Computer Configuration\Policies\Administrative Templates
During installation of the DigitalPersona AD Administration Tools, the following nodes and settings are created under the Computer Configuration\Policies\Administrative Templates node.
Click the setting names in the following list to view the details:
DigitalPersona AD \ General
These settings are used to configure and govern general features of the DigitalPersona software. They are primarily applied to both server (SVR), and client (CLT), but in some cases are applied to only server or client as shown in the following table.
| Category | Subcategory | Setting name | SVR | CLT |
|---|---|---|---|---|
| Attended Enrollment | ||||
| Security Officer authentication | X | |||
| Require to complete or omit credential | X | |||
| Authentication Devices | ||||
| Bluetooth | Lock computer when your phone is out of range | X | ||
| Silent authentication | X | |||
| Cards | Contactless Card Usage | X | ||
| Allow enrolling only one contactless card per user | X | X | ||
| Lock the computer upon card or device-bound passkey removal | X | |||
| Allow the use of Contactless ID cards as a single (Primary) credential | X | |||
| Contactless (RF) technologies | ||||
| Face | Use Infrared Cameras for Face Recognition | X | ||
| Face Verification | X | X | ||
| Device-bound passkey | Device-bound passkey authentication | X | X | |
| Fingerprints | Redirect fingerprint data | X | X | |
| Fingerprint enrollment | X | X | ||
| Fingerprint verification | X | X | ||
| OTP | Allow sending OTP Push Notifications automatically | X | ||
| Send OTP by email | X | |||
| Time-Based OTP Validation Window | X | X | ||
| Push Notification Server API Key | X | X | ||
| Push Notification Server Tenant ID | X | X | ||
| Custom SMS or Mail Message | X | |||
| PIN | PIN enrollment | X | ||
| Recovery Credentials |
Recovery Questions:
|
X |
X
|
|
|
Self Password Reset:
|
|
X
|
||
| Allow One-time access code for Windows Logon | X | X | ||
| Windows Password | Re-randomize Windows user password automatically | X | ||
| Event logging | ||||
| Level of detail in event logs | X | X | ||
| User Onboarding | ||||
| Allow user onboarding | X | |||
| Proxy Server configuration | X | X | ||
Attended Enrollment
Security Officer authentication
Specify the occasions when the Security Officer supervising Attended Enrollment must authenticate.
-
If enabled, the Security Officer must authenticate upon those occasions selected in the Options area.
Options are:
-
When application starts
-
Every time when saving any credential
-
Every time when omitting a credential enrollment
-
Every time when deleting any credential
-
At the end of enrollment, before saving data
-
-
If disabled or not configured, the Security Officer needs to authenticate only when starting Attended Enrollment.
Require to complete or omit credential
Require that all specified credentials must either be enrolled or explicitly omitted.
-
If enabled, the user must complete the enrollment of all specified credentials or a Security Officer must explicitly approve the omission of any unenrolled credential.
-
If disabled or not configured, enrollment of all specified credentials is not required and omitting a credential does not need Security Officer approval.
Authentication Devices
Bluetooth
Lock computer when your phone is out of range
Configure whether or not the computer locks when enrolled Bluetooth device goes out of range.
-
If enabled, the computer locks when enrolled Bluetooth device goes out of range.
-
If disabled or not configured, the computer does not lock when enrolled Bluetooth device goes out of range.
Silent authentication
-
If enabled or not configured, when Bluetooth credentials are allowed for authentication by the Logon or Session Policy in force, authentication will be attempted with the previously used Bluetooth credential immediately upon entry to a logon screen.
-
If disabled, selection of a specific Bluetooth credential is required for authentication.
Cards
Contactless Card Usage
Improve the performance of Contactless cards
-
If enabled, all Contactless cards are used as Contactless ID tokens, with the best response time and maximum coverage of various types of contactless card readers and cards in the product. Some types of cards will be used in a less secure mode than is technically possible.
-
If disabled or not configured, Contactless cards are used as Contactless ID or Contactless Writable tokens, with maximum available security. The choice of Contactless cards and readers could be limited due to secure technologies they support. The response time could increase.
When changing the way Contactless cards are used, all users will need to re-enroll their cards. This does not mean that the cards enrolled before the GPO change must be deleted. If saved, they can be used again when the GPO is changed back.
For SEOS devices, this GPO is recommended to be set to disabled, which is the default mode. This allows SEOS devices to be used on any NFC reader.
