myDnza80Knsc0o3pHf/E9BvUILCvPt/zBX0mXRL5LQ8E8OBmt0DGVuZ+QTHG9TMewO5UHYLv3Ggv0d8LSX++i2xSx/s6CVnjDMVilC9ZmzjyADOTuAcdTqXaLLU1dY/D1E8lXWVUoF3q03aaQn/y6H0BHmPQkfdXJPfSBc6azUScC8OeHUVzMq3GohAbDjOIIz2C75Pc5J265ajYz7KxwP8xNat23Lf595E+kLiQXSoi4T4ZlaKy0Ll5ahjyfWZQPPNIR0UdvugADfI0P4L4MS9XZbjHEEoaaMs8lRsDGpPNO4JwvfC7dh1BOlwdw3LeK2O025BNEZAJ5EPlqHG4QHtEmMk9zlj9nRrjy+UclJPwhY6wRWGhIa+XKMYNXINhEn8I+FV79+51ZKBa3lgcDs/7CVe3YN39v+YN424kpb+8MVMk0fCVrlMdDTZxJcqnqXbHXJ3J7D8NWjgHhMpE3FfEIzUyHFNEh5eYrsI1HQRJ0OxBI5fUmB9HHC4u844hvMLUVrokEdLTL/wApOqxr6yP1Ldhv6YvldVPVT+IUSNEUJDEg8kaDoqj0H69dOdBovxj/ABWv7n/iK9brPwq8fWf2jVfVy1E8tXVzc8jeeR2wP9AAPy1knHHEM/EFx/ZNsk8OkiBeWVjhQozmRj2AGcf3Op/0g8TzVlUOH7N+9eRuVyv2z6f5R+vyGqzSU9NFRhQprKUzBSEJ5rnUjfkHfwUPU9+vdcF+I65WGxfoX9/+oLoNIyne/LH9o9SxBY6NKKAOWJa200o/xD0asmHoN+VT6fMm6ymPgW1vR09Sx4lq4/HqqxxzNb4nz+9b1nfOEX7IOdidK2wrwjbVvlxEFbxLc18SihkH7uNF28dx9mCPGFHRiPQah8JWiK6vU8QX6smSy0rmrqauoHNJVSsT+9YH4nY5VE7f+7PlbLTa29v0E9ClQrG1e/eP8JWehoLYeKuIYpIrZSnw6Gj5syTSNuEB7yPszP8AZH/aANp0uv0g8US1VY8UVKi4mYHkgp4UGfDU9FiQdT3Pqdz7day6/SBxRBQ0NO8FHD+4paVDkU0Z3xnvK27Ox/8Aix1UtHbrbDw9YUiqImYZYDK10in4j/8A20bdB/zH33AAPEr3E5PHuf8AaQttHEcq6mSpmo7Fw7BII0YGjTkwxJGPrUi/fI2jQ/Au+xJItlNBbeDrBLTpKOflzXVIPMWP/TT1Gev3j7AY9sdrp+FLbPNVzhrrMjSVtU53iB+IZ+8e/oPKN+YnJONeLVvF5Sjd5IrbGWKCMZaX02+8em+w/PLalF06i2wYP+kfH3MXWs1zGuv9T/sI9f7vNfK0VtSjfVlcx0lMrY8RtjgHt2LN2GP4dF+FLCtQ09fc5hFTRANV1IXAAGyxxjp2IVfYk9GxC4NtMl5qzVMyQxxIRLIM+FSQg/AD1Jydz1Zj3JGilI8nHVYbXbont/Clvb95Iy/vJzkKcgdWY7YHsg25iQLr/NJGePc/MLpo2jr8vtJNBAeN7glXUIaLhW2nlhjU7S4y2ATsScFix64LNhVAWz2oR8ZVkMJnW28JUkgXIJX66y5YKoO5UbsBjJJLt5mVVrdNSVPFXEM1AlTHQcHWxORfAPklXylgT0dyy742blGMoo1bZLfRtWJd6ktSWe3QGCOn5yqoM5IXHWRsjnPUAgfEQAGytYQB+n+fE2DrWMf3lg4l4jo0tMSmmaOw0zeHT08S/wDmGG2+4HKOhOd/hG3MTifHl2u3EN2ikDIJ5JP3FOF5xyA9SDgFcjHuQQNlOCvGPEs92qUdY/3KnwqKjTyhsbYwOgG2SOgIUbnOnLVQ0tgtzXu8oaqqqX8OKFdmq5QMeEmPhjUY5mGyjCjqTopK109e1eWP+Z/KYM7XNu9hI3D1MbFaVuVxgFberjKwoaJjztPLnBeTH/LU9fvbKNhovbbPcTXVVip55K3jG6DN5ufPtQRnqisPhcggYHwA8oGTg908V4hvZhhZKrjm5IviyhQI7NT42VR0RuXoPsjc7kYNhrRwrw7PQ0k0n1NGIuNcrYmrp+8EZO/c8zfZBPc4ODf3M2TIirIbFYOHILZTxI9tp3wir5WuFSvcY35Vzuw6ZwvmOdU2eS5cSXuSkSSSSeQiOqmiX/DG6iCIDYHGxxsoyu3nOma+tuV8vIhiylYwWILCp5aKPPlijA+3v8xnPxtlC0cNDQW6a2U8/wBWttLiG51dPgvI7f8A1OnP2nbBDsOwK5Cq2bBPL/8A5fxIP6nXUdVKD9ntRweSxQuKeoamPnuU3UUkB7x5GXfo2MnyhQ11tVEthhkv9/MEd0MKxRwxpmO3QHPLDEvdzv7seYk/EdN8JW6GixerpHTwVtNDyUVEPNDZ4PcfalY/9zN6Y8lJ4lluXGt4eCin8G3UIfxpS/kJOefmY/E5Vdz5QApXZFOsWI6HU0bA4jlwrqrjS5vGkv1SxUobx5efy8vVhzHrnGWfv/lADk5KmOOCKKnjjpqWmRZqeOWMlIEzhamZDuzEk+FEckluZsk4aNTGJKSno6JIVoIk8aJagEI4U/8Ampx18FT8EfWR9yNgFEcT3pbLEaenaae6zyeNEJxmWF2H/mZsdZyD5F/5SnbzHfVK8nicXbWNxnXFN/8A2QBbqBaj9sOSUBfnlpWfPNLI2/NVPk77+GDhfMSw64N4amsyNPUBmuzMYyyuA0G2WjjY7CXl3eU7Qr/EVAd4N4ca0k1tWJZLzK3UYL0xYc3IudvHZd8naJcsd8akcS3+CzU8VHRRQ1NyqkVKeFELRqnNlSQdzFzbqp3mfzv5QoO/2E6Mn1NGuIbqbSI7dbESou1SIxBFFEeWJAcxnk6hATmOI7sxMsmTygE+CuFhRF3qHWqulTzNUzyOXChiQ24+LJyGYbyNlFIQSNpjgbhyalneqrGaqu9UWeomkcsVJOHyw3JJ8rMPMT+7THnZHrjXT8QPLYbHKY7cpxcK5QCZTgKY05dsYHL5cDA5ExGGL1J9hOAEHLfpPbnXf+JKqSx2eVkssLf8fWbE1Td1BGAVIXG2AQuByxISTc1ZR2Kgp4qam8aoc8lBRJ8UzeU8zbZ5chSTjc8uwxGqRStv4ZtNPDDTNPJJ5KOjVuZ52ODzMcbj4SSRv5dscitJtFF9QFTfb7UB7hKmZpTusKZ2iQb7ebG2clseYkiSmZpggnMn2+Sa3WSprL3UwpLKfErqlRnmA+CNc5BC82AoyN+h5sS82uge6SC+3wLR26kBmpaWc+WFcEmaXJ3cgkj0yTndizVpo6q81P7cvcK0dspAXo6SfYIBk/WJs9zk8q74BJJ3POYaCC80jXO9n6tw9Snx44J9hUY6TTA7lc4KoepwSDsBFUCSNUzQXuIXq65peHaXM9NBOMGpI6TzDry9OVMb7H0GjFFb6293CK73hJIaGFw9ut7/ABFu08o6F/uqdkG/xdGedKlobzeYZEo45R+zbdyZlmlPwyOv2pD9lTsgyT3IMirua+HSGKna91ILrChLR0kZOzSHuB02wXbYYGSOngcSRyunWCvhp6WGKsvksZMQcErTRE4MjY3CkgDAwXOw2yVHiOnkoJUWepkts03LVVSEfWbzPgjwoyMYTYgkYHKpUFUDNryMUrUkqRPUVFBNNy1NUuDUXicjHhRnb93sQSMDlBAwisxO0FDIZ/rdY6LVqogxAMx0SH/6vAO7nA5m9h0AVVzJxLARWekdao1NSiCriUQgQjMVEhxiCHYAucLzNj06AKoJs60xA6vusUUbYCY+IBvzLyHp0G+oj1HLEkEaLEo5kVIZMYxuyq/YDfnl7bgeY7eQRkEkndgAMIFG26gKeigbqh/zvk4GssE9zXdtEeKszEluZ2AGAoC46gBT0XuFP+Z9sAkaaAJ12bvgnvuck7nfc53PfoAqoqblXmOOYn1PXr1O/XfPUnc7gcsmRooI2eV1RUGWc9FHy9fQf646OeBK7vmIskMLSO6IqDLseij1P+9/z1Ur/dXr3McXMtMpyA3Vz95vf26DXl7uj17iNA0dOpyEPVj95vU/y7aG42xp9odDs/qP3E+r1e/0J1ONLXWN9LlGmsXYnOlrrlGkRqSYnOlroKNLlGpJic6Wvcb6QG+pJiIdddco0uUa91JAMTzlGvCPTXWlqTs4UeuugANe6WpJFrk53GutLUkni9Ne6WlqSRaWlpakkWlpaWpJFpaWlrmZItLS16BtrmZJ5pa9UZ6681MyRaWD6a6UAa91CZJxg6Q13jO2vAoGuSTkdddco0sb517qSTjB9NLB9Nd6WpJONLBOuuUa91JJRfpD4etQgF2aFIGUhZJIgY2GTs3Mu4987d9VFTcoFV4J47lBnmHOwjl2/jXyt+IGtnIBBB3B2IPTWYcY2mktVzlaNJ6KGXDLPGmIiT1U/ZJHqRn30VRew9MwsqB5gmWS33FR9YpmppUIErSfuZgT0w4wDv7jUimp7nRVUslmuKyy8oVhUgJOQRnAkA3+ZzoTdf2kkaypSpcBHu0aZAmQ9QUJJDdwyk7+x1LhBEVNFbKkQCWPmhgqAXRj1ZN9wRvgDtn7pGivxC49cG8ls5HMk2e/U9hlnkqqB1uhJ5J6t8pGT1ww8vN7kg6l0dNZ6+ne9cYVUVdzHnhoufmDnszEbfkdhqDFXCnHgyUx8KQlUdkM0RbuDndTnI02lrt5heop5ZqGXGZDTsJIHPuvT8wMapZp0cZHvOpYyHmGKax1d9me8RVEVhs8IxI3ITFKF6AITgnH2hj8NKLia9yoeGOHKSero5PgqKSlEco6551zgr0wcg4x76EXJuIZaCKkrWkrqCP/AA3pZdgB6odj+GBo5bONaK28PG38M24CvkGJ3d/3rHuSpwT16DI9c6Au0tiD08/A9v1hld6sfVx95MstdY+DYX8ennk4mdeaOOpQIeU5AZMncbdevYDUag4buHGzyXXiuolitSsWKMxXOOoUfZHqfnn2Yt1gsv1J+JOOKqKtYtzx0jS5Yt2L4OR32+fy1WK2tu99u0icMwR22mI5HhbmaJ1zsXUkgHbbl9tyRnWIqZyeMt8/H5SxsVQOePj5hfie8UkbxWbgimmpGiOI6mOZmYDccvmyOXrnb+ufbFQ1djia93+ns00sI5wAHHiHsvL0ydumB+G+m4p//BsC1F1t1FI0p8wpZjz47th9wvt37ew+nqY+Mbos8l4pzSA+WNSUZR6crdPnv3O++dEqXG2pvzMzLtnLj8hJPEnHD8Y1S0SVq2uNCFNNIhC56bOMg+w2xv75P2a3WOyWmStqn8fl2MKjmkkb+L7q/P8AXfUq6V9k4Tt60MENNV1roOSIAMiA929fl37+hqVv4arr7Vy3iorpbUWPOZYFCF/mBjy/79MZozKpSocfM66rvDOcn4j9Ytw44rBH4aQUMXljVVwkI/h9/wBf0OpUVpThkinoq6pn58BI+YBwc4yrAYH5Hf16a7pp7xRVbW+ir0r/ADYfxFK/mQcg/mfX0Ok8LfR7U1dKl0rqGaMliXSVw3MB0IOPh9jjbY7bALUaqihdi8Ga01W2tk8yDwJw1xBxTIhusq1lIinEkrlWT2HZt+/t1Pa7zfUeAaQPVU0PhjYOObIPU7Dmz33OOu/rp5uLrVw3R/VqOFmqF2MWVLk/gd/kP9dZrxrxDduLrl4apJDEDykAHbfsP9+3rpIlWo1D4X6YyZ6aU5+qFb59JVbeYZqW3VFOYWwpQSYZdvtA4I/300C4dsKzmSuq6iI+GMzTsQQm2cD8PkB7DTo4Y4W4coGuF+giaoILJCWPMWOdzjqT2Uf3IzG83K43C5Ce2c1GGGFijcv4i5OCeYsPQbbbbcxzhvpq0ryla8/PcBtZmwzn9JduMOPaego2tfDYanxs9QpIcnfpjfJ/P05RljQLNwVVcTViyus0XikcgiUc7kdDjH47YHfc+YlKGycQKi1V3sVGSgL+IoKjG5JIXb88Z79tFYvpLp7PSz2qkpxR1j+U1fIWJz0U8pJXv0OTgkY66NrqoqXK8sZizWu2DwsL1/DNi4Ks4a43uvepYkJTROjnI3KgkAkjucgKOp6Zza53/iGvdRcIGusaYaBXZzIpIxnmDZ7fF7+XpnUtTPfK01JuVNcJpCFM3ijCgHYcpxgDsMco64Y761fg3hqzWKiFyq56eecbmXmDqhPp3Zj69emNQV2VDfY2TILFc7EHEo/DFseOSKtr+Gq5VVQVgZWK8vXYKpIGdznGT1zq1Xb6SrVBStRUscdDWovlilcKMDGACRhRuN8d9hvkR+N/pDEytbbFH4khPK0rKGCMOoA6Ow9PhX7ROwFEtvDlVxFcA5NRV1Mr87Tu5kJb1Bb4z/EfKOw1TdZby4GP7S42IcKeZzdEu9yrPrVUgqpGLCMRPmNAeuCDlQfX427kb6v30d/Rq0ojuV6GQQOSLpkdht8K+w/10W4a+iO2W2i8arr6lZ/jdxJ5F23LA7MfcjVW4+rKPh2RoLHeah7gjYZQnhiNTkZkMRVRk4wvIWPfGcHMa1G/p1gg/wB5b8KQd7nI/tNB4uvlg4ctoVoqeWQExwxLEHJcdVQfaPr2Hc9jhHFd2kvU0lTcHKQMf3cAfxBtn12duvmwFXJAHYQaviCunnEl4tZq6hlCeQusgjUenRU32XbI6j1I2ins00zVks0xc9PrQAVMe+Au3bfGiNHpKM5dgTMdXqbQuEEr0HCs9ciy/WWo4s8yKV5mc+pOx/H8gBolFar3bIyaasiaJfuuyHvgb5/nq1TjlQSc0bK+8ZDrh+vRskfroBcUuFTITU08kUAzhegI7kt0VfxJPvgEPMUVr/S5MR1nVWufNGBAs9/4ijlYoomh2jYSJ4iseu/r8up9NeDiSjSTlrLNF4krBnEcjKwH8YOQd9+U7d9FKGlnr5xBQjIxymUDAVT2UfZB/Nu/fGzfRx9DyfVUrbxAFQgFY2Uc7+nX4V/U/rpXqrvIBd3xHGmqFh2KsymzWa2XMG4tLXRAnc1MTNHn/Oqcvp3wNT6yjp6NlU3S2OrHAdapGBPp5ScH2Oto424l4b4BojTxU0LXLlxDR055O2xcj4Rjf1PyydfP/FtVcOL7g1ZdWi+ssxeERQqrIDgemwAGxbJ6nc7nLQ+Ja2zlV9Mms8P0gOLDzJFTQ3aYFKaFWg3JeN1cn8jn8P6gHQ+qj+oR8s1NMrOPgZfM/wDmPpn7I9d+uhdLYq76z9WtDmaoPkjK8wCZO+MHzHO+ex6emth4S+jHjaCgimq7zG8jjLU1VzScvXAPKykfn+Wtb/ERUc2juUq0AZdtfUoVj4fqLjIKu5gpGP8ADhGxI/oP99zrU+E+EGrDCjwxw02QFDL5fkB30SpuGLhSq0tXbqGRojymSiuJjbmJ2Hhyo+SfTm1WeOPpAmsM7WlBcatC3JLmmizGhAwC0Z5WGScr02AbmyRoO7xRbR5dPcMo0Bq9b9S38R8S2Lg6k8GjeNmyfDKKCXIyMqOjEHbmPkU/eby6yji7jC9cSM0FXN4dMfMtKoDAH78jMDlsdzv2GBsAU91stfUzVlVeqqOd3AMtXDk5xsARsNthtgAYGwGHkss9wCrQ19G1EWyXjYlj7nbc/wC/XNtJodPX67SGYzPU6m9/TUMLK/U0BrrlIKNBPUydESFREhzuVQDH49B+WrpwR9E9Xcag+JVTmobBaSJyqxHfc4xk79tXL6O+GbFE3JUXKmpFUjnaSQLJKfQZ2A/l21rlvq7VRUf/AARp4rfCcPKG8pPTAxksxOB3OsNffWnprHM20dVjD1niUq2fR5WWxUo4OIZKiRuqy0FPP+J8RCwH/doXxrTCx0EhqKnhmo5ldY5Wt7wtzgdF8OUBsHGTgKv2iDsZHH/0lUtC09Fa0VpnYhowftf+oQckj/pgjH22XPIcbu90r7xWtPVTNPKSB5j5VA6DAwNuygBVycAZORdFo9TqjuY4X5m+p1lOlGByfiN3fju7mdmlp6FbZNy80BlaVcp8IOTzHBJYZ6Z29TDXiWhMKtcLBEHOWWOnkIJH3guTt89SKejapl5IUExY4MpQNvvso7kfgo+e2tY+j76JIagJX32Dw4pMP4Z/xJfdj/v2A0ZcfwaehoJUfxTetZn9qg4eubxO881vckBPrbMiL3zzFcD55+WNa59H1PRWuEC30dmucg6SU91hZl+S9j79daAljs1JTqkVrgVUAVEjjAP5jf8AHTqWDhx3jN2tduleRsRRvCHb3wTucdz0GktvitlikN1GdWiVSMCDZbrUUames4cusUPVnRFkVfU5B6e+su+mW9cTXO4RLZ3rTFCqusSHwBG/UHlOCSNjk/kdaJ9L9Lw3beG3it9LRiWaMqqQnkVP48LsSDjGdh1xnXyxeqOq8b63DPUyzISHBbJY52y5JJyOu2fTHXW/hhbzPMCZE5rNqrsLcyXUWu+SzvVXZa6qneTxGLc7jn6Z3zv25jv8saYnHgDnnTwwDjlK/p7/AC0OF2v1EGhhudf47nKxrMSsfsd8H5fz1YbFUcezUi1MlHNWxnI5PCBJH/tJG2ny69K+NuIms0TWHcTmQLbbLhfJeWnRoqfPmlYf7z8ht/IaXwbwGsi+FS0sbrkCWeeMMB+Y/QaG2GprvF8O4Wi60qjtT0qyHPuCyH9NaFZ7zeOSGjoq6SKI7RRVNpdT/wDYI389YajxDA/pnmb0aJW4aGrL9GvDUoEU1sSd1+KQZQn8FIGiVX9FHBMNO81TDLTRr1IqD17AZzk+2o0vHEnDDxLW3KwVbTEhgTJTvHygli/NsoGB1GSSMA6o3Fv0r/t6mMFvvNNbKnfnqMMWjQ52iyB4eR1fdj2IGkq6nWWvhbP3jT8Npa09SftAP0o2/g3h+Saltv1mS44wlKxUtH/HM2P3Yx0QZc7fDrLUph9Y8ab97N1Hblz6D7P8/wAdWIWkTkijulvqWYliRUDmz675367nPfTbcP3OFGZKZpFH/SYFmPtvt8zv/PXoNNWAubW3GItQ9hOKV2iBBSxjmBUA7nrgJkbnP2enzP6ahQW4PIaa1ws0suxkA3PsvoPfv76sdFw3c6+pEVVCaSBTkq3Qf/jH3P8Arq+WPh6loYlSCMFj1Y7k67YlXuBJWbQMZ5mWL9Ht7CgtR3BmPUiMnOlrfbVwlXVdOZYqdipOxzjOlof8VpV42ibCnUnncf2nz0ijc/npLjPsNN00wdOUlQcZBB2O+Nv95HfTqqVO/fbTuq1bV3KYvtoaltpE86DlxtpMoK9NenGSD+GlGRgg9dag4mJA6M8RMAg/hroDYqAQex16Mb7bjS/lqZnMcYnCLkleh04nTB6jXi45x7a96qT0x21J2tcTzvnXhCliexHXXqgEcx17yg5z31JwA9xrAxjrjvpiZBn4evfUtRglfU51w65BI6jXQSOJM5HMFzwZ6jf11Ckj3wVwdHOVX6jY+2olRAD0G+tVIPBkViJVbjQSQzmsofJIPiTsw7jHce2p1ouMVTG2QizrG0ZLqGaLmGCwz29D8s77mbLH1B2I76D3K3uJPrlITHULvt3/AL/LXnfEvCCCb6ODPQeH+JDb5VvU2L6FrDSWa2C+P9VrEjl5YIWbDmYDPM4wcqudgceu+rfNLLU1Dzzu0ksjczux3J1gvBXFM9DVc8TGOVRieAk8rr/b9V+W42iy3ejutAKikfcYDxk5ZD7+3of67a0/8ds06qUHD+8w8drvJD9p7SXKwHMoPz1U+OeJI7NRMsbr9bkHkU/Z/iP++uifFF5p7PbnqZiC3SOPO7t6axieWa/XOevrp/Dpo/3lRLjZVzsAP0A0y8S1xX+hV9R7PwIr0Gl80+bZ9I/eNUyrL4l3uYeSnVyI4icNUSHcKPzyT2H4aOwU9bBUPTZAv9eg+tSgbUMBG0aj7LFdvUA46nXFIGiNLdZKMCqkHh2OgYcwiTO8zjvvk/xN7DWh8KW+i4J4ebim9tHPcajmmpFqPMJHB81TJ3KKT5R9punbXm73xiijs+/+5no6kB/qP0P8xOql6D6M+FBGgMd8niAPKf3lJG42Uek8g/8AYu/zo1HT10dTzkheIK2ME8my2ymIGAO4cjp3AOfiYa9asq7lcU4kuMclVWVMjfsmjnHMZGJ81TKO4z+BICjyqcXa2LSfR9w4vE12/wCOvdexegik8zTSHOahwfsg55c9TlumMD2uKF8irv5/3/4m9am0mx+vj/ac3qspvoy4ZW129VHEtbDjfrQwsBkn0lYYz3UYUeuqPw/aKupqzQQCVq2fy1cijLxBv+UMdZHyM46AhRjfTVGLhcbu1yq5WqLvWsZY3lPMIgScztn8eUH3Y++g1E8f0dWOmpbbD9Y4tua/8DCwy1MrZzUSZ6OcnGeg9y2sa62BFadn9h/yZozDlj1/P/UZ4sr14Xt7cD8NvFFeZoMXasVhyW6n6mIMOjY3Zh1Ow2wAE+j7hZeJKuFY1am4dt/71GlX/FIOGqJB3JIwq/h97ULhXh2o4juf7FoXepgafnudcXP/ABsw3K83/SXqT+P3dbC6UdDQR2i1gCjiIMkgXl+sSAY5iOygbKvYe50x0ukOob8PXwo+o/7QHU6kadPOf6j0P943XVELxxUtJGYKGmBWCM9d+rse7Mdyfw7az36SOLPqET2m3uWq5PJIUO65+yMdz39PmdE/pC4nisFvZIZENbIuVyf8MeuPU9vz7ayO1V6vPPWSPIlc7ErUSKStNH9qQer74Hod+uNNtfq6qF/C1HAHf/EWaLSWXsdRYMk9SfSUcdLHVJVTFCABcqhN2UHpSxfxt0bHQbdA2bxw1b4LVRLxXxBQh3Y/VLVaYzjxGA2gX0UfFI/uR1J0O4Ms9DJR/wDiS8iSh4etmPq8WMySM3TA+1PIRt6DfoBr1P2/x3xtNRxQimWNRTCKIjloqfr4CHsx3Lv1PmycZGvK36gWn/8AUdT0dNOwZ/1R+z0FfxpfqusuNXG0JPi3OuJ5YSqfYXHwwRjAAHxHHXIwxxVfpOJ7nTcO8NRSRWqmf/hY+TeRjsaiQd3boi/ZGAP4n+NbnDNRR8D8Kn/6PUgTTxjH12VftZ7QJvgfaPmO52L2Wgi4MtMiuZRfJVU1NQN3pw48oj/9dx8Ix+7XzYyQNZqhc/5wJoSEGTI9VU2/hOAcJ21GqrlMOS4vC45iTnNMrA7bj964PTyA/EdXThmwz2aha7Vc8cV8qlDROYwVpI8bELsBhR5Qeg8x+yBF4K4bWmMfEt1p446plCUVKACqxg7Ag9UBzk9WbJzgEsB+kLimW5VU1ooKkMh5mrapn2ON2y3ZR3Pfp6AtNLpwFFj/AE/6R8/cxfqbyW8tO/c/EC8VXtq+qnpobjPPQQeaeonwVYg9eVQAd9gMEk49dotmsEt+qxC1OIVkj5VQkL9XiG7O5G3MdySdgNhsMa4sFsnutdT09FTyOhf/AIaFlw0rHbxnHrv5R9ke5JNrqi7zf+C+F2EtTNhrlXoRg98A9AgxkdjjmOwTGGrvNpK5/M/7CW01Yr5A/KNcj3dl4O4ckSG00m9wrlXkEmBuT93APT7OfvsQCsNHHc5m4V4cH1K0Uo/+kas+UYA5Wzj7RHlPcA+GNzIW8p4AfC4J4QPKFw1dXDYjG5Ynt1yPu55z5ygSy2q20iUa2S1BIbVS4eedl/xmGR4jDuoOQqfaOe3OSB9ftx8fMKyVH3ki3U1H9SSGlH1KzUKhlYgA9P8AEbsZGA8o6Ko5jsE1n3HPFKXZhFTq0Nqpm8OCBDgysNwBnO+5JJzgEscswB9+kDjKC4O9ntsjw2qlP75wcvK5P/2TMRn3xk4UDAzh2jpWp5eIb5J9UttIoGR5uTJJWOMH45GIJ9yCx2AwWirSu5uSf8x+Qgp3OcDqTbBQQW+hl4k4gJWNCIlSMYZm35KeEHvg7n7IJY5Y7k0nucN4pat6aGq4vrkVLXbgnNDaqb7LkHbPdQd2OXbbrCrK+ZZaG+V1uVrhUKYeGrH8SUyE48eYfay3Und226DRA2iW3U1VTy3VjXTnxuJbsx5nVW/5EbDqzHYgdfhGBzE4s3JJPJhCIFEJWhqK02qvSlr5JEL816vanmkqpSSTDCT8RJz5umxboF5c/wCI7zday/QiGjEUMMQjo6WM8wogxBUgdC5+LLb5YN90aI367GtkpqWgpkp6eFcW6hIBWFDt48u2GdsDAPXH3FAYlarabV41NFUmnuKp49yuMuT+zo2+0SdzUPnyjcrzA/GwxYKKxn/Uf2kBNhwOpzQUf7JpZrfT1H1R4VAu9wjHMaJW/wCRF3aofcEg5XOOpcrfODOHIqAUnEN2pYqSKnhJstql+CjjyM1EuOrHC5PUnlVdgvLxwZw9Q09FSX260YprVShpLNa52A8QgearqD64wSd8AhRnPnD8W8Q3Diu9vZLRNIoLB6qq5cEdgcDcHfCIPhz99s6GZicgfqZrnaJHu9fU8S3SSwWJnprfFIXrKrAU8xO52wOc4IAGOUZAxhirjfU/qEFstcMS2xFLwxO3KlUEOXmlYYxTIQCTt4rAAeVVCcctHFbobLaYBJQ5ZQofl+vuuOfLj4YE28STo2yL5clhd/vcNmovHkKVdXUlZIY2XlFSV+CV0+zAmP3UXQ452zhRq1aZllAUbmnPFN/hsVN5HNRc6hlniSZAGZsYWqnXG23+FFjCjDEbqpZ4PsM1FP8Ata5+NNd53VhzL4kkBkyVOGzzVD7lVOyjMj7fFzwpYKmWu/8AEd7LT3OV1mjEkYkMZc+SRkOzyMf8OM9SOdvKNy/EV4pbFSc/hpUV1SHEEBk5xJzN52Z+rIWH7yXrKw5FwinJA4GBK43eozjia9Q2SkWKGOGprqiMinpwS8ZQtksx+JoubdmO9Q/X92oDPcI8MVK1huFyeSrvk7O0tRI55oc4DAEbhtwrFd1yI085JRrhSwVEFdJeLzK9Rep2LSSOeUwkY7geVgGUbD92CqqDIyhStye43KmqLPYXFLArCGurwuBHgcvgxhc5YBsELnk5uQEs7s9SR0JYA9n+0YudU94qJOGOHZRFRRELcq5ABzfZ8NAu2MeTC7Y/docFy5dWoLDaYKeipDNzZWlposFqhuXJPpjGCT05SPsFRNxbLdQWG009NDTtIsh5aalQjxKuXG7E9OXB3b4Quw8hInK0VKlvFVc7pURfWygaqqSCEgTJPhoDvgH13Zjk5b4cyfYS4BDfeC+HrHVLWz8QcQTJJcpPiIyyU0ZJ5Y0G5LEtjuSSepZua2UdFHCWrrgEiMSF1WVgVpkwcu/bnIJyeigkDqxkhWGskromuc1L9TpoiXpPHcDkj5d53HZiCcZ+FenxHn7po47xA10usn1fh2mHiqk3l+tFTkSyA78mfhTudzk4GuYLHmdJiilS8wtdbiDS8PUh8WJJwU+skHaaUHflzuqdzgnO2prFKuKC+cQxSRUMUqm2W3lzLPNk8jsveQ/ZTooyTvkjmOU3ARX28Us8FsikAtltZP3k8h+CR07yH7CfZG59iSJUpdIpKmCGs4jniJpqbBeG2wk4LsR69CdmkPlXCgkaYwJwCKmWt/aQmeKGo4hnjP1eDJaC3Qk4LMRjOSNyPNIRyrhQSG44qb6pIPrFTV0VRLy1FQuPrF5nwQYo8YxHsQSMDlBUYQMT0v1ZqGRDJUzW6eblqKhDmovNRuPCjx0j2IJGF5VKjCBiSdBRVFRVPK0qwVCj6vNNB8FIm3/C038ZwOd8ZGB0woSjMJYDM9pYplkaqqGC1KKKc/VRlaVTjFLTDYGQ4HM/bHYBQhOSL6pbo4WRaaQoQlNC/KI0G7KH+yPvy9d8DcjT0U0FIkcVJDGkUKMkeGwFA+IKeyj7cnrsMnTSRvJMzNkvsSSMHbcZBzjGchTkLnmbLEDWOcmXAnFJTtv0XAUbJy7KMqAp2VV6qh2X42y2BonR02D8PLjqd/XPffrv6k7nf4eqWn5MDlIP47b5+fXfffO533WRK8dLC8ksgjRAMsR8PsB3b0Hyz0AHRk8CcOAMmOTSR08DySSBEjA5nP2fTb19BqnXm6SV7hFylMh8kef/ALI+p15eLnJXygAGOBP8OPP6n1J9dDxp9odD5Y3v3/ETavV+Z6V6nulpaWmkAi0tLS1JItLS0tSSLS0tLUki0tLS1JItLS0tcJki0tLXvL765mSeaWlr0Lt11MyTzS0sb410NhjUJknOlr1uuvBrkk9UZ15rvXhGdSSc69C7dddaWpJPAMa9Olpakk8G2vdLS1JIteAY17pakkWlpaWpJFpaWlqSRaWlpakkWlpa95ffUknmlr0DOvNSSLUa50kddQS00q5DKcdsHsdSdLUkmKXKkkt1UaeeKS2VGfgOGhc9dvs/+0qfXUWkFTFfYnqLfT1MErAmbdvBcZwQRhgpPy5TuDvrU+ObJUXWgV6KOB6iPOUlOPET7vQ9/UayhgschhBeldsgwSk8pH8JG4+akgeg0TkWpMcbGhiCdK2uuVW1bBRJkiopBzfu3IwrBt9mGADjGwzupJh0ciSRyVK0lbT3CjbDlcxiqT7wU482MZXsTtsdNWSoe301dLV2mlnk8PwvEDFWmjPfIPKzg4yGG5wcAnInW+SZeDJ1hvkM6svPBGsjI1RAD/hsOp5SMZBLL36ZIod6Tx1Ntq2Dnme0klVNTJK0kU9LUx8wq4GCN3wGXoTtjfvkacLUFxQx1FJT1cqAlcp4cowcZx33HY6GWcW+ltU09FHVyU1fP5EldUEUhOCCwHlfPLg7AEA99WFaCur7ObnVW6mWspDyNNyKqSrnYkjIRz0IOwJB6AnRf40KfWOPmYDTEghe4JmsEksYSir46oDf6rXJuv8Alb4l/A6VBe5LJTNTrbko2GyyshlhJ6Z5hv8AmCOnbILD1Mi0prbfcIqqhbJaOqOCpzuOYk4IO2CddUPED0z/AFOsimiQHlEdUnMp27Hr+pHtokNXYvB7mJDI3qHMVks4u9w/aV4uNPMGbIPjBl+ZPp7fn3zO4ou9ipI3tVit9DV1Mw5Jqv6ujE9sIcenf5Yx1ZpKO010rVETy22fPlkpmwhHvjr+IA1wKKvtMorDTUdwBPlmgQJKw+Q2J67gawu02/APCiRCVyV7PzIdu4fvtHSfWpLpB4PVKOrTxFT5FskHb2/DVn4ee7cQSpb5oKiEtlYpqbdZD/lxkHpuDt7ZGQM073etSM1ioMj/AIadTEw/o2PQH9dx9AfRKbDaLR9Zkq4hJjlYyYBHyPTHsP56UeJXWUV/0+oXpKhY+HMCcI8D0tkMdZd1+rrznld026nb2Pufwx01Zr/9JFotNO9BSlXdF5QR0Gdh8/69s6B/TJxhRVdH+y6KUzI435MHJG22x7/7PTWZ2fhziGWGSrnuNOKEDKxVkfiBfkWOf19tI6qG1Q33AgRm1q0sUpndbaqzjW6PNKGRWbPOoww9877fz9+unr6lLwnSf8JxBWVFcF/dg4YBug3BBxnbqc9ACegm5cez2xJrM4WIAtz1NMnMBg4PMDgnHU/gD6EVYKOmvlcJDeaWRWILSmQqwztgg4K+mep6AqNtNq6F6qOAIDvKjLDJkKtvNxvdWou1BW1ExyolpcsB80ORnrlQe3m7jVs4Nfhm0N49weUVLN/iVCAY+anfO3UjG23TVpkq+G+B7OpDo8roOUJgs46Dp0XrgDr29st494tqeIcwSK0FvJ8tMoGZSO7dvw+Ed+ZsjWqNZu2oOP7SreX9TnmH/pD4xqZA9Nb4np6Qdasg4P8AlODv08xyfugnJ1QLdZpbw2fCMdKScuR5n3336799yT9ot0D3DXCnETzo9vuU9Jz7LTqpYHr1Gf59vTpq3V8t24QpI5bhJbKqpRsJAmAXx1AXlwxHUnIA0ci1af8A90c/EHc2X/8AtniDhwDb7TQtc3nqbYiR8yhZcFh67/COm+d+2qzW3K8RTNPQ1vhQrhcOPj225gQTk56ZLEdgN9TbtxXR3ypSevr5qR2PMkMw/dlgMFgwzk9gxBwBhcYGpFmsa1kqz1dRTSxr8CQyAoAT/XuTue+emrpU17ZzgfaVsdaFwBk/eBrffqhXzXWBBS+VTMkXhh1BPUKeXGd8dPnrVeFfpJsFitqTy2z907hGqIWOc9huMHtsDqv3G40Npi5F5efoEXsfQ+/Tbrv266p9yjjr5ZamsiiiQ5XCrjc9QeXBZunlB2+0dyDzUUAjZ3K0XN9R4l94v+kC+8TyGOz1cUFv5laNaSceL3xvsQfVj0xsOuRHCvC9yu9d4FLE6FHxJUOh5YmPXkB3dzv5jv8AIdAnCf0e1fElYsVvE9HBkMzAjOOxZsbD0A29AdzrV4Po4v8Aw7TfWqLiKKWGLGGkEkUq5wAqlGHMSemc59NL7bqdKNhG0wxK7NR6s5Eu3CH0f261UfKYVeRhl2fdmPXLHv8ALp8zvoB9IN54d4epmgakpqmtlGIUjjUvJ13XbGP422HYNgjVEvX0q8S8P19RaamrjuFPEAZA8iScgwQwZ+VckHB5Nxvg5wRqmS3ehu1bJPVXKYXCpHM4rush7BmH2cYwoAH4Y0DRpGvfdY4xCrbhVXhF5gviKniulY1wqPCp2Y+RYUyoxnAHeQgnJYnHz1zZLJxPUSo1rqZY4QQFUSkM5/HIO/8Apq12PhtqmvikuVVATIwCF25Ysdsk4AHt0+fb6E4P4dsHDVDFWSSw1lUw8skeGxtuEA/n/IaaaqyjR18d/aBaVbtQ5DdfeUTgvgDjGgt8dzrvq8NUv7xcTiFotjueZHUn541K4k+kniLhhDS14qq9mXn5UpIzL4Y+Ihon2GCDllGQcjpnTP0l/SoZnkt3D7xMIjh6nHPHE38P/Uf07DsCcMMYudQjVEtRWGSoqJSS5kbmlkJ7u3UZydh1zv10to0eq1v9S7r2zDLtXp9N6KxkyXX3Sz3i6VVfJeVjqJpc4qomAUncAEkgn3JO4ycnOZdFZKi4VaUtPVUaU0jeeYVAYN7sev4f/BFWXghLkqT3BHp4MfuqeM4z8x0A/XWlcI8BIjstFNX0iyEFo6eoYRk+pQ5BPzzppbc+mTaRxAa611D595oP0ecI2Cw0YqKOopqyq5Rz1Ksp5fZcdB/vbRa+8RW+00c8tWQihAV5n5Tg5HM3dVPQdSTsoJ21QOKZrHYaHlnulNWT+F+6Sahj5mcdOR6cRtjIwXbI9OYg4yK/cXXCatNNc6GjronkM0ESTyMUB2OWYnB5VA825AGdjpGEOrfcxP54jZmXTrgDmWnjLju43qRoKCZ6ShGUEijlZweqoM+UHvuWI+JiPKKTXeBDTvTyJkSDlaAMRzAkfGR13C7ew9BqVS3rh2vnljD1lBKBjxf8SNRv0bsPy31ZuEOGqF3NZSubuwIPiRKJFjz3wpOD7n8NegoGkpTCfv3E1q6m58sf0lUtPAcl3ZHq1np4SOWKnh2JB7Yx/rvrUOE/ocWkVaqaseKUkBIgWRl+bxlSD+OrxwzUcK2wLFT1cUtyk8paoUxFf/djA+XXTPGPHFDYKVhHVJPPICwkQLliDj92DtgHbnbK52Ac7BTrdQbDtqXEZaajaubGzIvE9sawWtmquI60OkfiGKeWKrQL0Bc1CMyqTt1yTsoY7axLiPi67islls60USBwySQ0fgHZQpyucKM5bbzebfl+HUrijiCvv9Z4tYzCPm544FYnfpzEnJJxsXbLdhgeTQOomWIgAc832Y0Gy/7/AD9PTROk8LcLutbBgl/iKltlQyI2vF3NCz1lst7QKvKZFUxMSOoB2z+A7747y7beuHrjGqz0dXQpz8rESfu85wATjGPx/qNEbHwZNcmWsvCAR7ckONz6Z9B/vptq40PAdnlUf/R8cS+qjB0U62VjhpWsJYc7eYX+jiosdtm8Wnt0d4nBARqerjlZMeiJnH6Y7Aa0wcX031Xxmt10pFzhpZ6Riq/+3OTqg2vgC0NTS1lclHDa6fzVFVXqrxoO+C3f2GvOIOLOBeHaI2vh+nrPGC4WKjrpI+bP2pWRwEG+Qi+c7Z5NIdQfNsxtJP2jbToEUnOBLzc+OrRQ2xjRVZrJOQsZGRm5cnGAgwztnoox7so31jvE3Hl4rppnDz0cLbNzn95IB05zjBx2RcIvox31QLvcb3NUfXTeLo08Z5OUyEnwlACAYbGOoxjbqSx1xT8W8Q0sbGpnEniLmKCeBWf8dsge5OdbafSVV+u1T+swt1Flvoqb9ZYrle6qogC1MriJVB8zbnA6knptoAj1dzn+q22FiCcM+Mco9vQfr+h0Vtl1muUGLvwmjhvMjwQnmO/UDI/PVwsaWGCnWMVH7IXO4q6SaNR/38hX8201TV0KMLxADprCeTkwVw3wtT24CRgJ6n7xGw+WrjbrQrnxapFIG+CNE7NaHqMNbJbZcy3w/V6+NmPyXOdEYoBR1En7et10hESlxAkW8gH8WdhnbQ9+tRhgGE1aVk5MfsdJNUOI6fMcEPmeR2xHGPU9taLb71w/Q2lle5RiRUzzM2HbPcA9jrBePeK+IKj/AIO0W1qWiT4THHzRp8l6u/8AGwAB6AHzaogrq2Iyq5nad2y7ylicg9ST1Pv0/HSz/wBPs1B3dCFHWJpuOzD/ANLl7nvtdIk08Zp0YtTxcmQvYtv8RO2WbPbWa1lrd5zPAsRqTgjnJPKO53+XVvXYZ0ZqqpcGWViSzfGRzFjv8I7/AD6egxtrq12utvD8scfg0xPmJ35vcn7R9unzG2mqaGqtcAcxY2rttbJPErUNumaX6vRr48khw0mTyKe5RT39z39NXDh7gG9pTrUxXqkikbcQyT8jL7HmAGfx1cLHw/S29P3KFpCMM53J1Z7Za5JHUFGJJGABudYX0hfUH5m9bluMSpUPDPHEUYkMNHVBerJNzAj5rIf5a0Hgzhm7VcQkufDrSqAMBK3w9/UZXf8APVq4b4cjgKy1ka5GCI/T5n+mtBtb06YiHIHxsB2Gkt2tsHpByIzo0gY5Moi8MyQqEjoOJYlHRYbihUfmRpaOcX3+mttwWBqifmK5KxScoHz0tYeZYYV5dY4n592e6Q1dP4qucZy3McMh/iPX5P6bHI6Haafm/dvs2cAnbf0I7H+fbOs7mp56Kp+u0DlHHxL2I9x3GrBYLvFWRcgBRkXDw4yV3+z95d846jqpBzlytl/h1ux+oNZTTr68juWo8rDBODr0ADb0GokEquoJfK4BD82dumc9x/Ft6EA7amDoca9Pp9Sl6blnltRp3obawng+evNwpX0OkQSAVzrpegBAH89EQbOeJyvwk82uskKOXv668Cjca925Rk4xrsk9TG+vSQDjrpA7bba5K4OdQTvOJ7nmII9dLI6DrnXsYOMj116QAcamZOTGyiqx99NSoMfLT5XPvrllGSDknVgZAINmgyCcagyxnvtjvo5ImVOfxxqDPDucjIOt0bPBnMlTK1dLa0rCogYxVKHKldsnU/hHiOqoKwFWMVSmzxkeWQd8D+nUdR7SZIznDHb7J0KulvFR+8U8lSu6uDg5+ekXiXhZLefp+GEd6HxABfLt5UwtxZWXTiO8xIEAhcfu8N5ETGSSe3qT6fhpuiionphUSK7WKhkAjQeVrjU9vkv/ANqu/U6F2m4tJ4lurgVkdSrgHAlG+cY7+3ft3Bv3BNmpb3ePrdfW0tDaLVT+IvZKWFcc74PxOT+ZI7DGka61kVgw/qH5/wA6jM6MZBT6P8/eF+BLChWq4y4rHNEpC+EuF8VseSmjHQAAbn7Kg++K3xLe5eLbrUXu7PmzU0iokUXkFXKoPJBEOyKOnoMsd209xvxbScW1sVstlXHbeHqWHHMTkQwdSo+/M/VsbkkL0ByV4FsMV4lF7uSm12C1w5hU4/4eLPxejTSEbe+/wqBrm8aavI5dv8/tOhTa2MYUSbwpbKW3W+r444wVGhXCJTr5RKwHkpox2QDHN6DbqWzS7zdbjxXfpL9d0NQ80nhUlKBhXxjEYA6Iu3Nj2Udc64+kPi2o4nusDxQPT2SlZaeipIQSsKbkbnGZGxkk9yTuAMXLgey0dstM/GHFxFPQ0kaoIkHLnbK08XfJ6sevmOfM2wdTYbjlj/mfyhDfT8D/AD949azbeBbF/wCJr+UrLpWktb6RutXKMDnIHSJDjHYkDGyjNRo0u3El9qI1qHrb5dWzcqxPN9XRjtBH/Eehx06fe01xPV3Piy8vca1fDutwVfqNKgCpQUq/CxOMqMDygY7n0zrXA9jg4OsCwpC0d5nUmVmOWgDDds/9Rgf+0bdSdHabT3NZ+HT6j2fiC3WVInmt0OhO4aF+GLUvD9hpaXn5AtdVPJ5fXwUAGWUHdm25m9gNV3iy4z2e2tV191IdgRFBTxBA3zLZOB3xjR68XGltVvkrKpuVIxsAd3PYD3Oscr62o4nujXS4LJJRJIIoKePOaiT7MSe3cnsN+pGvQ27NDUNPSefc/H3MR1B9Y5ut6/zidUtVXV9SLlLDDJPUsfqkci5MmPilkZskRr88HGOgOp/C/DcN9lasmqFjs9vzPUV1Qp5ZyD5pWHZB8KKOpPqTqTYLHV8SXeS1wlGBwtzqkPJHhR/5eM9FiQDzH279yfE93hrEpLFw9Gr2yN80q8vKK6Vcg1Mg7QJghFPXBJyc48rq7hadv+kT0OnrNQ3HuM3avrOIrrR2+1QSUsUSgUFIDzGlVtjUSY+Kok2wPsjGO2pPE9TRcM23/wAJ2RRLXt+5rqiI5ZmPWmRh3Oxkb/t6DBk11RFwBZ2o6aZn4lrF8SoqCMyUiuPi/wDwzgnlH2VOdicjzgqxRWmiXiK+QLJUy8y0VHK+AcbtzHqEUHMj/JRucDAAscCbHAGTJHDNrh4Ttf7YuBp2u9TH4sfiJmOniBwJWXuoIwifbffdQSTvB9kNe/8A4jvcc31ZHb6rBKxLyuxyzMT1dsgu3YYUeix+G7ZLxTcpLzdZZWtkUolaRl5WqpceVgvQADaNOiKM/wCbv6TeM0s1KtJRqqVRQRwInw06dv8Au77+pJ0w0unUjc30D/8AqPx+UB1FxBCr9R/b7yP9I3FkzTtZ7aweumASVozgRLjHIvpsN/Qfjih2qja4Sx0tKDPA0i4CjJq5Adj/APg1PQfaPmP2QIlKnjSPSmXx5JW5aqRGyZW7wofuj7bd+g2yWudRWHhERWyig+s8V10YCooIFDGRt06OR+Kr0wSOW2r1JY7R3/AnNPpwBk//AGZJr2ltCjhixAVPENeOSrljGRApODGv8mx8R8o2Dc0xKN7HBBwvw6y1N6uHnrak4fynqxJ25cgkZ+MjJ8ijnFVMVZwvSx2i2AVnE90PLWSgEvChBUqnL0PRTjoMou/Py2SjtD09JLw9RyvXXa4j/wCla4vhlUjeMN28oHMegAAxgAMsIyMDqGDC8nuTuH7fTRW8WOySrPHJl62tZj/xBB8zFvi8MHv1c+5HLW+N+J28OosVunSG3wNmonTdpBspLEbb7KEUdggOM5k8WXqCxWw8K2GaMMq/8fWDyjCg5z90AE/LJ+0xxU+GbPJfKpSAIKGnBleSfyhVA800h7YBOB9kHA8zMSbSgpG9+/8AOP8AmBu5c7V6kew8MRXSomu1URbrfTDxJpJWz4cXfmbrzN6DqcKO51Z5mpqmipL3c7fIlnp2MfDtlziSsm6GaTH4czdAMIPZ2WWgrbclxqo54uELfMFo6bHJNeKoDZiPl0HRF36ncxbqevW4fti5mAcQzQg08XwwWelAyDvspC7jO4+I5JXQrvzk9wpEOOYrVQ1NtqqutudVHLxHUR+LcK2QDwrZDjARQBswBACj4dlHmJxUOJb2lWIKSgp2FCjFqOmlHmqHyQ1TP69MAe3KNg51G4v4qppKiO1UazPaVbxC7ZVq+cHHPIeoQEnAG43HxMSJ9ht09I0NS8CVF5rl8WnjnUeHTxAH/iJh0WJQPKnQ8v3VOequz1Hud5fhepJs1BPbHPJKn7cnj+tS1NTgpQQ4yambIxzYxyJ8mxjkBt/BFjoayOnq6mmlezwymWgoZ2xPdKjfNVPncL8WM7KM9SW5ofCvD8VyjFZO9RVWEVBkdpTyz3ysGT4jZ38JTkgHAABY7/AS4hvMkVfNZ7AaeS916hquoUYhpIQAM9PKigAAfaIG3RRk7k8DuXwEXAnHH9fceILtNw3b6yKWWXkevqY4zy00anZc74ALKERQGJOSSWAIKnoqS22+W124VE8M07xSOrgTV8v2okYbKoB/eybhQSoJ5m55zrTWuhaz21qlozNyVlQn/ma2pOf3SH/qnJyekSk9XZsCrzcqW1Wxq6rWnl5k+rwwRNiOdVJxTw43FMhzzuN5WyAcczGVpmXA2+pjGb1daOyW767UCCsqalAsUaJyx1KrnlVV+zSIQcL/AM1gScgEiBwrZqisrG4m4if6zVz4mhjmQuAGPKsrqOoJAEcY3kYdAqnEbhu11d6rJOKOJAkzyDnggmXEbKCFEjAbiFfKqqMGRsIowPLaL/corLSGsrPFeZndYoC4WaWbGHyy7K/LhXddoUxFHhixBA44EqFydzdTu/XmnstEZ6lXnqpTIsFP4uXlc7SZceuMSyjsPBjwAxA7hHh+4yXKS+3oma7zkGFThRTAKMbYwrKpXAxyxIVOC7Ip74RsFVPXC93kCW4zKogh5Qq08YXKgA7LyruoOyL52zlFc7dbpN9dawWBy1XsK+tTKimQNuiE5IfLEjOWDMWPNKw5KsdvAlwM+oyQKZ6upmtdvqGhggIW4165HhkZxDENz4nnI7lOY55pXJ1Mr6u32e0wkUqxUcY8KioogMzHHQdc5BbmbcYJ3ILeMqye3WWxxloBBQQnw6Oji+Kd99h6k78zemRnHOXj2ihmFRJxBxBLHFVhOYZYiOijz0Hvt165Bx5gWjzA+ZcHn7yVZY6uJau8XyWCCqdczzEnkpIQciJc9N+vct6sMp7RUpv7pcK+P6tZab97S0s2FEmBvPN2xg7DoB88M3QUM/ElRHX1iCk4epgZKenlwpqCB/jy9AEAGy9AMdvKSVOIL6Gra1/q/DdN+8Xxjy/XSv8AzHz0hXqF+0dznWgWVnSqb4jXCtK0nDFNiVRMSprWU58SQHpEOqp9o+Y9hohBy1kUV8vsc0Vrhdf2dbymXqJPsSMndz9hD0HmPTIbfkuEcd8vYkprHA6fs+3mPMlZKT+7dk6kn7Ef/c3TYtTrWm5pPLDFUcQTofqdMzF4bdETgu5HUk7EjdiOVcKCRJJ7Atxe4RT1MMUl/qIz9WpSxeG3QHYux7k7ZYYLkcq4UEjlxTvRyRxyT1Funm5ampB/4m9VGCPCjxjEeAQSMLyqQCEDE8RrS/U5I45amuo6iXFRUKR9YvVRgjwo8YAiABBIwvKpAIQMSUt1BU19c3NIFlRfAqKin2jpUyP+Fpth5thzyddhjBCiPNmAlgMzu10dXW1jMJUjmjXwJqmD/DpE2/4Wm/i2HPIMHIA2wojNiOBIUggRIKCBCvMrYBA+JVPZfvP33A3OdcRLTBRT0oSnoIE5PI3KhVeqp6L95+52GugrzynlUoqkYXGOXAwNvskbYXomckFyMYHLGaYwJyQ0kpMcfhhcALgKQF+HboMZ2XomcnLEDRGgpFjTnxgDpv7n3z1yfXJJJLZI5pYApAGyr8/9+v6nc5OpVXPFSwGWZykadWxvnsFHc/y1YAngSucDJnk0sNLA8szhETHMcZPTYAd226dvkBqnXe5S183Tw4UP7uMHOPc+p99K73Ca4T8zeSJdo4wdlH9Se51B0+0WiFQ3v3/ETarVGw7V6i0tLSAzpnmAxaWkRjSxtnUzJFpaQGddAbb6rJOQM6RGNdKMZ17qSTgDOveXXWNLUknGN8a95ddaWpJOQuutLS1JItLS0tSSLS0tLUki0tLS1JItLS0tSSLS0tLUki0tLS1JItLSAzr3lOpJPNIa95Tr1RjUknJGNIDOu8aWNSSca6Ua9wPTS1J0DM8I20gMDXulqSYi0tLS1JMRaWlpaksItLS0tScxPCNtc43xrvS1JzE5wcddZn9JvDlRC815pnjmpZZAZ4HjACE7ZB6bnuRse41p2mK+khraKaknUmKZCjhSQSD6EbjVkcociVdAwwZ88yPIyGCmmWGZSHSGpHMvy3zlT0weYH72n66dKegpKYFLW0komSSM5EE/TIwdgSBuNjtkb51L464fl4du/wBWDGpo5MyU5mIBIPXDDADDvjlJ2650FpPDld15450bCT01Uqg+xBIwGG2/lJG2t7QMbh7zKknO08Yll4quMsdqp6O710c1vqFxUGGNWeFiMcwBGcdDydgQR0OpLtDScOxUtHWzVtyjQjwyrDx4SN8klhIhG2dsbbdSQ1nq3qLrJb1q4qOaJfOkxYiSMHrzYJypOdwcZYkkHIZu1e0/EdPQtVw2+rpnDUtTSxKI5COvlXC5I7jysMHGd9LmGciFZxzLLNDRUVkeoprO1PHUMDOs7OVjc4ys0bZz1I5gO4JzvgLwrHWU001gvFGDQyMWo5mUSKhI+EnO/sdtwM45jovxBdIZaKC319w+tWyXys0A51hOSPLzDKjchkPTynuTp6WgpKOw/Uqavr3uFIniUXKCJuXrlJEBEqDIbBGQGPXIOsEuK8HuaMm4AiAbRRxzXGot8FWlBX06GQR+MWhkzg5XPmA5d8HpvuOXGp63CotgZrnFUU08Xk8eB1eJjnBB/Ed9DrHJb7vTC4tDW0N5oC3jLTyfH5uYkKfUk7dMnp5tQb/WVEVULvZueaAnErx5CyJg8vOBnlONiGGN9HU6hh9RzBXpB5UYl0hutBXwc1TTwVeBsyjDH/ft+Wp0EdQ0Ba1XJQGAzSzL5CfTlPT8NVdvqFLFT3KpoBGsirI4ifkGG3BKqe3tg+2nUlu6KtTD4Vwo2chJI/iGMZBG2CCf1HrrZrKrfqmQSxOYY/aX7Lq/rV0s5iIbPOpMsR/DOR8gf00xxhxLcr/AqW8oaKMZYUr85PzUYYenbvuo03T3lZKnH1uCbkHI0MxyQTucH1/A69qbZZLhKJgJLdUA+WaJuUfgRt/LVhpkcDEzFmM54k/6P+CzdEWrrUCUysMIcNkjpt3PzGB2A6mZx/XcGWqja3UVrppaxVPK8aAchz15vXPVug6bnbVazxJby70UzXOlYFC6uY3Ze4BG5H551XJ0pKqoKJXS0FUzZkWsXzemzj8cZwQNhy75Gs0W5+OpulxRPvBrV19iqWpqXkuS8xIpZk5whOxGW8y7Z756Z5emjNnlp4qo1NwsNXRy4BLITLGuPnkjHTGdu2Bo9YLfbLbTMZJFhVR5nYZLewPT8P8A50MvPEU1QJaehKU9CFx4gO7L05skbA/ex/lBOSS2X8PgIcmCK/n5LDAlhn4rpha/B4TVZ5XX99Lzjxum45R5lX2Xc+o70WtlrKqvdZDJU1z4Vy4+AA7AjpgdkHlH8R30PhsD3aoIt4elGSTUDOc53wCdug783qe2joh4qsMIlesp7pAhCgzDLD2Gd/yJ1yuoht9omjOCu2ox+i4RoHUz3SBKmZty7k5H4jf/AH+Gg19tVvpZvDs9TOkhXLDxPIg+9nbAHqT377adk4viro/qtZ41A+eXxI4/ERjn02OfbfHX009RUjVvILVNTVId8mdZQQp9SDuW9yNvsgd7u1dnCcflKKr1j1c/nAy13ENG6xzRJdmO0cbx88uDsMHZ123zsTnpo5aZ6E1UE16stfQtyjlibPJy56JkbD9NabwXwdR2yMT1AFRUNuzNuT8/7fnnUzjPi610NBJQqsNbOfIFeISrzZ6Kp+Jh+Q75PlIFlz1ttTmFpUrrluJN4c4+4SpbZ9WtyGOVQCsBI85Jxkvk/ievoD01SuNeO79eJHoYGnpIHyCyr4buvQqmf8NPVz5myexCjPrpbI7jM1UVWmw3KAnmA9F9WbO+FwB06DAMcK8LcaXGqSntkxnpF/xRUNzqAfvc23XsM6Haiqs+Zcv+81Wx2XZWf9o/YbBU3R1hpowyA4EgTyrnsgOd9vjOSfftolu+jC1Q0DmamBqn8xwep/i9c++fx0/Yabi3h5Sai0oUA8zwwiZAO/w8rgfJW15fPpFpTzWxpKWmrimTGs5TxCQCq5cApkHO4zjGOuRhbqRecV4Im9NPkjLcRunh4bsFum8fmoyh8xp53gGd8c6L5JDsfKVJPyyRnnE3Etyaoaos7YpuXkellooleePuWEYC4JGd8f8AdgHXN8FyqJnuF0QnGSrKvNDED2Ub8x26nvueY5JH2+irLzIYqZHipy3mcgszn3+8fbtt+JtXhoHrYnMFs1zZ2qOJBg4qt8kyUtbZjFMBjxaKQqqZznCtt+I+WTtq18I2e1VU/j0VV9cqH3jiqGVJfwQkEnfqB8tXzg/6NaSkoxVXWFFAHN4b/ET6se3bYat8FRwbbrRUQ3ajpo1jOTBMoMWD0zkEDONgBk9gd9DajxF6Dis7hN6tGto3OMSsWWht9PU8lzn+pShclKiNkYj+EEbn2GTqBxz9IMdFSvYbDGpK5EjMAUXrkuejEfd3Ud+fcLWuMuLKa5wG12RK61WoSHDUs7IJAcZCQ55FA5QQAc/eJzgZ5PxFxBQgx1YWvwQqRTxrKdvtMw6fLc7fnxEe8h9SpA+JwulYKUMM/MKVdRJLPJW1VRJLLIfPO5Jdz0wud/TfrsAOg1I4b4fuXEtUtLR05EDHGOXIPrn7x/T1zuNcWOejvNTG9dYqinlI5maLxHQD3UAkD5D562/gLiKz0FItHQ2xJn5fOaKdJJT84jh1HtjRl+uSuvFQz9oJRomezLn9ZI4G+i6xWKATVFDT1FUy4JZAyr/c++pHEdl4It8n1282+20caf8APmXllcjtEQQ+d+2oXF/0ii304qKC11VbMrZFMY3Tw8ff7k+w1iHF1+vnFt1NfxBMyquVipgpVIlP2VXfJP457luyqjQXap97cA/EZ3aurTJgDOJdePuJrbDT/VuGLpdpX2ZEkqRWwx4PT98WDEjbyHlU9C56Zi19v9FOY1q1romwwaopxyAAb8zHv1Gf/jUioeGBMNlVP2c5Lbfa/t/Maes1mr79LzvzQUQOeY9/kO/8vn102r8NWjpjmK28Qe88qMSDBxbRVVQ8FRYkcNk+NSuYsnbfB66sfCsvCkVQtRE5Ez/B9acZU+2cZPvgnVw4c4epaRBHRQ+Ft5pASGb5nqdWm28J2+uYwfsylncjLsYlXA7ksADj5nWNuotpzk5E3qqWwcDEhWPwJlaTwKh+Uc2ViJUD120Qut5tFssjV5eSum3EdJBG3NnHV8gco1bOELB9HtgaSSPwqOZ0DGaKd4g2D1TBBK5+0dj2zvrFfpbvVfUXypSz3aphgikLUy4LE5bzZbPMx75bPoMaVprW1FnCnEYmlaUyTzKxxNxTxNxUwguddUQW+NsxUqkoi/JR0+Z39MZOh9NEsSLHToAvRWVe3t7f7OdcR8XXePme5R0lTTqMD63TAMzdwAu5z7nb1J09R8R2a4oy3OyzUwzh3p5Ty/io6j9NOatTRWNoGDFNumtt5LcRR+JK4p6KPxZGJwwHMAfb7x9zsPwxrQOAfo4qK+QVdWoK5y8jjKg//dH9B7dNd8Apw7HUK1NGlepAJiWdTKfTIXLfhga1ym4gpBTBY6KppuXCYeE8ifl/YaD1euIGK+SYXo9Io74Ek2Ww261UJp6WmBXl82Ru+P0/DU23W+F5fElpIIk7RLGv5sf7aiUt1tUMT1BuKTsxAYDd2OcBVTr1xsBrPePvpGCNLQ0ARznlaLmzEpz0kZT+8b/01PL15i3w688aXtcgDkxwWRFyepsUrcJQWaepeC2MFUjmaJW5j/Dnrr5s+k69i83MGmae3UeBFIsE7sJVGcFxkc+AThRgD8CNCau/XGpMklXWTVEz4HnfoB9nA2AGfhXAGfTQeqnHO8ssqt2LN0HsPXfsNs9d9NNN4Tj1XGLdT4pn01CBvrl9oP3VPX17NITyBHPKP5A/yHvqdFxfxFCop1ljrps4kTwAy+mAepP+9+upFvoa28SvFSRMqn45G6kb9SOg9hj8O95sHDNHbY0ZVEk4xhyvQ+3pot9Oyj0NiYpcD9Q5lTp71FIw/bNgpzKduZIvMv5HP6atlgu1rmkipTU09ECQq+MDGo/FgNXK2W+rrCqOZZlPRJB4o/JsjV74e4St0LrLPRwCXGOVIwoHzAwM6Ct11tOQ3MIp04s6EqlvsNdIqy0KUVwRsENT1ascfLOrJR1MFiQPWWW5wNjzztDzgeu46DV7h4esgp1JtdG5C7HwVz+ess+lC7Uluo57Xamq4J3YMFhnZooyD90k5/Ll9jpe2qe/gjMP/CrUu7MI33jSjiglagM5CKMusP7xiegjVtvmzeUejdNZ1V8d32StVmEtFAH5hGpJZj/Ex3dtt2Ow7AazniO/3qGoatqL1XVU8mVaRnJCkdD13+Q2/loVbuML9CpkqaqMU4JHNLGCZPltv+e3ro3S6anH9Qf3gN2ofGFMvN540qJK5zJUzlgTtGvPjfuSDpaox+kKUswmttJIwPVIs5H56Wmq2aZRjAi5l1JOQxmdTRhxkdf56E19E6uKimYxzIcgjY50a1zIgcEHr669FqtJXqU2uJTT6h6TkGN2G8+M3gTKI6oHJTYCQ92XOwb1B2Pf2s1FUryeU+Q52Axy49M7jHdTuPUjB1SLhQCbJHkkHRgdSrJepo5xTVzBJdgJTkLJjoGI3B9GG4/PPkratR4bbn/T8x6pq19e1u5eVAxzKQQdwQeukd/nqHSTcw8udjhoyBnJ6fIn22btg+XUyJ1I50IIPfXoNHrE1C8Hmec1mjbTHBHE9A7jS16FKtzA9e2uht00bBNs4BI6d+2uiDrpBjOvB19tSTaYkIAI0j1+ekuQpB7769XrjUnc4E8AJ3GMaRz+OvR5TjOw10QN/wBNSTjGY0wzvjfTEqEnttqVynG3XXDJvzZ1YGUbJHEGTQk52zqFNCRlSAR66OvFkk9dRJYAQQDtrZLPYyqhllZu1ujqo8MOWQfA+mbbXusjW+5qrM3lBcbS59f4vfv899G54yCV6jQ240EdVGY5AM48remk/ivhK6geZX9Uc+H+Imn0NyIf4J4UivPEsNIkipRKPGKOTyqy/E8noqgEn5Y2Ojv0jcRxXhxwpw9MYrDQFmnqH8v1hxs80nt2A7DCjvrPLXc57fULS1rkEbJLnAI9Cfl3/Pti68D2KK93emtVOYYYWbnkSR8eIykkBj2RAM4+Z3JGvIqoqciwcj2/2no2O9QydQlwFwtDdOa5V4+pWWgjMviTD/DTvM3/AKjEbDtgDou8DiviE8RVNNULTyGyUsjQWG2NnNTJneV8bkZOSTuc46k4J/SBxHbrlDJYbXO6cJWqQfW54xyvdKnoFUem2AOgA9Bua+jThYMG4q4kp0AA8Kmo1JCoo6U6egGcu3XfHUtphUjIeBmxv2/6EBdgcknCj/P7mEPo74aWwUP/AIiuxWqvFafFi5wDzHO0hH3FxhR0JGegGitfVJDBLWVc3KqgySyOfc5J9TqTW1MlTUS1VVIpY7luiqB29AANvkNZDx5xHNxBcf2NapVSjiy0spOFAHWRj2AHT+5GvRVonhtOBzY3+f2iJy3iFvwiwdxVepeKbnNzyNS2ij3lcb8ozgAersdsfh0B1JtNvr6+4w2q3wNDXPGIljj8xt0D9EHrPJ1J6jPb7MSggYGjprdTnnOXt8Uifg1ZMP0RT2x75udympeB7NNY6OpdbzNHz3WtBzLSrJ1jU96mUf8AsX3ydeb1epLEoDknsx7ptOEUEjAHQjHEtbR2a0HhCxIJKdWEFwkp2/8AOSg/+UiYbmNTvI/2jt0ABkUrQ8EWcXu4+DUcSV6B6WJgOSFBsJWXtEmMIv2mHcAZj2amoeGLD/4w4ipkYhTBa7Zn4sb8n+UdZH7k46kgDuGaCt4yvVXxLxDV/wDAxsJqmoZDytvhQq/dGypGOpwBt0AGG4H6QvnsybwZZTVtLxZxK1TLTiXmjQn99UzPuAM9ZH3OeiLlj7m6Cnq+NLvNJKyJbKZB9akhUtEI0J5YIh1ManO3WR8k/wAMC60Nw4z4rpbXRF6a10cbRvTqQVpVJBbmcfFIRgyOBsTyjYDV4v1ytHCfDqUlFGop4vLEgHK1TIB8R9ANtuwIHU7m6XTbs54A7P8AsIHqLtgGOSeh/vBnF/Fj2aghp6a3pRQhSKWGWQNJjvIyqcZJG5J7YxgbZZcKVrlXNDUGWapZ+arkdubw8/8AL9PEOcn7owOvSXW1VfW3Q1Mzh7lUASKWUFaaM9HI6Z+4P+47AZs9moLfwxY0vd0iDjJFDSPlmqJCcc7DOSObPux22w3Lvq9RhfLUfkPgfMxopGS5P5yNaKGn4ItyXKohFTeKkAW2m2JiU/C3Ken8IO32jsAGnwQHhqL9qXDnrOLLgcwxhjzU4O436g+YHJ3APMcuyYcpw9qjbjLiUCpvVYc0FKwDGPOcMR0JODgYweUnHImCYsdDNaZv27dv+J4nrhzU0Jy31VWOQx7liWyO5Lcx8zAhXwBtHXzGGT9R7ntktFRYGKgfW+KrljxGC5+qK2wRR0DY2x2GR2Y684nvEfC1vNjs8iz3eqGaqoVs+GOuAfQbnJxnBY7BcPcR3deD7e8EDGr4jrlPOAPEaIHYjbqTjB9cBR5VOcnsf7T4guIoI6eWoq6yUmd88xmUtsueyZG+/mPsNy6qxWN9nHx/nyYIxLsVX9f8+IUsdrqL7cEpKQmWEsHaRtvGI38Rieka7kZ/zH7IWyM9rqrbLCal6fg6glX67WIn7y7VAPljjHdAc8q992b25NNBNFU2Oir1p7DRqDxDd0z++YH/AMvGe6Z223dvYaL2q2x3KagvldbWht1N+54es2MmQk7yyDuzEZJ74wPKp1lbbk5M2rqC/eKk+t1N2oLpVW0CumjxY7WQPBt9ON/FcnYsfi367sfKBkNxXfYpIZaKkmaoo2mxVVKt+8uVQPNyKT0jXIOfkxySi6kcacQKxrKVKzxMti51kRB8VjuKaE9CNtz0bBJ8q7jLHbufwLtcqNqhpW+r222xE5nYHPhqeoQEgySdST95gBStQo3t37CXdi52LO7LaJWenrq2kjr7lW+S3UOCEcLkczDPlp499/tHIznnbVw4asKXdamSerlntHjqbpcV/wAW8VG3LBD/AOkCAABscZ2ULgNEnjmqEtS1SJnWC5VdKAGrHGy0FIBkCJQMMRsQPT/ElcX8S1FPRQ8P03hGr5DBHTUrcsVOp2aFCN8dpJM5Pwg/ETDkt3L+mtcTrjjjznm/Z9jNOXUGmjELZSNQcGNCPsAjzN1kYYHlXI5t6fsWhlo4JZzVyOj3KsReadpWGUijHeY/YXpGPOcHHhh+HuHVsUxraiqU3IIpknEXOtGh2RlX7Uz9I09MMQBjmLXCeislDJW1avTJAXiWNZeaRHbBeFH+1UPsZpvsDCjzcoXgUHqdQf6mke6V1HareK2uVEiRTTJTQPjb7VLC3XqR403VieQemg3D9qqeIrgeJOIljFPy5pqdvJEY02PT4IEyASN2OFXJOdMWO3T8UXFb7e440t0QKUlID4cZRNyin7EKA5d9+uN2bLW+5XOC10LXGqeRQroscaJ4cjOB5ERD8LgHyIdoVJkfMjrrbheB3K8udzcCd327U1mo2rqkymRZOWOMYjmlmC4CgDZHC7beWnQ4H7x8gPwpaKy63CPiC8QLJVTBUoqQIOSnQAsgCNsAACyqdsAySZGzu8OWWe6VsV9vkKNMQq0NEq8yQoeYqArdRsxAY+ch3c8qsTbbtLcKWlnoLF4b3MqPrlaz+SiRiGwGYeZzjnz1PLzsAqxqudjBRNFXdyYOvNXUxVT2CzTB7ow5q+uVjy0iZLYDHctk82Tvnzt5+QRyaKC18NWTmkV1pkOAAP3tVLvsBnrs3yGR15yFRUVu4YsL1FXJIlMj+d9/Gq5t/KM75yD3yDk55gzQu2eimqqv9v3vwqeVEzTwE4ioIvXsObAG+3QdOVeSoGZoOB955aLbXVNxk4h4geGGaJMwQk4ioIRuSenn8u52O22CMxSKKnHEcq1dUjRWCmYyQxSeU1ZXGZpPRBgYGwAA22VRzDTScWSI8niU/D0D86Rv5Gr2Xq8n3YgQDjvgegVSFLHHxS7JGCnD0LYZ/hNwKnt3ECkf9xG2eurASntxO2CcTQtNUzCk4Vp/3jF/3f1/k+02fhgXGw+0dznpqdC1Pcoku1zilhskDL9Romj/AHlbJn92zJ13PwRn/Mw6YL3Cnt4tyz3aLNFEy+FTKmfGcbIoQfEc45U6dCemdcxrXm4w1FTBC18lQ/VKMvzRW+InDO5HVj0Zhux8i7ZOoDkTn2ieGqa7Q1dVTJV8QSxt9Soy3NBbYmyGkfHVj0LdWPkXC8x16ngNSSKss9TQ1E3LUTJ/5i9T7jwkwRiIAHJGFwpAIQOTKq6SkpLW8LzVVQlTMFqXjx9YusuD+5XHRdjnGAqqRkKGOvKWOUzGWZsVJH1Vnpf+UOv1Ol6b+X95Jtjl7cqiOhaXVTH7fTT1NaXmlRZ//LSS03w067H6pTdN9vPIAD5e3KojLoy8goqREWkjBVVj8icoO6gjcIPtP3Oy6ct0CUFPGFjgNQYuSOKM4ip4tsqp+6NuZurHA9AH4xyKY0LFzjxpSOViRsAAPhAyBj7Oe7nbHOZqMCR6andnGebZhklQpBHTA+zy/ZXome7kYLU0HKipGvlH+/6n16nqck+0tOiKAAAB0GOn4fj+vfJJ9raunpKZnkYhBscdWP3R7+p7aigscASMwUZM7qKiCipWmkfljBwT3Y/dHqf5foabda+W4T88gCxrtHGOij+/qdK6V81fUeJJ5UUYjjB2Qe39++omn+i0QpG5+4j1WqNvpXqeHPbSI9Ne6WmECnPKdegY17pakk8wNe40tLUki6aWlpakkWlpaWpJFpaXXSwfTUki0tLB9NdADG+pJOdLXuN9e4GpJOdLXWBpYGpJOQM6QG+NdgAaWBqSTjG+NLXeBnOvMDUncTwAnXoG2+vRtpakmJ5gemlgemvdLUkxPMD00sD017pakmIsDS0tLXMzoEWlpa9wfTUzOzzS17g+mko9dTMk80tegb769wNczJOdegE69wNe6mZJzynS5TrrS1ySc8p14RjXeljUknGkBnXWBr0ADUknGlrogYJ1zroMkWkemvGZVUs7BVAySegHrrMOOfpAeYz2rhyaPxQeUzDPM47iPsTn8fTOta6zYcCY22rWMme/TXebC1rNBNRCuuAYrFIMr4JB38w3/D5e2sbpa6OZhGpaVk28NziZR6KftDrtuP4e+nnqZhJIykuXP71X8wc/xA9T79R2I0NuFBFVYamXklJ/wWbdj/A3f5Hf05tF21GuvC8wKq4Wtk8Sy8P1BoqmOtgSjucUBLRQ1GVkj9UypDFevQnHcY0c4ao6a/W6pKS0BgaR2pKeoflmppRuY1bbOdjgMCSQQMZGszWtmJenrlmO+8yHlmjIOxP3iD679sjVttV5h/YVTSVMdJWxzlFmrI4yJoyOjsAQcjJyGz1JU+qa4kepe42qweDC3CFTLJxCtTSV6whpBFWwzSCM+iyBtlJHUHbOMHudWjiB5rrcltjV8dHcaFy0EtLEQJsEnICNgOAx2A8wcHqdgNfBLabb+0Kw0lb4iiKaeHHO6ncMy4GSR0b7Xrvg+8MNcKNmlf8AZ10t0EXjwPNglIydsZxIMZGCpyBsDoewiwblmqejgwlxVWG3063hWpquOXMcngOshkOBzEN5WVh8QVgenfAJD2mCSlnluVtrxWUdSeYxgFGDHuFzjmJBJA6knYZ15f56y43OS+WWmjanYrFXUBYSMD6EEDnGxKtueXHoNeH6hbpJbXNAkEdYqlEafMLOQG5SdyuVORg4zjpjW1R3Ln3mVn1faRjWUst2FJWTyQwzZWKaKPPKT1jkjA5Tufug79eujFipai3wvQQzxVFNJltpCsqso2dQTjboQvUHucai0lDU3Vmt/EFEk3gxEU9X4aq7Rpn4nX4mwO+c/loeqyuj2+ikZ56U5jViBNERupHZ1wQNiCR26av9fff7yuSJxNd6aO7LBeGWppHYAVIXMseD94dSD15gcjv00dmoaugdjQXFalSwCI7BWcHcYbo2RuPUai0tNTXy0PHd6KFbpTk5YP4c0idT1+IqR6Nsd8Y3YppI/qC2yl56tYQ0ZhcBahFG4CgnD8pyRg7emNhpXc2CVOcSj0j3HcKUdzFtneBhLTMPMxBJTBOM4boMkeh30UnrrdX0ma6jgq0Vc8ynzD+o/A6GcByyXWWssN2ovHYoTDLISORwfRtwGAxjqDuBsdeT/s61QS08SLSVMm0bTlikZX41PbvjfBGOu+iafEAcgzJ9KQM5nFJYqpo3mstzWNGOWp+fnjwfslW/qM6H3CmKSL+3bPNCA3N9YpCRGx6ZK9M+4OcbanwVVx8RWqKRJEAHJLC2S2cbqynJ3ONiflorBeHNK3hTJVeXZJRlj7ZHX5EDRSNW3IPMHIYcEcSJarhQrA0NAFmMa5EaeR8f5Tvj5aBXetqKyRzXAwxLsY2yvXpzY3HryDzHuRsdTZbVRVsglkzT1BOeUryb/wAI6A/LXklDdYgscixXOmTpHUrzMv8Alb4gfxOo7lz6up1Kggwsg2WwV3FExp4IOSkAw8jqN16fJV6+UbfM51cP/wAl3D1BQF6asqqKWMZeZZTy/ke3451HsXGhs6rSSwikhzlknXKD5OBn/wB2ovE15vN1dZuUw0p3jenfnXBz0boNurNj8iV0LdWXbCf9y9J2Kd8BVt8v9lqZKairWuNMAVk+JCRnABwfL+O/45GmILraauYPUiot9RNsFl8ylOgGRhkT2wMj20S4ft8lxqUp7eiyMDtIoykZ6eTPxN/Efw9NbHwd9HdtpYFmuNJFUTE5IkHMc+rHudCai46Ybs5P3m9NQu4xxKLwPw3QXGuSW53SlihAHJytgOv3Y+wH6n37bTCtrsVvjjjRIof+VFHu0h9vU7ddVLiu1cHWWCSZqKOlcf4ktPKYlX05gMrI2xwhViflkjIr5xLWwvMlup3qLbMoQ0ksbJLKh3LZjPKFLAbbDoMHGSua59Z7ED9oZWi6f7maBx/9JCyq9BZfCd02adjzwQH+HtK/TfcdMAnDayDiJIqxXe4yzTVMh5udyGnYnqWc5IB+6Ov46lU1zsla/gU9TJa6odPGHiQKe4VxjB67nJ31ZeHOFBBOk05SoqJD5ZC2FGe4z/PTXSabSInpIJ+Yu1FupdueviVThvhviOKYVNLdpbehH7uBFJUegKf13Otd4Fs3FNKVqainpZqk58KSnZAxGN8RygAn351OrFYuHqO1xx1NwUSnmAwNxnqAMdT7DVV484/RpZaGwLG+37yTIaNB7ncPj0+Afx9VB1FjWP5Wmzz/AGhlSitPMvxxDfFPHqWYRQ3qelhmlUNEXikiKg5AYhgybkEcwLLscA6zO9m73ypNbNJBWRZJjSmkLxp6k78zE9yck9CcAYFV8tRWRyy3CuqZvGBDyTEu7k/cVs4+fX5Y3Z4U4Cvd3rI0ss09HECG51PnJ7szfaPzwNaU0NoxvsUEzN711g2qSBOU+u1VT9ToqeQzts8jrgqN+mR5R/vudaL9Hf0aySlaqZe/mnZdh7ID1Pv+uikPAnF1sw8tbRXaJQMlnMEn/vIYH/2j56Py3/iGz0QW6QtSwquSaqARgoOvLNCWTAGCS3Ltk65d4urr/TOD952jw4KfV1DlLw/Z6SB4I6eBhH5pJHALZ6klv941SvpU4h4eo4Vt6W+CvkMYZRPCkjDPQqXBMYONm6n7Kn4gP4l+kB75StR8Oz0AKMcRLOp5d9mAOzscZ5myBthScOM3rKa4ipeWtWaNyS8lROT17nmOc9skkk+530NpPDzqX8y04H7mb6nWChdlYyYMu8t4q6tquGuropucyJFFUuQmSSVHOTgE77kknqW7dQ3vianiMdZFFcXB8yTRArEPumTu3tud99W3hXhmsu1UlNR00zc+5A8skgPUkn/DT3PmP8Ott4P+j632aOOapihqKtFwgVcRQeyD1/iO+tdVdTphiokTPTVXX82jMwegtdvqzFV3Ph2voGI5mdY5JoOvfk5iB33Uau9lokrW5LbJS3BVG6Uc6O6/NM8w/Ea1yntdFNcFDwRM4bHOow35jvprjU8G2ulaW922grhEwDPUxBxG3UKDglpPRVy3rgb6XjxnUKdp5hw8OqOT1KTbFoo5XiuE70HhgZjeNhK59FB6nQPjT6QY6aJ7PY4UQKSHJAdAR3bO0zfP92vpIQMA/pM40ivckFPw/VXS1UKLySPJMZObl+DYseUA58qkDfLFsY1ndPxXfYHENwSluEMYHjPVwcq+2CMEn+foNFIPOO/UKQPiDOy1grSwJhuS7V81RJUS1Mk0rk88kjFvMe5PVm/2ABobW1oVyBzSzvsd8kn3x+eB+Od9cUnEvDty54qu11luIG8tI/MoHrhhsDqz8J2/h4t49BWx1cnZpWAIB3+WdOKrqCMJxFjae7OXOTBtk4YlrJFq7r8PaLHUe/oPYfjnV7s1hjkiEEdNEtOPsNErJk9+UgjP4aJWiipCQ80yLv0J2P46uVut0a0n1qeRKeiTdpCwAxoPWairbgiHaahwcwNa+CrRVukb2qil+/zRDBHy6D8ANanwrwrZbXbDDb/HpwpORHVSBVPpjOPw1lvFnG1HaGahoUZZAN4Q3JJj1kbrEp9P8Q/wdTWY/pFvHIyfW+Uco5Y4hyAb9h9kdeuSfc6QnS3ajmscRkt1Wn4buFPpgu1bDdJ6e21kCJylmeaKIMzKDheYDYHGyjck79dsgqeN7ghWK42+hrJSeUxiPD4/7dgf4eujV+uj1M0s8swZuvIWwqfM9tvx/DVZjp57lVmCjgZnYcrScuMA9h90fqffY6babRtSvDcxfbqhc3I4kz/xFwyzLDV22poXYDmMEvOPkfT5aKW6y2O5TLUwXWSoiH/KZMco9ARsP99ttT+G+BbZRgSVVPHVTZyVbmC/oQf11ZqTgDh+vnDm2PTv0DQyk/o4Y/8A2WuW6m+n6xkSCqtz6O4/Z6Okp4Vhpo0SIDGEAIHzxq1cP2aCrmCipgBG55mAI/DqdFuCfo+qLY6vTXu5U4YgNC0viIV90fmGrrcuGaY0zPNBRVJ9Gg8Mt7ZQjf8ADS2zxPfkCH06EYzI1qt9NRU/hQLgkeZ8bt89Ab/xrbrRCWWeMJkhZSM+IR1ES5859Tso7ntqhceXym4eqqmhpaGukEmAIoa4vDjuG2PMe2AMbdTrPLvxZZKu5me6Q1UdQwGZGk5lGOi4yAMfdAwNYUacXtlmmlt3kjAE2OH6WKhqaYRRLDFjCFjzOx7+mTj0AA1l3F3EE1dUycieNK5yUB2Gfvt/T+fXQj6xZqpQKXiAQmXY+KvKzD0BOMD5a5qrVXfUGW3JT1MJOyxSjB92PU/L/wCdP9JoaKjlTFOp1V1ikGB6udF5qiaWOWQHZjvGh9FHc/730HqVWpUzVn7mDHxMP3jgenoP97akXinqrYPGrKSpqJx8J8MlE+Xb8f59NVOplrbmzTVUop6YHDM/TPoB9o+3b2GjdVqk06YAyTAtLo7dQ25jtAj9VdqGGZo6OigKDqWVWJ/Fgf0x/XS1C8aOEclJSwlR1adOdm9+hA+X6nS0mNerc7gg5+0bb9Kvp3H+8i6Wl02IwdLXu4j/ACnhVWBDaHXGhSZWVhv2bRLSYcy4IB1ldSly7HGRL1WtW2RBdqus9vkFLXsTHy8qTFc8q/dYfaX2OrlSVXijn5lD8vM3MxYMvrzHqP4uo+1n4tVSspFkUhhkdj6ah0FfU2edUl55KPm5gVPmiP3lPb5a8hrNDboLPMq5X+J6KjUV6xNlnc0eJw5IweZdmUjBX567Ixv20It1fHURxvE6EsMRtGuz47AfzTt9nby6KQyrMOXYHAPXOQe4Pce+m2g8QW8YbuJtb4e2n5XkT0DHfOkM5376UanJUnbt7e2ugNyCQNM+4rBM9wDrw7HbSLY2ztpA7512W7HMQBydvljXQ8w37euvB0317n+WpOKMCejGN9cH4s+uvVJ179s75GpIROSp6ZGO+uHTCnOne51ywyMd9dBlsYkCeEMCcaGzwlMkDI9xo4U3OeuMajyxcykgYHTfWqvMeupW66jjqYSkq5B6H01Bt9bPa6haWsbmiziOU9h2B9vft8sjVgqYeTJUZHpofV0yTxNHIvMvb1B0s8R8KTVLvXho00Gvag4P0y6/Rxb7PdOIKKK51cdHSUUeaenVcKHO7Mu55pW8oXOw9SAM6zWz+PIoSMQQRKI4IF+GJB9kep7k9Sd9fMFJVVFomWCdmalz5JOvJ7fL27dve9VPF11lsrKs89ROoHKFkA5lx1JUBmJ9c4I7dcJvDdSujtYXqd/tGXiGmbV1qaT6feT/AKVOLHIazWiRpDnlnMYJDn7u3QDv6n260SzTkQR0b0DSNI/O8RbzVsuTyA+kSncjufwwZhEsFJURVtQ4RcLXtAAvKT0pIgNudvtHsMjsc2yy21LHQx8VXikie5VH7m12wDEZC/YI7Qx9ZG2ySRnJbQ+v1FrWkhvUf2m+jorWvBHAkqiH/gq2ftKplhn4qucX1lHmUclHENvrLjGyrjESdyAcYxoLwfZqZGqOLOJnqf2bTytLBzjM1TK55hvvmZ+u5PKMt6Zk2Ggl4ouNbe71Xn9mRP8AW7lXzLgTsNg3L9xfgjjHXbb0auVXcOPOJKa2Wmmlp7dTnwqSmUgmJG3LMehmf4mP2R6ADC7YD/ncNDHBipo7l9IPFD1FX4NNQQoVcc3LBSwJuYlPZFG7t1JJ7newzNPV1NJwzw0s4jVgaVGXDR5GPrD+kjDPIrE+Gm/UnHVwkpqC30/DfDsSTrIwVSoytXIrYDkd4Eb4R/zHyx2ABt1qt9HwZY6mSpn5q+QF7hVMeZkzuUB7sTjmx1OFGw3N09Bdto4PufgQO+0ImT/9mJls/BXDD0sTp4cYX6zMp3qJOoRc/ZBz8zlj2xk97udXdrmtbURrLPNlaOlb4FUEgsw+4DnP3myPvY84j4nfiC5NVyqf2fA/hUlMHwZZOuM9tsFm7DH8Oi/DNspo6Orvt6qCtFCoetqI1+LAPLBCPkMAdgCTsG0RqNQlSBK+vYfP3MHoqaxizdn9o/w7a6K2Wua/3uRnoUkLSPI2HrZupGfTpkjoCMZJXMuldJ5jxvxaFSAZFst7DAYLsCEBzyjYYHqFByWYMUUv/iZ//E3EMQoeG6Dy0NEGI8XGSoGR6HmJIzuWOSygzLBb5r1dpOMeJIzLQRnltdEUCKQNgnL1CD59zk8xZtLM5zzz7mHhQBk9CPUcjLc4OJeIovGudblrZb3AYRRjAM7jGMbDboeUKMIgGjXEFdHw1QSXO5vLNfq7PgR85EkQPViRuGOe26g4GGYkPXGsgs1L/wCLOID4lbJvQU/Q9PK2Oy4xgYxjDEfANZbdrhcrreJJ6iVzcZjgsMj6qh35V9JCD/2g5+JhjfT0DG9+v85/4gt1p+le43y1twrno0eSaplbkqGXLEZ2MK9y3Zj1+wD8WrbDQCjafh211MVNURxE327ZxHQQ480CMPtEYDEeoRe+vbdQT2NksVmaKLiGWDnqqliAlnp+XJYk7LKVycn4B/EdokItcttVQs8XCFFOBFGo5ai+VY3Db78ozkA7Ip5j5mGu22lzmXpq2jMO2qjoLhQUlQaOWl4St8gFuoWGJbnUdPFkA3PYAdhsNySo36QeLWpKqS2iqEdymXwq2piTnSghOQaeIL9sgcrEYH2AQAx0VuFbXW+Bp7lURU9z8LJSM8sVogxgRxgbiTBAz1Xm2y77VJLDR11KLpc1NDaIT5IFQGaQN8I6+aWQjAXOyr1wCzDqADub9JsSx9KyHw/SQVCrea6CeO0Ur+DRUsZ5paqU4PhxnG7HALSYwB/CqKbpbrTX3Kuq4DNFBVLEIrtVw/4Vup98UNP6Pgtzt1+LfJc6cs9suE92FPCEo7lDThWYHMdgpDvyqe9S43LdRnOxxySOM+KLbwjbaawWWNojGoKhcF4iRkSvn/mvjy52QYY7hAsdyx+80UCsYkDi26UfD7JQ2uLlrokNNTRR7GkQ9UX/ANVsgu/VcgfEQqQOHLQLUDXV0kBukkQlaSROaKihzgOy9/RI9y7eozzx+Gra1Mou1xjhaumjMsKTk+FTQ5OZpe4jBJAHWRjgdW0WnqUoopa+qqJYI4GWd5plBlR2G0zr0apdf8OL4YU8xx1PVHsJxa+d7Ryuq4LZTS11VLUUqUzklmcGeOR92OftVkg3LbiFOnmOqpb7fV8Y3CO6V8P1S1U2YKOlifkBCgsYkJ6AA80kh+EHJyxAPNupKrjG5pU1MM1NZKV/CpqZHyzscsUVm6yNgs8jfCMs2MAC71NTQW22mpleGOkgjRV8NOZOTJMaIjfEhYEoh3lcGWTyKoOn08e8sPWcnqe1s9HZ7W1xrHWKGNY1jWKPBbHmiVI26AbmKM+80uSVBDcO2yqv9fFfLvBkFcW+iALqiMxxsTl+ZuYkk80rcxJCq7KqC31PE1YlzvkLfVEJ+pULMXB5n3ZyPM7M+OZvid/KuACUt8lf9SqEt9AUmu9QnM0pVZI6KEgKZGA8pJAAA2VuVVGIlxJRm2iWADcnqSGSWOdqOlmQXEx89ZUsRIlDGwBznYNIwUEDYNyg4WKNAXJJ7da7UZJHkprbSsWJLEyzyk5JJ2ZpWK5J2IIzsVBgbmNFarTK8s8tPQQt4k88jlpqiUkEsT1aRjj5eXoQnhjrTTT3mrivN1hEMMKl7fQEjkpo8D96/YsRyn0xy58vIrZqpPJl+u+51baKrudwXiC+IlOkUf8A9H0RwEpEwPO3QZwAc4GAB0AQK/b4hxZL4gLR8PQycwzlTXup+Nj1EQI/Ej2HJ2lKeLnaJmkWwq2JGyVa4EE5GeoiBG++WOT7rbKNFkRhHDHFboIwRI5CJKqjr/DGoAxnGdsDGNXJAlc8YnklDS1tvkStCxWxUyyE8gkVe7Y6IB0HTHb0k0ddEtuNfLTijtiFUpV5P3lR2TCdRk7KnXG+3aIZILhF+0bmzrZomBggKHnrXz5GZRuVz8Efc+Y9sTZFq3r4KqelSqvcqt9QoS+Y6KM7NJIRtnszdT8CbFieBMDmcInsCVn7ShqJoUqL7Mh+p0pbMVBH0MjkfaPRmG5PkTAydTIBTWunmwZ6pp5QstVsZrjPg/u4hnZRgjbCqoOMAM2o9DLTU9HM6Sz1qTz+HNURgCW5zgEeFFjogwRkYUAHBwGbRmlpJaHlutekc9wceBHFAuVp1O4ggBwMnGWc4zy5OFVQtXaRFJMYehlggFZXzMLhUf8ADqlL8USHf6tT9ME4BaTY4GfKFXkmWmhzF4nLEqLEYlERxGsYxmKM9fDBA5n6yEAdAAFTUr1AlrqyRDlCjOGPLyZ3ijPUR5xzP1kOB0AGp6zTygRRKYx0OBykAbADHQj2+HoMuds+ZtnbPIgUzFGxLnHPJjkORsAMfDjOAB8OcDLnIm0UQ2UY5V9AANs9vx6e/uSzSJFDBzSOqRKNz0GB/TB6e/fJ5xF0vTzqYKXMcXRmzu39v9++dqNM9xwJjbqFqGWhK9XlKYGClbnlzuwOyjvv6/799VqoqJahw8rlsDAHYD0A7aa6nJ66Wn2n0qUjjuJrtS9p5i0tLS0VBotLS0tSSLS16oz10iNtSSeaWvQu2ljfGpJEAMa8APprrlGvdSSeYGvFHrr1te6kk8AA17paWpO4i0tLS1J0CLS0tLUkxFpaWlrmZ3EWlpaWpmTEWlr0DfB0sb41wmSeaWuuUaXKNTPEk50sa7AxpEZ1zMk416B669Axr3UzJPOUa8xv7a60tSSeADXulpakkWlpaWpJFpaWlqSRaWlpakkWlpaWpJFpaWlqSRaWlpakkR6aiXOvorbSvU1tTHBEi8xZ27ew1F4jv1BY6ZZKt1MkhxFFzgM53wBn8vx1iHFfFV2vNyM1TIYY4yVWlxlFHdWU9T65/TRFGna3n2g1+oFXHvCXHPHkl5nloYPrFNbG8vMjedsE+Yr3B+7t/Q0WrgeIrz8skcm8bocrJj0/scEdxqTJFHUcz0wKuBl6cnJX1Knqy/qO+euosdS8PMIcOjkeIjfA/wCA7+hG49dMQAgwvUVvudstE84mIWsy0nQTqMuP8/3x7/F7npppbbU1EyoiCcSbI0fmV/l/Y4I76m0FAtZKppmbDHeN93X8h5h/EB8wO+/cB/Rla7bYhd7nUSxVLKJFMRGIyO7ZypxvsfxJ66Xa3Wrp1594fpdIbjz2Ji7/AEe8Sz241EtsqJogm0if4yr/AA5+MY7H/tIG+qlTWWottWKuirOTw2wZ4yf3eT9odQfY7e+Nb9x59I9TdqSThi0zQTSM4SStUeF4qdPICcDfO4PuAAdVSo4Co+F6M3K+3SZbrMpNFBSMAw75YHonqD16k56prLnKFrRjPXzGSIAwCHOIWu/C92bg+3cUXG52WkjSMeZEwZ4m6llUlDnO4UZ6HBI3qfGcNOj0NDRS0NNLKnPTVdF8MrdgeTyhgQRkKCdwwBOuH+vVltjdrY1JDFJkVAhcUEzdWBUbRsdssmAeuAfMbFe7pwvQ8M0trtHCyw3updZGNW4miJOByxsTiRSBhcYOw3yNK0eykgnkZhnD8QdwlV0tqs81wvlijaGVDBVVFMQBkeZXVPgcDGQNjlTg9tVqajaur5KeupBUUNWDJSVETEMcb7NvzdzhskbjbUuqrqy5Xh0prfJQuWEdwt1XUlUlPN1VnIIOcEc7ZDZ3Oc6s1NQWq02mptohraes52aCmmXGx83IoIBV9iQDzKSuxx8Rq37Du+ZQ171wPaC0qkpuHhS0VZLLX0jFTGysrFGGVZhuGQgcpYHby+hJFy2uC9U0HEFunamqICRNFOckH4ipYblfixzZ22JAwNdm1PVTwXCllnoLlTsFML8wD/xIfi5W64OcEkHGj9ff1ttvhp6ymhqKWpiDJLEVaaEEnDrIh8wDHBRumx2OthZwGWYqmPQYHqeIKi1kY/fxFBmOVA3MuN3jJznGTuudtQ6qwy1JpL5bq0Osp8yP+7mUqeh25W2wQcbjGx3wqWlqrdU1Bq51ntM4Mx/cmWJXIyCVPmjJ/rozTXG3Gi/ZMry0yOrGCPIaB5Ccn4sFW989DvnfGrHJyBOJgDBjlZcp6CZkjcyyLGOZJIyjyIR5gO++SBn8gc4hXOhq+JbdUXK0tDNAgBkgWXklhIGFcEncdsN6EdtC4Hekuz26+0TyU2xSOZjHLT5ByY379NgCFOeurBQ0Qt1Uf2Xc4IPFI8J6lAyTJJvjnAzyuGPTG+xGdZuSnI5nVGe+J3w7dloqA8O1wWPxGb6s8tKEEL5OMsAMq2ceYAg77gDQ68LQi5pinqKOeXyrJDJlS4OOQoemMDp77dtSeIqiqslYRDiaGIczwGVJUKdcg/h0z8/TXF2ttFerTU1VmuENZ5B9Yp6uEo9Ox8uM42G4GegycEddaVW7fpPfzK2Vg+loQukFztMZWsgnqVQYkSSPzLsM7gbjr1UdQMnrqPbLrSTgrTTNE+ceFJkjPpg7j8DjVasFTxBbLqlPX+PIjZMRkYkJvkcpzuhPYEjoT7n6ytoop1nuFJSrG5CSSIvK3Nk45tiGzud8HJ9xo6q5kHrglihgce0nI1JO7JdqR1BJCvy8y49iNxpluGeRzVcPXHwSTnCnbPvjb/3A6YqZaqo/f2EwzxKf3tIJSSBvgoH82MDPU5yenTTNvu0bVHJPFNR1a/ECCrDr1x8j1220Slqn6xMsZHpMm2+63mwVAmrKNonzvUUnkJ9yPhb8cfLV3tn0o1dZbjSQmnqKnBJRWEE7DsN9h7kD5eoq01fWNCkWfHicgOUUB+X59Px1zU2bh66riNRSz42A8p+fKdj8/wBdUvor1AxL1O1XMF8R11wrawT3gmIJ/hxspEUOevIpzzsdsnfJ3YsRnTvDdkuPEVZ9VoKeTwnILsTu38Tn09unr6a6mtnENvj5IZY7rRj/AJNSviAD5Mc/k2B6aLcLca1FiLpTpLbiMF4Gj8aFsfPDp+g1GRq6tqDH8TgQO+9jmanwj9Htis9Jmpo4KyqZeVpHjBCj0Udv99BqPebbwfaKSaoMbWmIdfBkAQse7wsGjYkDYchY49NwIq/pIqzbTW09A9VJy4VqKQPH/XHuxDHpgd1ym8Xivvta1TXSiRlLcsWSIoAeuxO5ON8kk48xJA0gq8Pv1FpZuPvGVmsr09fAyfiTuLeNHgadaGCKexMPCMLCWCaRTuSoVmXGQAQu2OXI0Ipayw1kqQRzPbqtgCtJV7qGPqy756Hzb6NcM2Gsu86x0KSsXAzOBh3H8HZV/iP4eutd4Z+jLh6hpQK63U1XMwPMCuUXPX/MfVjk76Iuv/AcVNn84PVWdWM2LiZzwPwdBdLqDdrnSoBjdnA5xnooP8vzztrdLfbqGy0S0tHCqrjZUGWc+pP+xqm1nAXDlL4j22smtUUakyFZF+rxjv5JAUHvgA++seun0l1/D90qaS1XM3G1AMjzxh6bA9FBLb7ncb99uuhnubWD3ELrrXT+027jr6QOG+HKmGjqKgVFxP8A9XQeIsBxnLgdTt0z8yo3GQ8UceXu/GWMVMtLRSndVIMk2OnMRtgfdGEHXBPn1UrfNw3cKrngrqmkrJvOY7ivNk9fiHzzv8/fR2lsVX4iMvhy8+P36sJEHoABux9tl7nOj9PoNKi72O4iBX6vUsdqjAMrM3D31yohIHIxGeSKNFkmA6FmwMYPVz+ZIGr5wHwTxzXsailrI/qKADkm5jCcfZQk8xPqdaTwD9GkcSLW3uJgXIfwGbmeQ9jK38lGw9BrToUhg8OlQKmBhEVcBR8h00p1urAbFPB+0P0mnbb/AFOZlXDsfFvDYlUWuqp43IMpghSriY+p5Qso/wC1T89FZvpLo6ZY4ruaVY3bkkakn5ZAd9mjl5XToeujfHnGFv4OiFTcWE0rgmmh8VFz135SwONviO2+NfOn0h8cX76RJWFyhpYLeqhYoli80YyCSrHfJwNzn2A3Oq6ei/Veplz95pddVpht3TW+NfpCENLyWC11rxjZHiXHPkbkspJRe23nPbk+I47xBfrpfKwSXScymNSscKqESJe4VRso9epP2ix1UqOK+Wx2ltNbKg2WOOCXkQD1IOeb5n8Semi0PG90kkSkuVspb2Bs8ng+E+f4SP540y01NOkbc6c/3gN9lmrXbW3E8qapYhzM2ZOoUf0Hb5/31NsfDlXeZFmqwYaUHYFdz8gf59flvknw7HwhXV4mQPQ1O2IK6bCFvZmwCfx9taTQ2poyhrI3hjIyp5Dykex0zbVVMMgwGrROh4gay2CEU4o4KOB4epE0KyDPTOGBwfljRiL6OeH610C21YqjPxwOwP4ZJx+GNWyx2xKmImneJKdRlpOYbDQzi/jq0cOUq09qbxJ5V8sqgNJL7oDty/xt5R2D9NINTarN6Bg/aO6aiF9R4+8uPAv0d0NopJoBdquaSTztDU+HMqr2+MFh09RrN/pZu0nDF6ngt9DSusZ8ZTG7Jy8oOQAG2I3PNn5emq3TfSJfFkkc1bU6ycxKRMSSSMZLHdj/ABMcDttjFav94nuVQ09YzPITzhe4P3iT0+Z/DfVaPD9SzbnOJW3xChV2oMyK/E3DsqIK221lraQ55o3DgE/aIPTPqdznTsUNuqWeO03uDxe61BKSH236ds9+m+qq8EdRWlqGANUydJUHT1K57/xfl3GrDw99FVxr0WsknRSwyGk5hzH2Yb/jpkWvoXI6gKrVecHuPU/Cl1nqwLi0cVMu+Y35gfkfX3P4Y73ix2mmo4Vgo4gB6gbk+p0CThfiizuWgq61VzuCiVMf8g4H46J2SvupnEdfaY6lwdnt9UIZRj1jl6n2DjWQ8RUryMTX8IRL5w9YKmrccseR9pjsqj31oVptNLQwqYVDSjrIRv8Ah6azSm4xqrbRSt+2jQJTRmQ0t9tzQllHUI65Ejewck6jXT6T4blFJb4blZ1l8IHwY6oqkjHfzuDnlAO6KwJOxOMjSnUNbqH2gw+kJUuTNOrOK7ba1Lmoj8NWKNKTleYdVXG7t6gdO5God7+kW3VNgkFMD+9UgMT1+WO/y1gdzpuIqmU19eRXMVCp4JHgog6KoGAF/hUAfjvoebjXsgSXxaZFOC8iYdvZF7f7+eiKPBSRuYzC3xPblVEncT3SOoqWjp42aVz8Csebvux7D2H66o9ZbKGINNJKGZTk8pxEh9PU/IH8e2iFdVqrGmpo2Lsd4lbds93b+nf30FudwpaJfEq5FqKkfAi/AnyHf5/r20+XSUVJlwAIkOputfbXyZBqrfVTqaieqSGEHys6crEDrygdB7fnjQye4usqQW3x1w2xjcl3/wB+g/XrpVFTXXotPPN4FIpwWY7fIDufQDp6a5g5hmC3o8eRh5D8bj3P2V9h1750obfqn2aYHHzG1arp69155hNuLrpaoCn7ZqTP0EUhEoX2JOd/YHb9NO0XHUlfGoutmttaAMZKAP8Alk4/LUSmtlOi800aSN2yNh8tcT2a3S5P1cIfVTjT3TeDahAGLZ+0V2+K0P6QMQ3S3/g11YGz1VKwPmRJds/jjS1XP2BGpPg1kyKewOlrf8LrxwP5gxu0pOcyEykNyk7eum8fl21JIyMHTbLygg7qdMQZA0a0tIjB0taCdiXrqPVUysjZUMh6jUjSHXXSiuMES6MVORAdO9RaZ2aEeLSuf3kZOx9x6H31cLTdIa2BZfFJyf8AEJwQ3cPnYN7nZvtb+bQaeAEHAyO40KKVNBUmqomA7Oh3Vh6Ea8l4j4U+nbzaOvieg0mvW1fLtmjxOXbkfHPuM9M469d8juDuNOBcjJbP9dVuxXenq6YKSw5MBkJJaPGw9yo7MASOm48urBFJ5lVmyDjD7b7e22/bGxG4OiPDvFFtGyzuAa/ww1nfXyI9jIyflrzG2Ne+/rpfLTrIinj3iUdteZ173PvrwnfHvqSpyJ7r1BjOvBr0nOpO4nqd9LlGvAcaROdc5lsgzwgHbv8Az0065zj8tPnfGmwQWJHXVpUgDqRpoiV6aF1NOVzyjJ0alAGT20yyrv66spIlWxmVuqp1lQo6BkPUemhcEk9mkGfEkpC2xAyU9ce3TI/EbjOrHVR8uSvUHUGaIMjKykq3UaD1/hqatM9EQ7Q65qD9pY+D6uyvcYKy7+PLSUcTyQU9Kg87nJ8uMeZzhec9MdsAaKU8Fz444omE3gxryeHVOjctPS06ZIpo2+zEg3dvtHOc/azJHqLNPzxlnpWOSo6oT3Gf5dD31caXiSqn4UlstDJTRwVUgeZlHI06g7Rs+dkDeYr1J2JOxPjbEalylnc9OjJcoZOoY4mu37cqKbhXhaMraaZwYyIyDUydPrDr6do07fMnNhlipOErO1kog09bKTDXyK3mlkO7Uyt6d5XB/gB+I6gon/gPhsTUqvPf6sx+JPGF5qNZF8pGf+ay/CPsLhtiV1bfo74ckoaWn4hvscT3CSMC303L5IU7Nj0zuM/Ecsc7E76etmYBRz/H3mFtgrUluv8AOJ7w1Tw8MiWvrueq4jnQPKsUefqUfLtnosZ5egJHKvoTtSeMb+17XmklkpbVAw/dxqC8zHYAZ6sdwBuOpzs2iXHvFIuU89so6oChhJlrqnJw5zvv3GSPdjjGdtQeFrPPcq2GpeIQlY2akhmwFpYseaol7cxA+QAAGwwS7bk01exeR/JglVbXPvbv2+wgjh3gZamf61WyCmjRfFuDdRFDkcqE7czZxsMFiR66syRx8XT+FHzUHB9rOMbZnb0zkBmYqM9jy/cTOlWuvEVTJw/aJzTcPUBaW410mQZW+07Hrk5wB1GeX4mbKpVh4pkanpi1r4MtAzJI4x4g7k+rtjp0wMfCpLLQp5PuYaSMc9CELDbW4xuMVQ0DU/DNC4jpqaNj+/YbhVJ7dWLH/OceRVtd3rrZQUj366GNbZTqI6OADyTlcgBR/wBIEED75BJ2B01T3ekbh4Vi0M9LYYl8NY0XD1Cg/wCEp2wmSDI5ILEhRjprN/pEutbxNXLHIHIby0VFENgo2Lt/CAMYGOnKNlY61ppDepuh+/8A1MLLCOu/4/7gribiKvvd2N4r3JnkANFTkcwhQk4cjuzfZB6nzHygA2CwUtZY5aOjoaT61xfcFElLA45xRI2SKiUnq53Kg/5ztjMLhawjhxaW41FAtwvNcSLLbiOYEnCmaQd0BG33iOUbA5stJaKxrlW2OnuHPcJcycUX0tzFOY700ZHfoDjqcIMAHVrr94HsBLV0hT8zi3WGG4CewW+tMtigk8biK7dXr6gMWMasT5owQfYkFj5VGpN3nittyjuciQxVsEHJaKbGIrZS9fGfm+23xZbfoxHwDRDia90HDHD1PT0dKiQIhNBRNg8+Os83quVz6MV+4gzQqbn4ir53lrBJRRn6zcK2ZmCykHJkY9RGCRyjqxIPXkCi15b1nr+YQePSvcm26FLsz3K4SGGy0ZExaZSTK2SBNIOrEkkJH1JJ7lzqwU4rqu6QPDAILgkRmo4JfOtpgbGaufbDVDjHKMbeXAwEBbtdNWXapt9Nb6EvNKfEs1vmQeXYqbhVDp0HkQ7ADA25i9hv9xtXBHDklup6ta+sqiZa6sk87VspJBkbO5j5shV+22R8IbPCTn7ywVUEiX68UHCXDkdBQhwW/ffvMPNPI2SJ5c/EzEEoh26s3lGXqlis7zzC83iCKeqmV3pqaZ8IFBy8srdQik8zv1Y7Df4POH7fUXOtW+3mOSollkf6lSvIAZWwC7M3YAYLydFGAPsgGZHDQy1Us0DxuqzvLImIpEU4WZ06imQ7Qw9ZXHM2cbWUY4Eqi7zuaJ5Y44paqep5UXkqnmqIh6YSplQ7ZwMQU+wAHMwA61CJavja8CMR1NPZKSX92gzJJJI5ydzjxKiQjJY7ADJwqjl7BquNLqYIHqKexU03iSyyDnlmlcgeI2P8SeQ7Ko2AAAwoyb1TU9vtVpaSXwaS20sTjBcsnJnDjmXdgzACRx5pmHhJhFY62/8Ab67l1/qHPsI0YqG32cz1Zp6W3wQhVCfvIxFzbKo2LoWX51Dg9Ik0Gt1JUcTXBLxc45Y7fEzGjpXcszEkBpHIGWdjyhmG+eWNANuXlIKvjO5R3KvWamtFNIWgp3bDSkABmcgYBwUBKjyLyRoMlVNku1y/YMUUVJSmqu1RiOjpVTAQDKZKr8IGWXAO2WQEsZpDQnEsBu5PUerp5qeWG22+FJrtUJmKIgFIExymSQLsFA8oUbHHIvkEhlk0FHS2ykl/4h5AziWsrH80lTIcb7bsSWHKoz1XAOV52OHaI0Fvqqu4VIeeXEtwrWw3OSAAi7YIxgAAYOVAHKQsxqjpnNXHWVELLUbmlpGOfqw3zJId8ynJ3OeXmI3ZnL5nuWHJyYNeyVN2usFbeVSKkpQTSW4sCqHqZJTuCw5txuoz9on97xCTxXO9LReILCknLPPuGuDgnyg5yIgebfO5JOSSzakRQy8VTtTRSOlkjflnmU4Nc4J8if8ApjfJ75PqzMVoz+1J1pbV4VNY6Q4qKnlULUcvWJMjHhDHmb7WMDy51oBgTh+IToKSCSBWkMcdBGnwgALKo/DaIAD/ADYHRQA3FS8N3pTcbmzw8O07K8UWDz1zg+VmXqyE7LH1c7nbTEs9PdYZbjXOafhqnYHmdfNXvny7dTHzYCoN5GOSMYBKRCskrqWqqqTxbnIpNstjnyUidGnlI+10BI6ZCJuSTAMczgGY2DVmvpp6mmU3acM1ttxbmFJGdmmlI7nOCw9eROrEuIsBpJYzNUVNNUS+FU1Ef+Pdp9x4EWDhYgAQSCAFDAEAOx88OnaGodZ56mGplEdZWRDE91mAIFPBg+WMYYEggABgCB4j6IW+mkkq8yuscwP1Vnpj5YF//NKbp5sL+8kGPh7cqiOrNxLbcx+y0sj1hml8MTxr9W5oB+6pV/8AzWn6Zbyjnf2A25VEZ2uaIUvhKEZmTAVWIUJncEjfkzjJ6sfKPYa5hlVIaSKKOkij5E5CVVkBAKqRuIsgZYeaRgFG2pcMZyWZiu/7xz5TkbY26EdNvgGy+YswxxuM0HEkjmYLEjsxUbtjlORtsB8OOm3w9B5skNT1VNQRKhw7FdkQDp29gP8Ae+Tzw625iJRDScpIHmcAY9MD5fl26ZyJkLSOXdizE5JJyTpnptAW9T9RbqNaFO1O49XVk1XKWlPlzsg6DUbSA311jbGnKIEGFipnLHJnOlroDB66WN86tKzka65de6WpJFpaWlqTuDFpaWlqSYMWlpaWpO4i0tLS1zMmItLS0tQmTAi0tegZ15quZ2LS16F2669+zqZknOlpaWpkyRa9UZ1W7vxvw1ar0lorrkkdWSocBSVh5vh52Gy526+ozgb6sijOuZncRAZOuhpaWuzk8xr0bDS0tSSLS0tLUki0tLS1JItLS0tSSLS16Nzr3l99cknOlrsDAxpamZJyozpEY11pamZJ4F99Ll17pa5JFjbGkNhpaWpJFpaWlqSTzl14RjXWvHIClmIAHUnUzJOdVPjjjWhsEf1eAiprzj90p2QfxH19tBOPuPzBCaKx4YyFkerGGUEHBVff59iNZk7Gv75riOv/AF//ANP/AO2+fU6jS59T9QG/VYJVO45xDWVtxq3rq2pasEx8spGAf4eX7JGdx/MYJhh0njVax+VkHKlQd8Dsr9yPQ9R7jYcxzGBWZlDxyDDxN0kx+oPoeo/MHmopy4E1M7SU5IG4wYz91gO/oeh7dwDC2BiBLknMj1SSw1JjYNEyEMpDb+zAj8wQdSUiFRJmVAtQQWyBhJPd8bIff4fXByTNs1vqqoGmjiM8UeSW2Hgk5+En1+6dj/Cd9WWGW22OgVkWSSWTPNzbO5HXJI8oHp21Tvlpqo4wOpAprTQW6kNXcmWaX7PKSCrfwHqD/F10Wtt54v4mtpscdVcJaBDysVQOGQHID4wSwHpkdj001YOGLle4Ja+sihprbCPEBdvBCL6KeynA2O/pgZBMXzikR2+Hh7gejkggmQK1UuPEm9QpU4UDuc5z7jJD1Vq2EKFyf4/OE6as1gtniS6u68P8DWo0VmWK5XeZQZJXHOkedxkH4m9u3t1LHCtlrauma/cY00D2uEhyzy+BNyj7Bx5WHomARgAMMDXtDw/S8H2mG8cT1azVJbnp6B052fO5CdGQEd847476E8TXi78a1CSUtTTm0xnljWIAJS/wsnXxPnt6HBOgGq84lRyT2fb9IYLPLG7oD2/5jv0scd11dSxWyxQJSWKVDHTJSgctSvcFhsmO6nBHf01m9KaqlhVakw1tMWLPRyoQi56mMjzIdtyDv1OdWavWmsautsYSswzWxzHnim95Ads+jDDDsdClomv5WSxeLDI7hXp5TmQH/wBJzgOvzwwA77nQjaM6UlV6mq6jzhk8GeSm2188a0T1lVGCPrFLKc1EAGBnI/xQBtkDIxhgMDOl8cWrgOi4CoK+Diesu1WB/wANEspLuCQSiId4sHBAOwOdt96VJQWq3W4WTwIa2vhPPFVwHw/qUhIzl13kORj13wDsNSqiwX6ahguFyoZlhlxyXeGEMzY2/fKPiG+ObZjvzZ6aU2Bd3pOP4MNqZgvqEM3ziKll4aaot9SauOYhJ6YwBJImwPMqnIVyB8SEKSBsObArNmtNwjr0MURutuuREkSr1Vm2L8m53GQQpGSdz21fKvi+eg4HhohY7QqMTmsp/PSM2/mx8SP6g7jttjQO0xcR3OyVEC2Sn8Zo1eKvjKx/WBvtygcrnGfOoByNwTgCmn1DVg7xiXZA+IAu8bw1SUNHVz/WQpSKJ5uWRAuxRCcZIOPKcbHvnQmnipq2nemuUTUVWj4dohhJCDsTCcchxn4cd9uupiUU11uMlt4kNRT3RWzFUMp5pgo6tnKlgvXGCcHrsNFeI4vBt8Mkxgr6hQIi6HEnONwoPqy4IBypO+MnOma2/wCkwZqx2J3JDUTcOBCKaqpqJAoPieKAu5wyseZcc2QRjAJGemh9NVwXanhttNTJS1MYaIUjyELMDufDc9CW82NgOo3zmHbIqtkS92eVK2EHwmBj824PklibZu5267/D26uFHQ1Ea1tDLPan2E0Y5uRJF3GV3ZQdmGMgYIx5cm6kfT/n95XGOYXivLVJjsnFVHH4HJ4VNWVMIR4+y80iYJToN8kAnc64sFsgtN/jWmrzb5DzRtSVsImhmDEho+Zd98n4R36HXV1udfb4KO4RSUNS9VGJJI1ZZaeV8+ccp6ZxzEdMk9RqHcyvGEU9Zao6eCeGBXqaXJjKED41OcbHG3lwB21XaMYlgecx3iyuS03CdKeBZBCOaSleXnV4+xBPV/Kd/T7uANCYDQ35KlaaV6VyH5qaodpY3QliWBPmB5jkkZGQPbRDhyS4VM09n4np/rKyAiOesDfuZMAAE5yqsBjIx1zv3fjtkNorVMdY1FGdvArBHIFz18Nm2BwexVhtltEK5C47/OYugznqC+F7HeKC6RU086RwAeWR2DIQCPgPqCNgDnI6basMt3IDIghqmRsxsGKhgCMKrAcw35dznflzlicBrrc6mLnoaOSankXeKKoQDxVz0wQVKnmJA3GTgZ3Oh1sqaK51RifxLRW4GDECYnIyeRozup3bdT36ZOtt27o4+xmSIKzn2MKUtTR3Go8Sz3f6rWSr4n1Wswqk5wQrAcp+Q9fnp6oulbQS/V75b2p2zsxXMbD1B/sdV+t4duENU9QscMtPMfO8TBoHcDrk7ICSTg4xnbbGrZw9W3B7caGaM88UZ5qWrTmWVRtlCfi26AHqo7sTqDU7DgyGnd1JlquvOgNJVZT7kh51/A9Rp+vq4qyVaeriWnwOYyhec/gfs6ETw2QXBYAtRYa1jjkwXh5hsVJ+z2PYYIPcasN2pZLfbBzszVEUZeWOaJh8hGyghsjJ8wXsMnOtvx4AwZxdPycQQOHDG5rLVUvDKf8AmQSEE/P73yOdRbhNXoRHfLWlxiztMi+FKPfK+VvkcDTlFcaOZg9NUGGRu8R/mvQ6MU9yqOT/AIiJKqPu8Wzfiv8AbRKJU/KHEyLsDhhmF+AuOoLWho4Up5A7ZMVSPBqD8n+F8fj89WziD6SYYbJJWW1kpJkyqpVLufU5+EgfMazG4U9kroWEcfLI3VQMfmp2/TUBLZfbWvNb6oy0x3+ryDxY/wD2ncf9pGhLtEjPvK5/L/ibVXELgHEg8Q8ScQ8T4gutxkaiiJITZAwyTlsAeu2d/l1MKKniiiA5Vji6fDu3sB2/n/WfLVW6Rglwt0lvmXpJSgtHn1MfUfgD89E+F7JR1lxjlqbtDUUhODPAhcoPQqN1/Df1ONgatlaJ6BzAHotd/UeINsPBsl/qzTUdE6+Mw8QR7F/85H/2o2HUnbGtasn0K/su2oKK+VVNUkZkjIWSH5YYbD/KR89aBwhTcOW21KLLPTypgK7IQZGPoR1Hy0Xq5qdaMS1vNAvMB4eTzOd8KANyT6DXktfqiz5QbZ6DSafCYY5lI4fs/GdrYJTTGogDcvPRyAoP/wBzL0+au3y1C+kO8X2jtP1Gevo7XVT7iTLxtKv8XNuvUbjbPTUy7/SvSWy4CKjVJRGSORCCgIOCCw+Ij0U8q92Y7DOPpZ4sHGcqieGLlCmM4QHG52Bxk9j89d01WqtYOEz9zJqLqK0K7uZT7xZr5JVftK9ePcHwAsiOZkwBtv3wOhPTsBobK0cYzMUABxyDcZ9P4j/r1xruz0F9t1XILVWzCU+VaeJisUQ7GQHOT6KNz1J1bv2VeZKFKvibhA1WW8tVRx8kjD1ZSQcdNhnOnieJ11f07BtMVPoGu9YOZU7RbK6+yMsYMVNsWkYfF/c+3T5jbWncFcFF3EVvpyOUjxKhx0/Hrn2GpfBq2aqq0hUSSxxjz00a8kyj3RsMB760+3VNuqlWlo5o6SFNlg+CRvz/AKaw1niIVSK+ZvpdCRgtxiQaTha2UsP1c0SVk7jMtRULzAj0ydz8tG+HeDuGaKZTSRNbZJQR4dLO0UchxvmLPIfxB0H4u4uoLLQs4mjMiMU8RgWUOPsqoOZH/hXAH2mXvjd548uldVtOJpKWPm3Jfmkk9A5G23ZEAUb5ydyhqou1DHyxGz21UDLTS/prqbbZVhprVTUNRWTERyIw5Cc+ykBiem4wNYLU8VWKrnmqrxaqmiqJXPi1EcvOXI25iD1Ax13/AE1KvN0q7n5ppGcMOXDeZpR29iB+XrkdKtcEp5asCKmjnqc8q4XmCn3z8ZH5D8jp3ptDdQAd2TFduuruYjbgS0wUlurvNaL9S1ErAERznkk9iAdifwxucbbaijhm+1VWtJUUzU8bnZQwYNnvnPmPz2+fXQ61cBy1Un1u4VUquxJwDl/bJ2/pq92Lgzi+3ULVdNcoZaI7rFXxkAj/ALWDY/E/LWtuuani9ZmmlrsyajLdwd9HlHaoVmrYxLOcHkO4B9SftH9Pnqy1UkQdaSBGmkyAeTpGPUntqqW6biKkpQKuyXeCMrvPbJFq4j7+H5GUfIMdOz8Vx262GOnr7fzMQrMyPBPCTnd45ACT2G2Mkb6Ae4XncXjCqpa1wohm+Xi3Wam561z9YK+SGPBdj647D3OqNc+PaKmoneppoJ3G3h1UflU9RkjJz6Abn5ZIG8UUVwENRW0DS3KqEnK8ecS5xuWOTy4O2B5v8vXWeT0NYZvGvaSB1BKQkciRj37D5DJPcnrplTpK3XavP3gOo1Rq5MJXLiu9cQQmOkJttGVMc0wckurdUQfYU9OVd2+0zdNV6sovDCw0CJ47nqR52B2PTZQfz9COmiAd5V5o2EcQGBKVwPki/wDz+OvfEWL9xTRuZH6qDl392PYe38+mjU8LoUdcxU3iVzHOeIKo5rtYxJPHWVMZXZUp5SFX/MR/LP5dzVm+kPiNUYV/1aqpk2Z6uEAt7DlAJPtk/wBdDrhWUtAolrnjnnUfu4U/w0x7Dqf957EFLNW3mQzSssFInWVtlHt7n+ED8NLdaa9NwjZPxGeiWy/1OMCXml4s4fukTxVXDtRScxw0lBKu5P8ACcflk6Hrw/whX1kj0XE+Jwf/AC9yBTzejNtn8/x1VYwApp7UjqzAh52wXb+iL8uvqemoz2GvRxOtRHPJjfnB1KKNZqEy6ZE1e/TUMQrYMutXwNxC7ic+DVwKMK9K4YAeijoP9/PUSSgloAIpKWSD2dCM/ieuqxBWX21zrPC1VTEdWhc7/rn9dWC2/SZfIh4VTUQ1id0q4gSR8+v/ANlpvo710vp2Y/aKtVQdQc7o5jXmikPGXDVeM3Lh1ICeslG/KPyP99SoafhG4rzUF+kpXPSOqTAz6cw2/XTZPEqm7GIubQOvRzAWlqyjhCvlUPRz0VXEejxTAj9NLWv4yn/5CD/hbv8A4zNwca9A9d89dIDHXXuhoyjbpygldx302653XfT4BBOuCp5iV6jtroOJYGMr017r1h3HXuNeDWykTs6XppqaIEZUb6d+WkMHVyAZ1TiBKinmp5hVUTGOZPT9fw9tWDh6+JOvgOoWQA88GM98kpk7juU9dwQfNqPLEHHodC62ibm8SMmOVTkFev4a8x4n4N6jdRwfcR5ovEcDZZ1NBgnXwlcOHhIyrA5wM469xnbJAIOxAOn07++qVw/fJTL9XqcJOT0JAWU9M+ivjbpg9CCNtWqlmDJzx5ZM4K4wVI6jGdj3K7+oJHQfQeJ8+XbKa3w7P9SqS1GMj10h1+euR5geUgjY5HfXqnse2nwORxEfOeZ0BnvrlRhjvpAkpnoflrlySOZdj6ass4xE7AIGNLb102r7ZBznXKuR6atiV3ACO8wzjrrknGSNtNPLliM421ArLtSU4xJMCw+yu51GKqMmcBJOFEIO3v10xI4AJJ5SO56ar1VxDK+RSwYHZmOf00LqKipqDmpndvYnA0HZ4pRVwOTDKvDbreTwIfrLpRQkjxBI3om+hU1xmlyIYljHqdzodGY+fljHM3sM6n01BVTgnlEa+p0Gdbq9RxWuBDV0em0wzY2TIzKztmR2cn1OvATSETQRh485ki+y3v7N76NRWuFADIzSN+muZogcx8gUDsBrP/0VtQM2tzLJ4siHFS8S0fRxfrP+0qKS8I1XQw8xjjzhVcj7S/gObuQNjq4fSPxg80psllnikqahc1FQjAJFHjcA9FUL1PQAYGsRkgmt9Q1VRg8p+OP72/8AP0OrDba+K5UTCJlUyYEgdQOblyQkm2cA4OBseUdhhVq79CzVWDv3+YwsVdYosT29oYsFunu1wpbfbYXnQuGjBG8z/wDWcHoBvyKegyx3J1cLnLLVVH/gzhqoEkjBXutzDYUgDOeY9EUDIz6c52CYHz1E1ngpeFeFZUrr3eIwa2vXDhFY/wCEvz3DHvjkGwbJGW0mGkHAfD7LWV9eOe7VvNkFT5iS/wB3vv1+I7cmQ7Ldzbj37faapXtGP7yPS0icQzDg3hgtT2Kgfnr651KCZl6ue/KMkAdd/vMcHbTbI77VtT+IbdwZZzzIoOPreBnxmOMFmxsNwqgHB8vMVsNjpo7X/wCF7TKiWyHz3Cs5MGo9zvuucgL9o5ztznVZ464rpqqL9lWsvFY6NuQeGctVSZzgH7RJ3yfTmOwUC1Slzx1KWPgRcc8VftB44