Using the Authorization Manager (AzMan)
The DigitalPersona LDS role-based permissions, tasks and operations are managed through the DigitalPersona Authorization Store and the Windows Authorization Manager (AzMan).
The Microsoft Authorization Manager (AzMan) creates and manages an Authorization Store, which serves as a repository for DigitalPersona LDS authorization policies and defines a namespace for DigitalPersona LDS roles, tasks, and operations.
For instructions on opening the DigitalPersona Authorization Store, see Define the Authorization Store Name.
Although the group names, roles and tasks defined by DigitalPersona LDS can be customized, the operations that make up a task cannot be modified. You can change which operations may be performed as part of a given task, but removing a critical operation from a task may result in the failure of the task.
Those roles, tasks and operations defined by default during installation are described below.
The following terms are applied to the Authorization Manager:
| Term | Definition |
|---|---|
| Operations | A set of permissions that are associated with system-level or API-level security procedures such as WriteAttributes or ReadAttributes. Operations are building blocks for tasks. |
| Tasks | A collection of operations and sometimes other tasks. Well-designed tasks represent recognizable work items (for example, "submit purchase order" or "submit expense"). |
| Groups |
There are two types of AzMan groups used by DigitalPersona LDS:
|
LDAP Query Groups
The following LDAP Query Groups are predefined by DigitalPersona LDS:
| Group name | LDAP Query | Group description |
|---|---|---|
|
DigitalPersona AD Users |
"(&(objectCategory=userProxy)(objectClass=userProxy))" |
All user accounts in DigitalPersona AD LDS database which also exist in the Active Directory database. Active Directory users are automatically added to this group upon enrollment. |
|
Altus Users |
"(&(objectCategory=person)(objectClass=user)(dpAccountName=*))" |
All user accounts in DigitalPersona AD LDS database which do not exist in the Active Directory database. Users are automatically added to this group upon enrollment if they are not in Active Directory. |
To add an additional application group, right click the Group node and selected New Application Group.
Definitions
The Definition node contains two types of definitions - Role Definitions and Tasks Definitions.
Role Definitions
Each AzMan Role has the following properties.
-
Role Name
-
List of Users and Groups belonging to the Role
-
List of AzMan Tasks assigned to this Role
The following DigitalPersona LDS AzMan roles are predefined:
| Role name | Group | Default tasks | Role description |
|---|---|---|---|
|
DigitalPersona AD Users |
Altus AD Users (AzMan Group) |
Manage Self |
All Active Directory users have this Role assigned. It allows reading and writing public LDAP attributes from/to the DigitalPersona AD LDS database. |
|
Altus Users |
Altus Users (AzMan Group) |
Manage Self |
All DigitalPersona LDS users who do not exist in the Active Directory database have this Role assigned. It allows reading and writing public LDAP attributes from/to the DigitalPersona AD LDS database. |
|
Security Officers |
Administrators (Windows Local Group) |
Query Users Enroll Users |
By default only Windows users which belong to the Local Administrators group on a machine where DigitalPersona LDS Server is installed have this Role assigned. It allows enrolling credentials for any type of user in the DigitalPersona AD LDS database. Domain Administrators are assigned this role automatically during setup. |
|
Administrators |
Administrators (Windows Local Group) |
Query Users Manage Users Enroll Users Manage Licenses Manage Policies
|
By default only Windows users which belong to the Local Administrators group on a machine where DigitalPersona LDS Server is installed have this Role assigned. Local administrators are assigned this role automatically during setup. It allows practically any operation on DigitalPersona LDS users. |
Tasks Definitions
The following authorization tasks are predefined:
Authorization Operations
The following authorization operations are predefined:
| Operation | Description |
|---|---|
| Activate License | Activates a product license. |
| Assign Policies | Assigns a policy to a DigitalPersona LDS group. |
| Create Policies | Create DigitalPersona LDS policy. |
| Create User | Create DigitalPersona LDS Non AD user record. |
| Delete Policies | Delete DigitalPersona LDS policies. |
| Delete User | Delete DigitalPersona LDS Non AD user. |
| Enroll Credentials | Enroll DigitalPersona LDS Non AD user credentials. |
| Enroll Customer Credentials | Enroll customer (DigitalPersona LDS Non AD user) credentials. |
| Enroll Employee Credentials | Enroll employee (AD user) credentials. |
| Get Own Info | Query DigitalPersona LDS database for own user information (attributes). |
| Get User Info | Query DigitalPersona LDS database for user information (attributes). |
| Modify Own Info | Change user’s own DigitalPersona LDS user information. |
| Modify User Info | Change DigitalPersona LDS user information. |
| Recover User | Perform user recovery. (This feature is not implemented in the current version. The operation is reserved for future use.) |
| Self Create User | Create DigitalPersona LDS record. Must be a Windows AD user. |
| Self Enroll Credentials | Enroll own user credentials without needing Security Officer role. |
| Set User Account Control | Set User Account control bits. |
| Unlock User Account | Remove lock from user account. |
Enabling Self-Enrollment
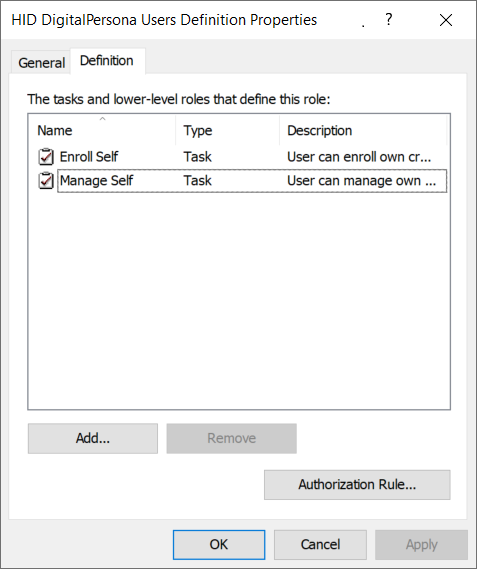
You can enable DigitalPersona (AD/Employee and LDS/Customer) users to enroll and manage their own DigitalPersona LDS credentials by Adding the Enroll Self task to the predefined DigitalPersona AD Users or Altus Users role or to another role that you create.
For non-AD users, the administrator needs to first create those users before they can proceed with self-enrollment via Web Enrollment. Additionally, the administrator must enable Enroll Self and Manage Self in the Users Definition Properties dialog.