If the GPO is set to enabled, then SEOS devices can be used only on the HID OMNIKEY 5427, 5023 readers. Also, the SEOS keyset synchronization must be done between the SEOS devices and the readers.
To use the HID Mobile Id smartphone application, the GPO must be set to enabled.
In this case ALL the SEOS devices will be handled in this way.
Allow enrolling only one contactless card per user
-
If enabled, each user can enroll only one contactless card.
-
If disabled or not configured, users can enroll more than one contactless card.
Lock the computer upon card or device-bound passkey removal
Configure whether or not the computer locks upon removing a card or device-bound passkey from the computer.
-
If enabled, the computer locks upon removing the card or device-bound passkey from the computer. The computer will lock only if the device was used to log on to Windows.
-
If disabled or not configured, the computer does not lock upon removing the device from the computer.
Allow the use of Contactless ID cards as a single (Primary) credential
Configure whether or not Contactless ID cards can be used as single (Primary) credential for login to computers and authentication when enrolling other credentials.
-
If enabled, Contactless ID cards can be used as a Primary credential.
-
If disabled or not configured, Contactless ID cards cannot be used as a Primary credential. They can only be used in combination with another Primary credential.
In addition to enabling this GPO, you must perform the following steps to complete the process.
-
Run gpupdate /force.
-
Close and reopen the GPO Editor.
-
Add the Contactless ID Card as a permitted credential in the Logon Policy GPO (for Windows Logon).
-
Add the Contactless ID Card as a permitted credential in the Session Authentication Policy GPO (For session authentication, i.e. when enrolling and managing credentials).
-
Run gpupdate /force.
Contactless (RF) technologies
DigitalPersona supports a wide variety of RF technologies when communicating with contactless cards and tokens. When a single contactless device can support multiple technologies, an administrator can limit the RF technologies to be used. This will help in meeting users’ expectation of how cards will work.
-
If this setting is enabled, only selected contactless (RF) technologies will be used.
-
If disabled or not configured, only modern popular contactless (RF) technologies will be used.
Face
Use Infrared Cameras for Face Recognition
Specifies whether an infrared camera can, or must, be used for Facial Recognition.
-
If this setting is enabled and the “Use only infrared cameras for Face recognition” checkbox is not checked, any IR camera connected to the computer can be used for Facial Recognition. If an IR camera is mounted on the front panel of the computer, it will be used by default. If no IR camera is found, any camera can be used.
-
If enabled and the "Use only infrared cameras for Face recognition” option is checked, users without an IR camera connected to their computer cannot use Facial Recognition. If any IR camera is found, it can be used for Facial Recognition. If an IR camera is mounted on the front panel of the computer, it will be used by default.
-
If disabled or not configured, any camera connected to the computer can be used for Facial Recognition.
Face Verification
Configure the False Accept Rate (FAR)
The False Accept Rate is the probability of receiving a false acceptance decision when comparing the faces of different people.
-
If enabled, you can select one of the following FAR values:
-
Medium (1 in 10,000)
-
Medium High (1 in 100,000) - recommended
-
High (1 in 1,000,000)
For example, if you select Medium High, on average, one false acceptance will occur when a face is compared against a hundred thousand other faces.
The higher the setting, the lower the chance of receiving a false acceptance. However, at the High setting, the system may reject legitimate faces.
-
-
If disabled or not configured, the value of 1 in 100,000 FAR is used.
Device-bound passkey
Device-bound passkey authentication
Configure the options for device-bound passkey authentication
-
If enabled, you can select one of the following device-bound passkey authentication options:
-
User verification and user presence are required.
-
User verification is not required but user presence is.
-
User verification and user presence are not required.
User verification is the process where a device-bound passkey verifies that the user is authorized to use this device. It can be accomplished through use of a PIN or through biometrics enrolled with the device.
User presence is not about identifying the user, but ensuring that the user is physically present and in control of the device-bound passkey. User presence can be confirmed by touching the device-bound passkey touch sensor or by presenting an NFC device-bound passkey authenticator to the NFC reader.
-
-
If disabled or not configured, user verification and user presence are required for device-bound passkey authentication.
Fingerprints
Redirect fingerprint data
Configure whether or not to allow the client computer to redirect fingerprint data to a remote Terminal Services session.
-
If enabled, clients can send fingerprint data to a remote computer. This configuration must be enabled to support fingerprint authentication on a remote desktop.
-
If disabled or not configured, fingerprint data redirection is not allowed.
When an administrator changes this setting, only new connections display the behavior specified by the new setting. Sessions that were initiated before the change must log off and reconnect to be affected by the new setting.