aOnK0ELeDQ0keQZCB+Yxnc9VB++2dMWqiprDbv23eYvr1bWP4dPSpsauQYHhLj4YU2DEf5R3JiWKkpqKkl4m4jZ0hVhDFDETzyNglaaHPffLN2BLE8zbG6Wa8UvEdLWvTU0vGFbCpoaZlBpbJSDdWZTsDy5Kg+7tkka5Y+eB1/P/U7XWc5PckQU11oLnU07VCScZ3CESXKvYYjstMRgKuPhflwAB8IIAHMdTKie28P2Knp6OmdqYOVoaQ/4twn+FpZMb8uduu3wKeYuREd7dbbcZ/rFRUW5KjxJpuYrNe6vcn3EYzkenNzHLMoFUrJbpxHfnpYx4ldOPBnaLCpTRgH/AIePsoUZDt2GRn4ycVr8w7m+mbMduAvcZmp6rii7yo0sdVIWMtZWyFRGAo3VD8KRIOrDAOAB5QOaxWW2xyQUNBa6A1NJPPzWygZCrXOdSQaqcdVp0OeVT137livFDS0ppIaChgastssohghhBV73UKRhF7rSxkgk/aO/UoFt4qRwjSXGorpY5L3UfuqurDBBhFBNPBjaKCMEBnHQbDcjF3fJ4lq6xWMmPXispOBeHq1VqVuV6rFL3KuZsfWGXYxqRjlgQ4U4xzEBF78maWGlr7/cv2te1mmj8XFPGgCSVkpGwUbhSFwCfhjQAADYM/TRVHE9xa43AyrbIpEVESPElTJuERE9cZCJ0Rck78xNjWPxAV5YSpR4CkcuIuRd3gR+0K9Z5+rnyjbrFXZx7+8iA2HJ6nAQSQSS1ElI0UkZ52JKwSRRt0znK0cbdd+aeTuScio1s9RxhcXt1vmeGzU7CeqqpU80zHyiaRV6k7JHEuwGFUfEWfutfVcUV0lktUqigjImrq6RCiyBPKHZR8EKfCkY9huzHVz4XslJbqeOiiD01PTszOWYJJzhRzlm7Tcp8zbiBGCrmRydafR+csP6hIHX8xWu30dstjMyCjtlIsnOzyY3G0gLr1Y5AllGcZEMe5Ymvnx+La0VdQHprBSvzQxHEbTMq/Gey4XAA3WFOgLEc718ar4vvC0lNKtNw1REITCoQSsgJUKDsAq83KD5UXmdssWY2adqTh6ipvFiQ1EzLFQUeSm4IIJJGVVSebJGQTzt5yixUb099ywAP5RxC1G0FHTUqvXSjFLSDMYQLkczfaRU5j3yvMQCZndo5ENBRW+OeolnjaTk5664yIoyMYwBjCoAOVUAxgY3GRIqGFaSKqkkqkMzrz19dIvIuFzhAM+WNcMFX2bJyHKwaOF+J6mKokhkSzwtmkpSCGq2z/iyDY42OBt0OMYPh5D1cmWGfiSbWKy9V9PcAklLbKZy1BTNs8z7jxpM99zj0JPVixM+qoaq7eFRU5KWqfeomU/va0jpGn3Y+u/2hnHlJLz6Kn+vkAgNQ5C4Uf8Amj05R/6Q2z97psgw7VRJPf66a20E7RUEZ8K4V8ZwXwd6eE9v4mHTONWUZORIeo1Eq3x2tFsZYrJTfuqyoi8qy8u5p4m7IPtv3xjpqbEKW50iu4Wn4XpgAkcakfXcHAAA38EHAA6yNjtsZ9dZKE2iKlmdKCw04HiwRqV8dQdkON+Qnqo3c4G+SNSVNStXTSyUIeukJFqtg2ECgYM0xHwkA7nogwi5Yk60BEridGKaSvpKiqo1nuhybVbGPkpB0M8uNgwBwT9nPIvmJOmVVBTzBqmeqhnlEdZWRgCa5z7gU8AHwxrhgSCAAGAI/ePrtTH9XqM1E08M0wjrauIYmuUwyBTQYO0YwwJBwAGAOfEcFIaUwp41VtVsv1aOOkwBTKf/AKtTdMMQo55NsAZ2AUJQtLAYEjU0cvil5Npx/wAITSY/cjA/4Ol2ADeX95JtjHblAjlU8CSIGCw+F4XhqsRIiEQO6JjcQ5A5mHmmYBR5QMc01OjRAqkIhEZjCxkiIRZwUTG/g5+J/ilbCjygATKmf6uQqEmbOX7FcDA6bBsbYHwLsu5LaldbWnasrZYqDLSTzRwKZZHZBnBPRiQMYAHQgbbbIPKvmJIHVtY1QoijQRQpsqAY9v5bY7DUeR2kIzgADlVQMBR6Adhrkac6XRLVy3Jim/Vs/A6i0tLS0fAsGLS0tLUkxxFpaWlqSYi0tLXoGdczO4nmlr0DOlynXMzs80hvroDHXXuNTMk55dLG+NdaWpmSc8uly660tcki0tLS1JItLS0tSSLXhOvdcSMFyzEADqScAD1OpJESCe+qXfeJZLnXVFl4erRTR0+VuV4Cc6UuNikQ6STbgeikjqxA1VeMfpCkvlwew8LNzUQJWrrhIYxKo+IK43SMfaceY5wuCc68orYslngiMTLblUGnpwPA+tkZHiMP+VAuTjucnGWLMQ77j9KwmitfqaVa7UltbiWejt8MTUkMAibMnitM77uZHyQ7knzEEjbAJxk6H9G/Ectuq4eFbvO8iN5bXVyNkyAf8hz98D4T9oe+s84S5rjeDWSqgNTVGQhFwoA3AA7AdABq13u1RVMD01QreG26shwyMDkMp7MDuDp/ToQ+lUf6u4mt1hGqb/49TYNLVL+jrimetZuH75Ipu9OnNHNjArYht4g9GH2l7Hfpq6r10sIKkg9iHggjInmlrrl316BtvrmZ2caWuiN9e4HpqZknnLpEa90tcknnLpY2xr3S1JJ4Bg690tLUzJFpaWlrk7gxaWlrpe+pJgznS11ynS5TqZl9onOlr0DfGugNt9SVAnI0iMa6wNLGpLbROQM6zz6Tqi71dFPT26Z44I25ZYlGHlAzncDPoQN860XGqnxfTS0dQ1yIkno5MLOmObwtsZH8P9dEaUqLPVB9QpKcTDaWcRllKGSnkwHjGxOPtKezDOx/A5BOuK2IU4BLCVHH7pgCAcevoR3Hb5YJtHG1iMQkuttAeJzzSchzn1Yf19evrqqUBZQyTK0lLKRzRg783Zl9GH69DtpkTFO3bw0cjzcnPPgVg28Qjaf2Po/v9rvvuS/DdkqKhzUBjTU2OViyby+3L93PftjbBAOptqsFOimquJjeGPdYyCBgd3B7/wAJ6d86cqK2e5PLbrT455AG8QgkcvcE9VHcE9enuYQqjmaKCY9UXD6nRCgtlPH40TcjLCeYRk9DjqSfU99j72HhvgloLXPxHxVXfVIHIcCRQ/O46eU9T22xtsNsjXsfD1h4Nsq3C8S/WrrKuYIY5OVl9yQfKv6dc56CZw7T13Hd0p63iGtqKWhjAWKNl5UyB0QgAZOM5ODtjtuq1epJUlTwPf8A4jDT0gH1Dn4/5kIxXf6QL7Dbbeq09siTCwoSiINuZnB3Y5+fbc40U4prOE/o/o0o7Oq1l+iYSSThxyhsfbG46YAGCcY+Yd444wo4lp+G+CKWGTwWAFSkecN05YyDk+hIOMHG4IxUajhKW1zm5XmCQOVMwpWfxeU9WbPV/XJ3GTnudC6dfOI3Hav8zew+Wp2jJ/iDJoJ+J7hNeLjXzSxsviTRzZWdVPYjoI/4l2OexJ1Dud2ippYXs8aQPEPDSRUB8Qf9Pl6Mpz0bPXO2c68r7rXXC4RfUOaKaIkwhMZQEblifskdVOx9N9ptNSwCrZmpo47o6+SJG/dT4G4hDboepKH1PKSNtN0QKu08L8xWzEsWHLRWC3UN3ucENXELdUSYIpJm5oGPUsrndv8AI24z1IOmOJmoaSp/ZvDHirTOeWScJyyVLcwOEHxIoI9s9+2VQWa58SXFaKCneaYn/DGyw79WPqD+I9sb6hDR2v6PRBXX+vorlcHQDMseJ164bKg5A+8V5sDrtpXr7FACoc/EP0VRPqYcwbwhwvU0Ntj4h44pqN44jz8sz+HMy4ABkz5ZGHocEjYn7OmOOeN7zdq+OitGLbaJhyU8sJDfXFO2zL02+yMFe+Dg6rnFrcVcX8QRLNE9UZADSQUx5oEQnZlYbMPVuvqRgHV+4S4Tt/ANoa43i8tBWsRK/IeaBTggAIRgntkAHsD6+X1FQrIa7lj1iOUs3DCdSsU/0WX6K1mtpaiKhnlIWe2VJDQVCA7c7D7RIGPTbBGcar1BXRUTT2+xXU0lQjEGiqnEsYfowgk9c/ZbYnJBPTVh474zr+LreKOzzfu1U+NRRApUSr05lz8SY6gbjcNzYwOOBfoja9UTXHiULDbnAMQHMrjt5d+vuQegxkaqGKJ/+T/aVI3H0SF9Cdhm4kvVVPBxFNRurF6ymmKyzS5O5KPkOpPUsMjGMk4IZ4r4bThvjJaVLvbZ5KsHkhnm8GOdB8KtsQCCSFLbEDGTy82ol8Ntsd2kNDVz3SOhwpusDCKohzsAW3VyB3bZtwDkYFRvDUldXPW1s1dcbTKW8W6QjM6Mw/5qtkgg4yCcns2MAaVpYHLhsr8e87vXbtxzLr+zbJw/c5/2u1XaBVDkeNvMg5ySjsOuxAw6k4Zc4KkA1+a7zrWSWC8SK6SPywVQjUOrBsKyswGYz1AJHU9wBrmWGkfhgQ3i5yVNvhieOiBmZmPMBlYwexIUnPlXA6EaiWaFhZZnpq2iulvogGlpZTyzxxnq7Ie2/wAcZI9dt9E0tuBOZkx+J6KG8WmrNLAkdwtsjB5YYh4kTAhSDyHJUnsdu4ydOWintVHfKatStlssoYZYqZIvMMEMCchWGxBzsevbXX1qhqKMLZJaqnuEBI+pl1zyMc5hbYkfa5d9yfUjUOO5PxLWvSXeQwXb/D8aVAUqT0AdTuGOwH5Y20WtnGDMtpzmWiuvlVwpeBHQzxSpCodI0POkkW5OOfr05uX33GcAR79Qy8W0NRdbSac05801OhKPC+Thxk4OeYbbDGw1XrV+1rci0NfAbhQt/hu2ZI48AjII3X33BHtvq1cNUVspbrHJT18lqqJGZHhkUywSAg80TDuCM9vUDoccYMuGH7/7ToKsCDK9wy09NP8AsriGETW7nMbNLGf+Gk35WxsVHQkjl+Zxry+cL0yLJ9RrZaGQyAGGaXyGQdCJPhb0BYZx31Yb7Xw0VTJRyQpUNR+ZeWXmcxb7o/XI3cDJBBOw2AH1ME96gmmtbLcUkJM1OnkmUED4V2U9ObbBJOSDga1W4WYB5/OZCkrmM2u5V1smjjuAkp64xskoOF8QeUZB6b7EdRkDoq4Ns4buAroamw1NXTUbzxlfEdOWKdG2SQLjyk56rjB2xkap/Cv1tCbVc4I7rSOSiUs+ebPMRlQR5SMZxlcj12zY62w2yF4YoqqppMgtD9abOBnJXmPUBs7N0JB7gaw1B3cJyfiaUnnB4nPG/DF0t9PPFXW+URh/FiejJkRQyHD5+IbqeuQQ4HRANN/RXxpNHJDYLqsTULMFiaSFOdcjBXPQbnIIw2evXGrlYqu7R2+Oi4jop2oF5UiutA/jpAScqWXHMmDg+YYIyOjHQ2u/ZdtuL1lbHaa6kSYK8wQZTmx8QBHlUkDnBB5SpyScaEWwONrcNNmrx6jI/H/CtuoqnmrrVUUgZSP2hRdCwHNkqOzLlgdz5XX7O/nDlkjgZ45riJURxGJnjMkaZ7OFw8Z2zkZ69NtXmouFJVcLUNTYaOWljlZVDYFRS8gfc4O4ZDkgdPiG4Y5xuXie52zxFoJ5ENOZA8X/AFIw4LAAjI5Tysuc+Vz0IOd69TaRtb295GqXsS78YcP01qaCouf7rxFzFUQyiWFupGJFAIOB0YDY9dCqaoqoDy09RHUL2SQ9fkw1Zvo+S18YWrmWqlprrEvI8kTcgmU75IBwewIBxsNtV2+cBXazTRta5z4ZMhMbt5mCtgj0yOZfTYqd85JWi1+TtJ5/eD30AjIE5mqbbVfubpSeCx6eKvlPyYaiy8L0/MKm1VLRSfYPMc/g6+bHsSRqPT3Goo6dobzQGIAlNzhRj7TA9c57fdPpoiKejWD6xZLpGw6kRElfxRtxpwurrs9LDmB+U6jgyL+0uIbNJHLJJ4jxsCr7JIQOoEijH5j8dEblxhVcRw/VpOIJaCdwUMdYgTxFI/wxINuXuQDlvtcwAGoNvrZUZ2rqVpS2xkBzt6Y7D5acmtFnuYY07qjH4ghwfkR31i+lS05HP2Mst5QEHIgS526429S9XEyQ4/xVOVIHuOgH/wAan8JWqpvcojoFflY8vMg/eMO4X7i+rfEfbY6aW1cQ2U81oq3eEf8AKG6n28Nsr/7eU6k2niZaSs56qgntdb0NRbiUJ/zRHqPlzataXK7SNv8AExr06B945my8G8EUFnhjeeKKSZB5EA8kf9z7nVvkLJF5YTKScAdvmfbWWWXj+tkpSGrqS5QJ/iSxjw6hB6FemfwGrI/0icO2+2MT4iMqcwSoPJ+LMT+gyT0AOvPanS3E7m5H2jum2scDiXGlsVnrCrXalpKghwULRDyN25D1B+W+ufpGoaG32CWpg8MzjeNZvPk+mSebHsD6axS7/SXcKyoaaid4I1H+K45HIP3Rv4S9PV22y2NgNu3GVfcKPwpah+QgeZuufQDqPkN/lrCrwvUWHd0JLPEaawVHJgi+8WQGraG+2mOaOFBGlVTy8rBfi5AMn1+FSO+QNDqeOxXflltV8jWR9kgrV8M4Hp0Bx6D8d9Cb7VUs37qWETuCMRkZJ/zHsP4R199xpq38F1N3kFVcpZYkyOVRsQvoB0Ue2+n9VWooX08iKmsquPrGISrrFxAag0z0rwRPjMxYHnH+YdvYY/DcG0cI8Kqkiw0cBqatwPNy9v5KNRbDwpxZSSFeHby1RTRLzNBVxkIo9TuR/wDZZ9tXKx3K/WmFpKm2V9vjcfvKikhFXA+O55Rzr+Cfjqn/AKkoBXpvvLrogSD7S0WHhugtlRD9eZamuc5EYXKR+/8AqdWGpoohUGqqJeaMDKiQgJHjqf8A51UbfxpbqenWSRqOpikk5GqKSpVnLYJ86seZTgHY4+WqH9MfHt7rab6la7fXw28Ah2TDeMT0LcucD2Jx6g9l61Xaq3kw/clCcCaBxZ9KPD3DkETUc8FzqWO4ilwqLnqzDp7ao30tfSdDxfajbrAnjU0sOKmor4B/w5ONoT9n/Ngsc4yNZDT26Wd/rV3dmPxLAGx+LHt/vqNTw7VC8tOEihTYScuETt5R3Pv/AD6aY1eAUkhm9v3iq3xqxQVQcwBLBX2tl/Z09Uap9zLHKVf12A6fM/povT8ccSW6l8G8vSXAnrT1cIY/9zDcH5nPtqQJI6YlKZXaZ+4P7x/mfsj9f5aH3RqKji8S5GOaRfgp1+Ffn6n/AHto2zRJQu5WxiD062y9tpXcYYp+KuFbrSNPX2mttJHk+sUrB1X2Cnp8hnT7WeluFEU4Sv8AbZncZMdQxjlb5825/LHrnWfSx1F5cyALS0cewYjCKPQY6k+g6++lO9SYDQ26Lxx3klA5mHr/AAj8fx7aXV+IX2Ma0G4Ro2iprw74Bhi4cJXe1hqu926qqH7JGCyfNmHQbdB+Y1FSCqryGqW8OJBhFA5Qo9FXoB/89d9M2TijiqwoIxcK5FU7RyHxI8fI5GrJQ/SFRV68t/4eoqonYy058OT5/wC8a30dFFNm61Tk/Mx1d1tiba2GJDp44oY+SNQoHp399dlhjGjcH/gu6gGhu89tmPSKrjyv5j+p05UcIXZYfHozT3CA9JKeQNr1VOrpIwpxPN2aS4HJ5le01NR01QP3sMb/ADGpdRS1NNJyVMEkTejrj+euQN8aIIVxzzB8uh+IJksFETmEyQMe6tqNLYq1DmGoWU9g64P5jfVjVByl2ZUjHV26fL3PsN9ALxxLFT5p7YC0p2MmfMfljp+G/v20l134OgbjwftGuhGrvbC9feNx01ZAWSrq46Z8/BlnP44U4+Wc6WhUdpudev1meXw87KCQB8hkgflpa8q3ibZO3OJ6IaGrHJ5hHJxnOujnG2nWgLRl1AAB017emvazzatmIdNLbPvpa9A1JzdOGTmJxsdNHcnOzAdPXUnAxnTUi8x9D66spl1bMaU7b662GkwycHY+vrrkgnbvrZTLzrXMiBxjPTXqnOfUdde6hMnUFXGhEvoGHQ+upljvUkEyU1a4WUDkWViQso7K56gg7huxGdSSquMMNDq+iSUEPgehxpB4n4SL/wCrVw38xtofEPL9D8iXWknDkyRKebIDxnGeb5DbmPts3UYOVEnnVsOpBBG2NUG0XSe3yrBWOTGBypKRzco+6w+0nsf9dXGmqlnHiKyrLjmYFsgj73N3H8XXs2/mZdoPEDUfKu9oVrNAty+ZVJniADONNtLgluoO2hF0vUVHI8TQzNMOqEcoH4nQOpvNxqAQhFPH6L1/PTezX0VjO7MSrodRacYxLTUVcFMWMsyRr7n+WhFTxJCgK0sLTN2LbDVbfHNzTSM5z1J666WRmPLDGT76DbxO204pWGV+F11jNrSVV3CvrCfFk8JfuqcajL4SHduY6l0tsq5xzOSqnRKltFPF8R8RvlqL4fqL+bmxLtrNPpxiscwNGk8zYiiYZ6E6nU1lkcc9TJj21YIKUgDlQR+51KSlXGfiPywNMaPDqKfbMAt8Sut64guhoYoceFCCfUjU9YCfiOx9O2paRBc46ac5AB/bRgwOovYMxy0iiADybfPUWopQQSvVf10TCEg52x01w0XU99SW2hepXZFOGBG+g1RHUUNZ9dgYsOjpnAYen9j2OrZV0obLLgdvloXNF1Ur89Z6vRVauva3cM0esahsiWLgfi00dJWPRQUss9TEIi8y+aPG+DjscYI7rkAgE8uscLWmOgs0dqtNUlyuNzPjXCvDbEdSvPj4QTlm9dgM8uvm6ennopzV0nph07MPQ/721deEeMa2O1VFHRVskEc5USqDh1IOQOYb46+x64yAB4nU6OzTW+XZ/f7T1Ndyaivcn9pfvpS4liobPLwvw/K5ig3rqtVwGcnGCAfkvL2ACDODmncG0ElzkevurC2Wu1wj6xORzCIE78o+3K56dMkKOiZ1IslpkvdaytKtLbKMGaWec4VVGxnkx02PlUdMgDLFibC89vkpKW51FBKeH6eUpY7SfLPdqgbGeXG4XcZxsoIQbknVrGUDYh4mNSNnLCPQu7XSg4nqbZzzvGKbhewP58KCR48o92JZiAOdthsM6nLSQW63XGGtrzOzyCfiC6/E00mSRSxH7W433wxUdFQkyaOKroKqtq7jWxHiCoiD3S4Ff3Vqp8cogiA258eUKOnwjfmOqlxFdFrRFSQUxWBUIt9E/mCK2xqZsfFI2NgdjttyKOcZF3k+whDvtH3kS63ybiC4q1HG8dXIPqtFSQ8xNDFkjbuZmOTkd2LndlALUdvo6G21FqSRlokZIrpUU27TyA5FBTdmJI/eNuNgOiZbm1Wals0VSoqWpamKMLdriBzNRq2cU8fdqp9wcHyg4znmKaRwVw6aOWluE9BHTV8UOLXbmwyWmnP/ADZM45p3xnfGSOwXySy0KPtL114GT3GbbSjhSnqr/eQkV9q4Vp4aWAAi2QY8lPDn/mkZJ6AZd2xvzZtVSTcWXOaaWWOmtdOVeeZSzIEU4RV7svMcqOskjF+4xbeJqZOKw7VNXHS2O3tLmqR8mqm3EmJCPNGAV535cMSFVT5BqFSU0MEcdNSJNSx05VowI+aWFn+CQr9urlB/dx9IlPMd8sa1t2fed2Gzgnj+Z14ZXFPBBUQBE+qLFER4lOG8xiQjb61KB+8ceWKMBTnG1X4luNRdq9+HLH4btNyLVSQNyQqkYJWGMn4YIxlix2LZc9tSOJbxU/WU4a4cRJbhIPAZIX8RYUJy0CP0JPxSyn4yMbIoDGuDuH0oaYU8LrNLUcjzziPnEwJ8uFPWLmB5EzmZlLv+7XchV29zrevhepI4VtENvo4qKidjhhI0qIAzuy4STlPQhQfBRvgXmmfA5V1HuNQ99kew2lhHRoUWtqYssuBssEXQsM5O+DI7O5xnCuXq4T3Gvl4csgkQZIrq/JkCBmHMgYbySM2OZgMyNhVAVVGiQjtXDvD5qqpfBt0IKxQqQ0lUx/Ri2Dk9CBgYjVjNzO3k9zoXI46nc1TbuHbXFUSx/uUUJSU0ZBMzYJGDjBycOWxglUc+VIhI3YrbVzVsvEN6dP2nUjyqCQlJHvsCdxjc9QRljnmYtGzYrdW3S5/t69IPrsgzTU2SVpYyc7535jkEkjJJBIyUXU+Ipfm8OMs9mjcAsOtfIOw6/uhkeoOR1yPEzJlwTnJjwpY+IIUiZG/Y0bZiTHK1bJ98jbEYwvKNs4VjhVQCW07Vla1mtccbQxMBcqkbRooI/wCHjA6k4CnHRRy+gRqsqqq41z2C0TCGZMLXVce4pVPSJP8A1T6dvc5ZZtHSlGXhvh0Cn8AYq6lfN9UB+yvZpmHf7PtqAfMqY7cJKy7V0nDtlLxAgLcK5OlIg6QxkdZmGc42QE7Eney2qlt9vtxRTHT0FEnK7nyxqqjJOT9kE5LfaP8A9l1aKO3Wy2fVqcR0tvpkLPIz/EOrMSevqT9r5fE1UyisFLVVlHKaZ5B+y7XjEtXINxLID8IHUA7IPMcsVA73x7Sg7iepknqqa4zU8jsWK2ugI5WkfvNID8OAdv8Apqd8s2B6Ai01cklU5EsoS63CAHxJZOi0VKOu2eX+HmP2mYp1NTiJaqoqa0pUyFYq+ugUlkGfLSUq9eYk4yNwTk+Yjkfp6d4WjLRJSNTAQwQQAMLerDaKMdJKlwd26KD6Z8TjH2lgM8zqOFhO9RKi0kqRrSxxUwDLQRnpBCBs1QwxzEbKFXso5n0jadnMipyOPBCI/kVFbLQo33c48WT7WyAE4x5AoGDNiKOJWjxE+eQEnmijbqST/iS9Scqu+SvEkrOTjCqcAIowFA+FQB0UDYDtv3JztRpXu5PUwv1S1cdmP1NSQ5WGTmA3LheXmfpkDOwA8qj7Iz1JzqJpaWnlNKVLhYostaw5MWlr3B9NLB9NaZmc80sEa65Rr0jOpmScY0tdka85RrmZJ4ATpAHO+uhtpamZIsD00saWlqSRY0tLS1JItLS0tSSLS0tLUki0tLS1JItLS0tSSLS0tRbtcaG1W6a4XGpipaWFeaSWQ4AH9T6AbnXCcCdEeqZY4KeSaaVIo41LO7nCqB1JJ6DWG/SJxvUcZu9g4fLxWQZapqyxT6yo9/sxZ+Zc4AHQE9fK2u4yrI4KymaC2shnpbVK/hiVFO9TXMN0hXGREN2OxIOuKO20HD8cldcBDJPgyRxyIEVcD/GlU4UNjdU2WNcZyThg7NRngQgU4xmQ+E+F1poYJaqOKOMsrxwzAJ43dXmzskIAJCdSMnYEsIP0kcTJc7BUU/DkzNbIpRHVXaZWElymzgxw7bRqCQST8OwA3B6Wkr+MqyKaqlkhsUkgd2nk8D66hO7M7bxxHoMjmcb4AAGh30likWW22ujcSwM7Sc8a+HCUzj92h83KSSQxwD2BG5HqBsuCibnFNZb4g/guv/ZVxhgrmH1ebAgmOwSQ4Pht6Zxsfw1pxC1EODnpvnqNUO226nrbLLFUxiSOcnmU9wNh8txnU/hO7VFDXixXWYyygH6nUN/9YjH2T/6i/r117Pyzp8D/AE/xPKbxqcv/AKpPvVunlET0031atpZRNSVA6xuO/up6MO4OtF4E4ni4jt8hkhFJc6UiOupObPhP2ZfVG6g/21W5oo6iM4O/Y+mgFXFX266RXuzlI7nTZXkc4Spjzkwv7HqD9k76w1mn81d69ib6TUbTsbqbKN9LQnhS/wBDxHZ47jQllUkpLDJtJDIPiRx2IP8ATRbSaNYtLS0tSTEWlpaWuZkAi0te9degeupmW2znXuuuUaWBrkgWeAbb69wPTSzr3Ulp5gemvFBGutLUki0tLS1JJ5ga90tLUki0tLSwfTUki1zJGksTxSKGRwQynoRrrB9NLB9NSSZrcba1iuP7OqHY2uocvTyA8pjydkPtnp6HHYjFerrPSWW4y3CUHwScrhdo8/dHbJ/LOPTOv3m1091oJKSpUYYeVsZ5T6+/uO41nApylVUWa9RkSJlYJZMkOnLupJ746/eGG65wz0uozwe4t1OnH6QFaqK88YVc9Pb6L/hFXzyZA8Mj4dzsW7cv6jAxb6q82rgjh+K1cMhai5T4NRLPGef35sd85GN+h0Op7xebTQpw1bo44KepkAjmI5THnqucYAIxgnf+WrbPw5w5wLbKK6X6rjqbgsnMKdxnxOb4gMZOften550BrLitmxxx7Ae8I0lQKbl79/tK7wtwRUV6wcR8UxyQUSHz4ALOPsll/IbdMj0JPPFvG9Tf5I+HeEaGSCiXyqOXBkA7sOgXvg7nbOO3PEN44l4/uho4YxQWuIjHKcxquNiD9s4wRjbf329lutBwu01utckFbcJlGJJdmMgwMOw2YnqBkEnvkgnBUZzutHPsPia71AIT9T8wlwlJaODkq6m7UPNcxH4iCnAcMvcRA4KgE7g9AeuNzUJhfPpA4ze422F6eQMOSSNzy0yjp5vvb+w9uo1Bo7dd7/cmutdUT0yq3N4zHkkJGfh+4o/31I1a7LxrU0NmqLJZKehNejnlqEi5FnU55iqjYyDfy9D1AOCutbKDVmwDJP7SiWi30dAQVeqKktdwqbdQPRT3UHnmhgjKJI+/Nyg9xjJQE7Zx6ag8J8H3LiuqcIpEJOJ6p12Xpsvvt2/s2rLwf9H9Rdy184jmemoyfGd5H5ZJSDnmLfZHv22xnAIfvPH0Ipqiw8M3GSmjZ8RVk8QXnJ2KCTORns7D2JO+qPq7WXy05x+07XQgPmMMQvU8Q23gJJLRRXGluNxZAPHqh50kxgeNIoIOcdTgjvnfFBtPDfEnFvEM5lWc1DPmqqps4QbYwfwBGPwzswNcA/RvcL4xq7ustHQc2XEg883r17bd/wBcDFqvXFdi4NYWjh5qghF5JYYxzxw4AwwBIIYbeUEZB+zsxF3ikkV+pzCCptAL+lY60Vh+jK1q1NXuavB56YbpUMTk+X7J6ebO3U9hrP8Ail7xx5dkrLa4r4Vbw46aMFfBOekqE5D9s9GGwIG2vBZb3xRejUS1n1mGcgitj38QfcRfsYyRggY9B9q9z2zhv6P7QtRXs8NeqH6tHSycs+fdu/vnyjvjYHJ6URQ7Hc5na7GYlQMKJ1wj9Hlm4Rtr3ri2aGaoKZMcmOWPtkk9x2xjG2N8DVE4/wDpDa40k9goK+oo6DxjHG9QT4jAE/upCTlV9NjtgMV1B4t4juHHVStPLWstZFjkopH5Y3PTnVu7eqtgj7OOmpnBn0cVQqv2ldZeRY/jqWGUA+6in09e3XbS/wDAtSDbcc/aEC9XOyvr5g3grgfiC93SKokpxb4oEAfJHgNHy45mI8rZGcgHB9hoxxlYuHOGblF/4euU0fEDxqrwnCxTdQC/QKT6H4tv8xcv30i2qyzC38LUzvTRg/WZRP5Jj05kJGFb/wBQDGdvNsdVGjsVZxVUItnrZ6yincuyyA/W4ixwcqeoJ6yLs2MnHwgULYG80nA+JpuUDaO4DvNworpUP+zqWG2cQA+akXAppzsD4f3G2z4ZJBJ29NVeZSbk1VTU0trr4jmpAYr4UmdyoIyqkY2JP5ba+ip+A+D+F+E3k41KTxgAAo2GQ4AADdWf29Bg5A2ybiC92mLM09Mtxs7ExxtIPDrYQNgC/dsY8p5lwQMgjW9NyX5wMSjoy9ypJVW6srFmqHNqqUHkqIo807EdSyDeP1yuRvnA1Z7lUPEkRv1GldTVS88VVSTqztj4jFIM59Qp3B29M0fiWinqad6u2TLXWkkc0kaeeM9czJ1U/p6HUThuS628vTyBZaNjzinkBZHPZ13BQ/xAg9t9HnOMYlFXjJM0W6V8tLm7WioeqopMHmdcpIcbpKAdm32Jxk7jrgd2iEcRUFXLapPDdI+aopJnCunmyJI2+1hiBvuBtnUfgd6WStLWusWkkmZo5aGtkCiQEbhJMcvfbIG+e2jsVDZ7bfs3BKyz1cZZfrMCfu8HIPPGfskZBAPL7jocLHwNhnVwTmSbPHUV9EbTeLbJLUUxZ4ageV0X0DnOAPcYxkemivBPDtqguTmKqCGQEBZ/3bRkdj909TncdOmdCqjia48MXV1SYyQqMxvFlRPF1zGSMHHXBDDrrmqgqr5SPd7NI9ZTZJaSBOSop5MkhigJ28wHlOMds6wcBvSf+5YKVEOcXxw2eZoqoSvUxDnWQMVmVcqQgbBEi4weU4GCMnJ5RXaCWX9kyx2+q/atGGkmJMZaaJyhBHKDlckLuMgHDb40a4UtVbxhSyW66/WYq+jUNT1MZ6IepKHyt8XNgb7HODvoXScIi1XwM9TLSMkzCaspZCogJYbsuMqeowwC4BPOdhrdLwF2n1fzM2Qk7gMTrhy/VvDNy+v0zzS2ycP+5pqoLJAQFbybYJw2eQY2IDb9bBemoeI6+S4UlTRzusPhT0ctN9Xlp9/OzRsQpblaQ4yMls5AXGpd4tVmemlkFR9ar1wjTUaIjjmB80sRyrZAOCMnKruSwIp9r4duUV9WpttZDUzI/JKshKvjPLyuG3UdOp5dts6quLSSOf5mhJrAEE2qovHCd+lFIlfR0CSEyJUBmVhznDOF2XII6cwHvrSeIqOzXuwx3VaSnuI5TI89I/72NMecA4G6kg47qT9w54u4ruGZHHi1UE8a8kdJOmY5eUDKI+c/Cyjpgjw8gljqdwtduEL7SVMlPRRW64xHGacCNwceVpIMhXG+Dy+4x3Ixdgd1fXxNcD34g36OLNbLLdo621XeWnfBb6vVjMRJG3Ny7qRhvbr5tsa0nimshnpViuNBAniqHSc4kpjKqsFfmGNirFGOBsV3PLjWNccXKazXWoWiqSlSstPU09ag5ULsMFTkZdQcIWOTupI8z5g8E/SHfHqZqKsnMi1TOslO6LyHJwVxjl9cAj5EajVK53/TILPL4xkRzia+VND9bjSmoLxQUzhWRlZf3eAPiOcODkNsc5BAA1HtI4fu6EUM8tFU4D+DKOWTffytuGHsd/lojxrwzc7nVVF6tUFMOWOBjTHMaxgAx9STzcy5VskdskkjWfUCXCz336vLSTRU/icwSoU5Vdts9dtvMM/LbTGu51r55gjIpbIlyqqqstNLCayJ5YZZCMmNlkTpjJ6EH55yDt0z0J4p3VZEkhlABDKCrgHcZHXpq2WW9Wu52mSip5oJatd0iqCCHxnyb42PbODnG3XNTutPw5cJZ1klnsc6qrrLkvGy55c/wcpwpGwGR2OttLrd4wP3lLKfiEKO5VtOAoKV8I782JAP66nLV2i6IYaiNQ/dJlAYH2OqtUWbiC0YaRBXQA8rVUB2UjPUDt/fTsVaXjH12AOrfC4G+mteqyMGBtVtaTLhZoA5WkmeVxnkYNiSL/LINxriC73ihgFJdaOG80in/wCsDEo9PPggn5gfPU6kR4wslLMkqkZAbr+f/wA6kC4Upbkr4GhJ25zuh/HVTUlp3A7T+018xlGDyIH8KwXJ+WiuD22pJ8tLWjlUn+FuhPuCToXf7ZxBRHlNC5jYcoqEw0aj0XHwj3P69rTVWG318BaFl5WH2cMp+Y6aGQ0PENjb/wCja2QQDfwx+8iPsY26f9pGrkWoPUNw+0xK1PyODPOE+HqeBBVySJUynfIwQutI4c4ZlrXhlq3+qUztyoWHmk9lHp7nbWew32m8UvdLTLSTg71VtY//AGUZ835c2rlw9x1JTP8AWVrqW+ozBMt5ahPbYYH4qPnrLU2s6Yp4P3lqKQjZs5E1CKzwU/JTqFWkjwUiRcc7ernudQuL+NbDwlQ+LXSq9SFxFTQY52+f3R7nVc4n+lezW60l8y0s/L8UsXM2fuxqDh292KqOpJ+E4hxdxBPxfLHLVUMFupkyQEHNUVRz8Ujbcx/BVHYDY6Q6fQ26m3FiniNLdVXQmQfykf6S+OLl9ItzlItdMhQCOOSEcnhoGJ8x+2enXGN+vXVZoLzxBwvFGI62aoY/8uTLw49N+p9xgD37F1KhDTUcUYRPi38ie7N3P6fLqfG8GE+IxMkzbeIy5ZvZFPQe5/116BfC0Qeg4MRt4szn1DIjo4wtVxpVbiSzmjMjc3iUpHMf4ipwcfPI0SioaO8LzWC9UdQSMLFIeRkH8K9z7/8AxqrXa20DA1NzHhMw8sSN5z7sd9/979QAqKGvr96Dw6emiwQW8oXtnJ6n339B6atv1NHA9WJZa6LwSw25ls4h+v2CFoo7bUlz8VQy8yk/5h/fJ9umqoKYGT6zdXd3bdKdT5z6ZP2F/X276IwcdX6wqlNT1clWq/H46c8bD0AO4Hv19hopDxTwrdyJb1Yo6SVjlp6FsDPqVPX8c6BvA1jjzCQB7RhSBpa/6Y5+YIVam4kFwkMCjCBVwqj0Uf1/nojTQx08QjQYHc9yfU+urFBZLZcY/EsV8parb/BlPhyD8D1/LUGvtFwomP1qkljA+1jK/mNen8Op0tKYqnndbbqLGzYOJAADAhgCD2I1BrbTRVI3iCH1QAanrsSDrtQe+mD0pYMMMwFLXQ5U4ldlsdXFvT1IlUdFkGuaWpvVom8WFqqmcdHhkOB+RB/XVmVcHYZ04qjkLuwjjX4mboP9fbS27w6lRkHbDafELS2CMzy1/Sdco4RS3SkprjGdj4ykSH8f/nRKS/8ABFbOkdZDWWaoYbqE50B98DI/LVKvd5ooX8Oip0kn6CQDzD8un4b+/bQmht9SpFdVTCmQE4yM59QB3Pt+ZGvM6jxFtM+2ps/lPQ06Jb13WjEuXFNgqLrIost/t1bG/wAMcZMZVe4xvgdNup0Cbh2qsMPj1VvnmkxnITmQfMjt/CD8z20LqaueqYpbqVldQB4ynDfM42/AbfPro7YuJ+JrRAr1FaTBjHJUrzl/8oO+PfIGhWI1B32qZuCal2VkQT9SulyY1HKqA9PEODj0AxsB6aWrRB9ItC4Y1/D1O84O7RNgEfkf56WjVGhAwQYCzarPBEGzOGIVPhXp/fTJTmUk9RroDOu4EMrcqjGvSxIDtEikEEjGuh01JmEZPKo8qjHN6n11HKlTgj8dSWBzPD0OvMba60tQcTsaKZGD+em3TsfwOpGvGVeQljgDr7a6Gx3LqxzI/KQdxk9jr1RnYn5aYnuFLEeTxPFPou/66gy3CaTIhjEa+p3Oh7vEdPUPUYZVpbbOhCrYQElgB76i1FfSqOXm8U+i76FSF5PNUTl/bOuFkVfhQk6U2+MvYdtKxjX4WFG6xo9UtJVDaIKvbPXXdHWz2pFUTl4g2QAPNCfVd/06HTaRVMjfdB9dtPfs8iMlyToN/C9VrPXZwYamro0w2rD1PFT3GFfEnaV2/wAKUfDj0UAdsfD1HbI2UTU2m4LUtEwAGAQy7hgehGoFFJPapT4YMlOxy8ZOPxB7H31crZcIK+nUFyylsLJjBDE9GHQN+jezbsBRt09uy4Te7ddVupMDUljjADTtzH0O+ilJRRKMQxZx3I0SSlUHzbnsT0PuP12O4IwdPrEI8Hr6/PXstOatuU6nktQb9xFkhLS5GWfp1A1IggVfhUDI08Iz4nOvTvpxUwQR0OtcwYYzOUTtjTiIAdzv6a7IGflpAebOcHXCZoR8TzA14Rga75SCe4OljblI7ba4OJN04KnO2NcAddO7hMn12+WuWXfI/H31JUNjiMvH1PY9dQaqmRhgnB7EaKFdv6aadAfKRtrVHxOFT2JW54ip5CPx0Gqqaaln+t0Zww+JcbMPQj01b62m8QYxgjuNCpoCNmHbbVdVpatWmx4VpdU9DZBhHhPiSGqp46KuFRLQePHNV0Cz+H4rLnlDHB23ODg/Lm66Jb6qtuFTHc6esov/ABDU0/NHLFj6pYKFTjYnOH6gdSMlt2YDWI1lFLFN9aozySr29fbHcasfC/Esj08lFI7rC7I1VS+IVEhUnlyepXJPvv2OGPiNZo7NG+2zr2M9ZRqE1Cbk7l7vFzgMFPR0MbSUCsWpoJh562QZBqJsfYGCAvtyj/mMJdvpWtTTvJWLHeGT6zW18wytsibGJCAN522EaD4cqcAlQsPh4Mp+vxSUlTeqlGkRnAEFBCmxqJR0VUxhI/YZ2AD2mzWene2xXKYMtv53qaCKtbD10w/xLjVk9EXJ5VPrjck8wrMAOOprUn+tu45w5QGGa31EdGlOtORNbqKp831ZG61tSB8U7nHKnYEY7Fi90uYuz1NpoqqVLTFIxu9w8QLJVSYy0Sv0Gw87/CijHYDVKruI3utwayWT63LNPJzPM2FklyMmoY9mIJCg7RKD1diVKCSNaGChplpxb4IfEj8TIgkRW3ncdfq6sPKvxTyewVVyKljkzuC5wOpJuFclU0KwJFTUdNEj00ZiPhwxg4jnaPqdziCA5Z2JkfrjVS4mvdRTVK2GyRTvdZmaMjm8SSmMmzrzfbqZP+Y/YeQHAYl/im+T2qoFttwqpLxUyFw0i800MjjBlcA71LjYKNoVwo8xZll8GcMraoSHSOWvmVvHmZjyxqDyvGGXfkBwJJF3dsQx/aIIQBRkyzEn0L1HODuHIbRSMiiKoqp0/wCJm5S6MvNjkUDdouby7bzv5FwisSUulZUyzyWO0SFasgtX1jtzeArYVssowZG8oYqPuxoOUDn8ud0WkqJLJZZTJeZMvUzsoC0ScoVnYjyhwuFCjKxqQi7lueXb6O3WKxTVFbI8NDAeaaRsiWeTcdAc85ORgHK5Kg85kaK+ceo9yYyMDgTymitnD1kaaYNHRREjcAyVEhyCMA+ZmwynBxsyKcCaRm7PRVl3uSXy9xjxuX/gqM+ZKZDy+Y7YLHK74+7tjwo3atcFVxFWQ36503hQDa12/A5YkwMOwxjJAHbGANuRVV3q6aovlbLY7XM4ooj/APSdcvWQnP7mI75JyQTk9W65YyZ8k8y3BAPt8RSzTcS1Etstsrx2lG5a2sUnNSf+lGd/L5jk755vtcxMxtF84sNhIgkiQJUVUYytFHg4VNyDKcn5ZJ3JZyzh4KhOGrFGkVQsQMzIOZKGM5wT2aU5OxPfPQkuRp42opF4X4dBFfyeJVVJHP8AVFb7bfembsv/AHHAAGuic5xPKWijooRwrwqGhmj3q60+c0vN1JP2p2xt6d8AAasttstFbbMKamlNLRwgtNO7gtJg5dmZuucHmY+vYAA92K30VtopKOlTw6emBeonlbAyd3ZpD8RO5Zum2B01HasW5xwV89NNJbGlC2yiC4kuEg3V2U/DGPiVT0A53+yBwnMgnUuazwa2qppmoi2LXbFHLLWyjcSyZ+FQBkA7KMu2/KA8sU9M9TWVtYpq2wlfWwqSKcE+WkpV6s5JAzuc+Y+YqFfWUU8lbUVNVmrQCOurY1LLTgnalpx1ZycZwMkkE78qjqmjmeqXIWiemXCKMMtsRhvjqJKtwcknIQHv/wA7gyeBJ9Iy0ZjWXxkaSP6rJTDw4oYwJBbgw2ROokq5AdzuEBOdv8WZyR08AjCqs3KURY3JWmRj5lVurSNvzv1Odjrh/BDItNG0MUSlIl5s8oJyzZO5ZjksxyT67nPCjGmOn0PO6yLr9b7JPcZAGwAAAAGAAOgA7DXnKNe6WmYAAwIuJz3POUaQUDXulrs5FpaWlqSRaWlpakkWlpaWpJFpa9G50iMHUknmlr1Rka95dcknOuuUa9AxpamZJyBvvr0jbXulrmZJ5jbXmNtdaWu5kngG2+lyjXulrkk85RrzGutBOLOJaWwQQo0T1txq28OioIT+9qH/APuVHdjsPc7a4W2jJnVBY4Ee4jvlvsNsavuMjKvNyRRRrzyzueiRqN2Y+n54G+sy4rrLpWV9HPdolN0lk/8Ao6zRtzikPQNIR1k9W6r8K8p5nHEt0rqe4i83MC48T1YMVup48iOhRtv3an4R6vs7eqb8oviS9R8IU9TK9THVcR1K+FPUBub6sCNo4gNi/wCi+2hWc2H7TfivgcmWijntXD9NVi6XcxPCq1V2ruUMecf4caL0Zs4CJ0B8xBwqioWqOu4yu0t5rrPUmyQvzU9A0mRIQSVM7tswG7HJCg5Zs7qwjhqwzXSSmreIxNMjnnobVE2XmJ+2fTuS57Z5e5Gg3C9XmW3Q8N2WKmeo5vKtKoSlpN8cwP8AzHHTnYkA45QTuQXOCQOpuhGAW7georYYbsTcZxcK4NmOmiXmSMnpyqww7dPMw36KgGHWq8XXVL3xlU1cUJihgjWGNPFEh26kuB5mJLEnfc9T10Vv13tPBomtVqamuvFNUCKytl88NGDnmUdeZuueuT126020VYiroai4vmnqpgZJsfC3N9r2OevYjTDwsKuoDt0ILrw/kFR2Zo1DD4FLFDjdUGfn3/XOm7zbIbjRmFyyMCGjkQ4eNx0dT6j/AE1MUDGQQcjqO+noscu4zr27FbF+xnlq/wCmcjsRjg6+TSTSWu6lVuMC5fHwzp2lT59x2OrJVUyzISuM42Prqn361tWCKppZTS11OeemnA+BvQ+qnoRotwffludPJDPGKasgbkqacneN/UeqnqD76A9VTbT+h/2hZAdd6/rGoaqt4bvDX62RNOrALcaJf/rMY+0v/qr2Pcba1mz3Giu1sguVuqEqKWoQPHIvQj+h9R21Qq6l51LoPOBnbvoPZbtLwXdZasB5LBVSc1fAoyaZz/8AWEA7ffUfMaC1umz/AFU/WGaPU/6Gmwa9AyNcU80U8CSwSJLFIoZHRuZWU7gg9xpwDGlcZTwD10uUa60tSSeAY17paWpJFpaWlqSTzG+de6WkNSSLS0iMa95dSSeaWNe8uuhqZknAG++uuUa90tczJPOUa90tLXMyRaWlpamZJ5qv8aWFbxbn8IFalVPKy7MRvsD6jqP9dWHSG2rI5U5E4wDDBmW0szVUK0NUifXIxjOOVXAxuP7HofwyGjtdRceIgvENzmeBFCRyOxLOo6Jv8AHTHffrzavHHdhc4utExjkRudyBnlbpzY7qe42/tW2SHiCgqI5RyzofDkiAwUYDr7+oOwIP5NEZblz7xdZWyHEH3Pimkp5P2VZGeipZFEaSxjIDdiF68p6E/I76E0dlhp0+v8QMhAPMsJbnXffJP2yfy3J76cpoKbh95XqFaquBP7t9vOM9QPsjPX315akm4gqzSzoSIiWSojTMdOT1Uj7QO52BIPqCV1wqKee5krG446kn69NfEFtVp6dSSYOdv8VfuOeq47Mfkdwdahw3wJZeHbK134lanfw0DcrY8OPpgD1PTf5DfA13EOFvo5sK1EbRXC5VKDlbIaSbI6gdk6foM9BrOqq53HjKd6Mf8Oadi9OE5jSxKTurD1AzhgMdiAMgJbHs1ROzhR2Y2QJQBu5aTuMOKxxQEs1FPU00EblqaGdwPrIAxyl+q9+XmznoTnK6s3A/0cUtBR/tzikxhY18RacgBEUDJLZ/v8zsNKmsXDvAtje4XNo66udeUlsEuSPhUemP032GqVdeJ6ziX/6HPi0qr5qeJZGMWB0WXryjuD0GcbeVxNrMuyg4X3M5uVTuuHq9hD/Ef0g0olntdinq7ZbpTypUx+YI+eqJ8QQjrynI6qB1Yj9G30bPcFW6XeSNaINzL4cgbxcHrzdOvf8ATOSY3BHA0dKrXK6Sx+JEnO80hCpEo3PLnYDvn8dtQ+JOP6Ojmmo7PFVQW+Qck88MpV5X7PGp6MB32LA/Z2bWdlWwGvTHJ9zOo5Prv69pa/pA4zsPDUqUfD9Gn7QpcKzRPyKqDqsh7nB6HcZySvfLpqer4wuTXKjuEsyz7ztP/wCYgwdlCgAFd9mXy79FOcy7DwZVXetV5XFVRO2YRECPFHXMmcFCM7qcYP5m4X6ssfCNIKbwxV3XkzBHBIY/Az0II3Ue/fsrddaV1JpgNnqcyrM+ozv9KxUFgsHCVk+sXuNEg2/4dt3mONubYkk9lAz8gNULiDi6O6mS0ymst1pnk/4dUkMoUeki7sUJycAkKd/PjUe63Kt4ur9pi1yTEfgTP+6wdi0ZG2TjLIdyc7sNhd+DOA6a20cl8vVSIYlHNLUzbM2Oyj7I/wB+2tjWmDZefV8THzHyK6h6fmUvh76OK+uqoZKsQ1dMWDwxQuWicZ+LnHxf07gYxqzXviXhThFZrdDStdrjEMrJGwU0zbAguOnQbgdux6Q+KuPqWOdoeGLR9Xt3hslQ/jmJqkHqwI+Ejs3c7HIONUGotYucJrOG6kSUucTyMP39Mfuunr/H8J6jHTQVmgfUsGb0/abLqUqBCnMkcU8TT8V1lOLjclp7lEvJC08pFJJ3AJC/unO+Sfi9V31V0sVxprrG93WSnrE8hpZQPDdfRSPKBjcdQeoOi1A0doHhJQU8dQq+HWpOS9NVLtgsp3D9eh3zkcpG7lPVzSKaGeilltrf4MDT4nplO/7p225T91sqfnrF6vKO3GMTXzfMXOYKq6CO2Xfmtjy0Fem/7t8IAdxgnqDtscjPr0LlyraO4sKarhpLbdNw0ioY4ag/xgf4Te4wD35e5+wcIVl9qYqWwzR11M7com2SSnx1Dod1PXff2xrYLT9FXDlssXh3emjusmAJ53Xl5R1wuNwfzP4aX367yTsbmbpWSMiZd9C1r4aqeLDbeOVekqhyilinUCnqfTL5xjpgdDnr63n6arVwdw6fHpKqSnrnQAUsBDh+wwCRhRudzjYBSMHVG4orrNw7cZLbYXiv1nVsGOrXIgJ+wjocgnPVeh6DqdV+smNRJLV2tJaykABqKKpfxJoANt/vAdAy9O+DrAUZfzEY4PYmu87cY5k231NdUT/uoaOvts+WESR7Lk9Sp8yscHJJyTnBOdWzhO222K5QVNsub2yWYFZKacF4plI8y7YzscgjffoN2F1+hPhPgXiazNW07+POFw9GWKSU5IwSzDDP7YwuNsHfUD6RuG7FwXOHmu0E1HNKgNPMoMgIYYAIznGAd15RgfBtmv4lbTs24I9jLLWwG72gVeMX4ZvUsdRTxy+BnxQHD8yEbvtgHOM5yG+E5IG649v9FXot34fYyUhXkeaEl/q5wDnnOGPQAcwG2RgAZYHe5Ke5uP2hZZPqeW+p1kcpkdUxsrS4PMe++Rgn0GoVjsFwtEzV/CdWK2JsfWKSTySkZ6cvQ+uPXA36aIVcEH3/AHnS2QRPbLxJFUmS2Xe30juQ0kVWlLzLy8uOdghBA65wcdwM76VdZrpTVdHcHrJ4KnnXwqyE88c4ww2bp1G4bl+IKAcaI01XZoq7xvDS2VMbmXleIiIsMZV0HmUgAZxtgbr1GrzezQXDhlq+xpI86uDNDTGNiSSM5AyjxnI82BghcgZfV3cfH6+8yCmDuHaKTiqkjF9q6eCOBRF+0KZ8wxMysCkkLdDluqgKeoyRtRuNbFdqK9MaFoan6rLz+JEOWTK5jJZT5lBKkY3GwHTrw914aa7U9PcGrIKUsGjqKRjHyPgAgoeYKw2G2cgD4d8W7jGohko6OopayC5xMyxwygGCrZmVUySCBnKIO4PkxnD64AVILciXHqUiQOC7lQ3yjnsN2ooKeeaMrCZ1LQCQfDsegO4OCSM52xjQus4VtMVxl5frVsl5CWhkkxgcxU+YjsQykHIyOuNdcHcbSWiukpuILfDVU5ABmeIcsiknHPt5SdvTfqDorx6fEhjuNF9bqaWaFzMGbnRcc3ImRn7OFLFQSeTZcMWseTjtTK1jA7wZdOEbZdIbVUQctPfqSJDHJF4fgVKRsMNG6Z5XRh9oYKsqkA41S+IP/o+ZaSlrKa6wmFpEiq0KyKAwCjOT5iMq3TlZTkY61PhX6QLvY73ErV9XNT7eFIjASFCABn1IA3HzznWgcV2ebjO30VdbXp2kaaR3BiKNUmRQGVsfDnl+yPiAOOY5ONYNL4B4PsZZirLz3KRaG4Wu8zMEe1VviFSjy8h5+4WQbH5HHyOdM8W0stpuUVOJXqxMrcsk0RCNIBjBbABEiZRthuFbVbvVsvFsrEnraGWKpdeWRzho5CD8eejEjr0OcnvrR+Bav9r0BoXjE+AFeOSMNG5+6A2+cb4/LOjWtrU+riDAOv3lE/bFdQxJdrPX1ERhVGlA3WanJ5Vd0OxZSPDb3VSOurZw1xJSXWHNfRQxSOciemGY5N9ueM5x8/5akX/gOjpaWkr6WdbaZppaZ4GBemEpGGjbO6c64YdvxGqTS2HiLhi5LVLAZEGDFLGRJGw3yo2IOR6j8tXNrbcryJYoD+cttwsnEdLGbhao/FjYZMEZyrNnfGdhgYGBk/nqNT8QkO0FfTtBPjJjcZX8fT8dWzgXii2cQ0snD9aXtdVWLiGeJigWUdGG+Oo3wT2yMaG1Fe0NfDbeJKGKpnhc0slREvJKk2/I2dgQ4wBjlAOCdmGL6bVY46MpZSSJGpUgkYzUc70r4BJiPMn46nR3KvplzWUy1MY/5sPX8RobQ2CGaFKrh65uyyOW8B25J15Th1wRuR3yOvffVys9qT9lS1DNTyQU6c0is31eqUnooXBWUntgb/eGjP8A1E1fUOJiNKGHBgN5LTcYiW8NiOuRysNV+6cP09QWkgZhIvwPnDr8mXB/DViFNbbhV+EkhppCcLIU5WHzXPX5HXn7Nu9DzMgSuhQ+Zl3I9jgfzGiPxVV45EzFTp0ZVlq7/b4jBUeDdKXGDHWIMkezj+oOm3PDVxBWqNVYKhmw3iHMUntzjIA9srq1pNSTELKpgcnBVxt/bUeusdPUoWQeU/dOQdbVVsvNT5mblH4sWVm4cO3SnjUUSQVVMd0kgfKKPvcucsf97arFbcUoZmgpUklrOjySAhh7Adv9/D1Nuax3C1ymezzzUjZ3MDAKfmhyp/LXUt4aQqvEFjgr8DappV8OZf8AtJ/k34a1OpZeLBiYroUJ3IcygvAkZ+s3eVnkO4gDbnvv6f72PXTbPVXEhV5YaZfhAG34ep9/1OriOE7BeKhpbPeGabP/AJOs8rg9ehwf0Oo1y4dutvz49MxUdCgyNG6Nare2g2qaykYC/rAVPSQQxlFQHOzFhkt89Raqy0NQc+F4LfeTb9NE8FRgjfSXfThtNUy7SoIitNTah3BjmVuSzXCmPNSzrOo3AbZtE7VxnxNZSI5JpXiXbw6lfEQj033H4aJa9aNGUoyhgeoIzpbZ4WndZxCk8Tf/AFjMm0vGfDd02vFmNLI3WejbYe/L/c6JQ2i1XJeaw3umqc9IpjyP+u/6aqdTYaCZWlK/VwP+YNgD/U+w0CrFaLNNaFeplbZpW+M/LHQfIn/N20C92o0jYHq/KG100atdxGJd71QVdlp3mrqOcqo6opZfxI/l/LVIrLjc73N4NMhSLPKABjb0wP6fj66K2niXiu0ULR1twkigA2Wbzlx6KCc/jkAeuiFDxjwvdYpKe+2R6UMAr1FE2M79xtkexJHtpTrda+r9JbbGWk0temGVXP3lYRKC1DClaqq6EjdQfw+L5Db1LdNS6K0111k8euZo4gBkHAPKP0Ufpq4WnhLhuoqGmsl5iqZSOYQ1Tcko9tx/Q69u1rvFGRHLb3CruCozEvv6k/P9NX0HhtKjcTkzHWa27kKMCDIY6S30wSBVRR0crnP+VT1+Z/LvpmWhNeWaoQRw9WLHLH3Zj01Ljp44XMkzGef0zjl+fZR+Z9u+uJKiSZuWHD8p2bGEQ+w7n33+enZrXrESl2HJMHS2S2c2VhOPV5OTPyGP5/kNLRRbZFu1U6GQ95M5/IA40tCtp9NnnEIW3U44B/tApxnlG/rp+Q+GnhL8TfEfQemvEHhJ4hHnPwD+umiTkljj1OjgcQQDceIgBud+UfrruGLxeYscAdT6agVF0ooTgy85H2U31BqOIJ3Tw6OARqPtNuTrG3W01/UYXVor7fpELTRmLdsY9c6gz3KjhBHi85HZd9BJ5qmp3qah274zsNM5hT0/LOlN3jXOKVzG9Pg+Bm1oSlu08oxTxKg+8251DkaWQFp5mYemdh+Gmw0j7Rq3zxtp2CgmlPmJPsBnQ2zXao8nAhoTSaYccmMh4lOwyR011yzyNhV5RotTWnADEKo99zohHSwohKjmYaMo8IrXmw5gtvivskBQ215N2y2iEFBDCnmIz6DUmTxFO2QO+NN4OcgddOaqK6h6RFz6l7OzPFRQuF210gIPXXuDjm/PSDKRlRk6JX4mMj1VMGyyqPloUDUUNSZ6bcMMSRsMq49CP66OsxIxsNRp4VkDEZz/AD0u1vh9eqXDd/MN0mrelvtDNjvMFZTYZiYxjm5j54j0GT6ejb7YDZGOU4m+FY5z0OOvsfQ+34gkEE5o8U9HUiqpGMcqd/b0I7jVn4Zv0dQnhMuCoxJDuSo9V7le+Oqncdw3na7b/DrPLs6/mOLqatbXkdy0qvKMA68jGGwenrrlJcoHDBo2xyvnPXpkj1wcEbH2IIDgORvr0dOoS1dyzzd1BqfBE95Tg5PTXufJrwdf6a9z1GNbSg5iUeU++uttgDrwDYg6QA767OHieoFLDIz6g69YAHIG2vFGc696gj01JXbmN7ZOuMHB5uuneUjqQR21yRlttdBxK49oywB3IGoVVTI4O23b20RK4Om2Qb53OrqxE6VwMyuTQlCUI+R9dB7jRSLIKqlYxzJuCNW+ppg6sSDn00KqYCjcrDHvrt9FWqrKOO5rptS9LblMf4L4nEcyw1cQliEiPU0TuyxzBDkA4Iyud8dvlgjTb1xLVX8xUNrR6mtrVTxXaEAKRsBybgKhyscYyBu7eYqBidxoSWE9OTHMm6svro3wbxPPTVPgTExvy8k0QJUSxn4gCNwCNjg5AJxtsPC6zQWaKz1cj2M9bp9WuqTAOD7zVbPa7dbKP6rSxRTiUN400kpC1fJ8YL/ZpYzu7j/EbyLtlm9vtxqaB4oqKOSqu9WVnp45I+V8gYWplTomF2ii6Rrhj5iMRm4ipFtkdRSqlZc6tkSKm8MKviJjkLKMhYIsjw4gSCcu+ThSZ4fopLWk5nqJKq9Vbc9dVc4Dqcc3hqzZCsAeZnORGp52yxRdCFieu4WR/oWD+GrBFbGlqK2T61dpS5qJjJy+GRu6K/VSAR4kg+AEKuZGwhK83GahZbRaQrXeYBi3KI1pVVTh2GcIVXPKmcRLkkmRmIau1xW1GK128RT3upC+FAg5RCi5KMVO6KuSyqxyMmSQl2/dv2a3QWqkmmmqcEDxq6ukO7EYbYkbAZUgYOMq5BZoUGoG0ZMgA+kdTu1W232C1SVNXOYYIj4lVVMCryuMdPtAgkYA3XI6yMBDEpKep4puEF0uFOYLXDhbbb+UAY3AkcDbcKdugAIB5VdjDoPrXGV0irZ6dobFSNy0NIwwahhzDxGGemzd/vANnxZRYp6h6q5m0W1mymVuNdGcCnT/AKUZwPOeUAkAcoX7PKqwVJIOT3Ojnj2/mPiKS6yy0tNM0dFGTHV1K/E7d4Yzt78zbEdBg58OXK31eoSxWCKGKuVMvIFHhUERHxEdC5HQficAAM3cZ56XwrDYaeEXERjwYyuIqGL/AKknvtsOpOCR8Kg1w9ZBbaVqClndqlh4lRVOoZ+c787Zzlz2U7KNzk45qrxyZzkSNBEtrA4e4c3rmHi1dZN5/q4bOZZCfikbflQ/Numj/DtvoqKllpaNwkMDM1ZVSPli/Vyzd27sew223wNoLaYUmsVkqpIGUl7pdXIZomO7AMdjOR3PljGD1wASpbfQ1VupYzC0PDsJAo6Nc+Jc5Achmzv4Wcnf4zlm8oAOhIEg54M5qaiK4wRVNRA4sviAUNEoxJc5RurMDjEYxkA7Y8zbADUl5JI5qqWerEdWiiO4V8QJWiQkYpaYYy0rEjJxnJBIzyKCEIE9zlfxI1roU5KiqQZShQ4bwo89ZDsT+DEfCpiryidGSKOOGmZvqcKnKw5JzKcjLStkksfhyQNyzNaup7uFEze9KhkxQ0/1eCKV4xRTRJy0FIuGFAp6u2chp2BOWOQucDPmZ0gCQpCmVROgyTuTkkk7kk7knJJJJ16zEkkkkn115pxTpUqHHcT3al7Tz1FpaWlomDxaWlpakkWlpa9Azrkk80tdcuvQMamZJxrrl99e6WpmSecvvr0bDGlpa5JFpaWlqSRaWlpak6BmLS0tLXMy22LS0tLUzJti0tLS1MykWlpap/HXGP7LFRbbM1PNdI4w88sp/c0KNsHk7s5+zGN29h14WAlwuZ79IvHNDwpSrCiLWXacf8PSc2AM/wDMkI+FB+ZxgdyM+sP1q4XFb94tPdq8SLFVVcq4Ad8nw4o88xRUyqgcgyzHJODoLNQ1d2juNXAZ5EQiSoqKli7yOQFDuRtztnlVRgLzcq43Jmy31eHKO3WWyoldfXjV44KXzCN2+1I+OpOGPLkkYUMgBLC6hsDBm2mJLEr1LLxnxRScOXGW6SWinqb3VgRU0EcoQRgbAAKeZlG3NIcAkgAkDGq1beCawU9RxpxHHSQT1Ep+q00ilaeBmJ6Ics2Oy7kkb53APcPcI0vCkKcR8WSG98R17hoaCOXM0jddz/y0Hd/Tp6mx3KlqHnS6cVVdM1wSNjDQxeWKhiA+EDpGAMczHzHYbA7gm0g+mElAYC4TqKWgujz3Knqa5JCvj52lqDvyxsRv5jj90pwB8RbBC1bjvj+R6irtHCgp6aaRz9brICOSnByCiMNmfG3MPKvRe7EbxvxxLf5DYeF0+r24Bknq0TEk+chghxlUO4ztkdt2yBt9vjQx08SZXPKiopPMc9AOpP8AX9eIN2WMysfyxgdwXLFFTIsFPG2VHM0rbs7t1JPy1aeGrfHVJJBLGHiWDDK3Q52x/PQu826ppLpFT1vKtRKPGkjUg+ECcAE92xuf66uXBNIDQTzt9t8fgP8A5OvV+B1IEZ8faI/E2csqZ57kGw1ktlrI7HcZGalkPLQ1Ln4f/Sc+voe+rUnlOCNxofe7RDX0clPUJzI3UdCPQg9iPXUDhq5Tw1YsN3cPVKP+FqCMCpQdv847jTFT+HbH+g9fb7QUr543f6h39/vLIDnbGgt6t9THUx3e0lVuFOOUK3w1Cd4m+fY9joyQynA66D8Q32KjgengZXquQknAIT0z8+mNbagIyeqZ1MVbiHrLxNbauzrWvMIVyUZJNnjcdUI9Rqo8WXeouHOlMrRU2MFR1f3P9tU6aaakrjVEvMJyTMp8xOPt/wCYZ/Hpo5QV08gjI8Goc+aN+ikdjkdfloDT378o3f8AM5rEsqw9f0/xLh9FXGJsFathukoFonkAppC21FIx+An/AKZJx/CfY7bco2Ovlympo3CUk6qwkdo5FPdTkf11qf0TcYSwzw8IX6oLzhMW6qkO8yj/AJTHu47H7Q9+qy+koxYDiONNeHUAnmalpa8GvdYQuLS0teqNSSeDc6WN8a70tTMk8AwMa90tLXJItLS0tczJFpaWkN9cki0te8uvQupO4nOlrvS1J3E416BnXWlqSYnIGdegYPXXulqToGJ46q6MjqGVhggjII1m/FVnlstyNbQKSHBKb451H/LY+o7H/XWk6j3Cjgr6R6WoXmR/zB7Ee41tTb5Z+0zsr3iZVUUFJfLMpMzSHOTLGfMG7kbZGcbrtrg8RU9gtQt9uolpq6Mcryn/AA0GNnX1yMHr+I2zJuVHPZLjKZI+Zcjx1TYSJ2dQOp/mMj0x5d7VRXKnhqB4ZEfnhc7oufUdCh/TPzyyIFgxF5BQ5HcG8M2qu4qRjXLUJTxHmFcEy3hknmVgB8G5IIwRvtg4W+Xe82DgK0rbbFHDUXArggEeX+Jz2Ht39MebVQ4p46qVtUdltkH7IhjTw61gMO8m4KqdzgjfO537gEiJw/Yam/UcZu8UsUUA8khPnkiHQS98DAwc5A2OcBgteovy/CfE3S0JwvLyLFLW8XSOZiYZYjyx1qpiLlJyY+XO2OzDp0OcB9Wm3UFq4Yt3j1GYlLbsRzSzP129T+QHcjrqRerjauFqRaSkSOeuC4WFTgRD1fHwjvgbkb+UebVLpJa3ih2hduSaIcsVcI/3YHMSYiPQZJUjYdDnZxZSWBFfC/MqQFI38tJddxJLe5v2G4kp6d3MlLHEWZYmxsJQBuhO+QByknlGN9GOEOC5PrK1VeEnqsZDf8uMHfyevz79dP2iyW2w216mqcU8IP72aQ5eVj2HUknsB/8AIW98XQVazWwiW22upIVfDJZww6s6jOUb7SDYdck5GuY2ErR+s4MMN10M37jG32aYxWKMVLpkVNUJeVJF+4OzYPRugPTm6aqVJZKriGrNVQVUstFO2ZJXyannbOUcHcN/F0bqDjygrwnwLX3WujauWOSIYaOOOTmhK9nL/aH/AMbdBdOJa2xcGweAqPUXkIDEYn5GQe/3U/zA57A6z3Jp2Ar9TmXVWuU+ZwontLw7ZOD+HWrrxTx+Aq5Wl5v8Q9gT3Y46bnv21nF/4rjvwiobvNJa6dXIoy9QZIFydklzv8nycdD0xpriu+1vETyXCGeesmp1xJRMwH1TPVgB1jP3vi7N0wa5R0PiyePVsZZGGOnb0A7DRej8Pe/Ntp9X8QbVa5aMVoOP5kma1VktWy3ZPqsURyIA4POOzFhsRjoRt6emnql4aVklpfFpq1F5adoNnK/dYb5U+h/Trrumr0pUFC8ctXbEzhVAZ6Rj3iJ+IesZ22OMbaTW2dWjakH7QSqyIqhASkp6YPcEd06+udtGm5QvlsIGtLBvMU/pG3WmvUkMU6R0dxAwlNz/ALioPcwsTs5+6xx1we2rbwN9Ht0usZW7wSU9pU80PMSJUb1XI/AkjGwwARqwcFfRjEI1r+JIvrMkmCtMVzn05vT5D9Omjl14qs/B9QlLBXSVEaj/AMqwMoiH3g3UKPQ5GOnTXlvErBbmqo5PzHmkTaN78STeV4ZsVpNRcaWOmWmGI5gSkrejc482Tjqdz6HWdXz6Qa/iSzS8L0FfFTwysCjV8fLJUR7eUyKSqknsRlvU7jUHjW6XzinieO5QBYXKfuBSuXhKEbspOxyDgk+uMbAauH0ffRTF4a19+VUpSOcwOmC+fQH4R/EfMewUaRtQNGmbuT8RhWxsPo6ld4A+imtuNYKqppnpYSAXMuQMH06Zz1wNztll6HRLh9D/AAzM8S0Ek1tr4h5KxGIXn7BgMAZ6ALj3z3sk9BScN0gntd1WgptmNJUyE07L7E+aL2YH0GD01UfpY+kCjruEqensEdXFJKeV54QCqEg5UEd/ng4/LQQa6yzfWYT5aKvqmfcSVVNwlfpKQVS22/U+Q9dQENERv5nVcEe+2RnooGDS79X1NxuRk4tkerFTvBcIZBjG3w48hjAzt5SCdvQn7BwdW8QzJFHFJUyMefxFOS253JOx6nzHyjsGOrVU/Q7fbTTObVLBdoXTxKu3SKTzHuVz8R/iGG9iNtHJdWzbSfV8zDYccDiHPo3+ix3sUNwp788MUsavSNTt4kbDcqSpOwGfXnJO5A8ugHE/A11sFUJKtGRF5hBVUb4K7MScDDHqNgMeqsNyuFbtc+BJDNYJ3eFyfrFkq5R4nPjogOMnY9N/XGQNVD6SfpIuXHElRRSTtaadRg0rE/vOXJPO/bfouAPfIyc66bUbaTuU+/xLl0xn3gri7iK2Xe6i31lbPJNThViuMEQ/9kiHHMBk7rygHOFHcLTtxHw3VGuoalZKKdskwsWhc4wcfdOxGDg6FS15nqzQ3qlkqivl+uRHlnj36cx2kUejb9MMNFbfU1lppmnpKgVVBIAskwXmUE52kQ/CemzDB7Hvpui1lfSeR/eDMzbuuIYp7fZr7aGutDKaUxzLHVU8qnkhckspPUpzefGcrnI2yM27gO3SBKi3ylIKVIQ8sc5LxEcxw43JHQA8nMMEElSQAI+j/iOyXPxrJX0otlwmCpHU0wB5jlWAGfskj4TnBAIydCaniS/8N3wGBFjko2AEMlOEEig4D8nQHGM42OT1wScHySR+/wDzLIAZbeK+FEpm+u0EpjpmPLHK58SIAszAFgcg8wcHORlARgEajcHXbiCw3IvdqJKy2SHeSKMckYORsV6KRtt02IG2pZ4roeJ7FJVWShe33qBOcR0sxjjYZ3PISACRgHt8J+yAahYr1xBw9xHm3SO6+KQ9OV5QGOOin4QwPTYZJG+sgm4Et/eXOM+mW29WaytXRTV1virKWYM8dRA3JOyjcM6DbOCwJGfOjbEEDVo4DpJkoTT8NXqK626U4ajqW5Zoznqrb5YEZzjmyNlXQ7iShbiOgjlNtSC6JLG08VORHIqkBTyrupLDlPlIBKIdty2cPVV3C16W4007RT8jNPSTwkBmBA+HfY9euMEbg7Dm4EHfz95bGTkTTOOKV7XK0rg0k1RMn1m3VMYeJ2fm5m78ocDnXH2hIM7AGuWS5cPi6yRVVIKZyBzp4pEU0edisg3Tf1xgnrqx22+r9IHC9bQGtjWrkpwpWQNJJGqtzDlOQWwwyNz2AI3BznjLhK+2ieXxqRlEUiyQTU7c6gMMspI3VSTzjOQMnc51Km3qVbkSOoJyvE1+ooYxY7jLHc6q62uSmX6xR1ChqulVSSkqOCA4Qkn/ACk5Y7DWZ1FfcLXNV0tvmamczkrSSjxFaQqW5SMAYkUBgfKeYEAbnVg+hq53G5uLNV0S1LoSycmUkjXuRjbHy76sX0gfR1JLPcq+21zw1Eyx1DCsXLNh/iUj4SHYcxBxgqSPSVWKlhVTIy7165ErXBl+sN7VhJSU0NQSolidAyyZ9O6t1G+cY66nfSRSUy3CKOijrI4apUgq6iuXKxxnOMSAkrykDzNtuOuNqLdbJU2m5VM9bRSUEjSI4qEJGWGSQCBykMQdjgg8uNs60LgX6QoZoJbG7RzSMoCSVMH7wrjzBULE/MqXPyGq32hX9QnKwcfaZelVI8hpxU+JIZ1SWcNgR1IB8OcHssqjlb0Iye2iVh49uhqWor0sV2VWPix1CLFKhzjyuBjIPqp9sY1e+NuC+Gqy21tc4e3tyhpp6FOZGiJyrlBvsRhsAkFc7AgaoN64Dub1sdb41PVW+UR5raZfEVth5nVSSMjBIGffrogWbl3IcypT26l6mt0d6tyvZzJLITgwTKBJH1J5WzvjHq2TjbQzxL5YpV5ppaaCIBpo6kkhDnB5WAz08xyFPXAONGeB6makp4pqVHoqVUEOJX8UyuDg7hQUQerg5yMY66tV0qghp6m4wsaOMMZY1AKvER5ih33XAbCsCRzbZxoavWAtzxOLWQMSHDcOGr09PDf7U1kE0f7qqclllPqHA7jfLA++m7jwBURu8nDV2hrY1weRXBGDuBnPKfzGo12is0lLRvBd46GmnkL0gknV4nZTgrj7PMp+DAJVtzsdBa1uLeHLq1bZykEErBXFJuhOdyU+FvkucDGxOSTKrblO6tszjhDw4jFcayjqmprrSTRFThgFxv8ALSWmt9fH4YMcnsRhhp6y/SgJK6pp+IaUyvz8s0UkKlO+4U9BsdwR8tHqWycOcVRyVFpLWydV5inP4kePXHxoPnnTWnxUjiwQV9JnlDKHdOEYJ8MnK3L8KyDOD7HqNRIn4kso5YKt5oB1hq18aM+wb4h+Z+WrlW2fiG0wifw0uFF1WeE+IhH+Ybj8dRoLlSTfu51MTdMP0P46PQae0blOIMTanDDIlVluVguAK3u0zWyU/wD1in/exfmNx+I03Nwf9ag+tWOvp7jB1BjYE4/DVpq7HRVI5kAjY9HQ7artZwrU0lQaqgkkim6+LTOY3/HGzfjnRaW6qkZU5EFejT3fUMGVmqt9XSyGOop5I2zjBU7/AC9dRK2spqBczkSSdo1OwPv/AGH4katUl+vdJ/w10pae7wnYiUCGYD5/C35Loa9s4Ou1z5oppLRUvgiCqBCs3zPlPsAdWbxPf6D6TMl8LFZLdypclxvjl2bwaYDboAF67e35D59dd1FZb7NH4FInjTnq2Mkn+vzO3sdWDijhjiqBRHR08UlId/GhbmC++OpPvv7Y0JtlppbexknDT1WctzHBHzJ+H9T/AD1khZidv95Z/Ry/9vaC4LTW3WRqq5s0cPxFC3/2xOpc1st1KA1NEscuMI5XLZ/hU/zP5DRFqiSpkCU6h8HAYDyL/lHc+/66cjhhpy0jsJpx8ZY7D5n+g/EjVzpaiMMJh+LtzlT/AJ/n6yqS2G4vJ9aMvKObdnkIO/qRuT7DJ0Sp+MuIbCFgpKyonjT4o6peZX+Sn4R+vy0TM01W+KfLE7eIy7D2Rf8Af46U1NQUSk1Y8aZxkR/E7n39v95GgrdEqDKNiF0a13OCuZPoeMbLe6dxf+HTEFGZKikY4B9x6+2dE6SislxgJ4YvtK8x+BKkcrL7Y2/T89VKKzVt+kWlggaOMHyRw7Io9Se59/56N0n0VVkFMZqeujacnOEyMfj/AKY0BZrdTpx6xlYxTS0XHI7jsvBF3aVvrkAmk++5Bz8htge2NLUGSt4xsMjUIr35QcgEk4/9rY0tZr4lpyMkfzNDorM8NKJVX+oncmnhCZ6FtyNQJpKmoOaiZmHoTt+Wo/jjdY1z6a7ihnmOSeUe+p5mt1XHQm6UaTTDiL90nTB/HXImd8iJMk6nUltLZBVmz6jbRejs5xv5R6dNFU+Dk82HMGu8USsYWV+KkmkHnOPXGiFHZzn4M+7aOx00URwqBj66f5QB/M6b0aOqsDAim7xJ36kGC2Rqvm8zdh2OnkARcKoA1MiQSAu5wi9fX5DTciiSQk4Un8josDjAgIuLnmRxsx5hnSCnGemn/hLLy7j102WLE8xz6aqPvLgGcFQy4bTMi8q8uMafUkH19RrlhklcZ1cZEsBjBkJTuR37++uNwxI1InhP9jpsLzeUkBta7sjiazwYOTpeuuQOqscHXSHqG6jtroOZI1LCJFztnQippXim8aEmOVDkEbEH20cGuJolkXB6+uhdVpK9Um1xCdPqWpbIjvDd+Lv9WqByzH4o8DEmepXO2TjdTsfY4ItdPLG0XiRtzRfqvr13xv33Xoc7Mc5rqNhkjyt1GP5jRPh2/wAsdQKeqflmyOWRjyiTA2DH7LejY+YIyD5V0v8ADbPlfmPcVa6vHvLyPUa9B2JOo9NKkkZaLOAcNHjBU9cAdtu34rkZCvRsGGB5h1BGn+m1aXjInntTpn07YaODB+Wl20gMDbS0ZMMT1cnONtegkrldJT3J216oKnIP4ak5ONyM69I7jXpGGJ7aXT5HpqTu0Tg55TkDOucacODnXO3QddScIjLrkEDf11Fmpg6sG3B0QznJGmyM5x01cPiUCiV2opjHnIyOx0IuVvEuJUJSVTlWU7jVyqIFKnmHy20HrIPDJwMr/LUtrXVV7HE1quehwymM8H8S1VuuEQZhFUxfCwUEP25gCCM+2Pceh1eLidHoqdLJTGe51jBIouXnCebmHXPMMnmGSS75kc7Ioxa50CzKSNnHwsNEOEeJKu31qwzPyTjIVu0gOQQR0Od8g7MD7kHxmt8OfQvk8rPV6PXLqUxnBm2WW1QWyGetqaiOerkHiVlc7Ar94gFsjl+1kghtnYFBGssamSbiuqWWZJI7JBJ+4gOQ9Y+T5mzuBknAJyOYkkuzMsSjrpeNKuGhYLTWymRJZoklLSVcpPXpnHNv3338zGNUslwq5oZf/D9g8MXLwwJqhVHh0CHYYAyC+Dt1xkdScuGTu5h2ARj2nVXLPLUNYbMywSxqBW1agBaOPA/dpjA58Aey4HoPDmqYbLS01jsEEZuMi80SSDaBM7zy/iBgdyPXCq3TwR2GipbPa4DVXOcc8MMm+5PmqJyO2eg9RgZ3YT7fQfsWRqSgH7T4jueJpZZjse3jSfdiXoB36L3OuDuTHM9t6R2eeOyW3nrb1W/v6iZ92C9GnlO+B1Cr69AdyTYeonqmsNnkeN4xzV9cSP8AhgdyMnYzMDnHRB5ic4BZtlvakqJ7NZ5zJcpuWS73aRRzR5GR85CPgj6IPMewL7LRrafCjgmg4cgfkWIZae7Tk/DvgupbrneQ5JwgJa2BnMrjEfoKalqaOKCnhK8OxkLTwrkvdJc5yc7mLO++8h8zYUeabXSVb3CaJaoLcWTE9Qi5S3xHpHGDs0rD1/zMOUIjP216qnDVlwMX7SlGFhjbmSkj/wCmD9o/ebuemAANeFmY5Zix9SdFUaMv6m6gd2rCcCeR+FT0UdDSR+DTRZKrkksSclmJ3Zickk7kkk51xrvGlgemmqIqDAit3LnJnIGdIjXuN9te41fMpOSMa9Ua9xpamZIsD015jfXulrkkWB6aWlpamZItLS0tczLbYtLS16Md9TM6Fnmlr0DOlynUncTzXuNs69A3317jUkAxONegZ11gemkBjXJ2LA9NLA9Ne6WpJPMD00sD017pakk5I6nXOu/bWdcV8SzXynraKw3QW600x5a+9KMk74aKn9T2LjODgLknIq7hROqpaO8b8bpDPU2qz1kdOKYhbldSOdKPP/LjH/MnPQL0XqemBjks1TeqyKgtFLNHTGYtBEzGSSSRussrdZJDvk9AOmB1LR0UnE1RBZrLSSUlmo35aeLr5mB/eSH7Ur4Jx7dlBbUWOpSOpq7Jwy8nhp5bleocMUiUnxEg6DBA+LO+MDrrM2KvJ5PxMXDXHYnC+5ndZNc1eLg+wyRVtXTSmatqGANLSybjPpIy5zzNkAgADrzWLhuy1lhvX7G4fja68S1Xnq66U8zITuSxOeUeucn5nA17wJabmauSw8L08EdQXzPUIxeOkzvln+3Io2z0G5G/nFk4gu/C3BFils1urCxY5uVybzPUSEZKKBu2fujY5GSF2Zfa5JLGMa0CptXoR6GKz8JUdVcK28eNcMc1ddGIKpv8MPqxO3NuB9kEjIx/i2+1PFM80NCklBY2fmKM2JarHQuT8Kei9MkncnRqG31nF8zXS/I1usVLtTU8jEkHszjbxJSOi5AHfCgnRCo4dejmCz0wBYh4KF2JZVA2lqWwOUei4BPou2a1JuMrdbsXgSq8PWuR4I4IIX/eHZEXzy/2Udfwz21qNis9l4VtE94uE0BrGiJkqAxCRqfKUi9BuA0u+c8qAkjPFstdJYrVNc7xKFkkXlEZGGOenMBuAcbRjBPcgZK5h9IXFct5rxR0/NIscgkkTm8kYGQC+MAtgkBRsudu+pxnAmNOc5PcZu9bHdeJa25QljTk8sXMvKQowBtk4+WdaHw5F9UtdPE4wTGCdu53P89ZdZJIlraelrmEMdS6hZjsoOdw3pt01shiHQDbXr/DWQUCsdxPrK284ueoniDHONtAeJbLDcKcrlo3Q88cqDzRuOjD3Hp30eibwiUkOFG/Mdsaq3FF2aYpTUZKxknmbOOYdPy/toqy1FUh+RMUUk5XuC//ABTU1FqqLdOUFxgBSaWM7SL0Dp8+57aBSIQqcxbmkccxz1G5/tpm4UU4qRPSP4c0IBQgbZIyQR3B6Y1Mo5kuUKyxRiJ4SfHj5slGIxt7emlI1D7tjHj2hL0gr5i9+8YYCSaJMKNmYk+m39tN03Pb5pTIClv51BfBzGSMlwPu+o986mU8UcNwaWpVvJGMJ7+/9tT0pBMtXX1z+XmxTxdfFfl/kD10Q9YABB5g1dueGGQe57BLE9fBGkZz9ZXmcjIbLDofTfUriaiQyDlLcsY50aMlWUqQRynsw2IPqBobRwVtliovrkQSjqJ0enJO8R5gQrDqEP2c9OmrdIY6p4GYB48MZx2Gf17dfbWmmsF6sG795jq1OmKFepdvok45a/07WW8MFvlIuWbGBVxj/mL/ABfeH49OmgLjvr5ruNtr7XcIKqCcw1kZaamqYz5kKsQDj8MFehBHbW0/RpxjBxbaWMipT3WlwlbTA7K3Z09Ubse3Q+6y6vyjx1HGmvFq/eW3A9Ne68HTXuscwiLS0tLXJItLXoBOkFOpJPNIDOu8D00gMak7ic8p16owde6WpOgYi0tLS1J2LS17jbOkATqSTzS17ynXWB6akk40gM67wPTSwBqZknPKdegba90tVzJBXElpW50WE5RURbxE9D6qfY6zTxWtlaIaqMrSM7eIGG0Umd856KTn5HfuTrYBqr8a2VZoZLjAgZguKiPGedcYz+H8vlovS3bfSYNdVn1CU26WmGeqgro40NTCeWEuPKw+43v2B7dPTHfEHH8cNnWjscMtArxlaqaUYk5ujIo/qR8htzCLb5jS1n7PqiGpGXFKT39UOe47ex9Rry8WeE3GO7LCJ6iEZKNusqjJ5h/GPXvjPUHJVtS243dCAktXkr2ZCsdkqOJUga6h6TzhFd25frEfRfE+7jbB3yMA7gMdBuNxsXAFBHT0SxVNzKYVVwOUew6IvbJ3PYHVYvPGdvpbUaXhwK7TRfv6qVBhAeoAPU//AGI9WzjVXoIpuKSGEjU9VzhHqTHtWKF6qf8AqADB2HMNxg5BEap7u+EHtN1tWsccvHai6zcRVZoqnw462LmamlUMIIgTvHINwg32br2bA2FisnDVFZgaq5SeNWkeZ225fZR2A1DSW08O28w06INvMDuXPv6nQaouyXOIW+sYUQZsUbNJ5XH/AEZMn/2nOx2bWxQqMV9SisG5floWTjGS0VNTTWuSSK2Sqedkw/gPv+8jU7EAncHY9t+tP4gkuP1w803iipAm/aHNzioU/aRj1PYk7jpgdNS7Zw7d7xVmGeleGONsGnOxBB6yHb8unpgbat1ZZLFZbI1DdauXnlbmSGKPIVvVB1U+/Q7ZG+daotGnsDnknuZP52oQqOMTOaGJKNknp5HppITzLUKcMrH3757jGD6aMKi3iP8Adr9VuGC0tMo5Vq17vF15e5Me/qM9NM1VCKNlnlljqYZCfq0kK5R8dQo3ww7huh9dWnhDgStv/JXXLnorcjBxhiGJHRgeudvi7dvTW+r1SY3qcQbS6d1/pvz/AJ7Sr2a3V95qlorXA4jJ5PECbn1CjsPc/wCmtb4M4HpuF6V603FqWqBDSBfNDnH2lPxN7jB0VpfqPC1SDNPTSJUEfvZGVZ2OwVWOwYH1GD/MU76T+LF4hqYaGhpKq3wQLyzwTHBZ/cD/AO1Gc9fTSG3V2as+XWMD3MbV0JplLscn4lsuX0iUi8OV0NBSLX1AUxy1EEmRAx3D4xkrvt2BGCT1OW2Lh+4cQ3EJTRyTNI3M0hPNk9zk/Efc7D56sPAvAV0u1bHXpNLb1jJH1kAcwH3cdCP4Onqc7a1mx03/AIbh+q1NLSxwSPgV0ERCn0Dp9n2x5fl3BbUJoty1ct8wpKG1W1rOB8QHwv8ARtBZKeOSjr3huKsJCGAkhz7qe/uMfLYatdPxBbKZZRxGyU80S8wMZ54mH3lPXrnr0P56AfStxTRWe0IljrqaarqCVkIfmK/zyfb88jWCtPdK25NJT1M7VzNkycwYj/MTsRjbl6Y/PQ1Ois1qmx+oVZqU07bFGTJ/0j3648SXueFJpGpDL/wwUHGNxuPtE/p8ttHfo1+j29VrtWtVyUMbgLK8kYkSoX0ZTs/ptgDpknRv6PuH4aeZbhxJZW8B9vrEOWgJ9Sp8yr7bj3PQbRS0Imt4qoGQUqJzoqYAZQPUbAfLQGuJoISkYE206GzLPzKtwzTS8MU/1Wst9PBA7+e40+XTJ6GQHzD0z8I6bd5H0oX+Pg61RXG3NFNWyHKZcEtt9rfPL7DHzHXWWfSV9KN1WrlpLI7wwo5R5V+LHoB+mcb5Hw7g1GhuFyvsIt13oZ6+L4IJ4FLSxHGcOMjn36gbgZ39RU025d9gxNfNVfQvcrHF1wvHF19kulfK71cp5cLH5QB0VRtnHr0HX31EvllujUkS8U26qWGYAU1yjGZduzn4ZR7HDehI1u30c8K2RKSSskq6esZVxIrAAxgH7QwCB7DA+Z1damlpZLdOK6GI25lwVqFBSVcHPl7ADv8Ajtq//qXlPs28TMUMRnPM+QamiqqK2QwTslVRgkU1VF5lI+6Cd1OeqNjvqA9c1BJzUkjJVBeUNGegPZs7YPoQfx1fePqqyUN4ni4Jd2pZN54ZcSxnceVeb419znH2SR5tU0UVsuRUUpS11btgU0jAwynuYXY7H2f8GOmysj4dRgwUKVJGcz2xvabpWr+0IzaK2NGIqYE5oMAg8xj6p36Hl9h0OyU9lqrvw6x4kgo66BQHju1KfEjkAwvmIwykgr6HKYwebJqX0TW6xf8AiKO1cRS/sedWBBnTK5zt5jtzdcO3lH2QDr6OqeBbbFTcvDrvbK10wzQnninU75nQnDg/e2b37aV6nWkWnII+8KpqyOeZ83QcKPSX+maxXelimkAZUnkC8ynOQT0Zeozt2zjOdXriSijip0muqSWu5MqxsWYhHXIHOkqA4BypOQRzIDsXGoPH/CtXap547vRQSSzSO0c8MmzSEBgE2Dc3kY+XlOCo5eUZNYsHGdbXR1PDVzqJ47fUlo6cVOGePJ3UEjY7YyME9/XWwZmG5eD+xnPSpOZdLJU+JXra6OupbTLSHlZjEWjlLbjxFJyFbsysMEe2A39IlKaSpzfKaITTSIZ4JVMkZLZDSxyAZQNjmAx8SyAjdc0atsd/scsUlNCZRFEJIWjYfvEbIZCN8eZSwG+G5xn00SymLjfhSpsj1UlLdlpigp51B8Rcq2YgxypJRSVBxkDA1lvNbj2/iWGCMHkSkcNWqzVF/hnsV3a03FHBCTDI9cgjOV9xn/t1oXGS11vtkVbcl8ORYmFPU0f7yOdBluRh0IRiWAz8DSAElRnIOLOEr3aLskTU2CkitDJBIOUBhkZJ+EFskZ23xnbVx+jPitKhv2BxBXz09RJjwZGxyh+U4JB74Y4bY+/bW9wVTvHBlUOOIR4S47tNI0cdyoqYo/lkaNeVc7NsR5lz1B8w32xk62Cpq1vdrp04enpZ3i/eLS1vmZgVIKhgfMjKxB+IkNnIxr5+404IvFHEI6enhqaFhKhWEBZVK7jCZ35Qy9OqkEDfJCfR3xJW8P3VKO5I70BKhlbyle3XOx2x7HprOytCN7d/Ilq3K5Et/EVaLRcs0qVVNRPHLzwVgMkT8rnmGCfjj6NgkkDrvsIoxwxfqtqGpo47ZcOYLy83NBMe2GG65zkZHTo2tW404QXie22yvt9xLBJyY/GAKs7g+WRup5vh3wc8oJOw1jlbwzUWetoFutFMGikaKOWGUrHy5PJiQdCp7sOoC4PXWiWFq/kSroM5E17h3h+6UdrmSOpevanyRRVRLTCMrh41JyWRgBjJOGVTkYI1m8dymsbJV0KVNNGYs00ORmekOS6gEkNJEw5wMkYJBxjBt3BF2ukEFJa7rK9yqEOTAUJmhUbiTmXJVSMEMCc5xjTt74TtU9yoqyz1MsMr1OVp6k88DyZLGEnIK8+SeUEAkbgnGcaLFztUyMBt5gmxcWW0PH9fmS3XIyqhqYl5UkR1ykpQ7YbbPpnYbHVluF1llt1QKeCOV4j+9mtso+Lr+8iO6+pGOY9NtZNxrapoZUe5WV4KSCp/4ZqaYyI0JYnkMuMjlOwJHQt105wfcY6N6ipe5x0csczLHE8pWoK52AYAK+fmD7HWtgQHNgmeTjiD7tLBFdpLXFKklJIjNuhAi37oR0Rix/yOw3JGu7DxRfbXC8cFWaCehwtRTAeNBNGDygtG2fhOFJG+CmD5daTcrRQ3SlhF6sy1Bc4FTGngzJnfODgMM9sr751S14HzVNcbDWG6qoINJOfDqIgvkZSu3NseUk4A6A6JpsVhhTmZkZhKpv8Awzd4aaW90Y8R5Ay1tHHzJEpYDLZOdmJViCMDB5SDtwOFDLE01guIrIYXYPGGKuhGzKwOCB65A9joPYbBXXOlr6aRWjlo5i6wkhKl1A8xCkedWTYnuwXbAzqVRLVww0Sr4V5DyEq8LNDOmVPhSZ2ZSyDl/wAyqcHcHh1ABw37yyIxE0fg7jDiOBorXW28V4iQARPiGVV6eVwOnzDZ0drYOB+IXaCqhe1156pMBBJn2IyjfoToTwzc+Drr9GqXOur53ulJGTNTzsomkkA+xgDYkg5IJHrtrPq6eycWVaxWniWqoLjESFpKp+Qlid9jkOT02ZifTbVayS/9JsS59K4cZl2uvAN0oXZrFcBVYH+A48OTH+U7N+BJ1XJa2qoZmp7tQywSr1ypBHzB0IW88e8IsIa+mavo0OAybqo/y9vkOU++rjZfpO4XvlGKS/RSEKpwJI/EC/LOGTf0LfPTOvxK/TnFnUFbTV3cDiVytqKWu/4dIkmJ++NlHrofcuEoKmDCMAepV15lJ+WrNUcMWmuzX2y8xQeIR4EbuCDzbcgI35gexB7b6jVVHfrKxWtpXeIHHMRt+Y20zq11N/8A7gg76eynlDKSlHxDYed6CqqYE+6pM0J+aN0HyI0819orjT+DxLYEmGN6mhyfxKHzD8M6uENwppQVk/dMdsMNM11lt9YpdolDHo6HB/TRK6ZT6qXxMGtJ4sWViLh+2XemZ+GbzBOAvmp3bkf5Huo9sfPVfuNguNCS12gMcUe+EGY1H4dfxwPlqx3LhBw/iwMJmX4WJ5JF+TDB1GivPEtmbwJp/rcA/wCRXpzbeiyAbfiDqG+6n6xn7zL8JTZ9JxKk9zMrfV7UhGRgydSfkP8A4Hz1YuGOCp6hhVXEtGjbkE5d/mf9jU8VvCNdIXrbfNY6s4JqI1/dlv8AMNvxOj0EN8ggE1BW014pseVsgn8x/XWe4XDIbn7y2zyjtK+n7QjSwUNqpisSJBGOp7t/fXkbV1epFOppabvIw8zfIf7+ehdvrqL63zXwTRVGcATLiMfIjVwpzFNCskMiOh6FSCNB3q1XYyYfp3Sz6TINNbKWKLl+rpJ6tIoYn89LRVI9ttLS03HMLCCfKVLaWPwJj5DH66K0lsijALgc2rHfrNW2ipKzgPCxxHKowrf2PtoZkHXtKQm3Inkb9Rdna3E5ijjTooGuZpN+Ufjr13HKcEZ0yvX59NacdQZQTyZ0ozsTuf009CiO3L6bk9tMBTzcq776kSMEURRYyep9T/bVZ0ziRsMVUkKNeRoG87Z5V6+vy17ChkPKNlG5J/nrmZwfIgIiX/edW4kA9omYSNlgFXouBuNNunKfMNiM509Gq7yv/hjt6+2kzmRzzjm5iPKOw1Ur7ib13Y4PUjlNtuuuWXG++dPSRmFt+nrrgjnz6Y1UcQoYPIjSnPXcZ03NACMg7dj3GneQAHB2zpZH99WDTqnjmQ5B2bY9jptt9jsw7jU6SFSMgeU9vTUV18Nt919daK2ZzqcDcdd9e4Ok6lcMNx2OvQcrt11ccCc7nEiK4KuM6F3ChVtiM7bH10Xxkdd9ckAjlYZGsrqVuQo4yDNqL2qbIkGxXuWhlWmrZCABypMd8D7r9yvoeo6jHXV3oqhagloxyy4BZMg5z3BGxyeh2Dfwts1Er6JWBJGQeh03aLpNa5kp6guacE8rjdos9cA9V9VO2vJajSXeHPvTlJ6Cu2rWptfuaWjq6gjSUnGCDn11Ct9bHWoHV4xMV5uYNlZAO+T/ADO69GyPMJwO5BBUg4Kt1B9Dp1o9cmoX7xJq9G9DZ9oum2Neg68Ge+kCM++joFOxg5BGvOqkdxrlc8x5vz1732OpLCeY3+WlgZzpE5317qCdngAwR2764A5SVGdd9sg6RAIwddlSI2wzt6aiVUHOD01Of1x+Om+XOx6auhKzI594Aq6cx5227j00JudClRGenPjY/wBNW6aEPnI0JraVossoyp6j01qypehRxkGWqtapsqZC4S4jrbRXxxzVDwzof3U6nHMcY+Wcbb7N0PrraODuIaKKxpT2qhlq7zPJypBu3jytkmWRz0Qbk537beZmw+vo46iIqQAwGx09wtxDW2W4wxzTPE8bgwzg43HTJ+W2e/Q9iPGeI+Fvom3Jyn8T1eg166gYY+qfTdHTS2OmEC8t04lunnYtkB8fbc9UgTYAdWwAMdBZOG7TLb/Fp4qh6u71RElwrmUdcbYHbHRU6KME79ab9FfEsF4MsMZzxDWSE1FTUEEOg7qNt1GwjAA751cCIblA1soZHWyI2KqpR8SV75PNEp7R5+NwdzlB0Yhcqmw4WMGZEGTDFkgtkVu5aAAW5XdjIDn6w5JLNzdWBPVvtfIaZnTx7obhIxZ0Tw6ZCAFp1IAbkA+02N2OTjAGBnLrOSixgKkabIijCqPQDXGmun0ioMtyYpv1RbheogABpaWlo2BxaWlpakgGYtLS16BqZnds80te40sH01wmWwJ5r0b69A9degAakmBOcb40sHXWN86WuSYE5AJ0sHXQGNe6k7PMDSwNe6WpJPAANe6WlqSRaWlpakkWlpY0sakkWlpaWpJFrmWRIonlkdUjRSzMxwFA3JJ7DTVfV01BQzVtbPHT00CF5ZZG5VRR3J1lV/4jHFdPLVXFJ7fwjCwMUcoKvciDsWXryZxyp9o7nOCBm7hfzllXPJ6k7iPiL/xPSVBhqnoOE4sipqySj146cqY3ERO23mfOBgfFTJlfiKETTyiy8LUYIijVeVpVXIyo6D0LdB25iDktUQz32hW830U9t4epgWpKR35I+RdjNLjcgbDbqW5V/iqdXU/+IJ4q6uhlh4aR80tIWEUlxCHBLYHkj7YxgdBvnWDWbe+5CDYOOFhqkWq4vt37OtETWHhWImEVCqwkrWPVUPUrgZdhktsDgEcsm6QWesmj4doC1soxIpkSDBYxqcIioCeaRsZPMxx5uYA4yTscU01lMlZUw2G1yRNkheWWojGCUjHVYwMf5u5A5eXPa+/VF04ia3cM25oqiuYQU0ZkAfwvhALbCNMZZm7knfHUbeCSScTfBC4US5cRca2jh+gPDvDyPT0aghmhbmmqG+6D3c92PlUZ+I4GuuHeGY/qovPEkRe7yJzxU5/wrbCckcoJ80rDJLMRjcnAzIItk4Jn4fq4awpHcru680ZePKso6sikjw4wBszbt1wNtWajvScy1MlMsiU/70xSYCPL1JlYncDYnoNgBy9xGt54mqnC4MIUlsqZpaNo0jhlK5pDIv7uki2JlVTjLdDztgscbKMB5VdLa7NDK8MbTSAiRpJCHeSTBPiMT8T4ycHCxjc9+aJHdo6OlnvXEF15autHjSySJkRRDo/J+iIcdeY8ucDJuPOK6zjBTTWqCS2cOghXkYkzVe5OWO3lyM4GMkZOSBy3VmY4Eq6KFzIvF3Edz4ouj0lsl54+dkepGeRc/ZjJ3JIG7dT7AaC11ItBRpTUyk0pcp4uB++cfEc99+/5ba0jhDhWOksguFZQVMNIqHHiLuyqMkAbbHGSOpzjA6tQ+IXqZr2q1cUkUka58J8AoCcgY7bHPQaK0qhrhWO5gxxWW9hHbbbUuUctLInPGsXMR3zkAY9DvnVk4Iv8lBOnD16lJOD9TqmGPEH3G9x/vrpjhZoKS11NdUEgSSCNMdTgf66AcSxvc5hKp8MKOZFTblPY/PbXq9fsrUFPrHX3+xiTRb2JDfSe5cr5cTXzPTQMVp8BevU56n8/00EhYczmVj3w3qvb8dQuHLw9bAaOcAV6AgN0Eq/eH8Xt/sk6umLQRxBcu7qoPTH+9tKEvN5yf/qGWU+T/ncjxQlw748zglQPlofU29rUsVyoZAKxMEoPgZT/AMs+ufXtqwRiQTR0MCeJO/xMMeYeg9ANOXJY7eEgTlqamR+U7ZC+w9cZ66uyryp/wzJXI5EEWhqGoaS8VbGoDSYWlxhg47P6AfrqdQRhaOW6Xhirxc4o6cDzMRkgkfdBP46BXSGfh+4pXsfFmnOZqfqGH/447asdM1PJYpL/ACVMdWzDlpoy3XGMlx2wM7f/ACbLcynY55H7yllAYeYnX8TutoxW0sNdeAVp6uVI0gzgmLv8hgYGh/D93e23RqOoLyiIMkDydZo/utj7YGfn89FrnTVtTT094ueYaV54kQFsELnqo9ABqPxoaO5mKKkoxTU8HlDKfOSWGGLeoOCP5dtUrZt+V7mlgU1bX6/zmE6qjpaygdTWeeYs8DqMmIIM4PvjIx6DvtoD49Xw/wATvdLNURpX0zkRogylSvdcDqjjfbodxuNLhmuEsdXaK2Qx1jHn8Q7B+Xo6999wR2yD00Xv1FQmsaGOTmmo3KwODtKM4Bz6Z39uumC7b1IP/wBRXufRvn2+Zs3BPE1BxVYorpQlkJ8s8DnzwSY3Rv6HuN9HBv018z8M8SVnDfFK3C3xOZyojrqN25RVIv2fTxB1VvXY9dfRXD12oL3Z6e62ycT0tQnMjYwR6qw7MDsR2I0rsrNbYMe02ram4SeBvvr3Axr0dNLVJuJ4owNe6WlqTuItLS3OvQPXUknmvcHXvKNejXMyTkDffXuBr3Xhz21JIthtr0DHTXgHc9de65mSLS0tLXJItLS0tSSLS17g+mvQNt9SSc69AyMdu+vcDGkvQ6k7KBxjY0pJWkjjzRzHbb/Db0HoO4/LtoLSVZmq2o6h3WSNQ6MGxzfxA+o/2PTVauniqqaSnnQPG4wwOsy4hsr0tX4EhKyRnmp6hRg47H+4/p1Zaa7eMHsfvArqdpz7SucQ2GM1grnjMlMhDVFIg5VJ/wCoMdV/h6KemxwObreqaFDSUUSSNy4AB5Qnoc9sfnnRyKrkrEkhhaOKrpmw/MnRuwx91h8+47b1O/2t6d1ltyCmo5JOWc55npXP2R6qeoY5ONu25gO4BfaAOjIS4MVTM93Z5okSa8xIPGgDcolX/qKOx+8o377bjRngzgea4TfXbiQdvM7gBEX0UdAMd9WS2WXhzgfhg3qvi/aE7BeUJIMBm6Hm7nvkdNAOJuJKniK0GOhmmpKKlUtU0jAJJLHnyyMV6qBswA2Izgg6C89zlKhx8/E2FKghrDz8S1XziC1WaoFnsldTTtLTp4VRLJzxpN0Cs4G2R0yTj1XWVXitrGus8MyzVNzZuWVZOqHJ+LHT/KNvnqFGZ7q/1a3R+HT9GmK4yPRR2H8/foLfa1ihjSKqmSSZAsMdZJsR2COe47Buo2B231rVpRpfWefmZWXnU5VeJE4borjaiaqbw64O4lnopcFHx3X7rAdx16H21u2/SBw1Fa46qpSeVZlZYkiQfu3X7JzsCPf8BrIbtcqlppaCCOWmVWKTM4xK5B3AHYfp+hMCyvUrXPBaaRayIkCpjdiIXA9+vOOzDp7jWGr0i6kbjx/vNtNqDSdnZhmu+v8AEd2d5A1TLI2w3wFJ7eg9+p+ec6RwzwJXUNPS1d5p/wBprCAFjUkVEUfpnfnX+HPNjv20Y+ieDh39m+Lb4pPr6sRNHOB4kLe/4Y83f5YGj/0hXduFbMK7HjzTjESqfKNs59APc68/qtW7uKa1xjiN9PpgqGxzmF7Stvq6DMM0ENKqZQKwUFRtj2G3TrrEPpI41udXXzUVLUNS0kZKExvgsOh3B2X26nvnbAG4caV1XO5upMkU75BphyyRNjHOgG79geY5IA7ga5s3DFTdapZamZJ6YnMXgklHHqT1z7HfW+k8OWly18y1GrNiBapAopqi+xv9djliKEha+KPCuufhkXJIP8Y/HGM62P6OOBLbBQQVbeFWNIAyRo2V+bn19tecP8L/AFWFZI4Qqp9sjCr/AL9BoVX8d2fheuaKymfnDZqHiwYCdznk7sOwX1xnsM9VqGbNenmunpVMPdLxxtxJBwnR8tR56lx+7jVQPwA9Pc/r8Jx2r+lOviWpgfFvoKgkMaM7Qn7zKT5ge/LjG5A7ahfSdxdX3qeK41Tx1cUyctLJTr5JB6eoI7r1+eqpRWeaqkFVcwD3jgX4V+fr8tb6DwlHr3Wck/tMdZ4kUfanUtvDHBtXxJWNWQ1EUlO4DCpSTmVlPfI6A+g3PtrW+HLDbuHqdaajgJqGXGw8zj0A6Kvt099ZTwLar7S3oVfDMgp0B5qqNzinI7sc7Kffv3Hpb779JL0NnrKe2UUM93gYx1bxy8wj9HPRuXpsMbkglcaU+KaF2u2Kc/lC9Hchr3HiF/pGk4Ys0D3Sqq2obp/ymgxzM433X7R6bHtjJA31j3GXGl543tpp6WtAaKP95RRJySvg7sBnEi/5dgeq531UuIrpW3Cseuu1QalX+Iuccq9dvTfooGOp650Ogt1TXGGsgkkp6YHC1C7TKw3x7fh/pqiaIUr/AFuSJ06nefR1GYBJPIKaCLmq+fOQTyof4z3YfgP5av30ffRyOKWnoLjbZ5pWA5q9G5RTkDbmB2I9hv6ak2PwvrtIeIKT9pQOy5raMBZnHdZBjc/xAfMDrrZOJuJaKx/R1JdeGIqXlpWCmmI5TTerMvVmHucHbGdD6my1WGyXprDZ9hMxunAl64SiWk4kplu9oQ4p61c+QenPsyHboxx/FgEE5wHxXdbXZp4+FLg15o0B8S31P/maPbtjdh03X8l+IZzxtx3xZxvGsdxqkgtsRA+qUp8IO2PicZJHf1/DvXaEm2Sx19BUzU0iHMTRbTE52VQBuO+e/wCY13ymtTFshdUb0S0ce3Wo4ocrV1//ABsIL+BMMIN/hTGRzd8tjGOpO5e4J4cvd3qoae4WCO9lV8ySyNFPyknDiTbAUdDIRkgY2G9Wu95e9XCP9uJ+x7qgDLMyBYKn0aQAAq/8RyD11s30U/SMtipo7PxLb0gLbrWQr/jN1y+MhtvtA5xjY7HWF1WpoT+kOBO0lC3qPcmVVFBFaXo6CeZpqdWNRRXIctTSLscqT/iA8g3zgsB2dtCKS8W57hBNebLJJSnCxTc2JoSQTyFhhui5UtjI3BTodou9s4dvtoStuslNVxcpaCeFx+7HfkYb/PO3qNYBxhX2qz3OW10d1mFO0SiKqEY5KVgWZAN9tupwUIGMAKCRq7PN4HfxCXXb3LNxtAv7Eavs1Q15i8NmWQsFqaZd5CH++NnZcjBzIuSXBGWSTcLVdyjNfBJRI0nkqYjgAnBwR2OCCCNjtjlzrSuCVqKO109LfqZa+1zArFXW5+ZqcsPMDjB5W3PL0OTtjVV42+jsikM1lrIrhTunKIz5eUqSwKuc78r7BuxO45caL078FD/YzNlJOZbaulqlsTVJuEV8t8BjfxQRHUREHCSNuMYBKswJHIx8xKjVNpbzSftBqfiK0pLJFK8b+MgaaIZxh+XBYjYZHK24PfVe4Tu9y4VrTR3GGaogVsYcEMnrgdR+H5+t3uXDkV8o5L/YrgkySTRzzQ1EgR8E8jhHGBk5CkMDv4fTv1MI20H9DOH1DrmaJwpJZbhZOWw1UcNNIpiNOZCYHz1CvsUbuAwU98HrqrcZvcLdV1iqsa1JZWroZR+4kbfD8hGD4qjflKlXRvXer8PQLYZRKk09qeB5Uqo2xzSqSMNJGxIZRt8PMW5jgeTDHq+rpeLOHq6m/ep+6MTsqF2VVYsAIz5gud+U5HTZTjFFAR8LxO78rgiQLHxHZIWkkopEtvj4DxS7wMQeobGUYEMPMMLvvuNSFtvEddXsaSqy7AN9XL+V1DcytG2SxYEZB8+4BJA1nHEVguFNRzzOVnoZ4lljrqZiUZxgEkAZTmABIOfMB6ae4C4rudrn/ZtyPPRAAoXUuvbB65GRjdfN00VZWnbDH3mKkmWW83istt9rvqrCjlrHRK2knAen+tEZEnoI5BsSMFSwydt4wHCF8SMyQPZKmf4uUkwmVTh0O2UYEgYIIwQSd9Wu9cOtxRYquttlwhRpKcJVLOAQ4DFg3idVYFt264AznGRQaux3Cgrv2VcaWWkuFdGOaSQERiqjyEZX6EOp5cdc7npvEyy47EvxnImk8LWWtttP4FsvooubDQ0laonoalT2U9Fz2KkZ7KdMcR2yvo6ieprbV+yJpVyORw1P4wBzyykgoHUbZGVYA8uSNVDge/3u0R0tsSEX2iqUd5KZkCyRsN2UAnBOMnA3+LbbWiiCLi+0xx8NXyakki/eJR1S86xyD4cKeyncLsuQCc6FAQNlTiWBHTSsVPFlmr44KG8UYmrIyHhqozytUrjPPE+3K+CDg7kgrkHcBau1pW2pKDhLiGI/VaotDTVcZSRmfLFUc/GCfMNmIKZBAzlr6WKXiKmuUlbdbCYo1kViKIEoTvl2PXJY8w2AU5AzzaqtLKKyZ2FdHFR1Q/ewSkBYXByShOMYOGA7gkeumSKCuGg7syt6ZF43pa+Gppqq8pUwV84MdShQgCQHAZWGQwYHOck5J2HcFN47j6tWctShOAkxIdfk4/rnV8sPFlRTVc9mvyfXbdzM3h1Q8XCgecI2OYhdpFG45C+2calW/hPh3iScVFl8S3VhQTtQzyhop0BweSQbgZx1APmHk310qKx6DidZQwyYD4a4o4gs5ipRWLJRnCpR3VGaPl9ElU5/AHHsdXWgl4drmlmai/YVfLCwMkhWaCUbE8sgXGcgHDKhGOp1PkjpaGmS0XG2tb4GPIYK2MTUZPtL1Un+IZ9tQKng5rVUrWcP1stml2ZYag+PSSZ7BuwP8XX00J+MIO2wY/iV2MnIOZCi4futFdZa2RK6jVgZqaekjZZEYDbCE7qT3U9Nh66McFcYXykr1gvdPNcqWFed6eCZPFkDkjJGMyEEHy9jozZeMLVwpalsvEXCIhnahkeKpp6jxFZASThWyuUJz/l3wDsanVcU8Jz0MVXeoSZ4+VmqKeEgKjYCOM+u+cMcdOXqBvWVYHBx/E2IwAe5f4RwRxdUyrQo1A4xjmKxux7/ALvoce2Ouhtz4Ju1vZpLVUrWIvVYz5h80P8ATOqbduFKi4PPc7BeBXlchueQ5UjoCcZUDtzKNum2hK8QcTWGvgS+Q1rNEOVJHdgQPY53/P8ADRlNl9PIORBn8tuGGJaxXVFM5iraV0YbEgYI/A6fU0dYpQ8kgI3Ujf8ALTlv+ke13aGOC4UcVc7eUrUHkcDptIN/zGNFLlw/YaqKCotVx+qy1AzFTVDAlj6Kw66aafxYdN+8Gs0Q7WVOu4YpGJemZoGO+Bup/DQCWw19tmaoo2lp26+LSPyk/Neh/EHV0rKG82p+Wpgdo+zHcH5HXEVdBIeWT923oemj92mt5PBmGLk+4lWp+JbmgMVzo6a7RD4jyiKb8Qdm/MfLUu31dgqKjNrudTZqw/8AJmymT6b7EfLR2qttDWf4kSNnuNj+egVz4YDxskTpKn/SmUEfnqNp7E+g5EqXRzyMGWKKu4mpk8P6vS1w7Srlc/PG2lqgNR3WhJhgnuVMn3IZsp+HMDjS0GVXPNc1BYdOZeqqmgqoHgmiSSFhhkbfOs74s4Xltwarog9RS9So3aP5+o99aR+O47dde+XBzv6//Or12tWciXv0yXDBmEqCQWzt299dZPQDzEb+w1oPFfBy1HNX2lFSXq0JOFc+q+h/Q6oojalLNMrJMCQEYYK+503ovW0cRFfQ1J5ngxTqV/5jbH29tcIrMxVBlj11wWJbGTzH9NPswp0KD/EYYY/d9vnreDYInssgRDBEcj7bep/tryJA4z8KL8R01ApkflHfqdPSuOXkT/DB/wDcdSVIxxOZZOcgY5VX4Rp+CLwl5zvIw29h/fXMUI5BK+Mn4R/XXWeXLHJ1ZTxzKk59IibpyhC2dgPXUaWJUchHDAfEB209VS/Vk8p/fuP/AGD++o0C8iCVjgnpn+Z1izbuYzorKLg9zoqNxjXJTB6be+u4SJ1LIpHt6j1H9tLlBXUH3mnB6jZzy/jpt4SwPTHcafUfrpAYyNdziTbkQe8bRg5BKeh6jTYXlJIyR30WZA5JBw2NQZYmjJaMEHuvX/Y1qj+0ptIkcYBznXhA330iBjI/LXg660lREMdCBqDX0aspIGV/lohy++ve2NVetbF2t1NK7TWciBLXW1NonA870/NzcqnBQ/eU9jq/We4wXCCPlkVnIAikVdnH3SB0P8P4rt5BT6ukWRSQu3cagU01RbZWaFeeJtnjJ2Yf0Pvrymt8Ps0bebT9Px8R/ptWmpXZZNOVgSVOxHXcfgR6g+uknxdNtCLJeIK+nQvLnfCyN8Sk9VfPf32DdSQ2WJXPI3Kww36HfBIzv19dx0IGj9D4gl67feK9boXoO4dRz10j2HrrzO2Rrzqp3300EXgz3Xo14o2I76QOxIOfve2uyZi9f569AOd+mul+HcAg99ejOcHbUknGw99clfQ675R0zvrnucg5GugyrTggnB6Y6g6jyxZJHY6lNnr+GuMZzvqw46mR54gSroypyoz6jQmvo46mIqwz6H01bJ4+YaF11KQS8YG/VRrcbbUKNLo7VtkQNw7fKyx1sUU8siIjAwzqxUoQdtxuMdj29xr6W+jHj6G+wx225usdxUBY5NgtQAPToH9uh6jrr5trKSOeIqw/H01Gs1yqbJVrDPIxpgR4cnePfI6b4/Udu4PltZ4e+gc2V8p/E9HptUusXY/1T7Z5j7a6Gs2+i76QYrvDFbLtOorMBYaliMT+gb+L0PRvn10hT21au1bBkTKys1tgz3S0tLV5xRxFr3GkNzroDA1yWnIB10BjXulrkk8Izr3S0tSSLS0tLUki0tLS1JItLS0tSSLS0te8upJPMH00sa714RkamZJzpAa6Axr3XMyTwDGkRnXulqSTjUO8XOhtFuluFxqFgposczEEkknAVQN2YnYAbknTPEl9t1gtv165TeHGXEcSLu80h6Ig7sfy7kgAnWJ3Dj2uu3FNNWm3UFynp5mNLRvIZYKYAHcYwGk7tKdgAQuB5jVmPS9zhZV5aHuJL3SXx/2lxU1VSWylkzTWdYwTzjPK85J5WlOxEfmCZyync6rF7uxljS833MVLGP8Ag6J2JLA9C3fJ2BPUjYYUAGPdqinpKqO5XqrW51YxFb7fTQ4jDH0QfZz8K4y3xHAxzTRaqi21EN74mH1i+zkNQ2+JucU3NsOg3kORlh8O/L5iMYs4T7mcAa488KIBvlTd7hVpU395HncqYKBhiOnVdlaRRtzgHyxjZM+Y521c7BYFpPq9deSKqvIUU9FIOfkXGFMg/kvTbH3ikyx28rVzXatjiqLijiGCBUHh08mCRGoBxlRlmwcIOp5mLoE+v1d7vrcNcLVXiTSyH9o3lTmOBf8AmGMnALBernAA+EfDoJ3A/OEpXuP2kHjniSrrrrUcP2RBcbrUjwJpXIIjH2uhxnHNgDZRk7YLGRwIOHeFIKiWepWtrguKmqjHNJUPn/Bg6BUz8Up7DCDcNqPdLDbaOcpbLhTUFolIihRGE1XWxg7O/T438x5iqleXsACVvXD3CscZez3R6lzLHTU8MZDyTMBmSUsQOYZOBgIg65bBU0C5+qaM7L9MtNs4xtM1uqKi51DB5FM1XTxdFQHEUPNjmkcnGeiqMYK9CKukwo7XJxbxKlNbaEBZKGhkTPinPlZl6u2AeVOndsKCTUuLr/ZrLFTUVtXxKOmIdsjJrKj19WUdBn3IAzjQ+Kg4n4zvP7cv8jVE8b/uKaU/u0IHw4xgsBg4AAUAZxsNVKY4HcrvBG5pLakvHHlwF3vcUlNaC/PTURYl6g5+Nz1PXHT2A7EvK1LbqwIYoZKlMckWfJB2GcYyfbv2wMZLVN0kBehsxRp0TM9Wzgx0ydCeYjG3TmxjsoycAfSx0ltfxYEqZ6zDOWwRK22ebHWFe+SfEI+4Dqqrt6mbPuMKcVcRzQcOQw1DtQNEhieTxCahyx5mznKxZ5QAOVn2GFUeYY3PUqZ6qr5AhZiVXJ6/iSfnkk+566LcX19Rd5EdVRaalTm5UGETmOAAPU+vfO+q7MhkmgplzmRgDj3Omek/okOO5i/9VCvtLLSzN9QpIZc+bzMPnv8A1/TT8/hRNKA3k5AAfT7OddzQhi7oN4wAMb9P9dRqlFmjRASoyqOe/U5x+mjQTccwUN5XBkW4WqTxIZKVzC6EyGYD4MDOR/bR/hW4m9EU0hiirof8VCcAgfbB9O+OumvHSeoFHEBFAqDcjp7fjnQSutc9LEb1Rh4XSUESYyoY58p9QcHWVtRT1J3/ADNktFg2N1/EvCl/GemtsZapH7szY+znt6DUdhK/LHQqZKxhyKFXJB9vxyc6e4LuUd5oPBoIhSVKECsQscr2znsv8s/mWkeG1wGhtHnrajHPU43AbGAPTbGq13BsATC2kpnMrFXFRUtU9PXSfWa+EnZd05jjIB7kb9P9dD46aosVQ90r4lNFLKGq6LPLIUOCZEHyIyPQ/PRK1xw2aR62tH1q5vvHETzCPuGPqdFY7clfLJfOJJ38ERgmMHeRuZuVdunQ/wC99Xv9Sfr3K6ZwrY/z9ZBv1RW8QOtfNMkdA8qRUzBgseD6H2HU7Y9tF+KLpbjbHslmpv3QOZJgvmYqDg56np7d9tUq6t4dfURwU81PY3l8YKmWWkLZUsB2U+nY41eblc7TboXoLNTGV6rCyVEmMlT1x8/b16jWNLZtAI5HtNtQgFWVPB95U6u3CskUU7mCp5PFppB/1Njy/iDjHfGNTOG6+C5SRxV6LDU0sXhmAgjJweUj1B2x0/Ma5pCi0VNJKGKAhZCOuA5U498EflqPfo7hPUC5wRotZQoAkgXC1UeWOW9Tsc99vUaP1NhosFi+/cEorXUVeU/6GS7tb1rEkqaKnVqnlI65YHoVI6nbOD30x9GHGVZwjd53qRLPZ55FFdGqk+GTkCdP4hjcfaHuNSKC+U8NsE0EJSrkqCKhZVBMBAUch9iS36alVsZulmnpbdRRUsU9Qsk7RRlpZ2APKM9+Xc4GAck/LS5xqKg46gmnLaS41P3PoKiqYKuliqaWaOeCZA8ciHKupGQQffT2sL+iHies4XEduvR5bDVMPAnLeWlcsVz/APgmYHP3SQehOt0XfrpcpzH6EERa9A2316F99e67mWiAxpaWlrmZItLS0tcki0tdBdtLl1JJzr3B9NehffXupO4nOD6a95Rr3S1JMTzlGvQMaWlqSARaWlpaktiLSAwNLS1JItQL9bEulEYiQsqeaJ/un39j30Q17y6gYqQVlWXcMGY7cqCpjuBqIWMFZBlGQqOVxn4W749x7EdtPJKlbB4tPFzSspjmhfbIHxI/buN/cEavnF9n+tQGupY81EY86qN5FH8yP9PTWbz001LdhdKBC4kGKmIEDnx0cfxDce466a1Wixd/94BZXsO2BOKXqKCGNKiuqai3FyKSJuqMP+WV6c49Tsc5xuQBdtp7jLUxXKSZqJYiWiVTn2JOfiyOudj01oM8FLcaF2ZBNDMo50G3N6MCejDfH4g6pNyFba5BREeOpUPTVDbJyE4zjue2OxGPTRlPlqpB/wDuLdQr7wR1J9WYFtslVSQND4OPrFLCuCuScOvcRn36Hb0Oq7XVDToZK1o0hTZYx8C/h9o/7OktdJbK1ZqVnmuDZ8pGecHYhwfsn07+2iDWeCqm/akaO0ewalbf6ox+z7qd+VvwO411FIbDdTJ2BBKdzyzuL5DDSXdpqSMFUgq8jmkTtHL02+63bOD21oVBTUNrojHEkVHTw7PI69/b7x9+mqm0lJaoxNW8sshHkp+UEtt3HTGoa3H9sQrbbm4pCjk0blz4e5yIZfbJ8rdsgHsdBalOcV9e8N0z4AL9wncuL547/HXWCJYliwjPJ0qBjcED/fffurxcblf4Vmt9VPXwB+SSGeTmkon64fc5U9m6fI9a3HQXSrrXoUglpQjeHIXQiQn7qr21o3CXBDUANTFI1PVRJnlTfbqVlJ2Ofu/y0PdVTSBYDz/M1pstuY1nqN8GcDnnFVWkyyncuw6ewH9dXee3W2xU37RkrP2aRu7MCyzenMnU/Mb/ADxtI4a4usdt8WatUVDU5AkWEhggI2cg9OnfptjIOdZv9K/FNLd7xLXRu0dINo1Yjb5D30nZ7tbbsxgfMZ4q0tW7OTLvxN9J0cvCUtFR0MRpZl8MVCSEKpxurDqp+e5GsOnqJrhUtHb153z55T8KfL/edO2dblLPJV0yRQ00i8klPOmVql9HHUDfZuo99WixWuKreOC0UrRuWCNRt/iRsem/21PZvz30z0ukr0RO7jPvF2p1L6oDbzj2gW0WyqtcbfVJzUGU81RBOf3Ux9f4G9GH457XGx2u1RpLcL/UVNtpIYRUGCaLErrkjAPQjbr8tF61bHwTSLU3Ro7hdmXMNImCqe59d+52645iMay3iDiO93K6m7VVzkWpTITH+GF7rydGBGxz26YGAMzc+oYrpuB8/wDEstaUKDfyfiWDizj2e6U/7K4fha02pT9g8ssvvnqvzPmP8O66zuqlNDVxS0MjxVqf4TQY5gM9D2K+oOx0SjMHEEbrZxFQ3Iby0ZzySgdXpyev+Q7jt21zSUUFDGxky8jHzM27E6N0GirII/vnuDavVWKwP9viOWZrZX3OIXqljobk2yJzZpag+q5+B/VTt6atlvs0tVdI6CkSOOSVwhjlIRN/Un/fpqn1lMtTTP8AWFTweXcP0x7+mu7NxDJFTvRVz11RbSPDgrhg1FPv2Bz4iD0O/pntnr9IlaFRz/Immj1BtOWGP4M3JpeEvoxpOeZ0uV8cBljU5CE/dB6Dr5z17BtxrH+KOPbper5PWVFBSvBKOR6HHKsijJ2PUPv8f6bAATf6R1VKl6paqCXzQ1iuZFl7Aknq23wncYx205w/wxdeIKlKSCnqFEmFU8mXl+eOg/Qd868p+C/Dgu5yf2jkajzPSowI5BaorhDJVcIM9TMm0tslcCanyNzt/jL8t+3mwTr208Os84rJJ3euBBwTjkP8P9jrfuA/oktlDbKf9vRQzV0akw+C3I8QPq64LH9B76mXbgaOirFq6+la50QcGSaHyVIX+IDZ/n1P5DQX4hLMzc0NjiY1NbaLiOrorXxBcKW3yu/hpVzeUge/v799s9iOr3LS/R9cpeGqO62/iKnDBhEIiyldyUYdFPfmBYKd/KSTqd9P9zttXdaGitVvoYqKni/dVCQssmCAMZOzEY6DOMjJztqi0dpijfwqUSVKyqM86crk4y3Mc+UA/L8NdVztBziV2isYPJmg2yqpOIbW8XDVympCF5pbPO5yMd4z0k36A79PiJyKfdqOnulctNXwS0FSHwiqwTmXPmyhXyHIzzk436NjRK08L3CulSOzxGWrPmjKnAjXtynbb+I4HzO+m5w5uUlv4zpKikuKYH15VxIR2Ljo6/xD9OusAlbMfLODLgE+ppon0acCcTo0dbR3J7XTRRCONJY/EilQZwoRsMRncuSM9lwANWLiGnYRCirLelmr5G5JqiEGWlqUOd8nowyThsZUuu3NnUHgrjC9WGmjprxIbpaDyiOtjPM0a42BPUZ7c2Rtsx1pst1sclo+uR1UMtMyc+zDp3Jydvme+hOazh+YZWQw4mAVFFU1NuNZVUNPX0XIwVVkHjRhDgBJccrHCuCrY3QYI5xmbwtQ2sirW2VkUdaqlJqKtXwll5gQY5B9gsDjfIOQQxIGBv0k8SW6StrJbUtR9XcGOdoiqKVfG6RsOWTBRTlgGJ3UjkJ1mtup7tbqmS/WWsNyjZzzPGDzYzurqdwem35EaOCm1M9j95iWXdx3LlxDfJ7dd2o7vQq0TeHJTo7H92rDAYNjKMTgHtnJ5cMNGuGJuH7xFgmqp6qNvJUUzeHWUbd1IAw6d++Oy76Bwfszj6ljgqWloLmkDQgqSwJPLygAnHK2Ao22YIA3m2rMlh4itlXDdLW5qyrKfGpSeaXB2PLjKsO4PvruMrjvH95w4PI4l/4goquwtTtS1Uda7iaWGqoY8/WIwCXjmjJKggnmX084x0AD2prDWV0c1XSU9suEbAk8uaeQjJGRuY8jPrjzHIwNXLgyqsHHSJ49QLNxLAdqink5G5wCvNjodmPtueuq3c+DrjYKuNmpI5KMVEsL1kMZ5YBzcwDpgthW9D5g+TsN7UvuUgcj4nCMDIl84bpY3ukclLIUqJFKyUzEOJ078rDPiDGdiD8wNecaU09LbHqKhhU0drcJUQ1Scyz0bA8rb788bDlJHUYJJ7Zxab1HwzQ0ctprZqijaVzURTHnVXzt4RXBDDoSuBgA53xq71N1l40pKaSCOkr6qkkEkJlOHcYIeNmA7qdjyhhgHzY1RFCtlO50MMeqVClistUrW+mqzaGWcM0EhEseXBZJIpNtmG+CVz07nJa103F3DtRJVwMl6pcgzSjLS47F1bLL+q/x6y++0NfZKyQ3ClkohDJyrG3wyQtuyg9PI2CvfIJPYakWDje88LXdYmqH+ojDRqclRk5BXcMmQegIG+4ODomypG5YczPd7TdoeIKO7Q+PIxt000X1epEqBwg35JwD9xuudijN5vKNZ7fuELdcrultu9s/YNzJYrU05BpZpE8r+U49QRjJIdcka0Phu92HiugE9xttPUuRl/C5fGI9eXYSDf4hyt129a5xRRXKASTUVW9ckNQlLRxvEWDK6nwwQwwGC80blhnAVs5UaySx6vT2JpsDrmUO9cLVdult9LVL9VoASHuUSieKOSM/u3GBlduZGByoB3JxgVq2UCfXqyfh69laygZvqlOjeeZGyHjCgnm5WGMgkcpDZwM60iivl3tNJRz0FLHWRVpCz2xJCzxydAx5wNzylemOZRjJO8GVuGXulvvAiqLBxFBUj/iqeHlCsxIjeSPOeVj5G6nm2yAc62VlsBwcTMEfSRPeH+OKy22mKLiyxp+zXAjWrpT4sIPo33T1yMg+2ij1/DdJSivsfEqW2BsExSfvKTc7AqcAE+i8p6knGq19IE3EdeBeKaho6+lnwtRXW2QgzgDlYOu+PUjzEHOW7DP5zbmlZbXI9vYgCSBlymfcdCNXrQ/Sw4/aYtlc4l/40qOI44I6tbZTmniQyx1VvZpYpTnPLyDZY2GVI3zkZY4Gs9mmWaE+ABFDytNTwc2eaDJ8SI+vL8Q64AbudTbLebpYJHlo6iooi55uaBvGpnPq8bZwffcjto9WVnD3EFNSVd1o/wBmVcsjRTV9ty0XPglcqMsAQO4YkqRtrfyFX6eJyq7ccGVCkuNUkP1qnraqjq6HCGSkkKs8OcI+3Zc8p9invq82z6RKyW306XOhpr7S48GoMQ8OZXAJDdCp5lGcFQcq3mGgo4JuNFAt0s1TDf7awZPGp2yzKRhkYb5OO25HXAxoXboZ5mmSGmePDGKpcDlkx1DcvXIOGznOxAG511WZRyJHUBiwMv1Nw/wjxNTrNY600c5kIFLMvhuG2yvLk77jAVmPfGurTaeIuHbs0niGIAkLIw8RB/Ccg4/H8tVC3JXYc1s6VFOMJM5IDwureVj7A7c33WJ1o/0e1k9bxJQ29LtJTUVRMYpYqyPxFiI6qu4ZRnGACB5hscaxtsQ9/wBxLVFiMe8tdo4jmNPyXm1zRwHrU0YDxn3MbHp7gj5alS8OWe+QPUWieKpwMt9WOHUfxRt5h+g0e4w4QpuHKf65TXf6urNvgYHzI3XHvt89ZnxXTcQLNFcLSKYuhyslKOUt7jB3PuCdZU23If6bZ/z4mjqvTiP13DdxoizUjiYD7I+LH+X/AOdBay4VVNGySxAMvXbB1Mh40vWRFc4RcSMZLLyTL+PX8TznTN1vVrvEXI7czpgmOY8j4+7zD+uPlpppvFTnB4MGfSq3PcCRTpXp4z3ARn7qAbfMkb6WpsFBa6hTJSSvHH92SEtj5EYzpaPGrY8mDGkDqHOQ4P2V9/7a8GxxufcjP5DXR2PmbmPoNyfnrwc2CR5AfQ/11uFm+fiIL5+uCe7bk/IdtAuKeGKS7xmRf3NYo8kmM59mA6j9dG1BOQvN7kbfr113EAV5X82D0Gw1PUpysqUWxdrTFa6intM7RVURFQCcDtj7wPfUNVLuBuzk41tl+sdJd6Mw1aDmH+G6jzIfUE//ABrJ73bZLJXyUJlill7OjA4X3Gcg/P8AXrplptTv9LdxJqtIavUvIkLKxqYl/wC9v6DXdLEHBkfaMbAep9NNU8QlYnm5Y1GSf999SWk5gBGMAbD0A0cBFj8cCJ2JJbpryRhDGJXx4rD92p7D1OvEKRRmonJI6Rr986gjxKycySHb7R/oNZM+eB1DdNTt5PcdEbOTLK2R1OepOm2JqZOUAlc/+7213PJzn6vFsoGGx29tSI1WCIKB+8I/9o/vrir7mWvuCDas85REvho2WPUj+Wu3iyuGcCXuOmf9dewoI18Rt2xsCP113AgyXcZ9Ae/vrXGYEtxrOZHCFWKnqNeEY1JkKyOQeo+1psoQSDtrJgRGdNq2DIjIUqcnpr1kDLud+x76cbXmuZM2wINqKZlcsow3XYbH5ajsoY7bMOo0ZKhhynpqJV0vfo3Y+utVsweZiUxzIAI6a916ykvysMOP11z8Ox663mc91HqaZZFJUDm7j11I0tcIBGJ1GKnIgKIVFDVePTnlPR1IyrD0I1cOHr5BWU3hykqExzAnzRHpuepXsG3IGxBAHKIqqZZQSNjj89B3jnpZxPA5jkToR/L3GvM6/wALasm7T/qJ6DR69bV8u2aYuUPK3f4WA2b+x74/EEjBPWN8k9dVjhu+pOhgmXHL8cO+VHqnqOpx1GcjuGsQkyisGDo2Cjg5BBzjJ/A4Pf2IIGnh3iYtGyzgwTXeHGrL18iODIPvrsYB9jrkA5z210OunIicfeejI2PTtrrtpsDrnvr1D9nHm9fXXZAZ120mTB6gjXo6Z9tLcZxqSEZE55Rj21xjOe2nMEjXPKd9tTMqVweJwy5HXppqSIMOo0/1GueXVlbE4Bk8wNWUZUl1Hz99CqqmWWMo65B6+urZLGChGME6F1VG2SyjzfLrrZWDja0sCUOVlatlfUWOfwpGZ6Rjsepj/uPb8Rg6+ivoo+kWKvhhtd5qVMhAWnq2bZ89Fc+vo3fvuDrA6qBZI2V126EemoFHVVFkqB8UlIx3AGSme4H8x39jg683rvD30jG6n6fcfEfaXWJql8uzv5n29+BGvQMnWP8A0R/SRHNTwWu81IeE4WmrGPwjoFc/d7Bu3Q+2vjVKrVsXInXrNZwZ0Bg9dda8Xpr3V5WLS0tLUki0tLSAzqSRaWveXXoG2pmScjc66Awde6WuZknhGe+kBjXulqZki0tLS1zMkWlpaWpJFpaWlrkkWgXGXFFDwzblnqFkqKqfK0lHCR4tQ4GcL6KOpY7KOvYHji3iWOzGOho6b9oXmpUmloxIEAUdZZW6RxDux+QydU69S2rhqmjvl6n/AG1xPWLzRj4efGeVUT/lwL2zuxwd28y5NZj0r3NFQAbmOBAd/skt6qIq3jO4q92qP8KgppeVKKLGREpbyoSN5JX3VR8JyMVziJoLckFk4ZoEdq9iymFT4ldg7cvN5kp17FtmxzHOBqVc5KpbzCJaCnruIalWkioGx4cWTzGacDZEHUJ375LEi6cO8MpZ45am53RWulUni3a5yDzhfsxJnHINj5RvsN0wdZM/le+TOCrzxyMCVDhHh42WVL1cUW7XuctDR0qr5C/dFJxhRnzueo223DEKmOop6usra2tjlryeWvr0TlSDP/IgG2Nti22BnoOYm6iqt/DNMb/cZFppTFimjlj80UXQSOPsKAcqnViQSMtg0OioP/HEwepkazcIxEvEs7cklWud5ZD2QkbKN3OAM8pZRGu44hAqHA9hACyXTijlpbb49Dw+C1PzQ7vUjOWjjBxzEkDmY9cdgDiz1JsNj4SqopoJGqHjWjo0pHAgpi2c5brIyjmYkbFt8HrorHTrUxrSWykdLfvDCoHI86AjKoOiR7DmPUnqTsi0rjdZb9xxSWG3TwlKUGB0VvDijY7sQT0A7uSSeUnYY1UeppUvgcCEaexcFVaXGoo5b2tLSLHIzSGNQYgCvKWbcu7Y5MAbt8IAJAun4n4e4dtV18exfXbtcE8KhpxOeWBScYb7RHqc5bGNgSdM/SZU2yyQw2CzXaO6Vat4kwiUiGM4I8SRzux7Ko2Ve5LHQrgLhSS41ButwlnETnCSY/fTv25B2A6j0xkkDcXLsw4MoqqhywhLhzgqtEi3jiCXlqmXnKFsfVk6YJ+weu5GewGcslpRKq60nJQ89vtAPgfWFiw9R/6UKZ6dds77ljux0Zu9vpaSljlvZ51AE0dAJcBx0EkrAfD/ABEb/Cinrrq1N+1B9ZiroYY+UIayXyAJ/wBOGMHyJ06bnuc4JpZcEWU7PMgVcNNaLW0EH7oxeYKpEngsNuZjsJJgO+ypnbfBauWW2XC6NNTwO1PQVhAm8RiXJzsQerFt87D23ODbeKai1UkMNHSU8tTzECNWAElQ478vZR032XcnBABzfiLi6pEs1pstZB9aZStVXK+YqVDsVQjqSNi4GT8KAL17RZhSSJVtObHHPAnn0g1Fmg8OzWepLwwufHK4wWG2WPc+gGw39Qq16z0szX3mlVlaNTIoI9vLj8SDqAkFPA0ggaSZQh5pJAA0rHbOBnHsMnGi3DFxW318VtvDK2VCxT/aQH/lt+QP4/PJCuVwSOIQ1QIKqeZZEiIpiisV5tifb/eP103W0qVFTzITHGijIHf5aJGNpZHeReSNRsufiHt7e/vrijhfwTVVCkw55dtubtgfrvphXZs5EWugcbTIFsgR+auKuKWKUc4HUqD8I/lo1XsblaaejiiSltsDKEwNmboxz3JBz7a7o7YtfCOdzTUMeOcjYcoySR6k4x3xnXF4ro7lLQwUiCnt8MnhxIvptkn399Zu5sbPeJVf6Y5gm+0dYeIIqvhmmhgioaZizNhVkjGchyeuc4GfX8NGrdd6Gv4beS1wP9blASbn3eN84Cj399SooZrvUNaLVEFpGRcsR8QGxZj6ZOf97125RDhm6UlxsEr1Va+00CgMsgxjlA++CCR/TbQZJrYsvfxDVC3LtP8AeH5bbQ2W2SV11kE11liZooRvyMQfM3uP9+mm+H6KsvsK1lzqPBtyMSB0XGMEKD2wOp9PnofRLSVlul4ir7gKiKRyiR5y5JG/MPs4/wDjT31mqu1UtLRRtHbYnCqmdiM7ZPuSPYfmdMF9ajBz/EVvhXIIx9vmQ+JrpFJXVNooaeNaZZQOZd8pglQcj1Y++vaFDYaiG3XMB6edcUs7HeBs4KN/CT0OmeIFpqKSflPiVsx5zyjZBjYH+3voxWWR7y9YzrkGDxCX2XJXfJ7b76HK+rchwfmFK39Paw4guqgZLZk5Bw6nB75Gu0q6qD6vTvIBTTyLIjcvN4cmOYAk9s/zOotBUzKqWeuJ8Qgmmmb/AJgxujfxDH44061TLSeGaiAyQvEhXmGxK42z1G469jom24WKNw5gnlmp+DxI12pK+aY3KOjBqGIhqaVBy+Oi4GR2LdDkeueh2k1tzMtRbv2ZJIls+rIIeYYMjADn+Th879Qce2pTVVS6w24vHFLSo01HNjeQEAcjH1wAPwGo0j1VFILp9UaaKV2qbhSLHjwXBYGeIHpsDzAfd9lwClhofnlfiFsg1NeFOH9jDclklrLPUtVeMp5MskhGyndtvXAJOfn2OLV9FPEtfZascHcTyM6RzyUlsuD55JWQ4MBY/axgqfQ49NUzhysuNxuxp1kNR40WXlBwjRdecEdMdc+upV9rK660MfCtJSrJR0iTzEh8tzKjHmU48pAXI6+bfONtF6hDxZXyv8QTRX+WfKsBB/mfQIORpaz36KONJbnDFYL9PG15jgEkUwb/AM3EMgn2kUg8w77MOp1oWswcxtFpa9AzrrXZ0Tzl99IDB6690tSdAi0tLS1J3Ai0tLXo1JJ5pa9Ixr3l1JJzr0DJ16BjXuuZknhGB114NzrvXmpmSecvvpcvvrrS1zMkWlpaWuSRapPF9m+qTNW06AU8redQP8Nj3+R/nq7AZ1zPBHPC8MyK8brysp6Ea1ptNTZEztTzFxMVudRU26oSVT/wMrAS9R4Tc2c7fZbcH8/XLt2oIaigeFZDBTSnmSRFDGlkP2wPunuB8xo9xJZvqVS9HOglp5BmMsM8y56fMf2OgNK4tdQKSdx9VnOIWf7LH7Hy9PTp05ctkIxkdH9ouZSe+5U6O1fsyuko5o/+KzkyE55x1BB9D116t4NHWA2xUqJFOJpGY+EV7ofvZ/T541ZLzbP2nQrCS0AYZpZuboP+k57K3Ub7H8dUlvGSqe2UdNipiPLIHXCwkdfmdFm02jYRFYp/DnfnMn3WGGKM3WkaoqIJn5MN5pIZDv4bHt7N9ob9c6lcPcK116nEtaqiJN/CO0cY/iP9NGeCuGKun5qkyFmqFxIkgLfWR93lzsB2bt1GemrlX3S2WC1ePLCR4b+HHThRhJAOh38x2zzHbHppbdqfJ9A5MOq0vnHzG4EdttBDZ4aWaebxYiBGKhxyzRjfYZ3Ke/xAarnG/GsrvJZrUslEkLFJZCuGJ7gDr/3Hr2HRjUeI75X32oeWskIgHSIN5APfOMn/AE2ByTxbZZr/AANRyPJHJAAkFzZCVK5/w377fZf8D6kRdG2RZdz9oSdUpBSmRY6yqpa1GoWc14OUC+bOeof1U9weufx0YitENdVmtkpXgq0UNLQseZI/V4vvKfQ7r01a+HeHrdZYgOVpqlz8WMvIfb20uNpbfbrfHU1cwgr0bNPHT7yDbpnuf0wfTJ1q16K42SqadmQ+YYT4U4NluEQra1zSUA38RhhnA+6P66g8c8a2qkov2LwvSU5WBuYVbDmIf1DdWJ9jj/MDsAuPFt84nsKUBqWiqKePE9FnBqIx0dSPiwMZTt182x1RJKuWon+q0K+PPjzN0VPme2sU01msszeeB0BOvfXpkxSOfmG62q/bjz1sCyftRQXqaJnLtJsMyRHq46ZXqOnTGgK071RM1yLIhwUplPmf/Mew9tdLS09K/irM8teCGWpQlfBb/wBP3H+86LwSpe3SGp5Ke7nZZEAWKt/pHJ6g7N1HXZxTpxpceYPT/H5xXdd+Jz5R9X8/lBksSTqqFeVIsNH4Xl8IjupG4Pvqatas1THTXmaBKthiCtI5RN/DMB8DfxgYPfHXUSoneGSSkpUxNG3LJJIpAjPpjqW9tvw00lEnn5wXLj968mCzA+pOwHt/XXNVcrn+nxj3ltLU1K4s5z7Tquo61axobvH4cke60/2FHZiftfPp8+upENHNVS+FCjSSEgADP5e3y6/Lrqw8L2e73Gk+pPb5663RZMbKeWal/wDwZPVf4Sc+gGw1pnBFmsNBbVqKJ/EnUYkeRcOp9AvUfz9dI7ddsBHvG6aPecnqUzh/gO5W+3vUmZAz4Z6GVOaKTvuOiH0xv657619FlyssFKLeaCO23KQ4Mkpysvpysf0X+uRpg08zAzS4p4EGcNsT7k9APbVKvvGtutU1VbKSiS5FuqueVYm926r64Hm/y9dJtQW1C7R/aNq9tRDH2mxcS8SWHhejmrK6sjkmVuRgG5mL9kwN8/wgZ/DJGI8afSzfrpJLFZ5GoosFSoxzlT94jIUfwr+LMRjVdjuNBxHVKtzaO3Xc+SGs5SYanvysMko38W+e/N2ft3B9xqrmtL9TfxQchT5lOR8QwfP+Bx6t20CfD0qBaw/pNG1T2H+n1A3DdwuOBTfVkudvnY5o509B8UJBypGTvsB6jJ1oPBHB9rudYsVJVNTQsvO9LUridf6S98HYDGeU9dXTg7gGhtKCquCrNUEAsrHK7dOY9/8AKMKPQ6tFXbqK8qviwFWiI8GYDlYf5T1A/TQFmp8w4xxNVpwMmQ4LTS2qmMFupG5juwGS7n1Zuv8AvbQiusdLfIDScQ0cVRG2WV0yJIf4lPUD1PT1Gr9Zw9CgM0y1MeN2YYlX5/eHv1+eqj9L13oaeljFNLGlS65WRTuo9vU/PI9tZLSF5U8zdlG3JmU8SQv9H0yC33WG6wTMfBp8hZeXcksOnL/H8JPUNgDQn61a+LGK2ysa0XIEE26WX/hZyM4KNsA3sduuAo0HvMck1VKxMs7zOcrktJKf4yd8/wAu3L100LHHcwlPRQAVyIFjpuctEZB15CAPN35emQdycDRihAP6kC3ZOFHEd4srHaCa2cQUUkNREgWnyBHJGQ3Uj/m5BPf/ALiNtP8A0e/Rpf7rXJPSzTWukRtqsHt0OAfjO2OUgKO+dDroLlTMbDxxb5JJEI+q1vJ+/gUHblb7ab9P69Lnwnxbf+G6SMx1K3e1FCqczEhf4geoI6Ee+421hdXYFzUZakohw0tU3Di8MCeO7UC3O3VAINfQw8lVD6loxvjbqpIyAfLjGs24pqLlabvDdqa4Qzx1rvGJEH7uRVbPNy525hlsY2bn2UEE7twZxLZOIYmlt1STVjeWKYgSj5Y6jPcbaof05TcHUdueaE0yXRm5jEiFlqj0OEUght/8RSMb5LEcuhqLyz4fgwtq12+nqVK23/hi8V9PFxDSfs65NvFXU7gc4U4+MHffs5zjGH3xq9XyGupbC1aK39pUClA9RG5EsDggRSEfEBgmNx3Rs78uvnmpoae9q0dkr5EqkwpoKqXEjDqAknSVdhgHBGBtqzcC8W1dkrIrJfGqFhK+E5BOURtirZ2YHoQdvc6ZWVkDJ/uIOGHtH6i6Wa6VdTSXejain8Vx4sUYVgVG4kUYDEA5yAMjtto/wRYa+juMFXw5fqeISEGMsMwT+iMOx7ZG47LnOoX0gcGVlwvVXe7DVR1cjpHOIsBAxBPK8eT1B8pU9AcZ3GaVSXW7cN3hqikWSOGQj6zRzIQEydwQe2cgHrgjVmAZMn+4nAMdTd+I4Kq4Qy26rtFLFV1KtIKOoXnikmAJeJH9JAOZT9lg2d2A1m6cMWO41cTWo80hU/8A0bVyMBlT51il7sM4wfNgg4Ua1HhO/NxtwfJRQ/vlK+G8Jk8OogIwVeNz1wcYBwRjZ9Ujing64Udzpo/qht81SiviU48WoSPLGNjsI2HMuDliclugOs67iBtJyJ10BG4TzgThWoF2ljSc24QScqUhU85H323wfcoBuOhzrZrlw81RwbOtRQ0l8lVByEPyvgHPJkjc9lz0ONtYhNxXUWaCiSSN7rB4gx5WSogjxnKv1GNxhs7BemSdadwnxpZOIbWKZa6QPyYE6jlf5Og6+/KSPVdQVkepDOVlT3KdW26CmoKmks9WklPcX8dKa5ZSTxJBnnikySHyo2PN5h275pxtPeKsKvFEc1PWQqVZWGDKnRwH+FgQOYY6MB3JOtC+kNa2zUptokN5paou9I3Kn7tieZ0UgdW5fEUr9uMgrgnFNp+L0mjNtulPFWUIwWhqB4odOXdoz1TbDAHIADDBONEUFLDyMGZWZHXUqFPebpZHe40lRUBnJV5Kd8K8uMiQg5Vg4GcEEcytjGx0Vpbzw1xhTD/xJalp64jzVltU86n1kh6ke683sBolceD7fdlil4OvUcVQY2VLdVnIYKQcI/flJGAcnc5wM6oVTw9UW25H9s0s9LWMfNGBycpz8SMNiv56LBavvkSpAdcy0V3B17oKcV1jrob1Y3HxQrz8vzXOQ3tnI740Oti00csqvGYRMOR5Ym+E5yrFTvlSAfwI76k8KVfEdLcea0TzVLEY3Phyv/Cc5WQezbHV8tVRw3xVJJS8QCOzX+JgquIjA7f5lOR1+Y9F1wWIR6TKY5wZm9I95sdUz0NY9NJVyHw3hyqpVr1iYdCsi9Acgnl9NW+3cS22+CCS+UMQnkTmirKMiOeMj41YA7kbnsMBjy9jZqzhVKOqr/8AxHb0rrPWU8Yjnt0WDHUx58OV0HmK42PISRgHk66yinnoK+7SQwzfs2Q1AqI4ZImlmNQAVaNMAAh8g+bA+WNZCx0M3NYYZE0qDgJLbeHqq6J71bahRzwqyxzxdMsvRWONsHl7Y9+q678PWu4pw9RQVVzgY+LQyVkZgqYKjGOXJxlWB3J2BBPmOxo83Fd6hEUBlqaqjjIkpuSYiaIHKsmQdyBlc522Oi1PxTNKgoL/AEdPeqcHJl2jqEjO4cAddt9sMTtkaudOLvtBzb5Z5kX/AMZX76zOtzqHq4Vk5TSVBLFfke5H4d9F7Vf0FTihrpbZMcc9PJgofmDkH8QdQqzh2z3uepew3hfr0pw9PW7yE9cjPxZ65Gfnqq3Th+7WqT/jKeRHXYDBZG/HQFujbORCPMH5zTKPiOCtqzb+KLUkbgfuq2nHMrem2cjburH/AC6Zv3C/15lltTJcaeMGTmDkcvYKWA5l/wC4DWc2m5XCnkDVUjRKPhLeZDj5/wBdaHYbxRzlJhz0U46TQPhf9P01k+otTiwbh+/950ADqVW4Wq+0DIsMtTG0i80iPG7KreismzDGN+ulrWfHvUqLJRm11QI8zzc6E+/7tlyfXI7aWiU1VBXsicyfgSAI1AwB+OkyDvuffXTFVUsxAUDJJ2AHqdQ/rwqNqCI1H8ZPLGP+7G//AGg69q9ldQyxxF6q7/SJKI2ztqBPdIFcxUytVyjbli3VT7t0H8/bTptk1Uf+OqC6Hfwk8sfyI6n8TqZDS09OuIoxkdABoQ6l7PoGB8mbrQq/WcwDW018uaNF9ZFHAy4IhJU/+/qfwC6G2TgOy22ApN4tfKc8zSnqT1J7k+5J1czlvi2Hprhk9Bj11RFZDkHmR9rjaRxMy4l4Ymt6GWlUy0YJJUDLJ7n1HvqvqqeG0k3lgX4j972Gtp8AZOd9UnjPhFqxDPbPJImWMHRH9x6H26aYUa5wNj/3iq7w5Ad6f2mdzzSVtTnHKo2VR0VddSuI18GL4sdfT3+evWU0vNByESg4IYYOR669pouQGWTzE7gH7R/tpkgDflA7LfLH/wC0cp1EEYZt3I8o9Pc6ciXP7xwTnoD3/wBNcRrzsZJD5c/mfTTyL4pJJwg6n+g1tFjH3ncQMjGRyeUH8zr2diSVGx740pXI2UBfYdtNKrM3KvmJ6e+ujiZAZ5ijQu3KNPJyt+66Rr1c9f8AftpIobMMRBP/ADH7bf016qeISikrEm7Me/v/AKa4eZdHKHIjRTAGDzKeh1yRtjUoFQpkZSIsYVM9ff8A10zyjHOp5lP5j56yK4jWjUC0c9xoA66GWUq3TpvroDf217jVciEgCQ6mlzuMYx8XcaHyoRs4w3ro4cddR6inUoQVJXtjqPlq9bkcGZPX7iB8EZB666UdddyxGI4c5Q/Cw02QV6nIPQjRKnImE6AzpuogWVMEDI6H004pzuNdY32Ou4nA5U8QBWUrxS88ZKSKcqV239Ro5w5f2L/V51Hit1XGFm9Svo2wyOhx2OCFLEsqFW/P00HuFAyn09G9T/fSDxLwrefNp4b+Y80PiIxss6miQzLJD4kbl4SeuN1PcH5e/TIzsVZnhjOe3bVH4dvstNOIalwJMgLIxwsuOgb0YZOG9znIyDcKWVJoy8HMVBw0RGGjPpj9cDO24yAQonh/iRU+Vd3O67w4EGymSB1IJyPbXpXPoNeJylMqQR2I0gCd/TXoAc8iIgCO56h699dhT+euRrvbGuyy9TxdiQemkBuQD217gY9RpAYOuTmJxyjHvrzGFOnMD014U32OpmSNdQc64dMjbOntjrwj013M6BBNZRB/MDgnvoNU0wbnjkXONiDq2OuVIIG+h1ZRhwcbOBsca2RwRtbqV2kHKyo00tVZKgyw80lKxy0Y6j3Hv+h/XW7fRH9JcSQQ2y6z+JRHaCpJyYN/hbuU/VOhyCDrH6mHdkcexGhSmptFSaily0BPnj/r7Hc7/h00i8Q8MbTk3Ude4jrR61bh5VvfsZ9wRMGRWUhlIBVgcgj1HrrvWDfQ/wDSWtJDFQXGdpra58j4y1Me+3Xl9V7dRkdd1p5I5oUlikSSN1DI6HIYHoQR10LVctgyJtZWUODHNLS0gM61mcQwOuuxrnlOuhrkkWlpaWuZki0tLS1JMRaWvQDrrA9NcnQJyNuuvAM670sakmIsD014Rtr3SGpLYnHTrqk8f8dQ2Sf9i2gQVd9kXPLI2IqRT/zJSN/TCDzN+IyuPOK6xYaq2cLcr10REVRWkfu6Zj9hSdjJjc52QDzeYqpxyhjqWvtwS12/6zcHcFKwlvCiTB/ekuMs7AZDtjYk432pu3ZxKufL5IlpuVTHw6Gp5Qb/AMTXUq8zVC5fPVSyg4jA7J1C9OTJOg1HV1lPfzDSVC1/FMpzPXSR+JDbFxthRs0mNlUYC7EkAZM6w25qqGrpLHXeCU5v2xxLIpk5O7QUidWkP2m7bZIzg2Hhix0FFRLRtT/syzANKIZ5OWqrB0aeqk+whORgAswyFByx0M1wUbV/vNEpLNvf9BGeHuHqC2WaaueuqXSV/Eqa1AXqrlJnsRuEzjGNs4weriYaqjsdLUcT8Tn6lDTy4p6d8SvJOOmFxh3HRVHkQjfmYENM4h4wttntaXCSKoBkZY7VTLEBPXONhJHHvyIPs56dQGbBWl/sS5Xqhl444omglp6UiCgokY+CJCdoo9/MF6u464IXPxAQsWOIXgL6oMu90reK7pHfuIacQ22N2eitbSEmRt/3kx6tv1z1OQPtEW3h62VVxlinumZnY88NINgwGwd8f4cYGAAPM2wUDQy1W2eorz4hR6/Adyy+SlG2CQNufoAoGF2GGbCi2kU9pt7W+ncFnBkqp5X2RRnLSMdt99s9MjuxNGwowJgCbDk9SJxNe1s1lrKuGRJH5AiSYA8U/CqqvQRAnoOoGBkZLYXHW1ryViU8/NL4hFZXnLhSSTgffc9gD7nGCRZuNL2OL65KO2SPBZ6eQ+JWt/i1cnQ+Gvpg4ydgCfXDFuD+FlnuEFIKNQ4wKWhZSUiU7mSTuzEDOOrdyqjIvWo259p1zt/ODeDODBXPDUy07fV5SHihd8vPv/iSNjZc98bnZR21ptQKDhemcmeKpuY8rcqZjhY7hOUHBxt+7z7u3QM1ca6O30EtJZZGnlkYrUXDnHNK42KQnGDgbGQDlQeVd9xEtVrpKKdKviSATSqvPFbFfkWNOvPOx2jXvg5Y9W1cWLj4mLbs/eQIbdduJPFrpD4VIGMrz1EuPEbpzFj8Tds4CjOFxtpVFXTWoCjpJIqishQs7OeSnpAMZdyemPQ79NgcB4fH3GU9dU+FBJFa7dF5mqFBVY0xtyKfMWPYnc9go31ld4u9TfClut0MtPa+b93DzfvKlh9tyPxPov5k9+vCgTioF9TGTuJ+LJa1p6Gz1EjRy+WtuMvlkqB3VR9iPb4Rue/3QOo7aslEAMQUqENLNJkL7HA3JPYdT6YyQZ4b4RkqpYhPC7pKpaCOBgvMFO7AtgBPWVvKN8cx0Y4sNltVNLQmpjrrmqNHFFS5FNRg/EeY7yOe57927aJppWs5c8zNrDZgIOJT6aoSkUyhQz9E26Ed8a5it8lbRSVFQviNKSQO5z0x79NR6zI8KGNWaR/KoHXJOtBsCx0kAoY4RPXIq8mNwcbAAeo3P4DRKAIpJGZVySw9oO4fuE9uqaey8RBkDoGhk5gTjfyOex1ff2atVQpU3ENTUEbcyRDYuoHb1ySBnvv6bU/iGy0cVuknrh9buNTGCqhjmNiSeYfxAFfzO22muF7zJDVQ2PiCSX92MwsCAJB0AP5Y9vlpe2UPB9PzCSFsGR9UtNaKm810XJGKS3xR7knCqmT/AG0Pjtwud++o245p4sYZvKFXux1LheqvMbwQFo6WNjlQMcuM7e+N/wA9NW6Wb63NFbVI8fCEgb8oP6DRNZK8gwNkDdwpHd44Kf8AZNgWSWqmbwmlVcFgGOMfn/X5cu9qstslkqHWputYjrDggiIMMZB9ck7/AM99eOaThq2yx0TGS51SnnlHWFDk7em2Tn8vUVWz2iWrpZLnWMYoIQ0ic52PcAfMkfnqU1iz1ZxIXZDiAqKnuUSz1z07S0Uv7yeNPKQB1dQOmP5ZOr5XXe3tY4rfYImFMUWXx/hZiD7dx+n66r61812KUFqgeKlBAKs+XY52BP8AT+eolphqOFzTTXVlkoamQM9MGHiIuciQdcKff1+eKv8A0BkfSfb/AHlseeP/ANvn/aFquzLT08twrHCFs8oPUnB8qjuf97DfViuVa9XJ9RoiyQyIhZRjqo7/AJ5xqtX+SqulY9ZLgwj/AAeX4QpB5eX/AHn11YLZDLTU8TBeZ5IV6bhcgb6ta+SpbqDqNq4EGX21JUU7U55jJHysrLs2fUHtuD+eubbILla6i2VZRqulTxF+yZY8g+Kg9vtL1GQemSLIttnDc7qcsjZz88jVY4gtUsrJLRlkmhlDKyfEpPRh+oI7jVdR61Fidy9Jzmt+ozWzQipEUic6N5EztlWGAQfUAjbv+ulXXKvQqXcR3GgjBieLcTK787c3Y7k7e++lTVcNZCUqY1huFIwEq82xXpzKe6kfl002io1YIqlHR2cglPiBO4O/bbOuoy2DmZsr1NiRrPNV2221ctGfCtFQsYqXGSaBi4wfUxswI6HGenTWmV104f4asdTaeHXiuNwqYfDqq8fCFYbhP99xk9tZXLVVTUjpTKUlUtFMmdnjZQCp7EbN19fx1Is9P9Qkp/rxL2wSlKefurshKwSEb4ONj8xrlZFThXPoPtLXIdQhasesDuN3QVEF3pa2CSaklhhilgnjOGV1Gzg9zt06HOt7+jHjWLiq3tT1SpBeKRQKqFdlcZwJU/gPp1U7HtnGJ5ZuIOadKZUUJyhEXZOXOFHuOg1yyy8NVVPX2ipljvFCOcBt1Vc+dXP2lbOSvbJ7gaYaqoJhlgnhurLMa3n05paAcB8VUPFljW4Uy+BOhCVVMzZaCTGcH1U9VbuPxAP6FBzHYi0tegZ0uU67OzzXoBOugNte65mSc8p0uU660tczJPAPXfXulpa5mSLS0tLUki0tLB17ynUknmlroDbfSwPTUknOveU69wPTXupJPAMa90tLUkg7iKkgrLRMJ1kPhKZEMaFnUgH4VG5Pt36ay2WKivVqAVhNTzLlJI8/gw7jWx6yzjOzf+FbzNe6UBLHXvzVaEnlo6gn/E64WOQnzej4PRjgvR3BDsbozC+rcNw7EG2eonWJbbdQPH5fjG6zAdWHvjBI98jvji9Wh6iSOopiFuMWBC//AFgOiN742BPUbHtqZX0iVUIUnlZWDxtuCjDofY/6++YNtrpLhJJQV3NTzQDlmSM45ZM5DA9eUjcehyN8Z0yDMp2/2gD1q689RubjpY7eYqCmIrd1nllyFDDYjscA7YGMbjII3qsl/np6maouEkldFVgJPTud5l7cuPhZexGMHPTsf4stNVVRSVdFFG1yjGZ1xgTr/wBUD74xuO/zBzB4Ps1H4X7QmmFVVn4yw+D0wNZ16etQWI5mNl1hcV54nlHwn9dqFnlqzJaiQYFVSrP35XH2WGcEfiNXG3pSwQ+BSRQimj2kY4EaDvk9z/s6HVtwpLdTST1UoWBwBKmd5B7Y35h2P4ar3F9dWVASkgdUs08fNTvB/wDWF2zn7pB2IO49u+DMznYZsqpWNwlgbimip7hLbbTWRNJInLBUyJzRxPnaMuOxzse3Q4ypNIukk8dXPNdpJFq0OJWl2ZT1wPQfLr136kdVzQwAQRxCSQjCQINse/oNGLbTftKCmh4hEfjxeWkqTuFHaKX1HZX7dD76V6XyfX2Jg+o84bOvt8wPTJW188c9K8lHFG4eOVTiTI6FfT/fUbasE1O1zgaNEjp7kcvIkahI649Sw+7J3K9DuR3w/JTzx1ElMYjE6Nh+YfCfb1/lobcq6CIPRU6CrqPt5byx98s3r3GN/TRdhSvDIef5g1SM4KN9P8Qb5IUMlU3hr0Ve7H0A7nXksE1bEElUwQZDCBW87e7kdPkP7jRekVLzLGKvwkvgTkiqCuErAO2OiSdgejDGnrXaq+4VxoKSmleo5sMGX4T3zn+Z2Hoeuh79Y1oIfj7TarRrVzXz94wlXHWBKa7zAVQAWC4E/EOyy7dOwk/POtD4F+jxqlUrbnKDFzZWOM5yf7+539ABqycEcAW6zIK65FKqr2Zi+8cf5/Efc6sbWKooeetsZPhOOaaj5uUOPVCfhPt0+WvO6nWDO1DxHun0mfU45j1HTQUiLRUNOpC4BRNgg9SfX9dRuIaaz0KtdJ69LXVoAxnyAPYuOmO3qegz01D4w4ztvD9lpnoqdzPVKfDhxhgwxnm6gYz1OeuwbfGK326198rDVXCYSkNlVBPhRk7bDuffc+/bQNNFmobjj7wm65KBz3LlxtxZcL/by1knjNNB5atqfIlBBI5lUjKoQM825645QDmi0VE82EiQeHzYAAJHMe227N7Df19dEeHrJc5rnFUWszR1aNyq6g5P8Lgdv4Nz/l661nhnh2ltNzhk4lti000yAI8ZzAW9CPsE9SvTPr10Qbk0gKryZgKm1PLcCVjgz6Oai6p41YDDTH4mYbsPTbr/AJVOPVj01pNDw7U8OeGbDO09MihZKSoOTj1Ruq/Lp/LVtpITN+6pgqoowGC7Aew1xPTpQKzzE7/Ex3LaS3ah7WJJjSrTqgwJ1Z44q9j9ZV43XrA4wV+Y7/PppjiysgsVGZty2PIoGST7D/4A1T779IkNI7Q0ESzeH8EzHAT1AP2vf7PudA77xDJxZAUpKn/jYlPPROQGkXPWM9/l1/E41kunZ/bAmjXIBgcmVrizi+611U58Xkp87or+UDP22+0fTbHoDvoK3FkkcJjuCLcLY7Z5HYo8bdMxN1B9v1HTQ+6yt9bNPFC88+eXwQuynO/N7+o/PRrhfg6puFX4tRH9bqDjMf8Ay4x7+2ttqVjECDM5zJnC/C9PxE4NiucJpWGZlm8tQg28rDbm9gMA9TjYa0uw8N2fh6DlpIc1DjlaRlzI/sB2HsNtD7VwXQ+G0sNTItxjACVMJIEe+eUEfEPn+mrjw7SVaSFrjHHUN0NVHsSP4l7fMfj66Bc+byphVdeOMQVcOHKC+QJR3ahSWFj8D9UPqCOh+WqVxB9E9fwyJ7jYK1KulIzJSTjzOB6jYNgd8qfcb62DiWSC22mWrAyFG22SfkPXXzt9IvGd/ufiW56pxRZOIEOef/8ACN3H8Oy6lYdDtEu6ovLSqz19suFSws9cLLcQ3IrVG9PI3TCyDG/boB0Hm6muXajudFX1S3+nm+tzqQZql+Z5vdWGxX5HlHuRogaWguplVSlLUIg/d8rNTuR1OfsH55XrjHfuO9V9poDaK5JbpbHO8cx3ib1hLDII6gnGfYaM/pg89wM+pSB1KRd6CCOpDRySBGCyKvIBITjJHtg58x/ADV34QW91tP4l9s9NeKAH93HUOY58Hsr7c3X7WO2+NtRFs7UdUL1YGN3oEw0sdSgMkRx8MifyIxq+8M3S2Xh4ollWjncYMUzDlLjqqOep32Bwd++htXbfUMqOJeoKOPeSKKkoWs8jcK18gqIAyy2utiJmCMPNERsSjYG4AwQrAbZ1XxWJVRU9BxHbXq1qUH1dkw1T4bZHNucSAEFW3BDDqOmtptvAFLVRxTXWExvH5onRuWZD1yGHQe24PcaA8acK0HC9Ql0gkSWJlkNRBIDychGTIWAJhw+G5sFeYZO51TT27uRwfibmtsSocN2L6pVi8cE3xAVxz00rYXJ7ZOChOMcrhc42dtXS8cUwXKmhouLqERmIGKrglQkKjdJACBupAO3VS2xPLrEuN73X26pprjQQz0lVGGaOfmXldGbLcrp5ZVJ3wT5ecjl76ufAH0lU98oRbr5TU8k6ry8hHKrf5G+wf4RkZ+z31vsK89GVDAQbxBZqI/WLZQV8VNIlW4NJVS86S8/xeFN0KuCCOYZ5iuOmDTKGG8cI3WSZYaqnCyYKyLnO/lYntvtsdHfpQs5tVua4009T9SMxg8Jj1pjhwjHf4W2U9PIDsdBbBx9d7UUNU316CnAR0k3YIRgMhPQEbFTlfbfRCjevqGDM8Y6m38M1nD3GVIvitTQ3FXWRoi2xkAIDcuw5tz6HfbWYcSfRvX09Y89smklipp5I5ac4SpjIPNgZ2YDPMPUNtnOrPwmvB/FSi52iQWi445i0Ywg/zIM8o915l9l0auyXGjLm/wAI+qyRri4wEsImQnwZ1Iz8JYq3KSCr745caqrNSfVyJwJnqYdTUppLxU0NIZFkOJViaI/uznBLKdxgkgjBJVjgd9FqDiuupqaO3cU24XOzc5BSr3ljTmCtyy4JzGxAIPMeVhjGCdXz/hrlJJTXe3VM00X7ymniTlr4ojuGbHlYAnHUZHKxG+h3/hoRU9fcqmn/APEdoqovGpZKZSrw1AUqfEjXzZZSUOBkEk8hGdFhtwyhmaKQdpkrhKK2x1FRDYFhr2jYM9urG8Orj26wygnmH5n1ZdFrmnCN9pXhvqoJYV/wq3/h62L3jcbSf9uR6k6zKwXPhKLgG50kFFWUvFVK6ywVblh4cYZQEYZ8x+z8I82Nx111ZfpNFXAbfxjQmrUn93NJ5ugwDzfEv+bzY1maq7TnoyHKcEZEl1PF104SrJbZabrWXOyy5UQ1AXxlUdeVxlc/7IGotbe+GK6hhTie3RzuJwDcaT9zPHG5Jjm5ehGchsEBSPhOlUcLW69LJPwldQjzbmgqsZkP8DfC3yycd8apt7oqm3xyW65UskEsQOC4xzIfiAz74YdRsd99E+VZWJkjjMtFw4OrXilquFLrBeIqeQ+JF8E8J6MGU774HXGcDA1Vq6KaIGO4LIlTTtnEg5XCE+YEbEEHzDp1bUagqq+lWK401RNHUUrLC09PIVZ16RyAjfp5T+Hrq+23jC28SUSU/FdriroCDGKiNVjqImGx6EBs7EYK9T1xqyMp9sGSys5OepT2liqaFqeLMkkSqnP8LcmfKwP8JIHyYeh0e4O40uUTtbbnL+0aVTyCKux4m3ZX7kYxvzD0GjVTwVHVUrVnCldTXWJEOYHPh1EadGBzjbqMsBv0J1V5LDcayGJZ4o/rdNJiahmzHI2ejHpnOMbd+XfWdjMnM6igjAl8houH7xtRztb6lv8A6vUbofYN/rn+HQ+t4UmoJ/EHPR4OzqMxn59h+PKdDrZS1YaJLXDUO+UUwTfY5uhMjYUA+5GPU6vVkuptFZ+zuI4amkPLtGVyg9T649xt89YO1T8GUVmBwwgy3U3EEUHLDb3q07SQSYX8iR/XS1fYLPRSJ9ZtN4elhl3Igm5FY/IEDP4DS0vOmqz2P3mwMrAtSSPz18rVTA5CsMIPkvT88n31PjCoOVFAHsNOlCd8516oA/8AjXtE06rz2fkzJrSRj2nHISM5OvMEaexkdhrjoSNbhfmZlo3yfLSxtgD8TpzfS66hAkjLAZzgnTUsfMpLY+WpJ/hA+em2Qdep1mwEsplR4o4VprsxqEURVSjZ+nOPQ/31nlfQ1dNVvDWxNA6dQemO2PUa2t0674B66F3qy0d1pjDVIQR/hyL8SH1H9ta6fUmo4PUB1eiW4ZXgzJFHjNyICFX9NOM6xoFUdOg1OvdqqLLKYpl5oyfJIo8r/wBj7fz0JLFiSTp2jq65UzzdtTI21hidgknHUn/eNPAGPMSbyNsxHb21xHzRfDnxj0A+z/rpwK0ZEafEw8x7D/TVszPqLl38KJturt2/+NOx8pTLeWJO3dzrxArjw1OI1OXbux03K4ZvKoCjYDXZTueys0jEkgDGw9BrqNDG4CjLEdD0x765i8hyRzE/CMddOjHKRzZH/Mf+g1yQEjkTx4ldS8OeUbYPr7eo0yozp+RypyAFIHlH3B/fSjUyjOAHzgAbc59vfWLLjmNNNqt+FfuNco9NIDB212VOCSMdsaWANUBjH2kapg51YAZzuQe/+uhVRAYskjMecH1B0fU77ddcTwLKhxgPj8/nrRLdvEzardyJXV8p3Pl7a7UjOnqulaIswBKjqvpqKpxuOmiwwIyIGyEdx3btrx0EiFWGQdeqQRjvrtV9OuoRKAkdQLcKADIIJB7407ZLtLQSrHUyEIvlSXGeUZ+FvvLsPcYyMY0WKowAcAjoRoXc7eACyAlPluv+mkviXhi6n1pwwjvQ641+luRLrQ1K1Cc0QAkxl4gc5z9pT3B9eh6YDYDSEbmUFTkHp76zy1XGa2yrE5ZqdTlSuOaPPXGeo9R31eLdWR1cYdJE8UjmyG8sgH2gT+udx3282lmi8QehvJvhWt0K3r5tPcnAg9Ne5OMHXIJO2CCDgjG4I9tJTntr0SOHGRPPEFThu52p7E4Guhuca5A39saSEjY9tdM6DOsHGl7Z0iTjXuBjVZcCcFfTXmMDHfXevOXJznVgZycYz/bTbqCMb7frp047aX5asJzJgqtpVfcrg9iO2hNRBjmSQDPp2OrOVBJyPnqHW0gk8pG3bGtq7fYzPac5EpgSptdWKmi3TI54+gOO+3Q+h1r/AND/ANJa0KpS1LvNa2bDJjL0zdSQPTuV/wC5e4GeVEBiBV1Hz+9oLOlRQ1f1+j2Ixzp2YDtt/PqNItf4cysb9OPzEdaLXK48q79DPtykqIKumjqaWVJoZV5kkQ5Vh6g6eTodfOP0QfSSbcwhcvNQOw8en2542P2lHrt06NjbfYfQ1uraavooqyimSenmGUdDkEf39tB03CwfeEW1Gs89SVpaWlrUzKLSwdLXY6a5OgZngG2+lga90tSWi0tLXQHrqSTkDPTXuDroDGvHZUVndlVVGWZjgAep1zM7PMH01Rr/AMSTXepktViqJIaNHMdXcofidhnmhpydsgAl5T5UAOMt0bu14n4sLUltllpuH8lZqpGKyV/qkR6rD2L9W6Lt5jHuE9Jb6BoYnoqOlo41MrStyQ0yjzJzAbkDAPKNyeUD4sizJ/TLNwJUPhwo5kJ46WjjmSijgoKSOMIqqnlanXJlaRXUEEuqHOcsMbg8x1R56+s46r62hsjS0lmQtJcbnIeU1DHrl9gFxv7gAAAAYVRHceOqmSitj1NLw6iNU1VRUsElq1G5klA2jjxgrHnpyk7Eattqp/q1iWOnEFtttIg+rQsxEkshyfHcAc3NsOXocAkcrFDpcOOYUTnuELLX03D1upqK20sJami8OHxo+UQKp/xJAdgckYTGxIZwXKRkFxBcnt1cEqaWa5Xutbno7S/+JMcE+PU5P7uNRuFbfGScdhdfeamCrjtVmhStvGAx8TAgpEGf3spGwABOB7nl2OZB9romqq6WgttWaiSsPNc75VZTxgN2JP2IF7L3OM5yBoc9mdJwM/tH+H7TV3y81Fzulf8AWqpx/wDSF0wzJEh2EEC9d/hAG79Bhc5sU0lXeq2mt9uURU1CpSmj5uZKNPtOxGzSHuwyBkKuSRhuR1qZEsfDfivSqSPFK8pmJGGYA9Mj1xhdtlzzE77crVwJwk0lTIFqagYiC45pGGRkDqQDnH3jv0G1SwWYjLmN19ba+GrfJ+8jhWAczySEeQnPmYDOXPZRnA9cktQ7tVVfFFLJcLj41DwrGfEhpWbkqbq+cKSBvylsAdh0GTvp7hy0VfFdYLtf5YKakp1MtNR1GWjQ95JlHxuT0U4B6duUk/pDpDFc7db7VWTNcJglXV1MzZanAOI8hQcEk5CKCchQoJxnigk/aaHjruAuHbQbVO6rHTC9Mhdlcj6tao+8kp6ZUHZfUgbnAN1s9NNDS/UYzUSUtRzSSTS+SorSd2aQ/wDKh8vw5y2CTsMaB2yhWD/gKRk8GldZqqao3Tnzs8pXPNJnIWMcwXfHM2SLJcXpmtxa4SyU9vbztG78stXg/FIR8CZA2GewHO3Ko7dYQdgmajPM6p7hTtUlLVIskykR/XAhbDbhUp4x1bqFPbcjGC5r/H92ouFqV4K7DXBiHWiZvE8NjuHmPSSX0X4V9zgnjiHj6HhCkD0sKtfqiHlpUCBRSRN0wu/ISOgzzEeZj0UZZRUFZe7j9fuUk9TUVDFook80km+SVz0HXzn8O51emln4H/1OORWMsZDqZrjxBVvPUFmVTzlGYhU/ic/06nb2GrhY7BBbac1dyAXOA3OmfTylNuY438PIAyC5GymfZ7TT2to5low9bJtTwU55j3wUP4/4p65/dgk8wsFNZYFninvB/aNecCK3U+fBiGdlZh1PU8q9zu2SdEll04wvcwwbWy3XxBdK1fcUmNCjU9IvmnqZ5MA4HxyvjfA6KBgdFXPWg17W6WQrR+NUyySlpa2UFfEJJ2ROyD1O59umtL4/uMNu4deO5iEv8MNsp2EcaZ6lyvTbOQNz3IOsueomqXM0vKpVMKqpyqg3wqjsN9UqBPqM34HAk3h2ia7cT0tLSAFiw879FPqfRffV/pEprHPz0oM9c+8krD/Bj3yAPvY/HfHrqu8BUjVDvTW2NzJyASSLtzOdySdsKAPbrqxXQtbKkU9A/wBYqHGJpeXILZBwnfsBn59jrcNu9JMFfg5ki5UVNbbU1ZLiSvfBjiztCMjc/wAXt/PG1XqeGYpKVrpeamWmE6M8IX/ELbAPj0BOcd8EbdRZqd6e32+R7rIJawScywZywwAd+27H5AKfUDSpKWqv9SKu6SmKhQM7sewXqoz/ADPvrI5VSp5E2VwWBB5le4W4jq2g/ZNQ/LMPhYjl+sL239R1x67emrNS1CU1kqKakj556gHmYDdf4fc+2qdxxy3K5U0FlgMNPTqBTrGh5lOTlvfPf120f4LvaUtTVUV5pmF1gjK+GrgeJkYJzvvg5Hv16YNCxqGG69v+JsVW3lO/eGLbZzR2k3i8Z8Mcvhwk+aQZx336Z/poRfXq7xX09NQQlLdCfJEp226En/eBn30empbnxHLPVTfu6YIwTsikKWCj3PLjv/LTNyqqS3WiW025S9T4eJZ1A223Vf1/3sLV27SC3sOoM6BlxBVphh4ft8cDJz18y83J3i5vtN6H0H+nMNpKH9oUr1tc7OVBwrbliPX29tWi1cOmmt1Rebm7CRo2eNXOWZyDgnv1Ou+FLHVX2uipKSndkYkhUG57n8Ov++mo1CKA78mBsGU7R1KpwvHJ4pt8qstukkDRvy5FOxPQ/wABJAz229tfUVq+je10Fupqqrq43hijTmYbAgDqP950Eq+ArXwv9HlfcJZlaoloWTB2BZl6azWm+kWtjVrDW1MqW93KUcjHaP0Rj6Y6HvpCXstsyv0/xGvCLh15lu+lCptUd8pYrTOklO0e4VSvLg4A+W2qCYZZp2p6YqJJIzjPcg9PxGplfn9oymXflUY7/lock7QSQsueeQFUPoTnGn6VbaMZ5iknNmTKvfLbIqw19PKIapJChBGQM4Az/Ceh/A6l09Qt6X9o+YVdMFingfqmFIHzGcYx2Oi1UFrVlKrzTyDmlTpkgHI+e+fw1Vp4KiO4w11ByGbHKFbZZcHeNvTO+D2Jx00Mcj1DuGIVddjfpCCvBNEUhj5qpoC0Lx7ZK5Y8/qcbf7yebdQtxDAIhzSTyyclRDzY8VWYYOfvKWB/XtqZbqWgrKKuvlFI6QxRhngKkPAxPK6kdiCR23zpunJJeO1r4dfTD6wssb4XlVSWxjffOQfb8uhxYvEyCtU/M9sdwrrFJTW6MQzVdSOaiuAB55Y+hQL0EoIHvvkbnWjU3BFsttgkuvFFWlOzK/KhfJDMpGG7s25yB+PfWbLRLU0U80kLVKSU8rSRKcSQzKhcSo2Nj5C3vgqeuNSeGuI6vie6x0/EtZPXVFLASIy4VJkUfEvz6sBufX0rXc+fJZsD5/2l7tOjDz0X1D2/3ky4cZ3G38bQ3S022KmekT6nU0i7GsQH4GI9DnkONvxxrdOGrzQX+0QXS3SF4JRjDDleNxsyOv2WB2I/2aMsFn4Yilu90gie91bmRIwMuuei+inv7Z3OqnYuNaq38T1V8io2WCoYC5UEWSZVXbxkHaVe425gPXfW4O1sIvp+Z2i7cMOfVN3AHbXuo9traS40EFfQVEdTS1EYkhljOVdT0I1I1uDmExaWlpakkWlpYPpr0j01JJ4AT016B669Ua91JJyR6a9AGvdLUki0tLS1J2LS0tLUncRaWlpYPpqSYi0gPTSwfTXSjGuZkxPMHTVZTQVdJNSVUKTU8yGOWNxlXUjBBHcY0/pa5OzHZqKq4avpsFa8s1M6GW21cjZM0S7GNj3kjBAP3lAbrzabuFAzVa10LctQkfIcDZ13Iz69f1OtN4v4fpeI7JJbqh3gkB8SnqY/jp5RnldflkgjuCR31mlvqJBNLa68JBdKMmOpp+bJyOki9MxuMMD082OoIDXS3C1fLbuA3V+Wd69R6hnWshBDNFURN1z5o3G/47EYPQggjVe4hhmoZp7rb6fzggVVNG2FUn/meyH26H54Be7RSUrmvpwSg2mT29c9sdfYn0J1IiijmgjqKblMiqQCV2kXcMrD33yD0OiAzcj3/mB2Vq2D7fxM2qJJqqU1VfKJZAfKSfJH/lH9f74HVjuMlR41saKaa1zbySIfNDJjaSPPUjuO49+szivh0xVf16Mv+y3fBgBw0L90Y9x909x8smRTCJYxFRRqSF69FUe/9tEV0q9eYue567dvvGobNDZwC7CYy+ZJ138YHoR/btp6aSKmhaereOKEAgocHIPr66cF2pKGeO01szukxLMyx8zUzH/mAdl+8O/XrnIOutdTS3HlujJNMpDQ8hzDyndWT7+Rvn+RGs/P42HuaCgD1nr94Rorl+2KV7bUyy0AYhaGrkfzMuP8J87qp+y3bO/YmBNElqLQVMf1Z4WKmIjJ5u/+Yn16fzLDtJUTGjpIfrM7DDrkFV/zn+g/01bLRb1Ipkvjx1FVEvJT1jDHJ6Rv6jfyt26HQhXYdw6hORaMdGAKGyVl2JkrFampSc+HnzvjoSe2tQ4Fu8trlaGsTxoyBzTn/EIAwOc9wMdfz9TDgonVijRkMDjGNRrzdKexeGecyVjbwwx7uSO/y9ScAdz2I+rKOm33hGlD1tn2mpXys/Z9JRXQ1kDxkNJ2MQUY9cdPUkY9tZ9xZ9J1fc4jBaV+qQHYz4JL/wCQHf8A7iPkDjm1VnvD3al/Zl5MNHCJfEp2jY+BBJsAkg6EZ3BAAUnoBg69htFSKxoJY3E4OGAO5B99wqn13J7A9dKa9IgGbvaMLdS7cVe8YpKyr5poqxHrqOduepilkJdCc5kD/fPpnze+rZwPwWb1XgU9QrQr5stlHQdwR1Ujocbn1UbatnAv0cO6x1V1UwwjdIwCGPyH2c/eOWOr3Pw/bZfBFtQUVTSbQzwrjHsT9r/fvoXU61R6a+BN9PpC3L8zrh3h622CmWOkhUy45eflAY+wHYf7OiDQGpR46yKNo32EZGcfPT9ineCXwbkipU4yHG6Sj1U//c9tQPpAvNPQW4mmmi8VwcYbYe5wf00nYsxx7xntCrmdR3W3WDCyV0aQ55fCkbdT/Ae49V7arH0m8UxT04pEikVWGfi2cdjnoV/rt11lt4uM09Q8sszyu55fEfqR2VR0x6AbegOmLdfpY3NprIZrjQuf8GPzTQHuyN+Xl3/po5dCy4Z4GdbuBReI3cKteYyO4QA9T0U79PU/78uo1Dbq+7SJNB4lLAh8tQTiQ/5fT8Nvno9Q8LU8kouElUtypi/LCVXlEe58jr9lhjp029jq92LhyerAMimOPttjR7PUqZJ4giVuzfeALXGr1GLvA06eVXuEEQEh9FlXp8mH6bLrRbBaqeWmRaHw1oz0SM7t7sf6amW2gio6b6tGmI/l1Oo7XyxWSfnNQkEzb8sYyJsfwjc/5ht6nSPUOtpx7CNaq9ncn1dMtuTncBVXpyjt7f7+es/v30kGnqzHaOXKHDSsf3YPcD75+XlHq3XRn6R+KKa4cPh6NDNTluWVlOynsG9OvfbWJ1kzz1DAJzsBucALGPfO3+9s6wTTjOT1K3XleEluuX0h1FZRtS3fxno33LRtyyL/ABKBsRv06fPpqr3mzvOv1q3zmvoHGxhjPit/mB6H1z07DXFHQVFbKIoI5KiZz5ZOXP8A7R/U/gNaFwp9GtVSwSVc9fJS1cijlC+cH/8ACKev8x2x0117ETgf3mYDWDLSl8J8DV98YCKJYKdWByykIPff4j7n8BrV6Hgmy0lr/Z9RAlcZU5H8cZDDcnA7b5OeudTeHai7Uv8AwFzp41RG5RUIvlA9em498DHf11d6e3U/gBxhmYfEd86Fat2PcIrqBExG4fQ9W0k37Y4Rq2DD/wCrSMOYeoBOzD+Fv11T7xw7Q1sr09xpJLFdV+I4xDIw6dT5D/m2wdmBONfR9fc6axwySTOvhqOZl5gMD1JOwHz/AJ6wb6YuNaTimdaO2IsMYODXyLy5Azsi7Ft/tN07AZ33Swkbe5WytVGZ7Scc8V8DWiOjulNNc6IkR09TCDJjIyFDEbE/xDYbgN2zXjjie68WySJV1vgxfHHQIxIkb1JH+I49SQB2x009Q3a/cMyGCOQVNuK8stPWP40NTFn7Oe2e48vrk64qrRbOIoZK/hiRKCbDPUWucYfA6+Cx2kX+HP5nWq6ZCdwmJtZlwplLpLpc7T4lJEEqoJpMy0EqeJE53+z2Y56rjHv01ZIrRZ7y6R26drVUIQpp5siNmI5uUSKDzEfdPm22B6684Wgo6+5eDcJmpUI5WkmYq7gHHmfGQoGdlGfca+kuEuAeHbdaY3rEo7nG0Xk5o1NMin7ibjf7xyT66zu1m07SMiXrrz7yicNWDiFuFZKO6+DUQQ5eirEkzzkHzQyjcBGG2SfLkZ321nfE3CVpluim2yJb3qoeemWRv+HqEJIZPWKRWBBHQHHqNb7Bw/crHXSV3B7eNSMMSW+tc8rj0ic7j2D/AIMBsc943tAqa+W51VDV28HmlgpTEEhjqcqrRMc4XxlJzJkKvLkgc2dWo1B/0nK/EsacCYlBbr/wjfUm8OaCaNiwRmPKSDuMg9PcHW08F/SDbrvA9rr51gMoKTRSqDHOCMbq2Ac+o5W920MMdfQ25IK6Gkr7XNCamlpJ5cssAwGWGYjLmPfmyuAoJ+QO32nhy/RytYKlZHj3ekk8k0Rzvjrkf5Sy/LWxGfoP6SjEjmXLjSlkiipq2W3tdae2wx+FHSKGWcDHiCoQ4dy6rgZ7heYYGdUW/wDEE0F9Nys1Q9soa/HiUlPKQscmMnc4wT122yDohZbjxHwzdqV6tpau3xlkwv8AiLE2A6e42BGMjmVdgM6XGFHZ7pcVoLnETJUL4lPc7ap55kxzpJJEB5gV3yM4KONsavp2Un4MzfLCBLpxHw/e6yOm4jthWqaIxG5UCgSl8bEr0ZWG+OxBABONAL1wjXLbv2lw/PFfLXykGelc+KAd+V0+Jfl27417xZw1cLdQfWoFhrLcCAKykHMI9xguOqEHBydtz10Aoa+822s+u2CuME4IaRU8o5huw9Cp+LByME+mjDgHDyoG5eO4Po66utU5kpahomO/hjv816avNs4/jraNKLim2RVtI4xicHp6q/Ufjn0BXTtJfuEeMGVeIKYWi6k4FZHH5GYd2Udfw3+Wur9wjcbXTrLKqVlsk8y1VOfEhYerAfD8xt76uGdBlORMioP2M5uHA9JXBKzgu5ifxom/+jqh8SGPqQCNmAwDncDbzaq0dBXU08lBdaSSlnf4omQqBjdZAe++c47Fsasth4bu8MMtXaRzxR5miY55EcDOAf4gMbY35d9tWC+3W72VEtnGVpF5tdRClbQzzj9+9Ow83JIPjZMg7+Yj7Q1h51bn4myhyvMqVlaotsEVbTV0s9SrGREyVkjxsRkb4PLjm6cygZ31d7RxVR32eK28U28OjqrLJNFyTxA/bBGOYbg5GDjO+2iNosdroaOalshor7ba0io+pTsEqBkbNG567AHB6beYartVenSireHqmhiSSmBkt718RjeFCfhQjJcg5wowvKd2wMGM1ig45+8yCjPfU1ng2efg2nnt1sSkv1kqJGaShnZRKTgZKsRhtsHDDGPtaqnGs9pqalxYTUUqOTzWi4wlljPdkO/IPQqzfhrKrjcLvGsckTytCg5+QP5oc5BwQdsHIyOx1dODOLKK80zWm4yLXypusdYR4mO+JO5+e/vodypHq4P+e02ycfIlfuEtzt9SYqIVNLCwBCEs++N8MAc7/Lr0Glq+SWemY5pbo9JH2hqoRIy/I5G34n56WswHx/pP6zHasOKTjHTXoz7fjr0DOveXXuYLODkaWO+usg+XH468I9s64TLYnJKquBvrxQp+1nHbXlQBgH01zT5IJ6DWZIlgJ22B16eg03g5JOw07gdFGTrkj13Pt2/HWZMtGAo39vz14yg9wfn0Gnup8v4en+uvOXGSxAOqGdg64UUFZA1PPEssTfErDr/bWc8ScMzWgtV0weelzscZMf8Am9R7/nrVMbYAAxpuSNWUggNtgjHXWlNz1NkQbUaVL1we5iahojy45p265+z7fPUmWPK+GsvNM28pA2A9M/01auJuFTB4tZa4hlvij+77r/b8tU+WRY1MUZ7+ZiNydO6bktGRPL6nTvQ2GE8mkUfu02Vf1OvIyACWG3QAdTptFBy7ZCj9fbTwDc2ABz469kGiINjE6VSSQzAH7bdlHprp35UAC4A+FT29z7/79NccwVRgeTqoP2j6nXK/vMknA6sx1JyeqvPuc8o79yfT56kIAVwdgNiR2/hX39TptU3znlC9cfZHp8zr15CPIo5ewUdvX8dc7nM4jrNHI/IdnOAGHT5H++myhUkEYI16qgDA3YjBwf0/vqTGA8axMclh5CPsju3svp+esXQDkRjo9Xj0PIwXfI0gN84304yFCVO4zsR0OkEA76xBjYYPUalgWUYJwex0HraB4SWQDPoOh+Wj6gA9NKSNZEKvuP1GrLYVM41QYSpAebK/jp2N86I3G3MrF02J6Ed/9dDCp6YIcdR66MRw4zALKyvckKnMM510q9cjOmIJMNg6lqCSQdQyV8cwRcrcGUzRL5e6jt76H2+sqLZP5SzQlgxUNgg/eU9jq1qo5COh0NulrWUGSBcN3X1+Wluu0NerXB4YdGNtJqmpP2h+z3CGujj5ZE5yMRuBs+Pslex/hx7r9wEI25gRgAjGQDnruDkdR76zSmlnt87PGA6MfPG3Rh/Q++rpZLxBXQgvIeYHAdj5kJ+y+TjJPfo3fByxSabV3aGzyruofqNJVrE319w2Nup14N2zrgMeblbAb09d8bf7yDsQNdKRnXoqrVsXcvU8+6MjbWHM6+WvQN9eEdxvr3WuJTMQzvpYPppDbpr3m1MYnROeUa59RrvXnLrokInmNtsZ1zyjG++vSPN+GkOmw1JwcGQaymWZGBH46B1ELRNyPj29xq0FQQRnOBvqHU06yLgrn01vVbt4PUzce8pdTSy0k/1yhbkkHxL2YehHprTfoj+kaa2VBjwZIHYfWqNjvk7cyn73v0bocNjmptVTtG2GGR2Og1XRyRT/AFujPhzLvgdD7EdxpT4j4YT/AF9P37iNtDrwf6V3U+17Pc6K7W6K4W+oWenlHlYdj3BHYj01M18u/RP9IlVaq04J3wKqkdsLIOnMCfteje+D6t9J2G70F7tiXC3TCSFtiDsyN3Vh2I9PyyN9Kabt/B4MNsp28+0IqMb6914p7a91vKRa9A0l6661wmSeco17pai3a4UVqt01wuNSlNSwLzSSP0G+PmSTsANydhquZBzHauop6SllqqqeOCCJS8kkjBVRR1JJ6DWf3OsqeMXHMktNw3nKQMCslw9GkHVYe4Tq3VsDY+VTVvFdUlXdoJKW1RMHpLZJ8UhG6y1A7nusfRepyenfEt+tnDVra4XOUhS3JFEg5pJn7Ig7k/kO+iqqQBveD2W/6U7nnEd3ouHLJNc610ighAVVxgFseVcDffGMD09tZ9DDc+IaD9r8Uxt+zqdwaa3CPzSzOTyvKvQud+SLcKAWbPKQ860UNy4qlj4kvEDCdWJoKVhmmo0xs/8AHJ3LYPVQu+MO3+/pB4VNapsCHIFQMHldgQxXGxc92GcdAepIWp1HnNgdCEU1ihcnucW8eHWPBMpatUDnji80VKObm5CM+eQlQTnbIJYgLnXPGvEEVRP+xeGJw09OM3K5zHMNMW6hmx55Tj4R0wNiF8tRuXEU1wgW02U/VKWnXFTVwnJkb7XKx+KRj9rOFxhRnc9WuGaWlp6NM09ugJ5IU3Bc9ST9piepOg3Yk8TQOqLz3HooolontVtaZaAyeJUzytmWukz8Tn0z23+Z0RstHU1tZHQUqFw2CT0UAHqfl/PU238P1U0xhEZhjXDSeJ0iHbm+eRt16ADS40vCcPN/4UsFNJUXiXyzIo85P8RHwKB1+ZHTJOPA7mWGdsmGuJL7aOEOF2kpamOrrqh/q1NDFvLUtnzcgHSJTgZPxMe/LymozWq8XOth4n4tKSV02I6OjU/uqRFA7e2Rt1yd8d2uFOG3S/UzXKpSrr6olJZQSnhjOBEpbAQHpn398G60dpqbxcqioqpokt9O3hRsgwhVTgLGN9s+gOSe5IB4ETG8yzWH6EkbhW0fWDJWzSeBQQgy1MrkKigb5z/8Y/LVeoqqe5z1F1dpqanqZmZSzZkfblEcK9vKMFz03yRkA2zjupMtDS8PUEKCCVueWDl5ueJD6DqS+AOv2sZIJ1Co6NZKsxW6SGGYx5lramQCKBFXmPKR6KM+UbDGMA869G/vHf8AaWRAOM8wUtbFQU5qrnF9WihbFNQhcnmx1PQse56ZyM8q8uaXxLxzUNVuwVaiuY5gibzRwHoHbbDOB0GMDpjA5dR+Nb/FWV0tr4dmeeNSBPXSDHNv29FzkgdST3PVrhTh0vG1Tz+DTrky1kuA0mPiCZ2A33OcDbJGQp1WjJ7/AFnPM8vsfpIvD1pqLnWtVSH6/WSHnmlmJMcWT1c7liT9kZycDzHbVspV8GSe3WaA1tf1qqmQjw4x38Q7qFBx5PhG3NzHyqXWjgp7cqu7Wm0cnNGVGKuuyMfu1I5lU7gyNjIyAAPJqZbKVaWiWGspkpaQtzwW6JjzMezSkb/n5j2AB1uzqq7Vg59TbieZI4dgCUU0q1ZVpGK1l1lUl5z3SIHfHbA3wfNyjbXFZclgR6e0xPBEPLJM7gOxx9pug/yDP49dDblV1NVXxpH+/mTyRRR/BGPugD+Q/E9RojTWUxctTdZSzHaKCLDMx+6o6D36DrkjWApycmU88kbVlA4pira6sIXyx0+ZJKiT4U9OUHqxOQM77jQCkhNRJHEJAokfzOd8KAST76M8XXdKm5S0cXK3gnlwrcyRAbYB+05PV/mBt1EUcJnrYKcMUiyvjSdlVjuT+eiXIACj2hFNZVST2Zon0fzMbAlLRU5Rqh2UuPiccxAye2/8hqyRwQWrxHVRNWvnlJ6Rr6+2R/vvqDaY4bbw9TWmgHNOkUYnlTcs5weUH/N6d9FzSU9qWNrjl5pUIEQOydtz3OCfy0EWI5ncKc4lcoLfTieS63Mt4RbmVD1kPXf2/wBdNGvq7rSS2+mdkpUKgkgb7kn/AO2Y499Eqmmqrkh5IyVZvCXHwrkEnH4A76hVjQ26int9GgkJXDyAZyc48v49/wAvXRKMGxu9oOV2kn2iastlmplejCz3GZFCEjIi8oB/HOf9O9VlsElXc6q4SVzUrQoZfHfcK4wBn2J/sN8A3F7JS2m1tc72eapeEinp+bGCQcFvl1x/TVfhp6q5Tx0xjZC77AjqScfnvrUUeZVuxkmZDWeVfsJx8QpY+Kq7iOywWN8LUUxCtEg5WfPceux/L3zq0yWals9CJ6zz1EnlMY35QyHH482P9jVK4ls9tsNvjqKN2W6/WDLDKjfYz8LDbykDOeoOMdCRcvo6/wD1yuaJWzy/WiAslO/xA9SR7YGc9x09lHmeUTu69jGNiiwbkhfh+gn4ovH1epqjb4AwWOOWn5lJycA9e/Lt03PzOsS2ij4L4VinFf4rxBvqxUAAO2clcdv0A9NP8biycN8NRPTGPx4kVY2yGchTzDJ/DWFXTiS5311Sad3iToB8IwO2hq67NSwx1MXC6fO/lj1IvH3GV0vc0tI87tTowwmdlwf56D8RwWt+GYKKMCSraJXLgfHgE9f5e56511dmobPaGJKyVtSeTDHdcnBx/f307w3Yaq5W2kmUFFK58Q9t/X+2m1KrWQEH5zEbiuT3BnC95kp65LTdJgWZeWmqH2Ei9lPodHJAPrdNzjJToPcaqt+t0c9ukQbTQkqMdcruD88alcLXk1M6Wy5sBWQYaN87TpjY/PfRFhFHoP0nqQr5y7h9Q7hVEkiucVVEXCzHlB2yuRtuNj1668qYYjQtNGOYu/iNGF2UEYJ/P+enbpE0EhhXJ5MFG7EZBH4/z09baeSkuRkbBhAPMsnRgSQB77Y0NuGMiZgEHBlYmlraCrkrqOBpIp4DHVRISBVRYAI/zrjPuBvvqXQ1NPTwmut9S/glR4Ew+yCSd/T0OP17krrHGLcJabHgGTIQtuAR39tiNV6GMWWaaWop2qbZMf8AiYhnKKw2mX3B+Ieo1mCE9XtCgPOG09jqFbneJ6eJai0h6aWnZ4p2QgiUEkqepHQkdwRjUC/Na56ejazsaStpYBJC0akeE4JIHMevMD+JI0SpY0pYIJxLG0NQ+7HDJMnmBG+wyM9cdtx10Z4K4ZsHEJrfHMlG0FEY1Qk4EnM3K+euwKjGxPLnprG10CbsdTtO8N3zIv0aS1vHXEEv1hxJW7STh2wsS53YD7u4x8/z0O9XHg7g6OSlpqSGvr6gcsrsBl8j8lU+vvtzb6x653U26K3SWWJaa7UJeRK2MgCaJweaFgPjHMHAz22313ZWl4ojlmlqZPCJwwdyZRIdynf8+/6DesNqTstbCjr7zO1Rpx5tK5JPP2lu+jjjB7FcquSoTk4dqpi86c2fqEjH/EGB/hknzY6fFjrrcVIZQysGBGQQcg6wgmj4colgo6ulnetg5Zogo8ijO+DvjdgebGfRhoh9DHGklrnj4WvTyC3s/hWyrkHljbtAT90/YPT7Ppo2lSULgcCXFw3BGPqm0Ab766Cga90taTWLS0tLUki0tLS1JYCLS10BjSA3zrmZMTnB9Nega60tTMtOcb695Rr3S1zMk85Rr3S0tczJFpaWlqSRaWlpakkWqb9JXDU9xgS+2aBHvlBGyxodvrUJ3aEn1zup7N7E6uYG2dJR3Ouq5U5EqVDDBmOWa4090tsdXTsCkgwyn4lboysOzA7EddtRJImskniU6N9RY5kVRkRfxgeg7juNxuDmy/SFa2sNe3EVKqraqmTNyQLgU0hyBUjA+FjgP+Dfe1DIDK0boPQjPTHvpzVYL03DsRa6eU209GMVCRSQSyGOORWj5Zo2OFdeuCfyIOqFeoK20yIlvfNFVjmjrCM49UA++O+cdj7as1FFLb7ulsnDSU5zLSOy5GM7xkjoRnIz6/LRS4UdPUUsqPGWppt5Ao8yN/1F9GHf11cOxBA/UQd6VJz7+xmYBIaaF5JW5QcGR3bJY+rHr+A/DboWsVPVXi2PRVkcsFtXP1WqJxJCT1AH/TbuO3XXlvsaUvEi03ELrKG81FIDiAgnY79j0JJ2PXbfWkUdtbl8NIzzg8nKBvnpjHr7axvYKATxM9Op3Ed/Mq1rtENrQ0scAhK436lvfPfROl/Z3JObhX09PBCoMoY8zYOdgnVify9SNKW+WmjvSWusjCyhzHTrUEqjSYJCsQchM47Y36jVHrqWsrLrUteYEgk8Us9FGvKiN6vjbp2G3pnWTXM4K9Gb+UtfqPUv9Zf+HZqeOh4brqllnpwkNXWr5IpsgBT653A6qDgFj01TxRVEdZPHUpJ9bz/xBlceI2O7N0VR26DHTHQyLfbXquVQhYOvkwoOR0PKOgHbmbbsCfh1pVl4LrxbaauvMDtBAygFSTMsQ7kN8WOzHB3O2N9LHdNKe8mFojakdYEq/CvCdZd6pY6aEscfFjlCj1AI8o/iYZ9AOutWs3B78NwUlVShbjJTg88DrnlH/pk75Hv/AKatNgpqCCkjgs8SGFhzcy75z3J7nRCejNMTPK2/3z0HsPTSLU62y1sxxp9IqLPLRLFc4xMj4hJwVzhge4b0Ptpy/SU9qoWqXOEUbf8AwP5DVOvPGNott0Ipiy1Bws7IMp/39MEe2T1zjVU4x4xuVVTrBPJGY2UPFKuOSQH09f8AfXWNdL2H0jibveiA55Ma4n49uktQRTsIIFbKoQCzkfovyHruToNVXD/xBTs1EWWth/xqIk46fFEceb/L19NVirqmnqDHEkks7nHIB5j8yOny6/LRyx8LSiSKtuEjrNGcwpE3L4fyI6f7znTVdOtY9PcVm5rGO7qCLfQXC7TZgDQwZw877M3so7D/AGTq42ex0lBDyU0QLH4nO7NovRo0vKlawV2bCVPLyrId/K4Hwv79D+eLrw7w0ssTMwKjGCWG/wCGqvqwF57lk0xJ4lPtdoq1q/rlDIYattiOXKTD0kHfoMN1HuMY02xuoZKeshWGbkyADlG91P8ATqNBOI66i4VpSyoTIR5cDLv8h3/Qe/Y5hcuObzLMWE5p05g0cKkNuO7Hv+ijtpawbUMdghysun+ozS/pNuBoKMRUckaPIu5OCAN98d/x29dYXX1crVE07zs8j7vPKeYt+fb9PTOrFWXY8TRGNHEN2iQFqZmxHMPVCe/sf7Eg7fa6ysrPAjglafmwQyHmB/hU9P8AM2/oNFaatKgS3cG1DtafT1I1FWXGjrBVUMjRuw88LDInH8YPQe5/LVhtlkoL5PAGV7M0hy1NKp8Jj3eNsb/I9NunTV24R4EpqGMT3MCR/i8POwPqx7nVqqqKhuVMaOWmDQL8BxgKf4e4+ehdTapOBN6aTt5kLh3h+gscAjo4vEmbq53dj/TRlqCoaUSSsVCnKop2+ZPfSsdDLbxhZDUouxVv8RQPQ9x7aMV9bRpQvO0sYRVySTjHz9NLWpB5hqLxB8TiEGdiEC/EW6Y986EXbje0WmdafxgGO5jUEkD1CgZUfPHsCN9ULjzjeZ2aC3S+FCp3nI3I/gX1/iP4Y1QKhjU00lVRTPJH4ZknDj971OW3+MdPNt8ts6tUj+/Uxa8LwJc+PbvPcYp6iSI11OzBqZ4JP3SDuSPtP1B5th/LI6tVmqWI/fTfZTHlUf1/kPfRKgvlfZak1tFUeDAxy8Uy861B+Xc/xbfj01PehpOKhzWSYWi4SnnnoZ/L4w7tE52I9s436r0JHlhAcQU5tOcysNUsuLfLiunLZSAbqjEYznufbp89MVXB17mb6+9QIKtCGgTnKjboFbop22B29x0Oi8O8P0Fqfwp6V2ceWR28sgPpuNvlqy1FncwqIXE8D/DkYPyI7H/Y0OLyGyJ0ALwJi8N2Mk5o+K6WSOpQ8pq1jw4PbxUHX/ON/nq38OXHivhnFVanF2s8UYlaMt4kXJncgDpj7w6ZwfTWi276OKXiSIQ1dKEiUYE7bPH/AJDjcfwkcvyO+gN84Bv/ANHgetttSldZy/NIjEp4bHbmBG8Z7ZBIPcHpojdXePUOZ1UZTuE0fgfjGzcV0SvSyeBVhQZKaQ+Ye4PcaI8VVlqgtc0d05G5Y8svOFCr952J5VX3b8MnbWCJVWK41pazXKC1XxT5YXIj523OOVc4ORjmUfNBnOqxxZeuKHkkt/FilFVSy0j5Mb5BAkLA/vWPZgT8/s6F/Cspys38/CndzOOK+ILLOj2SnvrQ0cM4eGqigcUbSnJYeGcuinO7LhWIyV2Gs+u9FerBc4q6NWgV2Dw1FPJzRv6FHGxH69ttS7zSU8zPUUxljhA3gdgXUd8kYBHsozjqBqLZrtc7G7lGQ0cmzUc6lo5j0BCdQf4hg++mSlSvq7+ZjW5PGJp/CPHi1UAo7mYI6mQDMVVgpKw6c3dT6c2COxOo30jcPQyWuS6WoTLNSuGNHGD4yJJ5pOX7yq+GDA5GSDkarNHQ2LiQrJTLNZ66RsGnqD+7kb0il6E/wnf2PXVtp7NxLaLGqxNUVVIj/uZeRi8DqewG4APUKSMZyBnOsGcKQW5HyJMEdTNbLxhfKCulqIJg0sKhWUDyTRjqD6kZzk74z6DVhkpuEOL6dqpGi4YujYbnB/4WUg783ZME79BggknOj3EFqsN4nStqI1tk1QMxV8C80ayAhXjnXoCrMBz7ZVg2cZ1Tb5wfeOGfEhucDCGQ5gqIfNCx3Awe3MuVIPXIO+NMFbcvp5EzPBz1Jtw4Tudprf2ZcbSClUQsQO8Ukhxjkf7OR64O3TV84V4I434bpzLbrlAXZsyWmrBMTgfZVzsT79R6jVE4T4vulko/q1SFu1mMYiemqVLxkfYdRuVzgo2NsgEg760vgLjeG6UUcfD1Zhuj2K6SeYe0Mu5x6KQfZV66HYtnNZwfiWKr7zm23SgS5PTU7TcI3vmzLQ1QzSTknqMkDf1BX/MemoHFaVM9vrLXxbFLbqahJrrI6EyRCYqfEg8RsBI23Ko4UEkDm6ZmfSfxRZXtn1C82uRWZuVIqmImoRsEnkkGQq5wOYF++2s04e4zvFpZqZ5hLb5OYCGobxUUHYHP2gMDPQ4GM741ZcWjLrg/MqCa+O4P/bTwQ0/1Cd56OiJMTvyo607MGUYJzzI/QDP5asdPx5HWVDUHEtJBcICwBEwwRzdHSTsDkHffB67ah1VHwPea+BKapk4dvRyB4ij6rJJ9pcjZfnsCMYzqv8WcM3i1JClwpT4eeWGohPNC6ndfN0+Wd8HW9e6vOOROWKGxniXKXhiiu3JU8O3KXmJJa31p5JSMYZQ3RumDgnHc6pktjuNkrpjPTyUyRkuGkPIQPY5/vqK1Tdobf9cBPhK3JMWbyMwxysp+90zjfbOrVZ+PppbXGbtHFcqcsFaKdSHjP2uVxkj72D1GRkY1x1S3joyiMyd9Rul46vdBCKdC7KAMfWPi/TbS0Ugp+CK8vNT3ZbcQcPBOmCp9iPKR8tLQX/po/wAMt532mqA517+elrwNuQuvaEwVYsAEk7685iR5Bt669AHU+Y+muXP3jj2A1QmXxPMKDvlj7aRIGzDPoBrrBA38q+3U68xjthf56oTOzhs43xgdhpcudmOB6Y/prsbdBn3J/wB/pror6kE+muATsaAznlH468KY7k6dwTknp+n+uuSeUZH69TqSRplGN/y765K/Iew07gk53B9O+uWQZ339h01JIzIoOc6qfFnCkVw5qujAiqBuw7Sf6++rjgcxHxED8BpuQc/Xf02/kNRWZDlZnZUlilWExSWKWCdoZYTHMp5Vjbbl9zrxSqoVzzJnr3c/21qHEXD9Lc4jz/u5gMLIBufY+o1mt1oKugrTTVKcjjoR8JX2PppxptUtvB7nmdZoGpOR1GMeIx3Hqx9NORAKdhggZGfsj1PvryIZ8qjbqM9D7n213I4A8hJHXJ6k+p0bFs8kcKAo2x0Gdx7n317BExbO5fOB6jPQfPXkaEHmIJY/p/c+g1NjiMeFwWdiVRF3y3cf3P4euuEgSRluWnPmVWJ6DqD/APo/z+WnS2Iiclnb/EY9T7e39PngDpwqh8sryEgvIP5L7f8Az6aYkLAiJT5/Tpyj+/8AvqdUHqkzt6nvi4IiAVhnLZ2CfLTjISAyksh6H++moYwo8MbnqTj/AH/v9JKYQYAyvcevz1DRv5EI0/iHkHa3IjXKW6a65SNO8uRlTt6HtpAdtCMCvBj+uxbF3KciNhAylGAIProRc7cBmRCdu/cfPRwA5xnXhA6HcaqlhU5EsyBxgymSRsHKyDlcdD66eppSMq5I+ejlytizRmSNffA6j5aAyRNG3hy7Z6No+uwOsBsqZDxCETBh6emnOX00Op5nifklO3r2OiUThlGO+qkS6HPEHXO1rUqXhULJ+je2q3/xFBVGSLyOuzKw2I9GHpq9cvvqDcrbHVoW+GUDysO/sdBanTV6ldj/AN4fRc1TZUxcP3uKqh8OVmQIBzKT5ou34rsPMMkDY5AHKdRsEIx3PQ42bbO3v09diCMggnOaqlqKGq51LQzRnII3x/casXDt7SVPq0yYKrloh2/iT1Gcnl7HJHUhkCW3eGWbX5WMbaatdXkcNLOpwDnvroHIz+em0cEKwYPGwysnYjJx/I/PB6EEB07dNeko1CXLvQzz9tLUttaLS15nfXuiMzOep0I0sYB99ea9U41WW9pzjbGvOX3131215jtnXQZWcEfmNcMN/hyO3tp79dcN11aUIkOppkkUl1ztvoLV07RMVwSvY6shHfvqNUQB1we+2NEVORxKMJSq+ik8UVNIxiqEOVI76vH0X/SDXWi4BkISbAWogdsJOo/t2bqvfy9AVbSmNs7lf5aD3Kh8R1ngYpPGcqy7HOlfiXhYt/rU8N/MZ6DX7f6dvU+zeFr9buILaK63S5HwyxNs8TfdYdvn0Pbvgtr5G+jTjmvs12RklEFWgCujf4c6fdI9P1GMjb4fp/g/iS38S2wVdE3LKmBPAxBeFvQ+oPZhsfzASVXZ9LdxpbUV5HIMOL017rxemhfE1+orDRJLUiSaonbw6WkhGZqmT7qj9Sx2UbnGtpjHr/ebdYrY9fcpjHEGCIirzSSufhRFG7MewH8s6pKxXC+XGO7X5BF4Lc9DblbmSk7c7kbPNjv0Xovcn2joa24XMXy/PHNcACIIYyTDRIeqR56sftORk9sDA01xNxAlpMVuoKY3G9VIzTUanAC9DJIfsRjuT16D2LqpCDc/cGewt6UjvEd8prJDCnhvWXCrfwqGiiI8Wok9B6L6sdgNU7iPhGslna48S3m1tfpYhJS0rTcsdIgbJRFOeZSCckrluUkE7BjdstMNjSbiG9TNcr0w/e1iJ5lBIAigB/w03xnbYkkjtULnU3u7VV0/bdfDa7XSzn69OOV409YlYbyN5QAgJGwz21hqncck4EvSqdAZMOXfiO6X6lW1R1sIoKdAtRV8vgxKgHRcDZNt2JLNg4221n9zlp72RRWYtBZ6fImuDgiWsJ68md1j7AdTvnfoaqKCp4ltZmho3tXC9OFeOnkfE9YN/wB7KffGFTv2BCkiZZrKK1ixi+r0UXxci5CjsBnq2O3YbnGk3mhwdvAhbHbweTBXDti+uVEVLb6SaQHyQwRrlmPbYdv9ffFwtljljeSV5Ep4qXKzzkgqp6cq46nboM523Orfw5AbTbXWnie3vWxlI1iwap0I3I+6xGOpCou5JO60Hie5VfEEU1m4USE0lERFUXFWJp6ZicCGnHWaZuhfB6nAA8xr5nsJxaN3Jg7iji6uqK2Lh/haOU1EcgkJ6+G5I/eykfE5OML26e2idp4WFLcXpbOtXdLvMAbhcKhwS0rHLZboAD2yd+Y5Ox09brPQcKWtqG3sjXL/AJ8gPO0THIC8w+KZjkbbKMj1IsFkpZmtzVNZ/wAPTqvMYtxHGucAtjc59fic4A96c4y04SD6Vip7HSRZWvkWSlgbDtGSxnkzjy8vU5PKAPUn4j5SDzx+HztGkcUf7uKFXwiEZBUEbZAzzONgMquSSdDamvKMpIkL7pAmcMB8JAx0PZmHw/Avm5mFZ+kC9GwcNVXjVSG41amGNVHKlOuN8DuQNhjOCe2N+hSZVe8LAly4tiNbca55I5TO3hqIiB+5TIUM2SFQ7nlXffBHQih3biO6XkzxU80kVFKQksibcy5zyKM/DncjO5wSScEQrbQ11/nipKaGQU7ECOMDDTkfaJ7KPXWhWaw0FmnTnlp6+sROZVUgQQgHHPzEY5RuOYgjJAUO2wKFe8ZbqW83HXcF8O8MQUtLDUXGllVJCBS0KAtJOx6FsYJJ7KNz/CuWFi55Ero4IaSKuuEeDDRRkSQ0uAcF8eWR13PKP3abnzHOo8f1m7S1E1JVctPGClRcZAUVgTkog3IUntuzHdiT5Q/A58H9k2aKSOKQZlcf4lTv9s/ZTI6dP8xGNa5LcCBvYE5j0060zS1UlT9eurnM1Y78yQn0Qn4m7c2+Psg9RLtVuqqxlRTIsEnxORl5D3wOvXv/APGidp4fgooo6u4z08CcvMs04wgA6mNSMsffB/DXtTc4IKY/VHnoqJ8nxm2qavLE+Xr4aEnr1Pv01byq0GX9vaYqztJFPFRW1JY6WKMzptK7t5Iv/wAIw3Y/wL+OOmqxxVenhoql4JGaQRtzVDkKz9cAdlXtgah3y/RxU3PMUpaOLIjjUd/YdSx9evrtqmwU1443qXaBmorNAwEs5OAB7E7Z9zt+mRXta5tqCG01BRuaAaRVUM4lEhJxI2eh3/8AnVijttXcKu00FFTs8dbKrMynIJ6kE9sDJ37b6gfV6KluMtPTZSjgZwDnJIHlz7k9dLhbiOWxXNlV3FC5IHmyYgdsZ9N+v9NU3sh55ENetXQgcH2mn1Vwp+HpvqkEiz1LAeLLy5w25wvsMg59tT44KiuENXVu5hdOfnkHLnfuO24wB7fhoRaIqJ6mO4ysKkPkRAjOCe5HyGiUcFZdR4xkMVHFl2c7KoyTgDudz+eitRalhAWKNHp7KlO/+0fLVVRVm30IcrIMBV+165/LUow0Nnp2NSUnqkkyyjfJBBUZ7DOST7L767gvFFQ0Zjt5WSqnAV5cHGygHfvvk+n6jQ6lo6i41UlROwWIMcs2cfM6DBY/3hvAGJXr5JVXKoaeqYlXICk5wozk4/3v89WLjW8W0VQjs/7yeOI80yfCh7EH1yBoddAJ5mpIRlFfC4G7en6Y2+ep1usFHQ1EZvsixRsFdwW3Ucwxke4DaOOp9G1faLG0qh97czjhjhaquFoa63GKT6usZI5xvJjoP5D+WTvqFxheaW08QRXLh6SQVkMzYqU8gdAxwrDGScAY9MYGd8GuLeOKiuH7Hs6mjtowPKcO+OhJ7D/ftqp8NWlq+Ay1CgDHMS3wKvr+mh20LMg8zgGa0a1XchOSJY04lquJ5jVCokLsT4sBB5kfvsO2/Tt7jGnobvb7dbY6OlHPXyoFlYjIUMNwD8u/fttuM5v9fHbbmlVbUdZYzyOSQFmTHQjHxZzuc9cdNWHg6lgv9UJqOULHgtLGSOdD3GP9/wAtUqG0+X1j3+YXbVkeYo/6gySlrbnXSuCziJ/jboqg9P8Af4eurda+LZhw5S0dFGITHHyGQnfYkH5dP9dCLreKa2WeWmhZDUzSHAU5IyRkn07jcZ9BqLw/bWqLSjHmYCR8AD+M6Lrr8xsCDvlEzCaorVNWDufI2T39f5nQm92aW5W/69Qnlr6GTlblHmx1DD+3volFP/xdXFy4fkA3+WpRkeAyGBMzEByAPiB2x899W1aA14nNM5Vt0c4U4gjvFK9BfYvCutLDvzjzSJjYj8N9K6TTmrDdGRuaMr0wN9v9/wBdApbXU3+p+t22ZYK+lPPHKTsf4T7bAY0b4dvNJd7IYJacQ3KjJ8WA7ED1HqOmP9RpUthrO0w22vzRvWSkQWqthE7LUU88T5j6YByOUe/T8dD7hE60qzluZEkIVsZBUjO4+f8AbRC4s8FRNHUJ4jxOCEYgfCQdvy3/AN46np6K3SwU31hqmKpgUjAwVyD5ceqkA7+uNaloKmZT5TJa3koKxTDappMxbkikdxkEf+m2Qf8A41O4lpqu12K2SwPKgrxJzpGxwwVimM5OQeUN6ebpjRuJIGik/aAhdBGyxK5AjnX/AKZPupwDtjPbtXqGsMUVNZLpNI1sV3/ZlVODmLLEFHwCex9dwRrDfsPI4hW0WrkfVPbHQx11yt6V8/LTpyczgbwh2wfwD4Of4jojxncLbbL0t24SR6d6aMQVYXeOaMkhXBPxODtzdM8oGRoatTSirkpijRU9RDLTIZD5mcjysR2wwQ43776JcEcL3G/wPUKqrCImGH+AA58p9W5hnHqNdcDh2OJSliMjuQOFVuFbOtRGv1+maQSc7qXYkHLMO4OM5z1yc6uvGlz4et9oqrXardFcnqEMctROMoAfu+/pjp66ql2usHB14lXhirkNNVU4S4qFDCNzvzoPvAdf1Gc6ctUc93pBSwo0scSDmeNS3OvYjHbGNO/DWXVEq/H2i7xAvpUD1jM0P6FuPzcgvCt8qVe6wJilqGberjUdCf8AqKOv3hv1zrVBvr5i4ioYIK6COlSSgrgkc9O0a8h5wB8B7OCPx+ex2T6JOOF4rtzUdxC099pEH1mHGBKvQSoPQ9x9k7dMa0vpFTcdQjR6rzhg9y869UZ16Bga91hmMItLS0tVzOxaWlpakkWlpa9AyNcknmlr3l0uXUknmlr3l11qZknGvQu3XXWlqZknnL769GwxpaWuSRaWlpakk4nhingkgnjSWKRSro4yrKRggjuCNZLXW1+E7uLJO00lvqGLWmdzzAKAAaZj95Oq5+JT6qda7odxJZ6a+WiW3VTPHzkNFMnxwyKcrIv8Snf9O+tqLjU+6Z2IHXEzWrpoapAsyglGDIxGeU+uo9HUyQVZpKvBYklGznxBj5Y5gOw6qM9QQHaB6yOoqLZdkjjutCwWoVPhlU55JkH3HAz7EMvVdOXGn+tQFY3KSr8LA4IPb9e/b88tn9Q8xIAvHoeRb5bqaqoDFKP3JPNFIoyYXPf/ACnuPx0uDvpArOFro1qutrjrvBTwqiR15eWPl2Ac/Ft0IHQ79No9srFq6hqeq8vgjkniOwDk7Er909cdifTBLl9sy1tMlOCBURD/AIOVu4/6Tb/+0np66wvUaivaepVVNT71+oSq3z6nW3usrqWm8IVUjsATzNyk55Rnoo/366JcOst+kS31GZJaZQIqrlLpyD/luT8WMeUnI7ebGSI4bt015uklFW89EseQ8DD95Jy9VPuPT9DrW+G7JHSwpHTQCCJdwQNz76F1GKawvUlANrljz8y6cGcHWyz00dW7R1c7gP4pPMpPYjO7H3PTsBq18k/iF+XliA6Ebt/bVe4Zqlt0yRTMWpW6E9IST/I/pqz3+72+mtc0hqI1dB8Od8/015K8uX55npaFQJkcQV4lJYqnxo5oooJGy8DNgKx6FfQ/w9+2dCONOOaN7XJSwq6zdDnY474x/vB1l/E90krayWWWpL8pJVifIgz9keue/wCZztoWlyFYFt1ZKUqMYppmbDEfck22BPQncb7DudVoCQHsgj6ztK5zc6tJeduZQo6gnCL8z/T9D111w+Kyv8Sk+ryVFsckszNyPG5+1Fn4flnfO/fMmy8LyTus12ICqcpTofKu/r/vOrvQW4tGscEYWNRgADAA0bYyhcQWtGzkwRYLDSUESmlXxC55fFZcMT3B9D7auNosM9QpJjJI7adtdkn51elwJAB4gfPI49D79MH/AGLba7tQUdKqVI+qtnkZXIOG+Y656g+mll2sbGBD6dMp7g+KhobbTFq0o2V6Y2267d/mdhoLRcd2ilrWpKKoxExwrOeaFG+6rZyR8tgehOg30qXelrKhqaCZniwCY0OA/uTncfPYazSUtKzIVEmBkqDhEHqxO2Pn+APXVKdI9wLueJy3Uik7UGZd/pG4iqa2tdKmEU5RQGyBjG+4PcHsf56ocgZzvzKzHPKPjb336fM/gNHrKlbW0a26vp6msgQFoKmOPmmpR6gHdk/zY9vUXHgngmhjjFbV1MdWpOUKHIPuSen89bpctKbR7TA1Nc+4ypcM8FV16dJXQwQq2Q26hD6g9c+/X5a0e3UNZw5UgvH9fppAFNQEHjLjs3r8/wCXe0U1O5h5KWMRxrsCFwPwGvUhEYMZ5iCerHfOgLbi5zDaqAgjtop465BMzqyEZVVORqTWU6U8ZbKqo3ycDGhNwulFZw9S08cDqR4qk4Q+5J2VvT199VnjjjGokt6GhIjp5BkVKkNzeoU5wpHqfw1ioLcCbs6ouTHuLONKW0gwU3PNV4/w02Ye5PRB7nf276oFTxvVymSO5RrUwSnLwxDDIPvAk74/i66r1bWhvEYNyK25Yndvff8AmfwB0InqERMysYUbcAbu/uAf5n8BpnT4eoXLnmLH1rFsDqFrvTeLTm50M4uVvZvLIgH7k+kgPQ79Tt7arRdhV/8ABhqysJBUrnlQ/Pv8z/rovwzR3kVxrray2+I7EOvMkwz9sdWyPlq42alt6ymnSgit1dJljCu8cw7tE3cfw7EdwOmrWoMYbiVRQTkSqWfhR6mQVV0dpaj4jCTkfn3+WrVR0NNWolsq6XnjDAxFAQ0L9Ay43B+W/wA+htdm4WqrhIGK+GmcFm/tq52uw0tsUskWZf8AqsPN+HppNYrK3cPrr3DMp9p4Yu8aRwXRUuCjAimIAmUfdbGx/wB/CdXy0WCgWij54+cqc4YdCNe1c8NLT/WZ5VjVSBze/oB1J9hqpXf6TaKCcw0imaZPiC42A7sdwPlvjvg6ind2OZsFSvkw5xdfqThulNQzKXTonwj5E9vkMn21iXH/ANKdxvA+q0RkoaMkiSqwBKy9xEpyF/zbn3HTRDjK7PxQ01TbKn63NEMvSNjnj75VftD/AHudtZNd3R5y1UGMvwlB2P8AF6n2HT9NdWk5yYPZqG6WDLna4Y6fnt88VRBIRzzbqytjPKcjJO32cj3PYpZ+L5mt62O/wT3q1Ln98zBamlP30c9PTBO/cnpobM01MfEmmdSRgQxHDYO2NvhH+zpyi4euN5pwCqUlKG/w8Y5v7n3OifNCDmYopPciX+xCkpUunDVSb3QuxzMq4elP3ZE+y3v0PtqRwPY7JdqotcKtvroHMsUpKh/vKWI6gkbbe2dwOpOGr3w3Uy3GzVMjwKP3jKm6r6Sx7gr77r7g7aepzbOIMQyRR2e7MMR//m85/hP2CfunbfYjVXrW9PQZZWKGX39kUz0poJaOMxAcrQPH5du2D00QsVj4joDy2Gpkq4XAU0M8mXAHTkc7Nj7r9OzDVFsPEF94Prlob7RPV28OFHMx509kk/kpyPTHXX0n9H934bvNpWq4ekBJA8VH2mX/ADD+22lCV3aVyM8QlcWTKr1Y6Oe/R1/E0E9JTSK/1oJTExJKseRI6JkkuvOh77oSNt4sVqvcPDlWYmghSkiV0tFwYzm6RtzYYP8ACsjKrDkUli6HOBtrb+KFtElEBdI+csCEVP8AFfG/lxuQO+dh1OBvr5luPFlpsXE5ho7rAxCywmWBHnokWRgfDnQEDJ5VJeIlcjfm3yw0zhjhDgzr17RzANy4etF78NOHqo2G4ZJS21hBhl5tysUoyMHGQPUbAY1nt+tl3s9zd7rQm31mGVlCcqcwPxrynp7jbOdFuL4LzS1f1usBmoZlIpqmCbxKbHNnETDZcHfl2x0xri0ceXCjgNru0Ed7to3WCqyWjGNxHJ1XA3HUYyNtM8Z+scwZSehC1o+ka5w25LdxjSw3m3seTkqGBnUeoPX5E/hqdNwxZeIqRqvg26rI2OZqCpYLIPYZ2P6fM9NAKzhmzcTM9Rwlc/HqSvPJbKyQLUL7Kx2f886qFStzsNz5Ymmp6iIjmXlZGU9wQ2Mn9NaqWQYbkTNlDHjgwvfaSpo0akrIZqashKryyKVYEHyNvvsds+hHpqfw9xbeLIqyROZKGcEzUcqCWHmHxeU9Aeu2P01Jt/0g011pVtfGFBHXRY5RKxxKn+VxuPxyNcVPC/izTz8JVv7WjZPEalbAnj9CFG0nplcnGdtdIP1VnMgII2PLJWXOz8Y2GGghutVY1hBNNSzuZaBSx35f+nuO4xkYGqbcOG7zYKl4brSyJTVKgJUIeeIkbqysNtv5E6DUK1VPI6TSSUsiSFkXP7xSPiXlO/4HuPfVk4U4suVFTyxyzJJQf8ymmVZInU9+TO2D93pnVk2WDBGDKOWrPHIlRWuq6CSRIZGUMcnB/TS1oZp/o/uTGolnnszkZMUIE0Te6E7j5HS1z8K3/wApPxan/TNwwBuxz7DS82PT216F9vx10MDYDT+YEYnADZ64OvOgyuM99dkbkdfbS5OxOugZnczgAk9Mn1OugAvxnP8Av9ddHABC7a8UZbqR7nqdckzmeHO46fLr/prxRsQAD/L/AF12wUD59AO+vME7E6kgE5BBJOcnuTrwqBuxOfU9TpwBQMAj56WNvLt7nrqktGwOUgNsPur1/wBNeMpYbYVe++u8YJAB0sY3zk/y1JI0y4G2B8x/TXJ5eXbcdydOsBk5Oc64bsST7DVTJiMFVIPt66G3e10lzpzBUR8w6qcYKn1HposVzkbbdQNclOw2/lqDPtOEAjB6mTX+0VNnmw6tJGx2lxkMff0x6aFwjfnOM9genz/311stVSRVUDQyxiSNhghhsdUK/wDC8ttL1dPzzUg8xwCXT+/z7aZ6XWj6XiDXeGFcvUOPiAEbwh4j8xJP4k9x8/X06akJOOQvjMrqATjAVegVR6Y/P5dY6+XPOBzkYH8A9B/v+uvWYgYGcnYL169/9/yGj9u6IyCs8d98L5pG39cf7/113FGAhVep+Jz3Pt/v/RQRCM7nJPxafBGt0rzBnt28CcBAi8oH466XvrrAPU6WiAMQYnM9TIOQca6UBicbN3H9tcDbprrqQR1GsraRYIXpNY+mbI6noAJIyNdBcjG2ddZEm+yuOno3+ulgkZGx7jSi2pkODPV6fVJeu5J4oxt6agXK3xzqxRBzdx6/66JheZQw6jXSgNt31mrlDxCSoIwZR5qeSElJATGDse411T1DQqiHDKScPnqNWyvoEqo2wFD4/PVWraJ6V2HISmdx6aOqvWwYMCelk5EIwuJFBBBHqNOAHqNBaeVqcBkYshPX0+ejFNMkigqQflrrKRzLV2Z4PcYuFDDWQ8j7N9lx1GqjcqCejqMMSrLurof1Gr1gduvfTVVSw1MJjlXPcEdQfXWFtKXIUsGRC63ZG3CA+Hr3ID4FQBzt1XosvTJGdg+wyOjYHcAi0QzI0YkR+aHpzd16Ag536467jO+xUtRbvaZaWQrhnQ7hwNv9DqVYr5JTTrHUyKC2FWRjhZNjhX9G3OG9yDkEg+edL/DLMryhjQ+VrU2tw0vHbS0xTTJLF4kPwj40PxRnBOMfIZxvtuMgHleBBGQcg7jXoNLqkvXcsQanTNQ+DPR0xpdtLS/lonuDDiehTr3Hr1GuQTnSGT310CdnR2Oeg02QSfXTgG2Drw7EjO2rThjZyBjXD9N+mnCDnXJ32PT110HEoTiRJYg6tnf56EVdIY8su6fy1YCNiTqPPEDzZHXWyORMyPiU+5UImAdCUlXBVxsQdHvo940uNkusWagwVsflViMrMufhI7g9x+K77FqspSmWX4dB7jQrUJ6OvwsNL/EfDBqB5tXDD94z0HiBq/pvys+qKH6SbbXWKKahpZai8zHw47Yh358ZLF+giAOS57bYJIBZtduqTWyXa61C1t2nHLJMFISFM5EUSn4UH5sdzv0+bOEOKbjaLjFE9S0FVGf3U3Z/Y9jn06HJ7/FtdPxlcuIaWntXDtMtLcpkLVVXLhoaWMHBdBnLsc7Ljbuds6T6S4Bitg9YjHU0naDX9J94a4n4hmpa0WDh+GOtvsiAsrH91Rof+bMew9F6t/Pvhjh+KzpPM80lbcqsh6ysl/xJ2/8AuVHZRsP109w1YqOx0BpqUPI8jGSeolbmlnkPV3buT+mhXH/F9Dw7RGnBmmrpuZEjhALA4yQD97BH+XOT2BYuy1LvfuAKDY2xepO4uvlmtFhlkvFQ0UEm6NCAZAVI2XIwHboMHIG+MEkZVaa2LiC5RXC9UzQWakYm32lDzID2L5+Nu5zt3OehDS1M97vQq7jyzVAGYaWEcsNOpPQD5nr1JP56LYOHae0UyXO/pyu4zFRrgO5HYj7Kg9fkc74BQXk2El/eMQdg21/3h3h6x3PiqaKapXwqMMXghU4BztzFj0G27nc4woOMKYv8lvtM0dutb04Smj8SRjhUbByXbORHCNjk5ZjjGSc6bpuIKO3WqeurpBTiNOarkY+HHTR7YiXYnmPlycFjsFA8nNlFdVVvHldMsAa38PCTxqgtnxKnB2eQZJwScImTvnc+ZtAkY4myIAuf3hKvu154+uU1o4fqpo7Wxxcbm2UapXOWA7pDkdOrHc5O2rFVmi4ctdJZrMqrKiEq4XDQqRjn67OwJxv5FJ6s5Op3DNLVQ2QwUtClNRjBggQBml7K8h7j0GMHt5Rhp1tskFAJbnWyM8ply07DmAkJPwZ+OQn0BxnYH4linBmVjlhtTqRrRRw0tHCKmkMLRKC4Zed3d+/Ltu2yqoyWA6hefPFxuFSZlp2DGYsfAo43z4bdCWI6v6t9ncDDf4fNbXyzTeBTxs05BKqsnwA9WZ89W7sDkjyqQuWapcb8VUfC0P1SALV3iojCkKADynoNsckfQgDBIA6AgjUKfqaVUcbVkvijiig4SoWqKioSouMqARImPlhewUDIz8wM7nWWUlvvnGF6avronmJbCxvlYohnv8vT1Pc69oXuH7Ta61rR1F0nIjjklKssTMcDkB2BA6Ht2x2usE62qEW6OOaWeTIjplYmaV2PV8boCeo2c5xhckkmusk5YfpOsVRcIY7SUtJaqY00UkSK4KVVZJHzc+OqIm3Nj7pwo2DkHy6arYKc0K1NZ41NbJG54oC2amvYbAk4GFHTmwFXooJyDEqqdbe0dxq5Irhc0XK0SY+rwL25iNiAPsLt3JGCNSrXQz3OY3q/zmnpBy5Zh55cdERdsD2Hb7oOdbhTYck8CB2NtXbjkyZbqWtvfh0MEMdOkQLCKIfuoh9rGepx1JPzI6aNQXC32cCislOtwuT9ZiOaNW6ZA+2fc4UdgRvoXNXy3OnmioeW12SLCSSMMeJjJAOPiO+QoGNydyCdSHoKuKyCpp6Z7fbZCEE0xxNWE77fw98Db1J1wn2WZKp7aMV1U3jvUVky3OuPxF28SGE+/Zz7fCNV3iS9x2+N6u4VLTVD7qhPmY+vsO36DUTibiOC00/1SmKzVTbBAMhT/U+356rVFZq2vlN0uxZpHbKRtvk//H5fLQFpLHaIfTXhd9nAjtqp63iW7JNXRPNEWxDSrkByTsCBvj26nVn4ipjRU5pa+t8NKZD4VFTY5UcjIG3lHYnq3rjXlqp5aNeYqyTgZEYcJyL05nYfCN/me3UNqv3eokqGMoGYnkKLLycqtjsgPReme/rg9dko2LnMut3mPgDiDp25aR/Nu7KgPt/vGvI6XmpGaMBiWxjHX/edc1SNI8FMi5OObHuf9NaBYuHaW32qCuqpRKzIrCBN2bmVX/DHMBv6bdCNa0g8gSuqsCYYmV3hqruPDlPTSV8LG11LFIix+HBwfkM7A9MgjscaJxNxKJ7VTwWqIxUrRhRvuW7j8N8/03zSJbXWcQ1Mkg5zS06ZZfshRnAUdCT/AL9dN0ldHwrfRb5KuG5W4EYcHZWGxG/YHIVjjIxkAHyhuops3Y4hXGpr2j6pf7TRx26w/X7nhdyyo3xMfRfy0kus13EdPSxNGM4Ma58xJ6n8dB61bheZw6yGoikP7srsqpnpj7JzsR10SSeGyWxoqQq9XFu0oGwYb7fjjWwVW5zADuU4hOw/UqG4VVwqZkxGD4W2TI2cbD5Z/wBNBL7UVN1ucuWc5bb0XH6a5ooZqpolYnBwAfvfL09NFUSChQyVQzIzEoi9XGdj7A4P9AdV2hSGbqdHqBAgalpaOgGLhLyJIOXxD1BO3T8SdvTQq63ySqC0VuQwUiDlWMAAt7tj5Zx0+fXU/iF57nNFAFC7ZVQPKuf99dNwWOK1W6WruE6RyMvNCp+OQ53PsAM76YKw1By3QgBp8g4rHc54c4Ze8zz1NVyx06SYeRhsO4wO532A76DcT1tLY7/HUcOxMsUI5JX5+YVGOpODjPbbbG2+ptXxBNW0ppKdPqlOzsXVDuxP2fZQMDHtue2ht3oZfBggkhbz9m2wev8AI6xNJtBXoQirUrUcnkyNXKLiDX0kjSU0z5c580b53U/rqyWG4zrajTeIsaiV1IA3PmP++h1V5WNiq46mjl8eQ71UIA5WX1HuP17eurZwtSUNTa3qaZ/EJldyjfFgnpj1G/5fgOVnD+Sx5Hv8wi0bq/MUcfHxJLRH9pTMNmMeM/8AaNTLJVRi5xSzrzMIvh3327Y39+/Tv01H8bnr5SoBJAx/fUSVJGlpn+Fj+78voRj+uiX2tXs+8XjIbcIZulOaO4PV2UyLC6F0I+LqDg/h/PVfno2kuQrbQrU10DoyuzciEch543zsAxAxnpvnbRSCeeirKeOqIV+WOSPB5gQxDe++OvTr+cviKKSfiBLnTxgRVkh5gBtz8uDn3xvjf5nScqPpMPrtK+pZ1brpBfOHS0MTR3CmkxOrHLxYByp9s5wfQaUwg50FQsg8AxspQ+bG2wH+/wC9Vq6ya21MV5oIAtdDIVqIwGInjAzyuB3GDhvzO3Nqx/XoL7YkuVAil4QA5U+ZFVQvKy/1xqtbFSQ0vdWGG9I6rQBnpZnDxSxFqdjuYzjmU/MYAPsdCb3QpNQySTHdiH+rtnlfs242BGxz7H2zPyhakeU5ESITgYzg74P5+mvLnC/JHTmVDmPxqZydiNtj88YPYEauV5xBq7CpzKrTGYqkVWjMwfmgqCP8XlHTI25gMZHfGrdVcWVVntE9hov+HiNS9T9aR8ModQwVdthkg5/LBOdVuuUtRy0RkeNHZZY1XY5HT8Rv+I9zqA8r3Pw0q8ioiTkfsHAOFcD2GxHbbXNv+l+vaEHDAuvfvGqgST1CyHIhkTmfHcgkNn8QTj30UtVcbVFKtNNLFSVCghm2NNLnY/5CdvbPz1HqG5aUonKDG3MPYHCnPvkLqZaqFqn/AIeNfEMvk36ZPrn56I8w1+sHGJimLAUboyZMJbsqpWSNNMF5SjYBX30e4Y4Tv0NVDeVknpKymy1HWovMSfSSPq8Z6HG5B6HrqTw3aIOEuIaWC9ET0s6hKKsZSI1lx/gydz08p7jrvo7xXxWKqAU9qnVkBIkYZ5iR1G235H+h02GsGuQJUOfeKRpv/TnNljce00HgTien4mtLS+F9VuFMwirqMnJgkx2PdD1Vu4PqDqw6+b+B6Ti+n4vF6sXiVVUin6xDNJiOpjySUZz6nox+1jHfH0Bw1eaG/WiO40JcI5KSRyLyyQSKcNG4+yynII/oRkRh5bFCeY9otFyBhCGvSMa6wPTS1zM2nPKddAbaWlrkkWlpaWpJFpaWlqSRaWvQM6XKdSSeaWveU69UeupJOdLXRG22vOU65mTE817ynXqjHXXupmdAnODr0a90tTM7jiVP6QeGJLvBBc7UqpebflqfcL48Z+OBj6NjYn4WwfXVQt9dTXCl+s0bMV5ijK45XicHDI69VYHYj1HfWt6zj6Q7O1irKriyghDUE/K14gXYpjA+tJ7hcBx3AB6qcmaPUGs7T0YNfTvGfeAblQPJWLcKaQrMi4ZSDyuMHcgDJx/L3A1Kopkq6XlkUqQAroWyUbAPLkdeoII6gg6k/CRvnO+R39DofcYxSTCuhUcuMSrnA5c99unXfsT6E4PsBrO8dQQerg9xq7Wk1M0dXA3JcISDzKcGZR3/AM4/Ua1qzrb6vgmK9CtiWSKLNVzMEVSOpPprL0q0rIYhTMJDKviJJnAA9T3z7eu2h/EcNYYnuNNIyyRoBVwhzyAb5mVe/bPpgHbc6X+IUtcihD1NdKyUlmIhm/8AG88k5gtZenh5sCcriWT2RfsjrufMdtl31FF8qLxRPT85/aEaFmhBwKhPXbYOB1HcdM9qK9WqvgmRncbKB+8f5D7I9z+R66s/DfDNZUyQ1dazQKj88MERIIb1J6lvc7/LQp01VS/f5llvssPwJCoEuN2qDHQIeQbNUOMBPZQf59flq58P2Cntqc0IaSoY+aVupPt6aPyWaqpJImqITTpUeYZUAAnOx9D8/wC+LhYeF2kpuf4RseZhv+WhL9YgHEIq0xLSt0VukBScxkxZ/eIvVP4gO49u3y6X7h61Uk1GJDysrDK8hzkarPF/E9u4Ph8CKBqu4SbJGASc+/8AYfpqnWHjmulb6pVyx0FTK5eAxH93zfdbHQHPUbZ9+qtvNvGQIamypgGlu+ke/VNnU0NvVEODlj8Kj/7o+3T1z2zCDiavpZ5Jp5JK2mkH79J3J8Rf4d8DGdsYHYZ17xNc7hWXKaOuRmqU3ljc4SP+Ik7Y756HsD117YuHq26zq0YkbO/ilD+aKen+dvwGi6qKqU3WdmYWW2WPhOp1caNpoUraCWWot8pHKxGJUY78kmdlI9T7YGdtWHhLgqasWOepXwKX4l8p391U7k/xt+A0cs/By2mBqiklxUEAspPMj9/Pndj76tdprWrgIyohlUfvVbqPceo99B26pmG1eoQmnGcmKhoqO1U4p6SDDNvgHLOfUn+p00tp8KpapoikRkOZIGP7tm/offVopqGEQYXdu5PfQW+XCktEUk1VIqqvUk7D5/2GT6DQfI5hexQvMKW2vp0hKzkQOp5XRzgqf99++qvx1xVR0EUkNFIstUV2VT8PuT0Ufr8uuqPfePppqznWlQ0aLgmXyu6+wB8o9M5J9tVq+P4tCtfQTtJbujuc+JC33HB6fM+u3UZKp0rORu4EHt1YVSFka83KprajxauoaplByiA4jiz3AP8A9sdz76h0t5rLdK4jVa6CQj6zSOf3ZHqCfhb0Jxn00MrKxYUAlYxKTlUH+Ix9d+nzO+nrXaK664M6/VKPOQgG7f1J9zpv5FYXaoisWOzbjJNdSfXqc3Hhr/jYGfEiOw8SkP8AEvcfxb/1MyxcMIkwq7g31mc74J2H99FbfaYKJkaiDU06/DPH8XyYfaX1B/Ag76P2qFp6lYaqDwJsZwgPhyD7yH+YO4/InLzjVw83FYYcRmnpWdQI0O23TRKmtEEkHh1cQkUnOOhU+qnqG9xq7WXh2OSiJ+HOME6dqaWgsqmpqWGU3GRnp6D/AH+GhbtUHGISmlZeZ1wfT1lHSANM08C9FkGJQP5H/e2id9u1DRW16uWeMKNgSe/pjufbWScUfSNV1M7wWVAkS/FIThR8znf5Db/NqstxrXRs8NaGutO/+NGSFZB95Tty49yPw0KunsYZA4m/4lFG2SOPeJa2vnkJnkgp9xgN52X022UH07++qJPVk+aD/hYeuw+L5Dqfmdh7aOXakWopWu9nnN0oc78uDJAfR09vvHb1G4zU6p4BUAMvjVLHAijPlJ7ZPc+w1uNOqLuEBe1nYiOyVCyRmaCSSgnjOVrFbbIyd8bkk46fkdPtcaa9lor7HLQVwjHh3qOn/dsOgMoHQHbzbfMdNK28NV13fxLkxp4/swgYzj27f721eLZCKCiS3LHinQ+VcZK56/ge46HQTanBwBkTVU29yqWLhGWzVa1VSy1Ex8yOpyjD1U99XSmt/wBcUMkGO55RjTdutVZSzH9lpEKcnLUEhIhf1MZOfDP8Pw+41qfBFqoqiKOeejnpZGG0ci4Ge+hmrDn0mbKpeUKzcLVlXUcyIeRGwJmyuPkeufbRjiH6DrDdqES0Uoo6x1zIRGPClPryj4T7j8QdafVUaQoORRjp0xoFduJqOwUszzTIREvM6s3Ksfu7HZfYdT9kHVVJoPqhC0LjmYDerZeOFJ2sfEtKa6i5cRO5HME/gc7MNvhfbp5l7wLZRGFjceDLsn1qEgmISGPGRnl826n/ADZQ7nm6Ayvpc+lduJOa12uFJIubH1mWPyxnfeJDvn+Nt/QLrHJ6cWyoFdHVTrVI+0sTlXz683b3G50cn9X6hxBXK1nAMuV5424mv1bNbb+JaCnTy1sLkxyy4H/MYjOfQY5R2XVIvlFR0j89ud5omB5fFUCQAbnKjOPmdvbVloeL6O/xR2zi6kdZE8tNdaSPLx/51G/L64BHsD5gNvlluPDkKXLxI6+glbMFfTNzQuPTI3B7crbe51qunFXKiYvY7tnMrljul1ss0xp5AaWQ4nppQHglz2ZTsT7jf0OnnpbRf5RLZpBZrqcYoKmQGCQ/+lKdl/yv+eo9cjVR5gRGFXI32I9cdF/DbQWtqaWmBjjHjSEY/hH99ELZjg8y9YLcieXmnuFnuHhzUs9troQAwZSh6/r/ACO2rPbeNKS60qW/i6g/aEKjlSrTyzxD2brj2OR8tCLHxPUtTC1X2jF5taKeVJWxJTj/ANOXqvyOR7aIPZoaq3PU8D1S1qoC09K45K6JT2KZ86j1TI9cauhKjKH9JZl/+X95zeeAS9M1w4brP2xQAc7LGP8AiIV/iTuPcZHvqvWie4QiWGkNSkkQMiFAQw5d26dMdQfb313aLldLRWioo6uSmmRs43AB/DcavVs4ps16kZbzG1pucsbRfX6YcolDDBEijAcfkdu+tQFbleDMGcrx3B9t4worxRrDxfQGvdML+0IMLVxqejZ6SDtvv030W4pobpeLRTV9qlo+IYaJAPrVPCI6xYwMBJk+IgDYEZGNVa+cNXGwSNXSQQ11smJRaulbmjKk9CfsN7MAdQrTcZrNc4Z6KvmiOQFZHwEPY5HY/wBfbVQ4HFglmp3coYPrAyzMqAEDpvg/j7/20tXtuKbBcgJ+I+GqSqrRsZud6dn/AM3IpDH320taeWPZpjvHus38DPfHtpBSOg10BjS3I2308EpOSB+OkMncb6WN/NronlGN9TM5OQm5Y68JJOFG3r213ykjLHbsNLc7ADGuS3tPORVGSdz+uuSHYbYC++vTgHbzt6aXKTnxSB7DpqGdE4U5P7sZP3jrrGB5jlvTXRPl28o1yCADjbPf11SdxEdx5h07a4zkkD89d4BHcD9deEeXO2NVzJOcDJP55Gl6gZ16oPfp699LGTsBqdSRvkwc7E9fbXGD31KCAA51w4HTv2Gp1JGUXpnYa5kwVK4yPl105g5PvrnHXB37+g10YklJ4l4UyXrLZHud3gHQ+6/2/L01UOUCRmK4cHG431sTY7ficddV3ibh2Kv5qimCxVWNz2f5/l10w0us8v0v1EfiPhfmjfVwf5lAU767HXXs8MtPO8M0bJIhwykdNcjT5HDjInknQoxDDmdjfXuuV2GNdavMjPVHrroDGkCNIakqTEf006ki9D26NprB16DjWb1CwYM20+oehtyGSQOXDYxr0DlYN2OmYphGOVxzIf008o98q24OkuooNTfaet0WuTUjjv4nQU76Yq6RKmMg7PjY41ITYlW310Bg7aHUkHIjP7Sl3K3y00rsibY3XqCPbUKGZocvEcrncemr7UQJUJyOMj17jVXvFqkppC8fc9R0bTCi/dw0X3acqdyxlLgAUYpmMjzMD8B9/bRROVlBXBBGQR31XIuZAzRghvtoe/y/tqVQVD0454wXg+3GOqe49vbW1lYPUrXdnhoZMYZSrqrA9QwznVcvtiOWmpIg6H40J3H99WWCRJohJE4ZSNiNdEA7EZ0G6hgVcZEOrfByJS7NdprfOI53bkXyrIcnkGfhb1XODnqOoII1c6SdKhOenG4xzxZB6nYqRsc9iNj7N5SAvtlEitPTJ5t+ZQOugtpr57bIEYuYVJxtlos9cA/Ep7qeukF2mt0L+bUfTGgsr1Y2WdzQEYMoZTkHvr0aiUFXFWx+NE6CRl5mAbyuPvAn9Sdx9rbz6lAgjuDnBBGCD6Edjp5otamoXI7iTV6NtOeep6uO+vRsfY65JAI2217tphAczonbbXm2MZzrzSHXbXZ2IjHXXDYDHtnXfNvnXhBzn9NSZMcRtsFSOuuCCdOMqgHHXXOCBvrqziyNIgO2PbQuqpCvMVHzGjLZ67HTLJnO/TWyNiVIyZU7hRR1MRVxv2Pvp/hXiKtstfFFUzvG8bZgqA24PQAk7Z+ex6H1BKtpjkso2PUaD19JHURFJACO3toLxDw1dWu9OHHvGGh15oO1uVM2qf6TY4+GDPHQyVF13UQoCI2wpJkL58i7bjqMEbHcU3wq65yJIsclZX1fL4sxTlZgdxFGi58OIY+ZxzHbYUOy3WW1ziiriGpifJIeg9Afbpv+B7Ebr9Gl7s1xlqpbrWfUpypklaFQJqnA2SI4CQooAz36Y2BI8rZqLFcrqPqEefhwUzT0Yzw1YI7CVcUwr71I+HjhUmKmbBIUv3YDrg+u43yTv0tssljqL5xBcGaXaOIxgEhvuRjoSN+gwD0xysdecccc0FttMH1WkipKJVMNBQ0wPi1TZ82D1xnBZyMnbG+qfwnw5deLr+LrxDNywUw5mVP8GjTtGg6c5xj8M9ASB3ck5lUrVRz1HeF+HLr9IFctVd5UtVkpW5ooJSTHFsTzOOskh64998ZAOlW2zW+mZLfbqeFooB4s09WP3eSDyyyqPjc/ZiGQB1zvpvh76pWVE9KssdHQU8ZNMqwly7FgFjVc5Y58xJxzEb4B0Tprva6B5aeCjNwmQE5eT90jEgF3YbyMTjOOpwq822h9wJyJD1zBdShpJGYzVMqSklpiwjmqiMllTfEaAfFIT5V2BGeXUC4VVTX1CwRIjyRJyF+QiCij7qinpnYYPmb7WBkP3W1FRc6mWVJXCMf39Vy4Hl35UA2GOwBwuM5JwRmnGHF1Tc524b4P/dU0ZInq1J5d+pDep9epztgdSFXbye5RULcDr5k3jTjX9kSPYuHkWpuj5E0znm5D3Zz3Yfd6Dv3BplHYhMJa6vrZqmrlJeWVm+I9TvufXRi1cO09DCAjM7Nu8jbM59fYe2rTceFbnZLA17uNMlPSiJnBnlVOY9kwTnmONlGTolK+dzzruANqSktR3GrvDw2SNKb6oD4skZ8NYwRykls4UY2ySBv6nRGCaClxbbKzySsPDqa4AhpfVIx1CHPzbuANDLL+2bksVvBeSPmMi00YwHdif3j+p3+Ju2wzqw2xo7bWG12GnW5XqYGN6kpzwwDHmCAZ5yO/UdznsZswuTAGsJOFkxaehsMEdTc42qaqcB6a3ocu+2zvjovfHf33ZfUgqZ6pay8oKqskXmp7fGwVIo+oLZ8qrvkknG+fNksGGaOheaRKn65XO/JU3KUCVVcnJSIZ/eyfIlF6knZhHeokcSh3akpA3PUPK/M8hH2pG7nO+Og7DPXEsK19Mh9bYMs9nhiqqrLiKZqcGV5mT/haOPOWKofjb+Jup7Hrqm/Sh9Ic93uAoLQ0s5QeHExbm5Qep2+0e7fgNhoVxRxjU3WkbhrhpHht3OGqp22aoYbDm9FHZPxPpp3hKwQUsxDoz1HKXbn2I9SxPwgdyemgvMZuF94aalqGXjXCfCaxYrrqTLUM2wxk9egHqT/vOrPVqBBmJljA2DYyF9lH2m9+gwCfVZJKJhZEZ2byxxxqQ0vbCjqqds4yemOqmJUVa08/OjrJVqOUOq/u4B91BnBb36Drn7WiKKNo47gup1WRlpGuIgtlulmrY2MuC6UnMeYsejzN1B36devw9TRpp5aufnkkB8oRQq4VV9FHYDtqwXmGpuCRwoSFlfd+pJHp945I9tV6AAVUqx5Mak8ue/Yf30RqKGRQTOeHahbMmdR1XJdlamVWkYCJSwyASMEgd9aRwfRKyQ1NaStIlQvMD2TmAP6Z1SOBqKm8ZrtXlXSnmBWHvJjGSNxsMjOPXtq4re4ZIzRQjw6VFVY1HUnPxMe/9M9OuuaJwHxMPGlLVddR6/yrFQNT2teVfDDzlduY46j8dVwcNQfs5rpcDyqxx4Y6kE7t7nHQeuNWmsphRWvxJkz4m2T33ycflqvoKytpnjiDSEsFCLvvv276vqURW9PPEy8K1Fr1/wBT5gzhHiVLHc2oXmkltsrcoJOGX03PcdieuMHHVbnX03LRM1PNHUx1EnPHKnRh79wfUHofz1VKzh6mgpTW1EBeI/4ijYtsTgH32/PUDhTiIW6Y22tdpaGQjkLNuPTPv2z3G3ppS9Z0xDDkH9o+G3UKfY/zNLpXp4xBQxDnlMfnkU4CfL1Oce3z7T7Pw1WV0gNQxWBdjKwPmHt/bROphsNz4kS4WGEU9unjjEcYJJRsDxMjcjG4+ZGNtOcV8RlIkt1vUCM4jMnsdth/sfPTBkOoCbO8Tz41B0tj+acDMrdXWWyimE8USyyxqVRSPdtz+HL/AK9NVO6Ge4vLVVLZlYFVHXGdv9/00XttBNXVUgUlQp87nbA36f7/AC17fnttqq4aRH5U5FLu2dzzZ6DJHwjseusa1dMlu4x3pYo28gxcLcNQUNMldcCrP1CdVXfbbufQDVe4pvAqrxKiAsCTyj02GDn5DTt9v9ZdVMETNDS4wBjBYemAdh7A/M9gNpKYR3Yqw8pTY46kbf30fSrWAZi68pWhIEDyxs0NUzADljbLHqT/ALH++mn6e6TWW8z1ERJpHkAmRScjYeYe/sNdcSMKWGojGMlipHbqc6KcPWNLxX1gqJCsUcoIx13Ubax1lSNaE+3cP0dzijef7S0UzwVjw3CiZHR4gWCjbbuP6jXlYoRac4zyyj8N9VSnq5+FOIp4MMaASZKZ3j3+Ie2rrOIKqj+t0zI0OVc8vQZPUe38jodLCua37l7ahjenUEXSOaeoE3OVliPLht84PbHT/f4mYLpPQlcELzyLOgxkNjJH4jPpoTdytK4dGzHI3Oe/KTjP89Nz07VVBDNAzPIqICvZgCV2GsXGQRMF4ORJPE1umqnimiRfDaMKcDp5c5Pp6566DtJUWC9SXOnRzG2DVUxyPGBwDjrht/kcHvsbZT1zUjKsr7tFy+E2+6jlP/2QyP550zfqF77QmpgUfu8KQFGGwAN8Z3PoT3Oh7fcGF0PzPayqo7nZoa23oCEVQjgDBUL398Df3z6jTMTo0VOJ2JULzc2M7ZIYe+38tVSgqZuGzFOVeS3VP/mIhvyNuOcf1Hz1a5olqKGOeg/eRBTyMm4ZDnG/566jA+k9yl1WPUvUF3dJCwUlTJBujjbmUnOc+mTn8TqJX0ZkWKeBjHJ8cbjqjdxj0/oRqw0cMFTRwCZhGEJDOR0X7Q99j+mnm4Tu8Vmavlp1+qrMISwcbtnAP+UnbJ+8Ndd1xtMpU5U5EBcO26pvtaLfRwH62wxNGp2QEfGP4dwQe2Mddatwxw7a6Dh1KVpY4lq4x41RKQuGI6bnAwTjcgDG50L4hsFppbXQXyy18NquNNT+LSvJL5pgRzYZerZJKsoyRnOMDeqcRcTS8VfVHpITSQEFZaVGzyTHzN/2kklR6d++l+57yFzgQsqF9aiP8aVddfC1NUOHjyVKwtlHIPUeu+4/PT/0f2ioqeI6W1XqUUlRPH4sTyLtWRg4JXsXGNx0PXfONW36JLFRT295bjSST1SOGijK5R4z0PTBGQw641cuN7TYqzh9qu6V0dPWU4JovBIMqyDdTEdssDy57YJB66YDWeUAKeDMhpRdnzeoetdliS1yLbYhBSwqWkkGMtjqcnr8z+GsfreOlsnHFReLdSs9DK4iuUEf/PC7CZR/1F6Z+2NjjbE66fS1UXS1zxLSinenp0StgilwJh0MgOOnfHbcHpqqU1k/a1QJ4X5kfDCJhhyPcd/mNtH+H6Xzla608wPVas6d1qqHE+hLbW0lxt8FfQ1EdTS1CCSGWM5V1PQj/e2pGs7+jq13nh5KianjM/DhJkq15h/wUnUyqD1Q/aUdPiHUjWiAgqGUggjIIOQR664rqSQD1GS5KhotLXuD6aQHrq87Fg6WN8a60sDOdczJOcHXoA17pY1MzoiG2lpaWqzuItLS0tSTEWlpaWpOxaWvcaWpJPNLXu50sH01JJ5rxlV0ZHUMrAggjII9DrsD117yjUnJktxtrcJXtbVMxNlqz/8ARMrfDA3elY+3VPVfL1Td8+XKH4fQjOtD4hs9DfbPU2u4R88FQnKcbMp7Mp7MDgg9iNZrTLW01ZUWS7+H+0qPBLIvKtTCSQk6j0OMEfZYMOmCWui1AYeW8C1Fe07lgg0b2q5AwJK9NK3MOXGITjpufQHYZJ9NtzayGRFliZfEAypG4I/qDrsgSKUbOOmB1PcfkdDkAt0yQ5cxSOQhwMISdht0B6ein2ZdWceU209GZj1jI7EDVdmjtNz/AG5bYV8JpP3sTjm8Fj1H+Q9j2/LW6cAW+irLLDc6RW8RhiRn+NG7qPQe/f21nCMVYyKgcMpWRG6OO4OrTwxxvRcI2vkro5WoZpOWEomW5vuYHfbb10r8VRjUAsJ0IUWEseJoFYtIKNoq0KYumGyc4HQdye+qlB9IC0tLURWySOvjpHZZCzZdEB2ORkOB0yD6Z76zn6QeNqi+1jwxPLDSsSFp0bLyL/GR0HfAwB9o5GqlSV1TSVSVNNIq1EC5UKcRxr/Ge4/T0BO+lWm8MdkLPwITbr0R8J3LRxXxC12r5awsoVxtM3UrvsPbf5fPpoPHTS1LmJY5MSL/AIa7ySD1bOyr7t+A0Ws1qp+JqpKuytGjs+J4Sd4H9YwRjlO5DHp2HUDVOFeEaC0xh3VZpyeYs24z6kn4j7nW1upTTrsQSlena5t7GVeyWGqmt9LLxFT+JBAw8KoUksinoGB3cDsx6Zz650Whp6OlpxFRxhgQCoU5Le5OnQHMnL4YMf2i3f5DXFLT/s5meEFqU7lO8fuPUe3bSd7C55jRE2TuspqhKYTmLxuUgmMNgAb7++hqVdMQTJIKVlbKOwwY29j0IPpq5xT07U2TInLy9c7ayH6RK5Hmljp6kwU/RuXZmHz+yP1Ou1IH9I7kuOwbsy31HGQpbbNJHGlRNA3JOsTjCHfzHfKjb57+m+st4s4kqLlWs8kglI3QDZEB/l+O59NV+O4z2mrFVRSLTFDgRkf4g9GHofxPy17dPAuFtkuVphlVYBzVltT/ABYCftL/AAH16j5Z5WNOjWpsvzF9upa1cLINTUkuSGDuoyWOyp7+36t8tRrNXXCG6eLZU8eVsCfnH7qVfukem/U776dtVirbmFlrc09KN0hXY49T/vOrta7ZFSwiGliCqOwHXRzgMOYJUpBzBdBw9apquSvpqZlqB55aOU8xh91P2l64Pbp2wLJa7fJM6+EuV9QOmpFBZZqmRW86SqcxunxIfUe3qOh/LV14eoPqLJLcI49zgunw83uO2gX1JrBSGJTvOYIouGajxQWTyjcsRsNWS30NNSRfCshHx842I1YaySnSjeV2RVVc5zjA1jXH3E9VUyPR22YR042ZxnB/D7X+9u+gc2XtgQvalAyZoa8U2ignFOldDytsqO2MH2Pce+s/+kviGapqGgrFNPCRkR5xzfNu4+Ws9epaMuI2Mkp/xJZG/m3b5DJ17ScRBFS1XoTV9CfgmRf31GfUdfL+vtopNE1Z3NyIK2s8wbRxI9fU5Q82YIh0UbNv/wDa/M5OhUs+IuYuKamJyDjdv8q9T8zqff7fU0XgTUqi6U9SSaWqjGYs9gRv5+vX02zqTZOFJZpfrl5kMkh3EYOQPn/YaaI4K+mAits+qBuHYrybp9bsA+pAEc0ki8wl9n9R7audst1s/aBaS2wW+6S5bkU5hqPVoWO3zXYjuB3MQUqRRhI0CqBgADA1MitEdZD4FXCJISwYoSRuOhBG4YdiNxoS1dvqUwus54MjU9teWTCxkMNicdPY6M0vDtT46q0TOCM9NHODLRURTEeJ9bhQeV5CBJj7p7N8x6dPXQBHBJT4RVAA6enz0mv2u2QMQ2mgkcylWvh6nhTmmw5HROw+frov+1qa1oiVsojjc8qBlOCfQEd/bQfi/ie28PUzzyzxht8E7gkdQoG7n2G3qRrCeNON7rxNI8NMGhp1YnLEeIR0Psq+w/EnroWpGLcTVmWoTY+IvpHoKesktv7Sgjc7AO+NznAZlzyHp1OfkemCfSZcb7UXUR3uVYYEPNBFHvCc91HcnuTv6nUKO50EdMKGtVJF5tp0TLJnqBgjmz6Hb01HFxutqpViudLFeOH6gY8N5ADFnsjfYb+Hoe3ro6ugHlu4G2pL8CVqpqklJipkEcmcZyACMb752+Q/PUL6v4aEV6nb4UOM477dvmfwzo/dLNTTW57zwhMblSJ/ixkf8TS+zJ/91v7euglrrlWJ1u8aVFC2SyO5UhvvqRuWHvkeo0RgrMCCeBBtUCxeGiw0WPNyg+b333Yf7xrq1Xmo4ahnQzpJS1JxPb5l8SKb/Mv2T7jDDQ27XuJJnjtiOMkhXI82PQY6fh+Z0KhoJanNTXSiCI75bq3yHf8AQe+uG0j6YRXQfqeWytt1BxXSpPwtUGjqj8donmHmPcQyHZv8rYb0zqoVVHDRSvDXJLHMjEGAoVcH0bPT/fTU3EixSRWyExxEYaUjc/j2+Q/XRamvq11MlHxdRy3OnjXkjuMQAq6cdtz/AIi/wt+B1dSLPsZ0sF9+JUap5miAK+HFnZF2H46i0809LUJUUkzwTxMGSSNirA+oI1dq/h56WiNyoaiO52onH1uAf4ee0q9Yz7Hb0J0Aq7TFMhkpiI3+79k/j2101spzK+eDwYYg4ptV+Vafi6kZanHKLtSIBMP/AMIgwJB7jDfPTF54arrdRftCmlhutoc+SrpSXjPoGHVG9jg6rEsLQOYpYmU+h/pojw5d7rYqlqm21TQl9pIz5klX7rqdmHz1otmeHE4aweVhHh7iG42uRo6SscRyDlMDtzK4+6cggg9MHpovAvCXEk7KFThy6EZVZAWopT/OI/mPlppH4X4nJU+Dw3d36ZJNFO3pnrEfnke40F4itNys1bHDcYGgm+JGxlJB95SNmBHp76s3AyOROIMnHUkcS2C+UFRHHX0lRzlfK8Q8SKQZ+NGXIIO3TS09aOJuJLPAaaz3mohpG8yqk2F/AHppaoDV8mTD/E+pQPXXoAHfXu56a8AAOWOT216KCgZnJUuc7gep769wqjlUcx+eusdSxwNIAsPL5R+upII30OGOT2A17yltjsPQa7CKoOuWbHTOpmWnmAi4UaaJJYgDmP6a9OceY7HsO+vQARjAAHbVSZJ4Ov3j+g16M5Pc+uOuugCO+BrknIIXYfqdU953M8B3wTk+g316AMZJBPb01yFwNgP6DTiJkk4/E/01yWHMSLncnGfzOuuXAPbGvdsba55jjUkxOWJA203y42GST+encHBI29TpBcD299ScIjfJ7/66bkUjAzgDsNSCM9sf11xynuNScxGMbdMfjrh0znqDp8gk7H2+evOTAxtn/fXXQZyBL5Zaa5w4kHLMB5JQNx/caz+6W2qt1UYKpOU/ZYfCw9QdayV3Pr66h3Ogpq6naCqQMp3HYqfUH10VptW1B+0W67wxNUMjhplGMa70Sv1jqLTKWb95TMfJKB+h9D/PQoHGvQ0XLaNymeN1GmsoYq4nYONdDfvrnSBxreCkRwnbGljbOuQc69/HUlItdwyMhI3KnqNcaQGTtqrKGGDNKrGqYMpwZNjw65Bzv+Xz171yN8jXNup5JZf3eQB8RPT5anVVK0TB13Q/p89JNTR5bcdT1/h3iI1K4fg/zIqE40niSSJkdeZT29NdcvprpTyjBONCZ+I3wDKzfLMyHxozt2b+h/voGA4kwoMcw7ZwG1ohCspBAII0BvllV4zLAMAenVf9NHafVf6WgN2l/wBSwBRzyRytLTjDdZIicBvceh0dpaiKpgEkZz2IPUH0Oq5JG8cpjlPJID5X7HRK3V3K3gTYV/U99E2oGGRMqbcHBhQgntoNe7MtUGmhjCzdfLtk6OpgrzZ6665ffQmRzmHKZnNJVVNrqfIrhA3M0YOGVh9pPRhq62i4QXGFGWRPFIwjKMCT+HA6Efd/9uR5VYvllSvQyIAlQBs2Nm/11T0+s22qkAUhicSxMMB8fyb30i1WifTt5+n6+P8APaMab0tXy7poakEsCOUjGRn8vYg9iNjrvsdDLJeKe506rLMVlzhZG2YMfsv2yfU7N1yGyXJHmWQxyLyuBnGDv1GRn3GPUHY4Ixpt4f4kmpG08NFGs0DUHcvKz3G3TOlv179tJScnfXi46Z01i8zzBznI16CPUAa8zvjXI6e2piVInRz6Ajsca5YHGRg67U7Y1zld8DGoJUDEZwcnoNcFfKc53084B+euW2GNaCVIkaRM7EaH1dLliyLj+ui2N85GfTGmZU/D21ojYnNsrNXSpLGVdfz1BtlfVWaYQzszU+f3bjqmOn4fy9xkas9XS5BdMA9/fQiqp1kVkdcjG+dB+IeHprUyOG+Yfode2mbB5E0r6KLRZ+J+Iqma63pY654f+Had92HaKM9FAzkgbkfDnWptHbqekW1QH6rZaZh9YqHHnqJsdgN2OBsBsO+wJPyjRVdTY6kAu7UvNlXGcxnPXbt/8j32Phji6K+fVxfbmUjp4QsLBdpB3GRsGPXmIOcHqQFPh76bKrDXZxPRHZYnmVczULjXW36otNaGMcDriWoaMKy7bxRjO7Y6sTgDqQDvWK56f6l48jCitMJ52y2DNgEEliPhwcFsDOSFAzvEvV2oqGkNbdJIqSiiXEULHdgDkcw64zvy9yckk7nPjUXr6Tr8lAsjW6yJmZ2fICxL8Ur47AbAepAG5ybrWEGAOZgi+YcngR/iG7XzjGnaK0xyUHDcbmF6rl5BLy7lEHoNsgbDbmOSAJPCXDjsGhoIFSlgXnkmkPKsWdsu57/Lc74B1cb5RLHSUsUkT2yw08KxUFMQBLOqjqi92JJZmOFG2T6xrOZq8rMI1paCjJ8NW5mhgPr6ySt69T7KNiN61DHbTjeo49oRtQioIzFZ7e9XXkZ+vTpjwx96NDsmPvvvvnbpqi8YxQ3mq/ZgrSIqP9/X18rt4SM2QEGd2Y+p3J6D1vFTV037Thtc85XxSSYebzMwGR4pBG+2RGuygHJycmm3aj/Zd8D3GCa93eqJngHL4dIijbIAO+Bt9gLjckdaUuj25Y9TtiEV+mKio4KaxslOz2y0vnxauUf8RXN91VyDy9sZHXzFc8pJQvO1OLbbbdNBFMgVaKDLVFUOv7xlHkjPXlAGfTHnEClRquoFxuFcskyeVJ1jDIgG3JBHsDj75wox5cnBJF+OqDhG1yyRxJDIyEwwgh5qiQ/C0rnfkB3wBgkYAPXW91+WwTxBqKe8dyvXHms9ZPWXqWFJadRGI0wVjJ/5aAbbdTj8Sc6pNRWXLimrWGEPFQh9uXqx/qff/wCdSbbbrjxXdFqbpJL4DsSsf2pCT/XWs2ey0NiplYwRmpGEjiA5uQ+h+838PQbFj20Lff5rbUHE2SlaBuPLQHw3wtSWS3JU1USiQqDHFuT/AJiP9k9tSUE1XUM0dORI5DeG2FOB0eQ9sA5C5wOpI6l2tq56mskMUiM/WaoY5SEdNj9pjjGR8gNsCBJXhMU1ErYZvMSMtI3q3vvsvQd9zk7U0sFO3uCXahd3qM4uUy0qSxxSvNPKMSzAEFh0wO6r2zjJ6YA8uoVntauz1NS4jpvibm2GO2ce+Nup99HK6mo7fbhW3GXlnlPkjXd2PfHvjO/QaDVdVNJH4s8f1eFF546aNsELj4iT8Ax1c7ntgYOmNDChMt3F2ooOpsABwIJ4xuTSNNHTKsVNEng8z9XbGeTbvv8ACP8AuIGxqn1j6pSNLHjnY8iH026/z07cnnqBHVTuiCQ/uouXBWPqCq/ZXPc+ZjvqFcIv3USMcDI6n1zoO+1rMkmPNNUtKBVEsXAtvmnpK2udTyYSMHB33JwP0/LVjq4FoUjjhRXxjmyMhSCD/MDXfD0xjscNPTnEUvnGO/UA/l399WCyUFHPUxtcTyQQLzuN9z2HvoTzjWDtkesWH1QFJNXV0AiqSclh5yN8YJwB6bN8umrb9G9HHFxRa6WeMB2qY3X2Izj+h0G4ru5Wqf6kiwxAfumAGUOMZH4A/LJ+ejf0KTU3/jSkqLqxSONZGQt8Ic9GY+388Z1pZezUttEFrqFbgSw/TdwXNWXOStsMJIEBqKqnXoqh8M6L8yCQPnrErvZKWmpGqpYfFQjzoDjn76+w6qRVvtUFGXSgXH/8ZdfOP0rUsLcVXL9mBvqvjhAhx5Wx5woG2ObJHz0LodQeVIzxDbUGQcyj8CcU1FpnWgrZS9NKQoOfi3Gx/T5/z16Gkoq+mS5mojNKqtKxzuiqMsT+G3uSNZ3ceFqC38LtX1aJJNVpurHHIDvzAevv76AcMcRSQK1mrZ5VppyORw2TtuucdT/P54yQtjaU+nkH9plqNHVrhk/UP3l3vl/jpllioYgrZzjuD7nt12HU/rqpvBVXW4wKIzJLIDgKvcnfp/v30do7BPXlkjIWHILzdQR1znv/ALzotw+KG0VH1+QiOKKAuGcgYVjhMn1IUtgZODsDolrCayx5JgSVCtggGAI5BwfHQWiprq5x4iQOypkAAhTgE/PoNUuScVFZmnyViiCpkY6Af15j+Oi/EnEtXfJmRByUMTcyR8uM46Z/3n5agcI2SuuE5FPA2MHLbD5knt/PWm5goJOJzCMdoGZXL+sskUhy0j+IQQeuSD/vGrLw9XGgFeFXMpnA6ZI8o/3/AH05xxZ4LFTKjyh5pBJIT0GR8IH451zw9QyXCarMURZ3mDAdc5QH8dRCrXqSeCJzVb10rbewY1UwfXqiOWfHM5ZOYnOc7j599QrDdpeHaoUtQx+oygqQd/CPQ/8Ab/fB23FuvfD1TaLTFWz55nlGV64x30Fu1BFVMkpVSFcEg9GVhuD+Z1pq9OHryp/Iynh+rO7a36iH7hRx1NuhljYGMKM43A7Hf0wBjv2O+oswFDBGiPzCMkc/ZcYPp7nVZ4fu81mrDaauQmlZzHEZMnkbOCjD0/puO2rUtIrRO0LnwvEGx35eZSCpP5EHuNKVtLEq3cYW0bDvXqQpqeapo/rKLJIYWYSYOTjZgf10WtNZLT0EZjmXxWlZQGA82wON9u3Q7H540OtUj09BMyPyESIckdMhhv7dNSniWspJY1RYymHCDO/mPX/3a45yOfiYqNpyOp7c4YrvSyU1LEIp6ZneMb4Ksd1375PQ9vz1XuF7nVcKyHxcG2zyGJgQT9XOQc/5D+n5asNhpKpY5pHZlHhMqOT+OM/h+unbjBTXC2vRpGFqZVd+YKCJGAzynfJyA3T73fuIYVXZjg9SZcFpHtJS3FlljmMi4PxRsBgAjrgk/MHUuLjGei4Zls0MAeOp5kckZCDAzgdc53HTGBvqi8JXH9mSU9HdHeOglkaKCaTcwNtlG78u+Qf9m7WKz01fdY6epbw0klBYhebfBJwO+2fXfGuhlZfV7TKyoo2V6MG2q3119vX1emDyTSEuADnfOTgk4ABOeo2I31Zh9G1fbZqmut5iku9J4c8dGwzDWRHrGTtvkEA4GD3IORbr/wAPW3hC/wBou1OxjpgrLKHfJcpu3/ujyNuhUY0zxD9JNqCz0Nht/wBfmOUjq5+ZRIvUqRsTnAGTjfsO4tjPdxX0ZvVivO48wdxDxZFXWCmvFoqmo5HY0lRSunLJC4HmjYH7SsoHTYNnWf1E9xuNQOeWaeQdHdyeXf3999C1/bEtbPc4o56wTsr1MS9ZcdGA+8Ox/DW+/RzZ+HbhbKS8Wfklhn8yTVGOZD3XkHRgdjnRujur0yFG5MpqNO17BlPEyKbhWqq66pqKVvq1bH+8XxBhQTsyMv3Seo/i1cuB6uxfsKQ3pDQyUMgjrKeQfvYZOvl9mG6sOo6Z1dvpEWy8LmqulPMtfXTwgeGpBEbf9RmB26dOpx266+e+KLpX1dwa6yTeNUEeFJG2wnjzkJgdMHJB7H56NossuO5OB7zC5EqGx+W9pol847nt6VVLw9StT2yYgyQuwLSbEHmfO3bbfpvnTn0RccikrF4cujMtumk5bVUSNtFzbrAxPbsp9fL6aoFicVyoGfmpif3OTuSDgq3ow7j/AE1brVwY13RhOqw2weWaRgQACeijufTHfGnVuk0yVeapxFOk1uq841WCbsOpGlrPfoz4zp6m5T8I11wNXV0pIoayTANbCB0Y9DKo2bHxY5h31oQPr10tBJnoRiLS0tLUlsRaWvdIDUnZ5r3B9Ne8uutSScYPppYPprvS1JJwBvvr3lGutLUkngGNIjOvdLUkngGNe6WlqSRaWlpakkWh9zstsuVVBVVlJHJUU6usE2PPGHGGAPvgbHbbRDSXrrmccicIBGDM3vFBNb6toJOgOVYD4l7HUCrp1q4PDkJXJ2YdVOOo/wB99aVfLbHcaQocCVd429/T5HWf1EUlPM8cqEMhwV9D6ac0Wrqa9rdxfZX5TZHUA0tZNFKbZO7isjUEsUyHjz8Q33I/kB3yATaCEU0kEwaWlmH70A+YH7499NXmiFV9XqYkT61A5aJmHYjdfx9++uqOsjkd4ieVgAxTBGAe4z2Byp64ZSN+usgNp8t5YDjcJRuIqeSxVP1eZ2eGUc0EsfmepX1z0GMjOeh6DfOp3D9hq7qEmrR9Xozho4EOc+5Pc+531bqqhpq2mNDWgeAx5opPtQP6j2PfUr6PbbUw3oWasjLLzeQjcb9GU/dP+986yuOxCSepnWn9QAdGE+GrdJSsiUMfhIuMEDGMd9adw9MKpwlXgTIBlPsn+Ieum4uHmp9n5ET0XqdReIr3ZrHRCSedIXjbCEHcN6D7x9QM++BvrympvFzcCP8AT1Gocy31cEXgswCgjWc8W8YpbvEpKBfGmXqebCp/mbt8hv7jpobxNxvVVFpSpp5sW6YeG7JkSJJ91h1X2GMn+eZ3K5M5/eOUXm8qL8TfluD7DLeuNX02ia45bgSmo1q1j0y60HFctxDW2qqUgrh/5acArFzH/lt1xnt/Lsapf6ypirJxUgx1ER/fGXyrEcdQffrtkkHOcaql1uUMZ8GX4jslNGRzfjjp8hv76N0JHFNuht3ETfVqyE4oavmwHXtFL+ezf1JBaLpxScoOIvNxtXDHmBHr56uYxW1GlcbNUuMBf8o7fz0Qs1uqLdVpX0tTKlwXpLnOf4SO6n0/rorRWyWmmNCKYwyRnlaPl6f0/Hpvqz2m0RRDxJgHfqB2/wBdGOaq19XOYNUtjnjidWSRLqeZIBS1a/41N2/zJ6qfTtrRuFuG0kj55MqpHcfy1ndbSGCoSqiZomDbOo+A9M/L1Gr7wXxX5DR3DlWqjXIAOQ6+oHp+ukmqZwvp6jbTqm71SwTW6K3xEpyooGSx1U+KONaS0hqeDM1XIvKIFXJf/MPsj3O/oO+m+M+PIamk8O3Fo03DSsCGH+Uf17ayWrrPFZ/qwCqx88rblj/90fltrDTaR7jubqaajUrUML3LovFsl6iFuqZko605EMbSkwzj7hP3tv8Afak3yeeKpkirueBozytExww9iR/JeuhUrCZXSEc3/UmdsBf+7t8l/PRG2XSK9R/s26O8k0EZFNdhDzGL2k9U/iPTrtvlkta6ZvtF7Ob1g2rqwkIM7mCMfBGBiRvkPsj3O+vLbabheF5Vj+p0Oc+7/wB9WG2cG/s+p8W6N9ZqD5lbqjD1B7jVppKXnPIi/kNaNZuGc8Si1hT94FslsexwFLW+UI/fUs7Zin//ABG9CNvX7wPWpYLjk0okiZSBLBKMSRH0I7j39PUb6m0drYyHxBgD10ft1iSeeKdkaExnCzrgNj7vuPY/hjS+23y+UhlaF+xJFo4XlmpC/KCcj8dEIbEkDf8AEANj7A/ro5SVaW+NYqiQNEx8koH/ANsO2q1x9xrbbNGVEnNUOuUjjwZG9CAdlHu34A6DNztxD1qRBkwlXVtJbIRJI4TlXmCKQCAO/oB/EcAdzrOuIfpWpjXctBG1ZyZWR4m5Ux6BmHnPrsB8+us94nvdy4gkc1k/gUXPzGBHJUnsXbq7fPPsBquVFelODDSoWYfgR/Rf5/LR+m8LawZs/tAdR4kqcJLbxJGbzNPfaConuUfNmWFv8al67FfujGxGdvUao9bO1cpWmQoxbOVXCv8AIDcnrudvTGmoZK+gr0utFXvR1q7hoxkMvcFc+Ye529wcaMU90tHGZkpEMFl4ibOFcYpa4+xHRvbO5656gs6YV+hxx8iAm7zfUp5lVleniJ+ssHlBwSrZH/cRnPyH5jTLVVydJEiysMkZVl5RylD1wDsB76d4hoo7JUOl6LwVKdYjjmPpjG2D6jPqMjVRuN8qqwGjt0ZihJACr3P9T+Z0HqAtLYJzNaK2t5xgSXUXaCw1/wBftFRLBXKNjE+yDuG++M9jt89FJmsvHlGHleOxX7bMm60tQf4h/wAtj2PT+WqrHQU9IfFuLs0x6QqfMT7n7P6n5aYr5JatRC7LTR8uY402Ug7ZyO/vvrFbCxx7Q/C1jiSLnaajhyreirre4ruvNKvk+a9mHv09tDq+GolZZ/FFQ7DmIzlgPb1xqx8PcWVNtgSz8RUxu1pAwiOR41OPWNjsR/CdvlrriPhpJ6T9ucLz/tG1LvIY/wDFp2z0dPiX9R76t5QByOpXzGJ5Mq1nvE9sqlwQ0Z8pDDIIPUb9vY6ulvNBd2xAqU8zDYLsre2NUlhHUgio8jYyJFHX5+uiFDS3C206V3hmajZuXxEYEA9gSPhJ7Zxnt01k3HUyuqDj4h6aGps1wNfYalqGpwVlRRmN/VWU7FT6HSV7LepvDdYOG7weisT9RqT/AAt1iJ9D5flp56yOuoGlSVmkSMDEhwRg9W+8OoyNx6aEtGlSGgni3I+Bu/y1vVaSMHkQIbl4PMavNrqKOdqC70TwyLuofoR95WGxHuNtAqu2yxkvCTIg35T8QH9dWygudbb6IW+rp1vVmH/1SdvPD7xP1Q/Lb204LJBcYHruFamS4QxrzTUUg5aunHfKfbA+8v4ga02BvpmqsR9MooVTkcp5u/8Aro3Y+IrjRUwtdRDFdLU7eaiqQWVfeM/Eje66buCUbKZZ5BE4+0PiPzH98aDyVkjIUoIzHGfK0h6t8z/TWW8qcCFoNwlogtnDNYZHo+JqGzIGwaS6xOzof4XRSGHvsdumlqrQW0zAv+9lb7RUE/00tV8z5E02r8z7IAYg4zj1OkN/gXmPqdOAFsk9PTXmvTwDHxOEQA8xJY9s9tdMxB9NIgkba4fC9DltVLToETnI6jXA210BndiRrtV2OcoPXvqo7zO8RrlJOwyf99dekKNs5b07a9JI8qAAeuuSQDjqdQmQTwgk5J/HtrwDJIz19ep06qZ3PT/fTSOF2AOf11WdxPFUD4tsdu2k538uR/XXgySfT10unT8c6hnRPDnoc59Ne46Btz6DXS7DYY1789tSdnPKQSNiew7aTdc9/Xtr3AxttnvpKMDUknnL7765KsdtvfJ6675crk5A7DS2A82AfTXMzmJxy7bbD11wQTkDTnmY7nOveUdNsD9NSTAjHLvjvrkoBnvp5lxnGdc467b+muyYkeaCOeFopUDxsMMrDII1Q+JuF5qItVUQaWlO7L1aP+4/Ud9aGVB69O+uGAPQHGNsjW1F70tlYHqtJXqU2uJjWuhq68UcKiQtWWxeWTcvCMYb3HofbodUp1ZWKurKwOCCMEH0I16LTatbx954rXaCzStg8j5nuulPbTYIA310vm6aLi/E7G51Jo6Z5nwMBR1J1HUgDBOjFBNAwVVIVsfDrOxiq8TtaBmwYQpokSELHgcv2dSOoB5SdtxqPE5AydxqVEwODjY++lrc9xrWNo4g+toGVTLCMp3HpqEV23GrMoAwR31Er7WWzPTLgnqnr7j+2gXrxyI90msJwrwIF5Tr1evrr3fJUjBGvOQgD0Oso1BzBN4tKVSF4l82+VH8xqp1MEkL8kynAPlYdR/v01oir1buOmoVztcVYhYIok7g9D8/f30Xp9TsOG6gl2lDDIlVttc8TiGbdW+Fs7HRuJgyjzZ99V2spJaJ3R42aPODnqp/vp231rUzqGbmhbYN6fPRj1iwZWD1XFDtaWEDOfbQ+8WmGvgIchZAPI+P0PqNT6Z1lXmRgQdSOX8dBcqYcMETNKukrbVWlv8ADlxjJ3SRfRvUe+rPw9eaasi+r1TMhjA+I+aHbAye64AAbfHRsgAoYultgq4eSUEDqD3X/fpqj3e21Vuqg4YjlOYplHT+49tKtXocnzdPwfj/AIh2nvGPLt5EvE0bxOFfr9lh0fYHb8CDj0IIyCCeF2J3GPTQThm/JMn7Pr0wvZQM43J5o+5XJJ5RuCSV6sGPyx+AFywkhkAMco3DA5xuNt8HB6HB6EMAX4b4oLv6dvDRfr/DvL/qV8iNk9h17HXvt+mvC2DudeA+bpp6IkGRPVJPXXuvCca85vbUxNImz2ONcnca7YZPvjXJH467JjM55M9tcOvvnGnO2vCeoA1MznUYKZQ4330PqqYEkgYPy0TbPfUeQAnA27a1rOJk/HUr9VTKwZJFyD1B0KgmqrHUc8ZZ6QncdSnuPb2/rq1TwBj083robVQcwZWX5jsdY67w+rW14bv2MK0OvahuOoXpqyhvMrXG6zVNxaOACkgLDwufOCz9yAO3c9fTWoWS6Wy08OpbuHYxdOILgwmrqloT4UBHwooI8/L2GOXOSc7DXz+VqLVMZqcM9OzZeP09x6H/AGdax9FHHNLRUj0bQ0amoYeHWzKWFOB15kAJfG2AehO4OQdeJurs0reXZ7fvPTKUuTfXLrHaqhataviBqm53CoTmjpzLzTSqM+Z2O0cY/vjoSBPEXE8dHHyQvGajGI0pziKEH7n5bv3x5c/FoZxhxiJBUUtFI7RyNmonlIMk5H2pD6dMJnlG2ckazmSsr7zcTQWpZJ5pAWkcnovdmPZff8NLLdQ27anc3q04xufqS7tdp6mviFLMz1hdeQp1Vs7Bff8A3660SKonltFJHxg8aS/F9XpVDSSqdwGBPKQSAevJ0I58YGccI0rx1zGlrUiqpMqtQ8Qyq9+VifL06jf30PvN/qKm5SUlrkaeodiPGBzgeoPpt1/LRVGgNA8209wW/Vm8mmodTRePOM+H4LHTW20WwPfnnK8sZMjKCMAO323J6KAAMdthqrWjg241nECftlxPXAeLPCXBWD0Vj0LDv2HT1Ab4BtAtt6hrJohV1iecBjsG7fIDqTq80dTHT008kUsTvUNzTTsuVJye3cZ6L+J9NWWk8zptWtcL3H6mloKKWE0DSNPGnM8qsE51A6j7ifxHc9u5EaadqgM7SlYvgebl+LvyICc43+e+TjOWbkMSRePUsywuPECFv3k5+8x7D3/LJywgFqq5zFUj5Y08uAuwGdlA9d+nUk776Nopz6VEV3X7OWMfgirbgvhUCDkU5jjBwG9WJ+9t16dhjbBFYqayUokeMVNxbCqhBAUnoCOvyUDmP46dpbiLZbVtlt5ZKgLmaUsMIR8RDHYAHq3Qe5xquVE01dUvHRSeI3KzSVJPKFU5yQT8Cb7ufM2cbZxooP5IwO4KaBcwdo3VPJ9eM8zvXXOQiNVxzpAc7KqjZn/hGQO+T0i3mVbTb55agLWXGY4EDOHSNsnLSHpIwGT90e+41JjlhoafwqFyqMPDkq2BDv6pGOoG/wAz3IBxoLxbFFR+BFcYSGP7wUXNh37KZSPhH8A3Pt1I+WY5MMqAU4ErKO9VUtM1Q9TJK2ZJG6Me+PbUSsMlVXeFD52JCRqPXp/PRASmWSWoYIpwW5UXlUegA7D20uF4lN0jlK5YSc4XPXk8x/UDVHUEj7w4PtUn4mv2m1QU8CwcwT6qkcJZthkLj89ug1HmSd5DCCQCQOvX/TUWnuE1zZWJ5gznK4wAScn8em/tqzWmkgjtf1utYNLIuVQ7bf8Axrmp0jUoGByDFuj8TXUWMhGCIFS0mWd2YZC9M9AMf21Dq7hLQc8VKvI3KY/EB3IyScfn19vx0duFWamQoFCI8nOyjuc53+X+/XQ1KIyM00mG3PXt/v8ApoSpy+F6GYeyA5Mu/wBEPFkspaguzyN40QjhqH38NVYNyt7dMHt30B4+ulFZeMI6iBBJUU9aKhUBIDsrk7kdum41XZLg1B4xo1xKY/DJPQbknb8R7evpquSvNUV0TVDs0shyWYk5/wB41ulILMyQdrGQBXhS93Suu6zTVCIgyCsUQ5UXfsO39umND6LgR6yklu1cHioFjLuV+JgN/L/f+er3BZaKlWniqHCI2Cxbv+8jGB+Bbf21zxzezUI9HbR/wgXDYG2wPw98bdTv6AaIWp/ZciZjW1KwQvgzPOGuIqi3T1NgrKtxFIfDSYd9+h/i7H1379XKmC41Nx8GSIsxfmjWNiUxjAIJPw4HXQG42l5mdolIizl9tWLgDiaS03GCkusfjw8+IpGHxH0z9727/PqL5dmnXzMemMG8vUkop9UtsfCTUdjgq6weaWdEC42AOSQB64Hf/XVksdztdi4XpEeQNMYy2ApbLk5I2+I+w6bZIyNCfpM4jpa6CkpaMsYIwzAiTlJLDAfbsPTr8s6q9tWrrZgZmeeTlCDmycKMYHsMfZGrbH1OMxduXTE59oD+kG6VF1nnnmZlAkKqC2fLucdMfl/rrTvoiFKnD7SycomdlOFXmdvL6Dftqk3Th6esuwoyu7NIWBGM8v8Arn/2nU2yzSxT3WgjcR06SIpVdgRg9SOo229O2NZ6jBtVE9hC05pLGW76QbrT3aje307RloMyeQ59gSenfOBn3wdtU5YB9WXnPLzxsrH31OaFnEzRg5ETebpv8v76JWSGmnpI3l5PrCE7t0+ajTqixFpKnmefvos/ECxeJQeJ7a08CVZTDSqPFUjGSNj8jkE59/TUvhC9PbXgt13LSQ1MPLDIx65PwN7gjP6jvq03GlSakmVRh45wFDdSCOn5jQO92CKtoG+ooJ2pwfFiU78gJ5TnsR1z25tILwM7h3PRaW7I2PCrUjlqmGEF/Hi8nuQQ2D74z8866skdRQ10vONlRxuMjy+cD8l6aB8C8QtDcIrbcpD5W5YppBjnXG6tnbmAPv69M6ttWQ9SmJPLUh1aM7MHKsv/AN1/vrrJbdwGZW2k1tx0YToJ6CpoJaGGT/i5I1WnB25XJZChyf4s/h0Gq/CK1bsslREY2WUSFQgUAjcgAbY7Y6b6hWw1QuFPO2XWneN8nsAR/p+etQss1uuMPhzlYpnJp38XYlirBd+4Jx7gnfsTg2U5E4mD1KPxLYKCtobhEvKZ/EEz03yyHI9uhHz9joTwtd57PXU1urplk5sfUJXkGXxysI3HqCQA2MHBGTg4IcQVfJeoZKdWOAjqxznJ3PzG/wDvroXeeHBeK6SniXmqGmQqBsct5SQdv4D6b9tcK45PtN0YEbW6hy/Xi9XmvlWvZmWnPMkI+FcdM75Pl2yfXU/6OeHY7rc5VqagRQ05Viw+Jl6qRnYdtz07DOjH0frJwtxvS8OcZw0slbUwhqKuZuZZ1Hwqc/8AMUgr7522xohS3KzcC8T1fMrVVOvNEscZz4kLjmj36ZBGM+2s11AdSiDEq1GxtzdS28N2RLNa56d4RGkU7AP4eGdSeZCfwI1i97uL8M3u4R2+SRLTUOROkJICsOkgAO/lIDDv166snEP0p8QcRWR7cGhpIEKgqieZ0BIwW7kZGcY79NVumsdZcKGtNTHKZOX6xCzg/vCD5sHuSGz3zjUppCNufszQ2ZGF6jlorHqameKpd3p5Kdhz5yH6EY9RjP56D0VCI5ZEl/eSo5Us3f0P4jGnbKk9rXx3hf8AYviBXm5CVpHY4APohP5HRiW9x8P1sjU9vp5q6YKyTSDIQAEZUHbPTfH4jXpKL1r5UZPxFF9BcDJwPmR6mwVXDzJxFW0jfUCyfWqLnCSTp2dd8q+OgPxhTjfGT1741S+xLb7Wop7eI/3YGwlU9/l69z3xuNUu63OprpvrVyqXqCQeYM2xB6/LP899zoKS1DVMC7R0MjK4kGxj5s/vAPQ/aA6HPvrWhWSzfZyPj2EytItqKVHDfPzJt3hqKavDULOkscgkinR+UwMDkHPYg6336KOOYeK7a1LWNHHeaRf+IRRhZl6CZB909x9k7dMayapoTVWRHiVWjZQzKvUHuT6jOd9VqimqrHdqe40dS1NWwNzU8irzH3DL3UjYjuD+Om2q01dtXmIeRAfD9ZbRb5Non1rrpR31XeAeKaTim0meNRBW0xEVbS82TDJjse6MN1buPcEasmkM9SpyMxaWlpaktFpaWlqSRaWkBnSIxrmRJFpa9A215jfGpmSLS16F99ekb51MyTnS13pa5mScAZ17y++utLXMmdwZ4NhjXulpak6BF20C4otH1uI1UCZmQeYAbuv9xo7pavXYa23CUesOMGZYSY2Kt2Ox1AulC74q6VuSoiPMrYJB9cgbkEAAgb4AI3ABuvF1pEZatgXEbHLgfZb1+R1WnzjkJxp0NupryItIalsGMWqpjqqYHy5GAyBgxU4B5cjY9RgjYg6OWas8CpgSRijo/wC4m+4T2PquqndI5LTP+04F56Y7VSADPLk7j5Ekj5kdCMS4XSraTnl8RWwYirDlK4+IY6/799AWDzFNb9whCE9Q6lyv/wBK0ypVWqOgf67ByrJIx5Y1JGdz1O2CAvUH8Dldzu1RX1j1ckzVE/weM+yxj7qgdBv8K7+uNWC9203uiCE5udMh8E83KKlOvIx9fTce+x2zO53VYJTSzxtLUjyCjQYCEHo+P1UdO+dCaPRVIxyPVO6vU2MMZ4lntHET2hpJSBU0EwKVaSthJV9Bvsw7Y/E+jHEdDUiOCusMwqLVWj9zXlssnXMTD7LD5DPzBwAprZU18qVN2kGMeSFdlUdhjVw4cmkt4mhFOKi3TKFqaYbBh95fRhgYPt8tGvpCnr/aB16hX9H7wTaLVBSKZHHiTdWd9WO2USSsrVEXNAeobI5vw9NO1FoipRHVQSfWqObLU0pGxx1BH3x309BUoZRGTlicZ98Zx+I3Go9wZMIJeqgq2XhuknWJkpa2TyNhaWqffA7RyH032Pv69Zk7PAzxSsYFXHnz6+nuDjYfEDtqq33ia1Wm3OK+SNwfKEO/Mfu47n2H4466r9Bd24ntX7Ar2ms8rP8A/R05kCtKpzmGQ9V5ux3ztud+ZOUbJx1GYZQOTLDxJxzAjPb7VGK2rxh+QgInqWboo9uvry6qsFZWrVxVU1bLLcF80PhEgR+vKO/uTt89Qvqk1A0lC9OKAQMQ6EDmJHcDv/mO3pr1JlELNCVhgJ80r78x/Hdj+mjK9Girl+YDZqnZsKMS4Csj4hQRuYoL6qkmANiKtA7r25x93OP6VyuqRC7xVayeMPJ9VU+YH0Y9vkNRaCCuuThLXG8ahgWqm+LI757fhrQ7ZRR1k0Ut0iha6ooQVgj5fGxsA/o3YN36e2sSxp4HU12eZye5VrVw9cLqySXD/hqVcFIFGNvl/U6u1vtkFBGopIhFjcFeudEqGjkkfwwhDA4IPbVpouG53hRvCY5PU9tDW3qvc2Spm6lYt9NNHB4aU/i0n2qYbGM/ei9PdOnp6C4cL2aCWcDGVHVsYI+Y7HRG32uGlI5xzuPUbDUmslSnTxjIIaoDljfBJk/hIHxD+Wlj3ZyB1D66fdpMmstLCPEROY56HpoNe73QWamlmqpowqbEs2FU+hPr/CMt7aF8UcdtDw41TSRLUOD4bmOQFEP3mIOeXO23fYkd8Vvt0q7rUCruk5kKj93GBhUGeiqNgPfpq1Gme84HUl2prpHEsXFH0h3C6T+BaQ0cIP8AjyJucfcToPmcn5dNBaniK33bwaK/VEdLXEclLcACI2PZHxsB6EHHyOxqtTcJJ3MdMnlO2R0Pt6t8htqFWQ0yRu1YVlbo3P0HsfT5Df5ae1eGJWvp4MSt4izt6uRJ/EFJdqOsaluKfVigyrBvK656q3QKfbft120KnqIoE8OFedsZwq5J9wD/ADb8tSrTxE8NOtnvdJNX2NjiB0B+s0ZxjmTqSvsd/wCRi8V0UXDdvS60pN0tlSf3FZFuhPpIR0b2OP5gG1XisEXcY/eD2UNaQauc/tIDxySxtNWSqkOctzHY/M9WPtqvcQX6kI+q0EKyt2kZckfL0+Y/PUGpqLpe5vMzLGNwuwVV9fRR7nbXsKUNH+7gRaupI3JHkX892/Hb20tv19mqPlULxGFGjr0w8y05Mtlq4lor3w5DavpCgklpY/LSXIH/AIiD3U9XUdxv+JxqHxBwvXWGjjqLQYKu0VIxFdqduZZAc7H/AKZ/h777tjVfkgaokMtaxlc9idholwvxBdeE6iU23kq7fPtVW6cc0Uq98Dsff+eik8EuVBbYM/I94OfFKnJrrOPv7Su1lFUwsZEJYnct31BlIqAA2IpF6A7K2f5fy1p1RabVxJRTXfg9mkVBzVVqc5npvdRnLp7/AC66p81tppi/iKynHlK9j7j+2r2+HV2Jv0/6j3mVeuettt/6H2lfDui+DVRkqOoPxD3B0Sss1ytVatzsNa8E69SvRh9116EabaneHEVUniR/Z7Y91P8AsakU0MlOfrFOxkQe3T5jSUhkMYhww4MPIvD/ABY5WRYeG+IXPwHajq29j/y2PodtB4hd+FbrLTSxPBIvllhmTKup7EHZlP4g6em8C4wMtSg8bIxvtjv/AL9tTrZf5aOlW08RUTXm0KMIGP8AxNKPWJz2HodtcIDd8GRbM8Tv6hbryizWYGirGGJKFmJVz6xEnf8AyE59C3QB7hJNBOIayPzp5WI2KkHAPz7fhqxVNBS03D9RW2Nae7UE0i5ryP3lKu58N1P+Ec483Q9M421W75xHFIiRyMtdUIpjDOM7Eg7nq2CNif10OVes8icFZduOp1FJ+7aV5A0P/VJxj8O/4aE1F1WOuE1oWQVqnyVCbOvuMdPn+umJIK6t/eVjlF2xGB5sfLsP940+0dNRQN4pSFAN0Xdm+Z/38tcNpzxCa6UQ5xkw3JX27ieIQ8S0oiuija5U6AFiO8qjZx6svm9joXebHXWGmjramEVlDIcQVNI3PTyf9w6H+EgHQueeqqYytPB4MDdz9r8e+i/C9wutjWSShqE+rS7VNPUrz08w9GU9T8tx21sG3/VLNgdSvyT1tSQyAKg+FRsBpauLpwFcZHna6VXDcuf3lKadp4ifvRsCCB7NuNLV/wAP95PNn0whAGNeDABLaTMOijJ14EJXLkafk5gk8YlvKg0kTGy+Zv012Bgebyr7655yfKgKgfmdTAkxFkITk8z9gB01yQzHmJwNegKuRnJ9NeorMQScZ1zM7G8Hm2/MHXqR4O42063Ku2Nz099cYZjuMn0ztqTmIi2x5fz1yoIA5up7dc662IPL1BxnsNeAdRnJ7nXJYTzfuOnTSOe259de98bg/wA9Jd8jIxqTs8Uco6k+mvRr3l6+mvMn/XXMyT3k/H214Rjr19NdKdv66WR8PfXMyTweXc7trkKCeZhk66Xuc9e/9tenAG/TXJJyo39/X10txnXqkcx317j0GoJJxgYIGNclSBkYz006cY2x665xkZ66vJGeUgH01yQT0z89POuBnp7a5HtqAypEZA9tA+JeHILmpmiKw1YHx42b2b++rAAQDj5HXmOvUasjlW3AzK2lLVKuMiY5W0lRSVTU9TE0ci9QfT19xrgDHTprVL5Z6a60/hzgqw/w5F+Jf9PbWd3i11dqqDDUrmMk+HKo8rj+/tp/o9ctvpbueO8R8KfT+tOVkADvroMTpAAjY68IIbTHuJDJlLWzxDAYsv3WOitHc4GHLJmNh69NV8acBxrJ6VImleoevqXSmlUgFSHX230Qpzkj+uqBBPLC/NC7IR6aMUl/qEAWWJJB3I2OgbdI/wDpjGjX1/6+JYLraUqwZocLUd/R/n76r0kUkUjRyIUdTggjpo/bb7QvjM/hOezjA/PROvoaa6wDLKsoXySKc/gfUaWWIyHkT0Oj1asMA5lJ5fNroLk+/XUito56OoNPULyuOh9R6j202Bg7ZOss5jReZCuNDHWRkMMPjAPr8/XVKuVvmoZ3AjJj+0vUEeutCxk53Go1bSRVURjkAz2bG40TRqTX+Uwu04sEotvrXpSHRi0OcEY+HVkoamOoQOjDHpoHeLXPQzlo12PbGzD/AH21GoatoJPEhOF+3H93/TTB0W5dywFbGpba0tMvmkOOnppqWkjqYXhmXmjbYj+vz0qGphqk51Ofx1N5Rjy6XnKw9WDDImc8Q2OW3zeIhLQ82Y5FGCp/of56ncNX94z9SrgJFlJ2GMSZwCVzsGOBlScNgdCFZbrPTxzQPHKiurjDAjIOqHxJYmoeZ41MlMx9Ph+foffQOq0I1Hrr4b+YXRqDX6W+mWqaJVhE0chlpnGVk38oBAPN8iQN9wSA2Mgs2oxqr8O3+WhmEFW3iwSELzOcBsbAMfstgkBsHYkEEEg2rlR4zPSZaDO64wYzgnGM+gzjfYZBKgkX8O8UZW8nUdwbXeGBh5tEROemkSAM65GMZBB+WvSDjfXogc9RF6hOgcnXIG5AyB30lODr1c59tdnQZ50O/XSGOXHtsdekjfHXXOMjHbUkODOACUyfTXGM7Y305uASd8ddcHPN6j11cTBzI7rscb/01EqIQwO346nkYzvvptlyPfGtVYiZe8r1enhIwO5Ow0CjjqbZIaimJZcjmTPX/X/e+rRWxieRkxsvf30Nlh5cq2PnpJ4hUuqyGjbQ6tqORPTM12okWmqBG+cMHH9OxHpqbZb9T2qwV1nijRYa1xFNUuuJBgjmJI3K4zt/TINdqYXopfrVOeU/bUnZh6f69tOzx097hEkbmKoTyuNhnbofQ+h/2PJNX+FsII5+Z6ZHXUoGB/SdT1VVcql6O3My03wvKVxzL8v6fnq2cN8PQwUzMpEI3Jkbdnx1O25x3xsO+Nd8FU1tobfLNWiIRxycmd+oHRV2LMfngdSRtnu53KavlaONTT0xwBEv2gOnNjGfl0HYDRKoT6m5gVtoX0pwJ1JXzPCaSnATnwsjrnL79M+nsNG6GoFNCkLKOWMAAkAj8QdtBrNB++5iCxHwgd21Y6Wkpoqda65nyZIijABLkeg+0f0G3qNa1Us7ccAQS20KMe5nNNR1FykaqnkMcC5kklc4JHrk9B/Efw149xSWNqG2RGClQgSVJU7k9EUDck9lG574GdNXSvmrYI3nzBQ/4kNNGw55gM+fJ7fxnbsue3STxR0UUlVTtA8inwaaI4kkU52HeNCN2b439cZOirLdi7K4NXRube8TQxPRMJZvApEYCV2PN5h2OP8AEkGdkHlTO/fTRhluC/UbfCYIMeJyM3mcf9WZj09u2+3c67o6apuf/FTvHHTwnwkcJmGH+CNRs7ew2HU+uvZjLLy2+3ROKVm5mTmDPKR9p2+1/IZx66FY49LcmEpg8jgR6JqWg/e0r/WKpV5frjLsntCuPL/mO/oBqicQwtU1tbXVQIVPJEp6sc4yfxyffWk0lFT0sE9TUzI00MRkC52GBsB77YzrOOJmdIYI3wDMecrnfl9cehzkfLTCrT+XU1tv6CCrabLRXV+pgWeZ6agMkZCu5KDPYEHP8zo39GlvNXVVdQyEoiJCpz9pmz/9zoFdIXkalpw2S+Cd9sk60bgbmtXD7CONHeWoMpYg7cqlB6ZG7H8tL0qN7EQ/W6tdHUGaEammPD5jnRQ7sGxGe6lSAx9wTn8Pw0291krVeoV/KiEIB0T2xp2eQ1waOTJMhJZm3I29dC7jTGgjdVOOfHlA3Yb/AMsfrreuxqw1d3xFlmnr1IW+g+/MP2OogqKZvFPLIoPP3/EakyuzKIYwQg2J6Z1SYKipkUyxuYwpBHKcY36/7/DWi8N0UktsSsrEEZVkVsjy7nv6d9tLr1Ckbeo3pJK8yBZ7BNcagyMOWLPmPrv29dAOJqWnp72DTAFYHIK46cpI6984Gr3WXNqGjSgoECtygPIexPp6apVRGZqp2Hmdu+qae1l695e2sOMGQqriCerqQ1WeVWfCbfCO2/8Ase2icsTAc8mxxsBoJdrcY40Zct5wT7ZOnqW5N4bU07ZCL5XPb2+WvUaO5dpDe08Z4poXFm9BGatoaYhMEhtwvy7aq/EtKzhSQBGgJ5QMFSevTro9eD/xKJygvybY77nRThjhW48R3WOKnpyV5AzSNsir8OffcHp6aX6+wEYP0x54QSqBjy0rfDF58VIrXd2ZWJxTznqfUfP+fbfrr3CdFRUVMJ+eMjkz4mdse2oXH/CXDnDvCDUEyKzzuGnqCgMicoLDk+6WICj5knYHFA4G4qqKWQWi5ylWZf3UpOM53z7N/wDPzUVWrU/pPpjvUUG+vdj1Q7xTxNTUlRUiBGepKSAgNyjeWU4Yg5AwwyBufUaIfRbYai+Cqr55kjik8LPIoBLcpzgDZRvqgcURzm+1Q8PEjuzqB0wdwc99aX9D91p7fw/VQ1NUqPGInwD5t1P44OO+Pnq9wIG5OcwdPShD8Ylx4ktNDbOG5KekiIdiCWwSx69TqiIzCCJ4wcqwORqwXfiCa6yiFR+4AJBbcnY/l+vzOgFPtQnAyMjGtdKXUYaD27HGRCtqpI7hHVQSOGmlICop32BYH5eXGh1mrKiz8Uxx1nLzSry8rfCyuoI2P/b/AH07bJ5KS/R1EL4IUsO42H/zo8tipeLI6O7ULGml+twxVK915iRze4266ydQ75c4Exy1S+gZMpfGXDBe2XK4W8Qin8GKpiVNmChyGOfUELv/ABDQ/griVp8W2vYisiA8MluXxgpGP+4Y/odulmqLnXWColt9UniBufkUnCjmByPmNtvVRqn8d2qmPEDT07MonkjlWWNQAgPVs+uwPocnQdmnavAH6GH6XVJcNry/3engWonLoWinKrShQQvOEK/CO4wu3v76AXiqeK61Sx5jxM/LykjbJHXsSP59xrngXiiokrlt9XIRcaOoVwA3KJmjJAdc5ww9CPY9dzcNjFXdVMx/dSxxyxPjmBBKAkZ2O+evvkawVuDmdsqK9SPUqK22UsrFfEFIr7DGcDB6fL/febXKaLiGmYY86DfrjlZlHudlHQZ0N4gX6naaI85DxK0RIBAI537+47enYjQSsrZ6ump3nYs+Chb1w2Rn8DrYpuJmWSBiW/6auIbPxFb7XSIS9ZREO1QmeaNWAzuftDynG/Q59DTLXdmvDSw1h5bpGStSe0wB/wAUepBGT+J9dQ6wSeFTTJjIDRsT7b/yOPw1N4esdPdLmkIleGqkTEFSg80MyjKtjuCBgjvvqq1DTrlfb+ISbBYNrS+8GcN0VVYZq2eRRKVZMdPDfcY998bD9dWe41VJDwxT3uuUB4wrNFnzMN0fA/E4z3AGqVwxxVU8OftKiuNCUukHIZYEwV5ugkX+Bhg5xsR07Cr8U3aru4eqlYACVn8MMeRWJ3299tCpW17k+0sD5PpPcO8XVtVUwraDKrW7w+aNVHlcHJ39ff1751VWeohpaeglkEyKzJRys2/vEx9RsR6jHfRIvLW2OGXm2ixgg7lCcH9cH8dN1VJHW216QLuwDx47OP5Z6flp3pq9yEr2IDZZztboyAsXhlmkcTOOnMPKvyGpTKaqiYEFpIDzgnvGfjHyHxfnpiiqPFH1as5mqVXmRgu8y/L7w7/nqRTNPBULIuFCnPJ1BH8R7+mPfTsaqt68KOYo/C2VW5Y8SNarjUW0CgjqGWJZP+FmBPLG52MRPdT29DgaMtFHd5Sjxx0Ex+KUjySN2BH2W/Tr+I2qoEZjSiMzROAETGcoegPoe3rkaI09uqaCtp7feYpfGeLmpfE6Tr9pG/8AUH6jB651nTcKztJ9J/aaaig3DzFHqH7w/wALJdrLe0rrUySVcEYTzEolQmd4XB+HONj2YA9M63Lhu9UN/s8N0oGYxSZDI4w8TjZo3HZlOxH9CNYba/GgqAInLwlQ0RO5jK/zAxnHbR6C+Hhi/C70CTS01Woa50iDPOAPjX/1U9B8Q2PbQl6FLCBGmkvDVjM2bXvKdMW2tpbjQQV9DNHUUtRGskMqHKup6Eak6xDQ4cznlOvQMa90tdzOgRaWlpa5IRFpaWlqTuItLS0tSTEWlpaWpJiLS0tIDOpOxaWveU6QG++pJPNLXpG+vVG2+pJOGjWWNo5FDKwwQehGqHxHamoKsBQTE28bf0+Y1oGo9wo4q6kenmGx6Hup7HW+mvNL59phfV5i/eZoeSSIo684IwQR29NBqSM2smCTIpeb/hyF2jXmOV9yM5x3GfQ6sVzopbfVOkq+cdcdCPUaYkWOeHkfdXG/r/8AOml1S3KGWAo5Q4aNOAyh1bDrujKeh9c6r/F/Dkd4El7oKdVu8IBrI0GDUKBs4/iA6juPcbzaVzaqpLfM+adtoZGOwYnZc+h7DsRjfIOi6+IkiSxOUkQ5BGhUc53r9Qml1K2oUbozPrVPHUqqu+JRvsPiHqPfRendYtkwFPX31zxtZI1kN9tSLGWb/jKdesbd5FH3T39Cc9DtWa3iCltcX7+Qy1Unw06bkt02x/L19NFW2o6bwf0i/TI1TGth+svFLcUtcUoqOWS2VB/fxsfhP/UX+IDfbqP1rvG1bcrPVRUVqp1lgqoRNT15P7loidsEdSCfh6jPUgjVQr5K+6r416mNPTLsKNDjPoHP/wByNWHh24UqW17De08GySHMDqMPQyHpIv3VOdwTncnudLWoYev2+If+JTOxTzAdLTctYamWRq2u5RzyvgBB7Dog/X5am+EjsY3Q1U5GeQdF98H/AO2bT98t1RYqtqSteKCnADxSREMKhT0ZBvn5nfORpyw2i5XoctJEaOhJy0jZ5pPfPfRHmIq4WDpVY7+qF6Cqg4gjS0XOoga7wrijrGJKSY6RTHoSM7H+p3fsvBtXNVGa+MfETbwAdl9v/jVj4f4dorMqmmjzKOsjDJP+ntq0UlMagZCsOQfF15B6H1X0PboexKuy01n7Rmle785At1sjjiEUEQVQPKFGjFBw5UVXMzRBY8YJfo3t76vHCvD9IIUnk5ZXZc5HQaL3Gljp4HlZlVFUlidgANLrdYXyFhtelwNxlZt9qWOBKuJnqoIyBIrf4seOoPrq6UMsD0ihGUx8uVIO2NZ8vFVvozLdaadlSMlZ43HLzKPtnPQe51Wf/wApNtqLrUUtFK9LTVI/d1TJ+5jmPQ4bqM9yAM9uh0L5bsfvN1dE5l94y4it1lgM0s6oTkr3Z/8AKv2vnsPfWLcVcVXa+PMolakoiMOOcc7r6O3YfwjA9j11D4rmraa5yy3iV5KsjmZ2bIkG+GBPbttv21WaiqqqwhY8xou4OMHHqB2+Z3010Xhin1vz/EVazXEeleJLpr9U2Cp57ViRzjxYHXKzL0II7DHc/lqVX0FHfqCS92IyiOPettzjMtO2+SB1df5e46V6Samo4+Vf3krdPLnmPqPvfM7fPUWCoudNcI71RVv1Gqg6SdQR91+xBx8I/Dppo2m2euv/AKi+vU+YdlnMT3DIaOkXO3mYHYfMj+Q0xUNBRRipuU4XugIHNj+Fe3z/AJ6NvPS8WUdTXcKx08PEUClqmgz5Zh1MkGds+x/Q/Fmr0VdWTSVV1leBVcrIZiQQwOCMdSc9QOh6kawu8UFa4rGWM2p8MLsTYeJIvHEFVXc1LQxmGE+XC9W/zHv8v01N4Wv1bwlDUw1ZSpo6n/zFtlGRID1yD8Jx365xtjQlKtYwYrPFy/ZNS483uB938N/UnTcFPHE3iOTJL3Y/01zR+GarWv5lhwJpqPEKNIuxOZabhw9DfrS144NqXmtsZ5qu3cv/ABNK2+cjq499zgbZAOKzGixxhYwAP1OnqGrr7Rc0u1mq3o66Po69HHdWHcHbrq6Q/sf6QkY0kcFl4tRcy0jELDW+pQnYN/s/e0501S+GvtsXg/6osvc69N1Z5HtKN89egHHTUurt9TRVclLWU8kE8Tcskci4KnXCxHtr0AZWGQeIibKnBEixR1NNWx3G3VMlFXQnMc0RwQff1GrXSXa18VS/Vb8ILLxC2yVY8tNWn+L7jH1/n00CVOw15LTRVELQzoHQ7EHS3VaIMfMpOG/mF0a/A8u3lZKvVmqqCraiuFO0Eyb4YdR6g9x76DyUslO/iQsQ+e3Qg9tWK08RS0FClo4kilu9jG0MwOami7AqftKPunUi+WiCjtgvFNVrXWSQeWsiUsBn7LD7DfPA0m1NdV2RcNrj3+Ywp82nDUHeh/aViAxVDmKWMwVGcDbAJ/pr28yQWsMlfLDOQPLHG4Y5/wAw6fh+ONC6u8S1cr09npyoA5WlPXHuT0H+99eUFqXmMs3LVSj4nc4jQ/1Pt+mvMWPtOFnoE04wGb+09s14vkF0judoItkSZBYeVZVPVWG/iZ9wdWA2+1X+damjiorFd5h/hseSCpb/ANMn/CY+meUnYEdNAqm4U8LFKdTW1IXrjyr8h/f9NRKCNK+4Br0s00T5HLG5BXPQjrv8+urVsxGDyJqxC89RXz9o2utktslBNS1UflczLhh/v/edQ6e1PUYmeRqh13ZSccnvvtjV3qK0UdtFFxDz36yRsEp6qNCKml+TnqB9wkjI2Ohd7slXFbxdLPWR3GycwxUQLjwm9JV6q3z/AA13yQeV5lfMJHHEERyQ0avGMTZ+x9gf3/QfPTDpJWksjBcDaMncD27Y9tP08CSozzHkx/zWbYn+v4a8kkjgYCAAuN/EOCfwHb9TrMn2lQSZHSiZUAcRJ6eKyqT8s6WlJJNIcsAx9cbn56Wu8ybp9aqAuy76RcA7eZv5aTNtyjYH89cquGxjJ9B/fXoQcSuJ4QW8znp+WvQDjbAHr3Ouwh7+Y+nYa92Gx3Y/pqTs4VVAJJxpMxI8pA99Js8xHX27aQBOyjLe/Qak5ic8vKDzbD3669O4wdl64/vr3YE53c685M+3trmZ2eHJOAcAa8x5dthrtRnY6SjJyDsO+uyTkLk8oyT3/wBdelQD2+f9NdEqPKB/v31wPmM++qkyTwk9D37aQUBMnH49v769wCc9P669wTnPXsM9NcknJG2dwP114QB0/LXZ668OMZ765LYnQIz5uuNeYB314BnY+vTXSrheZjrgOZwiJRnc7a8+XT+eu87b68CjoNWBxOTn59NIbdNdFQOulgAfy10GScMu+SdMv3A/PUkbjJ1y0YJ/pqZ5kjS4C5PXtrk4J83UdtP8uFwd9NsmScdfXXQZI22D0HTUWto6etpXgqIg6P1B/n7al8udjsdecuCRroOOpRlBGDM04k4eqbSxnj5pqPOz909m/voODka2J0WSNkZQVIIIIyDqkcTcJtDzVdrXMe5eHuv+X29tOdH4j/os/vPLeJ+CEZsp/tKqFz217yn569VZB8UZx6416N2xpsHz1PLMGU4M8XbrrtO+ulUZ3GvSmOh1ZTmZ5nmnaWrqKZ8088kR/gbGmmVh0314B+euFFPcsrleQYXa+1c8Agq+SoUHKswwy/I67hkWRcr17jQZdjp2OVozzqcHQd+hRxleDGug8ZtofFhysLFSeg21yR2OuaWoWVemD3Gn+VT20jdGQ4ae1o1CXqGQ5EjzQR1EZjlTmU/pqp3+ySUr/WafJBPxDv7H0P8APVyZWUHH4HXIVXVkkQMrDBBG2tKb2qORO3UraMGZxSVMsUjFByOD5kx1+WrHabgtSmAwDemuOIrAORpoAeQdCOq/P299VyKSanlwx8Ode56P8/76ZYTULkdxYpfTNg9S8kkjI6jrpqSNJEZXQMGGCCMgjQ203RJkKt5ZBsQdFo/3gJxoNkKcGHLaHGRKLxNw99WVp6cc8JHmUjOB6H20OsF3qLRMCzsYVAUlsnkGcgNjcrkAgjcEAgggEaW0IYFWGQdU7ifh7wuaqo1PKN2QDp7j1HtoXVaRdUvw3z/zN9Pe9B+0MxeDWw/WqAZYYMlOMEjJ2Ix1z2xsx22bylsMGUMDkHpqlWqvqLVUhkz4QzlF35ARglc7FSOqnYjV1paunukH1imdBOV5nXn8sgHVgT+pO4+1t59YaLxCzSv5GondboV1KebT3Ohy68z6a8U7sCCGUkMpGCCOoI7HSHrgjXpVYMMiedIKHB7nud+ulpfgPfXIOQcHWgE4OYixBJA02pYMcH304MEHOm2Q78uOuujiYvOXyVbbAPfUWpcxxEA7nYaljy5J3XG/z0NqX8SXbbk6azut2LM0U7pHG2fU6YqggQ8+5HbT0rhAQN26ajchfJfJPbOktl5J2p3DqqgvrfqC5IXZy0nw9F0OrI2pZlqKchG6EY2I9DqxzBViJIBHTVcuchMnLnp10FqKE8s7+Y20d7s428QjbLzBJOpnHIcENkbr/v10XjqnuNUtHbeZixAMgGM/L299B7DSRfs2orJ1BQjAB9B/r/LXnDF0q46yaKGYxQzHkbkGGx0OD1H4EZ6aXadhWQHPEZaqkOpZe5qFoFLbqJKWPFZcpfLyJ5sZ6DbfOPsjf1I1xXVSLIWqClZVsRHsA8UbdkAG0jbjCL5RnfO+o1O4eM01oRIIWjxO/MFcxjbMzjaNDgeRTk9Nzg6aFVFFKlLZ1kmqZP3S1Sx4kfOcpAn2B6nrgnJAJBONu/hOonFYQ5bkxytr/qErvOBPXFgWEh51ibsZT0ZxjZei+5B1IoqBWZqy8PMzTDnELsRNOD0aQ9UQ7Hl+JtvUER41oLXyqDFU3BPNhfNDSn8f8ST+I+Uds7aMWe1T1jCpq2kCu3NhiS7k9znfffJO/wCGqKjlsJzNCyhcvOolq7k4jULFTxDkwBypGv3QB0Ht1PfSjkWIyU9PkJzkFj8T42/LI/XVlpKYqBBFEFVdwgGAoHf2+eqdxLe6GxwmKmmWasy3NKmwAJJwnp/mP4Y66ZaeqnRjzbTkxXqXu1n9KngTviutW2Wd1dFNS7AMrnKx4yfP6np5fff0ObVrtPcmMrtK7EF3bqx6nP4ZGo9wuFdeKliGYQRg8xAIVF64X+/Xf3OeraiHxC48kcRz+WNJ9VrLdS5bGB7T0fh2hTSVbOz7ybe7bWxRwXVFPgTKAGXIaJtxyn0Oxx679wca8/Bldw9a6H4p6NYE8ZcYaF8Dm5h3XmJ37d/U5TwhxK0Ti23PlkjlHKrPgiQbeVs99hgnrgA4IVh9LcFcWUl8oxQ1zL9YZCviydJB05Wz+I36YIPQ4Do1r0sCB+ct4n4emqr2+0zeSOkhk+sQoZSF/wAIjGCf6YxoBezW3CvgokBYlQSAOmScDbsAOnTWlcS8EyW2qluFDG31BQXmhAOYsDJ5f4fbt8ulaklt9pudbWPygRAQKPvOPiAHU+YkAD07DfTW3U131BhyZ5rQaW/TXMp4WD7dw+lHG/1mRSodFbfuwZj/APc760PhCrhrbFXRGNfA8bw8HowC/wCus4S5PcKlphkRyVGQNugTbp1/311eeAo3Th53I3lqXb8AABpVqw3OY+07Bl4+YKuNsmo2NQvmpGnkhjctk8y4JU/gwwe+hEUSKZJGIG+tPrqIJwpT/WAMS1lRzq4+IHkH8l/XWWU0qErFM2GYZXP2v9dZ0WBcY7m7jMiVuWn5cYXlGhE1D4qzfVlYYjJBUdMb6sNRAZatwT5VJ6DT9FJSUMczVCZDBY0AHq65/wDsQ356LqZgrWEzGxFfCkQr9HfBNKkkFbfMSbeWN/gXGfiP9Onz15Ucb2+xyVf1RC80iOFSAgYzPKwDMPgHKRn7W+2M51V+MuIbpdf+Hic0tCrZSGM4JOerHv8AyHbVRl8aa4SxKpZy2T77dT66stDajDWH9JgSKBhBDV7u9xvPi1ddN4h5OZEUYRMkZ5R79yck9ydV6k4aq7rOoponwTny7cp+8T2+erlw9Z2qIZEbLu9PJsB3EZZR+YGrxV2c8NcORV8TxpC+WcLjmUZwGOe2dsnvsMnbVrjXW+wD9JbSWuyZJmXReLTVRsV+Ks8TGOnrEXyPgAlc+oBGR2znRG1UZS/V9JAHdFiiCn1Az/fQfja9y1NCLPHFGtKHaWPKgv4jPzl1OMhiAgJ64QDIBI0c+ini02e5xwXcIxqIQqy8uCVG+x9R3H+wPVbZpbAW+mF6qlNZp2VezLFFbKyjgNRJE0UbKwUsOpx76bpV/wCCYdgNW3je50NRbzBSzJM6KW8rb4Knpqk0kx8BgBkAZOnAq85fOHc8zXculs8gniTaanZq6GYYIiIc+4yM/wA9P0V0r+HzJHAxjzMspR1zhkfYgY67H2bvv1chlCBCdi0RXyehT/QancW2SSamS6UYJVo+aSI++/5Z6jSC+zaefmPEQMMiNXqkquJbBDVUTSNMCx5mGHbxGIOffDe+PXQGGkQ0tFT155o5oSY25d1dSVA7nGVCke2iVmulXZnt7qHaAqpaLr0bIIz33Hz6aO3OC1VXDEBBIjbxsuqbAnlYbkdcl9vbB0QLPMXyzAnq8t/MHczHj7h+jirVvNiq5CjyOyzcw8rjB3O2SRnOOp6baPcG8XS3Ghmt1XyxXKBOg/DEi9yCBuBuQPUa4tcniUc9quB8NOcOZgu8ZIxz7ZyOmR6bjvmocZ2iqsd0pK6jqv3wjVxLGc8kinlddjuOZSPfYjqNAX0FCQe/5jXS6lb0x/gl143lhrbxN9SRVpnjDRKCSOpO2fcnQRoTHaXWQH/GUj0GVIP8hozwZfbZe6dRWxLBVU7ZmVRvETv4gA+JD1IHzGOmjclnS5UdFToQj/V8spXfmXbJ9VOchu41FuGeZlZWynmULn56OWNukbq4PbByp/ppy210tLWxy0TcswwY3zjlkG6ke+dvx1Ims08FfV29t/3blQN9gM5/DAOmbRZa6rj5oYnlblLoFBJYDckDqR8tvU61a1NoLGUwcwXxBW3GqrReTVFqhCWRj8PKc5Xl6cpydvck9Tqw8MUL8T00zW+CSSZYi1RSj4oQBkN7qex99EuDeFZeILyaaFIj4iicPKcL4ZHmx64J7asFy+ju72biy3VnCdzQV0FOyhqghVmkTzGEqAcBlYABt/wzoZ7FrbC9wuv+quG/vK1Y6OVIZoZAFjA5WBIHlcY/TrqPTrKkclOfI6N5iexBwQB/XRC78ULe46OMUMFIIp545Y1wGikYjmiYd8MuxOcj5HPLQSTVsM0KNI9QOVgD1ZdiT8xg6K09pA3dQe+racQZd7ctQFqIyUlY551+JZF3yO+/xfidTuFqCa9131GVUp65F55FY8odOniJ6j1A3Bz01c6Dh6Ojo/rcpE7xusjR48uB1HvsTo7xJwy11pqaa3TJR19K3i0dWo3iPpgdUbYEfj1Gt3u2nKSV0hxteM2awUllr6F0xJzgwF3AyCdwV9Nxj/u139IVkpa6hEFyBRMlqaSI4aN13znrnHp0676i2zi22PZKlbtE9PeIW8GshB5mSQbhoyOqHHMpG3qfWu8dcRVN9vDpJF4EEWF8Jn5lJ+9nAyD1AAAGfx1ytmubids20LzAUd3q0je3l4/r1O3mqVG0qDAEqD1O2R2PrnR+wq9dangZi01OwZO5KHt8wd+vfQiSzzXAxNT88dZEQIpFXLK3QZHp9kruSMavn0Z2txW1E9bCKWutpH1q3Op58EZ5gD1Rh5g3c7Hprd9QKeG5MwFJt9S8COcDPdOEI3qp4JDwzVzc0xI/8lIx3mA/6bH4sAAE5G2dawACMjBHqOh05TUX14kOgNK4wVxnnU+vsQemiNXbqC02uCGFxHAuIogzbL2VQT27DQqas78NGtNJ2d9QSR6aWDrsjDEa80dKznB0sHXWlrsk5wdLB11pakk5wdLB11pakk8Ueuko9de6WpJPMD00lG517pakkWljS0tSSLS0tLUki0tLS1ySDOILWtxpfIMToPIfX2OqA0JhldH5hvgg9VOtS1XuLLQs8bVsKEuB+8C9/f56P0Wp2HY3Rgmop3eodykXKgSspHheR028rg7of7eo7/MaE8NXOc1EtkuYKXKkUHmPSZOzA9+3zzn10fQupMbHOOnuNCuJbYaxYa2lYRXGkJaCQ7Bh9qNj90/ofx0VfTj1rB63yMSZFNOs4qo4lDJzKVdR51OxBHv76zzi7hOCx1f7YstODQ1rkGSR8tTOf+WT1C/dxuenbe58N3KCvp2hUhaqAAToEKAncFgDv1BB9xqeWj8OaGohSooqheSohPRl/v30Chwd4mtqb0KmZJEp5ykIM8w6vsAg/wDuB+uidhslTcp41o4/rMjthZTGSg9RGvVj79PU6XEfD9VZL1Co5J7JKeejwBiQd1f+MbA+ux77fQnAEXD8fD0VwtABWVQsjvvLzDGUPoR6Dboe+stfq7K6w6jgzHQ6NDYVY5IlSpvo/qYuFYoLyErkp3MkKOOaSmz1II2K9MqNunoMOUNE6kQpGBygABehHYj21p9KZJGPiRckTDC5PmPufTUNbZHbK8VtNAJIBkvFjJQd2X+2kleucAgx02mBORBdp4SmnjSWpzEp+zjc6tFLSU1FStDFGqIBljt+ZOjVNV0jUqkTRkFQwweo1mf0h8QUVKWkqaxTGh8sIOAT7jufz1iXe/6jCNq0rmW81Isq+PCoNNIcMucKjHoQewPpqt8c8c0UVG9JIolrAMimj3PzPYD59fTvrKLnxrfrtStRUrNS0mCFc/4nJ3C/cHv198ba9obxTXWOGzXipjW4qOWgrZOj+kUnr7Hp+OQxNehs+p+oM+sX6VPMH3mee6T/AFmvlVYS2ViGQn/6RGhFTXIoaGij/hY9MfiP5D89K6w3AV88FyjamaJuSRGP5DI6gjcAdRvofUV6Q/uKRcuO4GCP6L/P5a9Hp9OgUARBfqG3Ekw7b7vTJQLZeKZPEt4bNLV4zLQsds/5OnXtjtuB3E9vutur0oWRRDIOeCaPzRzr2ZPvH59M/LQaqWKOA1F1mVY8EqpGx+S9/mddcM8b0DRycLXaCofh6fyxyKxMtG56Oh7L/D09iMg4WumkbvP2m1VbatOsfeRbjXW+0ozSOs9SeqK2f/c3f8NVupq7pf6gRZZYeXIVRhVXucbDHqTgaJ8VcJScM1gnuVSKugnJajqohlaheux6Kw2znJHYEb6DS1NVVxeHEgpKTryr1b3Odyfc6DB1niL7EGBCNum0C7m5MchqYbLWq9umaWvj+B42PkPrnqf0A99XGKpt/wBIoio7qIbZxdGv7mTm5YLkAPhPYSD/AHkdKTBGkKkIuM9T3OlNGsqcrZ2OQRsVPYg+untHgC115B9Q/tFdnjRsfBHp/eS7hRVVtrJKGtp2pp4jhomXBH+nvqMwzq4Wi+0PEVLFYuMphDWIAlvvRHffEcx9/U/od9Bb9Y66yXF6G4QlHXdWG6yL2ZT3Gm2k1m/+m4ww9os1Wn8v+opyp94MUZPTXr06ycrZeOZDzRyIcMjDoQe2n44ts6fjQD4gNE2qtg2sMiApa6NuTiWS3cRUV/porNxs6QVijw6K9quAT2Sb+5269D1E36y3CyVv1avhKAjMcg3SRfVT3GoUkCOjRSKrI3VSOui/D97loaVLHeKee72JmAjVRz1NGemYz1K/w/8AwU7V2aE7l5T4+IzFteuG1uH+fmB1UDfXUcbMGfyqinzOxwo/HRXi2309goFvMDPdLTMcQVMI8mfuyY3VvbbPqDtqkVcl0vID1DfUqIbIoGDj2H9f56H1fjlVS/0+TNNJ4JY5zccASXc79TQE01vX61OdublyM+w/vv8ALTvCdzv1iuE1X9ZEhqhyzUTL4iSr3Dr0O34+40xHSUltpy8h+qJvzM28z/P0H+8HUUVFZXZit0ZpqZtjKRu39/5emNeb36nX2Z7M9EBRpKsLwJZzZrdeDUS8OiH6zGDLJZUcBgOpaM/bX22I/nVDBcbg5WpzSQpkeCowR6g+mpVNYvq5SshqJ6epifmSqDkOH9sb5+WrJFxBbr3ULQ8QTJbrtgLFdggWOY+kyjPKf4/zxo5NAmnfN65/KDfjDehFBwfvKtFbEoWD8xQDzZA835f1O2vXqFnYx06rE74UnOAR7n+22it3tFdb680d0j5X+JFQ5SQHowP2geudQ5aeCJOZXDBeoB2Htn+g1zU6Lau9OR8TKnVkttfv5kehaqpqoF4xKqblJBlBkYJwduhxnT1PXNZKx7nw7OaaVhyyQlsxyA9VKfbX56iyVMsn7t0zFkcp5fg+Q/vp2GgOPGicBFO8jHAHz9NL9u3nqFq2DxyYSjhs3FR5aPw7FfMY+pyNimqD/wCk5+An7p/DQOShntdTNTXRPqbRNiSOZfNn2HU/PUqdY5zilhR3Y7TSp5Sf4F7n3/XVqp6K8vYY6bjK2VFyoEX91Py4rKRexHd09j+Gg7NZRuwTgw9dM5GSOJQjcKZWIpqVOT1m6n+2lrU+HOFbKKDxIKesu0EhzFUUCowI9HUnKt6g/hpaAezUBiApMIXysTWQCT5Ryju3c6cQBQdsA/mddLg9PM3r2GkcL18zemvZZgEXbI2X31wfQbD17nXpJZtwCR+Q17su5665mdAzOSDy4IKj9TrwHJwgAGev++uuuXmB5vy0uU5wNScnO25xknrr3Bx111y49z6a6HXPU9tcknAHXIwPTSwTkAYHtrodTnr+gOuebJIH4n01JJ4VAOPTXgXbGM99dKpO3T316fhyNl/U6mROgThV6kDPqTr0J3AOB39ddoOxPy14d+m2NTInQMTgjrnOvACeg04AW3x+Gl8O4G+q9yEzlV5RuN+w15vnzn+2vcdTufXSChu2B6a6DmTEQ9ter13yPw0lGDgDXWuzgE8IHzOucHuDrojG/X016u+pO4nIGMk/lr3CjffOumAA6Z14PzOpJ7Tj1OvOXrk6cO/U641JWMt1I7a8xk6dKqfbXnJy5OTnXZI3yjOMHOlgY210djka8C7HXczmJXb9YFqC1XQhY6jcunRZP7H31VY4Y2lMdRDiQHDKRhhrSiBjQa/WqKvHjR/uqhB5ZB39jo2jWGv0t1FGu8LS71r3KsbTBIpaN2T07g6Yks1UoyjJIPng6lpNLT1H1erUxyLtg9CPX5e+i1OyMu539PTTFdSw5ByJ5yzQV5IYYMrL2+tiGWppMeoGR+mmGTHxLg+4xq7ROAwwTt01I5IpFxJGjj+IZ138cR2Ji3g6tyjSgeCpGdxpoqQ/hqc51cL8tqpqSRmpIjKRhSBjc9NVCM5fPf10ZRd5q5xFl2mND7ScyREeQB42BC7ZHUfhoxT0lRJQiqjRiv2gBuPfQajWSpqo6SE4ZjgkDoO+tDoIkoqYIjcqIAF/376Xa9lxj3jzwV7EYkHiVSPz7N0xriSMjoNvXUviGeggqEaOQRNId0x/9l7aaiYOnt66WbWAyep6yq9LMgHkSMCQMaAX/h+OqhZ4EwRvygYI+X9tWWRMHI300+y9dXqtatsiWetXGDMvlEtPNySHldPhcd9HbNeBzCCfyk9D66N3uzRXCNnjUCXuOzf66pFVTzULmKYNyg4B7qdOK3TULg9xS1b6dsjqX+ORXG2CMbHXLxhjqr2W8NFiCofK/Zcd9WmnnV1ByCMddB21NWeYbXcHHEq3EnDonjaoo0w4OSg239R7+3fVPp5qm2VXiw8wPMGZASuWB+JT9lxrW2XC5HmXVd4lscVwjaWJQs43PYP7H399C6jTpqVw/fsYRVY1LZXr4kO2XGnuccTxMFmxyKQuA/8ACVHQ/wAPb7OR5RKRs5BGG2yM56jI+YPUHvqjSpUUFY7AFX+GRG2D+ze/odWe13eGvhCTMyzIcB2+JSd8N8z36N3wdyFpdVb4fZ5V3KzbUaSrWpvr+qEi3UY1yMD1zr083MVcAP126HfGR+PbqDscHXhJC5BGvVVWraoZDkGeZuraptrcGI43Iz8teA8ynBwe2deFhg++vMgAkkAd9akYGYMDuOI1VSCOFvU7aGSOFXljGWxvruqnMspCdPU65VFQdckjSLUXte5CdCHpWta5buMxRebJ6nrrwrj8NOgnPXTU0i8jHXFQIMCYFt/JkK4SiOAk9Bqrsz1FQEXdnbA0TvtTjEQO+c684WpvGrHqJNo4Vxn3P+mdLte+cIJ6DwyrC72kq+VCUlkjooebmbAIxjp/v9dRuH6Zt5OhQYB9++ol5qPrd2Yggxx7AasVrh8CiXK7tudBU1CwnMJ1d2xce8lQ10qxGnZ2aMsGaMseRmGcEjvjOj0VfTQRCC3+JJLOnhzVLKBK4/6agfBGPQde51VqlMjK7EdMafttfJTTEAnJUow+8D1GtFBoba30wNiLUyv1S/cNWaMyLV1CiSUqCin4V9PbVyo4gqNUSOERNnlbOB7e59hvqp2m7Wykt/12SUyHbFMGwwx99uij0xue2qjxtx1VXNvq8DlYgCFSLyrynqAOw9Sdz39ml2s0+lr/AKZyYv02j1Gqf+pwIf4/47jiSSitj/u8csj9ec+/qfQDYe/UZ/Qwx3GV6u8TTpTE5CLjmkbP2ieg/A/LqdQpKbnWJ0qEnqHDExop8g67E7E/730+600NteRqeaaoI5VDvsCdvhAyfz0kDvqHzYePiPVqTTrtr7+Z1V3JauLwKWmWmolPKqKSeY+rHuf0HYDTczintMr82GlYKMfl/Q6akingdVqhyyKufD2HL18uO2wO2vbohkloaKMZOQD7knA/rqWnJmyDavMgxwmSKRhGOUYG+rdwbxLVW2oigrS6xtgQzk4zjorH12GG9sHGxV7h2CmpaOrp54o6h3mTmw2BhVYEfm47fZ0N4xiqViy37ymBwiLsqbdMevTc7/y1y2pLBtXse8rVeyHnqfTfBfHdJV2tKSvOHiB5n7hR1yPbuOo/MDArjWz3K4yySOxDyuyqTsoZiTj89BeDeI56CWOlrpD4TAKkjnt0Cse3se3fbpbYKGkgqUruR5aMNzSRY8225Q+x6fj8s10JWuwiziZ66ksoavkQjwxSSVD0wijLH9423bp1/DWmcMTJSWGnhjMTtzO4kQ5G5I/poHxlR0dqp7PBbPCCz2//AIloukjqFUkj1yN8+2dxojw+p/ZVJFHkkJ269Tt+uqay/wA0ZHAg2koNK7Sc9wjcJT/4ctskhZpJKmqcZ+6XUfzB1m9LH/xbyvjK0bsMnp5cD+etMv8Ab56SxWqKoXw3ip5XK9W3lc/htrM4JHasmRBkijcHAydlzgDvuNTw/YGy0tqt2whYrdVc5YTY5iAFPrrq4xM1OhOx3J9Bo9wpwcUjSvvbhUxz+AW5Qo7Fzn9Bqatkpai800URlloXL4JGCCMHl9cb7HRGusrBPlHiC+HNcax53cpdHZqu4+J4MRWBBmSRtlAAyd/6adpeHXnrHaGJh5Ys7blmXmwPwI1onFVRS2mwzQRJEgkQwp5gqqW8uSfxz64zqh8VccU7xVlNZ4i3j1DkO+CI0yFVRjIfyqP4fZjgjCq21mUIIbaFCndJ1beLdw4kMsMqT1CKGYJjl/wyo2OeYcxG5GD2z2pt84juvEMgiL8lMoXEaE8o2xltySe25J7ewDSrJUrVSyu7vyF3LEl2OdyT131ZuDLBNXlI0g5E5twdgBnqTpnVWi2hn7im6xvLPliVisttXcrvBR0kRkkkXGQBkgdflp++hrfbG4fkSOWRCk4lVTzwMAMMjDoe34a0iOwrQ8SpJCFJhknVix5VwI4m3PQAczaqF1jEvF9YrMrn6sMnkKrjI7Ht/PQTuLb9uMiNanKU5MZ4Ov4qStsu7ck6J+5lJwJFI6j29R269M4sdJC0UMsLxlXAwQe+2qJe7SVME8LMiqxVZFOGjbOVIPp11ZuC+IFuB/ZF0CxV0a8sch2Djt+Hb2+XQvTXtpH2tyh6PxF2v0C6tfNr4cdj5hieX9ygUHfGADrQeDq6CrqBbqshQF8vPv5SOo9hncduvTpRZaUijw+A68wZSd9iOo/HXs1d4NRAU5o25UkRlODkdwexGOuueI6Nb1LJAPD9a1J8u0w7xfboqey2+SNeZo/GpyV3yQ7EZ/Bl1V7PVFKudqjnlQp50BwSARn2z3ydWGkvD3SmNtqJJHUSNKjkDly2AdgMj30Ons8sNzlKxjkkhY79MfDn3HmH56S1s1bDPcd2JvBnVdZkqJEmopTJTTQN+8QHbl3J9iowSD0x+JBpBNJcZLXdZHTw3PhPI3kRvi5hnYA531LpblU2shkjdl5ud42dgrZHLvjvgkZ79DqdxNDNLDDeoYUKJyBjy56Ejf1GdFNY+own7wUVpp82Sh8X2qr4avEFfRGWCRThGbIBxglW9eo9+h1cuCb7S1azVmfq00aATICEeF8gHrsV3GM7DO+2DqFeKo3Slbh6qRjIkiinlYjy8oZV9yChReu3IvXG1dqlqqA0rqqQVcHMhd1I8QKMGJsA5zsVOOrNnYnQd1TV9jmMtPfXegGZsdHTWmr4z8WWY+HJROoaKJubnZOQiRceQnm9cdME5Grx9GdFSU/DkcVNb18fZpAFA5g6h1529OVwO/TWFUFbBcLV4tIzQVHK0EkTllKnYhG36Z2GfQA9QdXCP6SZLZbzarbSyU8gjjV5ZJObzBQMjYHpjy52xjcaAsqaxMLOj0NhhPK+sqOAbxFJTUyTT0VVUU6HPkYbFQ3fHI4P56pVyutxvN6q6y5VABrWxMI0CqoxyggD7v8ALOiFwu6XKzVoqpPEmk8OoSRupkjJBULjA8jtt6KB7aAwQ1F0lQKBBAyHfPmfGcb/AIEaMrr9OW7mIce3UBBKu0XZmjg8SQSBJ6f7+D69iMbHW4Wa22e78E0nEHD1RNKyy5qoWUZpmI5Spx6Hb3665+i/hyxXmqaS50YqpzEAoZiV5owASwHUlSp39DoPxUX+jbjCvqrXNz09a7C42zkJEkTNzCRcAgEKR1x3wDrB7TvwsNrUWICZaUrKe3gtd8xyR4BRztv0I+f/AMabv3GFJLw7R2+3Rzx1GSrzPjlaMbDA9c+vTHvqpXe5yXqrWsFSKuJ1BgkC9Vx/PsSd8jcnT9DbKiopGwhKxsH5+wDHlbJ9Ohz0276PrRSoZj1AmsdWKqIDrqGrqK9a+ndmq/hZpWJEwP2HJ/TuD01YOFrK/E1VC1EOWQDwphIeVoWTYq3oQD2GTjI1plg4Mt1BCs9yZJpQNxnCD2z1PyGB7aI1PCUzXmHiTh6lEdRGqrUwqAq1UY2G3Z1HQnqNj21WzUhTmvqbJpy64bmK28H22htr0dOplrnTyygYZCNwV+6ARpX3hu4V1PR8QURjpr7SRFYzL5Y51z54ZP4GI/7TgjVytdXaKGka4zVCInUlhy8p6eYdQfbVR+kPjSnq6IxWmVwoIZ2HlbuPw7aGDNacdwnalKZP9pN4c41oGsKilR4ZoWMMsE/lamkGcQv8umehABGx1T+OOJ1r0koZWZqOTKkRsSYzn0Hb9dUmtaoeae7UKtLUhQtXADtVRA9D6yLtyn8PTT1lVLpCrxSCSllTm8c/8wentjoR+emmk09eSr9xbqdRaACnUvP0dcVzVMq8PXqdZK9Yy9HVZ2rYR3//AAij4h3BDeur1jWLVViFVTpBbppaaenkE1NKm3hyjowPY+/Q9CCOmjcDX6oulK1BeIfqt8pI0NTFy4WVT8Myfwt0I+ywZe25GQp2wmlyy5Mselr0DSIx01YmbTzS0tLXMyRaWkBr0jHTUzJPNLS16RjUzJPNLXXKNLlGpmSc6Wuj8OvAN9TMk8xpYPprsDGlqZknGD6a65Rr3S1WSeco1720tLUkEpnFdnNNL9agXELHIwPgb0+WgkY51IYAHvrS5oY5oXilUMjjBHrqhXu3yW2sKgcyndW+8P76caPU+Yvlt3AL6dh3CVi72omrhuNPVSUrwtzSFRzDlxgsU+0MbMOpG43G/VDXQ3GmeaLZlcxTRsDmNx1Bzv6HpuCD30aKE4ZDv169NVm5U37IuZukHNHTuRHUxhdiADy4x6dFPuV28oOV9ZrO8dS9T7xgwksNNNRy22vTxKGYg7HeF+zr6Ef1I6E6m/RT4vDXGZtlyqVFLOvxfYlX7Lr6Ht7bg6hxSQzQrLBIskMgyrKcgj2OvKwxSUP1SqZlRDmmnAyYXO3/ALTtkfj2GhbOayp6P+ZnAmHFg7E3O8N9Top6lYzOsaF8R7lgB21nV+42qZKfMZ/ZtMOhO8znHTbp+GT8tUOy/SrWcFVU9mu4lqGznwlHO8bYyGTJAYNt7bg74INF4kuVXxTdp66dP2dQuwxSpKTt/E3ff7IAHoNLaNAfMK4z9/aF265SgbOPt7zSbbx8l3qau00dWYqthmjmfeNn3/dkjYE9sf6Go3F5hcJZ7vI5q0bEkb48p9h0HzPXtnVdkqKanT6rSxgsB0Axy/8A4v8APVmpWHFVLBQ3F0jv0Kf8LKTgVqAfAwP2wOhPv74YpoV05DEfrATrPPBUHmC5a2erPhUqlUY9QM83yHf1ydRao0kCMsx8eR9jvnm/HufYdPXTNRVVAqJKKKmaB0Yxyq4IbmB3BHVjt06Z1Aram3WvMlfKZarH+EpBY/M/ZHsP00zJrRMscCLh5jttUZMt1sr14qoksd8Z6auj8tuuJ+0CdoZSOmT0P9dmqHE9wPDVZLamo2W4RHDLIvlU9io+1kbg757ar1dc7nfZVp4FKQHeOOMbfMY6/P8AM6vFsuNq4rpqPhviSrpnv9OnJbri5JWQ9oJmX4geux69CTkMkbXMdyafqOE0acNf3KGIK+7O9bWz8kIbDTStgA+me5/hGT8tepPFD+5s8LFh1qnUAj/KOifPdvfUu+Wy7U10kpL6pimpzyinGAiDty425T1GNt9MqFROVQAo6ADbTPw3wI24uvOcxbr/ABnys1UjqHOEeIjaKWS0X6Jrrw/VMGnhYZenb/qxdwR1x+XfXnGPDT2cQ19FUi4WWsHNSVqbhgc+VvRv54PuAEySCBo5whf5rEs9HUUouFjrM/XLe2//AO8j9GGM42zgdDvpy+lOjPmUde4itNUurGy88+xlc5TnGNdRRMW3G2rVxNw1FRwxXiyz/tCx1RzBUL1jP3HHZh0/sdB4ohnc76Oq1KWruWCWUNW21pEaBWjZHRXU7MCMg6sfD1+hgt6WPidZKyx5xT1WOaagPbB3LJ/L5baFmPlG++nEXy74x6aG1NC389H2MtRqGoYjsfEI8Q8O1FneOVZEqrfUDmpquI5jlXtv2PtoXyDoNFuHbzUWCCWnqI0q+Hp2P1mkmbAjPUvET0b+EfPYjOueMKSa22mG+cIp+07XVthatTzPTsfssPs+nN+eNsr28T/DgpbyR+8YL4Z+Jw9XCn9oKqjDQQ+NcJfAU7qvV2/DsPc/hnQGpvFfc+emtMIpaQ+V5WOOYe7d/l+muKa1zVc7T3GZqufOWTm8i77lm1Iq66jouWFFFXUrskMa4RD8u/4/kdef1Xid+sO1eB8RxpfDqNJyOT8mEOE6y4cN00/gVPj0VQpFXHUqDDL2ICnr8+o9hnUutoYbhZ5b3wTL9eEZH1ullfNRR+4+8n8Q3+e+q4KOvu0oe4ykRnGIEO3sP9BopSQNY6uK4W+qehq4OhhIG33Xztg+hBPtq9fhVvl77P7e8jeJVb9q8/f2gu3Wk1Mv1iskNTJ8W/wL7+g+ei8j0lIn2ZW6LseX8B1b+Xz0Zp5aDjRGioRHaeIh53oyeWCsIzl4s7Bu+D/roKlDJTTyJVo8UqHlk8QHmBHbHX8Bp1o7Ktu1fTj+8T6xLQ25juz18SPJ49S5aRiinY7+bHptsB7DSlt1MsLR1EYxjdMZY/P0+Z/XUiSrSFjHSoxcd8jm/sv4b++o600s5HicxyfLGvTP9dFfWMKOPkwNTsOWPP2nVu4gejpRaa+ie52FdhHzkzUx+9E56f5fhPpqZW8PxmjF5tFYLva2bHjjZqc/dkT7B9+mo0ywUvklJlnI2giwTj3PQDRTgyz8Wz3T65w8qU32ZI+T9w6k7rJnZh/saRX3ppHzU2R7z0OnofV1/wBcY+PmAGenBKQr9bm6EDaNfme/y0b4d4Mvt+mSSWPkp1P+JIvLEo/hX7WrhY7dbaPiEmrsQhrgMyW4t5WOd5KcnAceqHf09NX+kq5L3T5tYWKlUlDM64KkdVCdiPfca834m9moXfWeT/aO9JSlPpx/zAtg4OstsTnjgWpq+80oywPt6aKXKlM9MQU5mTcHOD+ei0VEYY0RpHlKjHiN8R9zjTvg58si7n7WvBajzQ539xymAMLM+reAqK4TfXaJ6qnEw5nNLOYeY/xKDjOlq6PDWUcr/VY45EkPMQSQAfbHrpasut1KjAYyuxT2BFz5BWPAA6nHTXqL+HqTrtVAADHAHbsNeYYn2Ovru6eeBxOQRzFQPy/rr0RgH4s66AAHQa9UE9dge/c6m6WnIX0xt+mly7bfiTr1+UL8u2vCGYb5x6f31wHmcxOdyDyHb1Ol2J7dydenyjIOT2x30lXJy4yey64TOicqC43yB+uukQAb7DsNdY7EZPppIDzZ6nXQeJzE85fvaQXB304qhfc52OucZONvz1ydnB6nSC82cnbvp0KM765bPQbDUknJIAwMfPXBGe+u+XXqoOnXPbUknCKQTk7aXyG3tp3lO+O36a86ZA3Oug4knHbOljbrvr1Vxn+elyknbXJJyB7b++nFHKemTpcuB6kd9eEAjHrqSTlhvpAZ7ga6wOXA21xqSREZ1x3xpwjA+evAuPQ6k5icE46682YD01667HXgBB31depWcnG4zvrk+UEacY9vXXGCflq0kaJzntpojI66eIBGc4HbTUjJHG0ksixxopZ3Y4CgdSdST2zBHEVNRy0Ek1YwjEI5hINip9v7d9Uq13Yc3JMSBnAbpqJxPxbFfq56ejkZaKBsRqRjxD98j+Q7DQpW16HQaErWS/vPH+La4tdhB1+80anqA6Aq6nPodOTVfKpRThh1x2/11RaK5T068kb7aIftQLSlgxLNtv2106QqYF+OyOO4r5WGecQKxZU679W7nUDnOOVDsOrevy1H8TxCWBOD3PfTtOvPIqAYycADRowiYEVtl3+8sXCcUcKvWTELtyp7eupF9vngKYom5pT0HZfc/wBtCa+5rBEKem+NAAPRP7nQUuTzM7EnqSe+g103mvvbqMDqPIr8uvuOTTM7tLM5d2OWZjqTZ7jJGxjYFoex7r/pofymXr8PYasnD9qX6sKqYZz8CEenc61vCBMMOJlpLLUs3VnmTElDDr1GdelFYE6aqJ4kkKgEkHMjvtj2Uenudz7d3lcgYbIyAcHYjSOykpz7T2Gk1i6gY9xGSuNwNDrvbIq+JgQqvj4j3+ei/IpBz0OueTBIOqqzLyIWVDDBmX3Ognt8rRyIxTO/t7/66l2i6SU3Ksjl4zsG9Pnq919FBWRGKYDmx5G7jVDvdnnt9QWCZT0xsR7ab0ahLxtfuK7aGpO5Ja6apSWNXRsg+h06eU5xqk2u4yUrAglos4Ze66tlDVRzxB0YEHWN1BrP2hFGoFgkHiCyw18JcBUmAwrY6+x9dZ9X0dTb6s7NDOm2TvkehH2l1rGS23XQ6722CviKSJhxnlcDcH/fbQ1laXIUccTdLGrbckqtivMU6fVqsGN498Z3TsCD3XsDvgbEEABSz5Vhz4IOysOjbA/ngg/IggkEE1S8WmpoqoBlKMvmjkT+Y/qNTLDethR1YG4+EZwRknK/iSeXsSSuCTldVZf4XZg8oYZbRV4hWfZhDqgjykZ9NR7gv7nlJ5SdOnkQcwfnjbdZM+pOMn8Dv3wRsQVA+V/ElZsbDYZ16B9ZXdTlDnM8u2lfTWbXHU4EYUYB0m16SQuDvrgk99BqAowJm77jFjIxqDXSBEY56alyuApIOgN9qQsJTPmbVXO0ZhGnq3sBA1VKZZ3kPrqwJi28PZbyySDfHr/vGhfDtKtVdYoZQvg4Jcntgbfrgfjp/i2p8WqSlTGFODjXnrLCzEz1tKBEAkOy05nqUL787ZJ9tXIqOTA7baD8MwBY2lI3Awui7sQ2M9NMNLVhcxHr7wzmMMreg03CsKTLNPnw0bJx1ONO1NRDBGWkILY6f30CqqmasJCgpF6jYt/Yax1upU/0kGWmuh0rcWucCSLreGqJWWDCpnpnYf3OpHC/D1ZfJ3ShjmqJQOZ1jGWx05iT0G+h8NuFQoBXlVe40Yss9Ra6mN6WWSGVThHQ4Y+x0u/Dmgg2ciN/PFilaziHYeCvqrO9XKaJYzhvGIL9PsqNz89h76hX6anpfBpLFA31iTmZqlyDJgDcr9lB182+ADv21LKy3OVmrazw+UZdpCSSM9Ao6n/e2q7xHc42q3paRSlOmFOd3lI7se4z26D56Nq2bCwEX5c3bTIdMuZuRiCebrnPTvn8D+eodwnL1rSBivJhQRsdv9dToCIoWkx8CH/f6H89C6KM1FUnPuXcAfidDhdzYMZEhVyZeuH4OW2xQheQlAxIG+Tk6IVkMQpRC+GVs5B3znb+2vLe2TIyjyrhR+unqhQzgMMjT5dKlmnG3ueMfxF6NYwP0yq8QWj6vBJLBHzQYAAbfBz317wlxHJb5Upqp8wbKrsfhAzhWPp1wd8Z7gkat31KWopQDHnmflU/e2JOfwB1Nqfo9t9tt8NTXFnhnqIIpGjBIgVnHORjcnl5saRatQzlbDhhPUaTUqFBXlTDtvaTiC40ixMod8Q46HnLDqPxH4EHcEE63wnSUVutkFRNylmQeGTgEJjrvsBjGSca+VrLfRY7gIUqQ1A+8Tc/MYUyeVXIztjuM8uT2LKdmtnE814pYoJZ9kCrjpzYHl5sbdMY7dx1yVT7nwh4htlS/WktX0gXNKynonpypjlopSGGcFfEkA679up1ndimSC9STMhkWKDJA75ZQBn8dWfiEF6S0whsg20jb3kl/uNd22xwU0VWcc0woaiQtkgDkjPLj/uKb620wVQeYFcckziWunuEqiTzNjmSGP4UGOp/DudOftKgo6ZJ6urC+DDMDynfmMoUAL8RyEPTt6DJELiC5U3Dx+oW9/ErAgVlGVKEAAl+69O/m/y7Nql1cLeM1VVSM/l2BPw/a8o+eimKhAq/3gyIxOX/ALSBfOIau6zyrztFTgNhOhI3O+Om++Onfc76BWunqaqRIqdC56bDp8tSrXSTTyAhDyMOUDG5z/PWocB2qgt1mpqgoi1E6jDEbkn00VYy0kBROYa0EGAY+EpKKjeSqC+M9LNKydwFj2z78xGrdZqcW20owdYwvOeUEK2ATk7kbDqScAdyNBOMb5B9cqoZBkoqwYQ/CRKrt6Z2UDt11XHram51LtIWOcEL945zv/vbtjfIrb7G+JZNiGROK+LKyG4straOFPGeVXC5wSqrkcwyGHLseuT2IB179FVlqr9dhhwxFK7SyyNnrMDn3PXQW82+onr6eCGneWd5CihVJy3N0A761D6DLJcbffamkeFTUJSLzLzZC8zlt8fLtrlti0uNvc1FfmVEHqS+OOD6W2cOJUwO0kiyjxWYfECD2/311lnEFlCc9RC/hMjLLE4G6bHO/wAwOvrr6F46MENinpK2QPNIeWNyMYbIPKvqfYdM5ONZLLF40WGG28TAjbRtamyls8iBrqVqtC55g3g/iL9r0v7MrsR3BUHh8zbSDtuex6D0Ox7aOR0YrrdyyAieFShBGCMHOqTdLE4pDUUpZKikY8kgHw79PcYz8xq4cAcWCt5qG4Q8l0iABXP+Ljp179gfkDk4JH0+rOnPlMcj2M5rfDk1Wbk79xOLTHPFXSQTKVLIwDnbO3r+W+rtw9eKSoelpLwrSr4rU7SCMnyyLg9O4IBI9sjrqvTTQyXOCSPlCOpBXG4KncfloHMzQyvS1HVTygnbOPU/11prNJ5y+YsB0Ws8k+W546hni+2y/WDWRh+Zv8RWGcEDf8Nu+mIa2Wilkp5iz0dVTr4kQPUlMBh25th7EHHpq1cNV1LXUFPaalMSSRERNgnnJDLgd857d9sdwQvGNqeO22mpVcl6MRuMZB5WZB+ij89K62NbFTG7oHU4kW4UNLe6+muNIQA6RqxhAYmTlAxg9ywJ3x105xHDSXXhyWjmRIrvSSL4LZCl2BOUyerEMfc+GPXTXCV4itKSyvB4sPOviLjdRv5gfUH8+nvorfrIldAa+3zRSzRl18NDk4Q7Y268rLjI6g7aLfbcBkwNFNBLCZXcrpXQXGlrBSQBlhWnlVIwPrKphcOOhcADfqe+Tvq42a3x8WzU0loiM08kYXHOBjlG4fJG4GNz2B2yNFqfh62cRQCqaTwKhlSafbPMAcOwXIyeUuSM9Y99m1C4qs9x+jDjaC58Pu81NJD47ocN4gAxIeUYHTcgYyCMbjOlN7lGKLwY4qK3oCZY+KOAXsfCf7UklSWeKVA6IMIqNsdzud+UdhoBwnwjdayKseN4oUoIJKkmV+UlVAIA9zlevrrUjxRwrxL9HNTXS1uXqqdo/Ddt4pcZAA2HXBHcj8dZRxi8kz00kc8hpq+ijkK82xdSUdfbzqTj3GsdHZYyMjdzK+sKwPtLZaeOOHbXRUVVYaKUVlKgNUZD5pCygMc4IAB6Dr12HXQDiziGbjd5LjVU0FPUUhWPCcxzGQSM5JJOQ/XtqvcPUZasWIgCOZGhJIIA5hjb5HBz7auvA3CdSsMtXUxqlPLGw5XIyT3267EEb46nRKmusZ951XYgqvUA2C0XKwRNd6iinn4c5w1YEA5oN8GRR0K+o3A6n232z0dtuFqWktUcctNVRAh03DKw2YnudQOGY6qaywU0w/w18IsQG50xt7ZKkZz6kaIcPWuh4DpGqqa4KloknX/hp2wKJnOBhv8AplsDfpkemsPMYsTC61DDmFaO1TUNBT/Xz5oxyBm6jtj57DUl+MbNaaXwo38eX7Sqen4/066qP0k8Zy1lAKWOF6ZQ5SZTswbG2fQEf7OsyavYE87YUnA9PkPXRlNBsGScCD26kUvtrlg+kfiZTcDcYo2Fvq2JmjTJ8Nxt4ij1wdx3Hy1W46kyzrGp8eOZcHlOQyMOuenTcalRU09yoKyFo3UcviwuTg86+nplS2mbbCLBKjrzSWWfHnK70rN0PtGSdx9kn00RUBTx7TBybufeEbFbjTzGWocyPkq2DgAZI13XWyeyV812pYHe2VD81whjXJiYbGdB/wDbAdRv66uds4fqWmicQl0lXZsbZHf5YI/LVkoxQWeXxq1klXqQegIGCPfbH5HVLdR8dzSqk9N1IPDdlp5aFaqTl+qcgcOhyHB3BB9D+uqn9Il+pJKqhl4eZaa4Wxy0dUyAxmNlHNGcblSPiU9CAeoGmuN+JIbZcTSWOrmprLVEhFTyiCRuq47IxP4E++q0+aqQs48+TzKei77kn5/r6nReiqOpy7nkQfV3HTkLWOJrXBfEdJxNZhWwL4M8beFVUxOWglHVT6juG6EEHRrWLcMUd9t16a7WWFp5kTFVATyrWRD7O+wI6oTvknsTrX7LcKS72uG40MviU8wypIwykHBVh9lgcgg9CDrbcMlcwup96AyVpaWlrsvFpaWlqSRaWlpakkWlpaWpJFpaWlqSRaWlpakkWlpaWpJFpaWlqSRai3Shir6UwyDDDdG+6dSwMnXQGBqysVORJtDDBmbVEElHVPBKpGDhvY+o0xUQpLEY5VDK6kMCNiPQ6vPEdqWug8WMDx4xsPvjfbVLAwxR859Dp1TcL05794ttqNTSl2+KHhe51NHW1Ph2ypPiUjSYCq+fMmezYwcdCBnrkE8KZarxYxUjkRsMqkFvx9P9NSbxbYLjQSUk6c0bjbGzIw6MPQj/AHtnQPh+uqqdnoa4P4sCqkVQy4WYZIwTgb7DGdzvuSDoDUVeX31Can3DiQuJeH1rhHG8aGsgXko6hzjmB38Fm9CclT2OemTqhr9cnneORHpvAJSRX8rIQcYP3d/x1ssZp7jTMow655XXup9D/P8AXVU424cnusRlpWYXSBc4H/1yIDGR/wCqoxnuRj5DultFZwev4gus05dSy9ykiohpE5IEMkoGcAfrg9Pmd/bTcilQK6tqzAqMHRw5BDDoVPVmB79tD57rSUQ+r0MS1VSOuB+7U+pJ6nUJKesuRatr5udUPmaQkRpt0+fsN9MSdwO3n7nqLErK43foB3L01yfju0VK2iQwcU00e+VCG5QqOqntIO4299scucJbxDmovM7RnP8AhuMyMe+EO4+bYHoDqWLkaWdTZAwniYMtYwwUYdCg7fz3/DVxrKCk49pHu1HBFHxTSRhq2kQYWtUbeNGPvdMjr0HplXf4cbXBydnzG1WtCIRgb/iUh6ueojaCkj+pUbY5gCS8uO7Hq38vQa8jghSJowmebqT1OumBBIIIxsQdeAEjPTXqdH4bRplwonm9Vr772yxxLzZLpTcX0EHDXElQkN2hXktV1f8A5nXEMp7+x79t8hqtdLZWWq4zUFwhMNTEcOh/Qg9weoOoixh1MbjKnV+sdfS8V0EHD3EdSqXOIclsuj9XP/Rl9c9j3zt5s82LbtC2V5Q/tLbl1oweHH7yjJHntqRBECwJ2xolX2qqtdfLRV0BhnhOHU/oR6g9jrlYxjqdGeaHXKxb5TK2Gkjhu7VNhqZmp4lrKGp2raBz+7nXuw7B8d+/Q6m32x0v7OW/8PytVWeRsMCP3lK/dJB1HzP9iRkaAHYZPbA09DfzwjWtXidA0y8lTQsOZapN9nX7J9D19iNKtURpj5qHHyPmONJu1S+U4z8H4kFUklHLGuSBk+gHqT2Gh1xvNvtp5FIrKnoFU+RT/X+Xz0c40oVvVhiv/B9ciWSQj65SttLRv/EBuw9D29cdKzb6Ckt8BqHYRnGTUTbuf8q9vn+uk2t8adxsqGIy0vhFVZ3WncZDlp7nd51mukzxRNgRwKPMR6BR00att3ThNGCeH9WmXkmt/MWWoHcP79ffsfQi2uc9SzQ2eExq2Q9TJ8Teu/f5DA/np+2WNQTUzsZJB8U0p2X+3y66F03h1+o9bnA+TCr9fVR6RyfgQ7fbNBfrH+3ODKqRbWm9dQ4/f0b+46lffr7kdA1ttVNSRB2Hh8wyNss49QP6nb31KpbpNYbktfZJWS4IOUtvyyLndWTuu32vwAOjs9FQcY001fY4GorrGOeutOfj/wDUi+8Pb+vVhp6xo2xjv3gV7/jEyp6/0wBLWFQ0dKmOzEHf5Fv6D9dNRUTzedwrcv4In57D5nUhfApYis+Mqccg2APoT/Qfppl6ipqRyxqI0HTy4A/yr/U76aoQT6eT8xO6n/XwPiNVsNIiqXBaVSDG4yCrDoRjBJ/L8dGKO901/gS18Xv9UrOUJS3kDr6JPjt/FofT0QRGqJHWNPtzSHb8+/4akUlLLXSLBbqdz4hAWV4+Zm/yJ/XS7xBqa/UW9f2jTw1brPSF9H3nNytElgqTTXMCDoYyg5vGB6FMdQf667tlFdrxUCjtVJJAr/EI95WH8TfZGr3aOFL/AEXDxgusTXO19Upy3NVU3XLxnGO/wf8Axq08OV1DR22npqCjhYTnkhlgACTN6MTur7bqfwzpNd4pZeu3PXtHWm8MqobOOT7wDwp9GtDb4xU3d0lceZolbyg/xN31b6ecMgpbNSoY028Tl5Il+X3tSY7ZJUnxLlL4wztCm0a/P10SwscfKqgKuwAGw0qe7Pf/AFGi1heoBuHC1BdID+12kqZvsyglTEexTHw49dVerS58NV/1ipqmZCABclTm5gOi1KD4gPvjce3Q6CjzNkyBQM7YPbXFRCrxlCgKMOh0KSwO5f7e0uVBkbh69U9xZaWZRT1hXmEfPzLKv342+2v6juBow9OeUhds9R66odRw1NTOyW6PxKUnxRRluXlcfaibPkcdRuB8t9GLDxLLSp4V4Z5qZTy/XCnLJCfSZcbf5gB2JAznQep0teoU47+PedSxqzgyw+GU8uTnvpaIoIpY1kRldGAKsCCCD3B0tIT4a4PBhQsEq0agZPU+uvc4OAM50ly/QAAd9eg8oONh3Prr6nEYGJ4VJO+/8hpE9hudLOVwvlU/r8tdBMLuBjrjXMzs4Az5s7+uP5a8yd1QAnO+uwrPsNgOp10FAXAJCevrqpMg5nCIATy+d+50iQMhRknqdegdgOvTXSAdwMdz66rmWAnAQnPTPfXuMDG+dd4J+H89IjbA69tRTIRmc4zkdfw6695AN+v9ddKNjnr3z/XSI3w3XXZzE56+bPXprzGxztr05LY304F5Rt2/TUBzJiN8mDnH4aSDDE4zkacIydttcEM2yk799TMgGZ4TsVA836DXCrjOdOheUba4IOc4212QDM5wev8AP/e2vVHKNjk+uuxsMDv1J14FwdumpIROcbEDXgX312R11wQc6kmJz66W/bGvcb6QU41JyeY9tL310oxuQM689e2rDqSc8p31wVwTjTg6YwMaQHprokjXJnqDptsHI3wP10+2+RnGuAuck/hq+6VxGOQklj0H6ayX6TOMRcZJLPbJM0KNieVT/jsD0H8I/X8tWP6XrzcaKhS201PLDDVJmSpxgMv3FP8AP8vXWREdQRpv4fpQ39Rok8Q1pB8tP1jLpj94pwfUf721PoLnv4VV5W6Bu346hYwcqT+OuWVXXBG46f6adqxWJ2RbBhpZUccueYAepOuRKZNs4X09dV2Grlp8KxLwg6KxVUboDEQxP6fPWwYMIBZpSnMJLMAvL+GNPQTvESyHEp25vuj20OhODzMdz3074oQdflrNlz3BimDxJDMFHMTtrwBnPM2y9hppAzHLdew9NTKZR1JAA6kjYf79NULYlCMSZRUpLDm5ebr5vhUep9tXW2RqtrjKtzrjPNjruf021TIZoHieNpGiwMoOXJkb+LH/AMD8daBYaVv2DAzDJ8BWx2Gcn+uletsIAH3jLw+seph8SpwoZqyaXmVAjczySDCQLuAx9WPYflv0YrbvECsFDGVp0bmZ5FBknbfzMew32UbD3OSY13uMks5hRFigjckRgZyx6s3qT+g2GhbOSxJ6aJSgMMvBG1JQ/wBM/rLPQ1kdRHlSAR8S53GpmRy76paTPA3io5T0Pf8ALR2z3WOsHhuRHN90/a9xoHU6UpyvU9L4f4mLgFs4aE3Az/FqNVQR1MRinXmH8tS+YMD2OmyN8jQSkqeI1+qULiCwy0chmgHMh6Ed/n76F0VdJST5jYjHxR/21p7IskbRuiujDBB76pPFHDzRM1TTAsmfxHz020+rDjZZALtKVO9ITtlxiq4Q8bebuDqcrK22+qBRSTUsvMMrIDuPXVss9yjq05D5ZB1GpbpyvI6nab952nuS7hQwVlM0M6cy9j3HuPfWf8QWR6OVgQxRjlGG3yx6HWkg7YOdMV8MM9O8U0YZSN86EbaylX5ENTKnK9zObRdpaeT6tVnnD7BjsHO3XsG2HXY4GdwCCrxIY/HgOU3yO4xjP8xnuMjPVSwjiG0vBM8qAtA2wLDYj0P99R7TcpaN8SsxjwAXY7r6Bv6N1GT2JB87vfSvuTlYwsqTV17LO4acY1w3TTuFlUyQ7juncfL9du+CR0IVpiMHcaf6fUpqEys8lqtHZp3ww4kWqflQgnGqncZ/HqmIOQNtHbzPyQuQd+gGq9SwtPVJAucu2CfT10J4hYVXYPeN/C6c+ow/w9F9Vts9c48zDIPsNh+ugKF6m4PISSS2Bo5xRULSUMVHFlcAbfy1D4dpg0yMwwqDmYkbZ0rUAtg9CNrn2px2ZY6CIQ0yRgdBpi43CKmRgMMxOB/pqPX3Rgfq9P5i3p3+ftqFDTO8heTLynv/AG1s2oe/+nT18wGvSpV/Vv5PxOPDmq5eecnlzsmevz0RpaPLjnGAOi6kUVNyKCw5j6+mpsaZJ5d/U6M02kFYwvcH1GsLctwI2sKjZVGdEbSYIXJnjHMdhJ932+Wm0i9NtOCIsTvo46RGrKvFDeJur5TqSLrBHT08lScBY0LsfYAnWfUk8cscjFD48j8zOTnK7nHtq08V3RYbHPQR4JkAjyD8Pc798/11U7PFyJzAE8u4B15/8M+mYgdT0ulvTVIHIwZNrGMduc9CzYx/v5ab4ep3qKnEYI8NOfOOn+zjXl48phgycKMn56t/0b2WWpoqqs8I+HJIsCtjO/xN88eX89ZNaEyYVYMjE7s9ZJDNyMAy584J2I1ZrPbZbpP/APR0TztkgoFyQff299EaThiOytS3a5KogRZJVhYbtyoSmR6GQoPx1zbOI1tlJFT2eARNjlZn2ViAMlsbtudl6fPpplp9eUAWsZnl9Z4aLWLMcSTXQRWimoo6lh9ZWaoLqBtsUQYP2js/T9NQuJL69zDioUcmcIpx6dPQbZ2H450CvNYZbi3h5Z2dmOMDJOPTp06avXAVtt//AIcqKqtt8VbUzSmGMSrlY0IH5Z36b7dRoC/1brX5MY6Rdu2tegJkF6sUjK09EvNF9pRv4fy9tc8O3iqsNQI5mZqVCAsnLnws52PqhP4jqO4OnvZDC1VJGQtLEXCM52OM4GfUnbQ/iaa1UFHcWorXFXGp/dlGGAirGqBiR22zhdz6r0OVyq1aqPqjOi4o5J6lu4OvlFdK+iluEyLHSwCNBkb45mUZzjcnIbIUgE51zxtxQa+pjjtnKkY/dmSNcEgOGyp69VHm2J3wANYdw7e6mx1CLMxNI7EKcE+Hvk7dSmdyOudxgjWmUTpdYoTSyRoCBzb5wDk5BHUHff2PTDBQwhRtrjmaXVBhvTqeQL++5YlMsznOF3399FVtPjVkiScs0zI2FzhY8r1OrNa+EhDYKioWd4Knw2ZQQAz4Bxv230LkulLZa+uFwj5TTqII0JxkKirzdOpIJwMn074OrCsOTyPaLbS/AWQZKGkslNDJ4bGSITStM4wMpBIyr+YGg/FXERhoqG3Wao8GURqtS0bZbHLjlyDgdTsNx3IO2hHFfEkl5V+RZI4o18meu5wdgcAe2/uT2AQsWlRACSTsBreustYC8ra4WshIWeImlXl3PinBPfVu4IsFTX1apGmAMF2bov8AmP8ATroXY6CZ4EMsZP75QcdRlSf5Kda/w3mkowIaXyRxqwVdgCdsn++h9XbglROaVNxBMptFZ4o+IKSXEhSKaeUPy/EqsqLsPUh9tSOH+L5OFvpEnk+qP4k0CeQv0Vck5A3yQRtnA750Nq/pGobBFcFSjkmu0cApaUHAjjbxZWZz3PxKcfnjWe8KVNVXXuiqayd5ZpBOXY7sx3OgTSSxZ+oenFZCzT/pA4sl4pvMlcYvA2CxxKdlA7H+egbIfGqlAJAbnAHvvqZR2CquEvNBHyJtzMTtj3P9BpQSJTXWoglHmC8gb3Xy/wBNek0WpTaKwOJ5nW6N95tJkWkljppaoNEJFki5uQ9DjGf0zqmcR2otdY6mgmWJinNHIFHlcHBVvUH07jVzVlElG3IV5SI3OeudjoXWRNFJIUO6llb8iCP56A1ujCncBxDfDvEM+hjzGuHL695V0PLBeaf