Computer Configuration\Policies\Software Settings
During installation of the DigitalPersona LDS Administration Tools, the following nodes are created under the Computer Configuration\Policies\Software Settings node.
Click the setting names in the following list to view the details:
DigitalPersona LDS Client
These settings can be found at the following location:
Computer Configuration\Policies\Software Settings\DigitalPersona Client
They are used to configure and govern DigitalPersona clients.
Security\Authentication
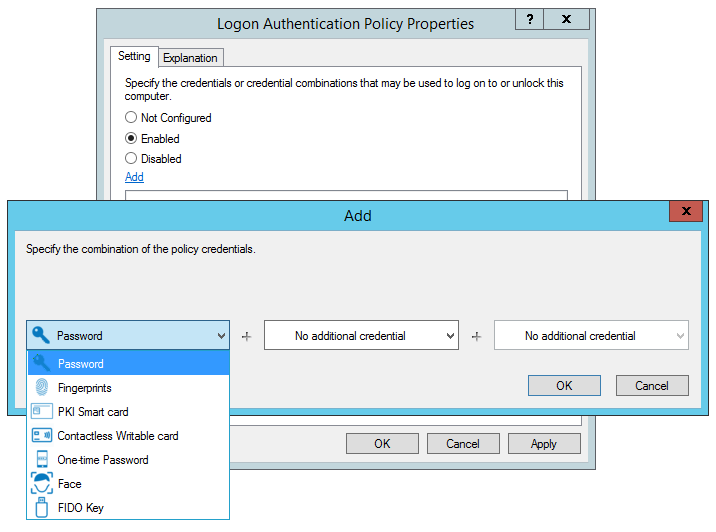
Logon Authentication Policy
The Logon Authentication Policy defines the credentials and/or credential combinations needed for authentication and logon to Windows. By default, all supported credentials are listed on the tab.
-
If enabled, only the specified credentials, in the specified combinations, can be used for authentication.
-
If disabled or not configured, any Primary credential can be used for authentication.
Primary and Secondary Credentials
For the purposes of Logon authentication, DigitalPersona credentials are defined as Primary and Secondary credentials. Primary credentials are considered stronger (more secure) than Secondary credentials, and include the following:
-
Primary credentials which are considered stronger (more secure) than Secondary credentials, and include the following:
-
Password
-
Fingerprint
-
Contactless Writable cards
-
Contactless ID cards (when enabled as a single (Primary) credential by GPO)
-
One-Time Passwords
-
Face (requires a separate Face Authentication License)
-
Passkey (device-bound and synced)
-
RADIUS
-
-
The following Secondary credentials can only be used in combination with a Primary credential:
-
Contactless ID card (except when enabled as Single (Primary) by GPO)
-
PIN
-
Bluetooth device
-
When selecting credentials to be used for the Logon Authentication Policy, the first credential must be a Primary credential. Additional (optional) credentials may be either Primary or Secondary credentials.
-
To add a credential or credential combination to the list:
-
Enable the policy.
-
Click the Add link just below the configuration buttons.
-
Select the Credentials and/or credential combinations that can be used for authentication during Windows logon. Then click OK.
-
Click Apply.
-
To edit a credential or credential combination:
-
Click the credential or credential combination and edit it using the drop-down lists provided.
-
Click Apply.
-
To delete a credential or credential combination:
-
Click on the X that appears in the upper-right corner of the item.
-
Click Apply.
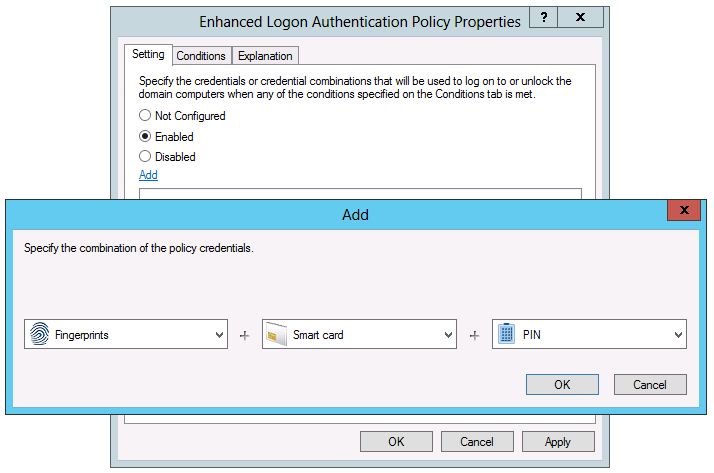
Enhanced Logon Authentication Policy
The Enhanced Logon Authentication Policy specifies the credentials or credential combinations that will be used to log on to or unlock domain computers when any of the conditions specified on the Conditions tab are met.