The Do not compress fingerprint data for redirection checkbox specifies whether to compress fingerprint data on the client computer before redirecting it to the Terminal Services session.
-
If checked, fingerprint data is not compressed on the client computers before sending to the Terminal Server.
-
If not checked, fingerprint data is compressed on the client computers before sending to the Terminal Server.
When an administrator changes this setting, only new connections display the behavior specified by the new setting. Sessions that were initiated before the change must log off and reconnect to be affected by the new setting.
Fingerprint enrollment
Configure settings related to fingerprint enrollment.
Set the minimum number of enrolled fingerprints
This setting requires that the user enroll at least the specified number of fingerprints.
Enrolling just one fingerprint increases the probability of not being able to authenticate. Enrolling several fingerprints will increase the probability of false acceptance.
If disabled or not configured, the minimum number of fingerprints required for enrollment is 1.
Set the maximum number of enrolled fingerprints
This setting restricts the number of fingerprints that a user can enroll. Enrolling several fingerprints will increase the probability of false acceptance.
If disabled or not configured, the maximum number of fingerprints allowed for enrollment is 10.
Fingerprint verification
Configure settings related to fingerprint verification.
-
If enabled, allows you to set the False Accept Rate for the fingerprint verification.
-
If disabled or not configured, a FAR setting of Medium High (1 in 100,000) is used.
Set the False Accept Rate
The False Accept Rate (FAR) is the probability of receiving a false acceptance decision when comparing fingerprints scanned from different fingers.
When this setting is enabled, you can select one of the following FAR values:
-
Medium (1 in 10,000)
-
Medium High (1 in 100,000) - Recommended
-
High (1 in 1,000,000)
For example: if you select Medium High, on average, one false acceptance will occur when a fingerprint is compared against one hundred thousand fingerprints scanned from different fingers.
The higher the setting, the lower the chance of receiving a false acceptance. However, at the High setting, the system may reject legitimate fingerprints.
OTP
Allow sending OTP Push Notifications automatically
Specify whether to allow sending One-Time Password Push Notifications automatically, without needing to explicitly click on the Send push notification link to initiate the OTP request.
-
If enabled, when the OTP tile displays, either by user navigation or program logic, the Push Notification for the OTP request is initiated automatically so that the user can proceed with granting approval from their mobile device.
-
If disabled or not configured, the behavior is the same as in previous versions of DigitalPersona software: the user must click on the Send push notification link to initiate the OTP request.
Send OTP by email
Specify whether to allow sending the user a One-Time Password through email. Requires also entering valid SMTP server information in the SMTP Configuration GPO.
-
If enabled, the option to send the user a One-Time Password through email is shown in the UI.
-
If disabled or not configured, this option is not shown in the UI.
Time-Based OTP Validation Window
Specifies a validation system acceptance delay for OTP validation in minutes.
Time differences between the TOTP validation server and a client device generating an OTP token can result in a mismatch of the OTP, and subsequent login failure. This is due to the fact that the validation server compares the timestamp when the OTP was generated with the timestamp when it is received. Although the duration of validity of a specific OTP may vary for specific devices, this window is generally plus or minus 30 seconds, for a total window of one minute. In some cases, due to network latency, or inaccurate clocks on lower-end OTP hardware devices, the gap between the originating timestamp and receiving timestamp may be more than the validation window.
This setting allows the administrator to specify a longer validation window. Note that the value indicates the total window, for example a window of 2 minutes would extend the validation window for 1 minute before and after the receiving timestamp.
-
If enabled, you can specify a validation window of between 1 and 20 minutes. Be aware that a longer validation window increases the time that the data may be vulnerable to attack.
-
If not configured, the validation window defaults to 1 minute.
Push Notification Server API Key
Specifies the user’s unique identification key on the Crossmatch Push Notification Server.
-
If enabled, and a valid API Key is entered, OTP Push Notification is shown on the logon screen. The API Key is provided in an email from the CPNS Team when a tenant account is created on the Crossmatch Push Notification Server.
-
If disabled or not configured, Push Notification will not be shown on the logon screen.
Push Notification Server Tenant ID
Specifies the user's unique identifier on the Crossmatch Push Notification Server.
-
If enabled, and a valid Tenant ID is entered, Push Notification is shown on the logon screen. The Tenant ID is provided in an email from the CPNS Team when a tenant account is created on the Crossmatch Push Notification Server.
-
If disabled or not configured, Push Notification will not be shown on the logon screen.