/ABI2/wCaRnf3b0Pfod9yfrKUXGnzGCZXjDY7kkf/ADqmcQWKo/aa1lsbkqiwaFx0YsM8p9jnVj+j7iuluLc1ZTkVqKqOp+IEHIOPtb537jPfVKNWaj5b9e021mgW8ebX37j/AHj5Hg2+hdlcEHyk7ejD5dcg6sFkrhemNqrGk8viNC7PzEFmBI5f7deoGpdwt1FVWg4qYgkbtHCEPNtkmPf3RgP+w+mNVa3UlVBdHppoyMK682DsCNtx0wcHWeqoFo3r3MdNeaiK36kutstVRXGvpDGxDReIpQZVgTkEHpjONN8FXiejvKxzP+65jzoRkAhcfPoMbfkdWazX2MGSkuUYlnmppIBM8qqPOpKtknGc/gw3G+RoDfbOluqlubrJiRFmi5MBTk4OT887e+l1VpHBh9lYblZZuI7WtLSC4WV38KObxAUwR4Mq+IMH2KuuR2xjrqTxJxJw1XcI0dvdPFq4ZBnwAVZhuj49mXPoRttkY1WeG+KKi3EWyYtLTD92FUZwVkDjr0HxfgfQ40/xhwvHTJUV1ESsAKzpy4AEbkqwK5GOV1A7Y5hnWj1JcMN2PeZK7VNlP1EzV/rfCN/q4Jf+IofFxMEGAy9VlQY2yCG6d/mDZK6sNTaYBB/xEELNPSTnGDE+CyHHUggE/jjIwS7e7ZVEUc9wSSKnYBBLynJjBxkZxkLnG2BjlHbXd4tEPBkomoXers8y/wDHU5ILQf8ArLjYJvuOg+R2ELhHA+YwGL0+8uXANstMVBFdat0qHk3QOPKhBxjHcgj5b9NX63WyfwZZRE31OV/EQEYOJPMR8s5/PVE+jmlp5LZNSLUK8anx6d/+oucA4G+/QgbgqR11Y7h9KH1fh2ps1HFDPUUqlAwzy8oOAxIPX1AO2dyOmsFrLORO1YC+riWPibi+yWmxz0lBTzCoWUhObqGJJyT2GeYbb6yO7Xmrujc1Uyzxk/4UgyhGd15fQ9+/udD6q7S19mSoqGIlkch/KAMr02H8HIfx0zboZ6whcGKE7lj1YaZV1op9XvBrb2JwPaS47kKCrbh6umd6GpiVrTUzHdRnKRSHuV8y5/DtsYtlsTyz1C+JKwBwR09teVPD0FZw4RJTF4aZsOSesT4BwexVsMCO+pPBRqaK8U/DF8YGaTy2+sfZZwPsN6SDPTvt6jVw/ktg9TpTzgD7yy2O2SzzoVQkdCB1IOx1ZuHeFEpbdKbnErwNK68jLswYDKkdxnIx30UtVZZ+HMSVMgaXJXI3OR1AH+/fQX6R+MIqy2xigaRaeRykmNstjOCfTB1hbcbDhYTXWlabmPMKU/FvD1ltS2RZAqp+6pWY8yrnOELe3bfpgddZvV3epa7Sx1MjAl+Rw/XIJH4d/wA9Aa7lrElhlUOjDDA7BR8+3+8a94dgqqi7pba+XFSw5YahzymoVR0J7OB1HUjB9dXSsUHL8zJ7TqAMe0kVVGKiomo5o+eCYFCCMkjs3yH8iR31O4Vs88FwpKC780UcrFaWdtxKV/5THu6gYUn4gPUHV5tFmp4KhpXAeRADkjYj1/Q6KVFqhuKSU80LNTVOCfvB13Dr6Hbr121VtU27KcTSvTAjDSZS2+OKmENLAMgbD+pOhjWmqsVdUXmlDPSznnuVOq9SBjx0A+0AAGH2lGeo3vPDFP4VAsc5Ek6bPJj/ABPRj76h8X3GK3U7SqfPg4VepPtqqWsW3DuG+Sqpz1BsbxyxLJDIkkbgMjo2QyncEEdR769IxrNeFeJls94mo6xo4rRUzF0APlopGbHU/wDLZjueisfQ7aXynOnCEkc9wQMrDic6WvSNeatJFpaWveU6kk80tekY0l66kk816BnXWB6aWBqTuJzynS5TrrS1J3E55TrrS0tSdnhGkRtjXulqSTxRg690tLUki1WuKrT8VfTofWRR6/e/vqy531VON+O7HwzGYKiT63Wuvko4vM7fP0Hz1eu40tuEo9YdSDAHMOV2dlVUPnY7Be+/tjVVvgF9aNrZDlY2/wD2gw8mM/8ALHV+g32GQNzjQCj4oulfxO81dRxS2mojMc9Cih1jjByGyepB3321pMMpqYlig8OUNGrpUdUdD0YAdT7dB+Wt9VqGZduMAwahFB4MrEVK9kliroah5kkPJULK45nOevb1/D5E4sskMdbSJNA+5w8TpsykdCPQj+41H8CK3uZJT4pk8pJ8zP7ADt7DbUemeW1yjMTLQztlBzcxQ46bd9j8wPUbi1Pt4M3Ye8ov0hcMRKKriKhoPEqo/PcKOLyhyf8AnqBvy/eA3B39Sc5npbhcsS1TYRB5KdNgB8h019IVdP4hWrpGCTx+ZWAyCDjOR3BHX1HuBrOOKeH4aOVrvbIOSjdgKmAb/VZD/wDcHsfw9NN9FYm8JbyPb4ifxBHRC9Q/P5mXqqqvKi8qjtqTbqyqt9dDX0M7QVUDc0ci9j/UEbEdxoxfrWJFNbSjfGZkA/8AshoJGg16ddjptPU80HZG3A8y83ShpeNbXNxDZ6dIb1TgNdKBB/if+tGO+e/49x5qdFECoONtTLFXVtpuENwt85hqoTmNh0PqpHdT3H9hq3Xy3UfEVsl4lsUIhnjObpQL1iY5PiIO6nc7fPscLxa2lby35Q9H4+0NfbqkLp9Q7H+8paw4PTfUhIVZORwGUjcHXajBAOno4nk5jGBhfiYnCr8z0GiWcbfV1F9aHd6e5abRcqbiOjg4f4gqFjuKDkttyk+36Qynv7Hv885A3OhmtE8sN2ZKIwnDmQ9fdfvA+o299V27Xyhpc0tJGLhUseX4coD6Ad/x/Lvqx0U6cZ2Km4f4xQRXqIkW2uV/Mw7RTH39f5H4vM2+JLp3KUHIP7T1FOgN6h9SMH+ZWKziOeokal4epnJ6NUMPNj1z0Uf730xbrGjSNUVbCsmHxM5xEnsfvH2/IamXYR8NTPbrnTNHUx9KKJSB7Fm+1nrt19e2hrxXK8kfWWNNTY8lPH5dvfHTSxK9Tr355/iHtbRo0/8AiP3MJUnFMlluyVFlBrawELICMRFO6EdMY/Ee2i964bt3E9O3Elgjm/d4+v2l2y9K/dlHdD+XptkAfTWqlt9P5lEQHVBgN+Pp+OlRXWuo7lDXWMrTTRfC+PLIvdW7uD+XcaaJ4b5IDL6mH9oubxEWZVhtU/3niCipI+ZuSRseVVPlHtkfF+G3vqPJLVVRHWOMbL0BA9h0XVrrrXRcUUz3yy0pprkh/wDpG3gEkeskYHVSfT19etbNdDFmOlRjIPtDHMP/AMX+fvpjTetg55PxFl9D1nA4X5+YoqSKBD43kwM8v2j889Pmf11HNTMKiOe1uaaeFg0U8ZwVI/i6t8untp2KkmqnBlHNk7RoDj8u+pixRRP4IRqipxtDFvj/ADHoBqal6lT+uePic0iWF/8A8cZ+8LU0dJxq5Wenht/FES7kDlhrx6g/Zf2/2AxhkpamSiFHK1bG3LIJlKpGffPU6P8AD/BN74hdJHHhU6MCrISkcZB2OerH5a0P6jPZK6jkvMlNWzqBFT3CVAOc/ck9Dts/59TnzNnijVg1VnAPXzPTp4bWxFtgyZTOGPo6ud1dK27yNFHkENKuD/2J2+Z1pVtttm4eUQUcBepcYOPPK/zPYfpqZTz1V1aSOM/UUiPLIGIMv5dAPQ99EKOipqJT4SAM3xOxyzfM6T3Xtk7u43rrUD0weaKsrcmtf6vAf+RG3mb/ADN/QaF3fhmGOOSazpDDIwHjUzD9zUgdmHZvRhvq0cwbYAkeuuZIjnfJOhC7ZyDiaEDGDKpaLzJCrQVfi+HFgSCTean/AM330/jH4+urHCFdAQwkVxkMpyCPUHTVba4qxlkIMc8f+HMmzL/cH0OuKCz3ehp3rKKAVFMrHx6ePoD95fuE9cdD7ddXVhZx038zPlO+pMWEkkHfUhKYlCCOun7Q0NfDzQnKg4I6Mp7qR1B9jqz2+wmenIAAzuDjVMnqXHPUpMlEx3AIYHKnHQ66ntlPcFFSFEVUo5GcDrj7LD7Q/lnIIO+rfcrM1OvTLe2qJxDxJbrCslR40ciqSruz8sSkdiwzzEfdUE+2qON3XcmAeDE/CV2oVUcO3ialppPM8EdP4yRt3wORuXPpt8u5Wsh4h+lqvqq9jbqWtqYV25xM1Mn/AGohzj3Ykn26aWiVr1BGTXn9JgXQHG+aiW5Rv+A14oLnLAH+EdPx10q5Gd/QsR/vGvSeTCKMn016MmDAZiwF82eZvXSVPLzPsvYd9dRpg5fzP2HpronzZzlv5amZMTwjG7A47L31wctuxwB+mnVDDPN1I2Hc6RGCMjJ7D01WWEb5fvZG3466Kltjt7a9ALEk9fn010qljy527nGuZkiGc4HXXgXrjsev9tOYUDAzv37nXJyDkdddknIAB6YPp6a8VCx7bacVMgHtrvlAyBsPXUkjYGAQM/PSVQNvTvrsKBt0Hr6685C2w2A1zOJJxgE4A216FAG3567AUbDc/wA9eBTnHf8ATXMyRorzNgZwNIjGcfjp0jA5QPmdeBR22x013dO4xGyNumuegPtpzlwcDIA6++myGYnIAHtruZycnfftjXmMjbfXarvjGddcoC7HA1JI1jffS7nXfL6768wNdBlSJwc9tcE4OMZOnMHp30lTfJ1acnAUnpr1vKN9dnG+MA6bY8xwNxqwMk4xk+2kpQynm6L29TqDdrilGBGuDIw2HoPU6GR3gIpLKTnqQeuiqtM7jdiK9brlrPlg8w1ehS19HJTVkSSxOMFW3Hz1jXGHB7UjPVWtZJabOSh3ZB/Ua0ueqaZc4Kjrynr+OoVRKAMk5JOwHUnR+m3U9RLbYH7mIlOuRjGx00yE9taNxHw5BXF5oOSnqScnlHlb5/31Ra+kmo6gwTxlHH5H5HTau0P+cGHHUh9QFb88fz02qtC/PESPb108y++uN06bj01sDiXDZkymr1kGCCr/AHdTIO5fdv5aDSxqw51PT8xp2nrnQ8kwP+bV1OTzMLNODysNxyYY7/jqR44+EbnsuhST7YTzMe/Yak055dzgnuT31CuYE9WO4Xo1iijM9QxCnoB8b+y+g9T+G+tXq6ultPC3iTFIgII0UAfa5NlA7nWM+M8sheRix2H+miF/vlZeawz1bgKu0US/DGvoP0376A1Gja1lyeBCtNqFpRhjkyK8pZyx6k50w8p5sKdctIACDudcKNyx/AaNOBwIAE9zPTvknf8AHTkB5fhbkb7w664RGbflONeh1XO2TqhAIxLgkHiWa1XAywjx35WB5VdtufRRTkbnfVBeRiQOY4HTRqyXV0/cVIZkHRxuV+ftpbqNHgbknoNB4l0lv95ZCDjIxps+bIYAjS5sqCpyrAEHsR210AcdNLY9ByJWuIOHxMrT03Ub8oG4+Xtqpgy08+JMxyAjlfsfnrU1X30G4hsUdZEZYVAmG+OnMf76Y6bW7fQ/UCv0uRvTuCbVdRIRFOOWQamVsw5eUEEnr7DVRnimpJuSbIwSAxG49v8ATXkcrzVSzRy+FUqMJIPhdR9lvUfy1l4giqvoPc10dhY4YdSxSRCRWSQBgdiD0OqrfLKYGeopwTGPTcr7H1GrHbq5KomGRfBqUHniP8we41JeENknv00kUY4aMGb3EzqlqpbfkkEQD4hjPIM+ndcgbdsD00b5kq4PFhYFyvNschgT1z89s+pwcHBZ++WZDG09L5XXcoP5j+2qt9Ykt0viAEqWyyj1+8PQ47d840M1b6Y+ZSeJplNQvl29yPenf60Y2BXw+uR31L4TplMktbIPKgwM/mf7fjpu81dLWUiypguSFQqP0P8Abt2yOkurkW22NKcbO+Ad/fJP89VOr8472m1WmFSbFgmvZ7hc3dseGG3J7dcakLKWUwUwAXPnc9P9f99dQFkaoYIPKnTHTP8AYaO0VP5OQKAg1Wih9QcnhZS+1afzjdDS8o8mSTuWPc+uidPCIxkn/XXUEYC8o2GnvD269OmnlNaou1Yg1GoZm3GOwIWXvy/z1Jij8uAMa9p4woAx01IneGkziQPtsR3+WmKKqLEN97WtgTpIEWNmeVUZeoOhlXW8wMcJKg7c3c68qZ3nbBON9kGpNDbDnnmG56DQtuox7wjS6JmOWlQ4gLGSOFugHOdvX/417b1yqry4/wBN/wCh/PTd7m+s3epdTlA3KvyG39NSqIBGZmOAiknf0yT/ACOlGocscz12lr8tQJK4foFuvFDeMniQQIWkB6YAx/PGth4FqYqThe3Sw06vNKkk+MbBpZOp+Sqmsaslyemo6qipUZqquPhlgcDG4xtuSSemw6demt5ttvSjjp6YlmSniSPc52VQN/TppNeT0eoQ5ka4rJV5etlaQktzZO2NtgNVe8W+eWojFFHyR52/hJx+mw1dZ6XxZlJUhcEgD/frtqTR0alqggDmWmkCrjclx4YAHc5cHHtqU2eWxaDOgZeZROFLEk1OtZXPyRc3lGfi9Pl/PV/jr6Kkt0EL+HDBFJPI0ZUrzcmEXH3tyx274yRqBxK1LR0vhWunaSaEcqkEcqDcE5B9R0X8T9nWctXTfXZI2G5djkD/AC9Pby/z0fVYbBkxdcpXhZbbvxM1wcwUdOYok5265Lkjv6D2H4k9dVllmeVuXDknOw2X/fro1aKKWpgYRxlC8bvk7ghRkn33wPx1ceFuEPDphPUr1OCmcFt8Y9tYWWLW8OpXK/MxTiywPyJPTKSUyZFUep3I/PUmG3XjhC12+8S80lrq1UnHxwO2G2XbKnAJA9AdiAdaTx1a6elvdb9Th8OlhndfDH2U8Ujv2wB+eqXxxWVt1oXhpj4dPHCqinU9QMAAn27LsO+M7nrY1I4mtVjVtzL9YuMmrbGtPlJZVUNFMGyeT2+8NsZ27ggEEATx0Yq+yS1tRGBUREEZ6DmYA49vbWScPXWqstQrDnel58uq7mM53Zfy3HQ+xwRp8lRFf7BimZZGblk8m4dQw3H47eoOx3xnCkmuwBppqKQ671lLjQyU87jIATAOevf+mjdgtygxOELEqpLHtnThoeeNYETBJUAY6ZYD9c4/HWpwcIU9q4Uhu11cUkiEDwi2OdMDlI223zvuT0AJ0zuvFdgJis1lkOJzwVbElCBjHyGrp1aRjhYx4E2cn59tWLiniq3Uqz2egi56hPK2DysuPvEfAP4fiPfl6nJ7vxJURVYltMklFH4gIaMlGUqrLthjjIY75z7jUK0mpasEUAZpKj91gbkltDVaU335c8St2p8in0SpcTkyXmWU487BjhcZyP5as30N2+GuvlKZcusQmOAeuQdvloHxDb5ZL3NTHyCIgPk9Mbf6a03/AO9/4Xq6y+GKBHjVI3kJK4JUnAIz299U1zDaQPmMdKCUH5TRYIo4wkCCNDjyxrtrNuKKZ04gmkYKsgYllHTqT/XW0cQWN7Fb3qpYuRB1dt9/fufkNY7e6h6usFW+eaRmBzj2xrDSWlWyJjemfS0AsS6McElXzru9U0i1AqYkykq8zDuzYyf66fq4WzN4XUrojYvCrqKlgbaZvhDH498EfP0+enY1WfS8QXaHBLpB9mrKaCGCepg8SJwE5h8UbRtlT77Hcf20H4n4bhjtsFZb6+FK6iqZ4IuQFuaJmMkYbYEqQWXPqB00VWkqVoKqAp5oZ+YqRjIGxHz3B/DXFpnk/akZZ3aN3AbYZG2B/lPT2P56A1el53r0YfoNeeEfv+ZzwDxEaq4pFUYo6yJwtVFKmWzg4PY+p/iHuDrWDZaOtrqSvovDKzkwl1wQS0ZwQfXKnf8ATOwzrjrhqnutvjvVkeKG7QGGJZGJRZUHMHVx1GDyZHVdt8EEscH8V3OngqaCQS0VxhIM9LMhEgcEPttnJCgnGzLkjfbQVGoY4RjzD7tOhBsQfnOOKFSku0lKEACfu27p1JO3p7eurDRXGCvsMdpro4/NEHhkz1YdQPRsj8fn1KXm00nF9PPcqBY2ldmdSmcbnIU5HYHH4arlda6iksVJLMBuSTldxliuM9t1PX1HfWl9KlSR3BKLWBwevYyFxVaGguSz0Sc8UsUbkKcgFkGQD7Hb8NWvhC9xO0FJcR4ySArGWbZRIvKw+Suikf8AxiJwwqXG1VdsmliMqqrxDl3I3222Y9Pnn120OuVPNb7bS1rR4MT5AAHKx239CMCNvQ850BvOMHuGEA5YTUuKrb+3OEwJEzLRIrshUl2QqOb8eQg4H2l1TYpaKksUi1dRElfQN4Kq4z4gA5kJXqw2wQAdu2oSfSLJDa47bQ06QRnmSKUuSqLnIjOeoAbHXGwG+N6/xDEJoaerR3lMQFK7FcFkwWjb2HLlf+0aqlJJ56nfNUddwWl9paG9VtLT01VScOzs0rJEv/7OZsK5UA/4JyFKE4wceXC4nGl/ZNxSdmjlpQ3K7p5keJgd07kEZI6dMHBBGmbZQGWthMcEtQsgaKWOJObmjYcr7d9jn0zjfbUbhupbhTiWosXENCam0U1QY1bBYUxJwB7oTjAOx2741AdhJEJTF689yVLRuFlo4mR2ikySG8xIcqSR03yn/tPzOkcLcNK9NDJXBlZFCooPods7emBpu4W1ZLrFdaCCNoK2JUEmMpzKPI4wdxjb3xq31nFnCNNYaSZalnqeQBok80mCuVYjt1HXvnXHsawZEgrUHLe0sPD9rt1TTPQVIWJZUK8u2Tt+uNUP6Y66zy0s1jo4I5OXlkDx+X6vKoyHU9Qw64GOuCcEjVNr+La6qrndKl/DyQgB2xv1Pc/oOwGol0meuigqs87Y8GU4J3UeVvckbf8AboiuhiAzniYtqxjag5jlt4lqbvI0FylP7XijHiPnapjHSRPT3X1ydE6YNWUNwoSCzGITRr35kI/LYnVdj4cr7s6fUElWrjYSQzoDlG9du3rq+cB00cz19BdKf6pxDSIVkh+xIGGBJGftKfbpn8tGZavT7TgU2eod+8f4P4VkqqeCrrSY4CoaNFxzEH0+78+urVeOGqS72NrTTQGMREPE8Oxhddwwb7399OcI0kv7KippVCoMqvUeXmOP0xq7WwUFsiJZwpA69APw7aEZyx5henpUSh8OTVC1UVuvQC3SEDxDuEqIiQFmUH35eZfsnPbWkW+ngSAK4AcHIJ2O2qD9KFbbqumBpW5KymcSU86Y54JN85H3SNiD1H4aq03G1wulKYpyYKym5VqadT3I2kBzujDcHXEUscTY2JVn3lx4u4kehnlgpJPCZDtIDsP76qi8Sx36mqYK2URVdPu5xnlU/aHqn8vw1W+IbhPNbaW4khjloJd9gV3B/IgaqUtdUCujrLczGqhJw7fAynZkYd1I9fnphp9PtO4diAW6nfkN0YYv0jWm4LLPGrwZ/epjmE6EYPzGCQc9PTV+4KvbWquh4ZuVQ0tPJ5bXVO2SwA/wHPdgN0P2l26jfLrdcoqiR0qYTU215CTRynElNJ9pQ3UEZ+RUro3eXpWo6KVJDV0EkSQThQUkQoSEPqrgKNx3wR200sAdQ4gOnt8tyhm47HXhG+qh9H/FD18slhu04e60y88cx2FbBtiUfxAEBx2O/QjFw1mpjRSD1FgemlpaWuy8WNLAGlpakkWlr3B0sH01zMk80tegHXWBqZknIBPTXmuwMaWBrgMk40td4GuCQM52A9ddEk9G+ht+ukVqp4JpZIESWZIv3j8pPNkDl9TnGqVx19Ktqs7y0FmVbncFyGIbEMJ/ib+g1j9wkv8AxpWy19dVfWI4/wDEqpz4dLTZ6BQds+nVj2GhrdUiSwWXL6T/AKU7utdU2S1U72pYnMUs0mDO5/gXsCCCD6EHVa4W4Oudzq0NZHVrNUgSLTp56ucH7bZ2RP4nwPQHWh2jheW5SW2uvEctHXKogS5y0oEs8KjIZVb/AA3ydmYc2MkD00O3taeHl/ZllpGmq5j4jJGTJNOeniOxOT/nYgds9tL9Rq+ts6lZb6upC4M+j622ukV7zBTMMeWiTzxdPtkjMzY9RyjsvfQS7WmS31j/ALJhnNqlLyQVHIDFTOT8IxjKH2yNuueltIWSZWvk6zsf/qcJzEns7bc/ywF9u+rTRTQXCkeBeQsg+EDAx8vTVK7Lgd5lwKW9CzJ6ekiliaRgzT/DIZN2B9PYfLbTbwRtHJTTpzQuMEen+udHeKLS1qrvGp1/cucBfQjfk/qPxHpocAs8YkUggjY6a1MLFDLMHQocGAKcy26rNFUOTGd4pOgIz1/PqOx9iNO1tIRzzpGr8ylJonHllQ9VP9PQ/M6I1VGlZTtTSkqwOY3xko3r/cdxnUO3zSo7UNWvJPEcYzsR2we4PY/1B0XVZkbTMWX3ma8R2c2iZKik8R7ZUMViZh5on7xP6EYOPUD2OqheLZ4X/FUy/uifOo+yfX5a3S5UMTRzB6f6xSzjlqYR1cdivow7Hv07DWb3m1y2WtELkVFFOpelnA8sqdwfcZAI/vp9oNaT6H7/AJnmfEfD9h3p0f2lHhA9c7aM8O3CutVzjr7a5WpTy43IkUndGA6g/odx01GutFBb2+sTTpBSuMgtuw9gO/8AvfQVrnXXBmpbHAaeA+WSof4j+P8AQaL1OprYeWBuJgel0loItJ2ge8vvF1LbHs8/FdopZWp4jivoIiC1LL3zjonfI/QZxnM9ReL4o8Rkt9vHwqoxn5Dqx9/56sfCYqeF2luVLW4eRSlSZz+6nTuhU9R774+WpPE1Ly2eHibg4iqt9Q5SWV2zJQv90gbAZ2BHt2Iz5rW/icivdmek0fkbTYq4PyYBSjoLJSmSd/qqkb85zO/tj7I/X2OoE1bcbopp7fA1FRt1fHnk+Z6n/eNSrXYWqZWqq2U1MyeZnc4RPffYDRaSSkpE5YgJZe2V2/BT1+Z29jrbSeEqh3Xcn4H+8Hv8RPVX9z/tDdolg4mt1LZ+JJVW5RDwrZdZAOaT/wBGQ9/n/XqFuRqrNXPbHpHiq4jhuY4b2IbsD2x+eoMsFTcJC0xbDYHKCSx9N/6DVyt1XTX+lp7BxDUotzj8lurmJy5/6MpAxk9j1Psep5U6U8/Qfb4gyONWDj6x7ynRUc1SS0p58eYjoie/p+J1IkkpaQADEznpgZH4Dqfx2+eurtDdaW4S2yrpjSSQNuvb5r6gj7R1zTUCxxPUTskMfVp5T1+XrovzRs3E4WL/ACGD7QNzRinqbpFcobnR1D0lVAcxONz/AJT2KnuvTVuqaGm4oge4UtKtFfYlMtbQLj9+B1lj+fp/shrbT1VbMkFrp3jL7LO6Zlf/ACJ2+Z/XWg8KfRkYZo6+4TzUs6edHjcGfPu3QD2G2vPazxKqt91HY9/mej0fhtr17bznPt8SmcP8PXa9S+DBTyU8R+KKI/vCP436IPbrrT+G+ArTaaYS1wik5fN4Y2iHue7H56n26rloqiakj8KZ+bJ5VwkrfeXH2sdV79tG6KgSpCVVVOKskZQD/DX5D++kOo1T2HexjmmlKxsUYjKzT1CiK3QrHCBjxnXC49FXvpyC00oRzUr9ZkdSGeUZyD2A6AaNinbkyF2GmZaR+dZCWAUdM7aBNmRiEYlPqLbUWudZKKSTwF2jYDmeAfdP34/Y7jtotaqwVjNT1AEVQoyUzkMPvKe4z+I6HRXwRlgRg9tSpaaguFEqToKetiwYalBjJA25sdDjbP4HXQwPDf3nMY5EboqBpNghA7alvaJhlipwBtqbwhWRisFDWoBUjO4HlcDv7H2/LVwqhA1O+SvTXNvzLL6hmZXeqmntUHiT53OFRfiY6GWbjeWmqvFhpgifC/nySPcdNO/SdHTupqRLiNB4bj0JzsPy/Q6olpqqJUkSWORH5uaMBsgoOuQeg782cDfOOujqtOnlbzKbgr7TLjdK6qt16e7QRxxQVBDRyxr5APuSr6ejDp/PRrJxZQrQIat/AmK8zxvsE/7umP8AeNfMfFvHlQ9Q9DbZhKq+UiFuZNv4xsfwyPQnTFl4uulHEKW7QC5UUzZeMZ8SPt+7/tqiaO1xu7HzMH1KVPjM3j6RPpCtxpTBQolYrbEsf3f4+vyO3trA+JGF6rHq65mldcABm8iKOwHQAenTRG8SeDQNcKGY1tsY4WRNjE33ZB9k+2qXWXOWpBWPdObYnp8wO59zpx4foEB3Y3GK9brH6JwI7KKNWwgZgO64x+pGloW1G87Fisk2+M4J0tegFbgY3YiI6gZ+kz6LTL5Venr212gCZCnfux16BjYbL6euvDjvsPbSLdPWTxRuQNvX310oAbbf316FOOmB216cY2wdVzJOhsSF+LvnXgUb5JOTudeZwvmG2ulXmGWJA9PXUzJPFUkbbLrrO3Ko6dtOKebYbDXhG3Lj56mZI32z+vrrtY9skba6VOpbpro7gkDYdPfUzJOBvt2/nr0Ljc4I17tgk9fQa9VCBnP+mubpYCccpL4z0/TXowRgDXWM+Veg6ntpYBzg99/c6qTO4nIUbjr6++vCNtuh9NOcox/vfXgGck6mZMRorkd8DSznYAD1056jXmBqZkjLDmJGvOT8dPMpBAHfXvL66tunCIyq9SNvX314R/pp1hnbG3bXJXrg66DOYjZBC9NNgb6e231wAc5/LV1lT1OThT6nXmvSMZOTps5PqNXErPGBOw651Bu1dFbqMuxBkbZF9T/bU4lgMDdvTOqhebRd6iqerm8KUdAFf4R6AHROmrV39RwIv8Q1T0V4rGSYJq6p6ioLsS8jnJ99EaGk8NfFlGZOoHZf9dO223LSDnk80rd/u+w1IqNgVXGcflpu9qj0r1PMV0uTvs7kWeRVG/mc9BqK4OSS2W6Z1IZFXJJLMcFjodcK+GCEs/w7jbqx9Bqieo4Es+F5MjXGoWEHmIAXq39Pnqs3CRa4ss0amPoq9x759dd11XJVygt5VHwoOgGojsWOE/FvTTKqkLye4pfUsW9B4ga4254MyQkyRDr6p7H++oHIQcnpq1RKF2A/H10xW2iKePmpuWKoG7Rk+V/kex9ta529wqnUrYdp4MrJGCSux14VEg5SuD6eun5oXilaOVGR1OCpGCNMlRnVweOIYDjiMI01Nkq2R3GilFUrLHnO/cemoJI6Pkj17/66a5HjPPEeU9sd9aK3HMjotg5h9HBXrjXpkHQdT00JgrecBCOWQ7Z7anoQi5J8x109QFqSncdUEsc7nuc9Nd83KMA/jpoShcgHJ7ntrwuGySdZETMqcx0OoP3sa8Zix7Y00pGdtSaOB56pKdEaSRyFVEGSSegxqpIAyZNsbC+YY336DRa3kUc2Xpmnqg3JDTOmRzZx5l+0d9l7nr6EvZ7PUGre3WeNKu7BC9RU84ENDGOp5/hB9X6DouTvobUVMdmuUqWS4Gd1TwzWqvKScefws7qO3NsSPQHQZvFpKJ3CkpNYDv1DVaRZIJBe62eqvdQ4aSnVwfqq9/Fb7528g+Hv6afpZUniEkbh1Pcao8j7czHc7/PSortPQ1AFMplZjvFnZv7fPWbaE7M55jPR+Infsx6f3l/AGAfXXjHqO2mqKqjqoBIvlbHmUndf7/PTjd9KWyvc9AOeoG4ktkNwpm5QqynbPqPf++qDU0dRbZzFKpCg9D6+utIMnPKSOg20xX0UFbCUmUZ7N3GgRq23kHqWaobcjuUVGSdUDyMrpvHKp3Q/77aL2+4sW+q1fKs/2WHwyD1Hv7aFXa2VFunYgcyHoOzajwVaMAsqiRFYHB6qdGsgdcqcwAXFX9QxD9SNiY8ZG++s/wCLponujJEoUL8Xu2rdcLrBS0TVDOCSDyqOudZpUztPO8jHPOck6X227AQe40qUOQRJ3D9FFUVskzJlI8bHoznYbfmfw1zfjH4/hAl+UhVJOcfLRa2ILfZzI/lYgufmRsPyGq42Z6pn6kHP46CZQABDVc8kwjZ6YibzDIA299WSGMYHQ6gW1B4QRgFxj230S5SjczHbTDRXKRtMR69WXL9x1MZPttp2BOeUD0301CVKnfGuTUnzLHtnbm7/AIaapwYmfLLx7ydLUJD5R5pD27D56iIJp5z5gXzjPbHtruionlbmYHl676O0tJHGuEUA6pfqPYTTSaEdmR6GgjiIYgM/r6akXOYUVrqao7GKNiPn9n9camxRHGMaAfSPP4FljpvtVEo29l3P640s8ws2I3SsKMSgwbuO/c++plU3h218HzOwXPt/sfrqPRDcsB0/+f6acuKMz01IuSTsAO5JwNYXNnMYp9MO/Rnb/rvFtDzDMVO31mQnoAg5v1IUfjr6OoaVY6Rq+oiLAKW5WODjGxI1QvohtdPQpc6yaJIli+r0KMU+0xMsmP4vJH776P8AEnEMNT/w9G/MVYMUKgqApDb9t8dOvqe2ha9JZq7Rt6EC1mvr0yEsf0lmNFDTTS/XZFCRHwid9yDlv1PQb/Ib6D3V3lLrBzxwYIKdMqN9x8xnv06nVbtF7lgH/GsZIyd2xuCTnAHYfLVjZPrzxlWykm+3Q5Os9Vo7NIcP7yui1tesTdXIASWTkWNWG4AI+Z6epyeuotv4Tpp55a8RF3DlQn2Tg9fft7auMcEMSpyR8ojDStkZJ5EJH/2WNeQmioaRYHmVnROYx9Rn3x1PtsPUjWIcqRiEsoxKbWVa0V3aAyFJgIIVYdQDKrtj12VRj3Oic3Ei3yqp7bQzSQFZVh5A2OZ2bBYY69dVnjiJqyukqIsCVgGxyjOcYHb0xqpW2aehuEJjkaOWKVXRh1Urvn9NG11LqM57EEZmpII6mg8R1Rqbxd2XaKSokIBPUGXVXWhkqBVCOMlVRmwB2UFj/LRPhGqN5ufgT48eVwWAGAw5wTj8Bq//ALHRA9PBCqt9X5EXuWlljjHz6nXNPXsJRveXuuxXvSA+H+DrdRW9K1KUPVzRc0nOgLHI3Cjt/XWatbrjw/XVV1tcfiW7xJ55qGMjxqeNJHRnVT1wEPMPh5Thtun0lxNbaWz8PLe4qiOUElecYLLgdFHTGx3zj59D858aPUXSqnMEjxRy8peENhZvMXHPjHMQWYgkbZ2xofymcYP94RRftaXbhi90tbRxVtKiTusv1xVhHmqpFHKi5bOMM3TBYMQDlijMFvXHF+v9LDbbjUlqWCQvHCFwsbHOffv3JPvvrNLNcK7h64GSJXeF2zPT5x0BGRsQGAJHoQSCCpIOlwi38UQRV9FIi1b7lsconA6g9eVxncHPuSMMb0nyLNtvPwZfUVm6vdVBVQC0EagczMzH8Bto3YrfURVquWKyq2MZ/A64hoxDUU6FCGSUEqRv13H6a0Tg157VcopTClRCz4kEycy498+4z89MVv2WFvtEzUGxNsrdq4fNVdoZhQLPK0TyFT0yJCBn10Stl9u/B3HFMeYmSqDRuOXAA8xAHbt1OdWs/SHwxw89dcVhpXrfE5YokBxgOHIXc9Sz7kgbd+msy+kXjuPjHiyhukdHHSBZ/CCpuTtuSe53OlQzbcAw4zGYPl6ZiDyBNC4t44ufEFK1IagrgZNOpxzgd8dyPQ/hqjTMWpoj187b/loSjVE0oZOdVBBD82CD8/XRlSKiljXI+tc5JAH+NtuQPveo79tONR4f5S7q+oj0XifnkizuN/8AOPumozQyG2q8LcrwysBgeoz/AEO3z1KCkyqQRuh0/Sx8kMolRGRZUdhIcIQCQc+240DqG2tGQTcJPslxobh40dZKf2jOEMZjOVJIw3NnfOw/Ed9BL3QfUa1icKQ2FAUjmHUEkfMHUajH1a+UssRZVEwyc/Fnr+PX+ej8sEV1tKy04YVEEqmeLuADgsPbWmn1A/1RfqdMT6h2IKrrhNTSV9KZWNPUhWaPpnO4BPUEA7MPTB2Oolxsk/FNTJebTMUvEPhwpK6eGtRyRhRG+CQGIj5gQRvkjGNGOI7BOYmqkbAhi5CCPiIJx+hGmbA0kdLV08a8qyxgnbIYA7qwG5GDn1BXI6aG1WmUZdOoZo9YynY/clfRzxjVQxyW5YDTXKlqD9ao5Yxz84xzAL97y7gbMMkbgYvNO9qvVumppKiNInqWTynmKrKMhh3IDJ+v4ayHi2I3K4NeKeonjvMFOCknUVHJvySMuAcgZWQe2TnfRTgy9/tao8QF4q2NwlXSsi5yD5mA7MMZONiBkbEgD1XcYf8AvC7acjfX17iGIljoJ2gpqgTBfFROQeUgE4bHYnkU52znI6Z1wb+bhQTWirkBMzo8ZMfVxnzEjvg/jsevUhbeWpq3hVVkqWEiYHQuh51xnc9HXVcvlrqLTVpMiuaZhzRSKdiOoPy6ZGsSu47sdSqHaoBME3S2yU09TTFDmMrMnKc7e34H9NFWst1pLRHVXGJ1pKgeEvOTkbZViOuB2zopaa2lW6qlyVzzNyLJy5YI++x68wJz74PfObnLb577wZJSSP540MaqNsOu6EnqdsD89Y26hqyB7TRaQ+cdyF9HDoeH1SCnjSRW5JgNssO5I67H9NGajgwXW8s1TTx1K1dIUljxhJQm3KRnfAK4z3JOhX0SXi1WUVjXyaJYp4eflkOP3ikg9fkT+O2dQb59IlZNdooLLmGHxWFLOV8yschWCkbjsebr90a4tLWWEL7y62rWgZzItHXVX0aXhbBcag1FgrZM2+pkPM9JODkIx74P/uHXfORXGFI7VlRWxwGH9554xsoVgHGNyCAG5cgkHl1TL79ZvdfLJcppaioccrF3LN/lyegHoNh6aNcB3+WmnXh2/ETUkyCClqpDlhvlY2PsS+M9Mk9yDpWPJPM2ZhehHvJFropqydYYI2lkOyqq7fgO/wDLWiWvgepjtk89XInjcgZYvi3ByMn+2jHBVJFRWzwaekjSoTyPJy48THTJ65x1Gr5w9RRyyB6wiQ7bdFHyGouqYkpKV6YdwHaIoUtkYt9MkKsAWBBBB9/XRW38LUFwqYLlVl1rKVj4NSjYZc9VI+6fTpove6agttGJFKx8pJA9RrP+JvpAwpgtEYHKpRpMkBvbIO4+X541wAscdwolafrlvv8AfLVQU06F4IpqJgkyA4C5GQfkf9NZdxLxlWVbvHTuYIezYwx+Q+z+p9+2qjdK6sqJZ7hRylrhDGXCkeSojHxwsPlup6gjUGnuFPX0IrqR2EZyHD7tG3dD7/z0XRpxv/qdwPU3ll3J1D1NcB4gSZ+WKTysO4z3+Y2P4aZuSyPG01NyJcqJSEPUSLk5jf1U7/LGfXQ2igqarPIDHF3Y9W0bWnML09TGOZuUQyE9yPhJ/ID8NFWVjHAwIPVYRIsFdDdeCa9Io+TwXaQxH44yQuVb3BUb9ww0PoadpIS0UeFXbORorU2uqoq79sW6PxVlj5KmlBA+tQn7O+wcfZJ7jHTXVpWF7fHLSv4lO2Qj8uCwBxuOzDoQdwQdWptNTYktq3DMAV1HPSSPXU8azlgFngG3jICcYPZxvyn3IOx08alKygMlFUCSGZeuMLIB0yOzqR8xgjRe6PS08DPLIqrjcHVFnqpY6ypqrXFJ4EoLzrjPMQP8VB1LADcD4gPUaKW7Gfg9zM1BvzEP19ZWChp6mkLx3S3SBoJYz5kPZvl1Ug7EHB1sn0ccY0/FlnMjolPc6bCVtMDsjHOHX1RsHB+YO41glhkWGpV5JPHWRMSSA7Mjen6EfLUyGe5cN8QJX2lljqYCTEzklalTu0bDqysMfIgEdNbCrKZ9/wDaVq1W18HqfTI0tB+C+IqDiixR3OhLJvyTwP8AHTyj4o2HqMjfuCCOujXKND5jUHMWBr3lGvdLUnZ5r3S0tcki0tLS1JIteZHXOodxuMVBJEJ0cQurlpQMhOUZwe/TP5ayLjL6YhNIaPhfyU3NyyXKVM7d/CQnc+hOqu4QZnRzNJ4y4tsvC9C0t1qgsjDEdOhzLKfRQN/x1j/E99vXFPB9PPZqiujpIpfArrbEQZvM37tiw3KkHBHr6b6GPY5L9c4a2MXGkhqFCrNUOZ66vIJJZEGyjfoMIvrrR+Fvo/FppJKkpDQq0TI1KSJWmB6+NIRhieyoMD1bS99cuMH3lgpJ4EqHAHCtdcLc9makonTxA9SkahUQjBCzT7nbr4ce/rjrrT7Zw7ZuHIY665TwzzUo/dO6COGmB2/dR9Ez67sfU6mW6qleip7dYLYiAR4DcvJBCMkb4Ht8Kgn/AC9dOwUEdJOKqaVq2vXOJ5VHLEe/hp0T57se5OlYSy1iJrlUGTGK01t2jBmzbKHmDo0qfvpcfdjOCo9333+EddRqOqelp5KSGOKnZ3L1DRrhpWP2mPU7fptqdOjsS5JZvvNqHVQ80fiop8ROn8Q9P7f6nTTTadahg8wC61n46jsD4Hse2idlmlir4yj8pz37j00Cppc4KgkN076N0NG5xJOSm+QAd/8ATW1mMQKoMGzLJxFZ4b5bGEb+HNswb+IdM6zMF6WqlhmTkeNsTp90/eHsf9daNbqwwFlRjlumd9AeJKOnqqnx38OOocEI56k9eX3H/wAaxodq8/Ebsy245wYDliDJzJqFcKL67Arx4WrhH7ticcwzuh9jj8Dg+uurVUpshk5oySqHPQ/dP9PbXVwq1imaOmQzyjqq9F+Z7aLLYORKgccwfRVAqImSRcSLkOjDcEdQR2I/t66GXyggmpJqWpz9UmPPzgZank7SqPbO477n1zNrKWrMjXIP4kwA8SJFwCo7juWGe/UbemnqeaOsgHLhs7+Xf8Ro2tww75g7J/afPdy4crIeIKinvczV9QjZBVv3bKej59CP9dMVVwo7Ufq0KCtqj8MSDyJ7H1/l89bRxZwtT3ezvZqhvqnMeajqoyQYXP2W/gY7Y7H8MZPDY47LNLRVkPgTwtyyLjLk+ufQ9cnrnbOmGntLjYDtx38mKtRQKz5hyx9vgQJ+z7leqgSXSSQgsAsCZx8sd9WfhyvThSSR1VJaWdfCqqPYxyp0we3MN8Yz1wdtQ3qnkXwKONVQ7E9QR7nq36D20oKB2YTTNkZwZH6fID+g0YKEKYxgfJ7gHn2bw3Z+PaFOLLX4NLTXSzT+PYar/BZV80D942HZh6nft8xlLQxxRc8pMYcc2Tu7j1x6e5wNEbDxElkrXgED1lvqiFrqZjnnHTnA6Kw7dz+WOuKOHGp6mGuoqh6+zV3mpJRvv91+5YYPX0PocUptKHYf7zW6oWDzB/aCZawMGgooxyjYvnr826n5DA0wttM6s8uJMdSdlX+389Tc01KTEg+tVA/5UZ8qf5m6DRawcJXriZ1LqEpAe45YV/qx1lqPEaachfUf2m2m8NtuwzekSTZrpR8S0kdiutUjXOActvukiEo7dopD9r59/n1IcL/R1dK2sNReJeUxPymR/MQR2Reg+Z1dbPwnw7w9ApqYkrKgjAMiBifZU7alrFVU6s8gmpqVyERxJ5+Xsr+nseozg68vfqjYdoP/ABPSV6Za/V/9yVbKG0WIfV7fTGWqceYjzyv/AJm7D21PShqavzV78sZP/l4zsf8AMe+n7THRrS5pECLnDfe5u4PvqWA2ThTpZZYcw1QMRt6GmlpfqrwqIuyjbB9R6HXNopKqjqSozJGxywPR/f2b+ffUqMnGG69tTKJ2EgIOCDtrDeVkZQZa7XbqaSkDEA8w6emo95tqJH5Bgew1DjuTUEZkpVUqN3iz+ZB/3j5dI1z4utzR7ytzdCvKcqfQ61ABHAnOOpAqYuVz3Py1FldFBZ35R331Gul4jalar8aOOlzgyH19PnoPZLpYbpLVS1FwWnFPhmWU45gTjI/HbGM6stDFSxHAlMgHELSViyeSnDNnbIJGD6g/7/PGuaPi2opWmpbq8wSEgGUoWKk9AwG5z2YDBzvjVV4y+kuy8OK9NRDw6jGAoUPUsf8AKdo/m+/8B1klfxtxPcrvHdYDHR+HkhHPitKO6yM27A+mwGdgNa6XS23nCKcQa6+unlm5ml/ST9INlhSWkpnM9TIpQww8sjN7O26KAd8DmbI+yRrH6ye5XYGOql8KnYj/AIeLYMe3MerH55xqwyW+gv8AHLX2im+pXJF56y27cxA6yRZ6r7dtVie5urNBBC6EeU4OD8iev4DGn2g8PrA9R3H49os1mus9uB8+8krTwUcfIRycvVF+L8ew/Hf20xPcmlXkpkBQjBIOF/E9W/lplaeWpbEgLADJUbKv9B+OummpaVc/4mOmSQv9z+g09FYUYb+wiTzSSSv9zOrNUXazVMlfbJUw3lqYJB+4lT7rDp8j19NFnpbbfo563h1V+uQrzVFtkJLR+rJ051/l31W5aiqq32JRF+HIAx/lHQabWhlhmiraeolo6qJuaKoViHyPTuf5euh7NKyHzK+PtNq9Ur/07Bn7xuqlrWmImiXmXbEoyR7Y6Aew0tWM8X8OVbEcU2qqkro/L9Yo4UxMPvMu4Vvl10tZjW1gYZeZdtC7HIbibuOnvr2NCPMx/wBNeoAo2yT69/8A40hls8pAx30snosRA5bBB/y+vz16VxuTv7DXqjHlU5J/XXS4T4jlj/vbXCZ3E5C8vmfbuBrrOd+g16xHVvy16qkkZ39vTUErEoz/AE08qBVJbr6d9JQEBGMn00kGxJzk9c6hM6BOSCW834DSIztjze3bThznlHXv7aQAAOCeXuT1Oq5lsThEOM5J9T6a9znIGQB39de4LdsLjppEZUbbdtczJG2LEYA2Hp316gOMHrrsKR1669IO4/PGuZncTzl/PSC79de9v56X8v565undpjeFyQNeEYG/XTijAxpEE7dddyZNpnCjbPf10uUf310FPr89IjC5x8hruRJtMbby9s+mm22Hz06ASMk4Oly7asDKmM8oyRrwgj56e2xuB89Nsp9tXVpXEjt1x314QQMAEt2Gup5YKaCWpqZUihjUs7uwCqo6kn01RbrxXeqfiIvboA8UMZL26RB4lTDkkVELgkSKRg+U+XuD11x71TgyCtmB2y70zxNTGZSTnrkYI9j6ag1TtK2AML2GmbNfbdxFT/W6GXpjnjOzof4h/XpqZJkqQnXOGOi6mA5iK8MSQYKmiw/k2bv6ajmIAHmHmPqdT5gigb4xvoLxHdIbdT5kIdnH7uPu3v8ALR1WbDgQKzCKWJ4kG9V0NJETJkA7KO7n29tUquq5aqcyyHA+yo2Cj20q6rmq52qKh+Zu3oo9B7aiD95schfX10709ArGT3PNanUm44HU6Yl8hchfXXigDYa6IwNLIUEk6I6gY+BO4UySWYKMdTriQtIeUfB6eunUjLJzOD0yB6fPXhxggbZ6n11zudHHc4mggrIRBUoSFGFmUeZP7j2P4Y1X7lbp6NvMRJExwkq/C39j7aPO/wBkdB6a5WXw+YMFeNhhkcZVvmNcCkciH6bVn6bOpVNcsCMkdO40ZrbYkqtPb+YqN2hbdl+X3h+uhJGNaqciMQfcRl41ccw64/HXUNQ0ZCyksvrr0gAZGuWCspBAyfbVhLggjBk0TZAIYYPYa7VvTcaFrzwZ5ckdxqXTyo464PpqEZ6mL1DGRJyEBgTq58JUSSWuaraoNuowSlXcZFyVB/5MK9XkYdcHp1wM81EWXBwNEqm61lZT08FXMWipY/DgjACrGvfAG2SdyepO5zoPU1PYu1Ticq2IdzjMsHEPEcctEbNZKZrbZVYFoubMlUw6STsPiPovwr2Gq20qqM9NMvUAblgDphBLVylIzyoOr/21ailaVwJwh9Q+TO/ElqJfCg8zH4m7L89FKanp6CIgnnnYbk9T/Ye2mIJYaOLwqZQznq/of6nUigpJKvMrsUhU4eQ77+g9Tqtjns8CNNPUtXCjJj9tetkrA9Mx8RRlnJwqj37Aas7SSyUfjhG5SeUPykBj3I9tO2Oygxq08JhgBysJ6yH7z/21Y1jD4BRWjxjGNsemNeY8V8QVRhRH+h0jYyxlOAw3LrvJ0Zu1meGM1NIvPF9perJ/caDdM6U1OHGRCHG3gxqriingaKVAyn9NUPiK1vRSmZATGTsR/I6u9TOFByfy0Ir5EaCU1AzCBlgemNWGuao7U5MzOlW0ZaZXfah2AjydzvvqJaaf6zXxQkeUnL/5Ruf7fjpXKcTVk0irypzEKPbRnhKnCxS1cgGGPKCfujc/rt+Gr4Lt6oUoCJxPeKJvCgWDO58zAdNCrJTtNOEAyScnTd3qTWXFiTlQf01YuGKbljeZh12GuL63lbm2pgR805TBJxgZBGnkqFWIpN0Pb+3+/l3zNqOVY+VgCW7DqNDWoZppSx+H17DWr0ADcvcAV8nDdR4KX5QmWVj10UoaAJhpBk46aYt0Sw+Ub+rHvoxTYyM7j112vxAn0NM20Kg7ljtLFgYA1Ohi740oY9gRqZDH7HXXfJnUTAxOYoySM6zn6S6rxeIFpVO1PEBj+Jtz+nL+WtIqKmOmVh8bkfCP6+2sYulW9fdKisf4pZS+Px2H8tSv3YzVBk4jlvTOPTOT/P8Ap+up1ueCHiqGoqmQQ0zB2535R5RnHz5ttt/bUekIjRpG+GNd/f8A3j9dDy71M7SyMWZ2LMT3JOdDnLHAhxAAM1ix3SrqLS8qSNHHUVEkq8pZSQVCYxzEDyoBt+JOp0TCmphyEFmG+O2QRjUC205ioaalGyxRBSQO+N9HqC1+PFTnzYnqDEvfZVBY/quvWUVpRUBPmGstfVahsfMHwwMwY8rSOFLEdcAasVpu0NkucqVcwlpEaONQnmw5jBOPxY5+Wpl8hhtPDtSIk8EyLyHl8zEnfzt2ON8DWfV0ju00zsz8z82W2zv1wNhsNLPELFv21kcR14VS2l3Nnnia3W3CGsiElJIREcrzZ+Id/wANCZXcnGy52+e5P89UqwXSajRI2JeEkkpnbc6vtBB9e5JIctzMqjHYk4A0gv0VlB3kcGeh0+sq1OVU8iBK2nklq3wDjJ5m1CudiZaM1XhcoZW5ZCMcxCk/7OtDt9khSonlkTxkSVgvNsp5SRk+2g3HlTDVU8MEJBCBlYqMAnbp+WsKLthJhLpkbTKp9GiRWuve5V00UUVLTuy+Kcc0mOVV9TlmHTVgTiYVdmmuFfdPCuJMbwxtFzLOockIF6AAkNvscd9VaqSaamECuEwDnBx4gznB9d8H8O+q9eZSKpcQJApUfuoy3KPlzEn8ydMKbAzB2irUadthVTLJX3atrQ5qamaVXYsQ8hOT6n10Grg37SjVEPNIoJ9ug/rp61LLUIokIGdl99W6zWfwb7HIyuzJSIwUDJy5OMfhjTvxCyr8L6REXhdd9Ws9ROJXKjgx3tU9xmHh1EaZVe7b439Ovz0Ftdnu9ruVbV2aCWaOKpcTUqZHMqMcMpG6uOzDce+SDr9bb6ueyVbNA6+GhJAOVG+Bzas/D/FvCXDUtVTVFBHIstRU+Mqx4kAMhKkg/DgbDfPsNeXvs8wbe57Wl9h7ld+iKus98v1vqqloxIrY8RkAyQCeVl6BhsSPbK+XZL79Nb2ihoVoaGNEmI/fogHJynuffXzXxPxA1HxvW3ax0/gRzSlnpclQ6DcZIOQ22Q4PMDuN9XWy8UUnE9EjtUZmGESR8A8wBPhyAbBsAkEbEAldgVQYI1TgWQkBXQlBzM44sqCaj43JwVBzknc9dRuF8z19GoBci4DAG++VGnuM4HW4vQqkiSJIQ5PU8xz+Wp/0Y0X/AOsdJEDKqtVc2VOCQCv6aZuyqwYfaBKhapgZpVvsM9SCshWFR1BILY+X99BuLKc0EyRRo6BHwDz5IPKO/r31oMbUdO0iRSRu8Y5nWIczD3OM/rqh8Y1q1NwkZk/dMQp3zjyghvTp3GRv1OnenuaxznqeR1tKU0+nuO2uYV0kQOPrRU5H/V2O4/i9u+p9OZJ1qKJ5C0QTyKfs5YE41XberwXGmjGQfE8jj5bEY0ftU6113dHdkqhG5OB/jAId/wDN6jv165yv8T0hVt6dQ/wvXCxAlh5gKSjnp5jIg8iEHmHbfbRW4K1BNLV0sgR5eYjJ8uDvjH49D2O3caMGmidoudPLkbEe4PT5HUO5QxUyU1RUo7whkDhG5XwhwRn8Dg9ifQ688th5EcsAQIYt1xHENvnMmOZVWN0Vic4QDI74wBtqBRUMMUSeKhEz1BTHMRlGBXlwNuhz6++vKiutlLV1ddaYDPRF45HRl5HAKspJxsGye2x643xrqgrqKeOpaSZSyxvLDg4ZmGy7An7WNvQ9xjRItcgAdTA1ruyZSL9H41Q7jOWHMo5sMp+Y/X139TkJeIa6gvst4tbTR1oMU0TA8qzIWAwxHw8uRhuxB39bhxLByzVLpgIsxK7Z5gWxt+mht2ofrNlp3kQowVopCBkkDcbfI9tctqKLgzTTakbjtHAhe03z9vL+1aFpKW5U8gNwpFQLIHTYuinodzzL26jY7X+0W+PiLgemiMjrNEjRDmHKx5cjH/t5cjWQ2jhaulWrutkT6hdqSSKSFRKTFVRkcvKSfhbmBwx6E8rbHVv4L40d7fLNTLLHVxTh6ujbysjrs5APwEbZ64zvlTrtVuV8tv0ml9CjNqdHsSJxrbmo46GflISamUnC/Cw2P6hvy11bOOa2zWxqejiDiZQgaSTmKEbjfvs3z26g76sd+c321U9G0MkVXDIzxrJGU8SN8kbdNjkemTtrOK+ianFXTzI6NEQ+CvTGe3fYnUs0ysMzGq/acT2qmqK6CaplcM6S+P0yBzHlYj3zydd/fXBkklpgkbOkquGUjGf9NwN/00xb5J9iEdabdZWIySp2P+/lq/8A0VWS2VJmmrg881PJgxdVI7N75xrJrRWu4S3l7mwe4LsPCs99vEjeNHAGVKiQY7nrgd9/XVubgSwrLHSFHq0nmWGoEj4wrkrkEfCwZlYHqCurpS8L1tVf1ukELQxzQYAU4zyjofQ7Lt89Erha0akelqJBTvNHyLJnHKzDyke+dAah2d8jqMaF2DmAOAq08O154N4qJkdl5rXcccpqUT/lt2Ei5wR32I2O0rifj632+dorfGxlUY5QwJGNjk9F+RyeoIGs3+kHiqt4gtcVPVxokhCStMowY5V2LIBjDBgwySR12GdArbdWvETUtwwl5i8zcoIFYvTxV/j6ZH2vngsRVSeC3U7ZbkejuXe78W118tlVBNIC0SiZEBOMDqN9zse+qp9dM4OSHI7ZwPx1DoasUdzhDtlc8rKm4KtsTnuO/wCGuqS2PJUTxzOVSnlMYUbe4P4jTNK1QgL7xaxZ+WjiVMv1tJKdfFlRgwH2dv5j9NQ6i1T2m6VFfbkNRGWV3pW/50RGVx/GuCAe+MatdtpFwEgjwehAHXVhpuGKqtakZIGZuYxsOmVO4/I/11a5QOTLU7uhBFhEN1o4ayhYPBKPIcdPUH0I7jV/sHBU1fQSk+RWHfYk9tVx7HVcI1TX63wmromPPc7eo3IHWaMffGMkfaA9c50VOP7JDaqaop5opYJUDRuhyGHsOuf5dzoV9SW9MOq0qA7m4ErN64fe0RiCqKMpXnVh0Gev65P4jWSX6rW132We0iSVJwTWwKMgkD/FUdnAG4HxAevXSuPOK/2vBFUrzJToSjKDuFPXOPwP4azO5DwpeZG8ERuCvL1yDsda01M4weJjdatZ9PIgWuD1UgqZpFqiwDpynMYB7jPX5nTKO4nVgx8ZSGQITsR0P+8DUi4MlFULOV8G21rFuVQB9Wm+0MdkJIOO3Nkd9OUtoq6l+VV+rQeuclvx76PpsXG3HMAurYNuHUiTiCnEU4dIqKVysqIfLSznfb0jk6+itzY26aZwZwxFdaJJbvC6yRY8MDI8RB0weuB0267aA22zU0NO9OsKskgCyc6hs75yQdv9++rHwrJWWN6a1zeI1pnk5LdKzktTyfapWb0bfwyfkTnGh77mpO0dGGU0rZyRzClXTTWi8LeOGqQyVMEYjr6GEAJVwDoB2Eq78h77qdiMXuz3Gju1rp7lb5xPTVCc8bgY9iCOoIIIIO4II1T+Na5bdHQ1lmnaKpjDMuU/dzRk4KkdzkfMahWviGlohLxNakxapm577QDdqSQ7GqjHcHHnA+IDm+INnqBlUMejCFtUsU9xNI0tNwSxzwpNDIskUih0dDlWU7gg9wRpzW00i0tLQnibiK0cOW9q271sVPEOgJyzn0C9TrhIAyZ0cwtqkcb/AEkWewTG3UYN1u7EKtLTnPKT05m6DWfcVcY3fiDgiSr4arK+mo4ax4ayBFzUNG5/dsG68pyQcdyPQ6G8OcCG4VjvTw1jorr4dEZVEo2zz1EqjlTffAy++Md9B6nVeVxIJEul749reOUrKx2We2kSPThwlNTKRurnOB5Tg53z2zq2WXgSlufEAvFrijWmqlE4lqB4gpSescURGDuMhm8oBGAcautq4StFlolqr3JSzGA+KkIXkpoD94KT5m/9SQk+hGn5qiuuDTVtLSz0NCYuQ1OOV238rqjA5A9WAyMbEDOlv4trgU95r5W31GPUkdn4e/c0qS1VxqfiIJlqagj1PXA/BF/h0RorNVXeoEd6mECMCy0cTHBH/qSDdv8AKuB682urTR2yggljgWZXlUF6knneQ7/Gx3I7AdB2AGnJJXRlaSdmcKAmD01SjRk8vI9+3gSKoW1VYloY0pqZcRskK8qxkbBgo2x2x/fT09QzyESEO2eYk9MnUWYtK5WQBg2xUdCPfTUJKt9WkJZ4x+7OfiX00yCheYHv38GSlZurHPv6a8jpzLkKfIT37a4iZmBBO57H+upUOIowgO2rngcTHdniRJ6b9nTrWQjmiY4mGB5SftD0z/P5nRinWSanaeMZjQAs3oPXQO7cQ263r4FQfrDyeUQKMl/bGo9PV1Sx+FUfWrZRzqzGAEMzIexPUe/fceusnY4+80RVadXHiGWSrNBZqZ6yqG5YfAnuTqO9PTUmLlxHXirqlccicxEUb9gMbs3oBuewOmqa5SVqGj4Zo4VpwcPVNkQA/wCYbyn2U/Nh00QttBTW2ZaySRq649BVTKCUz1WJBsg/yjJ7k6GGoYkhJdaVXloPq7Fd62d7lFQrTwVCnxKZ35JpB1EiqPgI9M5Oei9NRbRV0Jo2jysSxHlyVKlj646k66v/ABrDSVrQW4PcLinxLHIAkR/9STcL/lGW+Wq/bbjLPdnkrXiLzv4iSxRcscMnQqM7lTvud85ydxjahnJ2jkfMJ3LtyeDD0i1dQ/7rmpYPvf8AMb5fd/n8tCK+gazzpcKNylKNpo2YkISfiOeqk4znocEd82SOsWcGGKEvUpgOnQIcdz/brph6IyMTWHxz90jyD5D++dGIcSp5jHNFW0xDKCrbEN2PcHVO454VF8p0jBP7SpwfqsjHaoQZJic92HVSf76sDJ+ya9YEbMEg/drnJX+A/wD3Oeo27anzxRVFPuebOCrA4PsQex0fXYT6l7EEsTIKt1MFeaCjZo5EJnBKlGUjlYbEcuxJBHsPnph2q6xuaRjEnTCncj02+Eew1o3HXDC17yXamiVbnEmapUT/AM1Ev/MAHVwMZA6/lrMo7w9VKKa0wmPmbl8dwOY59Ow0yXVqV3HlviKjoX3bV4X5kuaOkoIVNWRESfJEozI34f30c4CqbnWTVNrNnarsdWOWop1J5kP/AFQ2cBvUA74GNwNE+FOAIgwqr3KZHPmKc2Sf8zf0GtCtZSOEUlmpUKKfj5eWNf7nSjWa93GD7e0caTQJVyP7yvcM8EWC2c1TUzLURKcxK45U5c7E92b19+2rfE1VUoI6GEU1ONhKy42/hXXsNrngV52c1JdueVPDGFb7yD+Y7/zJwP4i5X4gOg6exHtpLZfuGYxRdpwZGo6Cnpj4gBklb4pZDlj+PbUgFJeaJlDKwwQRsddlC3xa6iQKTk4/roRmJHMIwBI1Laa+3TLW0sL1NICFkjzk8v3T8uzduh2OrO1JS1FAtXQuHibbBGGU91YdiNeWa5/Ut2YAYxg9xoVX1K0FwevtDloZt6mnzsfcehH+9umgIsGD3MSNsTRJTlyztuc7nUWa6xJ5YgZHHUDTi0Mt2zMkwMDHZhsPcEdc+o7alCyCm5JaEoZk3KyjyP7e3z1kVUHB7l05ga6zXZrd46h4051wUOD3xjuT8tCXMlbA80kAaeIDnIBVXXOM7fCcn/5GRqmce8TV0VyE17ro1ijc+EqN+72+6R13HbJBHbrqp8SfSfxDf4xSW4uI1GBV1KDIwMZSPdVP8R5m9GHTRyaSwlRVyT8TKzUV1ofMOJf/AKQOJLFbeEobfVSSU9bExdlc4LMeqqoyWG483lHv1Gskn4iu9exW1KbXBgjxgx8Zgcg4I+Hb03I2JOjFnuqVtqjs/FzLLQoAtJcyoD0z9AG+8N9+/c6HcQUlTw5VLTzU4eRxzRTr5llXsU7Y9zn8NO9HolBKWkn7RRq9a5XdX/eQKS2Q0wWWU8rEZLtuz/Id/n099OSXBIz4dIhyOpG7j/u+z+G/vqKVqquc+IT5+qqSWb5nqdPLFTUoKvIp5RvGhGB826D8M/hp+lKooB4HwJ503F2JHJ+TGIIK01KVlLPLT1kLc8MkOxQjvnrj1ztqyRy0PFc6QT/VaXiULnlRuWCv+R6K/sDg9tViatlqY/DgTlj9MEJ88dW+Z0ybcahDLM7ZUg+MzcvIexB7H5b6ys0x/wDcT0zWvWKp8t/UJIr3uEdU9HUQNTtC3KyOuMEei+vud9cwUjBTLKRhtudyfyHr8hqwUt7oLusFn4lqVSvVQtHd3iwrnoEm9R6Mce40D4gtl5ttykpLgpjZfhcNkOvYqegHy1Si/d6QPVL6ijHrzlZy1TTQ5SJcyY2JGT+C9B8zn8NQpfrFQS0rlebrg+Y/M6l09JFDF49SyQRY+J+/y7nUy0U9ddKlaawW6SSRzgTSR8zfNV7fM/nqX6yjT8udzStWkv1AAUbVkKG2YjHNGiA9OZgufz0tadZ/oYlqqY1F7uIFS5zgqZSPnggD5DOlpSfHWzwoh48FrxyxmhBSxyxwuux/D07Dudeopf4hjH6a7BwSsYGfXQ+Y8AxOfg2ABY9Mdtepsd/M57aQYJkLu/Uk9tdxISCcddznrqSRBObpufX+2nVHKvl699IbZVfxOu0A6DOe59NTOJMRtUw2cb66zuVU79z6a66ghdh3bSVAFGc9dhrhMgE8TAXqQvf30ieY7jAHbSI2B/L/AE15uWAxk/pqmZfHERJJ9uw9dLfGx666KkeUddIL7j31zMgX5nKqcbb+uveUdjtrrpsNhrwg+u2pmWAxPCNsDSTqQNzjXoB+Z9+2uo15M75PrrmZIlTGvBsMa6bOeXP46513Mk4OCT2x0HrrwA5zrog5z+Wugvb89QGSNEbk/wCxpFcdxp7kHQj8NcPjp+vrqwMqRGSufXH664bGGJIAA3J/300+RvtkevtrFPpg41ku9fNwRw3VGNQeS5VibhRneNT+hx1O3rrWtSxwJlYwRcscCV36WvpNnu93Np4fCz2emYiocHH1px3U/dXt6nf01B4X4lhFAlO6SV9qSTxBTCXw56OTOfEp5OsT53x8LdxnfQG8cLy29eel5poEHxLuy/PGgQ8VagTQy/V6pdlkA8r+zDQmp07HJ7mun1AxNrREl5b9brrFG7PyRXdEEUUrn/k1sfSCU/e+Buv8WrXYuJ3mne0Xin/Z13hADQybLJ6FfUEb989iRrEeEuKKuiuDPTutHXsnhzQSKHgqo+6Oh2dT6HcdiDrRrdNbOJLctHTUk7tTqWNqWTmq6IDcyUMjbzRDqYGOV7eusKNU1Bw3Il9RpU1C8cGWfiO9U9sp8Piadv8ADTv8z6DWdXCsmrKh6ipkLO3f0HoPQacvFNW0rLV1NWLlQ1BxT3KPJWQjqr53Rx3Vtx7jfTFLSTVMvKiltxjAyPbXuPDLaGq3qcmfOvGadTXbscYHt941EjStuPkvrp2aJoZDG4wwG49NWhbfBZLYaysKmpb/AAovf1/11VZpS8rOSWdjk50yqt8zOOootoNYG7v4nJYDOevprulh8VyZD0336KPfXIiI87EE68yGPLzYA677a05MxBwZJmkQ7Ix5e+2M+n/xqI7HOe2vWbPlG2NNO4Q4O59NdAxO4JMTsACT002FMhy+y+muokLyAyHlycZPQavvANotc9W9HUsoubxAxxSMCOV4weZSCMvhtlztjJ6bY33CpdxhWnoNjhQZSEBQgqeXHTHXUa40dPXDmLLBU9nGyv8A5gOh9/z0b4sgpKG8TQ0qGKFdljLczpjIwx+9tkgbDOq87k99WVxYoYS1ZsosIzA9VTTUsxinjKsN/Yj1B7jUfl1YomSWMwVSCWHrj7S+6nt8uh0OuFuenTx4W8anP2wN19mHY/prVX9mjJGVxlYNPdT+fpplosHmRsH10+QRk65wRkg41sJopM9ppwMq+zjudSHnGCW21BZebfXi4A3JOO2oV4kKKTmS4laoJdjyxjUpH5l5IhyRj06nUeBZJmVVDMeiqO59NW7hzh5zNzSRpLOu7Kx/dwj1f1PtoPUWrUMtN9PU9jYSRLLZ2maN6hHw+PChUeaX+y++r/aLRHCI5Z1VpVHkjA8kXso9ffT9rtyU4ZlBkkcYeRurf2HtozBCAPXXmNZ4gXyAeJ6fSaFahkyKkR3ODqbQUryHw41ywGTvgADqSew9ztpxI15JJ5ZEp6WHHizOPKmeg92PYDfQrimrest7UVATBR9Wfm3qPTnPb2XoPc76Q06azX2/Cj3m2u1yaOv5b4kTiLiyOijehsEoebpJXL0X1EXp/n6+mOppP1wr5WYt2yeuuasSRymLlZHHVT11GG5yca9fX4Zp1p8lB+vvPn7eM6ptT5zHr29pIAMhLNnHp66rH0hXD6rZ/q0ZxJOcY7he+rDHLyDpkay/jG5ftG9yMpzFF5E/D/f668/Z4adG/PI+Z7PReKJra8rwfcQKsbSzJCgyzsFA9z01ark626zCGM48oRT6+/4nJ/DQzhOlM1bJUsMiLyrn7x/sM/prni6r8SpECHKIMDH+/wDedZ5whPzGYGWxBtvjMs+SM8xxq70SfV6Uch6Dceuq9wxRGWpU9VQZ6atC8qAhx0+HOtaBiBahvad0UHjfvZMgeh66JrGuOUKAvYag07+bmb4sddEYCGG++tHg6xpqbC5Ayp1Ko1ZCObf39NSoEGMDpp5oEjjMrsFQDudLdTWG5HcLqbHclUgyAf007LJI8TClKbYBYn19PXQNXqKklULwUnc/af5e2pMdzpKcJBGzMAME5yB+PU65pS5O3GZnqXrQZY4kXi2qitdhq28QfWZYyi/eJbbP651ltLu2cdCNv11bPpK+qq1OaeR2knLO+X5hgbD+Z/LVXoVIyQObG5/n/QfnpixVa8D3k0oycyTWt4VrYAnMjco+Q/8AjRjgbhqa43K2PMo8GafmKg9YkBeRj6AKp0FuiMUgp13OP16D+utb4WpY7Y1as+Qaa3RU0flPKrTP5iSOnkiYep59DIS1yqPczTV2CuhmPxDNlsj1niVc3LFBu5GcKo9/7ddey3dYGo46aEK0EL45Wx55HJPuMLyjbf3Guaq+1FQjRUrGGBRyBgMHHQhR2279T0zg40GnnVp5mjX4nOB6DO2vWVoz/XPm9tqV8Vd+5j1xrmmppPHYu3OpHTAAycAdsnVbp1mrKiQ4PLk9TorVrI9Pv8byAY1JtFBIY3ZEJI3UdgM7Z/PSvWlReR8CPPCw3kbm5JMI2bh6Sor6Kk3IZEdsdcMSR8tgD+OtF8KSwNQyGnKUy1SMVC7eUE5/MDTduFDZbnW1NQMOlUtHCrjlACAIPcnC9B652G+oF/4wkuBQmPk5Odo1dsEZH3Rso/M9dz2H1dtllWAPSBCdEtdVuc+omO1V+NTaYKWmKgLGTLyvklmJO/4Y20ArFZoRnJLMTk6ZtXL9UeXGCXZht7/6afldZgEzghen9dee27U4nogQTzB8kJc8ijf17aiyWeOqrGZ0BZY/KSPfl1dqS0AWx6qYYAj5lHr89E+FuGnu9wdAfAiQRRvM48ibAnP/AHfqdas+wDmU27uJntBa5KeRPIXc8wUe4A/vrVeGpLRw7XVFZemiDIIKYLM3IpRKdCRzHYNnmOCcnGNC+LloeF557VSSmSujfaoAVsrjOx+zuBtuT7ayTjK/3W9X2e43OVTM78xVUCoNsZAHyGT1ONydEPY2pIXPEF8oUZYdiaPxP9LXg3Wrp+FYWjoKxDE4qFBODnBUDoRk+vv2xktFVvM8oZix5i2T11GhYyVCMhIcHPKOp66k8NUM1R4kr7Rh+U/M5P8ATRC0JWABzMDczZJjcsK1k6oBhtxkDpsRvoFaKe7W6vnqKEDxohiWFieWZA26nB9gQRgggEEEAjQ4aBVDMi4IG5x11FajEdzqlkQoy8xyBvvysP0Os7qwcK0O0+owMiO267WjiyhjNWpWqhxEzt/iIc/4cmOudwGA82+MNlWEX9qujulGw5YitbHiNDt4fOu2R1BH4b6A8ROae9Crs6eFVopExdR4c643RlOxB75/oDo5brzbeJKWmjqZjTzwVKb83O8L82cZ+2hPf8/NkyBOj6dwH6jEMLkJWE6iatpDLy1ky08u0ixuVHfr6jf8NHqKrhu1oiorjN4U8cipBVP2Gw5G7kYzjfr8zpq40ILl4kBY7kdQwPcHp+Whv1eaGlYQQtKgnU+GuWKk+nqP5a9JptSjJg/3nidboXRyyf2h/hyFprxa4XClTUqi43xlgMfL++isEE63eIRR5cqCrDZUzGRue3TTfBtrkhudsrbhIIVhqopBCp32cHzH8Og1aLvLTUt4goqcLyq/KVX1ErqM/gRoXX60B9qczfQ6AivL8cyE9xT9lLStTQNcAWLcqYDbIMoc5DeU5BznsMncRVSCvpkkBblZpAVB/iJ/+60CuVyBijZVMkZxzKrfD7/6/gdE7JWNcKBZS0f1qOoOSBgT9DuPvbfj89ynOksVDZjiMU1tRfy88yHbIsGupnzvCcHv5SGH8tDpYqhZuelwJVUkKDgdzkeh26djq50lCs9TI8afZjLEfdYmI/rjQWe2vRXanpJl8WOVgAjHlyc4xzdvnoVbQAIWyZlmFJRV9EnOpFS6x8rjdWyoPKw9e+O/b29tvCq1kaU9dKIFnKok53CSoeU/mG6akmyT23hai4gk8I86LFJG7Bkk5Tgq47EAZBB7fLUG2343elS1NPGpYFlfOGDcrZ5vXJI374OR66VYsfJmVh2jGJXKl1pqdVQqao07c5JHM7gZIYbgjHMMHchsEdDqqXJ52vM14s8JjvQmSaTlnJSoiZT5QWyedW2BbJ8xVubfN9uNkqILlEHi5nKseU9G5BuB/wBuqVWUEcNzaGcHwg5TxMYPIcgMD64IOtLdMOwZNLqWXIbuGLXXw3aGG92x5kkibkrqbmIMAyASFPRQTuv2DjqpVift9XRXSvWO7CFJWSSjnlZhuSrAOR7HB9Dy6zSaS72y/wAdzoHRLnEjLUxh+U1bRnBODt4hU+4bBBzkg2qjq6fiOFbxbhHl+UTw4x4LDbIBPw5xkE+U7dwTai8Mvlv2OjJqdKUPnVde4k2zWqarpDSBCGRjCyjc9Nhj5Eav30KUdNS3SSC4hRMS1FPG46sp8pPz2A+R13wdeLXbLcJamSmjZkzI4cDmyOdcliMEZkU8x25QPTNJ4n4kgrb1cqqxStGXiEiug2aSPr16+UMdh123G5WqHLFccQjgKHm3cVcTrwzIlDTViFllBhRjs2QfIT1zv0GTt21jPGXH114hkf6vKYFjX93yfGw3O/59B+OeuqdcbpXXGr+v1FZLNULusrn4QN8IBsB7DA6+um6p1pLkkqtiCpRZUA3Jz1X/ALWyPw1vVUF+qdsvNn09QpQjx+HZHBHiUs4IJ3wr/wCozoTXUFRWkNRB0qIW50n6FG9R/Ud9E+DWY3SWjnhKw1iNCAehbGV/lj8dWW2UvNCixx4dCY3wPtDv+IwdHVbSmfb3mDua7MwVwtVR17yUddAlPdIvM4A2kH319j1I+ffObFSW2Z7jvGy/WIxzbZy6ZwfxUn8tdx8C1N5mR7exiuEPmp5FG6HqQfVTjcfluNaP9HtZQ09JVR3ym+r3y3gGohON1IG69mBz2/TprKy3yvR/aGV0i31CD+HOHMckk6iNdtvtH5+mtMp5rXb7ekTSxIyjmUHrn11lPH3H8FDO1HZkSSUbJIq9FO427ED139u+s4qOI66qqGaqqnkkbfkDZGfX1P46qqW3czvn16bgcmaJx5xo/wBaqKe2J4eH8zk4VT392OfkPUHWRpdXs1ZJznnts7lnZUwKd2PxKB0U91HT+RO/1PjSU1y5iy1a8kyA5Hir1/MYOg9aqSI0cp5idvCT+R9PlomvTqq89wVtUztz1LVaqjxlqKJiZFkXnU58pOO3bcaHtDUzEwxKS0Z5TI2+3b5HGNBeHWqbRU08VyV4qDxM08uf/LsTkI38Bzse2r7FRtDdMBSI6pfKPRhkr+mR+WtEfOQ3tIa+OOoNttlUU0kEqioLkScj/CzAEY39QSv465stK9tq4rc5ZrbUMFoZ328Jm6ROT0B25Se/lPvpPCnC5q5o2qsxoTsB1P8AbVrm4Ro4bRUW+sgiqaSbmWWNl2dSc/zz8j00PdcFbKdwqmguvPUA8K8FlpFerQuepUdB8zqz3/h6xwWKugr4BLRVA88WO+MbenY57EZ1Qo+Mq/hyc8NVVVIfCLLRXCYeaojX7Df+qo2z9oYbrnVevv0hvXj6j9ZlkRjhpCfgProf13TfdXSuI7WcRx09BV8PXRIq14XaS3VlQoElRDjzo3LjEq4BJ25vi651nFyra81S1llmenUjeRBueo2HT+x6YOu51aqeoo66Z1mdyAQ28cinysvpgj8QffXPCddFUVstpuMEaysORwMrhs7SJjoG326A7HTzQbaga7BwYj1gawiyo4Ilt+iPjiKxzwcPXScC1VLctLKzbUkpP+GT/wBNiduysSOhGNpr6sUkSytGzKZFRsHHLnudfMV+tUNEJFUrU08+VDdQTvsR2PtqPHxLxjdGtlmlutZIKJ1FGocJ4hUll8RyRkqB36gdyDq2prWv1r1CdFqi67X7mp8dfTLRUs9TbOGIlq6uJjHLVTgrDEwOCMdWII6azaC03ziusW63eqmkEzcq1VShPMfuQRDdj7AfPV6tvBdHxBxZBeaelpHkrozLO0jl6eCZcB2RBjxObPMNwDgk5zjWm0tHZeG8SZesuci+GJGHPPJj7CBRhV/hQBR3A66QanWBDgcmNEqZ+ehKZwZ9H01ooaip5DTxyQlJIpm5p6hcHZ2U8sfU4VckHq3bVqs9alDSUtk4ftgeSGMNy/DDGD9pmxjfB6ZYkHbvotS2u7XR1qLjK9vplIKU8L4kb/M4+H5Jv6sRtrx6I2qtVKYeFRTAKmekZHXHy6j5kaBG/UD1zYIKupw1jamWK43JhX1RbmQsMRQt6om+/wDExLe4G2kGMrMJCTG+zZPxe3y089U8MpoZJfHZN/EJ8p9xpnPt+PYfLR9NKovEHtbJ5kWMmENSu7oo80bE58vp+Hf8D21FaqWMtHMeVwcch6n309WluZVjGWU5U+vqPx1G+rK3JNGCzf8ALJOTjqUPuO3zx6aLQBTuglrlhx7TuEzSZLfux+p05NEWiBjAEiHKH19vx0kkQxc7EDA30Fq79LUTmhskBrKnuw2jj92OtTgcwYE547haW4U8NKaqZuXlUlgeuB1OPUd/z9dCFuN2v6k2tPqdD9qsmGx/yjqdcwotHJTrd66lq6x6guikYWOXl2VT32zseuehGdd8l5vEhMpe00CkKFQgzMATjlxlYxtt1b0K6Buv2cLzDEp38meU5tdlqjTUEM9xuzrkuQHmwe++0S+5x/3am01or6uX65da0RyhT4VPD/hpn77EZk/RR2A66fi/Y3D1vk8MQ0sKeeV2kA3P2nc9SfU5J99UPi36R5SrQWKEEn4aiWPb5pGev+Z/wUaBZip3OefiG1Ju4Tr5lznvEdttPj16NTrC3hJHGpkLn7IUADJIHsMY33GqXeb3c7xI0RkloqVtjBDJmaQekkg+Efwpj3J1B+jSbiC5V1ZFcIay40dapNS7MWdGx8eT7AbD0GOg1rnBXB1np6aOpfFY/wBkOByr8x3Os7GZwMdTZEVSQBk/MpXB/Atwufh4iSkoR08nKn4D7R1rvDvC1ntVOY46ZZZGUh5JBliD1HsPlqTVVtLQR5mbB6LGm7H2A1XLpfqmbyO31SA9I0bzt8z/AEH6a3pYou3PE7sVeSMmC+IrU9ruMjUeZIlGfLv5c/Cfcb4/HQ1ZJa2MNHzQREfFjzt+H2fx3+WrPZ7hLBRziqos0TDAB8uT/vv11Tmr4EnqJKMpUKkmJERx5CTs2T29T7H30Zp792VbuUsRRyI8aKn+ryU7xjwn+PJ3PuT1z76EUspgqGgeQyRndJCCA4+8O23RsfMaOrRtUDnqnV+4jX4B/c+5/LSq6KOohMbkq4PMjr1RuxGja7cHiDFcwdVU5lUOj8sqHmRx1U+v++oyNZ3xnwtCss17t1MseDmvp1XZCc/vV/hO5Ppv760KmeSGQ084CuhAIHQdcY/hPb8u2naim8TE8JUTKCN+jA9Vb2P+umFdpQ+YsFsqDrsMpPAl0WqK2utYPzeWJm35h90/01pVJAkSKiKFA2AAxrKuJ7OLXJ+0qBXWhd+Vk700n3T7ZOx9x6jVz4F4k/aNOKWofNWi5B/6oH9fX8/XQHiem3r51XXuJtodSVPk2djozQbPbfrMg2I1NruGhT89RTkc2M8p6Z7/AJ+mo1grmiw7EgHsdHKi8wNEVGC3oNIEIEZnBGTKdJEPDMmOUZw2ex9P9+uhlZWqhKwKXcd8aKXbxlMtSkRNOR+9XONvX8N9+2fQnTlop6CSFainIlOcEtsVPcEdjqxAVc9yqtniBaO319c4kncpGffH+p1YqC309PGABznplhn8hpm63igtaMaqYeIF5/CXBbl+8fur/ESB76xnjz6aQZJaDh9PrUnQiF2ES/5pRhm+Sco/iYazVbLztQTrsqDLHE0e8V6cOXgSUVXTtDM4SWndthIThVJGyE/ZJ37YI6Zb9J30q3g181mo7a8c6gc4nTECZ9F6y/Njyn7nfWa137a4jqlnvNZJUmPJjhixHFCP4VGAu/f899Wq319FfYabh+/VcbXKMctvuLk4kPaKRts+x7+udegp8I2hX1I/5/WKX8RU5Wg/qepU2o6+81ZuN1rJa6ZerzN5EHoM7KPQfkNSjPRUeEiCysDjdfL+C9/x29jri9JdaavkttbD9VkgPLyEDA91A2x764gtywqstZKYid8MOaRvw9Pc4GvT01Vog2+lZ5/UW2tYSeTI1TJVV8hWV2CnYDqSPQeg9hqwWO6Q262mw8TOaiz5/dHHNUUDH7S7fB6qTn00ImuSpzR0EfhtnBcHLn5t2+S4986iRUU9Y/7xWcfFyqMKB6n+51LNOLFyoxj3mVWpNRwTuz7QtxTQXCyyxxR+FNQ1K89PVw/4c6dt+p/y9PbQqmo5KhjJIQ4UZ5jsqf0H46LWa809iomtV1zcLHUPmSBBk0zf9SJievqBsfXS4ptVZQJT1NHVR1lnnHNSVcYyhHoVAwrdjnfVKL8HYw9XzNbqAw8xTx8SE0lJSIMlZX+ySCF/AdW/T8dRJpamswd0wNiQMj2A6L+Gn6G3LJG07EAfamlbAG/r/Qak0S/WJhBZ6Nq+ZiAJXT93n+FftH89d1Gqqo/91sn4mWn0l1/Fa4X5kJLTG1KZZwkcJGWklOx/qfw1ZeEK83CBOH6ijuF2tqKfAqRGGmpv/wAGvxOg7jfHUas3DP0V11wlSs4nqpOxER3I9gOi/jk61Ww2S32SIR22mSnIx51+Mn1Lddea1nirWtlBjE9BpNAtAwTmZDwl9G9vq7y0l2ur1QJ8Sn3z4yeqt0GOh2yPbWvWa02+1QGmt1LFTx9+Qbt8z1P46V44chufPPQKkFezc7RA8iTt95T/AMuX36HuNQ7PdJI5/qN1DRzq3IJHXly33XH2X/Q9Rpa5Ng3rD+uDDy5AwCTpa96bdNLQ+ZIB3bygfPXhY45Y9h3bSXLbKCE/U6fjjAHM3bpp9JOIogfbHXT3KSCq7KOp14uXyccqD004qgLvsnYeuuEyTxV8uF6Z3J1yuGBAyF6fP5a6OXz2T09ddDYgkb9h2GuZnZ4AAASMeijXhO5JJOvX6nvpDpgdfX01QmWUTwDmOw30gSAQMMT312Mbgf7+ekFGDjOO59dVzLTgbDGc++veXPfONdcgxzbY16NczJONeAEnY5Ouwvp1OvVXGy9D39dTMk5C4PXPqde/oddOMDXDDPfGugzuJyd+u+l312qlVyw37DXiqWJzqZnJyNzgH5+2uwuOg+WvVXcjXW69Nyf099dknDjAwOvf2GuCuOg+X99OZwCT0z37nVF+lD6Qbdwg1NbyJam5VjDEcBHPHGTgvvsD1wD1PsDqDjqSVj6cfpFmtJPCXDUvPeqlcTyof/KoR69nI/Ib9SMZlYKSC3UIjRgXO8kp6s3fRm6Wazz8WVtRwrHWzx1JMkn1mTxp0HVi7Y9cnv2ySdPz8JXiVFnaimp4WHNHLKpVJB7eunHh1yab1WdmeY8XNmrGxDwI7ZKuklgNI0pppi3laQgxSA9jt5D77g98ddB+JOFEmnlajjNPOo/eQSbAn2/3vqJOXp3eCQcsikrjOcn56mUN3qIaYU8zeOq/B4nVPZT6e3TRt2kV231HkwLReJGkeXcOveUSuppISY6yKTkQ7Ng8yH2OiNsvEtI8P16ZiFcNT10bFWRh0JI3Uj1GrpUUlFeU5iAJF/3uO41T7rZ5KB5FKBCzbREZRx7aRarRcnAwZ6jTavcM5yJp9h4ohuTyQ3eajprjUqFkrJ0/4G6D7K1aDZJPuzpg+uOpKQ0NTw9XVM1soppUgXnrbRUnmqaNT/zY2G00J7OvbqB11h9HNU23KQxtNSn46Zzlo/dfUe2tE4M4xSOhpaaseprbVTvmjmppOSttbesD/d9YWyp7Y7qUe3Stmv8AURi6ValcOMwlxNeormyrQv4kZAZpGXDO243+6AOijb5nfQ1IvDTlO5IydWe7WemuiQXOjqqCOqq2Ip7hAvhUFyfO6Op/8rU+qHCk9Md6vUNPDVS0dXTy0tZASk1PKuHQ9+uvZ+EeK06hAmcGeA8b8Ev07G1fUsSupPIxwB31FzgY16WJ664LZJVN27nT9TPNCdSNy7Lux0ooSWLHdtPUFHJNKI41LMdHqegWi/xDzEjfA/lqr2BO5rXUz/TAITlG+vFnMDrJHIUkQhkKnBBHQjUm8yU6SYixz75A6DQaVid8766CGGcTgrKt3O6qokqJ3lndnkdizMTkkk7k6axgZI214M/Eddg8wwTqYxNZ0V8NVPXmXONeQytG5dSc9MdiPQ+2kVwoLHGmZX5Pl76nYxLISDxG6ygiqcyUgWKU/wDJJ2b/ACk/yP4aDurKzIylWBwQRgjRaCKetn8On2XOGc9B/c6LVtspJaZYZnf6wgCrMdyBv8Xr/T9NV84VkAx3RQ9ibjKeBg6ft1BUV1QIaeMsx3Poo9Sew0VpuHa16phKUipk3ao6rj29SfTV1sNliWARRQNFTHcq3+JOexY9h7f/ADquo1yVLx3CNNo3sPMicKcOIn+C+e0tUV/NYx/X/wCNXagt8UEK09PHyQqc/M+pPc++n6KlEaLEqgKB2GwHoPbRSONRgLknoAO+vJavWNaSSZ6TTaVa1keCDlG/TRCio0ZOeomSMMpaOLnAklHsOw/i6dcZ1X+JuJ6CwOaEGKpuxGViO8cHu/ZmH3B0+16HO6q71tTcnuM1ZLJUlsmUtuf7fLsNW0/hdmoXexwP5gHiHjdekby1GT/E0k8TVluqGo+ILTE1tLHw1hQ4iB+fxe5O/vp662mkNokvPC9bHNSlcyU7bj5Y7aAWHjWGtphQcQQCVMcqzhdx89Tbpw1U2+ie6cOVpkpJBzOiNkN+GtxV5bBcbf4MUNcb62ZTvH/9QlTnrYZ6WcSIkcqLlAwJGeYDC/2O3XQXlXmOpFU7TTM7KoJOSB66aOAOuvQ1IEXAnlHsLnmCeLZ5LXZppZFKO/kQHY5P+mdZRIxyWJ3O+rl9KF2grK+noKSMxxUkeJCzczSSE5LE+nQAdsarVkpxV3WONlzEvnf5Dt+JwPx15rxLUG2zaJ7zwLRimjcezzLHbYltlky4wwTnfP3mH9AMfhqohzUVjSNvvqycYVRipVpgd2PM/wA/940DslOXlVR1YgnS63k7R7R4CVXJ95beFafwqXxMEF+mik6h2IPTXtMghgWNceUa81tWMQBjujSRNHuTlT01Po2IIzuNRhk7YHpv0OnRJ4Cc4Vjk46dP760PMoMCGY3SJRzZZydkHU6kJGcfWK4rhfhT7K/P1OoMM1PSxeKjid3GQR1P9hqJNUyTvzStt2Xsur6fQtacngQPW+IpQNq8mPXOr+s8yRArGev8WhRRkJIyfbUwAd9c1BRIJJG2CqWJ+WnI0tda4UYnm31Nl7+o5zKDxLVmovciBtogEA9O5/U6ct4BRM/aIz/P+g/PQgq0twaZs5dize+dHqTEas+QAidf9/Ia8zYSXJM99p6hXWqj4nEtWlLeo6hh4op2U4Uj4l37g/azq38K18k4qKyrI8erkBG2AQoxjJ3J3PUkn31QljaVmZskklj/AH19BcJcF0tw4Tt9BPHyyxwLJI2MNGzeb8fi1WjVLp7A7DME8S0p1NJrHEADmenKxKcAZb+/y1MsFpqK5iwXljBALkfy9dWUcPNZIaikUPMk5hpY5yM55mLyZ9PKijP8WrZLRW6ycPTiXDVcMTsFUgYc55QSeh5iNup9Neg/9URh/T5njF8HdCfM6EplHw/BMKZaibw6cKauWTG4Vm5I1+Z5Sdvvba8ut4tpcUVmpTDRQ+eV5B5pGRsAYzsOYfPbtqDd7x9Wj8MyHBjjjyRhgETl5dicd+m5zucHVcgk/cPjyq7cuBncZJ/tt00orD33Et7mOiy06bag6EIz1jVLRoC/hxAhQ7ZIycn5ZOTj311EWxtuzBjv36AaiUsRdxtgZ7d9GbbThq6FSDyrgkfIg6deKAJo2AiDwbL65STC1lpj9Q5pN28234nTXgg1c7EkiKnaRT0w3Lt+uNWW3UEiWscsTMRGSSBoPdPDpZ7ksSPKVp1BDjlxhoww9fUZ144uAuJ7wDJmo3KOgoeFxFPyFj4KsD9ledckntsDqm3Xi+ueGWloHakileXxTESFlVyTjlOw+fXp01VpbtcLlSsaqclE5isakhVOCM+59zk++oltr0nUpIeWQHp97WflMWzOFwozO64u5dyxJCN11WpqNqmUhFz/ABHqNXDwCYnLjZl6fLf+mvKO1ySRIsUbHIOyjO/MRrdWG4DqVIGJS6KytFKvhI8k7tyrjcknoBq08E8O1ddE7pCwRpyxJ2GBnf8AXWh8H8DPLdKeYtAjw1InWJj5mCNnA/i26at/Astg4foaKmuQiR3p/ElEnWIsftA/D3676vfqycKkxr025stwJn37ApaGz1bSIHnFM5DsNs8h6D+us+4yu9upJ/3Uvi1jwxBl5CCjGFAQQeoyNjnG/fprQfpz4gtsNx+oWSpiqIZQA7jdUzsQB0Le5zjtg76xGGiea6zSyeSMSE+53/QaI0lVlpBPZmGqtroByeBAkrSS1xMjbseUj5g9dDaNDTWp7hThFqIJtmKAgqRgqQeqkEgg+uilYEStJ2yJBj8/976jhQtir12P744/I/21rrahtCn5hugtJyRLpwbxTFWUop6hmjUYBDEloCfc7shPQ9cnB33a6WtFphJMxwq4bI359jgjWFzw1VDVePTy8k6E8rYyCDsQQeqkbEHrrQeB+K4p6VqCq/drgB0J/wAEnowJ6oTjBPQ7H10AyWaY+rowt669QuV7l2uN6jpoMsQuCMKN2b+w0X4kqaNeLxgmmg8RjC+AUBLhvNtnHKxxjcHGqzebQKiB5oAPFxuMfH/rqdfaatqLbRV6LiGOGJpBy7qTEMk/+39NMa/KUox9xEOrW7ayr7QLd6R4ppYzzRy08hikikIJJzhgPXf/AHnqX4SgnFPDM8DKn1pGjLL8Q5WG2fy/TXVPSRTXeWaqT90kjTBuTI5XwQx7YBP8jrUbdbIbX41MskBqhhiMeIQDuGDd+uPUa01utWtdoGYs8P0BewvuxiA/qVwqaeaajo3inCkFGHL4i83NlR17Hr66i8SUElTEJRE8EtOzgh1Oem/XVgu3hCnrKirlE0cQzKOb4f7k5wPnpumudpuVXNbYVqIm8LI8Y8xfKfGP1yPbOvP+UbMsonoQ230uZS+I7hUpw1b6FpHNHKTKRnI5+XlJ/MPqv8NvJDeY3gOXfmQPt1II3B/lq63i0rVcM09PER4kE8i+bsAxP831T6SlFDWo4cM6yE8o6phtz8sHVUs2ETrp8y4WC/Q1lHRz1MsUctNUqwLHzIG5VK+677HOdt89T7xRw3T11uaot0GfDeSPC7cyg5jP4Ly9ex1VKymkorkUpyFZWcoTuAFPRv4Tjrt8xvrRuDq/wbXUUld4KulUQyqAOQMq4YYwOTBB26DB+RFV2eJgVycGZfxBaj9ZoWlI5qiJJVkwTyty/FtvuOVtt8ttrniSGm4VgpuJqGoghuaCNbjRrIrRVoC8jOoP22Ks2ACGV/Ngb6tXGNOsvDlDJHt4EjwhgdwFbb5bMg/7dZhfqWaoixVE+LTyFOYDGFPpj3G/+bXLdKSNw6hGm1WxtjSxXOlpLzZHvliYTUMiq8kWSWpXBO2+5Q5IBO4Plbfc16hqJ4ZVcDDRsGBcYAP9f10G4cvNz4Tu4rKEF4JTieAqGWYHYkL0ORsR0I2PYjX/AKPOH+FeJYJbvS1RNPkOKMOQ0QPUcx3KZBAxg9m3Bzg13lD1cwizTh/VX1M/nTFUY6RDID54mboEPT8R0+YOjlPQj9mwmdjLJDIWy32Q+B+QYA/9x13eKFLJfZ4IwssFNIWiJGQ8D9vfB7/PVqsPD1RWTotKhljcfaPlCkfaPTpvrth6cdQZDzsgehtdfV1sFTS0skiRSJMWRenKQTv67a1am4Kq0u9xSMxLEAHx4mTzDoQOuCpP5aNU9oFLZqXmRBEyAAqAOVvtAj2IOs9m4sr7bDVvTVRlqaXnoy6yc3OIyFUkjsVC5xvucEHVaC7MVEMsqQIC8u7Xyz8HLzvOslVjzLnzf6D26/PWZ/SPxncauoor9aisbpO5R5FAGD8ULj7SsMdfT3OqpLcJa2Z6meTxpmPMzHAUZ32GpVNy11LV24kSPIniID08RRn9Rn8tM/wAdN5OYur8TxZ5eMCRau50158a529Pq8TnM8BOWgk+0p9QeoJ/XIJhSP5Sykoh3Jbct/f+Wgshq6GtWuoAZZyAjw8vlkXfyt7+np8tWfh+loLrEbhG7uQ2Hhk6xN3VhqUuU9B/QzaykWf1BHrMk9ztNfTJG68q+NAzHcup3H4jbRi0W2mijjmhXxBIodZGG5BGp9lpwtZDyJ5QwDYHY7HRzhDhqrlaamEUhEU7BGbZeVssAD8+b89dawVtkzNU3DAkKlsor0MTQLJGwKsrDIYHYg6n2WzXKyRQ2u4mQ07ygWmuk/5bqcrDJ6H7p7jbWocMWGhtwWeokV2OOR+iq3cEeup3F9VYZbLUUt0jWakqFKyrnGPRvb2PbA0DfcGORGWn0+F9RldS8wWmhSrmjkIY7KvVW7qfkcj8NDrl9JCVNOlNEqfWxlljU5L4Hw+mfT3xrN7pxLVtLLw9NWieIuwpK09KlQfhJ6CUDGSOvXvvWp51pXzCzGUHmBB3z2OtNPpvOUk8TO7UNTwDJXF1ym4jqHqKmTwo3IZAjHII6Nnrzfp7DVcpa95A9O4QVcfxFdhIufjA7e4HQ6I3dhJNHW58OnrF8TkzssgOHUe2dx7MNBblGJQr0gKSxHmjlxup/kQe476aV0BFynYi57d5w3UI1DZiS4Sn97FyxTY6/wAD+2QOX/tHrqHxBDNVNTXehYQzJuGx8LdwfY430xbrhTRGRq4SoG/dVUA3KqdwV9ujKfVceunIzUST1VrnYeGQOXwzsR1Vx7EEEex1bejDA5kVGTk8Q7YLnTXUGpijjc1BCVlIzbCUfEM9gfiVh647aN3PhS1VnPUQ0tTCZIinLDNzrGRurYbzKwIBBz22zk6yvxHstyFRSEvODiSJfgZe6n37g9j8zrWeFq1L/bY6m1SN45jZMKcEgDzKw7sPT8tUKE+k8iaBwPUB/wAyx8J8W3G+CS13HkpL/boTHLOmB44DcqzInfBJDDoCR2IxqvC9uttHFHMoM1RUxj/iZTzPJjqpPbBzhRhRvgDXzhUUtxprsKkyS0tdG/iQVGOYo+4OfVSMhlPUE62L6MuL4rtZ6igqgtPXU+PrNOG3hfHxKe6sBzKfmDuDpVqdGEAcciM9NqQ/c0a6MIKUSEg5OFQdW0Iv1RJW25Kc8qSAcyhegI6H5dvz0Ojq5ZZMVL83lzCenMu2+PX1/wDjXUjFs9c+uuVUgYM0fUDn4g8FZaUc/wC6kjbb+Fs4OfbbH5HqNJKhp1KchjZdmU9RpVAMNSJeqSnlf59j+Ow/D31HuU8FLySPKomPliUtgyjsvz9Py9MEooU/aA2PuEkRqACdQJq6nhrWpEljaSVCwi5hnmHf8dCPr14v0ZaiQ2u3/bqqhcMfXkXYn59NQKittlnkkt9mpJbpdXH7x2PNID2LHpGPyPs2uWXonEpXWzHiSqqiqa2Fay/VMlDHuZKOJxmUZ2ct9nb4hv67Z2apLpUV8K0HCtFDBRD/AOsnIi9Mg55pT7ggfxHppyazw3auSru0sgKxKXoJHzErgbkj7Q7jmyBg4AOdR75xvZbA8cPily+OWCIc0hHcKvf2Y4HucEaDsZ2+o4EIVFX6RkwnRWO224iruLmtrCOXxpwC3+VFGyD2UD13O+oLXurltdb+wWF0qqeo8ExiQAgNjALL1xkZAOc53HTVe44t3E/Etj/8Qw0stpsOyGI1GZ6hSfiY+h6cq4XPr10c4Ko6ii4PobXRUYolWqeoqfGX/wAwpTlUY7bdz3GhzeoTAGAf7wlKzu55MplzoeIq68imuqzvWxv5YCmFiJ+5H0BP3jknuTq7cIfRzCjpVXoFmO5iU5J/zN/Qas9jpaaGMywR8rN8UkjFnwOxY74GMfhoslfEhKQKJXGxY7Kp0EPMLFQOfmF8dmFrTQ0tFTLHBHHTQL0VRyjTkNPJBVvNQhlpp/iyucN6gen+vtqBbJxPOPFYzyZ2H2V/D++rbRY5MOQSRnXayAxTMIVBt3GAqm2bGSIku/xyNuT8vb20BuMdutYaqrZgWU48x6HsPY+259Bq7XLPgeFBjnOwGcaBU/C1Oalau4saqZfh5uig9gB0HsMZ751hcjlto5my7QuTKZVPxHxYzUtFG9Dbj5WllXBYey7gfNsn0C6nWr6P7daY5BTO/wBZkXzzNuHP8Wd2/EnV9WNEUKiqqqMAKMAa5lj50IGiaA1fOeYOxDcY4mcU4moqpqKoBUA4UHsfu57+oPcamMMg+ujfEVrFfAzImalB22LqDnHzB3Gq5Qz8ymKQfvF6+49dPKLVsGR3ALEKGM3Sj+soJEwJ4weUnowPVT7H9DvofRzn4CCGBxg9cjqD7j/XRtuu3TQ240pZjUwA+IAPEUfbA6EfxDt69PTR1TEQZhIlfTq6SMsKSpInJNCRtMnp8xnY/Md9UGvoZeHLlDV0skj0Er5gmHWM/dP8Q/XHz1olPMJFzkHbt0PvqHcqSFoZ0nh8eknGKiHfJ/jX0I/sRuNykbZkjkHuDW1bxx2Ia4MuRv8ATOvOiyxKC6qfiH3h6D+v4as0FEsHRizf7/PWH0FVPwvelko6wS0wYmGoBBGO6vjpsRkdwQR7WXib6abLb7aPqx/4wrhokHiSc3cKOgH8Tf8AtbSLxDR+WQ1XIMO0d+5SLOCJplZPBRweLVSrGvRQdyx9FHUn2Gsok45scXF09ms11WmqateWNTIGUMD8BIyqk78uCSNxkbAZRxJxfxPxZLKJp5KGkkHK0aOTLIvo79SP4RhfRRoVHaqOihIm8pAyyAef5k/Z/Hf20TofBrWBa04B9vmYanxKteK+SJP4vm4nu95qbZeqgxJHMf8Ag6cMEcjoxz5nJH2mJOD11FipLfbYf3rICvWOMgYP8Tb4+Qyflqx265QcYUZstRUCnvcKctDVMTy1aAZ8FztlvQ9/zzVRbatKiWOuRongfw5PF8ojI7fP5ZJ16DQ0V0rsUbcd/MT6y5rPUTunFVXT1KiKBBHBnIAXC/PHUn3O+uFtokHi1T4R/tydT68o6n8NSJ6mkpByQr4sp6Myg4+S/wBW/LUV/rlW55i+XwCAcsfQE/0GmIUEYQfqYrLFT6j/AGlptV3o7+sVgu1Y0FziTw7bdJeXmY9opT2z2O5984OqzcLZc6e5S2+4pItSrYaIA+Y+v8WfXXT0EEKMlWcD7USY5h/m7L/P20etV4pOJ6VeHrzU/V6xVEduuTMSr+kMp+0NtifTQX/9u2V9QhwP4ldrcGBGjpaRA0zhym3IhHKvzbp+Az+Go1RXz1ACQgJF1ChSFz647n3On6ix11LcpaGvgf6zCfMG2Vfcdse+u43p45fCgiNxqwcFI8iJfm3U/p+OtrNTVWu+1s/aYJprmYpUuPvIlFbZKh3lwSF3aRzhV/HoPlo1wpclt88tsoqaa9W+rYCrpFwIs/ejyMh/l19NWbh36Nb7xB4dRfZhR0XVIAnKoHsmxP44HtrW+FuE7PYYUWgpFEijHjOAX/D0/DXntd4wbeKxgCO9F4YtIy5yZk9H9HVLX8RIlddKhKByBBHUR8ro3/RZSAFfv5uvbOtc4d4btVkgEVvpEjPLgyEZdvmf6DbRK72akvFOyy8kdVy8iysPLIvZJMdRno3VT00KtdwqrZV/su9+IpVgkc8vVSeiuehz2fo3ffSp3Nw3jv3EYhNnENLFg67EfpnUqOEtt/TTiw4HY6GzL7ZCEZI664udBb71D4Vx5YalV5Y6vGdvuyD7S+/UdiOuj1FaKuqOVQJGftvsPw7nRy32Kipj4jx+NKOjP0HyHQfz11dwORNFqJ4PUyqeG/2F/qVRR/WkH+FIXO6/5seYfr66Wtm5R3GlrbKntZPw59jMWRQgLN17DXajnHM48vYa8jTPnk3J3A098Pmbr2A7aa5mE8A3y+2Oi68yZG26aXKXPNnYacBABA2Pc6qTOzzYeVdz/LXo+7nfvrkHYgdM7nSUc25PKnYeuq5lwIsFm2BA9ddY25F0geYcqjA9de5A6dNVzOxBQBjSYDrk/LS5iAdeD9dczOxE+v4aQUk8q7+p0lXcgYz3OnFUKuB+PvrmZ3EXKAuMZ/rrn13OR1OvegwOml7arukxOD6DXqjlOTvjtr0LvrvAHz9NTdOxsAnrnrrsJgZOu0XG5OfbXRAIIOrSAYjZHL6Z7a56Z5vXrrvB3ycep9NBuKuIbVw3bDcbtUCOIuERF3eQ+ig9TjJ13dgZlcSFxzxlZOEKSGou7yySTtyxU1PgyuB1xk4A6ZJ9R11hd9tD1Mwv9Y9TUXW4O0k6yYb6sucIme55cZ2AAwB00WkstTxPxXcuMquea4U8TgUQljEYjiLYQ+Hk49hvvknc6M2yZKO4wVMsSStFIrcsi5VuU5wR3B1QWAMHByR7TC3LDZKdYrjHaHnhrqV5VeF1hkilaJopGwVbI+IAgEqdiDotfOO+IeIqakguVY7JGohikVSML0OANiTjr11N4xt8V6udRW08cNN4ztJJFCmFGT0UdtCLMbtaLbdGjt61Nv8AA8GaWen8QU3M2cqxHkbP550fXelg3keqJ7aXTK59MF3OhEUeTUR1UYPKssYIGcZI3AO2hjiRIySoYjYN6e+upaqVm8aVWCSbg429NOUsqlGC4IPZhprS7V9HmKbaVfuRqaWSmfmRm5zuTnro/BUUl0pfqlcq8x7Hv8j66kcJ8F3PiabwbT4Dzu3KsbSAHbqd+g0Fvtrr7Rdai2V0fhSwSGN8MCMg74I2Oic03+gn1TGqy/S+rHpkC/WOe3q0kIMsPaTq0fz0BiSeOoeppJFgqCPMf+XN7MD31ebfdXiUQ1I8WLGAT1A9/UaiXrhyGshaqtXKSw5mh+y3y0r1Oiz6H4PsZ6LR+Iq4yh/MRjhDiuoo6ioSnSJXmQJX2yrTnp6tB2Ze49GGGXsdaDHLaeKLQfDFXNFRRg+GW8W5WlB6HrV0o/8Aeg9O+IVEbo/h1fiAxHySgYkhP9RoraL1VUNZTvPUvTVUT89Lcad+XDfMfCf0Okl+meht3R+RHVOoruUj9pcrtb6u2vAtVJDNTVQ56WvgbmgqU9Vb19QcEdCBpy10MlVUiCJNzuSegHqdE7Jf6a7rJQ1kdDT1tUwaemm/dW+6P2bb/wArUns64Vj1xnGolXQ1Nqkqai3mrampGC1dNMvLV28/dlXuvo48p9umn3h3jjcVXd/M8x4r/wCOqT5un69xLTSUVJQ03KjZbHmfuTqv3y8DzwUzAnozj+modXfp6qlCB0wR5mX7WhRy5yBud9ehoq3esnM81fbsHlqMYnh3OWJJOuliIJyNztjvp2OINgRqWf11PpacIuWALnudEM+2B1oXPEFzUrxgsRt6emmuXIyAMaMM4WJwxAYnIOgNXUJFIwz1OwA11GLS/lnOBO5pEVDntry3UE9zfmOY4euehYf0HvqRbLS0rmpriFiUg8rHYf5vU+2i9RMhAhpl5Is4x9p/nj+WsLb8cJ+sc6PQBBusjamGmi+r0oVcbc49Pb++nKWkUIJawskbf4aL/iSn2HYe+nY6ZYWBZBNU7ERE+WP3c/00QpomLNKzGSd9mkPX/KPQf79tL7Ldsc11FzO6Ok52R50QcgxHCo8kf9z76sttgO7Hqemf56g2ml8Rx5dh11ZAtPSUjVNVKkECYDyN0z2UDuT6D/UKrrWc7V7jVAtSFm4AndJETsMZCkkk4AA6knsPfQy53qKalmo7LW8tQfK9YoII9RHncD+Lr6YGc1ziTiOe4hqSlD01DndM+eXHQuR+ijYe530DWVkwQxUg5BHXTPS+BsU8y08/H/M8xq//ACdRb5dQyvuf+IK4ggeHnpauM8xOQwPT3B9dBYpamlb9+TNB2lHxD/MP66uqVkFXzQXBA6NsGI0PullemBmpv30BGdtyo/roVrr6Lv6vHx8GEbNNrac1nP8AIkCnkR0BRgwPQg6K268XKhppaelrJI4Zl5XTOR+HpqsmGSF2ko2Cnq0TfAfl6HUuhrFm8jDw5VHmRuo/005pvq1AwRPO6jS3aYlkPEI53PpqHdaqOioJqlz8CnHz7af5zjVK+kS6qYY6GFsnm5n/AKf11fVXipCZj4fpG1F4X295TquZp6qSdzkuSSTqycI0qxUT1TjeU5/7F/uc/kNVmjheqqY6dMc0jBR+Pf8Arq4XiVLdZzHF5fKEQd+Ubf0/TXjg+WLmfS66wqBRKtf6lqu6tytzDmxn2/3nRrhSkBlMp+FOmq5RKZJGk9Ttq9WGn8GkUtsW3OqUrubJmGss2LiEgQ22TrpI8g+muA4QYzgHr6nXsVQGYow5R2Oj/KPtFSakdGOhcDAGTojJTNHGI5BtjfUe1IslwiWT4AwJ+Q1b56WKqQkKCR0I7aGtsNZELrAfMoZhNJUBjzGBm84Ubj3Ge+pdRCsZBinjqImAKyJnBz2IO4PqNE7hRtGxBUEdNBp6d4eZ4emcsmdjpjpNbggE8RTrdCGBK9x4EdtCeKqgwWabHWTEa/j1/QHU9JBIuQCCOo7jVY44q8TU9KD0BkYfoP66Zam0CksIs8N05fVKp9oBpQWkBG56/wBv1xolMeS3Mc4LEAfLI/oNQqJcPzD02+fb9caIXGMrRRHB5S3KDjrhf9Rrylh55nvgcQ9wDY4riaKGWMM1ZWpDk9AnMC//ANiG19H8CQVlcpaMANVSnwjncAk8oH4ax36PZqahisLR+HJNDDNUMGU8oYxsq79yDKPb1I1cJOKqiiNClsY0z0kePFVyWZtxtj4QM9vxJ1vpNEdVUwx2Z57xTxNNNeuT17TQJqxaSqko5Igs0U8m5O/Njkw34em/uNU3jqz11HW1EtNVx1A8IPLAHDIoPmPIexzjI746561r9v1hqTMzFi7FpSzEmQk5yc9D8vxzovWXZZ+GLi6HJMPhgEeZCx5R/Mao2gv0DbxyJnTrtN4ipQ8H4lDAa41C4EstS0hDnI5OXbAUAdeud8dNHae2yECFtn8ZYzv3OSfywOmiHDVDFBDG/Kqs6ZYnqf8AedFLLCJalQ67fvJ+nQZCgk/gdbaWzDgn85XWJmoge/EhUNvWKcu+Nm6e2+jltt0VJUz1VwlVEijiyqnc+JlvkNtWS523hun4TS4UVU89wUYqoyp/dg53A+yNsZOqjcuKausoIxHBT0r0vPGHjTeVWBHnByGOCRnqQd8618T1LXUYXrOIL4ZpU09+M84zNOl47tsFgpIqC2QJUwoASVyjIV3Ujqc/nrL7rdai6tca6rk8SV6dVzygbc6AdPYdTvrwviiZ+4jwN/wGh1KjSUVcx+FVj/8Atgf6a88KxxjuepDkjJntIC1BMV9G37d/7ai09E0Msbx8xd0EmcdM6sFvomkoWSGIkBWJIH4avNh4Dqp7f9enhKxxxqCqncgDGmeivSi/c59jFHiOnfU1ba+8yvcPWyW5U8iOrF1CKOXfdpFQfzOtPtPBEtPbpHiQRz0/fOHz12xqmLfIOHq+qV0WJUkp41XGYynNzuH2z0U+pz21X6z6Z74tVI9HNyqSyB2QAlcnHl3x+JJ9+2g9QvnXE1jiF6VhXWBbyYvpG4tq6W7I8UjRT0pdj4bcrh2HKGOx5Tvn73y21mtZxHcrgFNbVtLyLgA7DPckDqx6k9T3Oo18ustbHPUysGklkyST8R3OdBKeTHOACWzucb6MooVSMjmD3OSOISWWSWsiMjEgOMc3XGf016khqKohpXRPE8xA7Z6fPQ6kk/4yIM25kAx26675JGd51J5Vfp3663tv8vGwzJdP5n1jiBLk4+uukWcCQDJ9M9SdKoINBcUGBhiT+JbXFbl6hiRypzrgDvv11zMc011x2xn821m4cqGf3MZacoAQvxLDcaFWyjDGDsQOnvoJdaSppXpKqlk8GdUPI6jrj1HcYyCDtj8tXSVFkXcfIjqNRa+jD2yISJsrkZx6+mm3iGm21c8iJ/DPFBa+Dwwj/AvFyeGaGswkaDDx5/wR05lJ6x/P4ehPLhl2l7ULrw/b6emkikmmEce7YGQZEwfQ4cddfNl1t0sDpVQuYp48NFMv+/09M6u3BvFFZalayXuGSlUwI7RD7EbKGWSPfeMgg4z5Rt8IHJ5rWUPpmC5yOxPQApqkJA5hviW4S2ylFv51lLQ0/isuCAApAA2yCDkH0Py05wfxDVIZ4qmdnUUxKvuSAuPz2GnOJLdHW0MTQMjyCDCuvR+V87/nqrWKCaG7CJwRFJzwtn7JYFf6jR2k1FbL5dk83qtHZTb5iHkTXLW9HxVQz22KpWincDBbox6jcdf999RauxXC3VlM1SssFTHHG0csSlkLKxGxXcHAG47apFJ4tLW00DtKxZesR+IdTsO3qPx1sdg4iustioo62WEoynmnVeZ8fY37npv31S9W0xPlnKmXqtGtybOGEH2+G4yQmGtPLPGWkIEBQSDBzjYDOcbe2oMlmR6yQxMAJ3KMCBsSpx+GdX63cSU08lNDUmB6wPmnMmAXGD1/EaCcUU9XVQy1FJHEkodJSkaY5gvp747aR2PubJGI4rT0AZzKFxLcpbelJAsQgqYXf6xN8TnmUIy4O2By9PfQT6+0NE1RRlqZo5o2j5WJCjlIPX7O3Ttq1cR08V7eeoiKmZ+ZiBvkt5iP/cTqnR0cos1fLgYj5AyjrnJP8lP561QgHiUevML0d+W40tVQ1BjSIzeMAOqnfmA9snOPQajXCyTTzusQ8VJqZnVlOQSmMnH4g6rlsLC5xMo8rNyH2B2x8tXPgu9R0c1ItW+ViqTFPEUySrKVbBHbHUflpjXeCmDALayGyZxX/RtBLwhUXFp+at8Dx4RGNlYblSx3J2IxsM9tZfZ6+7cM8RLW2tXkSpYStAq83iFtm5V7nI3XuMdwpH0xw5TRzW1oXAkMDloQ24Kkkc2Dtksrn8dZtxHwhTR3eqpI3NPJBUCro39FbcD5BgQfw0qB2lq26jipyqhhCpudm4vtVDxDB4Zen/dVsPxDwnJGR3KhvkRkg4Or7ZuKuHrDwfPaqmaKF6E/uw7gHlOSuT1J6rtk7dNZj9K0nDNilpONeF5qWkkrUX9pWtQFhmDDDGNcjLAjDquxxnKsAdVLilYrlb6DiC1ytUUYQQSMTn6v15Ae24yA2BnlOQGBA10qCz+mxxKastR/XQZ+ZbeJ/pKuNztdZSUeKemZ+ZldScZGcrnuSDkn5jGSNUqyXWSeGphaR5mlkD8xYkt6/wC/bUGkqEaoUSfC68khx09/w266F00r0F6ZJHIKNg9hgdf05tEIorHEzRjapJMsviGMlGGewjXR2x0lWZ4alj4CxsHWMf1Hvrq3WyFKOSq5QzrMqgn0IP8AUaOW+mkkwVG3fbRWk1XJQ9QO3TA4YdyGaGCOqq4o418ziVDjdkcf0I/XQupslxoq83izRc8+MTwY2qU9Mff9PX8iNQsfCNwr2pqulh8SNWMMhOBsd/yBwdHKXhyGnkK1oyRsY0OAPx76rdagBWFUV25yYJ+iuO1X+KCvgI8DIE0bbNE3dSOudj/sHWlXJrXbUnpYXigMiiQDmx5v9cHWQcXT0nBN5bimzPEFchLrRIwVahenOvYTD0GS3cZ3MDjHiaqvVsettlUfAaBZqWshfBdOjrgfAyhsEHJwScnIOl/rsOIxAWlCcSycV/SDSW2WWmhZp6ruinzZ9z0T9T7DVCqeLrlWTeLXS4pSSJKdPhZGGDnuxx3Yk++qOahVQeGMv1yNdRzcx5qiTYjcf7/rptp/D0VcnkxRZr2ZsDgQre4ueOqtcpJEcgkimU+ZSM8rr8wf10PoLk8yvS1aqbjEMsR8My/9Rf69dPz1T1VrjmjyHgYU8pIyShzyN/Mf9o1W7y8cKrPGzCshbKyJ9g9vmOxGrkCo7s4P8zRSbV2nqWukie4W2rt8p/enFTSg/fQeZRnrlf5ars11cgxUicgGxc9f9Plrm0XR6mriu0c3hVNK6vLGT8J9h3U7/mdSOJuWC7GW2qqU9ZGKiGQDcq2cj2wQRt6azS57yVr4zLGpaRlucSC9G0E3izVESynblk3HXo2Psn17dR31Mkd6mlBAMMlG3KY+Y8wXuG91J691YEbDUKBUG7edu5OiURd4PrdKviVlGg8SLAP1qnHb/MgJ+anHQaIGhNA8w8/MoNSLfR/aR7hGHjFSg3f/ABB/Fpvhu6VnDt1FfSeI8DEGeJDgkDoy/wAa/qNtThHAyj6tJ4lDVpz07nrtsVP8SnY/ge+oMcZjdlcdDpnX5d1W0QRw1T5mtXO5RcR04u/jJM8yiRHjGFcY2wB0/pocjVtJUxXi1FUuFOCBG2yzpnLRP7HGQexwfXNI4Zu7cPVmJv8A9kzvmRcf+XkOP3g/hP2h+PrrS6gJLBHPEyMGAY8p6+h/rrIUIQayP8+Zsr9OvU0OwXGl4gs8dxo5mWNiRysuJKaUbMjDsR0I7gg+h0RSYLG/1hhG8fx5O3zB9DrJrdX1vD1ZLe7XCahGAW40QP8A5hBssi/+onT+JfKfs4tMC/t+zper3XQChkQT0iU8/LmLByJXG3Kcjb7JHUZI0luTyCQ0MC7upNuN+kuEktusNN9cl6PKdoo/ct066hXx7NQMLve4/GnR1gRMmSMS/wAKAeZj1Gx2HQa5W5VlwgWg4Yo46SgHSpdCsePVE2Ln+JsA/wAWuzbBaqUJJVtWTVMytIaqTmywxhgMYAGB5VAXB/MXzGtyB18y4QJ9UgP+3uIXepmaW10R3dEP/ESDpkkf4Y9ly3XzDcamVFZw5whaWdjT08abkkgeY+p9T+LH31TPpC+k17dV1FrtlI61lO3JMZQUSE46FurZBzhexHm3xrNaOkv3FtzDKs9bODkSOuFiBP2E+FB77nWSKqnjn7mbbWYerj7TTbFxu/GPGAstPQS/UauB4xPkJICoLrIincBcE5Y7k7AdNAaD6N7wtfNJNLGVWoaKWoeozLKQAwds+blYHt327aNcF8DUVokNTVVD1dUwwxViIx6gnq38tXyLlemCZw0I8hI6p/p/bQtmpNuVqOSIUlG1cuMCOW+WSCz01sknkqIaZOSAP8KemB3/AB1ISVUyzgsw35R1Pz0Hr7hTUMTNUTBe2AcMD7+g9tz7aYtsF6voAgjNHSsfjIyW91Hf5n8xrGvRBfXqT+ks+rA9NA/WGYrhCa0U7ugE+3Ih6H1z7/0HqdT6G21tQzSVUiwUy/DynqO2T0A9hobJNw5wtTcs8gqquUHCfG8nrgDr+GB6tp+ggufENJQ01TLV2aJnc8rHDSoegDDpnvykZJ3JBGbXXecpWvjEtTWRzZC7X2it0ot1shNVVg4McX2T79cfjv8Aw6slhpLpMPHuc/hc24ijO4+ef6/pr3h+wWyyU6xUFOqkDHPjzf6fhozHt+Wgk0uTl4wFoX0rPa2nWajMUXldd0b0OmLZVtUxNFMOSpiOJAe/vqYjE6j1NIxqErINpV2b+If7/wB7aOA4mce8M4ON9chcbY1MhbMQIXGmWGWJ1cpgZlMSJUQcw502Yb6qnElo8TnuFGvLKvmkX19T/f8APV2UY2xqDWwGJ/ET4D+h11WNZ3CcKBxtMz2CYTR5xhlOGHcHXu413xRTraasVyDlp5m5cY6Hfy/PuPxGoz1dOsSP4nNzjKKoyzfIadU3K67hF9lRU4kGvhNPIalNoicuMbIT9r/Ke4+R9derMrKUxl+6Dcj/AH667nSqqlKuTTQnYoh87D3bt8h+ehTxT22ujKyO8Djkj5jsB/0z77EqT7jRKW4/KD7YI4jsdLV0tVbqqMw0dUeYPHIUMMu+HyO2SfkSezHWPDh82KunpLhGIp4mwxbzM/8AEo7g+uw/HX0O6xVMGeqtuNvw/wBjVO424YS929aN8LWQ/wDkpiSA3/oufQ48p/D570ha33Y7mFy+YmMzK5bgqgrRRkHpzZy3/u7fIfmdRIqOepBaQg8u5A8qqPU9vxOpXLBbueCsBE8ZKvCcqEPo3cn2H56j1NZVVYATCRLuoAwo9wO3zO+nNZA+nk/MQWg9Px9p3N9SpEBz4soIKsCVCnsVx5iR67fjqywTJx7b/q07fVeKKWP9zLgKK+Mdj6SAf31WKa1llE9S/hK2cNIMs/yHU/PpryavhppEjt4cToeZZgf3isOhB6L+G/vrl1YbkHLTunuKDGMLPKa3ild/rhMLKxVozvISNjt2+Z11LcghMVCnLnysVbJPzfr+C4HrnVkkii48tzSlEh4opI+aaJdkuEY+2B98dx/TpXY/qVGQlTzS1X/5tCMtt2P3dU/FKFzccY9pf8Kxb+gM595HioKiqk5M85G/KBsPw/qdOSRUMBal5TXVDbGCHoP8zf7+erVw3wbxNxTvyC2W0nJwSob5t1Y/L89a1wd9Hth4diQxUy1NQMHxJV2B9QvQfM5PvpNq/GyVKVDAjTTeEqp32HJ/aZ/auGb5xPwc68SUBRaYA01YkhDBOySDqyDpzdu+24vnAPDHDttolkoKUGpiPLIZgOeJu4x0X5jr6nV2hDIQynzDvoPeLPLSP+2LKFR41/fQH4QvoR3j9O6H+HOEnm+d6WPMbisJ1CaIOpOTrtQBqNaa+C5UxkiBR0PLLE3xRt6H+h6HU9E9emhTwcTQczyIbkDpp2rt9FdaT6pXqAQpWKblyUB6qw+0h7g/hjrrumhkmk8OGNpH9ANH7dY/KHrW3+4h/mf7a7WWByJoF3cSl2hK6yV6Wi6sBSMQIKh2JCDsC32l9Cdx0PrrQaG10sADMBM43DN0HyGu6+2UdbQGjmhHhcuFA25floBQ1VXw3ULQ3Fmlt7HEM+M+H7H2/l8um5CnmdC7DzLYNte64jdZF5kYEYyCOhGuhrk3i0te6WpJMZACAknzaSjmyx6e+uVTm8zEAe+u9mAA+Ht76Z5i8DM8DE5VdgO/fXuwGOgGvdgPQDbbXgBO7A+w1UmXngGRnB5R0Hrr3BbfoO+uiObY9Ne5A6jVSZJ4DgHAGNersOmc65A/2ddfDtqhPtOieEY/3vrpRg9AT+g14mc+576cVeUarLCJVwMdTr0HXmWzgb69xvtk6kk5OdwBtpKMbt+A11jyksPlrpFPxZ1JIhvueuvQnNnvnXXKO413y4GScZGpJONlBOdcnc9N/wCQ12Rkkjb0/wB+uodxraWgoZ6yrnjp6eBC80rtgIo6knUkkXiW9W2wWapu10qFgo6ZeZmPVj2AHck7Aeuvnc1Vy+kjiU8S3xGhtNMxW3URPlwD1PruNz3O3QDXnFPEs30n8UBpFnj4Wt0p8CD4TUMPtN7n/wCxBwNyTq8wizVlIq0ZhtsqKB4ecQH0A7p/LR6aawV+ZjiKb9fT5nk7uY/YbpPbKmKWEIHibmRygYqfkdjo1SWWiv8AWxqbjDS1EzPJO8ycsad1wR65O22qlE3LnOCvr66lUVUYZAwZsegOgbKN/rTgwhHGMGO1VDNRzupQlEOOcdD+Ood2Et1tzWtquSnpeZXMasQjuNgzL3OrnFc7pxQsfDlIlPFFK4lEMaBQWVcZz22HT10FuFjNHQrWNUwN+8aNog37xCO5HYaGSwqfX9UuwB/KU66cO2W28KySV9dOt2aT91SCIeF4fXm5+5PoPljvqlLRVYhap8GRYM8vMV2+WdavVwS32pp6eogjlJCQQoFCKMbAkjv6nQjjK432Dh6LhiWVXtdHOzrCiLzLJk5ywGWwc9dMtPq2UbDyTAdRo1YZ6xKFRVVXRzrNTzOsqHKkZUr+Oj/DdfbZbsJuIVqJ42cGR1YM6juQG2JxtvqRcuH7HFwpSXuG7890nZvEt3L/AIKg7Et6nbb31VzlXCMPOdyumlVqWg7Tz8xVaj1fUP0lrvtkor3xg9BwRQ1Bp58mngklDNyquWYk7KOu2dVeGrqbZPg8wGcFex+WnYah1BQlsHIJViCAeupXEF3rq+02y3SRUoprbGyQeFAqSHmOSZGG7H3/AK76MQNYAh5H7wIgVk2LwY5WUNBxBB4iER1QX4gNwfRh3GqXc7ZVW2Z6eaENG3xRtujj1U9jo7b5HppBLG5WT1Hpo6tVR3OBqO4RplhsegJ9j2Otm0GxcsMqYdpfEhYQpOG/mZ5SVklDGVAkq7fjDRsMyQfgeq60DhnixGipBX1NVNBAvLR3Om89XRKeqHP+PD6xPnA+E9tVriHhypt7mppXeSIDyyKPMo9G9RqvwGaCoMlKwgnPxRn/AAZv7HXn9d4ZsBevlf3E9HptcG9L8GazdLLFVPFPbvqkNZVDmp1p2/4K5juadj/hyesLYIPT00AjPNzxlHjliJEkbDDKR1yNDeFeJJIFqaeKGOWGb/z1qq8mKUj7W26uO0i4I75G2rjKLdfqJ6tKqpkFMo5ql15q2hHQLUKv+PD2Ey+YDY56anh/ilmm9L8rBfFPB6dau5eGkOgnpli5V8jnqG6nT1VMkKlmfAA0IuEVTQyJDXRoGdA8U0bc0c6Ho6MNiP8Ae3TUMy1FbIKeElyo3ZuijXrdPZXcu8HieOs011L+Sy8x24Vr1EqwwKWc/Co/nqdaLSkMYq6t+aT7OO/sv/42n7ZRU1tUmRDLMQM823Mf4vQfwjT7GaoleeaTlRAA7tsFHYAfyA1LbsjC9Rlp9GtIy3LTxTJUEQIuw6KNgPf+514aqmpoyiSANnDVGM8vsg7/AD1Hrq9Aogp0Kxvvyk+eQfeb0Ht/86hOrTHmbGBtjsB7aoKzjnqbtYAeO5Y6KJEjUwnMLnmDA55j6k99F6OFucAZIP66qlpqpaE7L4sBPnizt8wex1daC50FLAj0Q+t1sv8AhLKmEg9Sw+03fHTpnPTS/UVOG2gflDqtTWEyxxiGnejsdCtVXEhnGYoEx4k3v/Cv8R/DJ1TOILxWXeqElQ4WNBiGFMhIgewHr6k5J9dP1ks1dWTyVErzStuzsSSf9/podJB4TkMRynoc6a+H6Cun1Ny08h4x4nfqvSvCf53I/brpqdttup20/KvIc9QdQ5GLSEjcdtMrGwMRAq+85IwMalUddNTEBfNHndT01H12oxoWypLV2uMiE0aiyht6HBk2rt1JdFM1Iwhn6lT31XLpRNGeSrRoZE+Fx1HyP9NEJ6xaMc/ORJ9kKdz/AKahg3TiCpXxD5E2GBhV/wBded1KfhH9LcfxPY6HUHX1+tMH9jBn1qpaFlkcMiAksFxkDudZzd6k1dfLKTkcxxrTfpF+r2Dhr6rCQaqsPIW7hR8WP0H4nWSsSF9zoG7VtcuSY30mhSg+kQ9wVSGSqlqiNk8if5m6n8B/9sNcca1ni1PgIxIXYf7/AN9dHbdGtrsg5/KyRln/AM7bn8ht+A1SpXaprndt986Fs9KhYzUjloSsFIJJ0jIyBjOrsGWOMhANhjQHhunIhMxBydhouz5AAPTRemrzEeuuGcTosW3J0htvrlSTtrrm8pB6aZooWImsLGG7LS1hts1zWJ3p45VhMmNlYgkD8QD+R0ZhvOJRzxiMbA+GNunU6GWW8XK20sNPS1LJDHMKgRFQyGUAgMQepAPfUcDHxZ31r+DW1SHH5TAax6nDI0uAEdVFzKVKnfbodBq6iMZYhds6hW+tlpX8pLRk7qf6e+rBHNDWQhgwzjf1Hz0j1Gks0pyOVnotJrq9WuDw0qdbSMMyRHDDqPXWbX+Zqq9Tv9lWCD5DbWr8USw22nZ3kRXI8g7k/wBums7gihio6tyC0wCoGPq2c59OnTrqp1no25jHSaNRYbMSNboSzIuQMsP9/wD2unr/AFO0VFHykRMWJK7gkAYz6bfprmkLBWKcwYABMbnJ6Y/Maut64PS422Gutq8tatOkk1Pt+8UjAdDkgqfvDvkHB6gu4yA0ZlPcSH9G4l+r1tZI7O7FIQ7MSeVRnA9h5dWmPneTbck7agcJWuWk4egWRGR3cswK4OWJx+gGrnYbNJHXU8s4xyEy8nfCKW/pr2Gl2U0D8p8w8R3ajWuR8wLardUVkvLDGTvuTsB+OrDSWYPQtS5DtU1sUQYD7KK0jf8A3GrX9H/C4rnpqF5RFJVAMCdgBjOfx/p76j8VV9JwLfobfXUaVn1eokkdYpOUurKFx7DlHYZycZG+lviGuyprWH+HeGlGW5uoX4X4Ppbhw/cK+CuhWppo/PG7bheu3p8tc2W526mt8lFdbUahBD4SIMwyRMM4bbcHfqd/l01mlx4ghqb3WSWX6zSW0szQws+SqkdDjv8A7309ar9OpSOskeTlUKrk5IAGB+GNJvwN9gLL7e0dPr6KmVX4zxObpFW2t5y8rtSTL4YmjyFYEjCuOxz67Ht6ajUyMaM8ozzSDVzpys9NIskaywyrhkYcysu/UemhptiQDwaeIpGsh5VyWOM5AydztrS7WtbWtTjBBldN4dXRc1yHgiOVEDR25snLMo/vqRwTZzdmraUvyJzR5IGTjJ/toxVWljTok0sdNFJKiGWbKovXcnsOmuOGq+LheS6JWKFZJIlDNspwpOQftA8wwFyT8twuZgM7YzD44lvpqC22qYxHAijqYInwCScxyORtuTsNtErX9KFqoYpqN4TOuTgKRt8z0/DWOcRX6tutwkmDvDHLKZPEXKyFSnJy4yQBy7Y367k9x4ZIIwFIVemqpWWb1SyuU5WE+MK1auaasbABDMABjHXAxrLzUZOWY7ds41dr2ah7ZNK3MiLTMcn4jsTrOmlCsEU8zaO05VGJMwsQtwI9Vzf8IgORlz29hrihdjHIEGABudR55CKaHnHQv+OnraWlhkI8o2wBrfa1z+mY2MtS89x23xj6/CVy+JASfTRGyDJkZt8v0/XTNqTFahx0JOp1lQfvCD1cfy1LavLUD7y1Nm8kyp3HH1p9tvFG346ihlaC85JyAP5tqRcTitkbPSQd/fUWPyi9fwr/AFOidccVqZrowSzTQot4Ub1Ufy06/LJb2XPSQHHce+h9E7NDD4rcoMakb+2iUChqKcr9llPT305p1a6ivY08Tq9JZpLS6f3kWanSSkMcoBDD06+415x/HTzcM2WpjkYV9JTRxxTxg8yGNuXGR02wcaI00aywEMucfnqXe7ercF0cnKCpeWJsDHMMhgDpR4vpWXB9sT0PgfiXnDDcMP3le4F4sMMrW2vUco+OMDbH/UjHp6qOnbbYXg0KzxrUU7K+4kjkU7OAA39NZx/4cnr46SnpHPiyVPJTTc4Ro3PwkE9/L0zv230Z+jTjeezXf6lWpDKyMeaNk5kkXcFkX5Z5kxkblR8SnzDqa29M9K6rqQcfVNEslqo7fxBb6y/tJSWoVDc02Dklg4XcduZdwdvUY0qi+JTRmK0Gnant0xRpoEISRGwSWGNxzflnYkAaHcY1Et7p/HEySxyIhjmXHK2EGOnyG+/XO+c6p8RmjoLjC/P4iFJcHqCGwT+R0y0bq5xYZ57U0vTnaOZt/BFws88EdUsGKxWAcy+YjP3ewG/bVgqp/F8oYtyZXOc+2sL4M4kioa0LXCR6Q8rII2wYz6+49RrW4LtBP4xDKhQ8zL0BB3yB+OlviPh71MSvIMa+G+IV6isKTgiKphjCNUQiOKdpgxHLjnbHX/N6+vz1X4bbEl5vVvO0cyeKv+USAn/7EHRa708U9qnuMdSxRhHyjn8uM4HL6HfUO1iqq5pamfwlqVpZIiznwxKpXlzvgc/mz6H266ldf9IMJLLMW7DM3qbfLTVyYBBJwFA3yP8AXGptWVp7w8uHMbukzMoyU5gGJHyzq38RU6UMq1RALyjxVJHwvzBsD09Map/FEUtLVf8ADlgFVo/wVjj/AOxI11GODM2QHuaVY+I6W0QmnuldTsylyJM8qOHCyA5A+flAyC2MHVQ4l4xjul0jqI4f+HiV6edpIwOaNu4XfpjPmJzjoOmqHWSPPbnPM2YpQw3OAGznH4jTMNQ0skgY5ZhzE9sjWvlpjce5Q2uo2+0YvlvcVc8M4JmicozueYnBxt7aE8OXit4WuEjKgqbfKClVTOvMjoeu2dwcDIyD0IIYAi0XCVaiOnqT+8d18KT0DLsD+K8uo03DxqVIqiQQdlXtqWYWFUXYOD1JFXa6SsjFxtU7Na5SCqZ5miz9hjtnvhu/oDkBu6U8EbIk0IPjLhZsbhwPhJ/iAH46HUX13hqteaijaahIJqabHMAvVmA7jbce2RggHWq8K8M2fjHhuWWkr1BOCiNglD2yf5Efp0GAux9U2/D4OU6hDgSyy3TgaOqWmMjjEbOF3LL1/vq2WDh+OJv+M2I+GMH+Z/tr3gHimn4Ssb8PXeUOIog8MhXkzzFgytk4BDrIux3Cggaq/G/0hIHMNjXxPEziQcwT8TsxPsOX5sNVUPuyvvLsK1HJmgXW901ptM9MK1KUpjkIYBUYHIzuAPl1OTsdZ/xd9JVbLM9JBCPrQ8kjfZJ7HHVtsHqF36HWa19bVVs3jXKqaZx8KnZVHoFGyj5DSujST0tLcYR0/wCHqB3JA8jfiu34aa1aLGDZzALtYSCEnV3qJq6RprjO1Q4GACdkHooGyj2A0KsdzrbDc5JIKc1FvkDGopexGDl0HY4JyPn7gz1aPlyTzMR01GdakSpUI3heEweNunKR/L+emFmmQrtHGIFRq2DZPvG5niif/gz4sMnnhk7FT0/pnUeV1QeLUyebsB31CrqmOy3Pw1z+ya79/CVGRASTzcvsGBBHt+OuKykKOKiacFGGVKnPOPUf7GhE1pRfLA9UJs0YLb/9MLWK7CW5imkjApKlTBLnsTjlY/IgH5Z1FmgjpK6SndfFJJXlJI5SPU7fL8NDRI0qGNF8JMYJHxH5/wC8aMXY/W6KC5gYkmTll9pk2P5jB/7tXTTWWDNvvLLai+lIMp6dxd42eaKnZlKRnlAjU52Vx909Ce2c9tWDH16zz0hheOst0jSrE5y0f/ViPr0Dg98H10IkVaqnWVd+YZ/HUiKrrYVhvdGQ9wtyhKmNulTTg4Un1K55Sfukeh0bbphQger9f+ZjVd5jGu3v2kVRglgcjt76IW2aSnqI54W5ZY25kP8AT5dvx0wr0tSzT0XN9WkPNGjfFHnqh91OR8gDruIYf10elgvr3CAuhpfB9pMvlOlsaK729H/ZFdJzSwjf6tPjzYH9O4+Q05XoskaVEbK6OAQ67hvQj5jGpFsliaGajrAXoqleWYd1PZ1/iXqPloNF43D9dUW24nmoub4wPLGTusi/wNnJHYk6XqG07/aMd66iv7yXByMDHIBhtjkZ0f4duItHgUVRJ/8ARs8nhwsf/q0vXwj/AAN1Q9t17ar9aEoWLTvyjGVAIJb3GlQVTVbtFWQr+zpk8ORCMlh2Yd8g7/mO+tbrQ2DXyRMNMhQnfwDNPSQRSHHQgggjt/v+WoNDFSWC8JPc+eqsMkplmR2JjpJmOfrAQeUqftbZXPMMZbNattbVUksFnudRLzxtmkqCSDMmPhY/fXY5+0N/XVxtkS3WKSmlDTNAMmPGUZO5I749DtuNAX2JqDtYRkiFBwYZ4p4/sNir4oVdqqpbCtTUxBeRT0YA7L/mbqMbHrqq/S3wxxzUU1NdZ50hoK5g0FDTTFnTuviNgFz39B2A1XpeFKC18Wwo00dJRVbAwTchbwnztGR6nHkY/wCU9s6hXX2qkoKegWRnSnBCuyjxCT1JYdD8t/fXn9VY+ncDs/EO09QcEj+8rFZwnDxFFb79xDAyXOjpxDcI48Zmxjkc/dJGc9+g7DRSjEccAordTpFTr8MMS4X5k/aPz0RsyTUrtUz4EJUrIh6FT/X57nXdwklo5loKCjaeeReaMqvlIPf0P45+Wr2ad9Rh7TtU+06uoSgHYNx+Z7HHFSoJa6VEVhzLk5B9cDvj8teUddWXGqQWmkLpG45p5dlx3Gem47D9dSKDhgy/8dxDVBkzzCHm8gI756scem3rrmbit6uX9j8E281s48vjrtDH78w/+5P/AH9tZjU1acbKR+s4KrtQd1hwI9LQ8O22aa73WQRsGzyTtsh9FB2G/bc+gOvIblxFxUzUvDdGaC35w9ZOm5Hsp/8Au8/5B11NpOEq6ktsdTxNLDds1S1EkXIAIWxjykY27fj1OTrQ6FadaWL6qqLAVBQIMAD5awvU2HfngwmpVTgDmVvhXgS1WdzWVHNcLg5DSVE5LEn13zn8fwxqxXWhFdSGMeWVDzRP6N/Y/wC+g1L13qtY2H0y7ZPchWCtarpminytTCeSVT1+f8/y0UTQK8xSUNUl4pVzy+WoQfaXpn8tvy9Do3TSpPCk0TBkdQynWxA7E6pzJCdNSYtRkOBpyN+UE41ZTtmgMkHABO2NRxNA0piWVef7ud9Cb7dJKRh5T4LLkP2/+dDKeqWoucLSMyYAkDBSfEHYDHf1Hz0HZr8uUQddwldP6NzHiWwjGoVxraSnjdJmDHlyyAjYepPRR7nVS4v+kChtvPTU5apqxt4FOwLA/wATdF/DJ+WsY4qvl+4nkaCpmaKkLZFJBlU+bd2PudXOp3nbWMzI1hRueH/pG+k1RNNbrIsdwmRsAoSKdCOhZ/icj0XlHrza74UvVNW0n7RWKOFmIWtj2/cv2bP3Dvv/AK6zuT6nQQlZGSRgMAIfJ+J+1/2/nqPa75X0F2Ssp0HhAcksLbCWM9Vx0Hz65G+vS6DRJ5XoOTEmq1n9T1cCbYKl6hT9TQMv/Vb4Pw7n8Pz01LbYpg31vNQx2y/2f8o+z8xvqPZLxSGgidZHemkGKc8hLZ/6ZH3h/LRBlqalSWBp4j9kfGfm3b8Pz1sPTwZwnIzA8TmkrXpJJQ7gcxAxll6c2Ox9R8jqZUU8dTCVPKykdc9fx09PQwCn8MYiAPMHGMq33s/366H2+qUFozjlBwcbAHsVz9k+utkf29pQj3lG+kHhI3kNWwRj9rQKcnl3qox//MX9QM/LNRX0lK/hU8bPMNiXUZHyXoPxyflr6JuVOJ48qWWRTlWX4gR0I99Zj9IHC0TSzX6jhKzRrz18ECDMg/6yL79x2P6m0X7Bsc+mAarTbzvQeqZ64qq2YtI0hZ26Aksfmep1KalpbcAa6XkdvhgjHNKfw7fj+WmrHW1t5uUFrtCx29KhxGJ5GAdiegLnpnpt+Wtl4L+i6z2rFTcv+Pq+rc2eTPvndvx29tZarxU1DbUuPvMtN4YrsWuOT8TPuE7DxRfq2Ga0QNaoIpFdaj7eQc5Ln+Qz8tapJwzbbdfI71dbdTVUsqAVE0cZCMwxmQJvuO6nO2CM42ulPBHGixxqqIuyqowAPYDUpoY5IHhmTnifGRnBBHQg9iOx1599S1jHeY9WlVAC8TikRHhRoijRkAqV6Edse2nxH7aCQ+Lw7VeFUEyWuU8ySAbQnucdlydx9knI2OrTFEAuSQQdxg50K6bTNl6kNYydOp4kLiSNuVl6HUkxk/CNeFMfFrIzsr15ssizG9WHlhqolxPT/ZZN8jHUp+qncbbaP8IQUt8o/rjylOU8stODh0b0Y/26+uuSHilEsTFWU5DDXFXa7hRSDiCzQmCcD9/TEYWVevTrjv6jqO4Oyt5nB7lguDmXSlghpoxHBGsaDsoxp4dNC+H7xS3mi8enJV1PLLE3xRt6H+/fRRemrCbjBGRPdM1lPDVU7wzxiRGG4OntNVE8UC80rqoOwydyfQeupO4zKrzVfC9SoctPaGbY4yYc/wBPb8vTVoSphenWojkV42GVZTnmHtqt8YcU2a00Egu1TDTxOpHhuA8rj2T+/wCWsrtXHcdyNbarHcaq2SPkU/iqrMR2Knpk9wME/PrxSX4WZM4r7M2K4cTW+jkVZp6SDmGQKmoETEf5cE/njS18n8QitprpKt2Z5KliWMjNs4yfMD+elotPDL2GciBN4nWpIxNm6nLdPTXeQBn/AGdekYGSNchQcsxOf5a1JmsQGSSfwGvQCSeY7fz16o2yenYaXU64TiSeDbOf/jS9zr0jB/lpAZ3GqE5nQMz0E9D10uU69Ua7RT+OdcnQIlGBga9yPXbufTS7eo6aQ2GAdtSdiG2QNeqO+dtecuR1wBrsb+2qnuSIdfN212u6kjppKOY42204gzuBsNdBzJPETGSdIkP0/wDnXrHIwN9cO3KNu+uyTyd0iiYuwAUEknYAeuvm/wCk3im4fSTen4f4elkThqicNVVKf/WXB6+468o7/Ee2Lh9It6rePLr/APk+4RqS3jyGKrqYmBU4OGUnsg7/AHjt0zk3auGqThC0pZ6Sn5I6diJHbBaWTOGdj3JI/kBojTBN2Xi/XXsqFUODMzhpRbqRKOnpTTwxLhRynYf399Q+cs/7wMQp2U9x760LiXiGKhiMUKRvVEeVcbJ7t/bWfTySTSvPLKWlc5LHuden0zs65Iws+e62rY+A25pIhr6iNy5kBjPxKen4emjFuqYqlBImQO4PUarsMLeVmxjry9v/AJ1Po4pGnVI8iRiAoXWOq0dd43jgiHeH+I3ac+W3IlooKpoJg8blW9QcH5jRisr6aqtkFGlMxnjkZ5qgSHLqRhV5egxudQamwywQxSLJ4z8o8VO4PfHqNQYap43wuCCeuvM2VhuW7ns6rMrxDl3eAUdNTxUK0ssKHxJMnmn5t1JB6bHbGmazh02ygaW+0tTFPV0wloeUrgnPVvbH4765hmN0ucAq6vkjXlRpZMvyKNht3AxrqvuEs4aKokefwxyx7nAUZxjPQe3voXY9fCzbIPcpdztU8jfWadCJIzsG+BsehPfUWrpRxFc7fbrTZBSV7RpTzqjsxmkycyHmO2RjOPTWipTPUcLJPLV05hp5jGlMXHiAsMluXrjbvqr3W1xVI5kdoph8EqHDD8R20VTqucHj7we3ThhKhxRS22gu37OtVY9ckSgTzmPkBk+0qjryjpn/AOdD0cJJzAhxotxEs8Nro7e1upYPqyuv1uJSHqAzZ856bdBjG2NVyFjGSpAz769X4bVuQFjPMeIAo2BJTxq4LxAAnqvbUFpGDEPlSO3pqbG0bLttnqNdy0sNRGFbaQnZgd9OQxAwYtTBPMlWS/GNRT1p8WLoGIyR8/Uab4g4Yhq4jVWoKyt5jEDsfdff20Braeakmw/w52YdDqbZrxPb3yjc8JPmjPQ/L0OhrdNklq+/iN9Pqto2vyJXKunaKX9+0ivGcJUKMSRex9RolZb3VUVfTySVLUdbGT9WrYG5Q2evtv3B2PcauNTR2ziSmNRTMsdSo3ONx7MO41Rbxbam2yyU1VTKY2+KMjyv7qe2vParw0WktUMN7j5nodPrtgAbkfM0O3XKmuqG31FLTQ1MzczULHw6Wqc9ZKdv/q05+78D/pqOsT2mOWWBWnoo5OSRnj5J6N/uyp2Po3Q9j21n9NVvTQsrB6234wysMyQ+xHcaulk4j5lhNbUyyRrH4dPc4l8SaFD/AMuVT/jw+qtlh2PbSmnUWadsdfaMbK671z+8LRiAwCsqZCYXOECHzzH0H9T/AF1MutHNRWcVt2UQyS5FFRDpGO8jjufY9SRn01HoojbbvTV9tpaV6iQGSOkVvEp6te8lK/XI/wCmfMp9emh/Et6l4huz1R5o0UBREesYHY++dzr0Ok1X4iwKDgRJq6Pw1ZJGZBpiX5ppd2fpk741KjAZSNMoqkYxp+OLl82dOjj3iVcgR2kjctyncD1/lo9aoxGpnAO+VX2Hc/if5aGUcEksiwxfE539vX8tWaGnRIlRVwFGBqqAE5Mw1LNt2idRTGKORo8B3QqTgHY6GVEYmB38w/TU8RlZMdtRKiJopGdGAB9dEVkAkxTqAxULiB6h35SrbnoNR1BPtp6VueQnqAdtLC8hZiFAG5PbVi2eTFQ+BGuXfA1Cra0RExw4dxtnqB/fXNTVSVDinpATzHGVzzN/YasPD3DIiZZ64cz4yqdh89Jdb4otIIU8z0nhngj2nfaOPiBrPY6mvk8arLrGTk56tq5UlBFSweHCgUDYbddEI4Qu2MAdtBPpAvC2PhesrA3LKV8KE9+dgf5DJ/DXlLtRZqHxPbafTpp1womKfSjeP2pxTOkT81PS/uo/fGcn886BcPUwq7tErDmSP9449hj+ZwPx1DlYszOd2bO+dWng2lWGiardf8Q5H+Vc/wAzn9NFIo3AD2moyFJ+Z5xhW+BSCnHxNu3+/wAv11WbZCXKjPmc6kcQVD1lzZcgjmxkf7+ep/DdMHqecgFUGs8+Y5M5e/lV8yy0cXh0yxgdBvr3fAODrokgHlzk+mlnCgDG466cUjYJ5S5jYSTPAMDJ07TxmWZR1GcnTSA5PMSV9dS7eAQzgYzt89FVDe4EEsHloSYQQhM4AJ9des4K4xv66bQE9NdO0cKF5XVQvrpkSFGTFYUscDudKMdTqFV300HMKaRTKoPMT8Kj3/3+fQirtd2kHhw5WNhkY+Jx/b36fPpoBLO87lYsEqc+qqcdfc+5/DGvOeJeLqQa6ufvPV+FeAsCLb+PtHrxdpJ5mqJ53kkbuThj8vujtnr6Y6aH0s08zGNn5IzusajCjsD+umqlUWYAtzuACx9Tp2kPnZx2Hp/vvjSRKm+pp6reuMLJzvNT0f1qlbEqSh02z0O2x/DV/wCCeJ4LrFywI8NZGTJLRo4V1bHmlp2OwYjZkbKuNmB2YUif93QDsAMn5Af/ABrywWSS4Us90gqxRT0RUxS5xzPucZ656fnqtqZG6RLNvBm322op6x6ZmdZF8Rmj8NMLIQPNyqd1ddi0JOR1BKnOrxdBY7bbKa7Q1lNVJMjh6cvyyEbKRkDZiGJGdhjv3w3hfiI1lR9Srlhp7s/KrB8rBXhT5c4IKSDqrrgg9D1BvEVRDcqSSnqZ5IZFZVd5eVWRzsqT4wASdllACP0PK2x10uuZGFdh9MV+IeGLajWUAb5Jl4vqo62SejTwpAojp3chjEoGM4wAW98bemqPxBXVNbcZpqmZ5ZD8Tu2ST8/noxWUNRR1JgnjZHVsYYY3zjQyitdRcK+bkGfNv2xk69DrvKFamv3955HwxbvMfzc8e0VniaVZGOw5evpq2cPcPyVcaVM37qHBYk7k49BohZLDDR09Q2DLKlLsANuZ2VB/M60nhLg2pudNPGhXkhUJynYdQT8ztoWnWCpGbMLt0J1NqrjOBKvbbZLCrw0MWVLxwgMftE8xP5L+o1onBfB9DXUrTPMpqFcsqkDr/bVbk4qt/BV/no5KX63EZ35zJHgkBQPKPvbYz01UX4wuC3SWotks1FTly0al8uFzkAn+2k2sbz3yojnRL5Q2t/aXLjniOChs1fwrcbWk03O3gSq3KYj6n1+X56yJYBzF3YvkkgHoCfQf10Tv1zmrKtpp5WkkYZZmOSToXOGjjEk5KIxwqj4mPp7awqXaTmbkktmdTuWlMcIyVCg56DbuddweBEDI8ombO2O2mq2fykIgQYJwOnXQBqmRo/BDcuDgkdT+Oi9Hp21NpRINrdUukr3tDHGVxp1tlVTq+XMAQ43xkf66zgFiwCHA9fXR/iA/8LKD3Kj9dAVHmG3TTb/02uqzHcB0fiFl9RY8cxVRKwQKMYC539yf7anWYYpG9u/46hV2AsSDG0Q/rqfbRy0hAPUatWMMZpqDwJMty4aRidxE2f5aJWMZWQ9PP30OoM4mJP8AyjojY6iNHeOUDwy484G6n+o1nqKza21e5yq5aBljxKXdcColH/qf11FjGJL2Cckx5x+OnL7KBPNHGAxLnzD59tMUrc1RdjjBaEHH5aG1VqtUF+I30dRVifmaHBRCptdJMWPOaeM8o7nlB0/QS5pqqFhykICD+OnrEjPZLeW3H1WI/wD2A66krTiYVHKBzeGd8bHXNPZsgOqpFpInFAuVYg4wf01coqNaj6NCxi8VkuTRgemY9j7dNUq1ychMb5BGN/TWg8M1iD6PrrTKgaSOvp5gDt1JH8hppfqBbQmfmIaNGdPc5XrEz+6qn7Kk+rqssJmj5lOQGIU5A989DrOLzazHKJqcsAWGDupQ9vkw/LWoQKr2a4wuwBV1O/QeYDVbudIHch19ssM823Q+vz0o1ugNfrXqNvCvFRZhLD6o1wDxhLG/7PuMZk8XqnQS9csvo/UlR1OSNyyteTa0qMS0ziaCrgkjhmX7XMp2OOh3B/lkY1lt8spFjaaJeXwqjmBPUAjoT23AwdG/o243loawUVxBlZ3HOjDHjHPUdhJ+jZPcnmUY8pgRPRMqahTnuTJqZ6WVoVUSEeUMqnzYJGRnBwcjrq5UNRUFoqtGLQzUyM4HUADBI9sj8NezWqkro4KihnVoW5mhlHYYJ5T75Xpq8WeyWqzcNPc5JKapa3VKMtNJ1k8qsR8s8w9MDR9WuBXYwzPP2aAhyy8GErBQ09bb/qU5EUMqGcqzcrAcwYfLykEHvjRm8XO0WzgiotsNGGqDGYlmK5wMdc9c6yqh4vFTxSKujTwKd0aOOmLlxGMEqoJ+yOnLsPTRiouk14gDQuqwOAWQdvx76ys0rowbPpm9WtR0Yf6up3c6WovVvTlCxTvEnhFmwJtsYPo22AejdD0B1XbxFzR0sjlg7oGZW+y/Rh67Y0Zpas001DFV1OKWSHwjzbhSCcHP5a94ihpaiMxPOFq0POjFwPEB23ztzdPMeu2fXWVtbCw4Hc2qdWr/AClAkgCS11IqnIU498HIH6frqNR2uSdVmdvDTGQB31ZqegMlxkmlDKrxPhlXfmRdwQenTfO++u7PQSTQvEiklJCgGOvcfoRoWywquZsEDSuTRBGrKNOkeJUz6df5HV04WsFZxBRxz0dPJIqjkkbGysPU/LB/HQ272OW28QUMtZGY0qIwXB9MlTn02A21r30NtT2wXK2uUQxYlLHYYGVY/wD2urWWB6xiZ1J/V2mA7ZwBb4EnFWrTVbRMIzjARiO3+uqs1mHCXDUPGPCq70rhbzb1clOQ+UyovXBZW5lHzA2OdD+kTjey2eqaSOUPKyhlwOYn3CjBI2zklR7nWB8XcS3GppVnt081BDUSyhysg5lBbIAIA5ftHIwfMR88qaLHU56hwuSt9oMsfGNygvtbQ362MZKStpgrFX5gkqgsFJ7EgZGBgg5GdwK0taxdgI+dHPmUfzHoR+uqlwnxJV8K3HwVQVdvnGJqZgSvXOR3677bg7jfINmrhBNAKyhcvRTgGPJB5D91vfHfuN9M9Gta+mz9Iv8AFVt4enqO1CxwlTzCUOMow7/6+o1JsparlqLbKoRKqLlQ+kg3U/z/AD0EjukdIDEwM6tuwB6H1Hv/AD174tUlTFVJIOVWEkbj4Tg5/wBCOujbL1Vdog1KluTxH4a1KXKshaXOGBzsRsffTE89VWAsxCRD3wo1L4maJbiKuGJWWsQToT036j88/noYS8hLTOWAPwjoNSuu3UHHsJywpSMiPzRR1nDtRQxKJpqMtUxEr9k4EijPps356r1prhSKKKvbmpWOYnx/gk//AHOrNaamOirYpinMiv5x6odmGPkToHxHahQ3epogeeJTzRse6ncaJ/BKjAe/sfvL0awvWQRx7x+eJ45Cu3TYjoR2I9tELQGqKSst43dk+sRD/wBRBuB81/kNA7HXrC6224N+4ziGU/8ALJ+yT6b/AIaOosltr4p0B5o3DL740QtpcFG4YTNq/LIdeRItrYBTDnyt50Pt/v8AlqfTF6edZkCnGcqwyrA7FSO4I2Pz0zeKdKOvaSH/AAmIliI/6b7gfhnH4HT8Tg7fr663pbcuDML8ht0G1lPJZLj4tMHlop0Eixk5Lx5I6/fQgg+uPcaJIySQRzwOJIZBzI4Gx/10QgoBdKN7auBMGMtIx6CXG6/JgMfMDVTFf+xq54CSYpGPjR8n+E/3h7+o76Ca8aUk5/SFLUdSAD/eWFJFhGZpFjX36n5DRKQx3zhyoFMFWttsfkZ1H7yAncZ6HBzj220ASiMmKiaVZs4cNnyYPfPfRC1XOGkuMMkUX1gxt5wBheXocD5aCfVve3HU3qpSniDrX4ccsFLW8pQ4FNKeiN/0z6j7p/D01KqKlln8OijJboXYY5fb8NSuIbFBJd5IB56eWMVFG3YKeq/Lb9NM22pWNzb6w+JUgZglI/xgOoP8Y/Ub9ddqYqMMcLNLlDHOOYfttPHd7CaK4FpJqcZWUbNyZyrKfvIT+Rx0B0T4Vq6mlui0VaypXU64YjZaiE7CVR+hHYn5ardBUVEVUkyEqUPlHXPsfb21a6+gjulFHJSzGGojHj0U43Kdip9cHysO4x7a0anJx18TlFvGDLNdbXRVFvnpqiNJKeVTzljsw9z699COHrz+yRJa7lBLUVa5+pVLpn63F6H/ANRehG3MMNnriVwjcVu8ElLXIIrjRkLJATnlOM8w9VPUH0986lcRUMNTCKdnlinVleKSI8skLjdXB7EHf8xuCRodlDjrkQrJ6zxJtusl6vjmWvZ6KhG4jyFcKexPRR+p99FJbtS2taujs5juVVQU4b6rzefl6YGe46jmHQ9DtofaV4j4xqY7JPe6e2yUkAavjp4zHI5LFQ8f8LADdcEElS2wzfbNwLYrNampbbSqkxGfrDjLlvc9ge+PXSM3WOxWzrqHV6dK13LyZT6DgriLipxWcY1jUtG2CLdAccw9HPf5HYdlXWjWa1UFoo1pbdSx00Y6hBufcnqT89ccO1LTU7U0uRNT+Rg3UgbD+o/DRQjfQ/lhOJuCW7MbeJJYmjkUMjgqynuD20HszNbrhJaJ2LI3np3PcHt/P8QfUaOAdtD7/b3rKQPCcVMB54iOufT8cD8QNa1sPpPvOMD2ISAwNdA41AsdetxoFmGBIvlkX0bU7XNuOJYHInRCshVgGVhggjYjQi3TG0XL9mTMfqk55qZ2PwnupP4/yP2tF11EvdDFX254nKoy+ZJDtyMO/wAu2rq2ODOiFE67nSlnhp4TLLKiIvVmOBqhz8f0losAqL1LHSzI3hl2bnEh3xygbsxAOwwO+dZdxP8ASPeb9MUtAloqcHapk/xj/lHSMfLf1J1kbGztUZM0AAGWOJo/0ocRW2FIUFQzNn/ynN5mP3ivUfjj5apFv4tuH11PHiU0J8rwBcvg7ZB9fYbH01VYqSOlHjVkx5n8zFjzSN/v1Om627KsWKQCJD5Sw6t7c39BgayTRNv8x+5ZtaNmxeoc4iEFjqRGrhaScGSmZMZlHUgsRsRkep1VrjepagtHGoVD9kA7+57sfnotw9PHd7TLw5dW5aaRw9BUt/8AV5+y/I5xj3Prqu10qWirmoJ6fmr4DyyeIvlBx1VehHoWzkHppnXpUHIi668kZJnhozJH49S/hRt0kk+1/lHU/h+eos1whgHhUcbF+nOSOf8Asv4ZPvqM09VXTnmaSR3OMdSfx/ppzwqSl81Qwdgf8ONth826D5DJ+WmWmsNBweoutAsGR3DPBF7qbbWyQ1hZ7dUEGZUBzCw6Sr7jG/r8wNa9Q3N5SKQRiapCBg67Ruh6OG7g+gz/AC1gc9VPVIVgRI4V6DHlHyXufds6uX0dXqogENrrZ8cjf/R9RIejE7wsfut29D+GmV1a2p5icTDT3FG8tuZqv1JpD4lTJ4rdlAwg+Q/qcnUW7wRLAJS6xyrkJkfF6rgbkH/XXVur6i4q608ZpjGxSQyjLKw6gL+PU/lqfDbIo28Us0kpG8jnLH29h7DbQQcLxGGIIoKlXjVWDDOwDjDKfun31zcaQyAVNOQsyEkHGfnkdwRsR31OutvJUz06kuBh0H/MUdMfxDt+WmKGYMowQcjIb7w0RW24YMxIwZkfG3CkVLPJeKCnKU5bFVTjfwHOdx/Aex/tte/ow4pW5U8VmrSBWxJiGQ/89B2/zAfmB6g5NXOhDIZoo0YlSjI3wyKeqN7H17HWZcRWZ7LVpX25pVomfyMNnp5Ac8p9CD0Py9tEkLqK/Is7HRgLq+ns81OvcTdItTIRkYOqb9H3FcN9o1pqlljuUYAYYwJh95ff1HqfTppFrsdRLh6k+Cn3erH+2vNXUPS5Ro6ocXAFZE8BKiNqSaIyxSdQoywPYj3/APg7aExR1PDNV9Qrctb3/wDLynpDvsD/AAf/AGp26YxodHR09KnLDGB6k7k/jri6UFPcKR6aoQMjDrjJGqAcYMKNXErnKeXmDeY9h21PpbZPMoLjwhjqRv8AlqJYB+xqv9l1qggnFLO2+3ZM/wAvy9NWcHmUMMgjqNU8rE6i57jFHQU1NgonM/3m3P8Ap+GpOkNxkabmnigQvK4UZxue+r5AmolY4gs1VQVhvtgwlQo/fU/2Jl7gj9fUdR3Bl2fiy0V9r+v+OIQjBJYn+NH+7juT2x17aE8ccd22wUjtV1qURIPICvPO3+WPt82/LWKQfSJSXW9zxNFV2gVKtFHXrNh25upflA5CeuRsD26hpXuuJCDr3mVjrT2Zs3F30i2iyQl6usSiB+FGAeof/LGD5fm35ayPib6YbvcS8VigNvjOxqpWElQw9j0T5Aazy98PVlqu7RVPjVbyEmOdvMZO/X1/+emozy01KpeaQOw6pERgH3fp+Wfw010vhSMoa5s/YRVqfE3Ula1x95Mnnqq2pMs801VUPuWZizMdRKpqaFC00zF1OQsTAFD6l+gPyydDqq8SzI0NMiRxMccq5Cfj3b8TqA0byENNJzgDYHYflp5VpNybFXAiK3WbW3E5MvNp+k6lWl8HiC3TVskZxFPAiNzr/Fzg+boMjr36aWqctFIyByEhVhlfFlWPmHqOYjI0tZnw2sHBcTg8RtP+kz6ZGRu3xaQUAnOc9vbXqkqSxOT29tegEjPftpBunq5zhj130hsMDrr1vKPU+2kAc9ASdUnRPFUgk5z/AE111BA20gMZ666UdzqS0SjbtnXWSFI65768yOmCc6QG/L31UmSLBz649NegdcnYd9eoD64GvDl89AvYDXJIsZI9B204B0wN9eKMjfcH9dOqDg/076kkSgfh3PrronsMdMnXhJG2Bza5GAux213MkRIUZONYt9N/0hVYqzwPwnIZLvUeSrnjP/l1I3UHs2Op7A+vQp9N/wBJR4diXh+wOJuIapQE5SD9WU/bP8R+yD8z2zmvBVBBYIjVT4q7jVeaaZmJbJ3O59+/c5OmOi0TW+s9CK/EPEV0w255MtHAlFQcE2xIYqlVrXw88o2Lt2HyHYavlo434flrGiu1G1SixnCK/wC7DnvnqflqkXHiOlm4YksaUFHJO04matKfvRgfCD2GgFHQ1MkLSU8fMqrvk40eukSwbrRtx1PN26+xXC1Hd8wyvDN3u1XLLbKCasVizhY9yd9zv2HTOgC07LK3iL51+z6f66s3DPEN1tFWo+tzQqUMbBXKDlPy3/HVl4f4Mor3FU3m53eG30eSqhcNIzgDoo7e/wD86I/EvSf6v0+0D/BJdzV9XvM5WMmMhQNEuHqugoa0z1koWRB5AR099NXGkmo6qSJxyquSZM5UgHqD30BmcPKxO2f940QqjULweIMW/CkEjJmkRcUWcczfW1OepOdDb5dLMw+sxTCSVm3EX2vmNULly+5215NII1PLgY6nWf8A6ZV282Xxu/PpHMutJVxzDxKeXK+2j1qroo7bWUklJBLJVcoErJl4gpz5D2z31ltvq6iObx4WMYzvt8XzGrdabqlUMMVjlA+E99K9X4Y6AuORH+h8Yrtwr8NCpLksFbmIOObPUacoJlhLtJAkh5SAr9Bkddu+urdXzU9PUxoQFqY/DlDorZGQds9Nxpg757Y0tpoLMdw4EcluJxU00csfhTqHVhup31TuIOHTTAy0oMsROSMeZf76uhB+LOT665w2nenuaqB20LaPUJkro0TnB27HT8M/KQSCTq4cQ2Bah5J6YKjtuVA2b+2qjV0csDtHJGUYfZbtp/p9Ul4wTzPOavRNUcgcR+URVA5JFyu2dBq63SxAyQgvH6DqNTIZgpwxJ/pqSshxs34aKVSvIgSWMhweoLszy0tUtX4jxuvwhTuf76uNNVUd8gNHXU4DkHH4dwe2q69PAZPFAKOMAt/pp2prxGr0duV4YD5ZJX/xJ8Hv91f4R+Oewt9fmHOOY50mqXb3x8SBxHw3U21zU05Zox0lUbj2Yar9OZoJzJRBYZWOXpz/AIU3uvodbbwrYbjVcMx1FW/iSS5aOJ13MfbJ9T1+WqdxVwaG8SShi5HU+enO2D/D6fLSa+ujVZRjhh7x1U1tA3Do+0B8PX1fBmp44VqKV25qu2zkqOf76EbxyDs6/jnVllWjulI1wWrkcRABq50Hj05PRKtF+JfSdev2s9s4q4nWYioaSKpi2SoUedfZh9oaJ2a9VNJXRPLN9SrwCIamIjklB6jfYg91OQdJbabdG/q/Q+0ZU3V6hcS0gSQ1P1SsjEM+OZSCCkqnoykbEHsRqbTqe5+H+eo1DU010p1oTSwxzli31Dn5IpmPV6Vz/gyHqYjlG7b9HqDkpJ4lraiSW1eMIpajwystOe6Sp1Vvz9QTp1pPFAy7bO4p1fhRU76+viXjgq0PJSNWuu8uybdFHf8AE/yGrE1nY7hSdWnhygop6SGWkkjkp5EBiaM5Ur2wRqxRWeMp8O2sbfFNrcTNfDCwyZlFTanCnYg9tBblTOsZTlOSMZ9BrY6+yx+GzKCMe2sm+kO92+zVElLEUqa//pDpH/mPr7dflrerxQNAtT4WccSq3BYaKLxJ25ck4Hc+wGgscddeaoQ08ZWEHp2A9T6nUy2Wq4X2pNXXSMIz3IxkegHYau9soIaKEQwIEA9BoTWeLNjapltB4JXWd5HMg2CxU9ui5ivNMernro0kWBnPTT0aHl3GdLBAPppBZaznJnpK0VRgCNOQASemsS+na9fWbxBZ4XzHSjmkwertufyHL+Z1sF+uENrtVTXzYCU8ZfBOOY9h+JwNfL13rpa64VNbUOXlmkLsfUknW+jTtz7SlpzhRI0ML1NVHTRjzSMFHtnvq53aRLdZgkYwOUKo9ug/v+Gg3BtIZ6t6th5YxyKT949f0/nrnjWt8ScQI3lU4H+/99dF52oW+ZbHqA+IEpAZZGlPyGrjYqcwUi5GGbcnvqtWaAtNHFjYnfVzjHImw2A213Tpg5i/W2AjBnTNzk8vb89eqAMcy5I7aaClcsp69dORjMe250zXqI2TniODzZyR07anUq8sKqD89RIYfEcB25UPX1xqJV3I06vFDKrKpwJMdP7n/eO+tk1VdGWczJtFbqjtrELVVbFSLy/HIeijv/v89Vq6XIy5eSRSBsB1Qf8A4x9unqT01Aq61y7Rrl5DsVzv/wBx3wPYde5OuKenMkuZCHlxttsntpNq/ELtW2xeBPRaDwunRLublv8AOp4Fkq2y3PHG3Ufbf5/20RoqCSoZIIY8AjYAfz0QsFolqJUkbIUEZcnGflj+erHf6aK1cPVlTB5CIyoY9WZthn03I9tBVqlbc8mGWWmxeJldQ4eqdlxgucY9M6m29AQi92Iz/P8A/F1AjjIGTjrgA9dGbanNKAR0G34n/QaKsM7R1Jt5iNPaOd+ZWlZEVSh8y4Lkg9Nsp+epvAlvr7vQ3GKlIijpoxzIP+czk7E/Jeg22BOewG8Xeur44aKeqlekpWf6vCWJWLmxzYHbOBn5a0H6KX+oWJ5sFfrczNkrnKphR+vNoda3IJHJlb7VrXLSnXCgHM1LWxspjOA3R4z/ADx76svDfEssE0NBe6jwp0Qx0lyKhwVIwY5lOQ8bDYhsg99X27cOUN6p1qAoiq1GBKv9fUaoz8KVT3KWgq6UurMI1VehO+6n89tYOgddx4PxO16jaeepodDWJOBQ3GFlMUfOFBMhijA+ONt2lgA6g5kiH3kGxvhPhuolrfqlM6SPO3OjJgh1JypUjYjcb5xqnXjhTiX6OrJbaniNGqbFUsHpZ4Jv39FJ1VkYbqR1xqx8I8Rz2yro54pYqiCSTxKWWEKsc7k5zGD5YpiesRxHJvjkc7ipe6cA8TW3TV3+ro/zNOtFptHDX1huKx9WicokYL+ZmU8wPyGM6qVH9J10obvM1mMf1cyN8a+Vt8/M6hfSbdrnxJVx3eSdJ6F15E8EMqqV2YFTurDoyncHY6p/iJCQApHsO+iqGLKcnMWGg1uftC3EtzqLxeJrhWurzytlmxgA6GB5J5PDp1LHucbDXCU1RPHJV1OY4EPlXOC2+ABrujqG/aaRQjliVlXA2Ayw/Ppq1Zy21e5Z+BuPUeq4fqTSTc4aTpk74+WoFVIZYqUufimY79T8P9tEL4xK+Xckn+ehtQmPqp9AzH8z/bWNdb2tn2m52qs6q2LRqOilM5/HVVFU0VdIjgmMvs2Ph9jq1VXlCod/3Q/n/pqDJYo6uKKoohifYvHnZ/Uj0OnXhbjTszCLPEqBfWEMBcQOHpcg9ZB/U6CofMN9hqRXiaNvAfKqsmSrdVOP5b6iMxUjHrpobltYsIt01J01QQzq4DE6qN/Iv+/10Uta5g6dtCasn62RzDOFH8tFKF2FOyINgMZOl76ha2Jhz1lgDJ1IVWKY5GRH0/Eadpgx5hsBz9tRKBMRzljzEqMjPvqXRZdm5icc235a10LNbcCfiL/EwFowPkSm3FcyOkQO7jzfjpukXFddRkbU/wCWCNSqtgZWVF25xkfjqJQjN0uvL1MDbf8AcNCaukIh/Oeg0Fu/Gfiavw4A3DdsZj/9Ui2/7BojRqTMcDYxtjTHBlCx4VtMs+4ekjxg5+z0Pvo4iRhgiDoe2gFLZwZ1gCSRAkNMJUPQPgaI2Krko7dfKZhktDHIuT3Vv9dNUyAMeXUkQ+LHUp8LPAy5/LRYf+gAfmCvWCxgGh5/EukTDcoxOOmRv/TUDBdwkgzkgKR+W2jMtAlJxDWUSN+5lVlUknIDA4zn2xo5wpbrNTSUVz4jdjRrVqsqojMCmD5iR0PMAPUj16aMp8SQ17X5M85q/DWWzchxKrT20y26rpgvNlVYEHuDv+nrqjcQ2COKsPJTs48JjhVJxgHr7AjvuOm+t8+kCu4LWuEHDNLIsiRzGcsTh+6++PQ+mspusjVExeQBlbI5sAEemffQGp0TMvmouB8RxovERXZ5LsCfmQfo/wCLqugkhhr8sJ9gzny1GD0JJ/xBtvtzdznDa0S6AVlilqKepZ4S6MCGOVwSOVh6g+oHfoQQMqv9rSXhsSxD/DqWU4G6hxnp3GV6flp3gPjGooaj6hc35lfCc8hysg6BXJ77DDZHQBiMK6K3U18rPQ7UvXnuWCJpbbfEZgQUmDHHdSdGLNdzaq6WnkxNAkjxsgJAIB6jT14t8FfSLU0pYQkYyfiiYfZPft3A/A7aCX+nliryxzmohjlyO55eUn8wdMtLqlKFX6nn9TonRt6cESyXa4rXWiKSmDKqPIh5+vr/AEOhPDbGqu4oXdppauNoOVjk5OwB9N9OWimnquHaqM5R4J45QIm82CCp/wDthtpcOJJT3Klnhj8MxTqzN6YbY+/XW762tBtQQdNC7uHsML8I3GepeKmqnggqMgRTSuQCMFeSQ9OhwG+QO2MarwVQ0tIvPGiCZ4yrjGWVonZd/wDsMW+sijpIoroYpyAnisMk7LucnGDnV1rbrNRRD9lVkNXUSCREqGPhpITy+VsEEYwMHOxGCcE4RX0vZnAjii1KxgnqT/paFD9Xo6l5Qr084WVR2Vv0zt066zfiG+XiivdTDS1PhSRryM6gHqBnGRjr3G/cHUO5VldW1c4u7yPNHleSQBBEc7jlAAX5Y31Au8viClqEPOWjMbuRgcy7Z98gjrq9FW1MGXtsDk4g+uuEjJJI2Zp2PM8jksWPcknqfnrimhertVajjflFRHk5zg74/DSdMOFK+dwD59gc9P8AZ13ZanlucKSNvITEV9QRjRyNxjMEUYbMq9ywI0miXLKcE+/bUq23hbTXPA6GS31ADPCScIG3yPQZOfY7juDzXwzGGqpI1ClMnPyPrqBRgz0Xhhh4iZXmAyeuR/P9NYuMxrScLz1LVXwQwolRSATQyDKSHf3wQO/8+o2OurfKZGFNNzyxyNgKvVT0BX39u4/DVdsVzkthakqlMlE5w6E7p7g/7/nk1WQNBySwsJIH3Rx3/sdMNCAbNlo5inX1mtPMr6lkrqV6jg9iMPJbZsqykEGJ87j8c/loEhymfXRTgq4pFXtb6k/8FWqYZB90kYDD8cZHfUJqRqWqnpJDloHKE+oB66PUGi/aejBd63Uhh2IyqEHOdTb6i1Vpoq/lJkp/+GmI+7vyH8sj8NMhfbRC0BZmlt8p/dVa+Hn7rfZP4H+eiLxuXPxMqfQ32Mq9bQKyA4VkI7jrqRY68R8truTnkPlp5mPQ/dY/yOp1GrGKSlnXEkbFXB7Ebah3WgQwsZSqrjG/f5ayu2ugcHB+ZvpnKsayMiG6iF5ra0TKWloicjG5hYnP/tY5+TaF/WoaeHwpgzTJsFHf0315wxeJlkp0ndXTxGhSVxtKmMGJ/Q4OQe/8vKqjjtd5lRhII33Qt8XLvj8ex9wdK31zFTs4MZrowOG5Eeo6mtmqYpJJGhaNg8ccY3GNxtoxxhTRTwx8QJEEWrPLOsQ+GUbdffH5g6rjmqnLJCDBHnqPibVo4JSKahq7DXSELUgvGWOSrjv+gP8A2n11mmmsKl36lPOQPsEp1uqDTu1LWRvFb2fyZOfBP/4pPX01Z0igo0w2M+inr/fQ+up38SalMCrLGxjcMO42P+xpqySmmmS317YhJCU85PwH7jH0PY9jtoytPIXcv0n+8zd/PO0/UJZ42evsrooK1NuP1iAAbtF9pce3X8tQrrbqeoh8QAxuQJF5NmB9j2IOpNHUvQ18cscJzE+JARuR9pfy1LqaRKSslhBBpv8AGpXPTwm7fgdvwz31m5CNuHRl0BZcHsQRbKx62BoZAFrYgefblEqffH8iOx36HaycJVTxn6kzkl354SzfbxuvyYD8wNVq5U7SzI1vST6yrc0coGCD6gd/Q+o09FHVS1S1EyNT1dOVZ4OnJ6Mvqpxt6YIPTVBcA2xefgzTy/Tv6+RLpc6Od5obzamWK5Uw8udllXvG/sd/kd/XNl4braG70AqolkjfmKSRy/4kUg+JGz3H6jBGoUrRrPDPGVaKrQPlRtz4ydvcEH551Dmp6m1XRrzboGn8RAtVSqceOg6Eeki/ZPfHKeowQw3jzR37yyk/TLBXUdVFUU9zts4prlRNmnmIyN+qMPtIwHKR7AjBAI0/gziCn4jtH1qJGgqYW8KspnOWglAB5T6gggg9wQdUOzVlJcKGGqhkE1POnMrj7S5/Qgjp2IPppki42O7i8WhQ9UiCOWEthayEEnkPoRklW7EnsWBXavTi1dy9j94Zp7SnB6mgXqN7dcYrtCpKOeScD/fcD8wPXRqNkkjEiEMjAEEemoVnr7bxLw8lbRuZKWpQqQRhkYE5Vh9l1YYI7Eai8PTSU9RNaKlvPCxMZ+8Pb9D+OlBG4ZPYhwGDn5hnA0hr1sAnXPMAM6xyJeV+u/8AoS8rXptR1R5agDordc/zP/u9tWAOp3UhgRnOgHF15s9Jb5qe5zqodMsqkAoOzEnZQDvliBtrI+LvpFu1u4KoZ7DJHd6OaRqVanxcRxsudn5QGbvgAqMAZzka03NaMoMkSpwh9XAmv8RcV2myUktRUVUKrFtI7yBY0Pozev8ACMn21inGX0wV91lak4bg8VT0qZ48Rj3SI9f8z59lGqMKO78S1KV18rnrXXZAwCwxd+VEHlX5KM6uk3BFfZ7ZBVSW6RRULmFjGGye2V6KN+rn/t1suiPdrfpBm13OKhn7yDw1JWXOiqbTxJWvVR3CTxIamofmaOfoCCeo6DA2HsCdQ5KlrXVzWxado6qnbklJ6j3HZQRgjG+CNxqFLFVVFTIkzkyZwURix2/iHb8hqzXOie72iG7VEcn7SoIgJuXOaqnH2xgeYrnfl652OSMHitAvED81rOCeY9Dw1NeLI9dQCtqXTkV1MGIjIc8wznJx5dz1z221VqhIaCRkqVMs67cr5VFPpjqf0Hz1YrT9Is9nt8tv4bchJcfvWAJHuq9E69TknbPTVZq4KirnkrrtUlXlbnYEczvk7nGd/mcDVApb8pzeF67g2srJquXl8zAHCkAAL7ADZfkNWivpDxVZkqKhX/8AEFqi/fIuPEq6cdDj749/Xoc7VyruEcSclviEI6eJnLn/ALu3/aB8zpuxTXKnukFwtxYT055gT0x3B7YPQ51tX6cic8wZ55kRroJY/Bo4hDGwwQu5b5nqflsPbXlNQT1RLspVU6uxAVR/Ias3E9uonX/xTZKE1UNXL4dRTRyDlp6jfmzjflbqMY6++NS7HwHe794c18l+p0Y3SBF5Rj2X+px8jofUalajz3Lppy3JPEqMZhM31e20z3GpJ5ebB8MH+bH/AHjV14Z+jKuuk6V3E1S6AYKwjYjuMD7P45Py1ovDnDdqssISho0VgMeIwBY/j2+QwNHqeMAgnbQA11hb7QkVIo4ldq6aotFZHVwB5QFCtk5aeMDoT3kUZIP2hnuDqxUVTFU06TQuHRxlSO41KemiqYGglBKtg5BwQR0IPYjVXHi8PXR45sCjlbLkDaNidpB6Ix2YfZb2OS4ptFo+8yZSssuhF0o/BZqqHaMnMqj7J++P6j8fXRZGDLka91sDiTgwLTyc2VIBI6j/AH20Nu9vRllIi8WKVeWaLH+Io/8Auh2PfpolW0ppJQ8eBAThP/TP3T/Ce3odvTXUZV4zn5Fe+iUbeJkVxMzmtLWSuiqqVjJSOwKS/d32z+RG/Q5B36779GN/kvFraOoljkkgxytzecrjuPbpn/Zzq40iJ4heMSU0mfFQrnr1YD8sjvsRggHQq1VlXwveYp6SQinLfupM5Hryk99uh7jfqCBzUj8QmD9QlNOfw75HR7n0UN9e6E8MXumvdtWphYLIABJH90/20QnqIYF5pZFQZwMnr8vXSRhtODHiMHGRGrrQQXCkaCZRuPK3dToFb7xJbKw2y7lgQP3VQQSsg7An738/nr3ifjOz2Kn8SvrEp8jyofNK/wAk6/nrHeMvpWa51Ua0NpRqWN8sZm/eyL6AjZfUe4GuVE3NtrBMpa61DLHE2Xiriu22CAT11ZHBGeq55pT6FU9Pc6xzjH6XLhWs8PD8Zo4zsamXzTEe3Zfw1UeLaVK2JeIbVLLVUU5w6s2Whfupz0+XTv06VqWppadC0sqysBukb4UfN/6Ln5jTHTeFq/qubP2EW6jxFxxWP1ntSKiurHnneWqqHJLO55mP46iVJpIVImkWQjqkbDlHzfcfkD+GolXeJp42igVUiP2VXlU/Pu34k6gGFpH5pSXOdvT8Br0Wn0uE2ouBPP3akbtzHJlq4e4roqqnPDnEQBtsmEpqrB/4c9lJJJ5c9D29wSCE4o4drLFcvDrWM9O/+DN9lh26bA//ACNtRpKNYwRWMYh/0+Tmc/8Abnb/ALsaNcNcXUESrw/fueS1N5YJ3fnkpGztlgB5c+m69s76xasad9ycy6v+IXa/EDJShAHqGEAPmXnGXb5KNz8zge+o89zp6f8Ad0keJB0kYc759uyfz99TOMeGLhZK8mSdqihnPNDULvz53AZu5xv6HqO+BNBQyyxsYkxGvxOfKi/MnbRyE3puZsLALV8htqLkxiSaqlkaQyEMTuT5ifmT10tTXW3QHlkmmmY9TEAq/gW3P5DS1cGkDAzBtlx7x/efUiY6/kNeN5dhux0u5369deBQufXXi8z6ABPMYyepOulyMeuvQM+513ygL6++pmdxPMDOdJeulpAZ2HXVcyRAZBx+el1GOw6nXWOuNvXXhUscA4H2u+NSSebswUjCjr7+2nFBJ7DHppKM+UbadCZGB0HXXJJ4iKepyBsTrtmwNuo6DXmyLkabywydubUknufU7d/fWffTJ9IlPwbaPBpQlReaoYpIM55e3iMPuj07nbscFPpN41t/BfDklfVYlqHBWlp+bDTP6ewHc/118zUq3/iLid7vcKeevu1a/wC7RUJK56KijsBgAdgNF6XTi05Y4Agms1BpTKjJ9hHLVBURVE90uUzVl4rGMkskpyQT1/3+A0Wp5WLEly3N1Oo9RTS0tTNTVcbwVEblZYpQVkVh2YHca4EoA5E6nYnsNeuqRVUFDxPnmrey5yX7heGVf8MYL7nWgcJ1pazzxeIsVKFAlVsfvMHt+PbWVU0jBsBjnuc9dHqe7yrSildlCdMj09NY6ivzxzNNHetBxLfZOHrrxdfJUt0fi43yowAvbqdQK+juVkuLQSGWFoXKkkEHmB3H6akcI8TT0UyRpO9JGD5ZYjhhn1x1Gjc5hv8AMOVXkKyE85bAkHY46gk9fnjS6x7Uchx6Y2rpqZAyH1Rq/pbLpaaCVUmpqwZ+tnnyJBnbC9FwPzJ76qPFdljolWqp2ZYWAKxygq2D0K5+IbHfRjjimr7RUyUZaGVVRDI8T8ynO+M/z0F4p4mmvtPA9wkkkqYVWKIHACoB2x22/XWukVxgofTAdeamyrDDQXT2+plo5KmOMmKPqfX5ep0O+rtLNlwVwcch6/jrW+F5uF/2DPNdKieOGnpl+qwogDSzMDt3zv8Az3OqhTUQeokr61QHc8wjA2Hz0VVqzazbxgCC26EVqpQ5JgIUjogJRhgbAjbXkY5enxE6sdddEgiLMCZCMRpnf8fbVaq5wZFeRR4j5O22tfxO8YxBH02w/VmGqC6eEQlU3U7P/fRuGoicDkcHO/z1UaZkkUllJ32HQjRG2JL46iEB+TffbGsbNGpG8cR5ovFGDCtuRLKpBGlga4ibmXJHK3prtcHY6XkEHBnpEYMMiIAb41Aultp6+IxzLv8AZcfEuppGO+2lrqsVORIyBhgzOb3Z5aR/hyoOzjof7aFZaJyCMY/XWqywRzKyyoCp6gjrqsX7h3lVpKVS8fUxnqvy9dOdL4hn0vE2q8NyCUlYjkVhg/lp+ARGdGeMOFIJB6N7H21DqIZIWOxwD117HJkAE76Z4DrxEm16Hz8Tb+Fr5RXmER04WGpVfNAxwFA7g911SfpC4oH/AIgSlt8SutOTHK7dZm7/ACC4275Jz6CqQVTRFWjd1dDlWU4IPtpmReapaoLFidt+3qfx0pp8JSq4v2I9bxs21BDwYbuVst3EEJmhIiqwPixv8mHfWf3e1T2+WSkrKfyscmNvhb+JG7HVqp5XjkEkTlWU9QdG1lpLxTGkuESlj0PQZ9Qex1e2lQpVxlZtRqgxDA4aZhDVtSQlZi9Zb+nMwzJD7MPT31b7XfVk5HrqlnBjEcdyVPFbk/6c6f8AOj+fnXsT0A3iLhuptUv1iB3en6CVRkqPRh3Gq/EJqWYy0QEUh3emJ/dy+6HsfbXntV4c1HrqOV/cR5p9YHO1+5svBfFF04RuKmgjWekm/eyWsTeJHMveWlk+0PVfiHQg9R9CcHcW2HiWym422tQxoP3ySEK8B7hxnb59PfXxjYb0Gp3giXxqfn55qCVihR/vxsN45B94de4OjxqhJTyVlNXSqGwk1SRyMN9o6pBsN+koyrd8HcLGVbSMw7O0ekZmxfSt9K/O72ThFiXfySVyjf0xGP8A7o/h66oPD/DbNIau5N4kjHIRjk5PcnudM8GTW81jU9ZH4FzI6SEYcdih6Y/3vq7Qx7/rqW2Cv018CCBGY7nighCgKgwB2HbUqKIfEdzpyJABvt767Ax1xjQnYlyficAY1zyllY5VUUZd3OFUepP+z6a6q5IaeITVT8qt8EanzyfL0H8R/DOqhxFxC0isgCxwR5YIreVMDc/xNjuf5bAnTaS3UNhRB9TratKu5zKh9O/EsIoIbFQ+bxW8WaVhhmAyFAH2V6nG5O3TprF5G7ddF+K7m90vdRVSMxy2Fz2HYfkB+WmOHaM1l2TIykf7xx8ug/E40aawn9NZ2l9/rMtNrhW2WE8+zqhLH+I9f0GPwGqTUSNU3BnPY5P56tPGdZ4NIlKpOTu3+/y/XVWt8Zc+pc7arccttHtNfpTd8yzcMUoPiVDDYbDRxhsB215Z6bwKJEwNxk6fljOS4+HRdS4GTEOotDMYzgHYY15zpTjxCwA/npqpqkiBAAZxvjsB6nfQWuuHJuzEs3wkDzf9o/qfwA66zv1a1DA5M30uia05bgQhW1pHOJG5Rj4M4/8Acew/X0H2tBHnkqGIgJRBt4hGNvRR2+fXTYSaoJaQHkBysQ9fUn10Ws1rmqiSRgDqTsBv/PS/+pcdzmN8pp1wgkagt7moVIkPmIz3JOrXabIkUnPUpzM24jHQfPRC32+ClHPGMuRguRuf7DU9jyL5R5j31qSF9KQF7Cx3NJNBTAIxbCoqjzdhqp/SVcWjoYLcoPLJJzknYsoHb2OQfw0WqKuuo5Q9SjfVieZHUdPc/wB9xqrcaXIXfiBfrlQ7JFEE8THPghTgDJ2+yMZ7bemrigKnmE5MyouNtwrXjErMQVpV5R0Gf7frjRWm/c0tRMD8KnH4baHU45WkbYkf03/oNT6keFbFi6lyAT64/wBjWbHiOMYEGRR+JKxJIA3Ott4ethprHbKeSQQpDRNIQfttlTy/MsdZ9wFYv2hE1RIocyTpDED3ZmC/zYa+iJbFQ0VLV3CvqUK0XLBChAAlIYBiBnYAhjk7bb600t612jMT+KKbaGUQbwzZbn9WpnqaWb6m6yOkhGMhULYHruBotLFRG3Qxn/GaMO0nLvznJyPXHT0+ep44hul64NraaFaKWgo4woDtytFzNjnT7+Pw699tUK019TJcnWSSSaMIZqpmbcIoyzZPTYf6aJ1WhfUlrBwRE2n8Rr0oSrJYH3lf+kq58S+BHQXGsmmt4JESFiY8ZyAR0B77DsMapFmvFTYJ5kjiFZa59qugmOVYHuvofQ62GWotl7oj4HJU0zDl82Cw9m99ZvxbwnLb5/FpSZadm2YdY/n6jSgBCSjcGemqtKgEdS58PcQxfVP2jQ1grbbNypM9QTlcbCOqxkggbLOAWXowdOhuKgtpkkuFOr8qkCSCXHPTsRkBgCRg9VYEqw3BPQYRablXWa6NWWyRYpskSQt5o509CO4/lrReEuIoKmJa20M8RgUiah5Q8lIDuwRTtNATuYjj1QowBI216m4hrKtohu714kEca5PO4LDHYHO36ah2tT+3Isjo/N+QOis8FHdEjrqEosiJ40lOjl1KZ3kiYgF4weuQGQ7OB1Iyi5v2zGcHPMf5H++nmmGnsYNUMYBz+c81fVqKFIuOcsMflmTrwcKoHfOdDqo4EWdv3bY/M6I3ld1J6b40Mrv8VV9IgPzJP9dD0j0RmeTOq/4yR2jH8zqPZqt6SeN13AOSvrqTcVw7L6Rr/NtDaUgPk52U9/bTrwStbFdW955zx+56jWyHGJG4/NHMtJVUwAkkZg5x6Af31T2kHMoG5JA0Z4rLeJTIGwOUsf0/toJE3nQKCcMN/wAdA3hqbjVX1mMdHcL6FufszqqIasdmOPMNvkNGKBWal5FyoKnf10GqgP2hISej499HaRs0y8owMHfWVdQYktNL7MYAjlAgjhqDnOyj/wCy1MtyMyOzDA5gBv7DUakHLSyN6leo99ErLUyRJKwIUMpQ5AOzAA4z3wTo/RkreAPiKPEseR6vmUisyr+GoBxIM4+eottAN6uOSMmFgB3+Ian165ZhGuwcHOPfUKgQLfa18/FCxx/3DQWst3KfznovD68Y/KaxwRNMOH6DmwYzAoMfYj+n4atKrGUR4t15gN+oPodVjg+F14foz/6f5bnR4u8IV02JYAg9CM9NGPplvrUr3iJV1D6a1w3WTI0CnxT8zohb1BqSGPWJ/wA+U6H00scxaSE/Cx50J3Tfv7e+ptK4WqTOe4/PbS10ZKyjd5jKp0s9SnIk2st9teJK2SuIrjLAEpgnxJ4Y5mJ7b/11SK+sqBRCk8VxDytkZ7g6tFUf/pOnY9kA/Lb+mg96t4E8qL9mV16aU79gH5zWypXzmBrJI0leiyOWVgRk7ncdNQnwcnqpG+lbhJSXVCVJQEabrQ9IZyMssbNnHUYOvTaLxBSm155XX+HMrZqkijj8Sz3CIDKhVkwR0wwz+mdUy9WllV2hHMpGcY3B1cuHzU1DzpErRRzQSICBkklTjHp+Oo626UYxG0o5TsN9uuflpZrxXu3Vx94XdclYFvchcI8TycO3KGiuDiejliUxu7YBQjZHPoOgbtjByPh096G2322CSlc81LE55XwGVVy5BHt8/wA8gmvX76MHuX0fvxDHV0yz0FQ1K0HiA84B2Kk9M52zsQR01RuFOI6rh+WGOrmIp2zHHKc+TGxR+uU364JXPQjKlU64b0R6NuoTaZu8Nvt9oVhUEB5YSscLR5DdWz7EYXGfX21Tf2pSw33FQhrIIp1d0XCl1x15vXfOBqwS35+J2pqmZhJIhVZgMZTyBQQN8ggjfJHTqCGOZVsVTSVeJyzOwKMzEkPg9z+OitKEJ9fMU6uuyvhPabXV2C2Xex19xp0BqUctTk82JOb4l6ncA5x1Gpd44UgpeHqejZ18SmK+JIN8Njr69tZhYeMKmxXL66irPSzxxtLA7bE8oUkejZHXRm5cV0k9orqSyfWZEIWZllchychT7n4ug21S/T6lbQqHI7EvXqtM6Ftu09GVninmhuXM7B1K4UHO3KcfPpjQ0uJLZIGPKI5FkX2BHKR/9rpisrnqWzMzSEdB93XNv53leMkESRMmD3OMj9QNagEHBmSEFeI3PN4sgCsWblADH0AwBoY6NBP9YLMJI3DgDr10Vo1Uyfulzk8oIG+fYa7uFlqwjPJEYB4RlPjHk5lA5hjOMkg5AHXtqgDYzNkZN22D75IDfZeYkRSAOFHfmGd/z0L4egBu8lG2AZtkyftDOP5nRC8gyQ0FX05oBG2O5Ukf20GqnNLdaesQ8uCGJ/Q/11o3DQmrJBWEJ6ISFlzysNxpWi4m2OaOtUvQybEZ3jPqP97fLVgusSNVrUxDljqFEy+2fiX8DzD8NDblQiVSyjDY69jphVWLU2+46MBN4RsMOD3J8tN4TB42DxNvHIvRh/Q+2iNxkNS9JdWOBOPAqDjpIu3N+IwdV+grVtKxQVOXttSCMd6eQdQD6dCPY46dLFSU/ixy0IZWjq1DU8udjIu649zuCPfW34jzBtf6lgtul8g7q+Ub9o3LEYzysRnGQR0I7Ea4QGIeIzCMA5DE/wAtRP2oI0ECoZm6jmHwE9ce2vGjlnbxJ5CzegOw/HXL9dtGF5nKtOG5aTb7IVq4bvSIGSuXEjfdlXZvlnY/jqK9J437ydzKTud8KPx76l0CRVdFU2tGDTBfGgUfDzjtj1I2/DQugM1ZAviucDblXt7HQio95xCXYVruEUcVI1Q9vkciOpHIWXZY335H/A9/QnUc1NVc4orXXjw7rQuyQux/xQDgxk+oxt/8aLfVqdIvNjpjC/7/AJagcR0rVkEVzRSknMIKnAwfEUeST5lQB8wfXVrdIUAKnmbaTWB8qwwIRhkM9IskUbK+MNnsRsRpqBZop0qElKPEwZG6YI9NLh2u+tB6GpAFfjnU9p8dWH8XqO/Xr1k1ME00mH6+g/30+WjNPd5ikHv3g+op2HI69oUvxSaClvtOi8tUPCnAHwyrt09x/Ieug9ZRvXIVbfOxX19tFuHGhKT2KqYCKr+HAz4UvZvbOw/AactFmu1wleFYWiVHKydlBBwct1P4aH/EJUCvc0FTMQeoOs1VUcq26tMck8eI6aZm/wAQDoj/AMYA29QPbVvS01NTZ6Y1yyQtSSllfl3MTfEMe38hp1uDrZT0UsNVUOzzx8pCbAHqCB1yDuDqRwlcKx6kWG+zEVsClYJSMLWoPX+IAjI9CDpVZd7Z4/iM0qA594Vt9FRwx8lJTc8w8rFRncepPbofx0xd+GKisjFUk0cVZED4OF8gz1RvVW7+nUbjVi4epBETS8hXGAu3Udj89ip/yjVsorBUVEDGOIsPbQvmtN1UHqZjY45quyyQeE0U1DIQ0TkFom6lT6jByD0IwfXRumBlpxy9cbaK8TcO1drqY79RQK9TTryzQs3KtTFueRj2I6q3Y+xOg1quFFUxeNRF/AkYlVcYaNs+ZGHYqdtM9JqyfS0FsrCniRppJOG6w3SKNpLPUPzVsC7mmfvMnsceYdx5uuc3uN6WtpA8LKycoZCGzlTuN+/z1XIZU52p3UGOT19f9/zGhdDXjhapWhqmf9jSsFpJduWjZmOY37+GxPlP2TkfCRjZ0I5EsoBlotNyk4avUlwgXnoKlgLjCoyQRsJkA+0BgEfaAHcAatnE9RA9Jb+IKCeOWM4Kyo2Q8ZBYH3HX8z6apUwILdOU9NUXjlZbZTLdqGSoqKWmck0izEJTzNvzADbkbfPTDHuCcA6qjYQ6/rCdPaCNrT6CW8UDW2KuM6eHKPKFPMWPcADc6yb6RfpptttMtBZ/+OrBlfCp3B5T/HJuF+S8x911nXE9wvPEf0f0twoKiroDBKKW8UMB3dTtG5IGSudiOmSdttAaG02u1wiSYK8i7eGjDA9i39Bk/LQ9fhzM3rOB/Mrbr1QAKMmdXCTiPjGcy3ipK06nnWmjPJFH7nPU/wATEn31ZeCRaqSGo4dq6hGpK3AfryxyAjldPUg4JOw2740Ltl0DXCljkSCOm8QAo6nkAJwTjfH+Y8x9tSK20/UKlK9qulp4qgM3gQSmWaNCSAGJAwSN8nt+WmarXSuxRFXn2WtuY5MIwVV1gus9pNJHT1tK/hyug3fPRlOAI0bqAN8nHbV/4a4toaK0y2a/SpVUEgCqnRKc5yWLdSfbrqmV9zWvsk1zs5iq7ja4FjrYC7Hx6XflORgsYzk+h77nanmauvS/WqqeNIBjphI1/wB+2ToZtOSce038wp6l95a7xxFbKWcpaadaqoVmBk8MLCRk4IXqx75Y7HQqgvF5iu0F5qKkBkbPn38VehT5EbYUYG2dQEqqSlXwqSMzS4+N12PyX+rflpr6ncbhNzOsnKxAJPf0GdXrRazmYFyeTCfE8NNaXgu1jgU266sZIZRuYJN+aL0XfJB69cYxvFtVrrrufELEId2dunz9T8zovZRbaSml4Zu9ZF9WuTgKoOTTy/ZkB7bgA/hnUyg4Y4uvdXNbpfCttDSyeEzRZw+OhHc5GD7Z7azutRBuEJWprOTxKrVQW+3VDLLKa2cE8sMP9T0H4fno3YuD+IeIQpqQLVbTuEQEZHy6sfy+etW4c+je12akSpSjNTN18eUZyfUDR6OEIOVhuNLrtRYwx1DKqVQcCVGx8H0ditzw2xJC7bygtvLjpgdAw6g+u3fR2zOKqMgsDKgHNjbmB6Nj3/Q5GjEMeeo1DuVprKeX9s0MYKKT4q9BkncfJv0bB7nVav6q7G79pZgQciS4aRSvrrloGjO4+Wilgr6IwioaHxI3GVPcH0I9dP3Gd7k6w09LuOgUbj5+2stgI+8so4gmIgHHfT9TaP21StAIwzrnlcjIGRgg+x6Ef1A0Zt1gC4etfmP/AE0O34nv+mj0EccUXJEioo2AUYGi9OHTmairI5mSUkdVYq/9j1/Nyk4pnY52+4T3I7HuPcaKjBGRq28YWCC925oyMTKMow2OQcjB7EHcHVBt1RNHNLba3arg6nGPEXs4/qOx02rfePvBbK/LOB1CLxpIpR1DIwwwPcaDVNO9FMFJLxt/ht94Dsf4h+o0Z7Z1xOIZYHhm3U987qfUe+tVJBmcGqEljwTsdwdAL7SyQRmMQpLTSMA4ZuURAnPNnBwud/4Tv05gSP1yCKSaMVETlDhirbHPRh/UafaiNRH+8qM5GQFG2Pf1Gt87+u5jjHcz+r4/qvo/uXgc0plZfITHnxV7gDOM9jnod9x1jXj6YeJL0Clsi/ZKNsZmfxahh7NgBB/lA0b424Xhu1vFFIAssbZopiM8j9o2Poex/D01k0jR2qSWmr0ZaiI4eL4FU+7dT22A/Ea5Xoab23XHJHtM7NVbQu2vgfMKK1TVzmSWSWqnbLM7nmb3JJ7a5qKmmpYiZZBKe4RsL+Lf0GfmNBKy61NSnhRqEizkLgqn/t6k+7ZOmYoXmmDSM0jdBncn5DTinT4Xai7RE9uqGfUdxhux8WVVruLTw0qz0Eg5aumwFSVPVc78w7En205xXw/TRxx36yzNVWiqOUPUwNn4SO2/btn5aFvTxU4YVMgRv+mo5pPxHRfxOfbT3DvF0dlrmhSl+s2qo8tZTBixYffBO3OPYAEbHrqj0rUwark+80S02KVt4jJp4YVzWS+HtkIBzSH8O34kfjqJPdhGClAhjYdWU8z/AIv2/wC0D8dE+NOG0pFS72qoNXY6peaF0GyZPRu/Xbfodj2JD0FE7weIqhIh1kc8qD8T39hk6LqPnJudsD4gl2aX2ovPzITGol2dzyk55V6Z9/XUmntzSRkgDwhs7thUHzJ2/rqTLUUFGBj/AImTszAiP8F6t+OB7HQ+qrqurPnOFGyggDlHso2H4a0Dj6al/WDFNvNrS2cL8T2+3Uw4fvsn12zTeRZXU4piegGfMUz7Ag4I1A+kKxXS01MciTfWbXJg0864KqD0XCgKD6EdfzAraUxYMWBYnYk7k6uXCF9FnoWsvEvhvZKjyIszZeDJHRevJnfsRjI30BfT+GbzCePiMNNeNUprA/WUkU3PksAT3LHS1fr7wpdbfVKvD9livFFKvOsxkDOM9AckDHoR1+YI0tUPjGnBxsMg8HvYZ3ib18IwPi9NeAb4PXXqLgE5yTrrff115qetnQAXYb56n117rxRjcnXhPbvrkk9xvnXoHYfider5fLpNucA/6akkRBJwNdAADAGkAMcoGBrpVLZxqSTwAnYbAacBAG2Ao10MAY6a4Jycn8NSScEk9evYaA8b8UWzhOwVF2ukhEcYwiAjnlfsijuT/c9tEOIbxQWK0VFzudSsFLToXkc749gO5PQDv018u8YXm8fSBekv9yp5aexRSNFQwkeUAYyWPdj3P4DYa3opNjfaZXXCpcmDLvdrnxfxFJxHe23JxS0w3SFM7AfL17nJ1Y7Dfo6R4CDJTTRPzCaM7hvvbbg/LR262DhVXt9Hw5fXqY5oFasqaqPkjjf7oxvj2OceuqJOsSzuIGBQHCkdD7j20zRa7l8sDgRFZbZW25jzDVJaqbiTjMyXC+tbaWoZ3krJlaVgdzuAckk++2q9PN9RqWppSGUEhZFUgMM9cHcam2qtejqxKoVyCPKwBG3sdTuIayPii9PWVixQyykHKIEGceg7n9dEVW2U2AL9GINdRVenXqg2GaNQWDZ9PfSR3duaQFQOg0rzwzd7TbobmYZjRzORFL4Z5Gx1wemdQ6CtWRQJvKfU99Mq9RXqR6TE1+hejmGqaqeMZLHl9NWGx8T1tAhSmZfDZSGRlB/HfvqoE5bIPl/nrqOUliIjuB+A1q9YPpYZECrays5Q4M1Wp4vgfgyotZt9JJEzLIZXUNMp7AHsD+e51RvqbzUMtaKd2jQjxJVU8sZOcDOhqu0YKS5z3J9dGf20Tav2fGjRQkDnUP5XYfaI9dC16Tyx/SPBMIt1XnZ832E9ttxjpomjeFn82VPMNvz76t9VRM3ClVdoowael5BNIzDIdvhAGd9USkejRZTUBnPIRGEbGG7H5a9LVyUyUzyOYZv3gQHy55Rv+RH8vXVdSNxArP8A3O6ZjWh8we3E5gaSSdppnzzdM69MYaUOd8HbO+vWbwsgqQTsNcIrPjfC9T89EVV7jyIDaxxhY+OZ3EcYOBuTqy21EpKPnYjmYczE+mq7CRGvNkFcbjTNfdZq91o6RWLtsEUZz89E2ruAHtDNGm0lscyXeL6VbFKxznYjqTnoBo7ZqyqkolkuUSwSE7Y/r6H230LtFjjtwWsr28aqYeX2Ht6D+Lqe2p3JLWlmcqkcfxMdkjH+/wAdL7mRxgDr3npNLU9Y3MefiGSCw9teA40Mo60LKsdNG7UybeK5PM59QP6aJjDjmB3PbQTLgw8Gea9UA9ddbdxnXLpg5A1UcToge9WSCtVpIsRz4642b56o9xtk9JMyvGY3A+H19xrT9t/1Go9ZRU9ZEY6heYY2YDcfLR2m1rU8HkQLU6Jbhn3mVq5XZtSUdWHXRe/cPS0vNKvnj7OB0+eq8Q8UnKVxp9Vctq5Web1OkapsGT0Izkan0qh0Lrv7aEwybep1IpZ2glWWMgMpBAIyD7HXHrzK03ms4aXKlpgKNYJGLTY86vjlbPYfLpqo8U8JJIkk1vXDbloT6/w+mict5nmiRaaIpOx69cH29T89HuG+H6tY3qK+pkV5Rnwzvgnuf7aX6kJpjkNHfh112pXDiYpV07LMPFd4Z4z5ahR5l9mHcam0F1np6lPGk+p1oXEc6YKSg9QexB7qdjrSuLOF4qgsZU8GoOySqNm+frrKrvb6q3VDw1MHiQnP7s/CR6qex157xCmhgLKuGPYnodJZYvofr5llpqiOcLTiERy5ytKrYGfWnc/CfWJjg/ZOrhwrxg1P4dPd5vGpieSOtCkFSPsyr1BHv+o31ktNUmKnIkdqqiGxLD95F8/76N09wLIJJZudXUKKvl58r92Zftr/ABfEvvpTkHhoacEZE+g6d0ljRomEiyfAV35s9MY66ZuN0p6CMqPDnqAOhOY4z7/eb26DvnprJLBxFcbMrUtM7GllXnemD83l7tC/2kPcD8R31ZI7zTVlHz0xikiJGQyDmB9PUaM0OiW+zGeIl8U1raOkuoyY5dLhVVlQzvKzFt2dviOqRx9cjRWh41bEs55Rj07/ANNWiSVS5wANumsm48uf1+8uiN+7i8q+m3+udepvFek0+1BieO8N87xHWB7jkDmVtjht2yTq38H0op7c1S64aY85z3QdB+JJ/MaqtJTtVVcVOv8AzGC59B3OrjeahaK0lI/ISvKvsBsP9+2vMI3Jc+0+ghMDaJU+Iqtqu5uAc5bA/wB/PRLhuk8atReUciDQWkRpah5D0BwNXOwJFRUhll3Z/hUdTrOthnJlNSWxtWHPJFGSxGAOpOw0KuFwwpVGZQdgeXzN64/2PcjvCulzJyXZQFJ2z5UPvjqfYfiR00IzUVztykpGdiT8Te23Qew1W3Vk+lJhp/D1r9ds6qK1pH8GnXmbm6DdVPqT9o/oO2vIaVi2WPiSnq7f00UtdpkbCRx574xq1UFlhhVZGCtPjOcbf/PvrEU7RluTCG1YPpXqB7FZGC+JUDkjIzynq39tWFIUVAsYAVegHQacI5V8+2+m2JdSAeUaK02lt1JGOor1fiFenHqOT8Ttagn90nUdW1MpKpVHhTrzKe/pqDUrTBIVpvFMgU+KzkYJyfhHYYx3P4aeoGg8VVqnKIWCliCQgOxY43264Hpp4ugpWoqw/WebbxHUPaGU/pLBXoa6CNp6rxFROUGWTKqg3wCfh6k46ddtYbVCQzT1LU0ggqGbwWAKoDnOOmDgdu2dXDiy9y2+kq6ahnEsMnND4uDyyKSRkA9CRvvvqo/tKvns0NtkuEj0lPMzw0zMcIzgczgdN8KPw1562s1MQGyJ7LQN5tfmFdpipEPKq/fIH65/+5Gp95CpBTxjHMVLn1A6DTdBF+9VARsP57D+WpvHIoabiKaltdUtbBTBI1nA8rlVGSARnlzkgHVGbkCHMTLrw3XU9mp7NTwkmanIqpWVAw5x8Kjfc87A+nl9tXAXqou0kcVwlApVqYzJChGZGwzFj6knPsMnoM6oX0W25q+krrnVyM8rTIqu3TygkjbtuNhqdcKarhrndS2HPmHQ47j5e2pQiF+e4o1qu3A6lglr5lqpntlSlOKRWliBk5WyDkLGR1bcYHtsdC7TSXGsqVklneESKyeDETl1YEMG9cgnbQqGu55GZRyyZz1/3jRrh67T0FQ1VHiQlCGRj1J6EE9Dv+PfTB9TaFKKYpo0tS2bmECi5VVvvMktC4iUOVKH4WUHoR31eLHfLfc6Zm8PDhT4kbYJB6beo1mc4dqxi7H1/PVm+j+nilvMTzANFGju4OwICnH/ANkV0MND5y7j3Gj6oVn7CR+KuDEbxLhZxzx45niHUe6/21RB9boav65SzvT1UB/dzLsc+h1utpjZklljhfwweoGRj30A4w4Vp7rSyz0IWKpO5U9JO2D/AH1Qp5amq4czejUi1RZWeDAPC/EyXGUCMCluit4klMj+Es7gY8WFt/Dlx8ww2YMu2rfbK6Coqo6gopm5jGMJyeI+PhK9I5e/JurdUJ6DFK+3T0crJKJIpImyp6PGe2rNw3xMamYUl0lhirWURpUuuYapM55JRt+ByCDgggjOgSj0ncp7jICu9cMMzTbxIkkUbIwYY9NCKr/zC8x2IQfyGvaesEgkjqC8ckQzIZWy0Y6DnP2kPQTD1AcA+Y8VsUpqeUqwYMqkHYg61XUDZtHcHsoKH7R66OxnkA2HKoP5E6G064zvnynRS8R800nQDlGfy/015ZqBqsSLH1Cfjp7/AOPAqHdj8Tyn/koLmute+ZSuKk5q2EE7CLIA+Z/toVTkeKqjGzDp89H+PKF6G/fVZ8hlgQ4+eToFEczJhR8hrR2V7GYfMI0lTJQit7CcT8puEpJyQ5/Dc6PUpDQqqjlwuM6CsoNycE5JY7fno/S0sskOFXlXHU9NACwDOIa6EkRyjQClkGSSGXU61Uz1M2PhQMMnHy03BTiFDGX2O5xt2Op1mnYTikQcpyDznoQR20RpbALxn4gGvpL04x7yt3WKCnp5UUeYkAep1XqFWN6qP/8AHP8AM6tdzgVIao4Jbux69dVqiHJf5sjf6sD+mdAaxsVnE9DoV5GfibLaqWts/C9qkqqCoVqlXWBShBk856fmPz1FvdReKGq+q19B9VbCyFHGSAemrhffpLouJrfZblbbckNTQl8iRwwOGwRkbDoTqv8AHPFdVxBdxLUWmipXaFIGCKSwKtzc2T33x06aN8Eu1L11+bX2Oeep57xxalazbZznqVWkq5oaoyxvhwx3x27g+o9tWahZaoLKmVZSDJHnce49v1GqcCRIxO3n0WoKxaaPxTN4bofK2cH8NONdpEuqJPBE8/4XrLKLto5B9odq3Za1Afsbb99P1kZeWRmGS0gfA9//AJ1Grz9aqZHWNo5Ff4MY8TbOVHb5flopTtDJI8QJMnKpVT9sY+z77dP9nwuorIyJ7pHDDMqNRSctW4IyMkj89RLrRNHU1DY/dsc7e++tRt3Ad1vMAr6Ck8WnkZlVsgbgb/y0Jq7WscUskqnxeXbO3KR/XXKrtiGZahCwBxGLJwFfbdZouILhQmGiDI2GbzYbplR0986C8QCKimjaBSUV+UrnDg77H39+/wA+pSv4+vk9jezT1jGA8oZQoAwCOv5aqd9aWesnm58gblR3HXP66YeHeWSPNi7XtYKv6PeJ09dUpZakKVy0ylwo2AK4O38x01Rq6hhetWblSRRKC6+qnr+mrdSOJKOrUd0DgfIg/wAtAa1Y1n5kIDH4gvc9/wAdMPENEqjzE/tBvBvEn3eVZBXDfEFZw3djRzyOIoZTGkmM8mCRg7bpnO3UZJGckHR5hS3qhaqgUHB55Y1IPIW+0p7qdj/fqc+4st6VU/1pAMzIspwMZJAyfnnOoPCl+rLBPGxkcU6yFQeUkxd+ndTvlfmR7o3QqxKz1wK3rhpbbhTNFTwemHiU9jg8w/npmySF6mRMN5o2UY65xkfyGrVm33izNVUajZ1mlhU83JsQWU91PXPt7ECrS00tuuUbFv3aS4B7EZ6H8NE0ajJGYp1GmIzxPUZJoDzRqJUyTJv+86Hzb9dj8869tzrHVwyyEYWRWYe2d/01EaRqareMAZUlWU+xxp2mOQw1aw5bMwrG0YkyneSlqaiOMDmRmA298acub1T0yvNO8yMFkUmQsDy7fgQO3bXlX/8AtSQjpIFkH/coP99RWwAScnlO4zrNsjqXXhsxiqhLWZ+4p58/9rD+4H56C3SISUCvjzI2PwOrIIJYjW0MsTI/gkMhG+VwwP8Av10GEayQyR9eZdvmNUBOBDVODDNhkFdwoAcmaiYN7lGOG/8AswT+OpdNCJoWXGSDtoFwTVpSXPwZiRDMDHJkdm2P5Y/XRkrPT1UlMMRhCVY564J0bTaVwYBrKvXn2MaqLdFVwTW6R1WWYAwZ7SKDgfiMr+I0EsN4NBN+z68TLTLIDG7bNC46f7/D0xYnhEZ5y3KyNzLIeoI0N4toVmporjDCripBD82wV/tA/PqPY6zv3XEsO4Zo7UCbD1Cl+iSGdavIkjqh4i+F8JOdx+fb31Dp1nqJFgVeRCcBV9dCOH7lJSqtruvMaUt+7k7xN6b/AOz+WrBP4kUnKiryturjcMPUH0/LW+lUM2yweqBayt6sPUfSZ1QFLfVw1S+UxOG266ZvcZpOIJ4IvJT1GJosDs2/476c8FyOZ+3rru95msNFXxjz0shgc9+U7jRVnpIPxK1+tSDG4isXxnc+vXT1JNCapoJzimqU8KR/un7LfgdQ4F8YLIxyMfgNSRE0y+FTxCZidichf03Ot7XQL6j/AGg9KPv9A/WB2ts8FdJFMXinhchZVOORgfiHz6++rTw08vENSKGR0p69R51PlEw++D1we66lHh+etkojcswzcnKzFfiKjynHYkAjf099F34fhq6D6vblEdfRyCWnrY8AoT0LHuNiCPYaRam/nK9z0GmpymG5hi3cM2q3APVEVEo+FcYXPsBufx1MoY6uKs8HnMMcxOSy5bmHp2BK4/EHS4IuaVxmobjTpTXul/8AMRk55x2dD3U+39wLDW29nkimQdwufRhup0AbN/E2sTyxkTyloIoMsAWbu7bsfx1Dvlhp7igLB0YEMssfxxOD5XX3H6gka1Cx8JiptqSyEoXUEKRoddrZFQSsjEMQcap6u2l8HG4Sv8AO0l0FFe4xHXUiiSUgeSePOBMn8JIGR9ls61YXC3UY/cshjbfK9NZXxFUyVlPEPHFLVw5eiq4lyUfowPqp25l7g564IgcJX2W51E1vrA1LWw4+sU5JIR+zL6ow3B9sddU3maVEAZl14puMVVK6xAOrbY1kN3t9RYOInqYoZJaapXmmp16yY6On/qKM7faClfukalFEoOFXJ9Tvqr/SJXWtLUDLUKKmFsqVIwPbPr3wMn21ai1VYqfeVsUn1CCoKiGpp0lp50niI5opk6OpzuO/4dQRg7jT1W8FbQyU1RCKjxFKuhXKnbfPbBH89USkuBtTi5Upka01LlqmLPM1M+fM4HoRuR3HmG4ObbBUCKVJUbxKeZQQVPMMdiPXr+vtr0FNpZOe4GRzx1INmqqu2Tx8O3aZzTyZ/Z1Rzk8w/wCg7d2A+E/aGx3G53xKeEGKdEeCRSjRlchgfbUC729LxQSUtQnJC/8A7wQcgg/ZIPQ9RqDYK2WGsks95kzXohaKpI2q4x9r2YbBh+I2OtBWOVPRlSx7EDiReFOJTbapBNY64NC3MMEwt1RjjJZOq+q5HXOa5PYam0XuqtdRMpigIanq5DzeLC2ShQdScbHAxkHJGr3xNDTXa2SxGLxvDHKT6HsQfX3+Wqhc46i/cL/UpWccQWNGkpmGxraM/Gnuy7HHsMdTgcq1Yx8SrqH4kR7hSWxmSjjJlzvKSDIT/JfwyffXgS73sCSVuSGNAoyQPKPX+51Fo47dSRJJUSLUzYz4cbAgf5m6fgufmNSGrayrURRhY4fsogwq/If1OTqqkD7mBcjviTrNcIOGbjFVUxNTOnlkVThHQ/Em4y2R8gDjrr3ieyzRX2nNslea0V8Pj27l+wn24h2BX2/XB0wbSIKX61W1KU0Xq/xN8h1OrJwk73qz1Vhp6eqpooh41vr3GfBnORv6Bgcfn651V7FxtzzCNOjEH2EagorLY6RZq+dGmIB8NfMxPy1IoKTiPih/CtdKbdQHZpmGCRq2cB/RxbIYILrc5TcqiQAsJN1jbuMH0ORrUbTSUUEiJPEqQLtgbY/AdtKHvZzjMProVTxM74P+jm0WlhNVKK6s6tJKMj8j/XRvBstyXmyaOQYz/COn4rn8VPsdW27ULU9RmCNjEd1c9DntodWW9ayjdJ5Cmd0b7jdjj89u4JHfWathir9GalcH7w1YbgwAp5iogxkErn/Y1CrqWNKgtE6lW36Yx7aCcN1Uyq9tlwskB8mTk47rnvjIx6gjVqt9qqagB5h4anu3U/IahVs7JsuWHEgQxDOAuT20Yo7dVSwvHM3hwSDDowzzD5aK0lFBTDKJlvvHc6k62SnHc2CD3lH/AGVDY7ysU7SG21J2fO6P2yf0P4e+rjT08MEQSFFRfQDrri50UNfRSU0/wsNjjp76FcOVs0FQ1krz+/hGYXJ/xE/qR/L8dbbV7kAC8Q3rpOh171GmpJVijaR2VVUZJY4AGpwJePapn0j2FqmjF1t/KldTHnQ5wD659iNiPx6jTnEnHlls9I9RU1kNNEBtLOcB/wDInxP+g99Ytxl9N1wrfEpuGKZ4gdhX1a5f5og2X8cnVa7iXC1jJmdpRVJc8S5UV8+sRGBaaQVybTQE4EZ926Y9MZPtp00dRV+aslLr/wBJdk/u347ew1nvBfE1VcXR5wrXmnTDquFFdEOu3QOOo/TbbWkUN5oaunVqImqdhnkj6r/mPRfkd/bTeyt62w0V12LYNyHiMVlpilhTkVY5Ym54W5fgYZ/TXNDOCGUlQVfkkQEHwn/scj9PXaRNDVVJJqJPDT/pREj8C3U/hge2mJKDwU8SiijV1GCmMLIO6n+h7fnrigg7l7liR1HaymSoiaN05sjBU9x6azX6RuEReo/GjVRdYFJhlI/8wg3Kk/eH69fva0ugmSdAgLZOy83Xbqp9xpq50QmjOQQwIYFTggjow9CNGVWZIYdzCxAylW6nzTCsVOjCtco6HDRJu4PoT0X9T7abnvBCslBEYlxgmNtz836/guB7a0D6TeDTcfEudHGBcIF5qiJNlqE/6ij19ux27jWdUNIQoklZYYTsGkyM/JRufwGnFVgvXdY2PtEF9bUNtrXv3kVY5JjmRvL93oupkFvIi8V+SOLtJLsufQdz+AOuqivo6PyU0XizD7cqAn5hOg/7i34ag1NRV1cxaSRubYcxPM3yz2+Q0QlmeKhBDWFG61syxcOcT0dhke31SSVtoqziriYDy525403wR3ydx21xx5ZKqgliuFFVCss9SoamqVPNyqeijsB/8HfrX4KF3cJFGzux6KCWOrRwteqbh+F7NfZoprXVtyvSj948LHbnXHT3Xv7HQWprXTEWFufiH6a19UprVePmVKnpiWHKpMjHtks2iDUsFGvPcqhKYdRGBzSt/wBvb8fy1aLrwff0ukVHw34LUFQnNHVQ7uy+7Ht75x7ZB1aeE/okoaQrU3qoaqqOpRGOPxbr+QGgtV44R6KVxCdP4IhO645+0zi0xXe6y/VeHLXJCD/znXnlx652C/pq+8K/RIiuKviGqaWXqY1PMfxboPwH461G3W+loKcQUVLFTxD7KKAP9dS1jznbXn7b3tOWOY9qpWoYUYEG01gtUdJFT0sslujiXlEUcCzIfcB/hPrjrpaJiMjS1iLLB7zvlr8T0baXTc6614RttrXM3iBJ+Hrr2Pyj+eko3wPz9Ne8p7/gNTMk9B9ANegenfvpAYHqe512o236nVhJEi9RjTmAFwNeLsDvpE467e/pqSTliCD6d/fTFwq6ehopqusnjghiQvLI7YVVG5JPpp2R1iRixCgDJJOMDXzj9LHGlTx5eX4bsdQ0dgpXzV1K/wD1lwTsvqo7Dud+mNbU0tcwVZjfelCF3PEa464hqfpK4iWiopXXhqkdSvKGDVEhHcEddyPQfPV2r+BrpYuGqK4SrDFT1SgRxBgQFxkZX0x/sapNuItEUCUaeBHEMRgfz+ejk3ElTPSrFPJIZB5RzNlVB9B2Onf4Z6lVasfeeUs8QW5me3I+IG/YD3Wd4LTFJTVLZ/cKSY2Hf/L+o0ArLPUUcz0tfFLTVSH4HXAPy9dbHwWlqhsFZPBdZ6at28KIR8xmPufTVf4mr3rZfqdaorFH/UQHl+RG/wCWs9xdjWs1RtqB7OzM4tNhu90ubUNtt89XOqGQpEhJCgZyR2GMaiTKYXLDt3Prq50NPVWqrmqeH7jVwtNG0U0POVkZTsVDfaHtsdNX7haGLg+HiH9s29Z5pzClr38cY6sfT1xjpjfO2p5j1uEPRm6qliGxTB1Rxne6zh+nsNbUtPbqbeKnb4VOMZ/DsOgydFpuArZW/R/TcS09VTxzNI8L0yVGZWOThuTHlx6em/fVGkDx4yjZz6afpa+amR1ibBYYB6Ffce+uvRx/QODOLcCf63MH10NytM5p6lQUIyrA5yPbRbhS7xWy60typ44Z2ppFkEUy8ysQejDuNGF4lqrjwqeG6qlozTmoNQ0vgjxmbBG7dcfLtgac4u+i64cOcPW67zSiCa4qZYKYP5lQY+IEbbEH8caIq1u0eVeOTxBrdAH/AKlPQjHF/EdTxNxDVXmthp4JZyMxwJyooAAAH5dTobSKauVkjbkRVLu+NlA7n21X3rJUJSo25djqxW7iaVOD5+HxQUIgnqlnaqEX/EbD4ObPw7A40c7eXWEqH/UVDTguXtP/AHGoQXlUl3SJmwxUZOPb31b6Thi6Q8PxXqWnmFPNkRHkPmI3x/PVShkZ0jjhi8oIDEb5Ynr/AKauY+kC6z2VKGtlkqBSqVpADiNSTuzDv120NYtvVePvInlnJsJx7SvytLJKGmjKldgDtsNevLkqVICqNzpy4UVyprdT3CrgmWnqEYxyOpAcA74Pcb9tMWu21N2YMC0FGBuxwC3y9B76YVutaZzmYVaW26wrtjcMdTc5/qtEDy82GkI8q+3ufbVioaCksqGONRJUn42bfB/i9fl0HfTsLRUUIpbegQAYLr1Py7/j1OusR0pU1CeLUN8FOB/9t/bQdt5sPwJ6XS6RaBxyYuVShrK+VkiJ6/bkPoB/XpqXSUU1xKPURmCkXeKAZHN7nv8Ajp+22uWao+uXIiWb7Mf2Y/w0fii5dtL7tRs4WNtPp+MtI4t8LxhPDACjygDppiWiaAFiwWJRkuTgKPfU6411NbqbxZ3xn4VHxMfbVNut3nuMuXISEfDGDsPf3Ot/DtBdqTuPC/MW+MeL6fRLtXl/iFYqyCWRkjk5gD5SRjm98alDce2qrFJgjt7+miVBcyv7uc99m/vpnqvCSg3V8xL4d/5Alh2X8H5hVl9Nc4I6a7Dq6BlIIOvNJsYODPTZyMiN4DAhwGGMEEbEard/4ajnBmolwe8f9tWcjY7a5Hz1rVa9RysyspS0YaZNVU01M5VgVwcHPbXkMuBynWkXi0UtwjJdQsuPjA6/PVGvFoqKCVsoeXqCOh0/0usW0Ybuef1fh7V8r1GYJWSQMHIIORjtq7cL8XK5Wluxwei1GNv+4f11niOVPm1IWYKuQfx13VaWu9PVBtJqrdK+V6+JtdVHFUUvI6rKkg27gj1B1TeJeGlakcPF49MdyT8Sf79dVzhzi2rtMoiP7+jJwYid191Pb5dNaFHxNbpLeKi3SLUysMsWTaD2Kn4m/QfxdvAajT3pf6RkT29Gsptp3E4+Zh1+4cqbdK1TSlmhI+MDJA9GHcaDUxlhk8SjVYpTvJAT5JPdffWwVDrUSyOEyGJJz39c6p/EHDUUweaiADdTH039vQ6Pu0boo80YPzA9L4lVaxFLZx7Sv26uSSNkgUkK3PJSOeUq33kPVG9xse40Tp6snmqYZ+RlIVpSOXf7syj4T6MPKfbrqtV8BWcGYtDPFslQBhh7MO499P0lwkjnVKphTVWMJOm6SD0PYg9wdA5spbPUZba9QpB9/aWi431obfUB1MM4THKe2R1B/XWZ1LF5GYndjnVweRZUEDRYYDaAHY+phJ//AObfgdVm8QJE6TQsGR2Krgfa9MdVPsdFW657gA3tBNJ4ZTpWJrGMyfwhTKaiWpYfCPCT5n4j+WPzOmuLqszz+HGfIpwAP0/376IUhW32cgnD4x82Ocn+f6aCQFXmM0v7xuuAdh+fT5n8jod7AqhYwVMkmPWqj5IeaQhUXBZjsB/v9e2dS6yuKjkiDFj2+0fn90e25PrjbUP6zLUyCOBc46MB5V/yj+p30StlrGcYLSH176xAa48dSjslPJ7kOko5ahuefr9lRsANWS0WZn5WK+Gvdv7aI2izonnqAGI6KOg0bEQRCduUDRKKtfCxVfqGt5MapaeOBAkS4Hc9zorRUM02ZCpVOxI6/LUKzhq+8U9IikI0g5zjcqNz8thq7VTMvN4J5Bg5IONsEEa3qryfVF992F4lZq6GKSLAb94Oh/voS9PIJfB8J/E7Ljc/hqzVkTQwfWwjCJiVVyp5SwG4B7npqpV11nSVmoplE6qx8YuAEwDkDPU4PQfhp2ly1pPONS91mPcxu6ypbJZIK1HimQlTGww4PoQemgdVVT1aSSmWOKOMBljL4L7gYA+0RnPyBPbUC5VNZU1klRWzyVE8jZeWRizOfXJ07baGerlACkA/rpbq9azDGcR9oPDkrOTyYI4hq0kWGCUnc87MPtD399zobSR8sgIOcHP5f7GnOKmSO/VECfDBiI49QN/1J17bFKR8zbhRk/qf6DSzJJnqqlAUQnTN4ccsgOyjA/DYfqP10LHMzntnYe+iFQfBtwjzuwwff/ZxqBCjy1Cwx+aRiFT/ADE4X9SNQ4HMjDM3D6M7eKXgyhLDkafmmPyLbf8A2IH56N1VAtRG/Omyg8pHYnbUy3W9aGkgo488kESxD/tAH9NTTHiPA6tvpX5hLFhMCAZmV8sU9KzSIMehx10NhndIvCk8rlsHPsP741q1RSpNCyyrzo3UapfFHDroviQhiijOQN1+em+k1ChcPF2p0pc5WAxAkyYc4bbDddtHeEKWFLisE8nIrxnLAgZHMP021WY5JqZ0gm2x0ProoZh4qhX3UDlI6g/7OmqEVqD7RParEMk+mbNduAOG7EoFbBPOU3HxMTjocbaya+3ahq7zM9rphTwvuFAwvrsO3y1UYayN2EbsvP0BAwG/sdTbcA1WSx8oGt6fCNPZW1hYsT+0A1Hj2qqYVhAoH7x2/wBjor5QgFBHUgeWZRuPmO49v5ayXiKx1Vo/cVUStzuSAN1Yeqn+mtXo6yaMTcp/ddST1yT2/LT95oqO721IalA6hco3cH1GvM31Waexq2OQJ67Q6rzqltxjMyrh3id6Mw09xnmMEbf8PWL/AItMemD6rjYg9sg5GtBtlaGEMDKhJGYPAHMrDrmEdxtkw9R1jJ+DVA4k4dqLdIXOJIWyFcDY+zeh1Bsl2ltaNDLGam2u37yDPmjPXmQ9iOus3oKrvEZ12q52zW6uTxiZgYyroGUo3MrqBjKnuOvuOh0xbqmWkk8eJmR1HUHGoNpvEE9Osj1UdRTTNkVLMEWRumJD/wAqX/1Phbo4+2C5p0aNkAKkHk8y8rBuvKy/ZbHboeoJBGnngesqTdVbwTPMf+S+HXuFup5C/wB5VPpDuj3riyorp0Cnwoo+UfwoP9dB6OGR5FKoQgOTonVUYmvFTJISQHxj1wNPtgRNHGmwG+Og1mcBiF4GYTQS1Ss3eBBVHChvIV+/m3O2rfjmp8QxgkDqdgNVmhi5r1Gjbryjb21eEjCxqAowB2Ghc7WM1IyRApidGZZTzkoSfbY6LWm3megWRkblMpCuOoI9NSIYqBxVLVeL9ZaA/VuXHLzd+b2xnWk2jgWvtdot0SvHXrX5dBGMHPXuenvoPUapQ4HRhFFOfymKX+mZKKrbr131WpaQreZ5QPKtFTlvm8QOtP8ApN4WvPDtuqBdaX6vHKh8JiQVY46ZHf21lMVyd7vNSEAGaGMNkdfDjIHy21RrvNrBXnmMqqhWxBhrguZouH41jb/mSA/+86PLXSy1aPUTZPN39fc9zqr8HJUy2jw4UAUTSZdunX076tNmt6LVozFppAfif7P4dBr1tesqrpUe+J4G7w667VPk4XMhIlRPKxjTw0MhAdxufkP76M0FCsakorSycvxv1/sPw05HFHGZDK23iHbO2pkNSJEdIhhQNttjoYWX6qtwOoWtWl0TDJ5/eGL5TRRyrHJ/iySU7oAcHzIeh+eNLxo6mWnOFWpOOvlEhyR17N/PUjjip/ZdXRVaorSva6KVA6ZBIXB9u+qXPVH6vTEABSGz375xoanwpbayWPJmer8Zamzao4E0Xhz6RL7ZIDR086GHmOzjuevyP+99BrjWVdTTo4OeYFmI3PXf/wCdViGv+sqBMSZAAPEP2x6N7/xfn66MU9R4NFTGVPKGZCQdxvpNqdJZpmKsI30usr1aAqf0geamIuEi8ueePuO4Oot0R4qkTDPhSovTttjfVmrzDNW0dREhzIGDADPbqPUHGo11ovAfw2UFkyjAbjKk5+ehlsIQwpkDSmW6oaRpIAyxlo2T0zkY66CKDNEckI2diRudWCW1tFeSYgcrnA+Qz/PQN4XEtTCAAyMcMT1wdMBez1jBgyaatG3GSqkE26kdiW5OaNv5j+eg1RQJV0lXHGMTBRKvuV6/oTohAZJbTUCTK+HKrD+R/ppUXgxV0XiSYZ3KTRlSOUHbr7gn8tWFJOHlk1qqxWAeGL9W2GuUc0ixo3YZ5PUgZ3B7rtnqCDgjSVlor5RNPT8pZlDSRKdv8y+35dOg3Az66W9ZFkRxyyIxUnHQjsf76Yt10qLDWU7LziGReYqp3VgeViue+RkjofnggE145HYjgOty4Mt3EdHJBVCRd0kRH5wOpI3/AFzqLRNzDfuOnodWGmrqa+0CuhjZ/DwVUbOMnzL+J6dQdBpaNqSUHJKFtj3+WtVt38GLr6TXJNWf/JSffg5c+6sRpsnEzbZBGca6l89sib/pTEE+zD+401IypIrEg9sa0fEFGTJltrInqYKatmCLG4WGobP7tDsY39U32P2fltoHco5LTcXo3jfx4nKkEdMH+WMHOurmXY7DlR/KQPtakcRXA1NLAaiMOxVHifPnUEYZCe45sn23x1xqpGRkTepuSpldiMtPevEYk7kgDp6gfpq8XJmko6a40x8TxB4bsdzleh/EY/LVIuMUsvhVXNy4GQF9QdtXThydarhupp1AJh5ZFHoB0/8AsCNWTgzbUAOmZ5HEHIldwxI3ydvw1PooYq2Ca2YBE4zGT0WQfD+fTQ+HnbOR88dNTacrthgpXcY2x7jTOt1auJtjV2ZEq1zt8tQHV0ww8jr1399d8OXc0MwttzJemLYilO7Rt6H/AHv8+ts4kiik8GthICViksSMYlGzA/PY/jqo3S1h1ZpMdOjHHMPlqjVrameiPeMK7tr7TyD7SzVKuhw7AIRsQchh2IPfSoo1qaSutq+YzRGRB/Em4/TOq9w/dRCVtd2Mj0pbEE5BDIfQ/wC9/n11G2Wa2W+iWpjkFRLIuYXXof8AKB69N9C/jcjYRzNzoyrbh1Krwdw5U3enSedxFTjYZHX2AH8zq/W2kt9uPhUFP41RjBIILD5t0A0I4WgK3GtthlZKdWEqKuxZX3G/buNW2GKOBOWJFVQOijGdAtc3IM3SsdiC7nbqiqpmedwGUZWNBkDvknv0GnrS6RmnmSNUQ/upEA2XmP8ARsfmdF4lMoXIxntonT8Kq0FVGHwrIJVH3o22JHup2/I6Hc7h+UJT0t+cB33hiouZjrra/wBVu1L5qWbsf/Tf1Q/od/XNl4HvYuVFOldRNS3CjcRVtNIPNFJjIb/Kw3B6Ht2z5bKmYU6+Kw+sRExyY++pwT+PxD2Yar3Ey10lzW+WeoC3GBDEUPwVCbt4En8JIPKfsnPbWSjPU63XM1aj4vkhiK1PIrIeX8MZzoDf6+a7Tk04wCNzqoWO+Ud8sb19OZFalk5amjl/xac91b1Gc4PudWV7nbaWiSWSpjSMpzAKckj19h7nbVGsweZ1dxG0yM9saOlLK3iSqQ4XsSO2g3FC0klPS3221sFFd6ReamLg4kXOWglUbmMkfgdx3zXeKPpPj8V6a0IZSDjmQkD8X/oo/wC7VJudTU3qi8epcqUb/iI0chDk+V8eo+E5yfh30RVpbbxnGBKNqK6m7yZcLt9IVxvFsE1uhFKf8OpiZs+BJ3U4+L1ByQR266p06z1U31iuqHmkP2pG6ew/sNBo5ZLTIKil5ZJI/LJGdlmjJ6H3z0PbRQSCuiFVSyF4JM4+8pHVW9CNM9JpK6m24yfmB6i9rBuB4+IUtddTwzfV5CWhkwrkfZ9GA9j+mdT6SVrDIaSpI/ZLvhW6ijcnb/8AdN/9iT6HauJ4VMcs2T6D++rJZauOvoWp5Y1fwk5CrDIeI7HI746fIj00cyYOYPVYZbYZ3KBVTmddmJOw9Dnv/wDOol7ssdzpQJZpFqYzz08yDBhfswH9D1BI0Fs1U1grorfVu0lunISjnY5MfXELn/7Vj1AI69bTid2Kt+5TpgfEfn6f731ddzekwjI7EB2K5Comnt9wpY4rnAAsoUkKykfGvqjAZwemMdRoHxXR1UFaFi56WeBxJDKuzRuM4YHv+O251ZL/AGZZkSuomjp66lJeKVujeqP6q2N/TYjppuaZuI7AtfTxgVkJ8CeJ92jcDODjrtuD3G/fWLDyzhuROlSwyvczayUlPLfqv660dtgA8Z/RSeqpn7JOSB2GR9nJs9peWrqzQcI2p5i7Y+t1C5CH2/U/j10XT6OqquiNZX1EYq1XMSSLlcjcBsdFPQ4379QNavwJJa6qyhbfRJb5KdvCqqQ/HTygbqT3HQhuhBB0pvuI4U8S6UhjuxzKpwn9FsJnWu4jqXuVWTnw/sLq+iyQ0CNQClSGnZMeGFwMaKQOEYGMcxBB9tFq+L9qQI0cTeKDgebZfXQgG7kdwuusEH5lBtU01tu8lFM2YqhwAxGBz/Zb/uAIP8S6sHhzZJOxHroleOFY6y2MrtmoRSY+Xb3I/MD8QPfQm0GprYTDJztUxHkcAdSOjY9/765cmcNjmX2EcGTRcpfqQp38/KcqT21DRZqmbkUNI5+yo0dorA7eaqkCL9xOv59tGaalgpY+SCNUHfA3PzPfUWlm+qaCsk8yp1lgrKdUu0DItZT4bkUZ5gM9fU9fwJ9sWm0V8dxoUqYts7MvdW7jUjVbnB4dvAqRtbqtsSgdIm9fl/TPoNFKMACahQnUtGm+YsWTPK43Hy12pBGQcg+muJRleYHDL0J/301My86RubIIwR1GhHE1tarphU07eHWU554nHXbt/v8Arru6XmioqGSskqIYQmzGVwq5HUe59MaybjL6YY3dqThuDx5On1qoXyL7qnc/PWJvAOF5M4xABLS+1XHVsobGa65TwULp5ZvGfCq3Xyj4myNwAPmRrN6n6Rb5xLWyLwtCiUmDG9fXrkb94oQdvm2T76G8RW5L7YYaG53BKusqCZaSolVVYy7nBUdjkj/U50Bfie12i2G301G8VWoCTRlsMjdwzdPx327a1agthmPEX2ativoknj7gSmhttLfVvc15rZmxUmZuaTm26LnbB/nqjTilpUYuQzDcpGwwPm/QfIcx+WvLzxLUVStH4n7s/YU8sf492/Hb5aEQK9WQWJbsAR/IaJrqKjcBF1toY8nM9lvFVHKk1CfAeJw0bJlVUjofVj8zrXfo94pgqoWuBVIixUXOAD/Cc7CdR9xu/p/PLBRwU3OKh8N1Ma7v+PZfxOfY6at1/ntN2jq7bGg5DyyJ1WVDsVdiNwR6AD208p2airZ/qgYd9PZuJ9M+nqispI1A5/EdhlUj8zMPXHp7nbUJ46yp+Imli9EOXPzboPw399Vv6O7tbGhjamA+pVrH6uxPmhk6mF//ALk/h6au1U8NOheZ1jTpknqfQep0AQyMVMcKwcZEBS28UatPRq+M5ljzkv8AxD+IfrojRzLVwc2VZgAcjow9RpmWWqqBimiMKHpJMN/wX+5HyOoBpqi1k1SSvLDz8zlgMxk99vsnuO2op2nInCMxXihaT97EeSSMkq2M4PfPqD0I9DrGfpO4RcmS+WtHiCnFdTJ1Q7+ZT15T/fuDnfImjrKbxYgPRh6H+2q7eKB1k8eFRzgFSG+F17o3sex7HB7aNrfkMO4LdUHUqZ820FK0z+FTxmRgNwoz+JP9dSaqW1UA5aup8abtT0pDMfm3T8s/PRr6VeGbjRRftCyzyR2eVj48CrhoH75xsf8A4I2Oy+ha38N1Fxaku9KZa1zmleV/3ch7oR97uN8Hp1xkrUa3UPWTSuAIBToNPVYBc2Sf7SJZbZxVxNmC0UP7OoTszIME/wCZz/rrR+D/AKKLPbStTdJDX1HUqCQufc9T+GNXyliSKMRxoqRrsqqMAfhqbEmx2GvM2WM5yxzHqhVGFGJCmtERp0/ZsSwSQ7iGFQAcfaQD7WOo6MPRgCXLVVioBjfAlUdB0Yeo9tEI17qcEbgjXFfbWqw1bREx1keXdVXPP6so7n7y9+o361UhxtPctyOo9GnMMEa78HTdlqhWRsrKFmTHOgP6g9wfXRaOAcvmG+sWyODNByMiQRDtnGloiIuX7I0tVzO4gUr3GkFwf97a9G7YHbS2BwTt3OiJaIY7ZO+w9ddKuO+c9deqO+24/LXo3OpJPFXbIGfQa7QdM7nXQ9T01y5A2A313Mk6OM9dNsQBnsOmlnAO+sX+nT6R56WU8HcLzZus68tXUKf/ACqEbgHs5Hf7IPqdtK0axtqylli1qWY8QV9Nn0hVF7uEvBPCs/7tSUuVbGduuDGp9PU9+g76FcC0NptpihkxiM+VD/zD3JPrqt2aggtVH9Vp/M7byOerH10RpshjzEliOuvS6fSLXWawfUezPFa3xNtRYHx6B0Pn7zSvpJ4iiudPRq1HSwPTR+HDHEg2X1J79NUlqKtND9eNM4p1cIXI2DHtqMtSwlWRnE3J1VjttorQ108kE78nNTshQl8Hkz1IHb0z76sqHSIFXmDFxrHLscRcN31rTcFqhSQ1kS7GGbPI3zA1ZuH+IbfX8Qz3K9WuGtMyn/ho/wBwi7AAjHQDGgHD1ga8iolatprfDDGXDTE+Y9lAAJJOhDtNR1BGSkg67Yx7ahrrsJA+qXF9tKqSMpJ96MZqWWlPKFJ98n00Oq5VnTwrpCJQuyuu0i/Jv6HI07S5lrIYouXxJWCLzPygknGSTsNWi/8AD9tRYKC31Rrq9APrciuPBEhHwR4GWAOxbO51LHWsBG5lqa7LCbEOB8fME+DwyeA5aWO31FXdjMGFUZcCKPuCg36emc56jGNViPhW4VnDldxHSLCbfRypHIzTDmLMcDC9SPX/AEOtepvosr4OHVuf1hPraGYuI5VKnAwqBiQB5g2WPQH1GqYnEFTDw3X8PMFoobkySVEscI53wNs98H2P89wFXblqTnmNN5JC3jaSJmsZkppVcDLK2x+R0RunE16usyzV9bLPJGOSPnYkKvZQD0HXb30ZvUdnh4ZpaVLbN+0Umdpa/wAbMUqH4VVceU/PB/PZm2W2jtNmF2v9rkrI7lTSrbQszJ4bq3L4rYG4znAz23G41srqV8ywczpRw22o8e8icJ8Ky8aXMWylNOs3htKXlkCKAo38x6H21Va2inpat/qpPgqSDg5/2PcamySSwhgkjIX2YKcZHvqPHUupBUZQ9j01Fdg5Ynj4l2Stl2YwYVqOJhJQUMAgp4TTQiJREnLzHOSWPUnc7++mY6uU0/MEwhbJIHU+n4Z1AqoKWoUSD93J20YsE7x08dKXaYRyF0TOVQnGSPfYb6Y6dAiFwMxfZpha+3Mt1FVXi82yBeIal5IKeMQ08UjbRx+nKO5wNvz1JaaSpdaakiIXoqDq3z/3gfrqJRR1NcSMqkcQ5mdtkjHqT/snXVTXJyNR24usTbSTkfvJvYei+356HA5MbIoRQBJsWYpvq9vCz1n25R8EXsPf3/LRO1W1aZjIzGWdt3kbr+Hppy0UK0dGkQA5jgue5Oi0CD029dA3Xk+lY0o0wUbjHKaNcDI6aG3niW3UJaCnliqapdjGrZ5D/F/bVd4q4rT6w9st0wQAYkl6F/ZT6e+qTNSnxDNE7K535h1zo7w/w0Mwe7r4ivxLxJgpr0/fzLNWVk1bO1RUymRz+Q9gOw0zsNBKa5Swjlq0JA/5i/1GisE8cyBo2DA9wdewr2bcLPnOpptDln5+8kI22/XXYfAJ66YHtqPdKjwKflT/ABJPKn9Tqmos2LgdmX8P03nW5PQ5Mcor1UUtc5iIkp18pU9GOdyPTVst1wp66PnhbzfaQ9RqgwRjlSNFycdNFLVS1H1lRS87T/Z5e2kGporIye57XTXvnHtLoemvAud9exxTRxKs0iSOB5yg2B0h7YxpXkRuBieDHQ99cVNPFURmOWNXU9jp3H6a9XHfGq7iDxKkBu5SOIeGWi5p6XBTqfUapNxaWmBDbMTgE62qQAgg9+uqpxHw/BcOaSJVR/Tsf7HRDeLNWmxveBWeGI53rM6pp+Y77HU+mqZaeXxIJSj46joR6H11FudsqaKVlMZ5Rv03Go8Up+0ddqO4BgYtuQoCpl7s91pqmkkhdhHVHHKvZh7f2/nqTgY3GdUJZsL1Oi1o4iKfuq/LJ2kG5HzHfTJbksXZaIls01tTCzTnBEn3i1UdzLoXRalFByvUA5xkemqDxDQT24GnqIVaMk4yDyn3U9tGJ7jM1Y9ajlJWbIPp7aGcZX6WuoI6d0CsDkkHqfX2153U0BGOOVnsdBqWsUK31StwXSSl/wCHqFNRTHYfeX++uzJPX3D6zCn1hYQG5m6v6ZPcj+m+oWypkjOrPYKcU9uEzKAXBlb3H2R/L89Ktg3cHiegHC5gm8VyywxIVaONQdmHmJ7gfpqBTu85xy8qA7KD1+Z17dZfHqCTvk4H9TqbbYVCjIBwf959NZHJPMuxAEOcOW6R4chRucliNgNXC30McCDkGW7sdBrNVLInIo5OUbqdsf30fimPh7DA9dF1n04ERakkMSZKVo4wVOC3pqJVNIedpG2X4cdNdAeYtnfS8I5Bcgj0zt+OiFAQRezlob4EUrNU1rruFEMe3rucfkPz0bulxoKWhZp5uSfmBAJHLjByuOpbp7ddVqW5Q2yzRUcB8Srcc0gB+En1/QY1WaySepkaSdtz3I/TWoIUZg21mOD1Jt04hnrENMwk+qgsVi58ZJGOYn8F6dcYOdAik07nAz2+Q0QoaF52Hlbft31arZY4YVDyR79QoOsLdQF5MKp0xAwJXrRw81UQZU8v3jtj5asLUdNaaKaoI8kMTSMcdlBP9NHIYkUYUEew7ar30o1AoeD6lWGHqmWnTB9Tlv8A7FSPx0ud2tbEY1AIMTDZ5Hqql5nOXlcsx9yc6L0Snw8D4mIA/PP8l1Epaal8KoMs7pIqAwIsfMJG5gCCc+UBeY533AHfROhQGVNtlXP67foP10T9ozrPEbu7EMkanAC76K/RfbxceN7TTMC0f1jxnP8ADEC/81GgVe3iVLt1GeUD5a0f6A6KM3u6XOVlWOhpFhDt0DSNk/ojfnrOwEITKs4E2ZIxg4zvvg64mRg2B2213QXO3VMoihqkZx9k7E6fMfmKk5zoJqmrwrDEHrtSwZQ5kTwtgmfYaYqouYsuAQdtEGjC5YfZG2o8mA2Dk++o7qvE6BKhfuGEqcyU6jOclP7aolYlTSVR5l/dk7EjBHz1s4Q4Zy3QaAX+ww3GN8BUkx2GzfPW9eufhT1B7NKrc+8z+21CNJy4DdznfRqyXSCCpK1jAK2ySfd6/F7e+glXa5rc83KhUIuCD13OotHInMHIHNjpp1Ra1eNh7iPV6RXyHEvNbTvTU7RtjLKrA9sHmI1JttMzVs8UnMhVNh75AGqzbLhJ5IZSzQ9AOpUe3tv01tXH1Vw1X3CgrOG54KiOSE+K0R2zkYyOoPXY6E1eqZGsVlzu94bpdKLEqKNwn7zPK6kiIlhmjjbIwyEZDA+3fWfcZ8LSU9MJ6BW8DJZlG7Rj+q60K5ws14LM5BA2xrwSw1h5SOSVGIXG2QM9Pz0u8xlWNwu05Exi3NcrK5q6fkdZB++gP+HKv99Xzhq/09VSiSndnp41CSRspeWlXPwMoOZYfYYZOqEfCSXEPByTIamlUc+MtTr8JPqvofbWe3Cgqbbc0rbdI8NSu+QMD5MP6a41WV3LCq9Rn0maNV2uKqBqqRxysniugkDZU9HVhjnQ9mGMHZgp21AlhEcLRhSDjHTQ7g7iVatgsKeDVKfEko1kC8zYwZYGIIVyOqkFWGzAjpbfCp7pTrLRsqyOSihUKhmG5ULklJANzESTjdC69O1atk9L/wB5ndpAw3JK1RQEXuI4+yPw1cwmFxjYDQWkpSt3mlIASKKIKPXygE/nqVdbzBTIUTDv6dtUNzWHiAWJtbmOzyLHWJzkYMUmP/adWThLj6r4dhoap6vxBAvIFmYlVXuBvnt0G2s7NbNVpJI5BPLyqMbDQz6nU1ly8oeULgAFvIvz7aLStA39UZGJiWtIxUcHMtH0xfSdcuNJouaBKaKDGCGJznY4HRRj5n31ldCVHFTYzuHx/wC1tS7w7MGI6DHUe+oVF/8A1TGwGOZGP/2Da4NOlFOEEZ1Xtc/