Custom SMS or Mail Message
Specifies a string to be used as the SMS or email message sent to the user. Requires a previously created Nexmo SMS account.
-
If enabled, this message will be sent each time the SMS or email OTP feature is used. You can specify a custom message with a limit of 140 characters. The message must also include the variable placeholder: %s, representing the code that will be sent in the message. For example, “Enter the following code to logon: %s”.
-
If disabled or not configured, the default message will be sent. The default message is “Use the DigitalPersona Verification Code %s.
PIN
PIN enrollment
Configure settings related to enrollment of a user PIN.
-
If enabled, you can specify the minimum and maximum length of the user PIN.
-
If disabled or not configured, the minimum length of the user PIN is 4 and the maximum length is 12.
Recovery Credentials
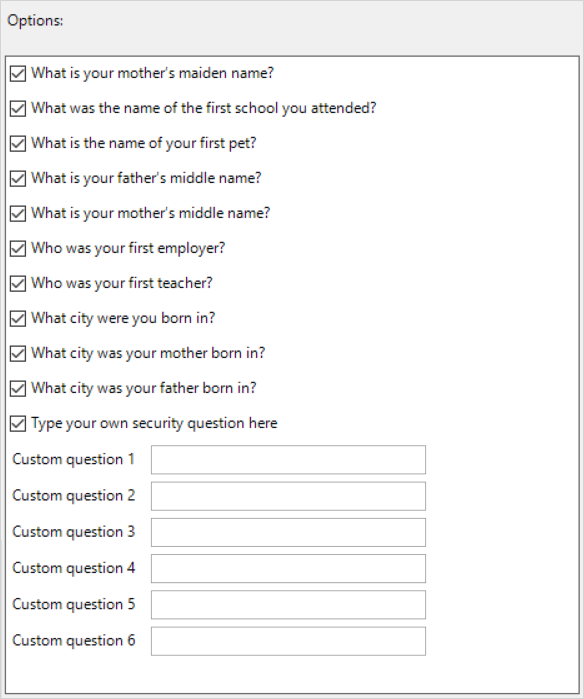
Recovery Questions
Enable Recovery Questions
Recovery Questions is a recovery feature that allows users to gain access to the computer in the event that they are unable to authenticate with the required credentials.
-
If enabled or not configured, users will be able to use Recovery Questions to log on.
-
If disabled, Recovery Questions functionality is not available to users.
Once enabled, the administrator can select or deselect from the provided list those questions that will be available to the user.
There are also options for the users to be able to type their own security question during enrollment of the credential, and for the administrator to define up to six custom questions (for example, to allow localized versions of the question) to be included in the Recovery Questions to be answered during credential enrollment.
Allow Recovery Questions for Windows Logon
Specifies whether users can bypass the current Logon Policy after using their Recovery Questions at Windows logon or simply set their Windows Password.
-
If enabled or not configured, users may use their Recovery Questions at Windows logon to reset their Windows password and bypass the current Logon Policy.
-
If disabled, users may use their Recovery Questions at Windows logon to reset their Windows password only.
Self Password Reset
Allow users to reset their Windows passwords
Specify whether users are allowed to reset their Windows password using DigitalPersona Recovery Questions or the Forgot password? link on the Identity Provider (STS) page.
-
If enabled and the above conditions are met, users are allowed to reset their Windows password using Recovery Questions or the Forgot password? link.
-
If disabled or not configured, or the conditions specified below are not met, users will not be able to reset their Windows password using Recovery Questions or the Forgot password? link and their Windows password can only be reset by the domain administrator.
Conditions:
-
For Recovery Questions, the Enable Recovery Questions setting must be enabled, and Recovery Questions must be specified in the Enrollment Policies GPO.
-
For Forgot Password?, the Path to DigitalPersona Secure Token Server (STS) GPO must be enabled and the path to the server must be valid.
Path to DigitalPersona Secure Token Server (STS)
Specifies the path (URL) to the DigitalPersona Secure Token Server (STS).
For example, https://server.domain/dppassivests.
This path is required when the Forgot password? link has been enabled on the Identity Server (STS) page through the Allow users to reset their Windows passwords GPO.
-
If enabled, and a valid URL is entered, the Forgot Password? link can be used to obtain an email that can be used to reset a user's Windows password.
-
If disabled or not configured, or an invalid URL is entered, the Forgot password? link will not function correctly.
Allow One-time access code for Windows Logon
-
If enabled or not configured, a One-time access code may be used at Windows logon to bypass the current Logon Policy.