qMu/AUlPHw/M87gBamQYz8vz/AA0ft9fHJVReAQULbHpj8NV/gWx1FzsdRLToUZa2ReZvhIwu2dG0sMluzOHJl5gHTop33/H30fo7ad+LOYj8US4qfKODPHDMztlm/eEHOidsB52znHLoVSzBnLqx/wAQhgfn0Oj9AiOByFQcDIB99en3L5JAnia0Jv8AV3Cn0gTtLSW4vuzWmKJcfw8p/pqn1EUi2umkKkLzMM49f/jVj4mnaSmoiJOXw6TlHfO3TUKgEtTZo2SkecMWTlzjcqcNn0BIP4aW/iRp6+YzbRnU3HnEqlTWJCML52B+FTotabr4lkBmIwk+AR9nKnHz0AutJsWii8M52A6H8fXXVEtS9prkUeZCkmDt0Ogb7vxQweoVpKPwhyO5aY53aNDFISucgA9PcaL07LJSxkEEklcEY1Q7VcpIyFkHL2K5/UaudnRqqmVIniyJlyzsFUA7bk4wNx6aQ2acpkGeipvFgyO49LSol8oZ3xys6Fh6jmOf0GqjxFbJKW8VACeZXIYY6421eblNR1M8Yidz4TCLnIxnOxJ+Rzg4Ge4BzqJxfBHPeZ512EzeKB6c3m/rrOl9uZo6gyjW+WlqaGWiWBlq2LEzs3blGFC9BuM569OncUqyJIJJAOdDklup/HRiWianvXiLkENkgemdRZYwwmhcAOhI/pphXZlOIDbTg8TjiGankqmkhjKmaNZfmSN/1zoPcKOOvs2ekkEuM9fKw/uP10Yq6ZDRUjs26lomYdu4H6n8teUdOrR1NOq4d4jj0JHmH8v11HqXOR7y9OqZcAyo2a4Vtjrgo8RkZslF2OfUfxY/A9D7aLBVw323iSmZGmPmwNufHXA6g+o9fXYtTaqnDsrHAaNg4/Pp8ttD0qazh2+ziPJhEpPJzYBXJwQexwdj+ByNtAshHIjwMly7TL1Stzx1cOCMoGX5q39s6gqOUEyHzDRux1tBe+SqjZfHZWV8jAfIx0zswzuP/kjaaGD60frzyJF5slU5jnBwMEjvjO+tQwsUYi+yo1cHqMVZLwF4wPLvvpqrVJrdC/w+E7RkY7HzD+upi4MBRRk40PolL09XCy+ZUDg+6H+xbWlY4MGVsNiDarmkoWVQR4ZyMbnR76L6jmrzSv0kQoR3I6H9GH5aErjxWiAzzjlz8+mveCKgUHFVO87ckYmUOxGyjPKc/g2fw1FMOUZUiWNvESdo9l5GK7ex0+OWI+JnzHt3Opl2o6hL/U0sMJEvPzbb7HuO2PfRi0WCmgQT3GUO3Xkzt+J766usFTlBBjpvMGTBVHHLWUVRCInOCJYSd8MOoHpkfy0dtXCNPNTx1VVKH8RQwVD/ADOinhzTU3h0kCwRphkLbbg5GF/vqbwvcKRYZaZ48Sw4ZFx9g7j8twfcazuuY8ia117DiV672Cjko5qGG0qyOvLJzrygj15juT3BGgfDdzruEblHa7wWqbdOSIKoDJU/dP8AEPT7XUb9dJqZnqpfhLHGFAHQaCX+yxXCkkpauLnicYZP6g9j76Es5h9TY4MkR0M1RfqWe2r4zyjAEe4eN8kEH/N09jo5GpGAwPvnVG4A4iquBeK6agvINRQrJmkqXGdm6g/xeo7kEjfIOqcQy01ddJa+iC/VqgLKvL03UE4/HOszZluZw17cmQKcBN9P194ehggqfGCGFigJ7q+zD+R/DUOSojhGHbc9AOp1Vb9eqNqgU1S0h5XwwjHw4z69/bWtdRsPU4Tgcw7T3yGrv89MZvqiTJmRnbAMibfquP8A26PUUFsqrNPI8saZJQyl8AHqCP01l/Etda6WN5lqOZ85hmUHDsvTO3Xlxt89QDerlV0yw08v1WIglTGfOQe2fT5Y6nUTTtZwncl161gM3UL8SXaKyVCXmHliuUeYZU3EdfT9DE4G/OPsn0xvsMA+JamK6tDXWqsnmtFUAxibYwzfaRx6g9D3B2xggM09KtRTTWqokGZWDws5zyyjoSffofnqux1EtBVSmKndon/d1dMxxz47+zjGx0SNH5TbhyfiY/iBamzr7woTTQbYDtjYdv8AX9NP26tdZx4kfNCwKvGPtKRgj2OP1A1HVaZaWKrhmE1PMMo42J9Q3ow7j/Q64M7E8sa8qH8P/nTtCtiDHMUnNTkHiSJ4IqKoZJ2DhD1A+ND0b8Rg6hyPLaq92ghaSnkA8WNST4g7MM/aHb16aIRRNUUGZCfFpQXRmHxREksP+0nm+Rb002ZoGgKLH4jJtvvtrJ1yMGEI57WPRRRyRJUpMjwyDKP15h8tSLdcfqVSklMvMVO/N3HcH2I0CSWSinfxVL0kp5pFUbofvgfLqO+irLBCFwfHLqGRYz5SD0OdV83aNtvH+84asndXzLwqUl0t5pZIllpaiPMYY9RncezA9/bOnbDcaunqRY7g/jVIH/B1DnHjp6N/6i9/vDB9dAuFquaGqa218f1ZZMSQFgR4b9j8m6H8NWO40UNxpMTB0ZG3KHDxsPtKfvA7j5Y6E60Ql0yOCJqjYPMNx0uSGqG8Q9QD8I+Q0LvFJPRVDXe2DMwTknhBwtREN+U9gyndT2OQdidP2K4zSySWy5FFuUChiyjCVMfaVPn3HY+xGirKCCCAe2+qgCwTXO3mGOFa+lvVpiqYW58rg9iD03HYjGCOoI0q+hq6K5LebYgatjXw6iDmwtZCDnkPbmG5RuxODsx1SrTNNwpepq5Q89rmI+swquWjGNpVHfGMEdwB3AB0+jmpq2jhq6SaOanmQPHIhyrKe40j1Fe1yDCazxnMtfDMNDdLfDcqeUvBKuQuMEEbEMOzA5BHYjVhjRY15UUKo7DVIsEFytFTLcaaB2t8x5quEdSf+qg9QAAR9oe43u0Esc0KSxOHR1DKw6EHvqleBxGNWNuZ3qv3GP8AZF5W6xL/AMPN5KkDt6N/X8/XVgyB101UxRVEMlPKMq64I/rrSXIzHVIZQwIIIyCNLA0FsE8lLPJZ6pvPDvAx+2n+n++mjRIAyTqSA5nhHpqNcoKaropaeox4bDc+nvqBfuIKC2UUlTNUQpEgPNLK4SNf+7ufYAnWIcb/AEvzVhek4fp/rfKcGpqE5YV90j35vm5PyGsfNydqDJnHZUGWOJqtv4jisdDUUt1qIVhpN46l3whjzjc9dsjHrn2OqFxZ9MyOHh4dpzVnOPrM4xGP8qdT+OqJw3xJcpK6eDiitluNHclMcvi7mPIIyoHQYJyB26Y0IraEWC6z26sfmZPPCy7maM/C2Tso7E77g7a1OlL4Lnj4gDa4hT5f947dbleL5XGpudbNUPIcBTv+AUaiFaaiLNI+HH/LTBb8T0X9T7ajVlybw38DyRkYYITv/mbq3y2HtoSRPU+XdRnA7fkNE16cAYURbZqCxyxzCFzv9TIqiGQxrGByBWxjHTJ6sf09tS+IIf8Axfw//wCIaNOS8UChbjAo/wAePtKB6/6j00LWgipyTWSeE/ZMc0h/DIC/iR8jorw3O9Nd4mtKB6oHAQMCkikeZZHONsdlA7emta9oG0yodhyeoGtFmacAsCSQDyg5bHqeyj5nPto3Bb2mp5Ke1I81QFxzQHCL7PKRv6YTGjFZYaVLmsymU26pc+BTuQI4JerxsB1PcZyMfhq00MlDTtFAceK2AkMa5YdtgOg99h7647EcGUZSG9AmLz0dQZXhqIyhQkMmOVR+HfTot6RorzFUQ/AX7j+FRufwGty+mXhNILOnEFJBQwVEaqksMCmR3HZ8nYH12Pz1hFUKmaR2LMGb4sMWY/NjrTTah6m3LJfp/wDTZzCXD3EtPYrj4LpLJQT4WrjJ8+M7OoHwsp3G51uPB9ZBUyLHU1H1udk8SmqmOfGiPTHpjOCB/fXz1TW0SEqUGVGWAGFHzP8AfVn4G4no7bWR2KpuI5DJz00qAkUsn+b7rdDtjTLVLS9Ys3eozmhstDFNvpn0QYhyk4AGhU1ehZo6OP623wtjaMexY7fkCfbUCw1Ml4EkVykHjwHlkpk8sfseuWBHqSPbVkjp4wgCIqgDYDbGlZYg4jYAHqVSmets1UJJljNNI2FCA8qg/YOT+R/2TlRDDVU4mgPPG4/L21KlpYpopIJ4w8TjlZT0I0GpDLZa76nUEvSy/A57j0/zD9da12kHImZXjBgO924xvKxhE0Ui8s0R/wCYu/4cwzse+46E6yHi3h9rDULVUXnt0x5onUEGM56H03/t1xn6KraVJIyQeZHGQR/PVOvtrhEU8FREJqKYHx4+XOP41Hr6juPcDTHT6gr6l694FqdMLV2nv2gz6OOLVvlOtBXSAXKJchif/MKO/wDmA6+o39dXiNgBr5+v9orOGbtG8Lt4PMJKWojbHTcb+o2IPf8APWs/R9xXBxBRiCpKJc41/eINhIPvqP5jt8tB+I6IBfPp+k/tKaLVnd5Nv1D95b4eu2ptPlWEisVZdwR1B1CiHUamU5wcY20kOY3XueXW2vUj9qWvEVbF5pYlGzjuQPQ9x+I9C9aK+KtpSxXknQ4kjJ3U/wBvQ6lUzvFIskbFWU5BGo15tpmJvFpAjqoxmeEDZh3OPT+XX11YN5gwe5p1yJPAm5QcKAenTS1EtVXBW0viAlHU8siMQCp0tY8iWBBgrZRtr1ATuevYaSKc8zDfXQGSSen89Eg5kiX17a7VPNr2MZ3x06DXRIwdvnrsk8OFGuCBk/rr0Anf/Y1RPpg+kCj4Jso8MLUXaqBWipfvHpzt/CP1O3qRZVLHAnGYKMmCfpw+kX/wvQJZ7K6S8QVwxCg3NOvTxW9/ug/PoN8LtdE1CjvIxnrZyXqJ2JJJPXJPv+Z17aKSurrvNcLjVGpu1dIWmqJD8Oew/wBOnQat9LYSInQlOSP4st5m/DXodNSuiALfUZ5TxC99cSlf0j95X4gUJYHJ7576McN08VdcoKKpqFpo5nCvOw2iUncn5aEV7QRzOICeQHC79ffT1qvFXRwywIyiKZlMkfKMty5wCeuO+OmdNzgrlezPNoNrevkCW/jKxWakuTwWGtlq6VAAs7jHiEAcxI9M9On9TW8lRgnHrj01zNdC8QiiJXm+MHf9fTVsprfwyODQ8tTUy8QSTHmhI5YokBPXI3Yj/fXWIJpA3nJm5UXEmvgTnh28wUlOoT/zS7Kz9MdsfLQi/wBaKmvkzlpZWy46nOnouGrtLY6m9QKPqMDrG8zMB5zjCgZy3XtoGVkp5ieY87Dd/X5ayStGYsh5mrXuEVbBxJksMYkc03iSRrgBm3/HbpvnUuzyFZ0X614ALE8xJxn31Is9RAKCaGpm3LCRlJwGY9B+A/nqNdZBOeeKJYUVQuwwNv8AfXWfmbQVcQhaySHQzbOE+Go75wXO1wvlUA8Hgc0FQiwQohJVWU/EM7k+/wA9ZFfbQ8l1kT65FVyIiCR0OxIUZVT3A6c3fQekqq6FSYWdEHUgnl/37al0VxMFzWulDTHm52UnHMf94/IaDp0zhmfdxGOo1NbhUC8+8LW/hC7fW/qsKLMJB5tsrgDJyDtgai8T2etrqKkSKvlnWhiMdNBKfIi5JwvpknvrS7nd+EpOCqeelrkW4OAZFDsXwc84kHQYHoT6b9dZ5drzSIn/AA7iUscBYzuf9NDefZcwO3qbrSumXAbOZmzUIp7iIrsJqaLJ8QqnM2N/hGRnJx3/AJa5u9dJcp4JZ46dFggSnjWGIICqbAnHU9yTudXGSnku8UDCeKohd28eN4ziIA7AHbLHc7dBjJycARdOFuQs1rnFQq5/dOQHH+U9G/T8dGaexbHw3tOvU617llSZHaTwwCSTgDV34asqU9v+t1sv1emz55eXLOfuoO5/Qd9R7LaYLZH9fvSEzvvBRDZ2H3n+6v6n213X3KSvqMyyKCm0ahcIq/dX0GmrN5npToQelFqG5+zJlxuZqQKani+r0cZ8kIbJJ+8x7t/san8LUZqa7xZAQkI5j8+2gcKtzHI3J6EavNtMdqtiRcqSVbr4hj5sHJ6Z0Nf6U2IOTDtMRuL2HgQm8kFOni1UqRIB1Y4zqq3viGSsZoaZTHSdMHZpPn6D2/PQm71lbV1jPWFg4OyHYKPQDUMtvjodd0ugVPU/JlNV4kXO1OBJFRBTVi8sqBvTPUfI6HTUVXRqTD+/iHUE4YalL6k6fjnKgh/Nj330xXKdQFglnJ4MCRvHPzKNj3UjcaZaCWBi1O5jPqOh/DR2poaWrXnGz/eXYj56gy0tVA4VlM8R2Dr8Wia7x7QG3THGTzH7XVyTI6zRchQZZ/sn5aYhV66pafPl6Jnoq6nNSGSnFOp5I2P7wjqfb8dH7XZUhiSatBji6pAPif3PoNYXawDljNdLoNvpQcSDZLPJUkmP93CvxzMNvkPU+2rNRxwUkfg0icqH4nPxP8zrwSlkChVSNR5UUYA05TgEZ0luvazuegooWsYElU6ZO3TTzUXiDMRCsPXodO00WwGNTkVY42kdlSNcczsdh/r7ddAF8HiF7QRK+6sjFXUqw7HXOuuIL3TkeDEgwDkZHnb5/dHt+edD6aviqAFJ5W7jR6ae7y/MK8RY2t063eTvGY/UPhCO7ajY2OvXk55D6dtejfSC9975jNRhZAuFBBWxFZky3ZsbjVD4i4dmo2aWNSY+uQNjrSgN9cTxo8bJIoZTsQemttNqWqP2g2o062jBmLOXUkHYjtplmPbWgcRcLxy801GMfwjqNUaqpTSzlKrmVB1KjfHt76crraiuSYo/BWBtoEjwRTT+J4YyEUuxJ2VR3PpqqXKpapqD6A4A1YeIrwxojSU6Cmp/sxg5LH1Y/aP+xjVUTIyT+GlF+qNv5R5otGKufeSqGFqqshpgdmbc+gHX9M6tF+lWmtoRDhpCMD0A2H9fyGh/BtJztLUsAMnw0J7ep/l+umOKqwT1zhDiNNgP0H6fz0P0nPvGQPqgmLledj1VemjVsXA5m8rE4B9tC6GE4UAZLHfVmp6R1RQU8uNZkTGx8dyRQxc/MVBHL0A2/Ef20Yt9fyhYpX8mcB8fz9NDYI/DUAkke3bUomJyAXRJG7no3zH9dXrfbALEFnEskYjALMTyk9R1/DTNRK0oCqSqL30ChrZaRzG6lkA3QndR6j1Gj9MkNexkoo3WBiOVXk5mG2+SAO+e2ty2ecwB6SkZ8AZwi5OOupFvtMs8nQsOpJHTR+22ZBEZpiFAOFXPU6NW56ikjmjpX8MSxmJyo3ZD1Gfw1k+oHSy1dJ7MH2i3U1Ly86FxuDynDdPXfvolT0jyluUM2Bk4GcDUiioTLIqsyoCcFmzgflqRP4UHItNN4uUVmIXHI/dffHroJiTyYSOBgRVForKEsZ6Z0CIkjEYPlceU7HvrKPpxulKa2mtiQO2KYyAmXeKRnGG2Hm8qMMH7+e2tTy0mA5JOMDJ6DXz7x9VtdeMblNEeeOOTwl9AqDl/XGfx1rpxubPxLoozmAqcFnXA75GjVPiKGZx9k4H4bf0P56HwxpHUnw5VmRAPOFIzgZOx98DU2p/d29YvtNtokdxiDhYOTdwW3weY60b6MoJIuGZZOcj61Ul2APXlHKD/APbazhvLFI+fb+ut44L4cMHDlJHMrIUiTb3I5j+pOnHhiJ5m5+hPNePtYaAlfbH9pHhDKSQCD6+mrVYr4OUU9wfB6JJ1/PUCuoQjJyZU8uTtoc8Phuec527ab6vT061cMJ43S6rU+HWbl6/aaCRmMEDIc7Y7jTTRgg8vXv7aqtNfmtERWpDSUsSjmA+JckdPz6atNHV01bSR1NHMk0TjIZTrwuu0D6W3Y/U+g+H69NbV5i8Rp4+SEnPU6ivFzFiGPKT00RmwAoY5I3zqO6E9T5dCrjdzDoFvNsp62jaORQGJ8rDqNZze7HNQTM3KSQdsdDrWqlMooxjudMSW+mmpjHMgcEd+x9tE1alks4mFlKuvMyKllljUvKpXAIAzjRHh+81VurleAhlY/vI2+Fxn9D76K8W2B4I2kjBaPs/pqqUBeOpEci9SADpsrJf3Fb1PQcrNBnrYa2sE8ORkDmVuq9c6bssYmv1PERlQSTn8T/TQelWfIqY84Q7sOmrJw3TSrxQqyIeYeUehPJv/AD0r1ZVOuo5oWxx6lOYYqGjjnmix5QxVdVjiqwx18dRUxgR1KQnB7PsQAfzG+rHcwFqanxDgCU5PpvvorwTaZuLLzPTU6IKUOpkKncqN8D541gQ40z6kdLMTcqahKT20wWu4XMNPzTOaOqgI5HJxykdPmPlqVw7xNIK1qG5SQwXEgReM6/uKxQcqkoGCD3DjDKdwQdbz9PlPwxU2ymtVuhSOupyUarjGJFI2KD+Hv+WO+vmG/wBiloZjDMmeY5WQdH9x76D0Fh1de4jGY2dxUduZscUlNd4pY53NJWRDzPMw5oyTt4pwAVJ6TjCknDhD5jXLvbKmhmkirUcSq2DzAjf3zvqp8OcTy26ohortPKEgOKaujGZaYnbBznnTGxU52yMEba1C3VtLc6WK218MTM6Zp2gBZWXGxg6llHeDd13MZYfu9FKxobB6mN+nXUDK9yrU6g0zlhgY21qH0V8AxcRWxK2SuADMQkS+oYjLH+n66odztUtEAyMslNIgaKVGDK65+IEdR7/PODo/9G99ltFTCsdU9PzSfGPh+LvpmaG1Y/pHkDMRWaldEw84dnEx7iCKVHqIzheRyufx1FpMC/UTqPiiO/8A2sNTb2slQah3YZLZLE/rqPbIyblQSjdVBUn02ONXc/0iDD9ORvyOpvH0RR0x4Ck5seJ9dOwHbw4/9dT7/RLNRnGzBlw2PfTv/wB7xbKO48P1MdXUrTolQDuwBb92nrq28Z0Vqoqd0o5PrBUAnzL6+xOsK7a/Sp7g11dm9n9pglfTS01S2PJIJDn0YZ76L22swNlIcAAqexz11NrIo6rnjmABEnlI30PlopIJWz1HwsP99NOdNqWWllMV26OuxxYBHayoDNC0hJwMEe2rRwA8X7PiZkR1D5Cn4T1wDqhTyOsqI5824G/XtozwpcamkoViSSNiGB8vvvoW9dwOJSsbTzJNztyVEE9xpoo40Z5XFOVysaZOMZ7jpoFTQvHT1gZfD5omBBAG49tGaqoq5aGSm8VvDWIqqjbGg9khadJ2mcuxLAk79RnQtS7Tky/mZ4Eq1Q2ZDtjB6j9NGOHauoEdTTkkoy5wTtsdeSW/wwY5IzsNjjpp20U0y1qoRnmyoI7gjW25W4MoAyNkQvTy+LHlJPMMd+ujcM61VODIrNuVJJ5iMe53xqlUv1iCqFOis7M3KoUZJPTGNWaxTwrA8lQJG8Jg4RDy+YZG59M4zjB9xpa9OCSIzpvFnB7nFzoOWrjmGGRsANoRxFanFVK6KQzJkgjfONW2nrqGejjiZeWdXViWI5JB12+63Ueh/hOx74hjWeuWeMq6tDGzEHO5UZz75zn31lW+ARNmWZvSsJbfPC4yyEMB8tv5HU+wW56quj5JV5lYNhj036amfspXq50TClgRt77aDQSVFJUQuSyPG2CQSP5a3d2avK9wfywG5hXiXgi52+J5GhBRWIR0OQR2/TVR4ltpmSnknGHaIK23Qrlc++wB/HW00f0ri0WZqK4WKG5s8WELuAoYeU5OM42z+Oswutc95SaomiigKzcwjQYVFbsPbIGhNI2psZxauPgww2U07djZlHoaiqs1WJIHJGfMvZgOm/XI7Ht79DoVuraXiOkV0dUq1GCDgc5A6N2DfoRv0ziqVdIkkR5hzemO3vqFI9Va3o62nwC0ZSRQSFcqe+O+4OeoO+tdhPI7hiuto2t7y5iMxM8bKQw2wRjB0NiEkd9VpWxFzYIHdWGD/PRmy3Oiv9Mp5vDq1wuWwOY/db0Poeh7d1XiqoJWlZjTuWQ8rKBvrq6gKMmANpmRyPaAnhFPVNE/mkjcqR8jj+mlU2itkrRUheSJhzEnbYjfA699WOngUXQySQoZJEDjmGcMDyt+ujdwRZqNJCuOXKMD1Gg9TrGrfaIdp6xjMmUNUKxrfUFlWSppwOcjPhvgcw915s7eu/rmwUlEIZeaozJMOrNuPw7Y1R7HIyU3hMTzUlRkf5WOf5g6v0cjMiLMTy/8twNgP7e2q6g5cOJhWxRmRvmOq/mOAR2ydDJIDT3dKheh2OB9k/2b/wC20WRGJwwwR1/vrqeFV8GZ94o2xJt9htm/v+GilbIxLP1kQvZZ6aIFfBDMVKn3yCMj9Dr2WnWUE483tqJxckdlbxaImaKVVeFiemcgg/Jgw/LQGDiKuPM0j8oGxPLsfT+v5aiVNYMiUPo5h/iaxWW78IVn1wMlTCqgAbB1LDqeo5SAwI6b+uqZwnf5+GJRw9faiSSgqkLW+tK/A2TlHHYg5DAf5hnJGrHFeFraJ4ndAzEoyhfiDDpjv0Py1nvE1zggs9Rbqum+vRzsxhdCOZXB3CtkhSD5sjPxdtcOnb45E3S5ffqaPcKy12bNRcJ1llABxzYTcZHm77b4XPUazviW8teK2aqoKVYml+OQrjPuF7HHck567aC8MXSK7pT2S/SLDUxjloqxz5V3+Bv4c7+xORtkAxBbq9Lm9phop2rA3L4arlj8sdsbjGfno3S0rk+YcH4gmpd0AKDIPvA1FTvNT1Fvncu0mJYixyfEXtj3GR+WurJVM9IYImIMXwk9eU6I36x3iztSXGupZqT6xiWBnQqHHZhn8Pz0HqZI6G+LPACsVUPEUdlDZ5gPkwOjzsBDr1MU3OhRu4UePxOWSVuUjuT0PsNd3qBKmlF6iUOzMIavH2ZANmx/EP1B1HeKSSRixyO/pojYJqVKl7fUN/w1angyDGyn7LfMHWzrxkQavI4lXpZZ7fUyO0RlpJmzPCvUH76+jD9f5mJWjjWOSmAlikXmilHRh/T3G+m7jS1cE9RRSqqSQtyP2B9DqFRSNaiROrvb5GzIveJj9tf6jWRPlDzF+n3EI2+d6T9XtCdA9QlUlQDzMpzy9iO4PsRt+OnJYYaOrVIg8iSDmhVRnyEnYn1BBU/LR3h/hC6XeBJ2qoIqCUZR4jnnGeoxufxxq9Wbh222EQMV8WEZR5ZFyYi2POPQZAz+Proa3Wg8JxNqaCPqlEoOFr1dYgYY46SBv+Yep/E7/pola7M/BLw1FXyXC1McTv4fmo2J+NfVPX069DtpNLD9XrJaZx5Xyy+zD4gP0P4nXdTSJJGyOiujDBDDII+Wl5sZjkwsKFGJTuObYKiihutOVfwxgupyGQ/CR7A/z1Fslc1RD++b94uEl9+yv/Q/hqfEqcLTi2VrF+HK1zHE75P1J2/5bHvG32T9k7ema/LBJabw8OOfwmKN/Gv+o0z0NpZSvuIDqE8tt3sZY6y3/X6VRHKaeuo28SlqAMlO247rtgjuMd9xMstc1fTSeNF9Xq6dhHUw5z4bYyCD3Vhup/qDqNb5mUo6tzsoBU/fQ/7x89S7jSP40d0t/IaqJcBXOEnjO5jcjoD1B+y247gktwdyy6EEYMlGAvIknKP3bAtnpy99Wb6P0pLBUVMZXxbekvPLG+/1XmO0qj7hOzDts3dtV+hqIaqmSqpubw2JVlcAPG4PmRx2Yd/wIyCCbfwQYp6wqEj+sCPCE/bUZBQ+oI2/AHQmsXem4TfTnbYAZpKcjqCpBUjIwdiNByv7DqWkXP7MmbLjtTOT8X+Qnr6HfoTiJQTfsCpionJNpqW5aSVv/q7k/wCC38J+ye3w+mrHIiSxMkgDKwwQRsRpUDu/OOep7gOu+49RrwjI67jodVs3an4eqP2fVTg0TZ+qzufLGRkmJ26DAB5fbbqBmicYfTBbog1NYx9fqAdpRlYUP83/AJazOoGdqjJkOFG5jgS/8VvGIFrYp0hq6RwQxIAP8OT1znp89Z99IH0ryWyU22itrvXeGrs0+0SZ7gA5ffP5azC/329cTVQqLpVu/aNF8qr6AAam3iNr9YFqXDNd7OuZkTBknp/l94Y7+nTfWw0z2L/U4+wgLa0ZIrgO81t34irVqrxWyVDE+QN8C+yoNh+GuPBpKMMrN5x1A3cfPsv47+2okFfNVxqttj5I3GOcE7/N8b/JcDRe28OPKVaqk5+4QDYfIf30TWi1rhRiKrbGc5Y5MB1NxblaKmjCI+QcE+b5t1b5bD20bgik4q4ZFpqVAvVsBlt8pOPGjx5oj+HT8D23KV1opmp/CiizJGc5QAlPmSQq/idDKQGOSOW2c8tTEwKtFgJGw6c0hG/yUDPfOtksQDBlFLA59oP4ftZq41k5HkfGWUjLL6hs7L+O/sdSLtQ11JRNV0lNJ9XUlGnhVioPoZcDf2XHvq00zx23iKi4nVAtNLMFq6YkmKCqOPMR91x0PY475I0ni6/WR+GZqmlenlW4JyTUOMuHwcOqjofU9Dtv68ewrwepomnDA7TPl2QT1GeUcq53JGB+XfVj4alSihU1zMsJ3TIwwbsUHff/AOdRb3MlDWOsEKJJ3ZyHdfwxyr+p99V+aeeZy8btI7HzMWO//d1Ou2APyBBlwOGOZqZu1LUO9NXtGY5kVZ4YAXkAG4qCVyqFTjb075A1FoaavprnLapql1BwyilBU1Ee2JZJiScHpt/LGqZw89VSyeJCOZVILqwAjO/2s7atlqv9Pe6mWzwVFNFdIFaS3vGCY/4oTncjuB+XQY4CGGD3N1RrOPaWmt4wEVkPDMhSWig2ZY48KuOxZjvv3OsouF2ttPUvHSRvWTcx5IUPlUdssOv6aL2ng3i3iioaa7SijpuchgDgEgkHp1/AfjrSOF+BbBYkUxU4qZxv4kqg7+oHT88nS+3WBMqo5jCvS+7nMy6zcG8UcThXqSKCgJzgeUf3P4fnrTeEfo94fskauKdKucYzJKuRn2X++dW5FBHyGnYYwvTQ1epYt6oQVAGJWrhRT2usiqqHYKeWHfYjvC3sfsn8PTNxsFyhuNElREdjsVPVSOoPvpmalinheGVA8brhlPfVbU1PDt2aRuaSB95cD/ETp4gH3h0YfI99nNNgsGD3MCNhl6dBjI1DraSOrpWppwSh3BHVT2I99SaKeKeFJEcOjAFWB2IOnXQHcHUBwZoACJXLZNLSSvba3qPhbGxHZh7HuO2nK+lDAqfmDohcqNKuHl5gk6bxSeh9/UHuNQ7fMZA1NOvLKh5TnsfT5eh1vXbt/KYvXmUbiKz00tLLRVsYNHIeuceA3XIPZT+h36ZBymvpbjwrfkUSPHNE3NTzjbmA/r6j39Dr6GudGHRlZRnBG4/TVG4jsMNfRG3VQIUnFNN9qJuy5/l/7T1BDWi7y++VPcWavTeaOOCOjDXAfFVPxDReflirIwPGiB/+yHsf9+9uRvu6+baVrpwzfweYwVUDZVhnlkXP6g46f21vPBd3j4jtsNRRq0lQRiWCMczI3ofb3O2lXiOi8r+pXyphGg1Rs9D/AFCWOnfbB1KpZnhkSSNsPnbAyT7Y76m2zh6qcBquQQKfsJ5n/PoP11YqKgpaQfuIgG7ud2P4nSkKY4SsnuVW48Ii4yirp0FGzj95GxYb+o5T09jpaumlrcORNPKWZcRk46f012iZ3PQdtexqOh6d9dj26apMZyAFB1wxydhrt/h20C4y4itvC9iqbvdJxFTwrvg+Z2PRFHdidgNd74kkP6Q+L7dwdw9Ncq5udzlKeAHDTyY2Ue3cnsP1+VLlc7nfeIp+IL6XkrJz5QBhYU+yijsAP9kk6J37iC58Y8QG+XteWEN/wdEGykMedh8/U9zvq8cK8RUVPxbDfYLVb7fGieGaSnh8QKuMEgSE+Y+vQeh6FrQjaRfNZcmLL7F1Z8pWwPeUGKcLsDg56jUqa51LBUaeRsLyqueo0zxfCr8QVlRQzSTRSzFw7xiN2yck8o2AyTsPy0OqFrqEQy1tLJEkyh0dgQGH8OntWsR0DWjmeau8PdHIqPE0T6OuD1v9WiVFbS0xmViJppMLGB1/E6B361LQ3B4IqiCrHMwWWAkowUkZUkDIJG2gdLcGkgdEmYRtsVViM6tvBFrqbrFV1RemSjpggkMswRyScKiA7k/oNcdWqZrmbK/EyHl3qtCphvmB4aespOWvQtF4bBlk9GHQj8dOxXqR2Pjh3k3/AHwfzEnc5J66v30m8MPT2O2vSXuirFnj8R6anBLxgep7qNh23zql3HhG627hqmvksSChqXKRuXALMOuFznHXfH9M102tS9cv7zmq8Ps07kICcdzyovrBHSGWeKn8RmSneQuB2Bztk4741K4OpKG9XOYXO6RWyliiaR5HUuWI6Iq92J/rqqr51JwS3fHXTkFyeJFSTlMcQIUKoBAySckdTv31vbTj/wBuC0sc5s5EM1aCI5ypQnZebf8A+NS6W4Ub0jR1EMmVTEfhsAC3qf11VnrnmczSZH3F9B76l0tT4i4XlDdc+g1h5YsPrEJFuz01w99aVaUwruS2cA/7+Wrm1v4Xtv0dColqkquIqyVTGI+YeCmN0IOxxnqO+3bWcpIIwGzhz0Ouqq9zKFiCrI7NgELl2OCMDWOoHQU4AhumYckjPE6vbCECMy48vmwempXD9uucddBc5jJQJCVliDAo56FW36L3986n2Kzmlr4rzf6eOZOcOlIc8igdFwNztjbO3rnR/iW9VfE9ze4TJFDDFEqIgOEiRQFBYncn3PrpbZqGs9FZz8mM6NGqnfZ+gguWpkqSYKdGJkbLEDBck56DYD21DuN1prOpjgMdVXD4mO8cB9B2Zv0HvqPcq2YWqWS3ExUat4ctWRytK33EHYf0G+qzSqaiTnP+Enwj1Omuj0gK8zmo1BXqSzJNUPJNUM7ySHLMxyx9zrwQga7i3Y4G3TfUqnhWR8YGNNFUDgRcT/qYwjwxbayq5pljLRRHIYjbm6ga4udNVJWPNzuJc5JJyTqz8K8RwUFKLbUQKKbJPMo6E9zo7WW2huVOZ6RkkUj7J30vuuu0tubFwPYwvTjT66jFT5PuJn0FdHOngV8XPy7A5ww/yn+h0xU211UzU7+NEPQYZfmNGL1YZomOV29tBopp6OUc5fAPxdx/ppjTdXfyDgxVfVfpT1kfv+khnfrpdepzovUR0NavMSIZj/zFHlPzGoE9FPAwVxlT0dfhb3GtXXb9UlNq3DKGNRkg5UkfLUqBJZnWILzSMQAB317DSSrSyVKqfDjIDSEbAnoB6nQyqqZHqgkTsgj3ZgeremsOHPphgPlgBpdaSlpbaA7slTWAbDOUi/udemV5JC8jFmbqTqq0VfKvlkc59T30Xp6piBk6BsoYcscxnTYjD0wzBuSDolRU4Yg520NtMck8gCgkHqBqPxTxYLQq0tsiSpqMeefYxx9dl+8ffoPfsIKmtbas3N9dS7nMs9fWUttjzUPlyvMkSnDMPU/dHufwzqqXniGesbCMOUAhAPhQew/qdzqjXW6VNwZzNJIC5yzFiWY+515R3OWHAqAXT769R89OtD4XXWd1vJnnfFPFrrVKafj+YfLFssSSfXXDSlBsSD6jTEVVDOnNC4Ze+O3z14zc7+3bTyzG3aJ43a+7LdwrQ1+FCynI7N6aKxOpXIII1VFJB21NoquSIgZyvca8xr/BVs9dPB+J6bw3x96cV38r8+8sHNrlu+TtqPT1UUqllbcdQeulJLzDfYa8jqCdO21xzPaUOl670ORPJpBuB10Du9qp6+JgyKH9e2ivLzH2Gq/x5cxauHJ5EbllmzFH8z1P5Z/TQKb7X7hQCgTGuIXT9oSpEeaNGIU+u/XUBELEAAlnOAB3OupssCxO50S4XpRNchKwysA5/wAeg/v+GmhXoSyDAzLDEi2yxkYAKpybdyd2P8/z1TKhjNUAE7s2W1ZuMaoRpHRg9Blsfmf1wPw1WaRfEkZ8b521xyM4EsDgZh7hyBZKtS/wqRq+ta4hAZY350K55MZOqvw9TGKHmPxEZ6asdtNVEk0/NGIYEWSRXkCswLBQEB+I5OcDsCdV28ZgNj5OIPvMlKH5rbHJGnKoZJJOcggAE5wNicnGNum/XQYFgQVJLHfHrq/S2mlvUIloOWGUZ5m+y/zHY/L8dDG4fNJOVmiKyjqD/PWZdQOZEBUQXbaWaqCiYEqu4B2YfI6tVpi+qESREBthuMKfZh2P6agww+GcYwfUaI0rHn3OGxjPY+x0K1pltoPcs1FURzjDeSQDdD/TRyKjkjo1rjDiAyeGDkbt6Y699VGAgkAZDLuADuPdT3Hto1RVbSFI5pNuiuTt+PpqCzImT145EJtJI8aoJG5F6KT0zrnkHLnv7a7VSrldm36jpryeopqOPxKmTkj774J9hrqqznAGTMmZa13McCQ+IqpbXYKy4FlDU8DyKM/ax5f1xr5pZnLtkkljljnrrX/pXvcc1kWhSZY4qmZELH7oOSTjfAIXYfrrJahFR5Y0mWXB5UdAcPvjO+DjvuNMloNC4fuTSXLqBlOo/RKWiU4+Igfrn+Q09dpMOsa78o11b1/eJ6DJ/oP0U/nqHXyNLUsgB+LBOuAgcxm6kjAk7hS3G8cVWe0BS31qriRx/CW83/2IJ19X3ClhjLJGixKTnlUba+afodWoPHiV1KqNNQwySrz/AA5I8Mfj5862apu19ZmeV0IAyeVRjTTRaWy71g8TzXjHiFNDeWQScQhcsFyBggHQaZE8QAdWIGT6Z1Bkq6yVvPK+uVd8lixzr0VGnKDkzw+r1q2ngQXxjMfqDHOPFmA/Dc/0GhfC98rbRXhqR8xMQJIm+F/7H313xc+Xp4SwwFZsfPb+mhltjZ5eYDAGcfPXn/ENll7A844nrPBlavSKR78zZrNe6K8xM9OSJFOHjbqp/r89ThCc5f8ALWf8Bxsni1K5Vg+Afl/8nWg0c7SxgzeU40lu8NdKxavIjfT+JV2WGpuCI3UKrkKBuNdrBgDm6jTpjBlOe2nyo5cgZ0rDANGYgW6Rh0ZXAKnbGq3UcM07OaxUZ0zkRjqx+fpq03JDzHb305ahHEeZxzFRt7fIa1DknaDxNaWVG3MM4lCqvrkdwpqKRVjp3dQyIMKBn9TrqG4xr4tT4xZmndwebHLvtv26asXEtGK4PUQgB0A5V/HWa3CCennZXUnl+z6aIArsOwCDaq652LlsmWM3iuuxkpqaNqiplY+EeX4m7DA7576hRXLiGwyPVwXWqpKlICGFO5jHfIPc/jobarlWUFSKmgnME26hwNxnuPf31xdauZhPDIGfmTCnPQ62NLhWrH0HEX12IXV2+oTiDiK4NUtPWTNUhzlgx6ZPUen9dGMUd0hCYWeNyAc9Qf6HVM84BGMY99S7LPLS10bxMclvMp35h6HVRp1UDYMQvzCckwZxTYZ6W4SPGfEhZ8K2N+uMH399NWe7VvD0slvrovrVAJCJqfm3iYHdkYdGBHUbbeu+r1FLSXCBublMjkc0ZwQAf5nQa5cJVFVJy26nZkJzhfiQf0HudDsw5Dwqq4y8WDiCmrKHmqKiOtoqh/8AzMjhAznYiU/8qb/1ccj9JB0kE82NVnU0vMVE3IAychV855HUnKv7ZORuCwwTl1VbLjwfNFWUE6TeNlaimxmKQfdI7/z9NXTg7iSCro+ejaUwxRiOWmdfElpFz8JXI8aAE/CCGTrGQfK00uqfSvvTozus0dHiFe1/b3gh+FWkjeSscxlseQdcah09rRLpJHEmI4IFkAJ/jUf11pMyRVtO81Oyu5i5wokEgKdOdWwPETOwbAIOzBW21UI4njvNUWUqDQyA59VYHUW4srHMySk1MFM+g/oV+jgUXCtLNdZvFhuEcdTGsIPlBQeVj22x0/PWkXfhy0Jw3V26GiSnp5VAk8MYdhkZy3XtoT9CVe030Y2Jjlx9SjGD7DH9NWS911IlBNFVc6oV2CHz/h6H36e+qK+QCYUaqwpx7zCvpigoqU0FJTQxU0CQHkWNMD4/9NUs8jU5STLDHU9dHfpjr/Gu0ULurskHKwBw2fEY+YDocYyOm+RsdUeV5XpXJfyhdsHpptp1LUkTzpuCOZCvVIyMG3Kc2Qw7aZ4anKgxyYB5/Kw6H/XU6lnKweHUZeMnqe2uaegeLLxRF6d3+P01n5rVnDSzItq5WEYWDLIpPYjOoPD/AJXnjb767+uRjTyEwzOkmQuPiPb2OveGaN5VrqiSaFRHDHOqc+WdeY9AM4/HUVwYHsKmTaelhnkjim2BIAbuM99F+EuF2rbg60s0bPDJgqfUH0/DQeHKMoLkjOAdeUVfVW/iuskopvDdmZ1IPqcj+eg9VXYQfLODC6LKwf6gyIZ+kbhqttoaaa2LCu/76InzD30E+j+lpKyoqKCok8tREQjHqGPQ/nq0cQce3q424UdZFDUIQADy7jWdy3SaO9rPTwCnLMOcKMBfw0Hp01TKa34MKsbT1OHr5EtXGvDcvC1zeilnSqpn80FRGRh19COzD099M0dWXpcyMmEIXJG5B6ZP4dTqm191rpnmM07ySISPMc4wcfjohw/c4aqGamZwJCnMFJ9O+iK9NZWmLOTLDUV2N6RgSyx0DPconhwBOwTLHHK2e+g19twZ6hCnmRycd+p2/XRKiuC+BCHXmCPhSDjHsfbr/s7Sr6wmuk1QseBOTIAewO4/pqqMRkTrqDzKvHSR1dMsUqYYbZPY46/poRbbUy1NRTzM0gZGCg9ARuNvmNXemt5ltdUykB6eQYb+Ek/1x+eg0iSU185cDLLzqR69T/I60FvIMz27RmAZreVpwzjlXOAe/wCA0OrKLxbTUQcnKYXEqnG4B2Y/y1frPaoq6arjnm2jwwjUYLAk759NtQbxboqW+CAR8kFTFy4HbIx/PB1mlwNprM2U7RuEyujjqrZVeNC+H/i+Bh1w3+9uowd9ajwZxJT3GP6rVeSYYQ8/xKeyt6+x79NjtqpT0AYmGRc9QfmNSKCwy1FvaooJBFX0zEI7DKyIRnkcdx10LqWVeG6jSphYvMtXEVKKOtiqFBCiQHHorbEfmM6NJTmptrFAC4Hcdcaqtouq3mgmtFx5qWtiHJ+9JLRNnYMe6k9G674O+Oe58MpKhMFQvK/KMj8N/n8/fQWsOFVviVSsoTKvSB4780TxlDUQk8vqy+YY/Jh+OtKt0Ky26JZF8rKCPl2OqbxYi254rj5Q9JUJIoJxzb5x+OMa0aggWC0xLBMjqiYRsfHCwDRn8VKn8dTzC9IPxB9QALM/MhRQFAI5T5fsPjpona6SOebwJlyj7MOxB1Aq6+jpYmWqdTtuo6/P2/HVRr+NmBamoSxUdHQkBfmep/DH492OmVrUGO5i161cMYWeem4cu13o7q0klKCTB9ouwP8AVSrfidVC48RU87MlLQhVzsEPvtv201Vy1NxoKn64VeZGEysoGCvQ/pg59t9DQ0aLsAT2x000o03qOTiD2XeniP8A1qpqYyHPKPupsB8/XXDwLU26powFMgHjwgd2X4l/EfyGmcysRy+XOn6Z/AkjqFYLJG3N88aYipQvHEXK7K8q00Jqk2BTfIx1BHQj0OrjwbxhVs8FruNUIa6mTkoKxgMFQchGPt2z8Py2URfYBT3V1plVYJlE0J9VbfH4HI/DQ6rtyT07TiQq6sNuhHXDL+I/lrK6gXpuHYjCnU7G2N0ZbeK7tfrs5p7xWVEzREhVlYkpnrjsOnbVeqoRNa3ibBkpCZUwfsnZh+GAfz1KsF4F0h/Y9wmVa2NcU9Q2wlX7rf72+Xw+GKW3V3iTLy8rcrpJ9odCuP8AfXXKWQ1FMBcdyrh67dxOcz231D1tDG+cEDlx1O2pCxLEweQhCO3Vj+GueGbbM9/ay0U3Is48SKRzswxkYPy1p1h4KoKPEtYDVzdTzfD/AK6HbWlBtUczYabc2ZV3o5+IIqCqoVT65LItLN4m2D9ht/XcZ+WjFt+jeEyCa7TvPIDui7D5ZP8AbVkvdBHBTrUxRiONV8OUIMYXOzbfdO/4nVlgc1luprgdmlXlmGOky7P+fxfJtBW2lsMJvXXgkHuZ+sE3AdcamnjeThqdh9YhHmNEx2519Yz39PljF/SOCtpQyMksEyZVlOQynuNdPTRzxtG6K6MCGVlyCO4I9NVSlM/AVesEvPLwxVSYic5Jt8h+wfWM9j26HtkUnBzCAA0tlNSzz28od6qgKrn7yjPI34rlD8vfU1I0mhR41JEgBXP8vnp2meOCphuIbngK8k3Kc88Tbkj5HDD8fXWhWe026iQNSxKebLq7bnc52P461Hq5l0r38fEz+o4Lqr5b5qOoplWlmXlYzbbew66zO4Wefh65twvfSpdWH7Pr26SrjyxufXA8pPyO43+n8baqH0m8J0/ElkcGFZKmFSU/jXuue3qD2PTWqMU5BlrtKrL8zFaKJkiMH/NhJKD1H2l/rovbZQ8ZjO6nzJ/Ufrn8/TQSlknpaxLdWyE1IGaSdxj6yo6q3pKvQj7Q3HpomhEUyMhCrL5kz9l+4+XX9dMqbg8WbCnE8rYqiiq2uVDEZA2BV0ybfWEHQrnYSKM8p7jKnYggtYrpHmnudvqPEjzzI4GOhwQR2PYg9DqHNUxJEGZsZ2A759NV6sNVbaue5UUMi0c3mrIFGTn/AKyL2YD4h3G/Ub3tUKD8GWU5/OfQC3W1XSxkzqk0E6kSxnop75PRe+5xrP676TIbWlTZvGF0lhH/AAksUm0yb+WRtiWXoeX4hvnrij3WSoltEbUdbJNTsfGQLISkmRuMDrkbj3GO+qrWU8TxgNIYlOGjkX4lbsR8vfSn8CzudzcQ467aoAHMKXrie6XyqYXWbMDbRwoOVIvTlHY6C06Q0szpWkRuuWUoATIPYZwD65I9R6CBUXJ2jdeQLVx7SlftDoHX0B746HI6Y0zG7VsGJmPMpAIB6ehHuNx8idNE0a7M0jEVWahtxFhzJ9bfAiMlKvhA7ZVsu3zb+i4GmeH7rcbVeqe4RKcI2Gj7Oh6rj3GvbbR08UjipPJKmCV5clgejKDgY27kYORv3I3OmrorQlxoaVvqrZU1MOWCnfKGTAw3fC/jrJBg57MzZmB54hiWnp7bcxDAnNbLpme34ABjfdpIjnAXlIJGfcdsan22pNXI1NTRtVuhwyQycsI/zy9W+Sgdcb6q3CUkd8ttTwrcnCx1L+NQTsv/AJepG4/Bsfj076slLxDPHTLFTWs0lfTKYqtSmUjZeoVR1HcE4GD66H1NTK2fYwmtlcblmtWCyWi+cLRWy6QUsVXDlgIQURvTbPmHrnWcX+GG2XaWnoYDK6ZDJGuRgZwQB077nAI79NV2XirwJGllrJqyoIyQr4C+xbYKPYb++od24xkr6bwaODkUnLQRZSIH1Z880h/L8dZIrk8CWeysrz2Icp63lrpIqyRKuCdPBqqWBPE5Yz9pmB5VK7kDcnJGd9V2uVuH62poK6qklR8SU7xfHVwncMXJy2M4IBHY99DqOS4NHzNLiBc4HwRJ7f7ydE6Cei4kt7cP/WIai50Iae3SMp5Cd+aEnqR3H47HA0VtGNrHmZJutBAHEDVaftIK31aKCGPIzgKMfxHpn9dQGq7fTyeDSo1fORgKgwin3Pf9Px1YLFwLxJxCEqLtMtDSHcRgYGPZRjb8h89aZwxwVY7Ei/VqRZZh/wA2VQSPkOg0BZrcDaohNOjVeW5MzC08E8TcR8klwcW+g+zGPKMeyjBP6D31o/DnAVgs1Pyx0onlIwZZOoPqoHwn36++rbHF2x+OnRFjtoBrHJzmGgASuU8kltrnjqGzG5Bkbsc7CUfM4DDsd+hGj8cY5dcXG3CrpsLyrKuTEWG2T1B/hI2P59QNR+FpyZ/2XU5jkUER+Ju2B1Qnuy/qMHW9ii1fMHfv/wAyqsQdphKKBuX4dOLGQOm+rJZaaljmVZkDA7ZPrrjiC2CmkE8Q/dv+h1i1JC7psMkZgWJMjBGvLhbobhRtTyeVgeaOQDJRvUfyI7gkaeUYOTp+I4Promiz+8qVBGDKVZq2exXFrdWqEpy+BvkROd9v4G6g/wCuLrHKrIDqBxJaI7pSeVFM6qRGWOA46lG+eNj2OD65C8NXOSnl/Ztazc4/wnfYkDqp/iH+/dmri1c+8wxtOJaJVyMjroZcaYuwniwJ0GMdnH3T/T30TUhl203NH6HfUBxJiD6eVaqn6+cevX3B9xoXdKFZUZWQNkYIPfRGriaCRqmFSSN5UXvj7Q9x+o06Gjq4edeUkDO3f30RTcVOD1MWTPUzXiOxQXWH6nWErMu9PU4y23r6kY3H2huNxuI4Cu124J4my3lYYWaLOUnjO4IPcEbhv9RrR7vQLNGylWz122II6Ee+qvd7cl0gNLUMkNbCC0FQRhffP8B+0PsnzDbI0cG9JVuVMCspywsXhhN74fvFHerdHXUTho3HTup7g++ianOvnD6OOLq7hi8vS1sTrGH8OpgPUH1Hv/P8dfQ1urKetpI6ullWWGReZWB2xpNqNOaW+0c6PVC9eexJWloXNfrZFK0YneZlOG8CF5gp9CUBwfbS0NmG4lJ6dOmvCM7A/PXHOckj8NNVdVDSU0k88yRRxqWd3OFVRuST6a7BJF4gu9BZLTUXK5VMdNS06lnkfoB/U+g6k6+cr7eI/pS44pXu1ctm4bp25aYSkyAL1MrqPidvQYA2HqTC+lTjGf6QeITT0cj/APhmifEY+H6w46ufX29B76a4cuMVkudJcTRU9WlM6uKeVcxnHQEdxphTpCF8xu4BfqQW8sQpe+GbTR2SpuEN+iZ1qPCpaU07CSojB/xSc4QYxgHJOe2qgkskT86MQR07a1K7/SBbr5ZrwtztNC9xuZU+N4f/AJdV2AjHY4Gx6566otVTWN7TRtSzVxuRd/rcb8vh8mfLyEb59c7aL0t7kHzIsvpC/RBCyvLMXkdiWPmOd9HuLLfw/wD+FrfUwXOolucjESULxeRU7Mjg9Pn166rswVKiTAZQG25uoHvr1yQwJJ2A3PpohkFrKwOMSqWlFKsO57b7HIKKsqPrlLA8Kc6xzMQ0p+6m2O2fyAyTqBSXJxNiRmjKnOV6Z1JapkVWQY5TsAR209YaO21dyhjuTSpRtIvjPFjxAud+XOxOPXWo1Dox3cj4mbaeu0DbwYQk4gq6mljgac8sf21Pmb0ye4HYaN8P2w3xy10v6W6Dwm8F5FMik91wCOXPc/L11RuII6WivlTHZZ5qq3JIRFLIvK7L2yPXXFJdJVyI5SCwwR20Udt1WKsA/lATS9VhNmSPzmm2zhO1w2+7PX8SUUNZSJ+5EKGZal/uqRgADpnp36DVHkgEE7+IAd8ZzkE+vvopwvQNPTGslr6Wnp2nEDCWbzuSMkhRuVA3J98ddHeJoOE6Di3FLNNeLNDGgOSYjI3L5t8Ljfp+GdDVM2mcqx3E/aaXVDUVAqNoEo0hWSTCdO+nhIlOmQRnoc99eO0RdhBGI1LEqmc8oz0yevzOmIKOpqa0xIpyuM8w2TPc/wBtMbL1pXnsxbTpXtPp6ElQS1VXL4FOhklbooPb1+Q1buHbTTWvkrKw+PUnf5D0XPQe/U6bslHDQr4NKgknYedn3P4/26a7q50pXM1Y7sWJCRjd5mz2Hpnv+W+vO3XC1se09TpdKKF57h64XCGWllqqiQQ08ShPEI6kk7Adz6Ae2e+nOGeGqjiGP6zcFe22GMc4jLYecD7THsMDOfy9dT+EeD5qx4rtxLGDJGP3FF/y4R7r6+x/HUf6XeKDTU5sNFMUkZQ1Ty+n2U/HYn2xobSqWs8qnv5+I0tRaqvOu6+JSeO7ilzu0dDbh4Ntp15KaJVwFXO7kerdfljUOGJYoxGvQba4oo2EPiyktM+CSfT01KUDmGvW01+UgQe08va5tc2fM8jXfGpkCiNTt5jvpmGPcufw99P5zuTvplpKdx3GIfFdVgeUvZ7nanfOptsuNVb5uemlKgndT0Oh+ugdHWVq6lWGRENVr0vvrOCJerdeaO6J4VRyxTnseh1FvFhVgXiVT326HVVQrH2Dlhsfu7/z0Tpr3clpjSQNzs3lUkZYfL315zVeHfhz5lLY+xnt/CvGTrR5WoXJ+R/vAs9M9JUsoblOd166snDfDNVcyk1SHig+yp2LD+g0W4V4WJf67ck8SY7hGOQvufU6O8W3JbDYXlhbkqZf3dOPRj1b8Bv+Wgrte9hFKGM6fD66s3EYme/SBcKeGQWigCiCkPJ5ejSnr+A6fPOqjFFyRgc2SdyT3OupJRUVLSjJVfKpPc9zpwHC6a01ipNsX2P5rFpyuQuDqbbKkxMEcF4yencfI6ig52xp6NORMgYJ/QauygjBlVtKHIhusu3iwtSUXPDSYHiE/HN/m9Bn7I/HOhbckmebqex6fnrxtkCAjPU/0/376bwdUrrCdSxtLHLSHVWzPM8LFW6lGOQflqBLGY35JEaNh2bofkdHQSo3AYemuKoJMpRlDr3U9Rrdbig5mDaRLOV4lZqPEjUy07mKUnGV/qO+naC9PCQlfHy9g67g/wBteVdLKsxelPix/cJ3Hy1HXkkBRlw46qeo0tPiDGwsDxLW+HqybXHMs8U0csYkjcMrDII05z7HB1UOaopPPRvyY6od0bRK23iOoYQzHwZ+6t0PyOjqPEq7fTnBiXVeEW0jcORDSzOjcyMQfUaJUdWspCTMFPb0OhY5cbHXuq63w6nWL/UHPzM9D4ldom9B49xLGdhuRrH/AKWbt9bvIoY3/dUwxsftHr/Qfhq+Vl3e226eZjzKiEqD97t+usVrJmqaySd2DFmyT668jd4e2ltIae80GuXW17l/WRm+E6t/CtMKS0/WHHmf96c+nRR/v11VqCBqyvip1+2wBx6d/wBM6t/EM60tq5I/IW2Ue3Rf6/lrJeMtG2OhKle6lqmrlcNnJwP66kWemMk0cYHfLaHDDzgb4XVt4SpPFdnI9tZE+8rYcCGYFCRqBtqTQ0k1ZUBpnCqSAGY7KP6DTgp+V15t/YakxEZIxj213dkcRc3JzCNvmloakvG4fzbkHZt+o1c6I2+9UpFQPOOhB8yH2/tqipJtyjYZ/v8A30Qt9TLTSiSAkMB20Nam7n3nUfHB6hC7WOeicO3nhY4SVRsfY+h1DjpXL4CE99hnV1sNxp6+AxyAMOX95G3f56YutpkpQ09t5mhYedAcsn9xoYNkYM3II5EDVltrLY8UNbCEMi8y4kViB67E41IpAW+Nhg/axs3sR/XUKqbwUNTUOSCQOY7lvQaG1F1bdaTKREYYt1b1+Q/2dEabQXaj6BxA9R4hTpgN55hyt4lgtpenjD1Eiqcqpz4ZwcHPcZx07Z6dw9HNW34Vc6KZnpYjNIxdVCRggEgHG2SOm/tqCVgqV5eXlI6YOCp9RoVcaOaBTy4822Rsr/2OmGldtG21hzBNVRXr68q2RK39IFb49xip1fIhjz+J/wBANV6Is7qdsgfy6fqRqVV10VQtWppUeZ5+ZZ3dudFAI5cZxg7HJBO2mKQAMzEDbGfwyT/TV77fOctGfhun8ioV/EJ0nLHHLKTsgwPw/wDg6EqzFnkIxscfPoP56KTfurYFPxNj89CmOINz8Tf7/XGslGeYazy9fRPTlKatrhjzyLGp9AASf/th+Wr8lXOkRUOWBx11WeBKc0/C9Jtgy5lP/cTj9MaOFiNvbXtNDUE06jE+VeMXm3WWMD74/tJQmDZLbdtSR4f1YlcFmbG+h8YyRzd9SMbhOmTtosjAigLzgSt8QKs12kDnyxgIB8hk/qdc0oDxkLjHr/v5aaqeaernmc5DOTj5nUujQCnOFz6DXjLXBZm+TPpmmr8ulE+BNF4GtLLY6dwvmfLf/ZH+gGrRJbpVVPJgYJP4aLcGWoJa6OLCgpCgbPY431J4yvFqs1BOiss1WsW0Y7Z2BPprQak8VjmBHTABrDxKVBVmKQrVEBWbYntonkGMvGQRjOc7aoV9vSKRNUyKX68oGANReHeJ7l+0USQH9nMcBCPNzeo3/noLxDQJ/wC4p5+IV4brbGOxhkfMudVKGcjAJA3H4/6abYusfIRhSckA7nXkckNQDJEysCevpr0qQxIOx9e+kanmOyZFqx+62XkBbYDQi522CrRmdQsoOzj+ujVavlUL2GcaiFSoztq2/wBWZU8jEz65Wuopq8KykDmBz2Py0MrKj98/MMHOBnvv/prTZ4I6mURyJzAev9NU+82CTmd1RXPOAPN0+fto9NR6cMYFZSM5EE22joauZf2nPUU8ABJeCMO2R0G5AAJ7749DqLDRtBNzchIH2h0Py9dabwH9FPEl/WOV6YUlNnP1iqHIn/avVvnjHvrQPpT+j2w2LhejWjoQaueqhg8bmJJwjZxknGcZPudRrxniWrRwpMxvgDhWWvrrq08r0/7PQOyNH5mJdE5d8cvxZzrSLXHT28IIRGgRgSOUPzkeudj8jtqZbogt44+mwpH10Ird8eP0/wDsNRqWjqLlWrR0oUuxyCzBVUDckk7AAaXWsXMujbTKbxxa1rrjSvSQgDxC7pygZyw326aqFk4OuFbZL1xNafrtPcLbUxlJUX93hufnD+h+DHbc5z22riCsqLVJR2yhPgq9MrzuiAFzjcBupXIJz0O3pprg6sNL9HPEdLHDEPrdRGrvzENt/Mf31x2IVQZtRfgkzKeEuJDW1bUhhNFd45C8lFz+Es74wZIGIIjlI6ggqw2YMOlrelprzDI8HItxeKSmjYqY1kdh8DJuY5ds+Gcg9Y2cbBuq+iW+8XxtNbbXPHPCMpUEeGARvjJxn8NA5pbxw/eZeGuM/Aor2IwlPWT5NNXR52SY7cyk9G2ZT3Vhqob4h6MHXLCar9EvHc9v4TNikJeotwWEU8QKkbvnmkI9jsuw+91xLu30gVLPJAsiwbYaGm67/fkP8hk+41SLHeKarSoWUvDMtQEZ5nXmV+hjmYbE8+eSY7P0Yh9mk3CgWqLiQNHKueViMEHPQjRunFbjB7ivXC6tsjqQ73HUXGqkkBjITyoqqAFGScep3J65PvqAaVkhkVlIOOmm6mWsoq+WKQFWABXP2vceo1Opa56iALMik4xkDGmtCuoYdiK2NZMj2W1tXyLAFPKWx8idaBwvwTWWstNXNNJS003MojxurICThsrncbEYON9UC33qa1VpkhYquQ2MausX0n1U9unoC6c7BmyF6g6Ua9dWzr5XUP0NmmUE2diGuJeFbDc7FPcbbMEARn50jLAkA5UDqrdfI2/oxA1glK1VQXNYEB8GcqhXOftfqNG//EFzglnNNVSxw1GBPEjHDgHOGGd9IVFL9dpLjFCZWgdWaInOCCDkD+mrqXp+qUcV3k7ZKppF528wOG6A6itiPiXHPs6n59O35aC3Seopbt9YhJEbgcy+2n57jFLeKSSLJdiFIAz3xo1hkkwIoc7ZZqepmQq8b8jAY5sb46HGgF7hjS7L4ZdmkVXK55iTjf8AUE6J0cM02Q55FGcAdevrruelAuMJjQHYAnfbc9/+7WNjhHyJolRPBlUvFBUSV7vG/h82GKgbnPv215w/SRxV6ciN4hyGPXrt17autVaUmAckMygDA6baD1ayU9QRFCAytg7fz99Rryz4m4REXJjUJnhV0ZFJVvMFGdF6KrR6FHOTyPy57gH+fTQyarmF0kLtyjIdWAwR3GPfROGCKpp55KRR4xQs8SgAPjcsoHfGcr+XprBkKMQZavUK/EJ0m0syI2Y54lz78pH5g4God0puZqWpJAZG5Sc/799Q7VXNDPDIJcIG5gcZAPXPuM4yNHHjSooJVRlfA5gV6Ee2d8ddCNnGYQBxGKWFqDiaONgAtRH5T23HMB+BGNc8eUpWipq1QcxScrHuM7/01bLdw3VcR2WnuNI8ayW6naRi7YLFCHx+OW/LUfimgFTw9V8g5j4fiJj7WNxoZ7NtqvLqvoImXXWIJdJDgBZCJB/3df10a4NgVLpJTOAVnTy/5hv/ACzqDfkWSit1bGPJJDyk+6kqf1U/nqVw7Uha6jmLY5ZF5iOwzvrfXVeYmRJprCpxF9JPDf8Awa3aj/c1tMyhZgM8yE4KsOhXcdffQ7hDi1qukloJJ1o6uMcgkcc/gtn33KE9zuud/VrZ9MtHWU9ro6uKqmSl8Tw6iJThG2yCQOvQ/prGeJKOe3XmSqiZoJGw8bDrnoR8s50No6RZRhuSDGHm5bBhHjUXaKvLXCSZ5xhss3MGI6Ee22r7buNqs8J2uAzM3hxGlXtgKfJnG58hUdumqvYrnb+J7MbXc5BDMifuZcf+XkyRnuTEdvXlOR93PljtFdSU1ws1XFy1dMBPGpOQ4U4JU9wVK/l7aYVKj+lhB9XUTXke0KmtqLgzislYJktgbKP7/PXKFEJCgH20Lp5pGYK4z6e2iUARMgkDvjOm+k2rwJ5y8MeTCFoqOWqRZlIgyVY4yVBGD+HtqPJTfUqiamnI543I69RnY/jrgzt8MYAHy1Lup55KOs5tpoQGz95dj+mNbWLtIZZeizI2mQn52OEGBptYSPMW37Z0+0gyfCGflrgRPJlmyx7hemtwfcSzKPeO1YWpsTSoA01A2R6+G3X8jj89DIKeWfMoY8pXD8vTHvovaJIoa0RtkxyAxyqOnKRg50W4b4SrquSQVLLFSxTNEQG6kYPT3BB39dDPqFrJPc2SosBn2lGqKFJTinV3mB8vhbFW7HPrq5cLvTVNypbdxfRtT1yxDwJW8qzp0Gflj5j5dNEtXD1ut65paZVf753Y6Gcd8PU9xtiTSKUkgYlZU+KLP2h8jgn2z66V3WNc+T3GVBCLtPUh8S2c26qiq6CIJJAVmgCjYcp3X5f/AI+tBt8sNbQQVsG8c6B19s741nHB11rqqmgsd6QpWxN/wzMuFnUEowQ9COgHofKfs5vXBafVjWWhycQSeLTg9fDfOR+DBvzGs3sFiD5E02FT9oReFXRkdAyMMMD3GmuDVaKqruHZ3JZ8SUhJ2JAPL+a5U+6jVnt/DlxriGSEQxH7cuQCPYddSOJ+EEo7Ulyt7SvcKI+J4mdyg3YAD0wCPlqiDggzTymxuHtAcTHOBtjrp6roqe4UE1HUxJLDPGUdGGQwPUaJSW2a5mnuVsg8SKtQOwBwqP0bPoM6slj4bhp0V64ieXryg+Qf31QLk4l1rZjxMl4JeXhe7pw3f6uQ2ieXkoK59/CJziKTPr9lu+4O4ydrtSrQFLbzl4wuaZmOSVHVfw/kR6aF8f8AD9Jd+HJ6d6RJAiHEYX4l7jb8xjcEDVV4FvU9vlpuHuIZpJYWfnstwlI/egDBidh0kXzDBxkbjO+O52HmEIuw4M1IdNLtqItbTKGQyHmRckHt65PQaonF/wBKFltXiQQTtW1IJHJB8C/5n/trlmoVOByfgTfjGSeID+mnhukUmpUpHFUuGBDcpimHRlPY+/rrLkvU0NQKG6IpmTdplGOdRt4qjOxHR17bdt9O8ZccXviGKSknljgpHOTDCuFbfbJ6n8ToVByXa3iGocpUwbpMvVdsLIPXHRh3GNGaei7ZucYim+6pnKryJbaCXnnZZQhlbfmB+Lb+RGD+GiMk8MK4dvMeigZb8tUax10/gvRVWIa6jxzIp6rvhk9V7g+5BwRjVpoDE8KzR45XHNnOST3/AF02pIcQVgVgaqM9nlkeNWgstQ4Mg6mjcndwOyE4yN+U79M4F3+jeKVmABilOdjsHxnHyYbj8R21dZZadYWScoVcY5G35h6Y76qDIbfU/suoR1tU55aOWQeaI7nw8+x3TPbK+2uOgQ/aTPmDnuV+tpDLCs6uIZo90JGT/wC3uD30PS4eFh4YSsg8sq53U+mfu9x6/mNEbjBPBVsk/UHBx0Pv7g9dD6midP8AiKdE8vUEhVde65P6eh/HW4BxuPXuIESAdnvH1Vp08N3QkeaJmHl3+yfY43+WeutM+j3iGsm4VnsiUsVXA3MhpnQs8Dd+hAxncE4HvudZtRVFNvFEzlzHzxMVGWYdVwTttnrvkaUlbXxF6ulnYeIvJPGrnEqjoGwRkjqPx9TrDU1+YM1CSpwrbXMI8QD9j1JpafwGdT55o35+Ru4zjlUj2yf4tHKq9mr4VrOIYoBUNLClLeqdJCmWTJhqhjc4ywI2yGOfhGqrT01ZdVjmqJ2qIkHkLELFGN9h0C99uuifDl7tlovMdNG0telQfArUhTmi8Jtj8yDvv6dNB7lA2ueYXQHLHA4gejt7VUQkcqIF3DMeWMfn10/9dooCILfTtcqjOAFXEYP8z+P5asEP0d3C4cQ1NNPcS9ppyGph4mxhbdcAde49NtaRw9wxabNCqUNIisBgyMMsfx7fhoC/WMpKDiFVaJB6jyZm1q4Ev9+ZJ75Umkp+0KjBx6Y/+PlrQrFwfZLVRmKmpAGxjxifOD6g/ZI67asQQAYxvp2NDsD00vNjk5zCtoxiBrW8lPVvRVBUF3wDy4CucnI9FfBI9GDDR+ngHcEnUG9W/wCsU/ixxl5Ihuq9WjyCyj+LbmX+JR6nUzhys+t0ih3DzxYWQgYDg7q49mG/zyO2imQOPMH6yoB6kw0hIyAf7aSQnGOXVutooqulCNDGsgGGAGPx0Lr6X6vUFFxjqMazasYzNdhAg2CDkP7xRg9tCOK7QZIxc6PnFRAAz8nUhejD1Zd9u4JHXGLDhMnmOddpy8owc75GuVv5bZnCmRBvDl4NzoubCJURYEwB2z1BHsRuNE5qkNCY5ZncHqDvqn3Snlsd5Svo0P1aU4KDp3LJj/7JffmHoNWCKWOeFalHDI6hg2dsatf6eV6MiEkczzG+u0IU4Pfv2GpFHb6us3gi5UP/ADJAVX8O5/D89H7fZaSn5XlBnkHd9wD7DprOqtyciaBSYIoKOoqgDFH5Pvtsv+v4aZ4m4OhqqR6mBz9dXzZUYBI7gev8/wAiLkBt00sDR6eg5E08sEYMy6yVsjhqaqXlqItmH3vfRcHOnOPLHIpF2oExKm7gf76H/ffQ211iVdOHU4YbOvcHRW4MIGyFTgx+SPBzjQeqV6CY1UO0JOZF7IfX5Hv+ej+QRqHUcuSD3HT11YEHgzMgyMzR1EQlUY9R6HQK80KSIXQ+GQcq69UPqNeR3Kkpbo9HT1McsZ6BckIe6FumfQZzpupqaqsJ8FlhpjnzDdz6j0GiUcj0mZMAZU75Q1lZSTVJhQ3KjH7uKEENInZCSTkH7JxsfL6aoNB9Md/oVloaOmV6ckqaeoL+GrepUEZO3Rjj1XWpVFA9LUmaKaRpiMQvKxKsO8bexx/s6z/6UOFknV+JLVTkHJ+uxD4lI+1j1Hf1Hm9SNK6VtYJYcLMbbWpQvWPVK1cOMeL7tN49ZequPl2SKFvCjQeiquAB+GlqBS01XPAJIIGZOnN0B+WlpuPDtEvBH7xR/wCp6w88z6tZlSIu5AUDJJPTXzZ9Mv0gS8Y3CThjh6oZLJA2K2qTpUMD8Kn7o/U79NWD6V+NLlxVd5uBuDXLKoP7Sq0bCqO8YP6H16azr9ky2SMUclM8PL6rsx9c685o6Vc7nnodVca1wvcYijhpadYYlVEUeUenz99dxsGGc4/lpp0ZjuCc/lrpVKjmI2xsDpirMX4HEVleMnuejCyllXHuNWix8SWul4bmsNXYKOQVE6yS1pXM/KpGEU/ZHuPU6qqSksQAMDXb4dcb57n011wLRjMqoKHkZliW52Gj4r/asVgpa6hHmShmctEDy4HMcebffHTS4iko6rhyCOisNPTVYmeZ6hZG55FbOIwpOAozsNzsND+GLjHaL1TXCe3wV8dO4YwTZ5Gx0B9tXp/pJpqy1XlJ7Hb0rbo+Xn8IExrjAVF7dBg565J0PYprYbAczVVDoeRMrq7bXQQxSVNDUwJMpeJ5IWUSKDglSRhhnuNQjzBSApAxnPoNXf8AbnEFxqVVqqabkhMEKs+0cXTlHouh9n4SrbjBca3x6OmgokDSePNyNIT0SNdyzH8vffRy6jA/q8QJqf8A/XzKickYGBnYa8WiVshc8+NyB11auMeFKjhyqjiq56RppYVkKU84k5A3ZsdG9tA6V/CWRmUFjsqg/D7/ANddr21p5iHJmrMXfYwxBTvUUhKscqD1Xp/pqZ+05KhR4zElRgZPXXLxqx5zkZOdxpswxeLlgOUdvXRtNjKm94JbQjvsSH+Ga145ITBR03iRVAn+tyLzsOXogU+Xlzucjr+WrHdbjNX3CeueQSz1EhklnIAJY9Ttt+Oq1aoZpSscaHmbblUfpqZNdIrcWgois9Wu0lRsY4j91OzN6t0HbPXSi8i1y5EbaesUoEEKyVqWpMnL1TLlYD9kdjIOw7466H8QUF2ppaesudLURSTRiQTOuM56AY+HA7dflqw/RDwo96ubXy4qXo6aTKBznx5c5wT3A6n12HrrYrnDQPbZzckhalCFpjKAVCgbk50v/HJXeFC5+Yyr0DWVFicfEx3h76Sq22UDUNbGa5guIHZvMrds+o1UfFnuNdNXVEpkZnLMzdXY7k6jXiOiq79Uva4ZIaJ5CYkc5IX3/njtnU+KNY0CIMKNeu02kpr/AKiLgtPM6nVXXf03OQskR5Ixp+JQckkbDf5aZjwBzaJUMdM0bLVIWVxsR20SEY52jMFe1ExvOJXqy4VKVZkiwYuyEdBqXQ3aCYiNsxyHsdS7jw+zKZaBxPH3X7Q1X5qVkykkZD+hG40XTeBwIt1OkFhLEfqJZwQeh04jeTG35b6AWZbgzYjYNCD5jJ9n8dXjhvh6ouRWSQmGmB3cjdvkP667qtfXSmc8wfS+B2X2Y9pAtlvqbjP4NNHzHqzHoo9SdaBw5w/TW8LJ/izd5CP5eg1NtlBT0UAp6WIRxj82PqfXRali6a8hrPEHvPfE95ofDatKgCiPU6Kik5CqBuTsANYx9It+a8XVmhc+AuY4B6IDux/zHf5Y9NX36T72lvtAtkL4nqVJlI+xF/8ApdPlnWOKWld52bd+gx0GivCdN/8A5TBfFNSB/SE6SNAoVPhGw11jtkHXiEjI99dhQc40+iUMBOqdOeTc4HrqXTxeLPlnCL3J6AdhpoJyIBkZbr8vTUyNSsYB+I7nXa6/NbEF1epFCZ941U08kB5pBlW3DDcHTIJz10QgleMFQQVPVW3B1y9JFKM07CKTpyMdj8jrR9Oyc9zLTeI1XcHgyESACe2odW3IuQd26f31KqElRjFIORl650MqJeeTPQDYZ0p12oFacR1pELGcAg7N+ffTc8MU64deYjoyjDDXYGdvXXqR4bOdx315tt1h9MbgqvcHNTTxZ/50XqB5h8x3021NHPGdlbHbuP7aNgDvsfvDTE9Kj5fZH6eIvf56Ipwn1dwe9TYPTBlPVVtESozNEPsk+YfI6L0Nzp6geV+Vu6tsRodNDJDvKOdOzqP5jUGrhiMRl5tlGeZTuNO6Na6Dk5E8/foEsPIwYz9I1y5YEpI23bd8fjj+v56oAwEOSOm+pt4qXqq0l5C/KMZPfUEgs3KoznYD10l8Q1JtctPUeF6QaeoIJYuB6Iu8tWdsDw0PufiP5Y/PTPFtYJawxr8CDb+n6aPU8KWux8jHDKmCf4jux/mNUerlaoqGLZ5pG30DZ6QFjZDnLGOUEPMPUk9NaLw7Sinol28xAzqo8O0Znq48Dyr11oESeHEFHYY1gxgt1hzicSOY32AI7g99doI5MtHnI6qTv+HqNNNliSdedGB327a4JhjIktARgYHz0Qt80sTloZGQsjRsQcEqwwR8iNDFqRIxMoCHopA2/H++iNGEQqZZAkZI5mxkAeuO+oZkRCtETHKGgLK22/8APVoor/SLAVNXHFVKMlCvMrA++s5qryxmMMaGOHoWB3OvYlUp4itkdiO+mGh8NTUepz+kVa/xR9KNqD9ZcrgtU9StZbKuSJ0cSDfCc4zgjtnBI/HVUkgdJZPEjJcA5DnGPf30Xtd0aIfU6kAgbBlORnUyup6eoj/fOEfl/dkH3/3tr0FKin0EYE87f/XO9TzKiUIyc4Oo1+uQpbHWSkgssJXzDIYnYZ/E6OG21L1Ygp4XqJXz4YjUsWxvsPlqhfSfO0FuipHUrJNLzMCMHC+3zI/LWWuWpqiWEI8IaxtSqqcSmw4kdQM8wPc7r8vUaI0ykgZ+2w2+Zyf0GhNvDuzNgEqux75O39dWCgTmqEAGwy39B+gOvMDOJ9GwPaeXh+VY4wcnr/v9dDpELSRwj4zgY9SSNSbjJ4tcUXsQCde2KKSpv9OY1DMsni4PTC5O/wCmt6+xBrjtVjNeo0ENPDAgwkSLGPwGP6aleUtnbQiguUUjCN8pL15G7/L10SjcO2/TXuKnUqNpnyPU12K53DmPb5AHrrud3hjd8bqhOD8tSaGKB5o05mZnIABONzpriGWEUVSqxFWdwgY56A9vy1hq7/LqY/aa6HSm25B7ZlVxgMB00Xt8S4gjc7MwLfLpoQqnA69QNFKitpqejM8AkdigQqcZ5t+nt0314wtyAfmfQrAQpx7CaxwvxxFSXOkW7ea3h/3mEHORjb5gba6vd1svHnHlda7ZVeDFWeD4UskKABIxuFJOzHfp1Gd/XFYoK+4snjPzIwwI0J5evf11abHw9UVtzjp4ImqagnAjUgBO2SegHvquvKuxagkHrMrolcVbLwCIDa0VU9SsjFpPL/iOMBRzEbdu3bR61WuKCjlnVfE5QB4jHAySB5RrR63gqitNjpZ6uqWprfG5GhjGIVXlJ+bb43OPlodfaBYOFXucLxk1Ewp5YyozGFZCCB2z7f11emlzUbLTKvcqWiusQNwctK71z1JmyeXkKYznzZO/4anrPFJUSQB/3iHBBGCffGpf0X8UU/DNlr5p6H6yJ5wCykBlwvYn56rN0rf2jxFU3GMSxCabnUOwLgY7kd9tDvp//wAZX24+81ruB1LVhsn4hitI8Vgv2QBjUZ0zjfLabs1TJcKp6Z15ZFyecnAwN9/TVmpLfDD5mUOw3yRt+WlROGjAgiBLVQ1E9bT88LL40gVRjqM9fy1pX0U8LBr/AFdxrKBEibn8KOUZPUb4I23z11B4Rp/G4rpmOD4UTP8A/YHWpcLQiISNsCRt64zvq+dzDM5UNzAQoIANjrPPphXxrxwbbjuk14jZl9lKg/8A22tJYjmODrNfpKaOT6Q+HY2zijgnq29AFUtn/wCw1tkCEXj0YEoHDUTvwXxPfpQqx1lfG8fmBJHiuenUbnv6aBVNe8dLHIkBRJmISRh1x1x+eiStHRfQUPq6yeJW3NVcyY3KxZPTtnpqBwbSB7r/AMeaC50awgH6yXPKCdvDXIKjfvjWO1MZJi1yykASZcqqpu1yt8IRqiopbSuI418xGCVB/wDcNztvrRfo3+j40vDiycSQwr4hWY08L8/ofOw2Y/5dvnqvSXe02ZbjKYRTI0HM8r4UscjA33J2wNWDhzis1scdDb3gpJmRcCqcNLjHXwwfKP8AMQf4TqE5wJ2gruJbmaLUXGlp4PESrjgj7FsYY+gHf8N9fOH/AN9LPY7xdaGOsiEkyUk6B/q+XD7FATkY3B2O4BzynOqhxh9Lt4qZqtrVD9XZ2IE8p5pcZ7Yxyj2UgazgXa4XWr8auqWmcMwALBVQegXYD5DRSVEgkwtLnsI4wI7w1xItpqDa7kWFKrMYKxUDvBzjDK4OQ8ZxgqQdvXWl2e7FAlPUsCnh5jdCZAIx9pDkmSIDqN5Ix99RkY3UwtLWylc4Vd/TqRvqbYb1PZf+GlSWa38/OYQ2JKdu0kTdiDvtj8DrJqyvqWGZV8q02quWOqAV0V0ZAVKkN16FSOoI6EbHUJKEwR5jPMufxGhVju0bwRvDMlTSTt+6eMKgZj15QcCOUnqhwkh6cjHc8JcU6yQnxQzHlIBAODuMHcMDsVIBXuNH6PVZJVuDEup0Oz1r1K5eFUSt25k3Py1Ct7CO48oJPNH1/DUq/SkyczEDKn+Z0Ht0srXWEpHkMg8x+EbfmdGLxtzFxQnOI1VMyy5VzgE59RpqC4ETl6dC7g+bsra7mpZDOzO5kPMdgNhv0xqdHbJJSGcpCvXJHX8O2hrnXBE3ppYNmT7rBFcqOmqISFmaEB1z1On+FLWn7Vt8tVApgWthM3iDA5ebzZ79Bp1Y6GO2U/I5d1Zk589Ne1j1MlIsYkOVHkIP6fL+WgrmcDjqF1+Wx+80fiPgxqTjC7W2z0z1EdKBOsIfL8jKpOB33J29tUniHxBBDLD5fDbDLjDA56fp01rH0Xsx+kZZqieWpe42pJWnlqRN4zjmBZT2Gx8pAK7jGp305cJUktlkvVLEIqtGAkZdhIp+8PXpvqDBIMvZUWrZl4xMWomnEz8rZ33B/D/XUu+GFmo3CqCytHn3DZ3/AAca6iMb09FUshIqVP8A7hgkfky68vlI0tjjljU88NQABjsysP5ov567aQxBi9TtBEF3qhhMyM7LG+OU5PlyNsag2uokt9aGBIbBXmz8PMCufwzorWW563eR+UuoYH5jUSstH7Nn8KsnifxKYTwvE3NjLdG9COU7b6t5gyMmYFT2BJdssNw4kkmNnpHlroYzJNEpwHA6sP4vbv8APq1QXNqMwB8IATG+RuO/T8SCPb10fsfEdBw9Sy1FHDVJdnPknjn5YzGRuCMb9M6r9eqXeCVpZoo64tzo5OBIQejHsSGGGPpvjqB9h3MB1DqrhgKx5lnslymprVUpTzmJ0cOORvKytsenY8x1YuGuWrsNMH3wnhP818v9NZZaLmLdJUUdRRKzOQrGTmVo2H8j1yMb/lrQeF7zTUtsqPHbdGDhVIxgjG56KMjuR10HqaSUGPmGVMA2DKPe6L6paKy3sQGoawumfuOP/wBEH/u1X6CdYPM7AKd+urhcbpS3jiWYJCPCrIjCxHQNjAIJ67gb4GqDNTPTVciSsOQNgE+2jqRvrCtMGG1iRLFxhxTW3iz/AFFQWTC82Thdts4H9Sfw1X+IaNqvh631cgUlU8OQ9/Lld/nyg/8Adp8zwCAxqN8YBxk69ssrV3DtyoHUkwyiVCe6sOVvyKJ+etKqVThfeVW12OZR3hNLIJqV3jlQ5Rwdx6jHfPodiNX/AIG4uo6rwIrsBHLSBgrAZaJD8XL96Pvg/CfbfVQIjXmDL4h6Z6DUB4/+LQbx+fHMpwVztnP46o1eeR2I0qt3DaeppPFdnmpK1hEqmNxzxlfhkU9x6+nz0IpgwP744IO3rotwRxFT1sJsV9/dsmSrr/y/WSMfd6cyduo8vwO8RcP1VBWESqpBHOsinySp2ZT/ALIOQQDrTTako+Gges0Xp3L1B4mXPlBJGp/I1Vw/KvWSnlEifI7Eai26nlqZxBBBJUyHACoh3/TV4tPBl6p6CorLgsVPE0RXwc+Yg98e3vpjbqKzxnMU16awHkSl0S83LGqGVz0Cjof6jVltfB1yqiDXMKSIj4Mb/l/fWicDWe0x8CUdbS0cUdbBNLTVkmMsxByp/IjU6VYyuwyR30A+pZ+IwpoCCVa2cN263JywwB3IwXfBP+mnOHYzTXSW3yBiKhfDQn/qxgtGf+6MlfmBo6VHcDQm6U8gnjqac+HMmDG/TlkQ8yH+Y1nuyCJttxzDVN5++pQpUkRkkUFWGCD3B7anW60Vl1nWot1Py01QiyhmOFj5hupPqpyNvTV7sPCtFRoslURVTe48o+Q/vrMHcIRVQzGZPbuCBeqG48PTxzQsjfW7ZWquWhm5eU4zsVdQvMvQlTonwJUV9n41p7bxPBHT3uFPDdubMdXA2AJEY9SGVffYg+bBbVL/AEzLDFWQeV6Zs4HQr6ahcV8N27i2zRiX91Ux5elqUHngfGD8wehXoRrN1Ocr3Da69vpMsagFc+um3QHYgEao3AHE1fDcajhPiYrFdaQ/upC3lqI8DDKT8XX59jvub6eUjOdXRw4zCce0qnDwFmvlXYX2p5Cami/yn4k/A/pjVmBxuDqucfoFoYq+kcfX6B/GRBuzJ9tcDfBG/wCGqdxT9LNqoYUMcnLUY81OieJKD7nZFHvlj7aqXxx3MR6MgmapNUQwqPGkC83wjufkO+su43uFltctfRV4jltVSvjOiHmlpmHVlUbg5wRnGN9Zbe/pGv8AdBKlO5oIJPiKuWlYehk649hge2gVDUyJL9YbzA5D852cHqN+utV0l1oy/A/eCXa+teByYaXjGW+W+a0yVUhrIGzA7KFeqjGwY46tjAYb9PkWr9WygEs4UdcZySPkP66CcT0a2+qAp5HAb9/RzL1Ue3uNwc/rpUNyW8qYp1EdyQczoueWYffX59x6/qXpqfIbHsfeC3Oblz7/ABO6ivVCRCmT2J3/ANP568o6+qirY6oOeZDuCchh3B9saamhEanxHRfbqfyHT8dRvrsKNyxR87erb/6fz03AT35MVbmB44Eu9ZTJcoaeqophT1cY56KY74+9G/qu2CPx9jK4Yrmq/HpSrUckb4npzgtDIR0B+6wGQfl66rPClzc1LUdRJyxzEFHJ/wAN+xz6Hpo9dqCepK3GgKwXWlHKM7CUA7xv7Z3B7H8dU8ts5Hf8wuu0MOepaYIYoT5V37sdyfmdN3ano6u3yU1YEaGQYIY4z8vfbbHTQ6y3X9s0hmh/4Z0bw6iFt5IZB1Ujt7HuNFqanijOT5mP2m3P562XFi8TvKmUh0dxJaK0+LVwozUUzrj6zGOo3+2Bvjv1HcCuO00j8rkjGw3ycfPt+GtM4ktVPcKXlYskkZ545UOGRhuCD2I1QKwSpO6TU4krBvhDhJV6c647Z6jsfYjQwYadsP17TlqG0ZXv3gsQSQs0saPJjzMqgk7dx7j9R+GiEdRTIBy5qmm3VY/hHfJOi1u4Uv11RTP/AMFAd8Hy/p1P5aNUnDqcIVcVz5fr9uz/AMWGj81MenjL6r94dR19dC261hwnAl69IGHr5MrVNwzdahfrFwhqKa0iQPUCLPkXoXCbFsbEgdhnfGDsPCfCdis9NHLbaeKQsoZJzhiwPQg9MH21JjCSxiSNlcEAqynII7Ee2oVnqk4cuC0lSeWx1cmImOwoZmPwn0ic9PuscdD5U+oUsdwjKs4GDJVwp5LfVpUwLzKvMUUdGU5aSL9Odfk3to1TiOaGOeNw8TqGUjuDqfWW9aiCSByVz0YDdGG4YfI4Og1gd6SvktlQnIruTGo6I/VlHsQQy+x9dUdfNTd7judHpOITSJTv11JakkSNGeNlVxlSe+n46Vxnm8oPQnRe1TxNTtRClkqe4KAHlPuTsNZooPE0VcwHBCSd9htnOg9fSS2u5i429WeNj54wNvMcsvyY+ZfRgR9rV4pLE7yeJWzHGdooz29z/bGi5oqU0b0ngJ4TLylQNb0qVPPRlvJz1K1TRmSihroZhJBMvMrIfXsfQ6d5l5GGcnG/roI31rh+7SWx3b6lVtlDjYMe/tzfo3sRolCrM4RFLMegAyTqtibDgSATsB+QryAZ7nrrtUwoUeY57aIQWmpkjZmcQkjygjmP9tTaGggijEsAYTrsWc5PuD7a6KiZoqQUbHJX07RVKckDjBB6/MDsffQ+zUcVgvQoK9UlgmbNPMy7Ix9ugz+h+Y1c42DjPQ9x6HUO922K50LwOAH6o3odEIoAxOlMciTQBjYabckOFzgaEcM3GSQva644rKfbJ+2o7+5Hf8D30cIB7DOoRLqciNRluY75XT2m+ntqFcLxQ0bmIymacDJhiHM4Hqeyj3bA99cBAnQMye6I6FHUMpGCCNiNZbxpQVPDl4jrqCBpaScnxVDAcoHseuOv5++vOMvpestn542rVaYf/VqIiWU/5n+Bfw5vnrIOJPpe4huVYv1Cip6OjEgZ43HiPMB95zv8sYxrfT12WnFYzBtTbXWuXM09uI5a3mS00xnIODLITHGp7jJGT+APzGm5LfPVjNzqnqR3iXyRf+0bn8SdVzh6901XTC7UBIgc4qoO8TeuP95Hy3u1NKksYcEFSNiOmtzW1bYaBiwMMiCqm300lG1I8MfgsOXkAwANRKQGkb6syjYdhjnHr8x30SqK+nLtHTI9VIDgiIZA+bfCPzz7ah1dLXVXKZZY6cKeZViHMQfdj1/AD561U/EqRPZ40liZD5o3GgtUk1NVM3L4jlcMp2FQg/k4/wB7E6NUzEZSVcMPiUHp7j213WUqTRFScZ3UjqD2I1uMOM+8ybiYzxhwFV11xFfYKikNJOCeSpkK8jZ3C+g/h7fLGlrRZYJYJ35K+SgkbBk5DhZPRt9LXRa44B/aZ7EPayr8HcO0PCllFFTfvJW8085Hmmfufl6amVkEVbGUq40lU7YbVdtvE8xwK798v3lGDo/RVlLWj9zOvqVOzD8NKrtNfUwOIVVqqr+AZV7zwYsivJa5eTP/AC36H5HVMuVDcKItHVQNEQcEkbHWyOSNgMbbe2m5KWGpiaGohSVDthhnW1fiBr9L8ylmiDcpMQRWLEDY9vbTzMIowNySdvn660G98BBmaa1v4bHrG2+dUa72y4W+fkrYHj3wDjy/ho+q+tkJXuCPXYpwwjMcwVcEjJ7+uu0GGzjBPXUeCPmw+Ns7e+nxMqE98Dze+iVJC5aY4BPE2PhkVlo+itJRBZ5aS4VQ8SNj/wAVNynoB2QY+e+3XVX+lHiKkv8AXo8FvpKR0VUCwJyhQM9T3J/QapMNZKXEkUjKy9N+mpNHXS01xjuTJHUSRyiYpKvMjEHPmHcH00MmnAcuTmXazpRxJdjsL3q6UlNUyT+FJIOcwQmWXl7lFG7H0GpfENm4UgslVNQVlx+uJVMkUEsKjlhHTnPdz6DRGu+km9VtTLU07QUFVUSl5pqaMJIfLygKfsgLnA9yT66q9XUPUgF8nBOMnc5Pc99Wp861s9KPact8tBjsytKksjMqqTjv6e2vbTTmql8VyqRxncnoPnq83K90lRaloorHbaaRaRabx44vORklnz3c9ObsCQMaqslNyoIohiIdAOv5euifxL2kjGJgtC1ndnMdmqJfAemo3aKN9mkA80g9D6D2/PUnhKzre7zS2mN0gMz4Mj7coG7H3O2w9dOU9dbKfh6egFtEtzqJB/xbybQRDflRfvE9Se2w0LRuV+YHlbPUdvlqtQawMiTcsqMr2cz6do6W3WCzRwIY6WipIuUFzjAHUk+p6n31kH0l8cPflkttsDR20NuTs05G4z6Lnt+fpqs3Di2oqeGv2XWVFbV1AlXwy837uOIDcY6sxPcnYDQ6hi5h4rYyw7dtX8N8FXTkvZy2Zrr/ABhrh5dXCyTSRJCmceduun0+PHXTajfUinjZ5QFG516ARETjmP0sQZySPLqYQMbbaUaBBhfx1IpacT82ZUjCjJLemmVNa1Jlp5TWahtVdtTodSPE7xtzI7KfUafqJIq+IJNSrJKSAGUb69o6KerqfApkMhJ9MDHqfQavHD9igtqiVys1SR8fZflpP4j4hSvCjJnpfBPCtSPU5wPiCeHeFkRUmuCBVGClOP5t/bVwjjC4C4AGwA6DXsajG430/GgLbDXlbrmsOWnsqqFrGBHKdMntqRV1NPbrfNXVTBYYULMfX2Huen46SeHDG0srKiKN2PQazP6UeLUq0Fvoyfq0Lc0h7yydh8h/vprmm0zaiwAdTmovWistKlxTdp7rd5qmZvNK3O4B2UfZQfIaHo4IGmUJz592Jy3z05jDemvaJWK1AWePsuLsSY4CNzg76chQs2M4HU64iUkHGpEZ5V5FBB6k/wAtTriZ8e8epYzLOzP8KfqdTDudcxRiONV7nqfXXumOnr2Ln5nmNfqPNswDwJ0Rtrljgbga9B1yxydbt1A1jNRMHQwSgSJ89x8jobPb2OZKcmRO4x5l/vqY65YnTkZ5QMdt9Idb4dXqTk8GPdF4tbpRg8iCVQL1666XC++itQkVUzPKvI5OSyDH6aH1FNLBkkc6dnXp/ppLZo30/BHE9Lp/EKtSMqefiNhQ2c9hrhmCrgAj1PrpM5APy00GycN01hC9xE6JBAK+XVZ4zqI6Sl5UXlkkG+DsR/8AOrFPIkUZdzgazXiivNZcHxnlB2Ht21m7YhNCbzzA5Y5JO++inC1Iaq7K7jMcA8Rs9M9h+f8ALQpzg6u3B9L9UtBqXXDS5lPyGyj/AH66DHqbnqNgNq8SNxpV+HClIrdR5v5n+g1V6PLzl8dOmRqTfqn6xWyPzZA8oPrvv+uurZTs7Rxjq2M6yc7jNM7VxNO+j22zcTXOrrq6WOCWUBmkjhVEDdB5VAAGPQaJ3201lpm8KpUchJEcq/A/uD/Q76M/Rzb2o7SjquDKc9d8Dpq8xUrVsaUc9ItZFKQvhEZ5jnbHfOhC+G46gJwxzMZ3BHb31yqO5IRSxwTt7AnVx4y4akpq2prKKnxTFywgRf8ABBO6+6jsfz1VJGYxchxyAkge/wDsa1BzMt8awo67/wBNE4qCX6jGxByw5h7Z1FtdIa64w05ziRxzf5ep/TOtLaip5oswqo5BsBqllgQiVwWEotLZKZ05rncYbcuVPNJG7uyk4JVVBzjrgkaAPM9HUnwCzxcxxzDGRnY47HV5utokkkZiC2Rvn01Wa2gZMqV5horT6nadwPMDu04dSrc5nlNUpOpdDg9weujNuqafwpI64ysqp+65ACecdAd+mM/pqstTPAfEiyMb7am2+uR1eOdB4jDC7kYOev5Z299ej0+tS4bX4M8zq9A9BLV8iWEz4CVFO5RkPMjA+YHsQexGsj+kqVqniCRXkaTwlCkk5PMdz/PWiCcQqzs2EUczZ6YGswuyz1P/ANLShBHXSStEPEUt5SM5UHIG4xkDO+M41n4owSsL8w3/AMdqJua09CC7dCETI3JbP5Z/qdG6IBElkzsg5QfkP/nQ2mwJD0CoN8e2/wDbRI5S2qCMM/X599IVnus4XMGsQQ0mdz3+Z1avonoRPdKyqY48OEIhP3mbP8l/XVSqCFTAPU60f6MKfwOHWqCuGqJmYH+EbD+R0w0emGou2dRJ4vrvwemNmM84hm52pTDI0sYBHRx0J0Lp3rbecSBp4wOv2h/fVr+skQ+E5DL6EaYNNDLCxiwSRuh0Tamo0T59vmJtPfpPEa9vv8Hv9JGslzilf6zE4IjUtnuDg42+eNR79cy1HFHI2RzFtvX/AGTobc7TLAivRc8MzbkDY4/qNQpY5ViRKyTxJe5OwGq6rxBb0KY5M7o/CTprhYDwJLppWdASCFCs2iFjovrc3hHfGOgySTnAAHXQmnJKHl6ABQTq/wD0XcsEk1ZA5FSjbFVyVUDrk9OugBp2uYIIxt1K1Dcwint1TaJ0iqqWSm51DhW+Ijtn0+Wi/BVwqKM15pwjvIihcgZ3bGxPz+Wil0raStnFTdphPyR+QSPgbk+nXrp3h6WmrJJobXFRJ4URlc8p2Ud9xvp1RpqqKsbefmecu1N1+oz5mFHQEJVFYtYYWeYNUiLlnAOVDrtkHoQcZ21XuI66lNvqKQTN45mXEfKcYAGST0+z/LRK21LXOVnWrR/BO68hAGfw0G4xlpgi0MYzPG3O7hcZyp/q2htWoShwR7Q3RubLkIPvPOG6D69w7LCWbDTsQw6KwAAJGhy2+SklYSsOdXKYHTPTV04Ep4KPg6GseMs9ROYTjbbJPX/s0EusXPdmjUZzUPgfJjpRqLD+FRB1GunpUat7Pcxrh6mUUl1qwNkKxL+Lr/QHRigrGSPklJZMbHuNc2WlZeAkn5kX63csglh0VD1/E6dtFsrbjKsFDTSVD5GQg6D1JOw0i/1GNcnMuPBEb/tKvqoonmEMAHLGMtjbJA79/fWo2AU8lAqvnJwVfpj+2sx+j2WqtLXqfKlo7gtPy82VY83KwOtSp2hqKfxqUBHPmaM7f7+er14mumI7E9nFVRF5JQamnLbNGnnQb9R3HuN/bWUfSVc0/wDGHEE0R5mt/DcpVgcqGcFR/wDbjWmUtwnjDeGwbLf4b5x+Y6ax76Y7taqKl4jnjopYqyqaGCackGNl51yMZyB5M82MEjrqxbI4ml7jbxCfDHDw4k+jSzJXTUtvt8FRNUVTSMRlQSo3J2JGcnONunbWZ8W37h7hziSpjs0jNDG3hipk/eNIB9xPLnGOrEL6E9NMy/SdWtwvTWy0xAPTQ4aqq+XEbFv+TH0B3+I5b0xrNahvErnqKmZ6molYs8kjElie5J1dEOPUIG+1gAJYLtxDW3ZJqlp6n96QoMsoeTl+YAC/JQPmdccNVJpKoDzmLJJUHBU+o/toPUyFYVZV3Gccp213aKoGpVpRhvfb8tGlQMAQF0IP2g6Spgp7fWwtR09U8yqFkkDAxYOTy4IG/Q5B/DQ8zmepgb6pSUgBEYWDodj5myT5j313emUhwCdlGND6M4khyhXMu3bOujOCBGlQGAYd4Qpqm4cRVNro6aWqlmUBIUTmLHJ/pn8tRb5ZZ6aVyqPiMkMrAhoz3Bz29tRqKokpr7PJCJfFCeQx5yDze2rrYLVcr9BLNOWhkQZzJuG+Zz/Q/hrI+gbpV7D5hBlEt9XWWOUTUwjlhqVInpn3inHfr399aHw1f6eppGqqaZnpxgTrMTzw42CzYyxAHwzKCyjqHXIAbiWwNBFGIVBeKXDoOhzjce+qtDHXUdxettspgqIidwNmHdWHce2qW1Bj6YTTcGGDNWuFvjrS08AzICAwkxzKW3UHlJXcbhlJVhupPQRaa2eHW00k7cuB0GhPCnEKVv7uJGgqolbxKMKGZATlmiDEB0J3aJiATuCrebVtWsWupaZPFj8OItMvJkhhsGYEgMyjGCGAdDs4HU8rvbIVjMNRpQAXQfpB1VAtNS1FVCihRLyYxkseuh1VyVibNtsQFOi19r4KeFrd4LkmQy8y4CnbVbghkXLU+ylfNzaMWteTENt7k7T1CooylidHHMqT9emARqNHUTUoCu3PH0Geh/HUq3QNPbayOWRwDytk+2dSY6GD6updS5OPNnIOu2MB9UwUN2sNfR7eI6G5fXnpVmaIBgrkrkd8MNwd9jra7nxVbr3wLXBJ2khMS4dhl4nyCFlHbcbP8J9QeuB2mExT4WRCGVhg7Ed/6actl0qqKcrDUPEzqUJHwup6qR0IPodA2AhQyxtptVwUb3hyx22uqrNTUqUsrS09xZYwEJ51Ykcw9R+7GrLNa6mgqZrfcqdI8BZCJEyDg5H4baE2S7Gi4YijpK6moqyKvWT4GWaMb9M5Vk3JI2I9wdXjiC2X6uvkM9weGupqyn8KCrgA8NiwIXb7J82f66FZmcA+041OM4mXUxeaCnCRlmI5cD+En+mofEK+LT0UrOE8zRMfbIb/AO6OtFvPDMtBwXTGooUiraSp5JCpGSjpzA5HXzfz1SeNrVPR2usgqIjFNDLHKM91YMpIPcHmXVkG4CYvWyyr3an8EFCecKeXPp6HQ63yTK7RySZVzyrncHII/njRyWXxIy4wVmQA++q9ebfNba2IK5aOdBKvqNyMfgVOjVPq5gpTIyI+lwhuSR0ta6RzIOSKpYnyhdgr46r77lcdxtry6x1FJURCbmUFBzAnYkdDtsRjBB6HOg1wIp66UMpCmXmXA9dFaO4Q1FnajuGXigf9zKoy8OfQd1z1X3yN+ullIGds30+p52vJKVa8iPEAXU5U++u7/TrPcWkj3jnRZR6AEaDM8dE5AlWZR2jOVPvnRCtrY62iDU4eOOKXlWMtkhD0ycDO+saxwYYYOliSCTkH709j2/109w6JYb/G0hJjnDRsg9G6fkQD+GpkgialhQRIrqpyyjdjknLH17bdtDKiWVGjMWVKHI5fUdNWJ4mOSDxI19o4oLjKmcLzkqB6E5Ghd1j5YkljQDm25vfVy4rpIqx4bhCvhrLGrEH1Izgfy/DXFm4Vud6g+rWu3T1MhO3kPf2Hb565Y6qeTCdPuOMSptC0/h1SPJHJ5XRo8hkbbcEdMEav3A/EiVdPDZ+JKVnTPNFgcocDGXi9Dj4kHzGwwh6xcD8RcFXi2VN2oo456gyPSBmDBXjwxDAbbgnA31ZeOLZbeKKJakQCCGVuYeCcNSVK/EUI6dmHsw0vvsB6jFbNpKtLNYktdNSJJZ4IEhkQESIN3HrnrqU/M4cMVdWBBDHsdZTwhfLnYLv+xryOeRzmN0GErF++g7SD7Sd+q5+HW88DWW33WjFxmqIamCT4VQ5ZPn23Bzt6gg67S+eJx6sn09Sj8Ac9LcL/AGCbzGdPrUGe8kexx81IOpkjjHvqwfSLYYuH7jbuJLXHiOmkHiIu5Zd+YE98qSPw0BuVOUuDwQEyhmzFyjJdTupHzBB/HRDEZzBmQoNvxI7NrlYzM3hKhkdvhVRkk/LVisvCVZVnnr800efgAy7f0Grna7JQ26LFNCEY/Ex3ZvmdVJ+JZKmYQd9H9b4ts+pupWWmJVlxjG+/456/PVvgdtUpOW1cYO/ww1qByMbcw2b++rmgIHMvTXEML0xwNp9pInQT07wv8LqVP46DcNh6JZrc7s7QHZT1I9R+YP46MglI2kY+UDJ9dUHi/i2jt1xWro5Y3qKdC1RArgytGP4eg/HfptrrNjma2ELhjC/HfD9uvixrUzfVqjl/4WpUeeGUZIwOpDDIK98DuARTYePrxb6Wr4euFF4nEFCAFhMhQVSHPLIp6tkDIGxO46gjWdce/Sjcr3UL9Up46BACqTK2Zzg5ALdv+3WcXKWukqkucVVMJxho6h3JI/hJJ3Htntkb6g0dluWHAmR1qA4E0C8cb8Q36tNJV1bUdPISBDTfu15u2T1b8Tqv8VQsxguZCrzYhqC3Zh0P4j+WocV1F+p2qYFEN4iOaiPG8h686+p6nb4tyNwwBWkmjuaS0tUwMVwi5SxPwSDofno2lEC5QYxFeotcPhznMrZrYozyx+dvU9vw6a4aqnlcl5GAOx31HFLJSzTU9V+7eFyhz1JB7DXv1mKMEQqWb1O5/sNNK9rDJ5MBYkHEOR0j3CxyUh3mp8z0h7kf8xPfI3HuNVCUxicLTuyTdYZehVx029D0/HRu2XGop6xKvmPPGwYf2OmeI7fDFcGnpyFpp1FRTn0B6rj2OR+WuFO1bgGaV2EcryRGaScXSJ+ceHVR48aHO3+Yex/vriSmMW8hWEe/X8uuolXIytDW0Q5JAciQdm7g74wfTTodLhAZ4iyMuBNFn4D/AFU9jrtDsh2+3sZL1DAv7/Ec+vRxDlgQs/3m3P5dB+ur3w1XvXW9J5D/AMTCAs4+8o2Df0OqDHSsqc78scY6u5wP9dTLTfFttastLHJOM8shOyEHYjHfOr3OtZzu9Uz0+9vbiXK6Q1NBclvds5PFKBJ4ScLUIOgJ7MN8H5DvsftNwN2o0qrcV8F9udz5lPcFR0I9zoZRSQ1dMqRtmCZOeF87genzHT8BrwpU2yV79QRmVSeW6UkY/wATH/OQffAwSO49wc8ckf1E6PcMrIYbT37SxJb0kPNMzTMO7nI/AdBoRxLaOfwqilkNNVQOJIJlH+G46HHcHoR3/lYbdUwVlJHV0sqzQSqGR1OxB13NGsgKsMg9fcajIHWdB2mc8K3Y3WmeGpiWnuNMFFTADkDPR0PdG7H5g7jRpYQQQQMHbfVTWhnkqgaKZYLpTAvRStssin4oX9UbGfYjI1aOHrjDd6FpkjeCohfwqqnk+OCQdVb+YPQjcaRuCjFTDgQwyIGoieFq9aWXIsdS+IJCdqORj/hn0jYnyn7JOOmNWapooquGSmki8VJEKuhGQQeuvKyihq6WSmnjSSKRSro4yGHoR6aGcPVU1mr4bJcZpGppTy26qfctjrA5++o+E/aX3B1kTLbSeRDPBtxkt1UnD11kLxkctvqXO7Df9yxP2gBlSeoBHVfNY+ILBLWQitpEZZYgMtjHMBuCPdT+hYemg14tkRVfEUTRMAwKnBO+dj2IIBB7EDVy4QvRrohRVUgapROZJMYE8fTmx2YdGHY+xGuVkBpumH4M64ep6e5W9Kmdmdvhkj6BWHUH10djhjiQJGioo6ADAGq/LmxXrxxtQ1Z5ZPRG7H+nyPtqxruNtaBQOoQgxxOSMa81321yRjUwJeCuJrTHdrc0OAZlBMZ/p+OB+IB7ajcFVcc1E9LIix1lOeWbbBfrhv559CDo4JBvgEj11XOI6WW31sd+oASynE8Y+0p6/nt+OD666MHiUIwd0tGmnXlbxVBJ6MPUf31xb6qGto46qBuaKRQyn+nz1I1JccxpsD99H5gfiA7j++nBuNNSyRU0bSOwjjG7sThV9z6aGXu/0trg+sVEiJTZAaaRuRE9Pcg+wOqlgBzJiM8VW+VlF2oMrW0o5hgfGB29+/8AvGm4eLKN7SKxo2jdV/fI7BFiP8Tk8oH4kkdtZlxt9M1tgZ6e0h7lMPttlIF/7erfjqnUV2j49sVZZbkEprof3sJQcquQTggD0yQR6E4zsBVS1uQsxe1aj3Lbxz9M1vp2emopXuMw28GkJjiH+aTZm/DlHz1kHEPGHFPEKmCSpFFQsc/VaYeGnzOOp9zk++hjUz0VTJS1EAimgbkkQ9iP99fcaJJTlIhJU8lGjbqZQeZvkg8x+eMe+rrpmHqaA2a5mbaggOOjMD4cglhnmzqVHSSvEZEVUiGxmkYKgPzPU+wydOVtfRQeWCn55F+F6hQxz7RjYfiToDca2trJQZZHJGwLeYgew6AfLT7w7Usq+WoiXV15JdzD1n4jh4ZrxUQTSVSPhZ0xyRumd8Z8xI6g4GDrV7FUUdcIJkq5Ki1VShoFzhFJ6qwHvtg7A9txr5+en5ssSxY9266tX0bX+SzVrW6pWWW3VJ/eKoyYW/6gHt39tH6vw57azYTzMNJ4gq2CvHE+jqSONIlSNFVVGAANhrqaNSnQemq7QX2OlhSCpMk7uB4DRKW8YYzsenTucfzxNR7rXZzihhP3cNKfx+Efhn5688MocT0HYzOLr4EMaySTJC6/4ZJ+L2x1P4a5t1UlRAGXmA6YYEFT6EHpp+K1QQOZQrNKdjI5LOfxO/4aamp2jkM0KgsNmU9HH99aqx7EqRmdS06u3mQNj1GlrqCoR4w27fLqPY6WiBevvMthnzbFMQeVT17akw1DxtzCQqQdsdc6BUVdGw5g+WPUdCNSoahJCHJHoAO2meNo5nm1HMt1s4kqom/4pfHj+fmGrnZbhb7gnNTyjxP+m+zayiCV2J7+51KE7xg8khV/UHppfqPDqbhvXgxppfErajtbkTXjsflpispKWuiaKpgSVSNwwzqg2fi24UpWGpxVRdBzfEPkdXW13q21ygRTKsnXw32Of66QNpr6SSep6KvU03DHvKrf+AkdHktT+G+P8Jun4aoNwttbb5zDVU7xtnAONjrdS5xg7jTFVRU1XHyTwrIPVhvrerxBiQDyJjboF5KcTDYVWJTnt6dCderN2bA9xq+8ScDI+Zba/hsOiHpqmT2uuopitTTshB2JGQdN6tSlzbaziKbNM9OS8ajT7RAAPpr11lAV1XCscDOpdvjWWdS+CqHmILY5h6aO8ZcQtxXdYag2+joaemhWnggpY+Ucq9M+vf5DRN1hQ7BMa1DDc0qzYbIyAe3vqXLa7jT2iG6TUc8dDUOY4ahkISRh1Cnvj+mopwCX5fLnAx6amVlyuN0gpqKoq5paSjUrBCz+WId8DtoZ3YMNomiKpBJkCSGKQcxB5jsGHU/PUKtglhDOBzr7dfy0WwpY8pAXou2uOTflbpp1pEKjce4DcQeoCtsDVM/Oy4UeujcYC4VRt0AA12EVASoA/DXqDIxphu3QQDAxO0Xm74xohRxmJTIdmYYHtqPRwF2LH4V3+ep6hmfod9b07UBsfoRdrHstPkVDkztB6nHrojZbLU3OQkDwqcdXI/l6nRSxcNFws9xBVOqxd2+foNW2KNUQIiqqqNgBgDSbxHxdn9KdRz4R4ClA32ctI9tt9NRQiGmjCjux3ZvcnU0IBrxFOnkU688zbjkz1SqFGBPIgS22ua2upbdD4k5yxHlQfEToZer7DRloKYrJP39F1VKmqkqZWkkkZnbbJO+jdJoHvOT1AtX4hXphknmPcTcSzzhgzcg3EcIOwPqdZ7WS/WqjzEskZO/3mzudS73VYkcRMeZiVQ56/wAX+/bQ6ECMBRr0en0qULhZ5y/V2XjLcRxcc2ddAZJGulwTrpdicaJzxzBu+Z3SEEksuVXc+59NSoWQSK0hHMfh36nXAicIsSDLd8d20JubGWqJHMAmydiNSs5fmZajPl4ljV8jc67U41Xaa4zw4WUeKg7jqP76LUtZDULmOQH27jTRXDTzNulZOexJeep0zI+E9zpF8nlzqO0nM57jtqlrYHEzROZ0DvnXeN9NA504vTQsuZ6D116jFen4++vAM64qJY6eMvK4VR+Z+WquVx6uparfvGzueVFJDMC8YEUmOn2T/bQWrmWHmQAFgcbbjSr7jJOCkeUjz07n56j0lJUVcnhxLzZ6415jVtSGzX1PcaBNQa8XdwNxFWCKibLYZtuvbvqiOTIzyN1Jzqx8dyiO5SUSnIhPIT6kfF+u34arOSEx3Ol1tgj/AElJEdttKa24xUy/bbzewHX9M6unENUtFavDj8pYeUDsBkL/AF/LQzgGiJ8atfYn91GfTux/l+uonGVaJ6sorZVB2/T9NY/RXn5h2Mv+UAoPEmAOcevrq38G0LVNxXy7bAf7+WgXDNrq7pWLTUUayTMGYBpFQcqgsTliB0B760j6P6NoUEzJuBsD6nWEx1Fm0TS7F4MCwLMxWEMqtyjLBc7kA99G1q2WI+HL4YDeXJ82NV+1tFLMI2cRgqSXIJAIBIGB6nbROBImiyWDSY6++sXVRFu/MMQSpXxkTERKh6d2+Z0A4q4Tt9dAJ7Wn1Wq5SWRj5Jjk7j7u2B886kUtO6c8hqSrZGFxnIOf5Y/XTtUKlAAJudRkD8zt+p/PVa0we5N8zSnertNe6vCYpY9ikg3P+nuNW6x3uCqCxlvDlxuhO/4eun7tRxXCjYVDRiRDyoM/vAcdvb56pldb6mgcFwQmfLIvTP8AQ6eJoKdTSAeG+Yku8Ru095PazSopInIZkUsu4yM7++g16omqKh5iFLNuSqhR+Q20Cs1/khIjrCzpsA4G4+frq10lZHLGro6OjDYg50i1Oku0jerr5jnTaunVrlO/iU2tt7IGwAM6EVNDnLgYOtGrqOKdMrjJ1XrpQOHdyOu+w21arUY4nbKZnvE1zlpLJVRSZLuvhI/ffY/pnWfU+WdcnbO+rt9KEbx01EOaII8jkjnHNlQMbdQPMd++/pqoxxMsAbpzjA/HbRtlzWgbj1CPD9OlKnaMZkumAKdN3IH5nJ/QamXFsRxoT2zpi3pzTp6DLfnsP0B11Wtz1DHsNj8tVXgiHvnEgVh7egx/v89bJw7TrQ2KjpeXDRwrke5GT+p1j9tRam600MhHLJMob2Gd/wBM61KaumqGb6r5EAJ8Q/0HfTrwu2uoPa5nlf8AyOiy/wAuhPzku53CGnzztljsqruT+GhZlrqqdfM0Khhyoh3PzI/kNPWq0TVMvjMSFJ88r7k4/wB9tWOjgpqPHgqXcdXPX8PTXbNbbqya6hxAqfD9PoEFlrc/51OoPrDCL64iF48cvYnG++qfc3D3KVhjZzgatdTUFVeZt+UFvy1TAcysepP66Bv0B0pG45JjDR+KfjA20YUf3Mm0SfukB2JJJ76J2eviiZ6eGblmjJ5gGIO/8xqBAAGGSRhdxpyqsNw5w0kJSNnyso7b+vbXNPq/w927uc1mk/FVbM4liFS0keZDzbAfltq7/RJTTftKqqGixBJRyKpceVsFcj31mNHJPRRVUcxNUiKCJBsykkdR31qtjrHt1otCwSJlqEuwPQiR2P8ALGnVuvS6rbX2Z5zT+G2abUbrOhDNvhtdIZnpaf6vJKuHLHK/9vpqm8YJT/XJJYJOd2LBz6Y5QBqxVEvNJBS+IoPkj5Se5GqtdwDLK4wQ0pI9wT/ppZq8jTsSe440RH4hFA6zNQ4XskdXwZQx2+q8ekSrLCeSPkYj/Jk75YjUGutFPbOKnnQsyUlDNVyFzvzYbB9BuRo/9HkqQcKUUfIIw4MvKvbmOcD20Gu1RUS3PiOsSMMkRpKOMFcqxeUZBztvjp76RaqwkBAeo8p2g7vcw/8ARzwNBceDbQbpK/hQtLIYUOOcsQBk+mF1pFJbaK3UYp6Gnip4l+yi4GlYsR2inyuGdecj3Yk/10xxHc6agt83jOyymJiiIhdjhTvgdv00IAqjIjhEVUyZm3DEbfsFZcczVl5nmb3ClyP6at1zvNFbIzE7NNPHGGaKIjKD1diQqD3YjWXvxDHQW6kpovNJGHZxESpJYk+Zj069F/MayT6S+Kbxd73PRTVQioIivJSw+SIHAOSPtHPdsnVK1NjECBBvLGZo/G/0uxQg01ukFTMpP7mmkIhU9ueXAZ/8qYX+I6xviS4y3G4vWVLK00xMkhAwOZiTsOw9tDQ3nznJztpyWmFTLUv9aggNPB4gErYMpBUci+rb5+QOjUo2CZNZnmeU8wNPgHA9NRZT++Vi4x+mu4ceCxAydRZSxlH9tbY9pgjEsYUqZW8JI0wMpk/mdd09JKYo5xllK5J9DqK7AVOMfCi7atfDlNJUUqBfCUAAEySBRucdzv8AhqlrbX4mqHIOZn1wm5FkAb7PX01FpJedqc8zHMnU6KVFteoZgsiENGzNgElcZ2O3U4/voRSowip5FVuVZMEnsT0/lrYYCmb1MScCa/8AQ3baV7deq92ZnmnFJPExBjePAdcj1yG3G+rdWilhKmIbdAi9FPpqsfQ1JGtk4m8ZC0MVbSSuAcHBEynB7dtF7pLTio8WiaVYHxgSMCR67j30Aib2OTMNdYa34ErfEtXC0zvJyRgFGHQfnjQ6ps0M9VI0IVZSv4N89TeJ0opID4VNMjrFiUtLkSYPUbbbH3Go9oqnFbTlkJWROp7aZCjBVkgdGsPKvKVe7ZLDIssbPT1MLBldNmU77g6McM8SmoqVpK0rT3IsrBubw46pgDhlYf4cvYMOvQhhldW26W2GuiCMAH6K3pvqj8U2Aw26leSPAZ3XI7kb7fmNtAXhSxHvmOqL/Y9S+RyQ18ZhkQCo5vDXmQIec/YK9Ef+EHlfqhO6iE9PPFMoMRcb4K/Dqn2TiGWklShvkoAKeHBXOvMpQ/YmX7SdN+oxnIOCNR4SvkFDdIay40cFX4A8R46l+ZeXGzs/249xiXqvSQY85zFzVDBmOq0C3etODIFFAzUcrMjqkkZUNjADDtnodWDgbg+u4mp6uOl5Y2gi8QhmxzHsB89T+JL7WX2po4amKCmjhJBjiQLmQ45nYDu3X09NBqS8T2+njWjmanlMISUo5AbG2MfgdXZmZFMSWKK3w0FR0ktNVDOWUSYz3wRjfUarZoamoMQAcnOMZVt/0OpMlSwl8R3EhJDKV6bHUW9Ax1bNE27qMoe/TprZASnMyGJJpbtTVVfTSJEFHJGj4J+IDBP49dbDwd9ItMFW11y09PUqQFeQhaeo9Of/AKbfxYx66wCOoVEDuAJFfqO+/fRa6VjGvRZOYxSIpU9x1H4jbXLNP6fRDNJqin1TY7RdqSqtvElnqqmSKsidXghm8zryHITuCOwI2xjVg4pscV++jnnkiBqPqHkk75UAkfmusP4TvZtFzkmkqq1aWemaANAAWiDd+VviX+HqNyN9fQv0WXGmvPAlHFIxLiIqwYEZ23xnqNzoSsYjOsBzg+4nz3HbwvDkjKPPSVARv8pyP5oPz0L4kTNBbq1t1inMbg/dOGH/AN3q+GxV0MXFFOKdnp4EYc43wy8p3/8A4Tfnqk3KBq3hevjA80SpMu3TlfBP5OT+GiR6otavZwJVOIKYpJ4irzIBytv6EgHQukdmneFfNHMhAJ2IOM7/AIjVspcTrDM+4dVJHz6/rnUC+2hbfxVJDSg+A4EkX+UgMB+AOPw1sLQrDMwVMnIlcpJvKCxyOmO+2jFqVZzNCnlEkZC/5h01BqaDw6yQKyopfOG6jPT5/hqdRRS0bxTiF0TmGXcf0HTWD2Kr4jBEJTMdtzoYwJvKRj4up+Wjtt4dud3ObfRssfQzyDCj8Ttpzg6noP8Ax3HTXGBJY5gwjVjtzkHk/DO2tbSq8SiTkVY4wMBFGAPw0NfaVO0TSutQcyl0fDCWpaKnq5VrfDbxyCPL5W5mXfrtzD8dfUFgprelrgkt9LBTwyxhwsSBRgjPbWBXSVUijnJBMUgbHqM7j8da99Etw+s8JR0rvzSUTtASepUE8rfiMHWdT7iCYdpSAxEb+le3QVNipa6VRi31sUzMR8KMfDc/IK5b/t1ntt4dqHvVVa0eKngqcZDdIp0z0HcMvN+K62O/00Fxs9Zbp94qmF4n+TAg/wA9ZX9ZqWorVeyAKh1EVUewqoW5H/DmQ/gD66tYoJl9SvIaE5vox4YrrXNR3YTVxkGUl5uQwN2ePG4Ydjvqg2i4X/6NOK1tF1lNTDUMfqdYFIjr1zkqQPhnHUr9rquWJEmzRTieJJ4STHKodc9cEZGoXEnDdBxLZ57TeaVZqOYDIJwynsynqGHYjWZQY9M1RsDE9rLjTcS8F1b23lqeeIused1cDI6e34HOufo/SiqLHFLDEqtEBFnl83KAOUZ6nYgfMHWQLNxN9F3FMVLWztW0lS/JR1rbJXL18KTss4336P1Hmzz6J9Gt1gmqpmpHJoqp38FT/wAvcsIyOzL5wR8tXR88GUsXDhpoQAAwBjTMsgAIGo1wuVLRIrVU6RBtkDHdj6AdT+GqNxT9I9qtswpo6hQ59MM/5Zwv47+2rFviR7FQZMMcb1EFNSwVkksaSwy86KT5nX7WB3Gq/dPpgttvpPqo5zVxjlMUWHk26FmPlTIwftHfoNZhxnxPVV9whqKWpYQZHjRjJ8Qg5HMx3YEbY6DGw1VuK4/q19jqwwEdTGGDepG23z2P5aIq0rMAW4i/8YASyS83j6TuILg0iwzmkp3zlFcl2H8Tnf8ALA9tVaKvlpq2OvDkAMSeY/Ep+Ie+RoI1YBgRjnPr1/0020kkuQ7kg+/XTWrSVqPSIA+oZ29ZkjiJUo6iaCJedWxLC/XKncY+XTUKmP12llCsRMv7wDOxU9R+B/nqfWRGqsCyNkTW9uU7bmFjtt7HQa13CGgu8Enhc8Svls75U7N+mqKAn6TVcsOJGaGopp1q6STwZIz5ZCSB7g+o9h8xvqy2q6/tWld6VViuEbBp4cjOevMP9OvXrzAd3WyvXSVb0ZHiROWEan/EQ7gg+uO2qp9XqKWdaulk+ryxnyucjP8ACR1I6dOnXqNdtQP/AFE4Px8y1VgsXy2/v8S0cWxGqgpr4o5TIBDVqvaQdD+I0LSIKoZj4aEZyep+Q76sHDNwpL9DNTPiEyoVqYO6P2cflnb0+YWuVVLUQVs9LVsRNE5Vs9/f5HV9JaGOFmGopKD1RxaiJGKxJzt95gDj+g/XU8c1zsM9JL5qilY1EG+7J/zE/QNodHT8i87sqJ95th+HrqfaXmNdG1upnnlUjBZdj+HvrW96k7OTK0K56GBBNPDyK8crBIZBzKx9fYd9NRpN9cRrTT1D1KnHMwOGHdSo6g6vtFwPT1Nxmq6uaQxRyApB3UEZAJ9iGH/adW2zUlPTwvTRQxRtEcZAGWU9CT39Pw0BfqmcbehD6aVT1dmZ5w1w1T36adq6snimp3xPRyD95Gf7eh+XsTdYOHbZDQyUcdIgikXlk+8w+fr31xxFYqiWoju9okEF1px5GOyTp/039vQ9s+hOpvDt1gvVC0qo0FTC3h1NM+zROOoI9PfQq2EdzZ0BGRKbbGltVykslQTkPzQMfvdvwYfrq3W2oVZUmzhZPJKOmDnY/gf0Ohn0h2szUSXGJT41Ns5G2Uz1/A7/AInTFhrhVUYnY5JISdfRuzfI/wA86eaewOufnv8AOL8bG2n9IQqEbhatkr6dC1lnfmq4VGTSsf8AmqPuH7QHQ7/K0xskkSyRuHRgGVgcgg9DqFbpRPTGOTBZRyvkZyu+CfXI2/A6D07HharWFyTYaiTlic//AFKQnZD/AOmex7Hb0zzBqP2hAO8feG6yNxyyxEiSJudD7jtolV0dRUrDxVYY1NwROSpps4WrQdYyezjco3bODsdmXUMuRv6e+pPC9WtHcWo5iBT1Zxv9l+359Py9NCa6jem9faaad9rbTDNlrKS8W1K+jcmNyQVYYZGBwVYdVYHYjTV4tdLX0klJWRloJcc2DgqwOVcHswPQjpt6ajXe31tkucl+tUL1EcgH7Ro0HmnUDHioP+qo/wDcNuoGT1CI7pTRT28mqinTmQxjIYH+X49NJwecQ8Y9oI4ZulSkr8N32Xmq41L0tSRgVMY+2PRhsHX3BGx0Sp/Fp6zw1Zo/PzxyqN4JfU/wsNj2xnRSXgf9pUiLX1L008TeJTyQkeJFIM4fPy2I6EZB66K8PTR1FLU2S408NLcadcVEaLhZkOyzJnqrY9ypyD7wLjuXWs9whC37Wt8lBcIkiq0UeKg3UE9GX1U7/qD0OuOF6yQLJaasn6zS7KSd3ToD746H8D30Pt7SzBqIyCO50BPgO/8AzE22Pqp2/Q9Rru5s86R3qiiMdXSNyzxMdx6qfbHf0wew1qs3BB5EtOvCMgjTFuq4a6ijq4DmOQZGeoPcH3B20/q00Eb5MDHNtpPGkkbRuoKMMMD3Gm62upqNAZ3wT8KKCzN8lG51QONfpOtNjDRy1aQS9oY8TVDf9oPKv4kn21mXVZ3HzDNFUf8Ahq9mgqC5oKrLxSdkbPf57A++D3OneIuNrRZ4DJWVkNIuMhpzhm/yxjzH8cawyt+k+53O6xOLUq20P+9Mzl53GCM56L1OwwP00O4vpaKhva8SqWqqG4KCjY5gku/c/DnGfnzdNs9ZbHUMOIIdUlZIHOJer99KVXXI62Wj5YiMGruGAoHqsf8Af89ZVxHcrndpWFTc6quVfKruxCgegB7amPVLcfLFTyysoz4anCr7knoPc6iT1FJDGVnnSXG5hpSOX/ukO35Bvw12vTgfVALdba/08CB4aINIEVHlmP2FBJP5ddTY1a2VKVE9YtLUwsGSOLDyjHqAeVf+4g+x1Dr77II3ipglLCwwRDleb/M5PM3549tBGeeVshQV9PhGPTRioe14ge8ZyTmaXd6heJbA/EtkjjF3pAErYkCmRlHdSeh6kEb9V+6NV6zcJcTX6hnuFFRTSwoOaV1O52zuTuTpz6P6me11LzwSo4G5hIwHU9QT/vBwdahw9xCnC1Yl0pA8torDho1UkqxPwEAdc9PQ7bAjVzjGZ1W8wzK6zga+UNnju9VbZY6GU4SUEMCffBJH46Bm3SSK7woAqfG7EKi/NjsPxOt04h46tlBNU0r4orHXDM1HIEkqlYg5MaZKrk4O5PyzrDOIKsVlwlaiac0qsfBNRgsB28o8q/pqi2FGyJLEQ8bsyJM1BTKWkmNUw7R+SL8WIyfwA+eh9Xc5p42pqdRHAeqxgoh+fdvxzryajkZ+d8v6k7688FVI3yGGNeh0N34oYdoq1J/D/Qsu30XcTunh8P3SXkQNmiqCceG2fgJ9D29D7Z1uFirRUIYpRyTx7OuMfiNfMZtzxKrVkiUadR4mec/JB5vxIA99aTwFxabmhtwqvDutMh+rSSqM1CAfaUHqPTO49xrDxDSpndVz8w3w7U2EbbePibJM8UaF3ZVUDcscAaD1FwE2RQQSVH8fwxj/ALj1/wC0HUeyRRXCJaiqkapmU+YSnPI3sOg+eNG/AXGANJlJ943MrMkN0MrSJUxxl9yqR7D8T1+elo88A5umlrTdKT5IruHJlRpaSXxF67Hf89DY5q6kdYpkIIONxjVypohCgVXIx8TjfB+X9NNTvTzlo6mIOPvEbjTCnU+Z2Irs0gHXEF0l0j8IDmGe2evz0/FVK2cHI7++oVbw+kxZ7fPlv+m3bQyL9oUDstQjcq9M9D+OtnzawCzBa/KHqEt0J51B6adbxA4K9V7A4I1X4LyjDkYhSOudPG5SzuKelUvI/Qj+ZPYao4GfLaXr59YlutvGtVQMsUn/ABsYPLyMfN8geur1bL/RV8SBGNPMw3jlwDn0B6HWWWyjjo18eQiSpboxGy/L01OpoZCv1mqfw4AcB8bsfRB3P6DuRpZrdLUAAgwfmN9FfaPrOZqyZOc/6aZraSCphMM0SuMYOR0GoHBVPdp4xLUE09v5f3MUg5pH9Gyeg/n2HfR6ooplbCqWX1Gk7saDweY6WrzFyV4lBu/BqkNJQkgH7B1W2tdy5/qTQBAoZmkZgoCgEtkn/wCT0HvrRUnyruB00RpY7cbPVU1RQwTSy45ZpDvGAcnGiafELFGG5i+7w5DyvEwWaJ4yzuMoDsw1O4YslTfbslvpBCrNlnklkEaKo6ksdhjVl4ws9I03h0DspXzPn19NVNzNRsUwQOmR316DRE3pnPMS3qKmwRHrhTwxzTeHypHGxHlfnG2w83f599DxnmBJJ9NOyVHjKqgBVzuB3OuABnAGnlFZUcxdbYCeJ6yHTkETMwUAb6cpomdsAZ1YeHbBUXCXlhjIUHzSEbD21yy9ahkztVBsOBINvoZamVYKdGdj0Ud/nq/cP8NQ0CipqQJKjGw7L8v76N2axUlop+WNQ0p+Jz1J1IlydhpHq/EXvO0dRxovDa6PVjkyGyZY+mnI0B12q99M11XT0cJkmOD2UHc6AALdRmcKMxyUxxRtJI4RVGSSemqtfeIi6vDSMY4hsXPxN/bQ7iC9PUEq2eXPljU9PnquvI8jFj10/wDDvB2sw9nU8v4t/wCQJps11ctJpqTIWwD1z89D66YQqUEoJYHJz0H+9vz107cqlubAHXQK7zNI4hAPM+7b9F7DXonRal2IJ5TS2W6u03WnIEis7TztMw8vRPlrtQe2NeR7Lg6eRckDWJ4jMEme4I7nUikQ85kI2Xp7nXsaZITG51JCjAiQjOcf66yJzwJoBj1HqO0OUYTdwcJn9TqTURUVaCKmII5/5iDfTYAUBR2GNegHTBdKu0bu4hs8SsFpK/T8QVcbDURL4kGKiIb5Xdvy0HeN4jzBmVx3Gx1cI3kiYFSR/LTdZDS1v+PGI5ANnXWb1vWOOf5hlGqov4+k/tKp+1qilQfWEMin7SjzDU2huFPVDMUoJI6d9M3Szzq5eP8AfRjoV6/loJJS4k54yUkXuNiNKP8A1BvMIPUY2+FVlMjuW+M4BORpxDnc6rdHc6qIrHMnjD7y9R+Gp1TXPICqeRPXuf7aKOsQLuif/wBOtL7ZNrLikAKReeX9B/v00EmmlmkLSMXJ/wB40/BSvUMIoELsfToNXThnhAKVqK70BC40k12vyPUf0novDfCxWcqOfmVqw8OVdwlDNGUjG+dWm8pRcJ8LVVwAQzxpiInvIdl/Xf5A6t0MENND4cSBFA6DWN//AHwN75qinskD+WAeLMAersPKD8l3/wC/Xn/NfUWBR1PUJStS595k1dM9RVPK7FmZskk9dMcjSSqiAlmPKB6k6R6HtozwXR/WLoaiQEpTDPsWPT+p1s2WYCE1rsUmWkRxWqxBMgBE5C3qcEsf5/nrP6uZqiodyN3bOP5DVt44qgkSUanHYjP4n+g/DVRolMk5Y9BvqtrZOJogwMmGLFTmSpjiA8o661vh2P6tSABxHhdyTufbVE4IoA8nilc5O2fQa0BFAAAG41VRnmKdW+44hqOSOSRfqqNTRBFV/MXLHHmP4nO3bbUmVqqjnaKZF549mCMGA6dxt31DpUjS2mq+sRhxKIxDvzkEElvTlHTc99PsOZ2TKll2bBBHX1/DXdnzF7OQeJLWsVwDhxtvtro1zMhXnB9NMtJSpKUgeRo2VMFwAc8o5unbOce2m6lVik+JW6fD8gf9/LXQonQxMYqqmQSAyKcjuvUaYaueWBoqiIOmcY74+WnJXRjkgq3TI9NRzEPiyGBGxGtksKH0zK+sOu0wVJQsYXmg8yg7pnzDTduraiilLRNgZ8yHodT5KOaRXlp45CI15mZBnlHTJ9tDps7mRRkfaX+o02r1KXrttETWaO2g76TLdaLvBWHl5ikv3GP8vXU2pCvG3MNztrP1cqQQcHsRonDxK1HSytXZkSKNmDjrsMgH16aU63wjYPMpPHxG2g8X8wiq4YPzMu+kOoWq4wrhHgxwN4K9/h2P650EgB5sHfBJHz6D9ddmTxGlmmJZ5GLH3JOTrqnA8Qt2Xf8AAb/20EuRxPWooUAQnRIAJZPu+Ufht/fQ2aVmaRzkADA0SIMNsJJIYjf/AH+OhUx/dAbrzHWwPE42MwtwFb5LhxCqxQ+J4UbSHPTfygn0661mht1PR07vUcs8zYAUfAPX56oP0XyPRQ1tYIuaOR1iJBwQBucfiRrREkjngR42Dqwzn0008O0Q1Aw7YHx7zynjviR0rehcn59o5zl+vQDYemveUAE64VSR5TpxtojnXqqKK6F2oMCeA1Oqu1D7rDkwXem8O2ynoSAv5nVdooHc5RCVG5JHTVwvNrZrXSTzviKoZ2VR1IXy/wAyfyOmaamMoht9JGA0zqoUd/XOvMeK6gNqMD2nsfBKjVpcn3Ml/R1Y4bnxnb6eshE1NgzzJ15kVSxG3y1dY6CeomNEaOYVLuAIDGQwzk45cZ9NSfoW4fnqr3X1yVP1RFganhqM4IJIUlffGd/XGt2slmtlljlqIoy9QwLTVM7c0j4HUsdKk1Fe1gwzmNhpbLWDocAT504i4H8Oz3O4U0iwBLhHSiEjJkcAk/LodPcZ2iro7sz0xEcNK1Lb03+NhCMjHcZB/PWzWC1JBZ7dHXMtXNNWSVeWGQrM2Ngfmd/nqoXMJc7zQxU0MlZJV3SWsKIhyFVlGT6AYIydCvuUlkPAmhAKgMOTM2uV1X/xDMkilPCaeRGB8p5FPL8umq7LcZpaIwwSoZBzv4kjYzygHC56k5wPfV8vHCF9XiCeiko45q2ShVwkLACLnfA5m6bYPzxqt8PcP0E90oqOrnFEkcjGaeYl0Y7DAVVzuQd89xomzXGynyzBaPDxXd5g7m0cJ0hprXTRMSxjgRST6gaDJIEoJfEYgVtzV3ONiqNkD8wPz0TnvlLSUJ8GWNZGJAVwecDseXsPmR8jqhXavcShUk5OX7hIJ9e+kZ3RyEHAm23XjK02ejjgmnKSxKqiELmUnl9Ps9e+sr4m4rrrrUPzuKenc5MKMfN/nP2v5aqMtaxdnG5J8zse/wA9R5auSjrJY3gDVEakN4wBC5U/Z9R79D21qqk9zZnJ4MnyU9xq6wJFTSxtKvOviLyhk7MM9R79NZbxSJF4lr4SwZo5ihYdDjb+mrLeuJLpQg1cdZI08i+AHc8zKgHQZ6dBqkzTvPVyzyuWd2ySe5OjqKNqeZ8wKy3NhT4ncc0gUwZXkaRXI5RnIBA3643O2mKsl6lvNtzEY/38tS4KSSEJUVELYl2hxIFIbZslepHKfYHPXbGuHgiShac10BqHaPlgQFmKMHJJbGFKlVBXr5xrc9SoZcZkigjjWncSRqxYEDL8oBxsSfbrjXTUkEFzlpayohCrGxSWMGRGYAkKCOuTtnoOuvbejtCBhVxknm+Hp76fFrldoZ5NlcZRs9QCR/MaozAMIKuSTzG0pYZ2RoJWad5OV0ZQqqMbHmJ7+4AGrtw61ZQUv1Gm8Ni2OdwivkgMNmwdtz0OOh0Et1tVrnSweEP+IcdWznLYB9tajc7fb7ZcpaS3x8sEZCqScnGPXQWot9XEMoPvM2sXDgpKWeuuNHNLHzqk0JJTmTBZ15vs5XbPvqoXpaDwVSkt60yTXCR48Tc5WLfljx7YO53OdaNdYZo6SITEFWi8QAuN9zn8fLrNViaaot8I6yVBG3qQB/XW9WSrEzSnBcS/fQ3NGaLjKifmLzUkEsahSclJTn5bMdTIad2GGyoIxo3/APevRwT37iS3MpLVlCYubbCjmAyf/dreuHfo9s9onaqqYUr5+bKvIvlT5L0z131grFWM3u0jXNkT5krKXGVKhz4ZBUH8tC4Y4ylKysUxtj5ba+lvpp4ftY4OqK6mt1NDUwEMssUYVsZ36dds9dfOjoDTHmwGSXY/Mn++mVF3UTarS+W5WSYg8dR5fMpI207eqBKi3TUk0ZIiqiu43GT/APo6YCSeOnJnII1Zog/7VlBAJeWGUZHUkf66x1qAsSO5pp7mQAGZFxPYpIII1dC0ZHLzHbp6+h0Nsd6qrBJFTVhnloVIeKSM/vqU/eQ+nqOn8tfQl24Jrb9c+IjR8jyU9Y8iwMP8RHYtgHscFcdt9YrxTw7NS1AzHIvhDkkjcYZCOoIO+h3w3fcY03MnfUuNjuqSLT+EYponH7gwLlZBn/lL6+sHXr4e/wC71IutOtSlOaMIUkBw6NkNzNsQe47exBBwRrJrZUVlm88Ef1uhqFJqKR/hfBIJU9m99aNw/f4Kum+trU+NC7jxJZXCkP6Tn7EnpN8LbeJt+8XBHNZ+031OkTVLkcGRzMsYMBY7KQCOuffXXEPPJHTVkYI/djmAO4/3nU+vtKTVIqaRW3YpJEykFGxkgr1Vu+N9iCpIIOodaJGstPJFktExVsduv9tMqSrKSs8/bS1R2tAzusnM+cSbZPqNErhPHJQ0M7DZkK8w6jH8++g9QvitzL5XIyUxgH5amR8s/DoRyR4E+MjtnPX21uvRmR+JHNVNSTlVbnRjsex/trT/AKPeOnstPTrOZZLbI371FPngfp4iHsR+R1k9SkkMoMiqyOMjfY6L0Lj9juQN4nzvvsdYW0qwOO4RRqGQj4m/8J8TUFwvV5t0TG4LdIm8GWFAqsCBksGPlYczZX8uo0DpPo7qZOGY663VJqY6mKamqUGMrzBlVx6jdCR+Osp4Z4iFnuyXKnpYqtRHyy08jMAwORsR/Ptr6E+hHiWCs4WdXpWgp0kJLGUMIwdgGHUAAYz+PfS8BhkGNU22kAz54tC8tD+8GDC/KwHUZO388asddSR1d14XrJIh9XlBglZtjkEr/Ig51aeIeEmo+JeIEoqbmpmhkmHIvw4JZT/9io/HQyij8ThlZdua316SKT91tifzUfnrlr7hkQYUbDiC7TwI8/GlRDlcQ1HgM8p2CvzGM4HX4QPx1onEH0b2mTheWmeoCTIFk+tOMJGoILEKO2M6kX2JoeLjVxD/AM/bVqI8dDJCRIv/ANp+ur3UwJUUzxuOanlTG/dSP7HQVnLBjDqlypE+VOI6aS3V9JXU1RHOYTyiaPPK5RiOYZ7EqT8iNbfwjw7W36NK1WWlttSqzxyMQT5wGwqg9iSMnHTWaVNqIprjaXXmlpKho1J9TlR+HNGn/u1rX0AXVavgiKiMmXoJGh3O5UnmU/qR+GiHIswTMqVy+DL/AMP2Cy2qjanEKz83xSzKGJ/TpqpcNV8Fm41u1Gs0fgSnK8m6qV2A29F5c/PVqaoaKdkPb+Ws2v0xsnHwrYkCo8iTqcbAP5H/APsuT8tc3DoQ2wgY2+01KqrFMfMDkZ/PVHo6L6xLxNZXBHLKlypRjBCyA83/APsjlP8A3avUHJLSqc8yEArjYe39NVq/N+z+NLJcubEVUJbdP6HmHPHn/ujI/wC/UdujNmG4Yi4CrOeino2+OBgyE9SrZz/9kG/AjVj5xnfWe0NXDZOMHjqZVhhLtGzNsOVuhz8wv5nU/iTj+02UHLDJGV51PO3yj+L/AN3KPnqKDBkuVV9R6h3iu12m92Krt18hhmt8qETCY4Ud+bP2SOoPUHXzxbr/AF3AHHL0DVZrKTxgKKslblWtj+wsjHZZQDhZOjYwfXRHjPjbiDiCdhaoJacD4ZXwz/8AaPhQ/IZ99ZvdaaoufDdfHVvNPVU0vjM0pJZhkg5J328x/HRA0jMMniVXXITgTSOPLhdbkrVVFXyLb6klUdcq/MPiilPxcwOQVJxtsMaoUC/Vg0c6qMjGXzkfLUbgPjN7ZP8As66slTTTBY+aVsLKBsquT8LDokh9lbbDLaeJbLDKgrKGdp6Nz5H5SHjPeOQHcMDke+PmATorFqOxhzB9ZQXG8HIgeCaHklTmJcrmM+46D213f0+v8IxT9ZaSTtvt0/8AteTUARfVZGWc8uO3f56K2WaOspqugCjlljyhz1PT+q/lpjYB3nMWUgqcEQHTFfAVpCVONwNzrsVOG5YVx/F3/P8AtodQBlmaB8llYjGiHIiDmdwMdgcn/TW1TbkG4zjja3Aki1Tmmrg07c0Mw8KZfVW20JutD9Rq5IJXGImwvqU6g+22pjyl4mWNeUHue/499O3mJq+yUtwI55oiaecDqcfC3+/XWb8cqIRUfmF+CrqjyRxnzSKojLdSwHwn06YH4ac47tUbA3CI8rMcSqp2b3+eqlanekqUYyCE55Sc7g9QcfpowKmorZPDgWWrmJ2Lg4/AaG9Nb7iZ01sGyOjAUdPU0cq11JJ9XePcOThSPQ+o2HyO+rVJNJxEUeCFEvELCCohbGfZh2PbfoQcjviZb+CZ6uQT3achf+mpyf7DXfFtkahghuFrZoqujA5Hz8abeRvUDbHoc/iO9jO5ZBiHoqlQryXaOB3kn8W81Bdh/wAtDv8Aj6fhq522301FEIqaBI1/hG5+Z0I4K4mi4ggPjgw3BP8AGRhgk4zn8iDt1zkatKIc40KH3CWNew4kZIY0q1lduWNxyOfTPf8AQH/tx30qqB6WoWRhjwiQ/uhO/wCRAP56n/VueNlYddSoqRqq1ln8zwYjkz1Ixt+YBH/aT31wmWAxIfg9RjVZ4jsdZHXC+2LCXOFcPEThKuP7je/ofw9xcrXEPqr05BZ4CBk90O6n8tvmp12YM5DDU495AcHiVqzV9FxBajPAD3jqIHGHiboyMOx6j/Z1n3JJw/xBPTSgtCTySA9GjPQ/yOrzxHZK633M8RcPx89WBirpc4WsQf8A8wDoe/T00J4rho+IeH4eIbWS5jHLIMYYDO6sOxU/10Zob9rFD0YNqqdy7l9pLttT4EoJbKqBzN95D3/T9Do9PFDUwSU80ayxSIVdHGQynYg6ofDNYZqcU0h/fQDMeftJ3H4auNnqBNAEycoBj3Xt+XT8BpurFhg9iDIQwzIVqmksNZHZ66VnoJjy2+qc/Af+g59cDyk9Rt1Gj0kPNkEY01X0VNcKKSjq4hLDKOV1Pf3HoR1B7ahWGrqKKrWw3WVpJeUmgqm/+tIOqH/1V9PtDcemsuEO0/SYQPVyO5sfBMFFdbOk9QWlqY/JKpOBzDvgeowdSJaFeGaiW4W6AC3TtzVtPGv+G3eZB/8AbDuNxuDmm8F3b9lXdWkYiCbEcw7D0b8D+hOtY2Zc7EHSnUUbGwI30zh0z7xmOSOeFZoWWRGUMrKchgffQLiayz3DwauimFNdKRi9JUH4RnrG4HVGxgj5Ebga6dTw5UtIuf2LM2XUf/VHJ6j/ANMnr9079CcHScgEEEHuND4yOYRiVBK1q2NbtHCae525vCrqQ7sm249x3VhsQdGZojPHHdqABpGjAkiz5Z0+6fcb4Pv6E6DcYyxU9SLvaJUa8Ui8rwg+SoizkxSnog7qxI5T7Eg0+Hjyna11clpLyxKviGjWTleI5OUY47YOeX02Oqq3OByZm39M5PUuFsusNpuZiVi1uqxzREnBjkzgqQenoc9Dj10J4x+lSw2gNAlaKuoGwp6Ih2/F+g/DPz1kk/GdfTX365Mifs6duaanhTA9C4H3wMZO5IHqBqtcaW+K1X8VNLLz2u5j6xTSxY5STuy5HzyPmR2OtW01rAZ4zBjrUCkpzLhX8cXTiSaanqboOHre43WAF5ZP8z7nVduv/h2OkanoKQTS8wZqlmJYkd+Y76E/VBDHzzstLGwyDLnmb5KPMfnjHvqPLcqanytND4j9pZwCfwQbD8Sfw1ZNKqHPcXWau2wZJwJNczVaeIUjhp18uSQkf5/aPsMnRjhq5W6aOThe4y+LR12RG7jlWOQ9MZ3wSOpxuAcao9XcKmeYySyvI/Tc8x+XoB7a5hpZ6jLkFT1U530bWh9+oKLQpyOZP4iqbrbbpPY7liMUzeRUHJG69nCjrnHffII7aHKKipYkZ/7hq8V1K3F/DaScqtxBaVBU96iPpjPrsPkeU9CTqBbaW3JSLUmQTD7Z5uSJD6Fj1x/CG/DXCEqPPJlrN1nqHUA01omk5mjgkqHHYAn8tevQLE2bjVLT/wDoxgPKf+0bL/3EH21cKeWaqjMNupGqEO2VBhp/xJ8z/wAtVfijh64ULCUqjJJnBiXlRD6euuK7OcTIbU+8gm9Q0TgUMJhUHDOW55SP82ML+Az76sXA/EBaomt1wpz+x65SHOWbw3z8Zbv74377Eapf1NiPOc46jRiw/WII2xEPqfeVyEjU/wCY7Z9hvqzJ5fqlkct9Ms7cO2qxVbQ1sPjSBuaGaV+fxU+Z6nHp8+hGot1FA07RWyNatZxzeDCMlD67dB/I6n2att/FNubhmsmSSrhzJQzYYBsZ8gOzHHyGQSOuCKDdq+401RPa6yFaXwX5ZIF8kWexwPjBG4JJzqr4A4mvkDO4yfPDTQ5+s1Klh1ipmDn8X+Efmx9tDJ7t4HMlthWn7FozzSH5yHp/241BDSVDgZLgHAzsPy1LWlXlPPuPTVUdl6kO0cYgmQzysxdjknzYOSfmddUMc9HVR1NKxhlicMjqdwR30VpbXUSsWponeMdXJCovzY7DTdbNZrWP+LrfrUuf8KnOFz6FjufkB+OvRUa/TJVl+4qbRamyzCDibBwHxStzphWReWshAWtgG3N/GP8Aex+e1+/btAsK8s3iyOMiONSzn8BuPmdtfNfCdfxVV3ynn4cs3hQxSZYFcK6nYhidzkeutqs1SlBVPUvSiASkfWo9iY3x19xjv3H46R3FLGLV8CegpDIoWw5MspqbrOS8NHDEnYTOSx/9uQPzOlqfBLHLGHBUg9COmlofBmu6fKtIZUU5JAJ2ydR5nIJIY4HfV6bgO71NM1Ta4HqI+UMY2wGAPTB6H5bHVOrqGpo52p6qnmgmXbkkQqR+GjTaijZXA9jZ3NGKd+ZiCCHxs2cY99TEqFeMx1MaygjGT11GhURght9/N6/LXAducnHXtonIQDd3M1G8nHUZruHqCWMzUtQUJP8Ahld/y/sdELdQxUMPIiAHHnJ3Py13RwSTMvhozMxwiAZJPqNEZXhtyBYzHU1oPfDJEf8A7pv0HvqhJXo5l1rB+0bEf1XE9aC0j4KU4PmYdi3ov6nt66uPBlrp690r6+aKapX/AAqQjCxgdMDofkP11UKOGRpGlqOYyHzOzHJJ/votHMYt+ZlbqCD00E9dlikA4jPTmutgWE1WNhnDDDdNQ+IOJqHh6EI5+sVrDKwKfhHq3pqiHjK7R0zwEo0gHLHMwy6j+v46rckrzStJK7SOxyzMcknWnhH/AI69zebqfp+PmLPHf/LV0wNOl5b3PsJpdvvlFdn8SCqENW+7RSj+WofEFTcFbkeMxRDpynZvfWfHmUkgnPYjVhtHEtXTJ4FaBWQDs58y/jpjqf8Axs1vvo5HwYp0P/lgtXy9SMH5E9lnaVjktv1J3JOodz+q00BlqEEr4wqZ/mf6akTXOkq6iSooIGhgAwHfGW9SB2GqzcqpqmqOM+Gp2B1pptKS2DxiMdTeqLkc5kct4khOAMnOw1KpKV5jzfCn3tS7Za5JpELIxJ+GMDc/PV/4d4djhKT1YVpBjlT7K/3OjNRrEqXaILptG1pyeoL4T4VlrCslSjRU+xAPxP8A21o9vooKGlEUCKoAwNumvaRVRQAAPlqTjbGvPX6h7jzH1OnWoYEZfcbnO2o0q9cDtqTUNHFGzs4VVGSTqk8S8VJHFKlM3JEoPNKRv+A1WilrWwsvbYtYyYRvF6goEaNSHmx0B2X3OqHdLzLVTMwk5yejdh8tVS/3me4ho4ZJIoubOM7v/m/tpiku0iYWpTKj7a/216zw7wyur1P3PH+L+K3WjZRLArEEktue+ulbGodPVRTLzRsrD2088oVC3ftr0W5VXM8T5Tu+09mM3GpWONs7Km59z2GgUXO7M8hPMxznT1dJ4s3hq2UQ5b3bTadQPTS8sWO4z0Vda0qKx7fzHFXykdxqTABkNnTEQJc7banRKMqAPnrJ24hKLzmOAEeYdTsP66k0UXKhlPU7L8tNQxeNKAuw7ew9dFJBB4IMUmcDHKRg9v8AXWulr3Pk9QHxS/y69i9mR8d9dIjOyqilmY4AA0sjprpMghlJBHcaZHgcTzSkZ5hF7PJDDzz55iPKo659NB6oNC7Rt5WBwd+miYulWuyEZA3PfQStlLO8sjgDOSToXLqCXh7+VZgVCeoSvwnbUC6tQEOJIs1GNuT+uo9VcmYmOn5lUnHORuflqLBDJPKY41Lsd9hrzmu1NL8KP1npfC9HqKhl24+IzGgBLDGemjFisNXcpQVRgh/XVh4b4RL8k9bhR2HfV3paaKmjEcMYVR6aR36/aMLPQ06Ddy3UF2KwUttiHkVpPX00Wxj+2u8HXLaTvYznJjautV4Eg3SshoaCorKluWGBC7H2Azr5X4ouU91vNTWTtzPLIXb2JPT8Omto+nm+iiscVqifEtUfElAP/LU7D8W/+11gpby5Pc6O0qbELn3lH9T7fiMyenpq/cL037OsqySLhyPFce56D+X66p1gozX3eKJv8NfPJ/lH+wNXHier+q2wqD533/oP6nWiNgFjCGXOFlOv9X9ar5GLEgHkB9fU/nry3RMwCLuzHUFQZKgKDkeurLwzSGatB7JrCS44WXnhOlFPTrnY8uBo/GeZtz00Lpf3MQC9hjOp9DUhJA0kaOMEcpzg5BAO3p1/DWqDAiCxtzZk+NcqcH56kUrIJlEjOIyRzlPi5c74z3xqFDOAAMDbv66eYgHynrq8HaTqmPmeV6XmECNgPIQDg5Kk++B21GEs4jClebb8tcJMTiPIJzqTTyxDn8UMMKeUAZGe2fbUAnBOIpGCyMqcwC+bIyANeuabw42hlcMy/vVK4CnPbffbTcjFwwUkA7EaiyqY9sE++ukSKxJ5nc8kigrnC+x66iuoZCMHm9dOTFkfDMrjAOxyDpppi0hdQFOB5RsNUyRNgoMgTU7gsVPL336aq3F1a0drki5WDSME9iOp/l+urhVSNKWLnJxqg8dPitgp1GOROdgPUn+w0QuofYVz3JXpUa4MR1KyhyRgbDUujGUx94gfmcn9BqOy5AC7FjjRG3oGljBxjdj/ACH6A6A24M9KhyuY9dZAkCxj4j1GhVT1Csc8q7jRC4nnqwowfX2/3tqFHBJV1qwwqXkmcIo92OBqx4WVPJmn8EUAg4Vo0kjGZgZSSPvHb9MaKmiq/wBprHbUeaZyEWJQSXPpgddXr/w/FFboYiAqwRpGgx15Rgfy07wdbzb+KJ7iw/d2+hlnye78nIv/ANnIuqLq2QbkPIia/TC1iHGQZWbREaggT/unHxJ31KdUenlCLkGQKM9QB1/pqy2zgS83Chnuhh+oUkEDTGoqMqCFUnyjqf5aJWiyUcPBfD8UiYul/rREzk9YTLnp22Qfnr0Gn8cBXbZ3PK6n/wAfIO6vr/OpV+Pac0UtutzAj6rb4gykbhnBdv1bUHhCJf2zPWSEJHQ0MszMQSFYjkU7e7jVm44s9wuPFP12pUQpcrn9Wp42OJCmcBsdlAA6+uoC0cSWfiOa1xSCnq7nDboSckiIMWJJ+fh689ddvLN8x9XXsUIOhNe+g2KO38LxJVRRlJ4wzll33GSPfrq7XaSG22qe4QSLUUigBoHPTJxgHr36HVa4dgNNYaSJFxzKCAPTtpu7tO/1SLzEtUqzL2YKc499wNBiwKI1rfbXjEOfU4Km40poKmOGCkjCTUnJho8gkEeh3HbHy0TtNqt9koYaWggSCCNcFju3ruTucnVDW/PT3epu0zRRvLN4YaVuWNABgZxknZegB3PbroXX/SFUNXSukkaBGZRNICVIycckY6dO5O56jXPN3TWtkUE45lw4muVPR11RUSz+DEVHK4TmaQqDtjqcaweWTlqFmDhGXoRsQeuiHEHFVwuM/gRvLzOP3mCS757E9l9ht89VirmEbN4z8z9TGh2HzP8AbVErd2AHvMWsVdzn84co7o0UzCmjDO0bxlmwcc45STnboToLcayMSsV/fOT64Uf30HluDzOkcjKsQYEIvlGe23c/PXbTFmI6EYGjdVoW0uFf3mWh1tWsBav2j91n5ZqGVKl3lEZkI5eURPzbcv5DfTcMjyrPKzs0j5LMTkknOTnUaqAaaH2T+p1Jj2o5COucbaGBhWPmAOJ6KWphpkU7eKzNlsDHTfVfZlErBR329tXNnpVng+vLJ4bB+UoN+bt+uqiu+DjdcYK9Qfno2gkVjPUEfBdsdzylR1qcSB1YAnlI313R0E0sq+U4JB9NWGKatugetujeK6ssUcjLvy4YY9MDH89WXgpYmW71Mw+sGOJEgkkGSv71QCM9NlI1ndaAPTKITjBka18H10tAtXOBFSE+HzORknGcBevTudtWC/W+koOH6aKJF5jCAHbdiDIf97a7lrCsWV6477+mmOLp3npKSSTGZI1Yheg8zf20LuLWDMywoHEhcHUIn40s4wREKqmEjE7DMgOrncKmnqrxVGDdvrDYGdmAJGV9enTr89VjgCnWTjygyThHVyP8ilv6aI8rft0RByY/rRA+XN/rq/lizdmV81qwD8wfxMlJTVzxVazSLCkQdEIXmQLlhnsT0z231Sfo5oobj9JHDVI6kQvWFypOSAuWAz3+HVz+kNSLtc+Yknl6/wDYNVv6GCV+lfh52XIjWZ8Y9I5D/TV0JFLQzTDLgy1//esSqn0h3FMgZoH69/PHr6ppKrkj5Xy6e25Gvkn/AO9ojVuP6/mheRhQPylRnBLJ1/LX1FQc6x+bIOenoNYg8xqrEHiCPpXLScF1yQIHR0YFX2wCrbj36ba+WlkCx1EUm2CD/LX1fxnCJrBUY3LBQRjIIz0P8vkdfLVypMtKVxlgMjuP941vXbti/VV73ikqAgjcse2+j8lcTPFMoxmnj6dyrf6ao1TJPHgSA8q99FLbcP3KF/8ADwUHfGibyG5EWbCO59EcDSiXja9RjZaikpp098xqD+qnQ76YuEKCtsFZczDyVtPEWWVdiwHZvUfy1F+i2vrKzjWhqqmkNLDVWkR0+XyZFjZhzkdtzt7Y1pvE1KtVYa+mkTnElPIvvup0LjJjahQ1JnxonDxlo0rII9lkIdcbEEnce+qg1LcLNcGrra5R18roy+Vx3Vx3Gt84TpfF+ha5Oyq0tJc92I3ALKPw7aB8XcFVlIYK4wKUqFSWKVRlWyAeVvQ7/jjVD6V2mVpu53D3lN4R4jgq6fNNzo0UeJKUjneBOvlGxlhyc8o8yblCD5WthSCsoman5FYgSkK4YFSSAwbYMhJxzgDfZgrZXWV8T2uai44uENG70ksFRI1O6bFQGOMe2CNH+EOJ3nqBSVCimuPNzmFWCLUNjBeJiCEkI2KkFXGxDDpkpavlIY9dWpXBhS82eP8AZslcCY5YpVUrjY5zv/v11BtYDW6tp+YBmj5gOvTf+mreJae72yajXCvOeQYUoWZSGKhSSUcAbxkkgeZC6ebQqy2l4JoqbkCtKTGD65OOujadSDEt+gNbcypOagDw2iVYydy/cdiP76JcPRpy1MRZn5oyQD6j21dOJ+Aa7higinvISdPFUMI1Yoynrh8bH2OPbOpl5o6eCjga3U8MVHDVBkjLAyRrIu3mBIdCw2Pbpqo1GWx8znk7RiZ41IZpQ8A8oznJxgZ7e2rhYKm6cJTmWGrHjQsrABxyyI3TJG3f8D1GgFTTmKqOOaUhsGNB+GRo7w7SVjDklWKFKyMhXcZ3Bweb0OcaoSGBUzQArgy/cD8bPdLqYRHBRpNG0U8cis5AKjPIq9sJnl7dsjoTtPBU0fCdVVQSiphq6N1fA3SRDzKfkQo+ROs4ppJbHX10FppZvrHgBo53bEkJUqxYEbEAg4I7H8te+iHiZ6y0vSVtVHU1BclolTDN6lezdM4HrtuNChfYwpHViA0jsWl4X4Yvmec0UqxT5+62Af0/nq32aNmssETsWen5qdj6mMlM/iAD+OhNmpIK3hK9W2mdGWOR2ix02OR8tx00Z4NZaqglYE5m8Oo/FkCn/wCyQ/nrMrnibUjDAfMybjaiak4+rY4xgXCnDpn7+Mj/AOzQfnqJ9CtwSg4zrbepCw1kXNECenL5lH/sbVv+mu3ywNa7rCMNDI0fNnoThl/Vf11llXUCxca09xpz+6hqBIvoY85/VHTUToiY2Ao5n0Tcy7iOWMjmGx99VH6SKH63QUtXHzII2MUrfdRxjm/A4OrDPX0lPSiSqqEjQ7qWPxfIdT+GnLheuGlslTFXhipQtjl8xGM59vx1TgNmE5DjucfR/dmruGoGlAEsYMcq5+FgcH8jkfhoB9Lt7o4eEKt4quMVdM6TUzqy8qSo4ZCSTjqBtufY6xjjTi66WivnpreIokdixEmXHMdyQp8uSc9QdZ7xLe7xd5i1dXzTeIvw5wPkANEChujM69RkACbDW8Sz8W2VbsgenqGyuOYFg+OYYIA3B26aotNLJK5lldmLHJdznJ9ydO/RbXJNTVdvYkStiWEdub4gPz5xpu8wGG6TwqcLzcyenKdxouoADHxAr68ky0WiaJoT4eHPMdsf013La1q68S4w0qGKQHo4Pr75xquWipkpHEinlHoftDVsoa+nq4y9PkMuMg/Ep1tYpHq7gSemY7drM1LXVdHOgVopGQhhjmwSOmiPBfF0tlrP2fcJPFo3AjWSU7cuMBJD2x9lu2ADsAU0X6QrBBdglxjKx1EkQIONnI25T/Q6yq52vwzIlSgiZfKykb/LGuqiahME4IjCrUlDjsGaFe7NDWU4raMs8DHYY80TZ+EjQW2//R1xjM55Qrbgb+U7E/loBwdxXPw9VCjq3L29iEV5N/DHTlf+H0P2em4xi7XCggqUFVSqZIXOFH2omO/KfzGD0IIOdwT2i9kPlP8A3l9RpVP9ROpXOKopKC/ScihUnAkBHv1GfY50ykZcqd2J6aNcUwCqsFNWuOaSlPhyFNzsMY/QH/u01ZLHd7hCpjhNLAwB5225ge+ep1ul6VE55gj0l+pBJWIYlYHHRF3Yf20W4boq2rapj+qMlDPCQ0noeoIP9tWa1cI26kAadfrMvXLdM/Lv+OrDFAqxhEUBR2A6aHt1L2d9TemlVGJn1JwbRmkSoeWR5JVIPYRyKSpHvhv0YHvq52CnpGt0dRT00cJkXEgVdwwJDD8wdeU1OFuFVbjhfHX6xT7f8xB5gP8AMn6xj105YT4dxqKQ7rUL9Yi/zDCuP/tT+J0ITgwxcFYRSIhRjTFxoxPSOMZKjceo7/pomsRHTprtVA5gPx10Pg5nMZlRo+F5LnwvUTWt0p77YpueCX4fHpXJPhuR2VublP2fkSNGuCOIYrzE9NUoaa5055KinccrBh12/EfoRkEaIcFzi28ZQiZP+HqQ1LNnoUfYZ/EL+Tag8f8ACNTSXxq60OsF3oiPDc7JVR9Qj/h0bsSQdsjWFi4YlfebVsGXB7EtkCqVxgak0rQ0lV4lSSIJl8KXHb0b8DjQHg7iClvtM7pG1PVwPyVVLJs8LjqCPT39x1yCbLOI54Cki5B7jrqofMqVI4kKoie3V5qGBRIiY6jP/SJG/wD2khs+hbUyph5ZCMg+hHfTlLH9atBWQCWppP3Mwb/mwkEK34Db8tc2OmqaylFKkUk81KfCYqM8y/YYnoMjGc9wdaH7SxBIyJDaI4KnvqjcUUFRw9c3v9spzNS1BxdKNBkSL/1gOzDfJ7/Prtlv4Sd/PXTcgI+CI5P4k/0/PR2Kz26OglokpIxDKhSQcu7gjByep1ZV5zNEocj4nyS9B4M0ddb5hLTv+8gkQ5BHoffsRqzWuTkEVXEhKSZIA7HbmX57bfhp3inh+fgziCuhCSTWwt4s0KrkiMn/AB4x6gnzL36jodMQ8tLOqJIktFVgSQzIco33WU+/+m2DprVqd3B7iqyg1Nn2llhZWUENkEZB9Rpq6UFPcqJ6ao5gCQyOpw0bj4XU9iPX/XUS2zHlkgkBBQ5X+o/r8iMdNTlmCrvsPXRikOvM5nB4kWyXCoMr2u6sq3GJeZZAOVKuMdZF9xkcy9ic9DnWucB8RU9RaHpq2pjSakABaRgMx9Acn8j+HrrGLzNS18KwxzOkscgkhqIULNBIOjgjb1BGdwSPTEW13asnqamnNWtLc6ZSkscajlIYYEiZ3KN1HcdOo0tvz9H9jDaLdp3D9Z9FXG70EVM5l5XhKkM0mEjI/wAzYB/DOsrr/pGorLNUWiCqFxoSuaRYHIMZJ/wWdhuvdSP8uemcnu1yuVTUsLhWVE7KeX95IWwR89D5AJcoVL82xUZ3/LWNegtcZY4mlniiqcKIdvPEt2vEhjnqSlOD5IY/Ii+2BoTSVUtor1uFMC8fSoiB3dO5H8Qx+OB7ajRyeHN4Fa7LJjmVhuzgdvZh74yN+x0v2qgJSmiCnpzfE2f8x6fgNGV1VKu1RzALLrC25jxC9bHTzhjHUxmllw9PMN+bPTA6+xzjBG+hlJeqRaOawVUz01Kz89LVNgtRVH39uiEncDOMnsxIE+PJBJKsxc08hLnlySh7sPn3H49evtypg6fWFx082OhHromulrvQ/BEH85aX3KODBnj3EVdTSVyFKyNykwLZPMPVupz1B7gjU6htFVUnDc2PRen+uvAyQ1FHXV8ZFLyeBIxzzcgGUwOpxjCnpg4JHKM2iCvj2ggGZhjEcSiWaQY64GUT5kn8NL3sNRK4l3r3nOeJFpeHhBCDK0UKnu3Vj7dyfYb6cmp6OgPiysEUkAmfY4+8sY8x/Ej5HVmsHD91u1XGkjJbEmZVMhbxZ2BON23AHsNWy5/RueHcTpCtQG2M5yzN6g56HWJuLe8slHHpGZntp/aP1uCrttM0QjYMstUeUOp6qI12AYbaevFnt8F8iv6U4agrn5Zo33FNPnc8vTJOxPqR98astPSpQFopGC07ZaN22C9yp+XbUdqqgn8WMQy1FsqF8Orm5cRL2Vwx6kZweXO2/YavW4f0n9J1AxyG6hvhWKgjuEK1yl6XmGSDjy+3yP6avf0iWrh64cIS00ESu0S5i+qx+IVO3Xl6fM41h9TXVlrrXs1UKqaSFeanKMI45I/vPKTt6ELjf1BGTli4uuclrltcdcDQOCpprfDkAHqPEbc57kY1XJBl6mWpSjjOZm16lpbXWSQpSq06NgtUYkIPsgPKPxLarlyuM9VJ4k8zuwGFLHJHsB0A+WtD4u4WMtserp6SGhEQyI1OXkXfOT699UaltryTGKngkmk9FUk49T6D31upDjJmCsc4EF071cNUlXBI0U0bB0kz5geoI1oV8o4ePeGxfKKNRfKFQtVAp/xR7D36j3yO4xWammo7dEzXW4RxDvDEwd/xPwj9flrvhPiKviv9NJwxYpJI+bll5s5mjOxBJ6/gMaot6J6WMLr09h5I4kSjtsi0yz1UkVDARkPOcEj2X4j+WPfTM99tVM3gW6kmudUPtyL5Qf8AINh/3HWgcR/R1QcQ8QrdRW1FLS1I/fUxXcSZ3BHY+o6dx11aeHeD7JZIlShoY+cfbcBmz7dhoLVaxg23EJp09SDPcyS38Lca8U8r1bmhpO3NtgegHT8gdXvhX6LrBbHE1WhrqgdWfpn+f8tX0wOvUEfPXqIynIOly6mzfk9TckEYnlJSw00IhgiSGNeiooA/TTdyoDMn1iEAzKvKV6CRfun09j20RjXmXO2dOxIB13GmiW/6gZhj2lZornU2+DwoU8aBjlOZgpT1U59D2/00tHauzmedp6erkpWf/E5ACHPrv30tGC6sjuU2NDtF9XjoIoaRY3p0TCiM749SOv56zf6XuKOG6ejegejprhcMY5WXaH5n19hqtcc8XxUFyko+HK+WSQeVp48jJ+6p7/PVHhjEc31muYzVLHm65wf7++s9Lo/LxbaZ2/VmzNdY/WSPqlLWQc6hrc56JKSyH+o/XTUXD9xaflaJViA5mnEimJVHcsDgfj+Wp8MKzQtV1kwho1OCxGST91R9pv8AZI0YsdolvUIlnVrdYYj4gj58PNj7TN3Hv0Hb10VY5U7mPEyqqD+nHMD8ipQVDUDtDQwLipuDLgv/AOnGPfoB1PfA0FtUZLLUToQx2jUnOBopxNeYrzWLTUMfg2ejJWnjUYDnu5Hv2z2/HUeEb4/2NdoNljZEvaFTj4krxSSG677Y9dNyzcx8MnKjqR664lcxxFuZVGPiJwANRvFQoFRs/LvpppNIbrOeh3EviniQ09Pp+ox4yAkjAwemuC2MEH/XXEahgebbXLxyK/bHrr0w4GBPBH1EknmSUZiMkabdXqpxSISFxmZh2Hp8zrl52jUJGvPI55Y19T/vfRGlg+r0vhoQ0jeZnPcnqdY6vUmtNo7MbeEeHi5/MccD94xXyEoKOmXz4AwvYanWGyu5z5Sw3Z2+FNTLVa0VDUVDGKNt+YjzyH0Htol4/i8sMMYiiU4VB/M+ukjX4G1f1nr1p3Hc36QvYqeCEMadeYjZpSN2Pt6DR+mBz020MoYVjiVPQDOjFGvNt0HrpLa+STHdSYXEm05zri5XOkt8JkqZAu2y9zoPfOIKe3RmOIiScjoNwPnrPbrdamtqWkeQux+1np8tF6Hw2zUn7Rf4h4pTokyx5hfiXiaeukKrlIc+WMHr89V5a2Ysxcqyn7JG2o7KzOSSSdeiM9zr2Wm8OqqTbifPNb47qNRZuDYE4q6K31meRfq7k9umg9dZ6qlBcKJY/vLvj8NG+QAb67ilaLZSMenbWp0rJ9BnE8UV+LV/USn4KNzRko3quiUs8sFEplbnmOyj00UuKUT4k8FVnznI2GPXQCaQ1M7SAHkXZP76xZmY7T7RigRV8wHPxFCvKoGxPU66VRnf8NcrzA9OunYwXblx8vbXT1IpzHqfGceg1KDELtnLddu2uYVGSG6Y30/CvNJk55T/AC0OfUcTfdtXJkmlHJBn7T+/Qa7B1yGz166901pQIuJ5XVXG6wtO1fAwQMZ1J+tRcu8WfbO2oZIAOTjQ6rrSG5IPxb+2uXWpWMtO6XT2XttQSTcq2Okjy3mdhsinc/21XamqmqZCZDhR8KjoP9dczM89UBEC5O3vnVs4c4Tkn5Z60cq5+HXiPFfFmscjOAJ7vwvwWvTqGIy0B2az1dylAiQhPvY1o3D3DtLbkDsgaUd9EqCjho4wkKBR/PUxMA4O+vOvrWs46noU0qpye56i7bDXuugfLtrknqdZA5m08PTTEzBVyWAA3JJ2GnGIwSSAAN86pH0t302rhKZUDK9ZmCNyCAy485U98DA/7hrSqs2NtEqXVezMU+ky+ftzieqrAxMRbliHpGNl/Tf5k6qshwoX107KxldnbqTnTVLDJV1cVPEPNI4Ue2dM3IA2idoU53GW/gag8KiapkGGqG2Pog/2fy0L4xrvHrCi55V82P5D8v56tVQY7faTynkVU8NB6AdT+X89Z3XStNUM7dXOcazt4ASbV85ae0K9XG+TgavPCdMIqYO2xfcnGqnbKYyzRwgDfGdaLboBHSqgUDA1h7wXUtxiSeYhANORSkY1FmJDDPTXSOM41srRUyYEKwygkAnrqbTuGyM7+ugsROTvqTFUCNSxJGtIMYUgZBMxcHyjqO2pBfI5g3MCeo6aHJNzxBh3GTrqOUx/Cfn76bLoA1QI7iL/ANVau5gRlZKySxIO2vZGBXlPppqOeIkFsRn1xt/ppw4wDkEHcEHIOlllTVnDCOdPdXcu5JGKMCe4006jcgjU9ccpGN9M1MaEeXZ8/hqk2HEglhyBcDJPfWXX+q+s3qql5vLz8q/IbD9BrQeIKhqO3VM5wpjjON+/QfqRrLBzEjmOqM2Iw0absmOAkyDHYZHz7aJ24YeU9gOUfht/fQ+lA5+ZhsDn8FGf540asUAaSFHHVuZ/kMk/11iT7xz9K4kEpJJVl8YBbA21aPo2pFSVa4xr4orF8OQgbBFZzj8TF+egVZIWlkkxuqlth3OrpwbRD9iU6shYJGZDjs0j4/8AtYlP466rgOu7rMB1RJpbBwcTVLHfBVzLBWLysoZ2k+ywUE7+mtW+iK0JVU9XcGpIqgyBcI7DoG5hgH5L7ba+daOqnpaG5zgeKojjp4x9oM7c347IR+Ovor6OPEtvD1KImKBRyqRsfKOU/qDrXxCnTud9XB+In8Nu1CHy9RyB7w/9Klw8LgC5QQgiefkpljZcMCzAEY+QOvKKxtS1FtkNtWWO1UKwwyghmVgm/KvXJOPfTPE1wp73drBaagIJGqTUSSYAISMHr+JHtqdwpVNDcq+oknLLNOQGG6scnBx8h10oYYIBjltjtweJGl4PmunEltvFzqVigt6O6QKMszsMcxPbGB+Oqrw3w/8AW+C46WgC01LW3qSowTkiFWbkA7n4Y9aDxpd6ah4euEjzBJ2hbwkUFiTg4zjtnG521SLFxDbrZbKOkd0jNJEIlAJPjEY+EdT8tcZsDAmVldaMAJeblUW6106Q88YFNHl2Y8qqANuZjsOnz9jqn1fEVGKJa2SSKR+YlQF5UQb7kt222zgnsNZ3xzxVLcbxVOrnwGARI2IZFGN8AZAJ9RvoDdrpWVUEC3GtdY4lxEjbtjthe3zOr1U2XNtUZlb76613OcAQxxHf1q5AsLswVsryrhWPsDufmfyGq7Uzqj5rJSrHpCmOf8ey/wA/bQ6a6mIEUaiLfdyeaQ/j2HsNBaq6oKgqzmac5bkXc/j6a9BpfBBWN+oOB8TzOp8daz+npFyfmF7jc3ZpFiIhi+6h6/M9TqLXTvHbJJowHcRAgZwMnI66r9LS3S+18dHDG8ss8gjjp4vtFjgAnv8Ay1cqegDiSOanaWGmjDzIpxhQyrv7ZKj8dZ6/UVFkSgdGFeG6W1Fss1LZJEq1lt9ZV1BrJuaYRDmJxhFx6DR5owsfi5XBJGOYc23t+OpUlS0kf1eJEgiZhmJFwB+PfTJjGeVBzH00Fr1tVgbezGPhttLoRSeB8SJOjNUod/gH9dTxGBQNygHucfnohQcO1dXUrJOPBiKr12z+GprGa0VVT+z2AaGNgCy56oQdvkx0uVhmHZzyIJqeErrVilZVRU+stAxMgUKxUHqT6HTVNwlJBaZLmlG89HBKsbzkjkDHGBjv1HrrS+MqqSr4ckqqhI45Hr6khY0Cg8iomcDv1P56ziSSR1EZduXm5iuds9M/lrauwkbfYQSxcOW+ZGqo0+pxqmSxqkyOwG/+upPBKf8A6u3ipVdnq4Ihj0Pit/Qa4SFmtXjEHl+uxrk+yOf6aPfRxaqmo4AmaCIN4t1jyz7KAsTH+b6pYeJVD3IbboV+Q/XXfFFOaYW6OqHOpghkwmQeVl5gN++Do3brBW1lVWUVupDV1MbqoIXyrvuSTsBj10a+kHhmppqGzpNy1NfJKsR8JScKEAAJ7gdug12vAfJmexipOIG+jO3011+kVY6R6mlg5ZOVi6s4xG3fAG/8tEHoRQ8QGSfmljiqmxzDHiAN3Ix+mrgnCyW+9Vl4muUE9PJJLIKGLYKCpUY9WHcbag8NcO194ttvNSj08Cyu0jOPMFIAGFPXpqB8ZxLeQxAXHMr/ABhwxdr5W3PwrbTUlOssnLVPkNIOgO5JIx0wANUD6IOH7nU8e2d4kEQrbfUtBKTlV5o54wxxv8QOvq2ut9uittQok5uaLlJZebH4f01j3Bs8Q+lDhyKMwJ4VoVeSOPwwMvU/Z+ycAHHbOrDd5ZBhldXlWgStf/ev0bQ/SRf4C2fq9OY2boNpAM/prdL3f6K2xFi65xsTnf8AyqNz89h76+VOCrhdKP6b5YLTX01E81VVCRqqXkhZVEhw/qNsj3A1e+Ihd6qBK6rq4ZUnHMY0qFkcD1bl6jtk/kNZ+UwGRN7b1RtueZYeKeOXr+algV5FOxcvjHywcAfLPz1n1fH4dwlQ4yrEHByOupDPJE6QHYbHGds6Yrv/ADjeXJxvqbfTMQctmRa+hSopHYDDY6+ugxikpqYJjYOcj5jVpjHNStgdRpgU6TwskijGQdEF9uJkyBpYPom4paXi+yRGN5ZKVGgDGT41boPQAY/X219JQSw1cDcm/wBl0PVT3BHbXxtaqaWjvJeElDnyspx8jrTvos+lImohtl/nMFUoEcdURkNj7Mg7j36jUONoIl6LfKyjdSRwXCBwf9IdlC5aCR51TqRgEj9V1pFgoILjwbQieJJY2hClWGcgHb+ms+4Su1NFxpxbSyQGeS5ROiR0n73xDk9COow2c7e+tG+imQy8EUKk5MahPyA1TOcgzumVSw/X+Z89/Spw7DFx/LCEILcpjY9RlMfz1nnGPDRhLQyIyukhMTgdVYBlI/DW7/8A3wtG0HFdBcYgq80IL/xcsn9jqu3inp6gr4iBg9PGRkbgp+7z+a6wyV3ATQsUbAmSWK/VFLMlHxAwhnYCOOulU+HMAcqk2MHY4IcEMp3BHXWiW+4iY+DWuY5oiGLyOMoTsC7DAIORiYYVtg4Rsc1Z45sLNw5O7qJEjqFZWPcMjjf03Vfz1VbPd6vh96eluDzTW0KHp6lMGWlDAdM7MmDgodiOx6az+4hddi2rhp9i8QT0d/8Ao6rjkSgxeeMjDRspBKsDuCD2Osv4i4elS0JW+I1WGpgyMYwDEY35SMLjYjG/56r/AAjxNPSxLAk6vT1MXJGadS8cseP+WOrKN8xbyR/Y5lBVbRRwi7PCam4vLTHmaGnikHJysvMHDD4lJGxG2uBzkZguppK8jqUW40iwVCVSBwc87EHHTB2P56NPPELhBVQK08YqD/xA+GXmHNhh2bPfG+otdTStR+OmG8MBXXGTscbfnroTo9t8WSQQSFEdFCYEpQ4wfRsdD30V/rgJ6ki9CAXWnCSVFMcmJo13Kg7bDupydQI5qiio2qKGR6WemZHR0HcEoSPY5zo3xBGs1shqKeoj5oikjB/ijb1B68ucf721ARUmuksFRKsj1RYkofIQwBDKO2+dtUHGRicBAI5h36PeJqqv4jk/alSFaVQ0p+sCGKY+rkd9huPxBGTrT+CLzS22k8OfneUSyU/LHhgCMsBnpj4hnXz/AF0UEdbNBLLFDBGhYcxPmI7LgHc6n0HEEXDlMtZbqeaZIp1KuzZeMHqOU+U9SN/Y6yUHOYQH2PhTyJqX0mXqtrbSZqqGGGjWQNHC/wDzGB7t1J9hrHOOKpWttJcoWDo2YmUD4SuQBv8AwmPrrviXi69cV1E0E00dup+TxEUEM8mOmZPTrsuB2xoDTsZuEa62OPNE4qI89RjIb+a/lrSunHZzOvYrtmJ+LL5XUyQmreFEjWMsjHnYDYZbr+A21qnBcy3Hg2iaU8xERgkz3C5X9Rg/jrDaGblwsS5Zh8R33+WrlwRxRNbKSpp6iFpoTIHypOVJAB/kNZ6mncnpEw8wAndIf0jU7LT09awMjxs1NMf/AFEYqSfmRzfJhqiVs7tBhdsdhrTr7PT3iO6QQBwtQiVcayLysJAoR9v+1D+J1mZaPw2QrzHp5j3+WiqssgJm9ZGeIS+j64tRXmKTmCFGwPnnmX/7ofjq/wDGkaJVQV9Ov7mYeQ+it5l/LJH4ayShmkSrDZ+HzKB6qc/yyNa9A/7S4Llp2UiaiPMo2zyHzDb8/wA9WHDYEvcPeBZUQshSbxC6gnykYPp76foZpKKUSCTwyvbuR7j++oUVUcARjlz376caJpcE76M0z5BWLbK+ZZK68VFfwvO1P+7kpJQfLueRh6/MNqk1kX1zmad+Zj3Prq0cNBYquaiqGCrVwmPlJ3z1B/T9dKxcJ3a4wyy0VOVgimMTzv2YdRnt1HTUD10EnucFL2YxxKBV29FT/iGRAwwARkn8NT+Db1V2JnjqKaaWyf4bPIpYQqfsvgE8m5wdyuTjIJU6lR8D22lHPWf8XNnJzsv+upNXbIvq3grCgjK45OXCkdxjQeot8/uNtOfKEhwWy2z2OQ0B8SCY5dWIZlLAYG2x6oc5ORggkEEz+GJWnsEAkbMtG5pJd9/LkoT8wT+WqUkdfwRUGupRJJw+zBHUozCkJJODgHMWSTgZK5JGclWvXBgp6yquD0Tq0FbTiQpzAmORBzAgjYqy5wwz19CCRfM2rtPtLtTzuTqEI48j39NFLdRtNFzKo22OdRYkxuNGrG6pIVPRxj8RrR244mIGDKzxdbqmiWnulKR49NKJEOPtAggfj0/E6YvEEcJiuVArPEvJXUwXq0LDzJ8+UsvzXV+u9uStt8tMyjlkXY+h7apdgMhtFRQyRgz2uXmUnvDIxyPkHB/9+sw25c+4m1eAcQykcckavEQ0bAMrDuCMg68anxvprhM5oprex81E/Kme8Tbxn5DzL/2aKMg+EjXcy+JXb1AeUTx5DjuOx3wf9/e1eL4FvPCtt4hRcyGIR1GPXJB/JgR+OgMlsqK4NT0kMkshGwRckfP0/HR36LlaW03Ww1asoD86o2QV5hhh8gQD8zqw9Syta7Xx8zO+IbHV/XUv1hcQXeFcMpOEq4x/y37Z68rHp0Ox1b/o7rk4tpf+GKU9TEeWqgm8rwsOq8vX/fXGCbnaeFLfROstfJ9blG/KVxGD68vf8dQuN+FJqisj4m4XKU18plAKg8qVcY/5bdgw+yx+R2O2bKRzDFr3DDSVVcP/ALHiFwhdqllPLUqVwGjPXb0HX89WmlWCOGKSnREjKgYQADHbQLgXiql4mtzpIhgr4SY6qlkGGRhsdjv8x2/ImVaKj6lcp7LN8IXxKX+KM9R+BzrZCMZE0VQh4h7S1xCTgqTkrt/bUSsutHTBw0gdk+IL0X5nov4ka6XA7msrn0oWE3K0C4UqA1lFlgPvp9pfy/rr57r3gtEzqyyGyVLc7+Qn6jKerr/AftL26jbpsPGn0tWe3JJBT1K1MuD+6pSGP/c5HKPwB+esJpL8aq9VC1KGKirHOEzzeCxPlOT1HY/hrbT5t6H6xdq2rQ8nv2hmnvpStqaGbmWsSNXRgcrKgHlkXbfYnJ7gk9c6JxxR1IWSZ3qARkeIdv8A29P01S62mNA4pqqRoaeFyaWpUZNC57Ed4W/+x+WxsViu/ic0NaPDqsk+Cik4IxnGMjBzkHoc6M0zYGGPMCsr916lihVQOUAAfLVe4xtlRzRXa3Ex19JkoVGedOpUjuPb0z3A0XjqKiT/AA4VjB7yHJ/If306KbxV55pndgQQAcKPkB/XRFtYdcTJX2mUyquNLc6c14gKVEeI6uHm2ifsduqnpnPpoM9wmLNHH+7VuoUco/ufx1I4utc9ivP7RoVHgVAKMh2Q53MZ9j1B7H5aHQgVUHj058ucPzkKY2+62TgHVKRziwyuoHG5BG5cybM3QggDbHuMd9OwMzyiORf3vLkco2cdMgeo2yPf0OvD9XhGZZeZvup0/M/0zpias5uVIIxFytzK6DdW9cnc/wAsaIbavNY5gy5b02HiFHgxtPIsJzkKd3z8h0/HGm6arWnRzCoaEHly4HNCxO23QK3Y78p276gKWnJy2GX4lBwPYj2P9xqRRSJS1QklhWWBhyzRdnQ9Rrqq1w3ZxIrLWduIMrxUR1L+PzPFJ8QJ+Nfc+o/nq5fRhNTxj9mBIo6yLMlMwUL9ZjO7IT94f2PY6D3SgaGRLc8iyQTgS2+pc4EiH7JP3hjHuR69RYqIKRwkTu1Sh5opgSvI47oOuR6n8tZ3V1XVcfVInmVvhj6TN8paygooBNNOkMb7rzbNzemOpPt1znVloPpAoZaJ7femSgpShVKqs+KT0CxfET88fjrAqTiSvqqF56JIKeqijUVU7MZJ3YkgPGDkqp2zjYHb0yzb6q5GUTpiGY7tPJ55T+J3H4aSLS4JBjEakVfTLjxZIz1EzUweSl5sx1twBQDfZkgA/VhpmisFwvnnuE804U4ZpzhFPosY6flqycMGhqqVKveoqx5ZxI3MQfUE7DQziPiehs9f4i1kYAUiWJTkN93BHQjf02Os95zjqUKPaciOXzh2Gqt9Nb65frklJ+8pHkYqZVX4omYe3f0wd+TBgT8TwQUpgsdsEAj8kslQngRRONiMdz6gZ3z11Urn9Jl3utXDS2KkepZJVdBEmfMD69P/AJ0Z4s4SHFFXQXVaiptIlIiuEBBBjbscduwztkEehOiTYGXd7jubjT9B5X+IOLqdn8OtuE1ylztTwZjiz8h5mH5aj2+38a8TxiG30P7Nt5PZeRfn7/Mkn21qPC/0f8LWJVZKE1U43Mkxzk/L++dXGFwqeHEiomMYA7aWvq2PAhNdaIOBMr4Y+iG3U7rUXmpkrqgb8ufKD8/7Aav9stVHb4hDR00cCdwi4z/fRhYiG5x0134IxzAaCcFzkzTMEXC3FInqo1JGAZ0UZLKOjj+JfTuMj01ItEiSRmNwnOoGcfaHYjRilU/iDtoPdaT9n1iVFKcRM3lUdEYndPke3odu+mFRFybD9Q6/4mJ9J+0K/VUePdRg6gzUfhk7bHpqfb3appllSRQjdgMkH01Ogt4mHKqvI56b5OhmTPGJZe4BjjIOpCICPfUq42+aj5WlQqrEgb9xqPD5SdSqw1na07tjqDy9NLXagEb6Wjcic2z5bpooaKIYfxahtiWHTTxWOkVKiuDySy7w0yf4k3oT3Vffqe2mbnMtlpKeqMST1VSC0PMMxxgEjJHc+g6amfR9d6ekvJrLlTNW1MrbTs2XQn0ztppY7WZb2EH09SghZbuGOE6ir5LlxEqcwH7mjUeSJfcf0/PQv6ROIfrU78O22QCNDy1kinbb/lj+v5djqx/SRxBPZLEn1MEVFWfDjk+5kZJ+fprKqOLlblz5ics3cn11lpd1jixuh0JvqnWpTWnZ7ksRogVEQbbAalUkDSyhEGSd29Md9MdFyd87Z0YtMtPSQeLKkjF/ukb/AOmnADE7EHJiey5a6yzHgQLeaeFzLTGQsOYZx0yO2g/1OS3wNPC5Z+y/EBq21M9NUykGmwp2XLZI/HbUastvh03iQyeQZPK2tS9um9JgKGjXKWHMqKXqWKQCsiKZPxLuNGYaqKWDxFkUrjJ36ajTW6KTMgwDjJBGx1Mslopwq1coDsRlVx5R7n1Omek1zbCzxXqPCq2cKnEmWileV/rcsZ528sSdSq/3OrLBTQ0QElYBJMRkRZ2H+b+2h1LclgJhhi5agjmEp3wPQa4SdmYlskk7knfQru1rEtHlNaUIFX2hJ55J5C8jc3ptjA0SsMBln8Ujyp0+egUUhyMd99XC1IlNblYjJ5QxI7k6F1HpXA94dphvbJ9oRhVUUsxCqNyToPfuIxFE0NI3IDsX9fYaF3y9TOHRRyojFeUd9VxpGmzJIc+ntorw3wjzvW/UWeMePDSDZWPVHKiraZix5vf1OuB0zjGuFJB205za9dTSlS7VE+eanVWah99hyZ5v7DXnUdddgDGde62WDZjXL765bCgkkYHXT3bUO4ScvkPRV5zjv12/TVLn2ITCNJV51oSC7rMxPhKfPJuR91dRFIVQFI99NqzSM8pO7H8h/sa7wMggdeulwE9ExHQ6Ed5WwCSCc7akU6FWOdNQ+bG5GNTY8DJIzjf+uqOcTWvBnoOAyZ3PXb8hqLXVstLMsUIVgo/eZ7n0/LRG3Is1YFftuffUG8Ww04Mwm5wxyeYb51WthvlrRurPxHqO5wTDlZvDf0bbUt5URcs2c9AO+q7HAshw241MhA8PAGABgb6Me8gRYugRzkHiSJZ3nBz5V+6NcUduqqxsQKcE45saMcN2Za51eVxy+mrtTU0NOojhQKAMZxvryvjPiZqUqO56rwvw5cAgYEC8N8MUtAoklQSSkbk6ssaDc9uw9NexAEYG2nIxjI14Z7Gc+oz1KqFGBPFBBydxpwYxsNehc9degY1cCcJzORsdM1lVBTRmSaRUA9T11Bv13FviwkZaRthnoNUyrq6iskMtRIWPYdhp74V4Q+q9bHCxB4r42mh9CjLQrdeIamZwtL+6jBBBI3Osh+l7iy6cQ3OKCuuElVDRKYoAcYUE+bGPU/yGrtfKx6S01E6jLomF9iTgH9dYpcJTLVOxzscDT3XUU6dBXWsVeB236y5r7WzIshwux36DR/gOi8SolrXXIj/dof4jufyGP/dqtyHIz6HWjcPwJb7PCFAJSHxW/iYjm/sPw0gXlsn2ntfpTHzBnG9YqRilVunlOPzb+g1TaUGWo5idhudEeJah5a1+Yny+X+pOolGuEDHctrF2y2ZofSks3CVIZJ2mO4Gw/wB/lq6IOWI4zofwdRRCmCnI5gNx6k6JVEZR2iOMqSNtVXuJrrMsRI75AznOm99znXTfFjXh+PGrzHcI4khwDncdRrvmMnIn3jg/LTLqANvXXtK+Z2OPhXb8dE6Yb7AIJq3CVsRCiyb7HbXktSq+XJLHoo66FVNZJzmOLy4+Jj/TRHhy0Gv+sVBnMcUADSnGXb5ac360VekTz2n8P8whm6ntNDWV0vhIjSN/00Hb3OjdNTQ2+Bo55jNM32EOUT8e5+W2vBUiCHwaSMQx9wDu3zPfUfruSSffWFOlfVeuw8QnUa2vRf06hzJSFGB5Ty47NriQBdzpsN5emuZZG5CGOR+urajwzaN1Z/SZ6Txjcdto/WU/6TK0RWyKlXHNUS5P+Vev6kazxGPNnOw1YvpHmJv3gfZhiUD5ncn+Wq3CS/oMkDSVxgEGe20KjywRJ1GpKcvXmwPz3P6DVz4TtdTcaueClVfEWHlyxwFLEKSfwJ1VqBQ08YI2JZvy8o/TWo/RkEpbRcbljLBycD0Rc4/U6EucqnEOtPplUuFvgorNeCeSok+vxUNPJjGSvMzkD/sA/wC7WocBcL3SutLS0sISmLcgml8qkIFjGO5+Enb11W7PboKhOHKWdQ6tC1wkyNnkkkUA/gBj8dfQoUUtmiijACxQ5wNs4XOh1uO6BXnjEzmKxUK2SDnJM010UhgcKwTmbp/lQ/nrReHbw9HAaC707wJCMJIwwRv6dToBw7DT1VRZUlTIUySH8WVB+QY6sP0x36hHDtJXVNJKiVM4ipjDjxWIOfOx+FdugDH3Gqmwk8wVV4JEEcR3kUnHdwrKcvOKC0IsZjQued2LnYe2NdUv0j2mmsDszq88SAmOEjLsB0LdFJPpk6q/A93dLvc6uKLmllp2dg7nlCrjr94+XYbfPWe8R3WnuVzmq4KUReK5MjYC85H8I2Ue259SdFK3mjYw/IwUBlfK8S0cQ8b3O41SIZXpKQReIaWNiVLY2JJOXO3VvyGgcHElzq3NLPO0dPM48VwMucfePUj22GgFPIzLI7b58upVPgcmBjvoivSoXVfmS29q0az3AlhnuccZKUSMmOksmC/4dh+p99B7pcYYPPUS7t0zuzH+eg1XdJmrmo4FCMvxO39Br2z203K6iESfvZW5eeQ516GzU6fRLspXmecr0d+ubzL24nk9XW1pCqWgiOwC/Gf7aP2LhlkiNRXN9ShK5wRmST5D+p0ZoKehslSohhaWaJgskzYDe4QdF+e509ea2Ctrpp6SkNJTvgLEZmkPzLNuToHT1X+IsTnAh+o1Gm8LTAXn4/7kvhiaCyX+2haU0kEdXDJIXX94yBg2ST2xvtqw3O1pYaG8JWRSNPWTLTwJG2D4fMJGPyHKo9PMPfVFklllZpJJGdu5Y5J2x11sK8OQ3DiSonr5mljj5EVBtzYUZJPudV1eip0epqx+smh112v0t39hMxa1sI3ljcMkalmHRh8/9NH+H6GjgtoqHiVp3kIDEZwBj+udFeKKKlFBXLHCqKlXHHGB9nL4z+Wopi8KhiAOebLfmz/20B45cbblP2hvgumGnoIHuY7UVaiYgHmblAwO2gQzPUzMSSZJQvTqSwGr3wjwxFd6etq5ZuTw5I4kAHckZP5Z0Oslvo3oo6WeEGaa7RxJOmzIBNlj+SYHz0nUYBjgGe8Vsg4ftmYTKjpWPyZxylpmAf8ADr+GqhXxWw2+jSnWZa5Vc1QI8hxuuO+SOvQatH0gLPQ2e0QNP4iyW+OQYHLjnZmIPrqnRVM1ScSspWCmdIwFAwNz269ep1uDhIG/1GXT6O+HKS52QT1xLJTVfjrCvRyI8Dm9vNrV+GeHKKewR0vJ4FKk/OkUQCjHLjG3TVL+ieIf+EJm7+IR+ia1XhxOW2Ljux1Svk8wzR1qx5nkFBT0sDw0UMVOhYkqigZJ76qXHMZ/a9lpyu7zkn811e2Ub+51V+KYRNxRY1OMIzNv8xrQjiGahAE4gSxwQte6yqMaGZpXBfHUDtqxLJhEULg+vrqrcB1X1u615RSI1qZky3xEiQj8ttWm6eFR0EtZKGZI15iF66ogzmY0KAmZH4ouJpbFXOcBo4S2wDH5Y1glt4kqqL6UKFTPaoIqW38qzVM6oORfFYeK+cqQSRsC3KQQDkZsv0lcZ1dLYanlXwI54SyCNQ5C56tnGT7DA99fLnFt3qLjcZ6iRi/MwAZwvMV3xnA6/wDx20VWm6ozDdnUCHLrUmT6QPrsTxsZKuaRTGOdDzcxyueo9M9tGEuEkRTw5GjkiGI+Tbl989++qhTt/wDTlsxkZI6H+HViqpFidV5eZmOF9NG6UDZgwHxQFrRj4lytFxjqfA+syRRySnCESLhyMdRnK9ds7HfGilaB9dwfQA/PWcAySTAyOFBYeSMYHX89Wq1XOSW4wW2oBdn5Uilzup7BvUe/UaG1FSgErLaV2wA55lkpBzRP7DbXEAALKwx766oD5HHptroDdh7HQ7ngQtT3I0KhLoAwBU+ugF7toFXLyYDo5UNj36H++rANq9A3mY4wfTXN4QCqlkA6t0/X+us1chZVwGPMHfR/ejw7xLFWV7VCwAMjGJsSAN3U+vv89fQP0HXiin4Y8DxH2k8pcdASeXJ6ZP8APXzrXUsbQvIfhUg8vofY6P8ABXFlbw3RwmMl6cuQ8fXI3zsdj0Gx2Pt11ouGBMyrs8lwfaav/wDfIURkttuqQu48aPPzUEf/AGus6CS1lFbngUtIyyQgDvsrj9WOtL4trBfrBa4quLNM9eIj5jzq4U7D1Ug99x79dVWlMEVDbooY+Q08qKSBjO7An/7EaHH1GEXuC5Ig6WxyraKiC4hSsqh2AOeQK6M2f+3n1n1ZZ6eNrHNBTxzxxgRVMUiYVuSVl39QVCg62iqiE3iU5/5qPCT/AJkKZ/8Ass/hrMpJDHzuoHlq3Kg+/K2P/sjrOvOQZQNiVvj/AIVuP0eXWVqOklltE0gaotcrHmhOdniYfLZh0wM+xXhTiiNoI6+nqxUUbyZMrsqMsh6iXO0Uv8ZxHJ9vlP7zWm8dVNVfLbR3C4Okq00sMyRcgCjzDPvuNYVxJYZuHJJL3YqiOAwROKuB1JiqFSXwyCvTfY4/lqpwBiHU6nPpaarDEk0czq+Y5WcboysjjdlZT5lYHGVO47ZGCe5rTTrD9YiMcEoBDF25VIKfkDlT/XVH4JvjVVNaamhQxQXKpSgjhmPN4chblWNiN3hydjs8efLkZQ22skjudqobqgkWOWNnSN238kjKwYjrhlbBGMjBwvTXQ+Ww0H1elKKXTqQ6iohkssVPVDmYKVRxsysPfuNxkaD0dxD1ERjQQ+AqCTfPOQ3KD+R09dYxPRuBhAsnMMds9tV1mVZ+XlJdc4bPTTFRzmIbG2nJkq61EjVs6zZLeIRzY6jsfbXVBIGo6mmJyGTmwfUHOubsc1r9g6K5Hvj/AE0xaT4dwCHzAty/gRrXaOsSq3MG3e8B8zRSDlLEBj36b/pqw8NpHUUdXzzr4sQbkjGBzA9T6nQWtgWOolUnIVsHHfXMEqxOwMQdehQsQD+I31hjBjHJYAiRI4/q9ZKhPL4b4Udds7f01a+DLtTW29LNUci0s0TxylhkdMj57gaqtyAWvhkx/jRgsPcbZ/TVltFla5Xy1WmOYRvWzRxo7DIXnOxPyzrtleQQZyxuRj3k273e0y3mlq7bA0IRyszAYV0bbp7ap3ENCKG9VMJ5VQvzL8juNF+L6N7DxfcOHBIspo5zCZQOUOMZBx17jvpni1frNut1c5/etH4bH1xvn9dVRNgKCa0MccypTPHBUhkyxVgwz0/3jV/+jm4yLXGgcK0UkbQhidwRun4bD89UeaAPIhAGWHfVs4Bt89Xcvq0M6xNGEctjckEjr+A1lZZsG4w3aXT8pPkpUpq+WGRsKr+TG5ZTuD+WrPw5w3drwo+qUxp4e8z7ZHz/ALaN8PWi2txk0FVTCcvSyPGWOyMg5ht32yNaDTTBEUIoVQMBQNhrCzUtuwsolQIyYDsXAlotgEtQDU1A6Mdgp9u+ueDYTSV18szMQkhWriHuDySfoyN+GrFLOz9NtD7YRS8aW+tChiXWNwftK55CP/sgfw1ZCcHMucAjEK2PhusuX7wUxUA4Mkwwn4eurRDwZbFCtXRisdRsGGEH4D+urbtjAGBpqToRq+wQ9aFEpnFnC1JdOHay2xwAGSIiMH4Qw3G36a+YrbS3LhKOqrqZpnoKGrMdTCqkyUKvllkUdWibzhl7FSw6kH7DnGRjWJcc26O2/SaiREeDd4/DlTG2WyVJ9cOpPyYjVSoIImbt5RyJC4fvFNdqYSQuhflDEK2Qynoynupx1+Y6ggHqSQq4YdV3GsevcB4LuNJX2+Vo7bWVQi+rruaaV/tR9MoxHmTI9QQcY07h24G40TSvH4csUrwSgHKlkYqSPbKnsPkOgqrH6TMrawRvWX+lkWWEN2YZGqdfqZLXxZT1xU/VKpTDUgfcbYn8Dhv+zRO2VckDAElk7rqVxPRCst4wQHU+Qnt3/pqKdrTDMiW3h66wXqGpFFIIW5qWeRvKmCfI2T1w47Z2c6vFs4QUNz3CUMP+nFkA/M/213wxWtcuFx9aBbMJGR1wNv7H/wCNHrHVGstdPUsMNJH5vmNj+ur1oMxnXWp5jlLSU9LCIqeJIkHZBjVTuUP7D4xiuK5WlrR4c2Btzb4/376upGRobxHQpXWieBzysF5kb7rDcHWpXidsQbcj2nssDPJ4gcDftpyFChZi2Seuh3CFY9fZY3kGHj/dt74/+dMcQX5bdN9TghLTtG8vM3wqqjJ9yfQbfPWe4KMyKcjMDcfcLVjVQ4p4Yk+rXunXMqAgLWIPsnO3OB0J2PQ7YIBS/SDa77wzTXaKWOjuVBKvOHfAVySpTHUhsEb4wRg7jVB41+luvqZTTUNNzH79UAyj5Rjy/nk++sxl4gucF3qbxUz/AFkz71iOu0q7Dp0zgKMbZAHQhSOJU9gLqOJk96Z2Z5m28SfSykFQYaSnmFWfLPC48OEkjZgQ2TjAHYENrNuI+KL7enK11awgXPLBH5Y1+SjbXPFsEc1sorpGCpbMTA7tgM69e+DGd+4I6dNBxvRx1MrN5vLhepIJHf5aY6bTU43tzF2q1NxO0cSM5xpcrZzJyxqfvbE/IddNVlW0RKxoE9x1/P8AtjQ5nd8l3b5A6ZK+PSgim0gepjmXy31Ud3tDIzCWspByMrAZmiPYjffGfnv7ar1RDJa6unq6d8QxSD6vK2/hZ/5Tk/YOSAe2cfOJw9VvR3NJ4iw5fKwB6j+/f5jVxucMSShWjVoalSXiI8vUqwx6ZH66FtqKnPvCtJqhYp+JYKKeOopo6hAQsihgD1HsfcdNSWqY6ePmlkVF9WONUayVU1uvUXDck0stPMrSUzhsNGO6se49D/s2uCngV+YRgt3Y7k/jrWq/ePvL2LsnNzEFzpnpWpZJoZBhmI5ce4zvkdRtrMrpSVNuu80XhKJlQAhNhUR74/7sdD2II1sMYAXYYGqx9IFvjltbVykJPSedWA6qSAV/M5Hvn1111B7kVyORM85ElUTI3OjbqT+oI7EemukRiwAUlj0AGc69nX6kgryA0ExBlhHc5xzD0Iz+I29Nd1NVMryQpyR8px5Byg/PufxOtq9UE9OORBbtNuO4HgyR4Bjw0kqRTKCUX4iR3DDsD7/2059chFOJKaAB84Yvh2VvTpgexx00GTmZ8sxPt0GpuBEvjqBjHmXsy7nH88H/AFzyyt8ls8TtdiEbRDlqmbiC3zWCvkAnJMtvmdt0lxuhPYNgfI4OqxLFI9Q6VCFKuMkNkYLY2P8A3DuPx0SlHgOJY2IK4ZT3HQj+Y0U4qpomo4btOpE8ijnMbY8+Nn3H5+uulVpHmrLI5tzW0B0EdQ0qy0YY1CZyVXPXqCPunvnROW9W6gpia+QpMG5TAp3U+nN0IPqM5H46FU9RWXB4aSnaKmik8sgQEcxzgn3/ABO2r1R/R/RWym/adQ6189KjTmGXIjkUAkqSNwcZwR0PYjIKrV6rzjuQYhen0y1na/MqlHc+Jr670nDltkggfZpCpUfMk7n8cDVs4f8AoclqStZxTcjLnB8FGyB/T+etKtIpGtdNJQwLT08sayRoFCkBhkA42zqUw5Rykk6Qvc7HuNANowJAsdltdmpxT2qiig2wXA8zfjru5UqlWqFj5yE5ZowM86fLuR1H4jvogIuYZDYGpMMYAA1Wqw1vuE4VyIGs8hOaSSTnZFDRydfETsfmMj9DozDFv00IuFMaWqXwGCnDTw7fAQQGX5Hm/VvXazWhEq6SOpxy+IobB7Z1tdWFbK9GVQ5HM4ghZhjGdPxUcnfYaK08Kqu2nWhUjmOqbOJoBmC1pVQ7b66kp4ZoHp5kDRuMMvrqYjIu3ID89ORIs0qxooDuTjJ21BlT6e5NmeJTYxNZ7g6M7NE25bHxDs3zHQ/novHNOrB45mGdwVbGrVJwzBUxYq5ecjdQowFP8zqoQRtSV81vZudUyUPp7a31CsV8z395zYU7nkodyWdixO+Sc6bAxqUyZyAdNmMDQByeZI0OYdjpac5tLVQ7CSf/2Q==",
"login-side-panel-top-left-radius": "0",
"gradient-start": "#003087",
"logo": "data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAPMAAABlCAYAAACYydVhAAAACXBIWXMAAAsSAAALEgHS3X78AAAFsElEQVR4nO3dQWgUVxjA8W+DEA+G7MnSHhq96EmSxRwLRuxNWoLHeDAWwfaULVTYU5P04kKg7lGp0M0hQg+laYs9VbKB3JqyEU/qJfHQUk8J5pCepnzjjmwymyXb7Hsz883/B4uyhmSS8Z+ZeTNvphAEgXRTKFWLIlLs8iEA3NoTke2gWdnr9lU6xlwoVc+IyJyITIrIcOwDACRhVbsMmpVGp68di7lQqpZbIRMxkE6LIlIOmpXt9qXbF3OhVK2LyA1WIJB6T0Vkoj3ogegvhVK1RshAZoyKyL7d7TDmQqk6ISIzrEcgU0ZbG+FQtGWusw6BTJppDVjLQKFU1RHrEdYjkFk6YB1umSdZh0CmhQ0XZOzuJltmIPOGBggZMOHEAOsRMOEUMQM2sGUGrCBmwAhiBowgZsAIYgaMIGbACGIGjCBmwAhiBowgZsAIYgaMOOH62ygOnZSx86dj7/fb9pt/ZeP5P6aX9cwHw+HLtc2/dsJXL8bOvyfFoUHny9ZvjfVXmVvmwziPWeNY+W4q9n6/rf75SiZuPTK9rNOfXpDZ2x/F3u+3+QdrMnd/rafPWrtzRS5d/DD2fhbs7L795aphR68sch4zkHbDpwbDX0T6mr39Nu7llReyvPIy/DMrOGYGDtC4b3xyQX769pps/vZFuEeUBcQMdDHy/rB8P381E1Gzm41M0eP5TqIBOFfH7VHUGnR54cmxB1tdIGZkylEG5iYvn5Py9XEnYevnbDycCpejtvRH7N+TxG42zNFBKz1bcHP2cTiY1W96TH3vqytS/+Zqqn50xAyz6r88k8kvf3T27ekg2cYPn4XXJ6QBMcM0PWd82HF2P4yeOx3udqchaGKGebWlddn6u7cr2nqhQS/fu5b4j5GYYd72m71wl9slHRir3fk40R8lMSMXXMesZqbGw5H0pBAzckEnjjx98dr5t6oj3EkdPxMzcsPHddZ62konnSSBmJEbvmZD6SkrH1NVDyJm5Eavc7SPY+5z91NVDyJm5IbPmJPYOhMzckVvDOGL71lWxAw44vs0FTEjV/T+a77olWE+d7WJGbniex7yxLi/+6KZmc+svwGPO4KYxOkE2Obz/5SZmPVOED7uXAn0wueWmd1swAhiBowgZsAIYgaMIGbACGIGjDBzakonnpcXfo+93wu9kbreQhXoF58PoTMTs97nydLjOWGDz5la7GYjV3zf0sfnBoaYkSs+HqYf0UM/tsyAAb6f7UzMyBWfEx983N63HTEjV3RCjg8/N1563cUWYkae6KlHX5J43CsxIzd8DX4t/voskdOkxIzc8DG3WJ8HXV54EnvfB2JGbviIefrrx+EFTEkgZuSChux68Et3r32fjmpHzMgF1/ew1gtEdKucJGKGebpV1idMuKIhT9x6lPiPkZhhml6LrY9ZdSUKOanj5HbEDLP0vHLj4ZSzY2U9Rk5LyGJpCiQQ0YjL18ed7lrPP1iTuftrsfeTRMzIFN3SdnPpotvTT9FAl+8nYxwFMSNTXMd6GL0YRLfESVymeVTEDHShEWvAtaX11BwbH4aYgQ501pNeAOJ7GuNxEDPQegj7xvPX4QQJfaV9K9xJQcbuBh3e7xs9z+djtoo+d/e4gxJpX1adWO9jcr3Ow+11Lq6OIBeHBmPvp93/+V5T6qzzmAF4cZaLRgAjiBkwgpgBI4gZMIKYASOIGTCCmAEjiBkwgpgBI4gZMIKYASOIGbBhj5gBG8KYt1iZQOaFMTdYj0CmbQXNShhznfUIZFrY8EDQrOiWeZV1CWTSzruYW0tfZj0CmTQXNCubEsUcNCsbInKTdQlkymLQrNSiBX53aipoVuoEDWSGhjzdvrD7zjO3gr7M6Sog1eYPhqwKQRC/OWehVC3q86lbx9IjsQ8A4Fs00FWLjpFj3XaK+UDYJ0VEX8XYPwJwTe/Gvxs0K7tdv5CI/AcWjrxEPw4iaAAAAABJRU5ErkJggg==",
"login-position": "right",
"login-side-panel-top-right-radius": "0"
}
}
}To protect against Cross Site Request Forgery (CSRF) attacks, the HID Authentication Service generates a server-csrf-token value attached to the request for each call, ensuring that requests to the HID Authentication Service only originate from trusted sources.
This value is passed to the portal after the first step authentication is validated (or during redirection when the portal is on same domain as the back end).
On the HID Authentication Service back end, HID Authentication Service checks that the server-csrf-token attached to request matches that of the request parameter (passed back by the portal in the body or header).
Authentication Workflow
The Flow endpoint retrieves the workflow defined in the client application configuration (workflow_id) to authenticate the user and is called before the interface is displayed to the user.
The workflow configuration defines the authentication factors (first and second) and associated actions.
The interface display is filtered based on access criteria so the user can only select the relevant authentication methods, including conditioning for the first and second factors.
Sample Request
GET https://[base-server-url]/<tenant>/authn/flow?request_uri=urn:hid:43d5b009-7b52-4d6f-a8a9-0d8de27968f9
server-csrf-token: urn:hid:256ab6ef-12c4-47e3-b220-0e96c161d283
Content-Type: application/x-www-form-urlencodedHID Authentication Service validates the access criteria based user context (authenticators, devices, ...).
Sample Response
HTTP/1.1 200 OK
Content-Type: application/json
Cache-Control: no-cache, no-store
{
"actions": [
{
"actionId": "action.change_password",
"accessCriteriaId": "access_criteria.common_to_all",
"type": "CHANGE_PWD",
"retry": 3
},
{
"actionId": "action.forgot_password",
"accessCriteriaId": "access_criteria.common_to_all",
"type": "FORGOT_PWD",
"validityPeriod" : 900,
"retry": 3,
"resetPasswordMethods": [ "email", "sms" ]
}
],
"firstFactors": [
{
"factorId": "factor.user_password",
"accessCriteriaId": "access_criteria.common_to_all",
"code": "AT_CUSTPWD",
"type": "LOGIN",
"retry": 3,
"expirationWarningThreshold" : 259200,
"constraints": {
"minLength": 1,
"maxLength": 50
...other constraints...
},
"actions": [
"action.change_password",
"action.forgot_password"
]
},
{
"factorId": "factor.pki",
"accessCriteriaId": "access_criteria.common_to_all",
"code": "AT_EMPPKI",
"type": "PKI"
}
],
"secondFactors": [
{
"factorId": "factor.push_authentication",
"accessCriteriaId": "access_criteria.common_to_all",
"code": "AT_PASA-2FA",
"type": "PUSH",
"retry": 3,
"pollTimeout": 30,
"pollInterval": 2,
"okStatus": "approved",
"upon": [ "factor.customer_password_with_reset" ],
"devices": [
{
"deviceId": 15168,
"deviceFriendlyName": "my phone"
},
{
"deviceId": 15169,
"deviceFriendlyName": "my laptop"
},
{
"deviceId": 15170,
"deviceFriendlyName": "my tablet"
}
]
}
],
"enrollActions": []
}If the user does not meet the access criteria requirements for the requested resource (for example, they do not have a required authenticator factor), a workflow template cannot be applied and HID Authentication Service will return an error and maintain the error in the PAR context.
Sample Error Response
HTTP/1.1 400 Bad Request
{
"error": "no_template_found_for_criteria",
"error_description" : "User does not meet the access criteria, no authentication template applies"
}Authentication Portal Design
The Theme endpoint retrieves the design for the portal interface defined in the client application configuration (theme_id) and the returned value is the content from the payload.
Sample request to retrieve the theme
GET https://[base-server-url]/{tenant}/authn/theme?&theme_id=ID_THEME1&request_uri=urn:hid:43d5b009-7b52-4d6f-a8a9-0d8de27968f9
server-csrf-token: urn:hid:256ab6ef-12c4-47e3-b220-0e96c161d283Sample response
HTTP/1.1 200 OK
ontent-Type: application/json
{
"ui": {
"hid_portal": {
"gradient-start": "red",
"gradient-end": "orange",
"logo": "data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAVWZqWNWH.....<shortened>...LVjB1zBZk1nJTi/LYLKyb3YxefWSOu1b1t9HnOP+eHXbHZnV95bz0evVCtToyzZqNaY6q1UK9dy/UNmzYsGHDhg1C8D/J9batc1Yi+wAAAABJRU5ErkJggg=="
},
"extensions": {
"mycustomelement1": {
"color": "red"
},
"mycustomelement2": {
"color": "orange"
},
"mycustomelement3": {
"mycustomlogo1": "data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAVWZqWNWH.....<shortened>...LVjB1zBZk1nJTi/LYLKyb3YxefWSOu1b1t9HnOP+eHXbHZnV95bz0evVCtToyzZqNaY6q1UK9dy/UNmzYsGHDhg1C8D/J9batc1Yi+wAAAABJRU5ErkJggg=="
}
}
},
"localization": {
"hid_portal": {
"fr": {
"service_name": "Mon service d'authentification HID",
"service_tagline": "Construisez et délivrez rapidement vos solutions d'identité de confiance",
"company_name": "Mon HID Global",
"application_title": "Mon service d'authentification"
},
"en": {
"service_name": "My HID Authentication Service",
"service_tagline": "Rapidly build and deliver your trusted identity solutions",
"company_name": "My HID Global",
"application_title": "My Authentication Service"
}
},
"extensions": {}
}
}Authentication and Authorization
The Code endpoint provides the session transfer/authorization codes after the user's credentials and consent have been verified.
The following samples illustrate the successful authentication flow (password and OTP) and consent verification.
Sample request - authentication with password as the first factor
POST https://[base-server-url]/{tenant}/authn/code
Content-Type: application/x-www-form-urlencoded
server-csrf-token: urn:hid:256ab6ef-12c4-47e3-b220-0e96c161d283
request_uri=urn:hid:43d5b009-7b52-4d6f-a8a9-0d8de27968f9
&grant_type=password
&authType=AT_CUSTPWD
&username=5619630280
&password=54917067Sample response for successful first factor authentication and step-up required (second factor)
HTTP/1.1 400 Bad Request
Content-Type: application/json
server-csrf-token: urn:hid:256ab6ef-12c4-47e3-b220-0e96c161d283
{
"error_description": "Step up required",
"error": "step_up_required",
"secondFactors": [
{
"factorId": "factor.cust_pin",
"acr": "1",
"code": "AT_EMPPIN"
"type": "LOGIN",
"upon": [
"factor.user_password"
],
"constraints": {
"atLeastOneUp": false,
"atLeastOneNum": false,
"notBlackListed": true,
"atLeastOneLow": false,
"minDiffChars": 5,
"notOldPassword": true,
"minLength": 8,
"notUserAttribute": true,
"characterRange": "onlyNum",
"maxLength": 100,
"atLeastOneSpecial": false,
"notSequence": true
},
"accessCriteriaId": "access_criteria.common_to_all",
"retry": 1
}
]
}Where:
-
HID Authentication Service generates a random server-csrf-token value attached to the PAR request which must be passed in the subsequent requests and responses by the portal (step-up, consent, redirection etc) to prevent CSRF attacks
-
expires_in is the validity period (in seconds) of the authenticator and a warning will be displayed before expiration based on expirationWarningThreshold
Sample request - authentication with OTP as the second factor
POST https://[base-server-url]/{tenant}/authn/code
Content-Type: application/x-www-form-urlencoded
server-csrf-token: urn:hid:256ab6ef-12c4-47e3-b220-0e96c161d283
request_uri=urn:hid:43d5b009-7b52-4d6f-a8a9-0d8de27968f9
&grant_type=password
&authType=AT_CUSTOTP
&username=5619630280
&password=41096522Sample response for successful second factor authentication but the user needs to sign the consent
HTTP/1.1 400 Bad Request
Content-Type: application/json
server-csrf-token: urn:hid:256ab6ef-12c4-47e3-b220-0e96c161d283
{
"error":"consent_required",
"error_description":"consent not signed"
}As the user is required to consent to the sharing of their data, the Consent endpoint is called to retrieve the consent prompt containing details of the information that will be shared:
Sample request
GET https://[base-server-url]/{tenant}/authn/consent&request_uri=urn:hid:43d5b009-7b52-4d6f-a8a9-0d8de27968f9
server-csrf-token: urn:hid:256ab6ef-12c4-47e3-b220-0e96c161d283Sample response
HTTP/1.1 200 OK
Content-Type: application/json
server-csrf-token: urn:hid:256ab6ef-12c4-47e3-b220-0e96c161d283
Cache-Control: no-store
Pragma: no-cache
{
"consents": [
{
"clientid": "spl-idp2",
"sharing_duration": -1,
"description": "spl-idp2",
"sharings": [
{
"scope": "openid",
"description": "openid",
"status": "accepted"
},
{
"scope": "profile",
"description": "User profile",
"status": "unknown"
}
]
}
]
}Request to redirect user to SP with authentication successful and consent verified (or error at any step of the flow)
GET https://[base-server-url]/{tenant}/authn/code&request_uri=urn:hid:43d5b009-7b52-4d6f-a8a9-0d8de27968f9
server-csrf-token: urn:hid:256ab6ef-12c4-47e3-b220-0e96c161d283Sample Response
HTTP/1.1 302 Found
server-csrf-token: urn:hid:256ab6ef-12c4-47e3-b220-0e96c161d283
Location: https://api.mypisp.com/cb?
code=SplxlOBeZQQYbYS6WxSbIA
&id_token=eyJ0 ... NiJ9.eyJ1c ... I6IjIifX0.DeWt4Qu ... ZXso
&state=af0ifjsldkjFor further authentication flows and code samples, see Code Endpoint.
Enable FIDO Enrollment and Authentication
As an integrator, you can enable the APIs to deploy FIDO enrollment and authentication workflows for a custom front-end application where the device is then activated and associated with a user in the HID Authentication Service.
The FIDO flow is more complex as it requires managing the communication between the passkey, client application, customer back end and the HID Authentication Service.
The flows below are illustrated using WebAuthn although this is not mandatory for custom flows. The only requirement is that the format of the objects passed to the HID Authentication Service back-end APIs is respected (see the relevant section below).
Framework Guidelines
In this use case, the application framework (front end and back end) requirements are:
-
The client-side is responsible for the communication with the FIDO authenticator
-
An authenticated OpenID client performs the calls to the API endpoints
-
A workflow configuration is defined for the OpenID client (see Create the Authentication Workflow)
-
A component capable of interacting with the FIDO authenticator device leveraging the WebAuthn objects used by the API, for example:
-
Running inside the browser (for example, a JavaScript component on top of WebAuthn)
-
Directly on top of CTAP2 or using specific platform API (such as FIDO platform authenticator)
-
-
The enrollment process is protected (for example, by pre-authenticating the end user using another authentication factor)
The following sections provide guidelines for the enrollment and authentication flows.
Custom Application FIDO Enrollment Flow
Create the user (see the Users endpoint)
To implement the devicebinding option, you must also create a pending FIDO authenticator for the user
To protect the enrollment process, the user must have an existing authentication method
-
Authenticate your OpenID client for you customer application by calling the the Token endpoint to get an access_token to be used in the Authorization header for the following requests.
-
Start the enrollment process on the customer back end using the PAR endpoint.
-
If EnrollmentProtection is configured, authenticate the user using the Enroll/code endpoint.
-
Send a request to get the PublicKeyCredentialCreationOptions (the parameters required to create the FIDO authenticator):
-
On the customer back end, get publicKeyCredentialOptions from the HID Authentication Service back end using "enroll_step": "getcredentialoptions" on the Enroll/fido endpoint.
-
On the customer back end, send the returned publicKeyCredentialOptions to the customer client.
-
-
Create the new credential on the FIDO passkey:
-
On the customer client, send PublicKeyCredential = navigator.credentials.create(publicKeyCredentialOptions)
-
On the customer client, send the JSON-formatted PublicKeyCredential.response (authenticatorattestationresponse) to the customer back end.
-
-
Register the FIDO credential (credential ID and public key) on the HID Authentication Service back end:
-
On the customer back end, register the authenticatorattestationresponse on the HID Authentication Service back end using "enroll_step": "registercredential" on the Enroll/fido endpoint.
 Format of the WebAuthn enrollment object
Copy
Format of the WebAuthn enrollment object
CopyCommented WebAuthn attestation object
publicKeyCredential // the WebAuthn credential containing the response attestation from the device, see https://www.w3.org/TR/webauthn-2/#iface-pkcredential
id // the base64-encoded string ID used to identify the newly generated credential during authentication
rawId // the credential ID in binary
type
response
clientDataJSON // a base64url-encoded JSON of client data, see https://developer.mozilla.org/en-US/docs/Web/API/AuthenticatorResponse/clientDataJSON
challenge // base64url-encoded 32 bytes of randomly generated UUID
origin
type
attestationObject // base64url-encoded bytes of CBOR ArrayBuffer, see https://www.w3.org/TR/webauthn-2/#iface-authenticatorattestationresponse or https://developer.mozilla.org/en-US/docs/Web/API/AuthenticatorAttestationResponse/attestationObject, containing:
attStmt // the attestation statement used to verify the credential public key came from the authenticator, see https://www.w3.org/TR/webauthn/#attestation-statement
authData // https://developer.mozilla.org/en-US/docs/Web/API/AuthenticatorAssertionResponse/authenticatorData
rpIdHash // the SHA-256 hash of the rpId for the credential
flags // bit-based indicators about user and authenticator data
signCount // 32-bit unsigned big-endian integer of the signature counter
attestedCredentialData // variable-length byte array for credential, see https://www.w3.org/TR/webauthn-2/#attested-credential-data
AAGUID // 128-bit identifier representing the type (such as make and model) of the FIDO authenticator
credentialIdLength
credentialId
credentialPublicKeyThe clientDataJSON and attestationObject arrays must be sent in the exact JSON format as in the WebAuthn response in the request (credential parameter) to register the FIDO credential.
CopySample request to register the FIDO credential with the WebAuthn attestation object
POST https://[base-server-url]/{tenant}/authn/enroll/fido
server-csrf-token: urn:hid:256ab6ef-12c4-47e3-b220-0e96c161d283
Content-Type: application/x-www-form-urlencoded
{
"request_uri": "urn:hid:43d5b009-7b52-4d6f-a8a9-0d8de27968f9",
"enroll_step": "registercredential",
"username": "testfido",
"enrollId": "enroll_action.fido"
"credential": {
"clientDataJSON": "Y2xpZW50RGF0YUpTT05jbGllbnREYXRhSlNPTmNsaWVudERhdGFKU09O..",
"attestationObject": "YXR0ZXN0YXRpb25PYmplY3RhdHRlc3RhdGlvbk9iamVjdGF0dGVzdGF0aW9uT2JqZWN0YXR0ZXN...."
}
} -
On the customer back end, send the result (success or failure) to the customer client.
-
Custom Application FIDO Authentication Flow
-
Authenticate your OpenID client for you customer application by calling the the Token endpoint to get an access_token to be used in the Authorization header for the following requests.
-
Start the authentication process on the customer back end using the Par endpoint.
-
Send a request to get the PublicKeyCredentialRequestOptions:
-
On the customer back end, get publicKeyCredentialOptions from the HID Authentication Service back end using "grant_type": "fido_challenge" on the Code endpoint.
-
On the customer back end, send publicKeyCredentialOptions to the customer client.
-
-
Get the enrolled credential (registered on the server):
-
On the customer client, send PublicKeyCredential = navigator.credentials.get(publicKeyCredentialOptions)
-
On the customer client, send the JSON-formatted PublicKeyCredential.response (authenticatorattestationresponse) to the customer back end.
-
-
Verify the FIDO attestation certificate and signature on the HID Authentication Service back end:
-
On the customer back end, validate the authenticatorattestationresponse on the HID Authentication Service back end using "grant_type": "password" on the Code endpoint.
 Format of the WebAuthn authentication response
Copy
Format of the WebAuthn authentication response
CopyCommented WebAuthn response
WebAuthnResponse: {
"getClientExtensionResults": {},
"rawId": "Mb9UD5Mh3fVotLV1TBVV2d8F3GmYZmzp4t9za16dMjcnc9mq54sYVgLxDlKBl9iYQfqr22jEgIt1YYNZ5F8r04P6vPT8Rb_IDcR65KXyE86PZkf0UNE0N8W8SkuzMT3Sk837X7o7nUsX",
"response": { // the FIDO authenticator response containing a new authentication assertion, see https://www.w3.org/TR/webauthn-2/#iface-authenticatorassertionresponse
"authenticatorData": "zHUM-fXe8fPTc7IQdAU8xhonRmZeDznRqJqecdVRcUMFYfOzqg", // ArrayBuffer containing the authenticator data returned by the authenticator, see https://www.w3.org/TR/webauthn-2/#authenticator-data
"signature": "MEUCIHxzf1KZNJTb831gqw0oit-6ms8DoSXLaM8zyZ4Q6iyjAiEAwbguOZU2iJae_I8-Q7qlFwR45isZ-XYVMDgU2SkABU8", // ArrayBuffer containing the raw signature returned by the authenticator
"userHandle": "Kosv9fPtkDoh4Oz7Yq_pVgWHS8HhdlCto5cR0aBoVMw", // the identifier used to map the public key credential to the user account by the RP
"clientDataJSON": "eyJ0eXBlIjoid2ViYXV0aG4uZ2V0IiwiY2hhbGxlbmdlIjoiRjVjSmhMRW00OFNpdGN6MzNiVm51NXpBMmEtRk5MYkxGbURfd1UwT1BIUSIsIm9yaWdpbiI6Imh0dHBzOi8vd2ViYXV0aG53b3Jrcy5naXRodWIuaW8iLCJjcm9zc09yaWdpbiI6ZmFsc2V9" // a base64url-encoded JSON of client data, see https://www.w3.org/TR/webauthn-2/#dom-authenticatorresponse-clientdatajson
},
"id": "Mb9UD5Mh3fVotLV1TBVV2d8F3GmYZmzp4t9za16dMjcnc9mq54sYVgLxDlKBl9iYQfqr22jEgIt1YYNZ5F8r04P6vPT8Rb_IDcR65KXyE86PZkf0UNE0N8W8SkuzMT3Sk837X7o7nUsX",
"type": "public-key"
}The response array must be sent in the exact JSON format as in the WebAuthn response in the request (password parameter) to verify the FIDO assertion.
CopySample request to verify the FIDO assertion in the 'password' parameter
POST https://[base-server-url]/{tenant}/authn/code
server-csrf-token: urn:hid:256ab6ef-12c4-47e3-b220-0e96c161d283
{
"request_uri": "urn:hid:43d5b009-7b52-4d6f-a8a9-0d8de27968f9",
"grant_type": "password",
"username": "testfido",
"authType": "AT_FIDO",
"password": {
"authenticatorData": "zHUM-fXe8fPTc7IQdAU8xhonRmZeDznRqJqecdVRcUMFYfOzqg",
"signature": "MEUCIHxzf1KZNJTb831gqw0oit-6ms8DoSXLaM8zyZ4Q6iyjAiEAwbguOZU2iJae_I8-Q7qlFwR45isZ-XYVMDgU2SkABU8",
"userHandle": "Kosv9fPtkDoh4Oz7Yq_pVgWHS8HhdlCto5cR0aBoVMw",
"clientDataJSON": "eyJ0eXBlIjoid2ViYXV0aG4uZ2V0IiwiY2hhbGxlb...G53b3Jrcy5naXRodWIuaW8iLCJjcm9zc09yaWdpbiI6ZmFsc2V9"
}
} -
On the customer back end, send the result (success or failure) to the customer client.
-
On the customer back end, send a request to the Code endpoint to end the process (delete the context and get the result).
-
With GET, an authorization code is redirected to redirect_uri to end the process
-
With POST using grant_type=code_request to get the authorization code in the response
-
-