-
If disabled, a One-time access code cannot be used at Windows logon to bypass the current Logon Policy.
Windows Password
Re-randomize Windows user password automatically
Specifies how long a user’s Windows password stays randomized before DigitalPersona will automatically re-randomize it without involving the user. The setting applies to users with randomized passwords only. It will help to avoid the display of the Change Password dialog at Windows logon when the user’s Windows password has expired according to the Windows Password Policy set by an administrator.
-
If enabled, DigitalPersona will automatically re-randomize the user's password in the specified number of days.
-
If disabled or not configured, DigitalPersona will not automatically re-randomize the user's password.
Event logging
Level of detail in event logs
Determines whether DigitalPersona logs events such as credential enrollment and authentication attempts in the Windows Event Log.
There are three levels of event logging:
- Errors
- Auditing
- Details
-
If enabled, DigitalPersona logs events on the specified level.
-
If disabled or not configured, events are logged on the Auditing level and Status Events are not logged.
Each higher level includes all previous levels. Events are logged on the computer where the event occurred.
For most normal tasks it is enough to set the level to Auditing. This would cover all events related to logon, authentication, credential management and user management. Setting the level to Detail will fill the log file quickly.
Log Status events
Status events provide information about the state of various policies and components on client computers. They are logged on configurable intervals and generally used when events are remotely collected.
User Onboarding
Onboarding is a process of enrolling authentication credentials in DigitalPersona software by a new user prior to accessing certain resources.
Allow user onboarding
Determines whether User Onboarding is allowed.
-
If enabled or not configured, an enrolled user will have an option to enroll required authentication credentials prior to using them at Windows logon or the Identity Provider logon screen.
When a user goes through the enrollment or onboarding process, they authenticate with their Windows credentials first, with a password for example.
An HID DigitalPersona license is taken at this time, regardless of whether or not they complete enrolling other credentials. The next time they log on, the onboarding option ‘First time using HID DigitalPersona?” will not be shown for this user.
-
If disabled, an unenrolled user will not be able to enroll any required credential prior to logging on to Windows or in Identity Provider. An HID DigitalPersona license is not taken until they subsequently complete credential enrollment in the Enrollment UI.
Proxy Server configuration
Specifies the name and port of a Proxy Server. When specified, all HTTP/HTTPS requests from DigitalPersona software are sent through this Proxy Server as an intermediary.
-
If enabled, and a Proxy Server is specified, all queries are sent through the designated Proxy Server.
-
If disabled or not configured, all queries are sent to the original URL.
DigitalPersona\Server
The policies and settings in this table are implemented through AD Administrative Templates and are used to configure the behavior of a DigitalPersona Server.
Credentials Verification lockout
Allow users to unlock their Windows account using DigitalPersona Recovery Questions
Configure whether or not users are allowed to unlock their Windows account using DigitalPersona Recovery Questions.
-
If enabled, users are allowed to unlock their account.
-
If disabled or not configured, users are not allowed to unlock their account. User accounts can only be unlocked by the domain administrator.
Account lockout duration
Configure the number of minutes an account is locked out before automatically being unlocked. To specify that the account will be locked out until the administrator explicitly unlocks it, set the value to 0. The Account lockout duration must be greater than or equal to the reset time.
-
If enabled, you can set a value between 1 and 99999 minutes.
-
If disabled or not configured, the duration of the lockout is 30 minutes.
Reset account lockout counter after
Configure the number of minutes that must elapse after a failed credential verification attempt before the account lockout counter is reset to 0. The reset time must be less than or equal to the Account lockout duration.
-
If enabled, you can set a value between 1 and 99999 minutes.
-
If not configured, the counter is reset after 5 minutes.
Account lockout threshold
Configure the number of failed credential verification attempts that causes a user account to be locked out. The lockout applies to verification of all credentials except the Windows password, which is governed by the Windows lockout policy.
A user cannot access a locked out account using any credential (except their Windows password) until it is reset by an administrator or until the account lockout duration has expired.
-
If enabled, you can set a value between 1 and 999 failed fingerprint verification attempts, or you can specify that the account will never be locked out to fingerprint verification by setting the value to 0.
-
If disabled or not configured, the account will never be locked out due to failure of fingerprint verification.
DigitalPersona Server DNS
Automated site coverage by DigitalPersona Server Locator DNS SRV records
Configure whether or not DigitalPersona will dynamically register DigitalPersona Server Locator site-specific SRV records for the closest sites where no DigitalPersona Server for the same domain exists. These DNS records are dynamically registered by the DigitalPersona Server, and used by DigitalPersona clients to locate a DigitalPersona AD Server.
-
If enabled, the computers to which this setting is applied dynamically register DigitalPersona AD Server Locator site-specific DNS SRV records for the closest sites where no DigitalPersona AD Server for the same domain exists.
-
If disabled or not configured, the computers will not register site-specific DigitalPersona AD Server Locator DNS SRV records for any other sites but their own.
Refresh interval of DigitalPersona Server DNS records
Configure the refresh interval of DigitalPersona Server Locator DNS resource records for computers to which this setting is applied. These DNS records are dynamically registered by the DigitalPersona Server and are used by DigitalPersona clients to locate a DigitalPersona Server. This setting may be applied only to computers using dynamic update.
Computers configured to perform dynamic registration of DigitalPersona AD Server Locator DNS resource records periodically re-register their records with DNS servers, even if their records’ data has not changed. If authoritative DNS servers are configured to perform scavenging of the stale records, this re-registration is required so that the authoritative DNS servers (which are configured to automatically remove stale records) will recognize these records as current and preserve them in the database.
-
If enabled, allows you to specify a refresh interval longer than the default value of 1800 seconds (30 minutes).
-
If disabled or not configured, computers use the default value.
Sites covered by DigitalPersona Server Locator DNS SRV records
Configure the sites for which the domain DigitalPersona Server registers site-specific DigitalPersona AD Server Locator DNS SRV resource records. These records are in addition to the site-specific SRV records registered for the site where DigitalPersona Server resides, and in addition to the records registered by a DigitalPersona AD Server configured to register DigitalPersona Server Locator DNS SRV records for those sites without an DigitalPersona AD Server that are closest to it.
The DigitalPersona AD Server Locator DNS records are dynamically registered by DigitalPersona AD Server, and they are used by DigitalPersona clients to locate a DigitalPersona Server. An Active Directory site is one or more well-connected TCP/IP subnets that allow administrators to configure Active Directory access and replication.
-
If enabled, configures the sites covered by the DigitalPersona AD Server Locator DNS SRV records. Specify the site names in a space-delimited format. The site names have the following format, in which the <site name> component must be present and the <priority> and <weight> components are optional. The <priority> and <weight> components must be a numeric string value:
<site name>:<priority>:<weight>
-
If disabled or not configured, no site-specific SRV records will be registered.
Priority set in DigitalPersona Server Locator DNS records
Configure the Priority field in the SRV resource records registered by DigitalPersona AD Server to which this setting is applied. These DNS records are dynamically registered by DigitalPersona AD Server and are used by DigitalPersona AD Workstation to locate a DigitalPersona Server.
The Priority field in the SRV record sets the preference for target hosts specified in the SRV record Target field. DNS clients that query for SRV resource records attempt to contact the first reachable host with the lowest priority number listed.
-
If enabled, configures the Priority in the DigitalPersona AD Server Locator DNS SRV resource records.
Specify a value between 0 and 65535.
-
If disabled or not configured, computers use a default priority of 0.
Weight set in DigitalPersona Server Locator DNS records
Configure the Weight field in the SRV resource records registered by the DigitalPersona Server to which this setting is applied. These DNS records are dynamically registered by the DigitalPersona Server, and they are used to locate a DigitalPersona Server.
The Weight field in the SRV record can be used in addition to the Priority value to provide a load-balancing mechanism where multiple servers are specified in the SRV record's Target field and set to the same priority. The probability with which the DNS client randomly selects the target host to be contacted is proportional to the Weight field value in the SRV record.
-
If enabled, configures the Weight in the DigitalPersona Server Locator DNS SRV records. Specify a value between 0 and 65535.
-
If disabled or not configured, computers use a default weight of 100.
Register DigitalPersona Server Locator DNS records for domain
Configure whether or not DigitalPersona will dynamically register the DigitalPersona Server Locator domain-specific SRV records for the domain it belongs to. The DNS records are dynamically registered by DigitalPersona Server, and they are used by the DigitalPersona Workstation to locate a DigitalPersona Server.
-
If enabled or not configured, computers dynamically register DigitalPersona Server Locator domain-specific DNS SRV records.
-
If disabled, computers will not register the domain-specific DigitalPersona Server Locator DNS SRV records for the domain they belong to and register only site-specific records.
Dynamic registration of DigitalPersona Server Locator DNS records
Configure whether or not dynamic registration of DigitalPersona Server Locator DNS resource records is enabled. These DNS records are dynamically registered by the DigitalPersona Server and are used by DigitalPersona clients to locate a DigitalPersona Server.
-
If enabled or not configured, computers will dynamically register DigitalPersona Server Locator DNS resource records through dynamic DNS update-enabled network connections.
-
If disabled, computers will not register DigitalPersona Server Locator DNS resource records.
Identification Server settings
Perform fingerprint identification on server
Specifies whether fingerprint identification is performed on the DigitalPersona AD Server or against the local computer cache.
-
If enabled or not configured, fingerprint identification requests are directed to a DigitalPersona AD Server, where the provided fingerprint data is compared to the data for every user with enrolled fingerprints in the Active Directory domain.
Note: After enabling this setting, you will need to wait about 15 minutes before identification is available - or you can restart the DigitalPersona Server to refresh the settings. -
If disabled, fingerprint identification requests are processed on the local computer, where the provided fingerprint data is compared to the data for every user with enrolled fingerprints in the local computer cache.
The default is “not configured.”
Restrict identification to a specific list of users
Allow restricting identification to a specific list of users with permissions for the computer where the identification request originates.
-
If enabled, you can define a list of users who can participate in identification, and then assign this list to a specific computer or set of computers.
-
If disabled or not configured, identification is performed against all domain users.
For details on how to define this list of users, Identification List.
DigitalPersona Workstations
These settings are used to configure and govern features specific to DigitalPersona workstations.
Advanced
Always show the Windows password tile in sign-in options
Specifies whether the Windows password tile is always shown in sign-in options on the Windows Logon screen.
-
If enabled or not configured, the Windows password tile will be always shown in sign-in options, even if a password is not allowed in Logon Authentication Policy.
-
If disabled, the Windows password tile will be shown in sign-in options only if a password is allowed in Logon Authentication Policy.
Do not launch the Getting Started wizard upon logon
-
If enabled, the DigitalPersona User Console and the Getting Started page do not start automatically after user logon.
-
If disabled or not configured, the DigitalPersona User Console and the Getting Started page starts automatically after user logon.
Add user-level credentials to Other User sign-in options
-
If enabled, all user-level policy credentials not already part of the Logon Authentication Policy will be added to sign-on options for Other User on the Windows Logon screen.
-
If disabled or not configured, only the credentials (sign-in options) defined by the Logon Authentication policy will be shown for Other User and user-level policy credentials will not be shown as options for Other User on the Windows Logon screen.
Identification Server domain
Specifies the name of the domain where a DigitalPersona ID Server is hosted. Computers attempting to identify a user based on their fingerprint credentials will send the query to this domain.
-
If enabled, and a DNS domain name is entered, queries are sent to the specified domain.
-
If not configured or disabled, queries are sent to the domain that the computer belongs to.
Compatibility with Microsoft fingerprint support
For Quick Actions to work, the DigitalPersona client software must always maintain an exclusive connection to the fingerprint reader. This exclusivity prevents other software from using the reader, including Microsoft’s built-in fingerprint support.
This setting enables or disables those Quick Actions that have a fingerprint credential as a component (called Finger Actions), thus allowing or disallowing use of the fingerprint reader in other applications.
-
If enabled, Finger Actions are disabled. Other fingerprint software can use the fingerprint reader whenever the DigitalPersona software does not require exclusive use for authentication and fingerprint enrollment.
-
If disabled or not configured, Finger Actions may be used, but other fingerprint software (including Microsoft Windows) cannot use the fingerprint reader.
Allow DigitalPersona client to use DigitalPersona Server
-
If enabled or not configured, DigitalPersona clients will attempt to contact a DigitalPersona Server to obtain services.
-
If disabled, DigitalPersona clients will not attempt to contact a DigitalPersona Server, and will use cached data.
Show Taskbar icon
-
If enabled or not configured, a Taskbar icon is displayed on managed workstations.
-
If disabled, the Taskbar icon is not shown.
Allow VPN-less access
Specifies the URL for VPN-less access.
This feature allows logon to Windows and access to other resources when users are outside of their corporate network without a VPN connection.
-
If enabled and a valid URL to the DigitalPersona Web Proxy is entered, the web proxy will be used.
-
If disabled or not configured, VPN-less access will not be available.
Requires installation and valid configuration of the DigitalPersona Web Management Components.
Browser Hardware Support
Allow Localhost Loopback
Configures whether to allow client computers to use Localhost Loopback from their web browsers.
Some product features require communication between a client’s web browser and a locally attached hardware device such as a fingerprint reader. DigitalPersona uses a web service named ‘Localhost Loopback’ for this purpose.
-
If enabled or not configured, Localhost Loopback is enabled.
-
If disabled, Localhost Loopback is disabled. Features such as fingerprint or card authentication will not work within client web browsers.
Localhost Loopback Origins
Specifies origins for which Localhost Loopback will be enabled.
-
If enabled, the administrator can specify those websites for which Localhost Loopback will be enabled by entering the website origins in a semicolon-delimited format, i.e. www.mydomain1.com;www.mydomain2.com. Localhost Loopback will be enabled only for specified websites and disabled for all other websites.
-
If disabled or not configured, Localhost Loopback will be enabled for all websites.
Caching Credentials
Cache user data on local computer
Determines whether user data for domain users is cached on the local computer.
-
If enabled, user data (such as fingerprint templates, other credentials and secure application data) of domain users is cached locally on the computer.
This provides domain users the ability to use their enrolled credentials when a HID DigitalPersona Server cannot be located. This is a convenient but less secure option.
-
If disabled, users may only use enrolled credentials when a HID DigitalPersona Server is accessible.
-
If not configured:
-
For DigitalPersona Workstations, user data of domain users is cached locally on the computer. It is equivalent to the "enabled" option.
-
For DigitalPersona Kiosk, user data of domain users is NOT cached locally on the Kiosk computer. Live connection to a HID DigitalPersona Server is required for all use of enrolled credentials. It is equivalent to the "disabled" option.
-
The data of local users is always stored on the local computer.
Maximum size of identification list
The identification list contains an administrator-specified number of user accounts. It is used in conjunction with cached credentials to identify a user by their fingerprint and, as an added convenience, frees them from typing their user name and domain at Windows logon.
-
If enabled, you can specify the maximum number of users the identification list can hold on a particular computer. Type the number of users in the Maximum size of identification list text box. While the number of credentials that can be cached is virtually unlimited, the maximum number of users that can be added to the identification list is 100; the minimum is 0.
-
If disabled or not configured, the default value of 10 is used.
Users are added to the identification list in the order they log on. The most recent user to log on is added to the top of the list. If the list has exceeded its capacity, the least recent user to log on is removed from the list when another user logs on. If a user is already on the list and logs on again, they are moved from their original position on the list and placed on top.
Once removed from the list, a user can still use their cached credentials (if enabled), but they must type their user name and domain manually.
If DigitalPersona is deployed in a networked environment, it performs identification locally out of the set of users in the identification list and then, for added security, confirms the user identity using the DigitalPersona Server.
Disable Applications
Prevent Password Manager from running
-
If enabled, the Password Manager application is not available.
-
If disabled or not configured, the Password Manager application is available.
Password Manager
Authenticate other user for Password Manager operations
-
If enabled, a user other than the logged in user may authenticate for Password Manager operations using a credential supporting user identification (such as their fingerprint), subject to session policy.
-
If disabled or not configured, only the currently logged in user may authenticate for Password Manager operations.
Display password complexity popup
-
If enabled or not configured, the password complexity popup displays when modifying logon profile protected fields.
-
If disabled, the popup is not displayed.
Quick Actions
Settings: Credential, Ctrl+Credential, Shift+Credential
Specifies administrator-defined Quick Actions (DigitalPersona Workstation only) that are performed automatically when a user presents an authorized and enrolled credential, or credential plus the Ctrl or Shift keys.
-
If enabled, the administrator can specify the Quick Action to be performed by the DigitalPersona client.
-
If disabled, no Quick Action will be performed for the selected credential and Ctrl or Shift keys combination on the DigitalPersona client.
-
If not configured, the default or user specified Quick Action will be performed on the DigitalPersona client.
For each credential or credential combination, select one of the Quick Action options to be performed by the DigitalPersona client:
-
Password Manager Action – If the active window is associated with a personal or managed logon, stored logon data will be filled in. If there is no associated logon, and “Allow creation of personal logons” is enabled or not configured, the User Training Tool displays.
-
Lock Workstation – Locks the computer.
Other Settings
Fast User Switching
Fast User Switching is a feature which allows Windows users to quickly switch between user accounts on a single computer without quitting applications and logging out.
DigitalPersona supports Fast User Switching when using credentials which allow identifying a user without typing their usernames, for example, by using fingerprints, contactless cards, etc.
To turn on the Fast User Switching feature you need to disable the Microsoft GPO setting Hide Entry Points for Fast User Switching in Computer Configuration | Administrative Templates | System | Logon.