-
If enabled, and credentials are defined by clicking the Add button; then whenever the conditions selected on the Conditions tab are met, logon authentication will require the credentials or credential combinations specified in this policy.
Note: When the specified conditions are met, this policy replaces the Logon Authentication Policy in force. -
If disabled or not configured, the standard Logon Authentication Policy remains in force.
To configure the Enhanced Logon Authentication Policy:
-
Select Enabled and click the Add link in order to specify the required credential(s). See Primary and Secondary Credentials for details on permitted credential combinations.
Note: The Face credential requires a separate Face Authentication License. -
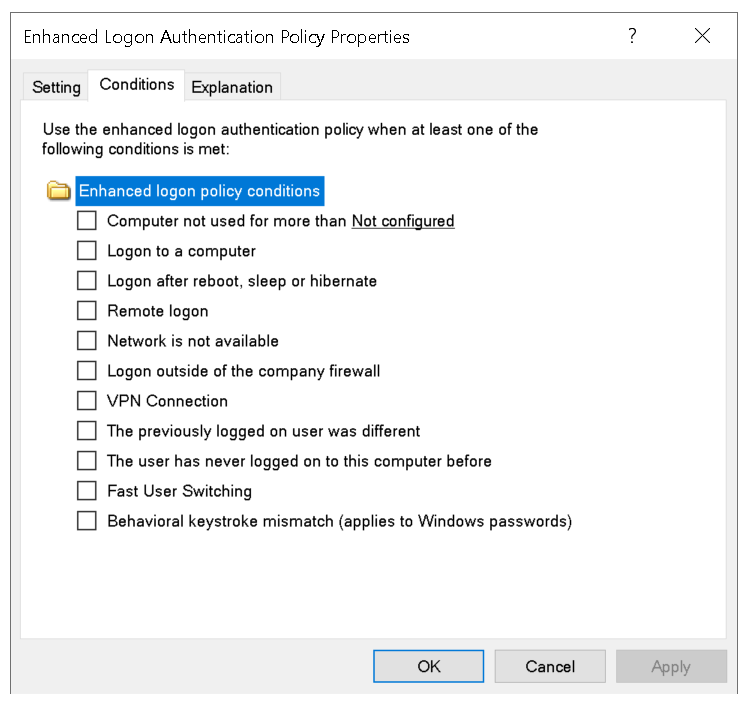
Specify any conditions that must be met for this policy to be applied.
| Condition | Description |
|---|---|
|
Computer not used for more than |
If checked, this policy will be used when a user tries to log on after the computer was locked or logged out for longer than the specified duration. Note: The screensaver will not trigger this condition, only a Windows lock will do so. Restarting the computer will reset the timer used by this setting.
|
|
Logon to a computer |
If checked, this policy will be used when a user logs on to a computer instead of unlocking its previous Windows session. |
|
Logon after reboot, sleep or hibernate |
If checked, this policy will be used when a user logs on to a computer after powering it up. This also applies to waking up from the hibernate mode. |
|
Remote logon |
If checked, this policy will be used when a user logs on to a computer via Remote Desktop. |
|
Network is not available |
If checked, this policy will be used when a connection to the network is not available. |
|
Logon outside of the company firewall |
If checked, this policy will be used when a user tries to log on to a computer which is not within the corporate firewall. |
|
VPN Connection |
If checked, this policy will be used when a user tries to log on to a computer which is on VPN connection. |
|
The previously logged on user was different |
If checked, this policy will be used when a different user than before tries to log on. |
|
The user has never logged on to this computer before |
If checked, this policy will be used when a user that has never logged on to this computer before tries to log on. |
|
Fast User Switching |
If checked, this policy will be used when a user tries to log on while another user is already logged on. |
Session Authentication Policy
The Session Authentication Policy defines the credentials needed to access Security applications during a Windows session. By default, all supported credentials are listed on the tab. See Primary and Secondary Credentials for details on permitted credential combinations.
-
If enabled, only the specified combination of credentials in the Policy can be used for authentication.
-
If disabled, the user is not prompted to authenticate by DigitalPersona security applications during the Windows session. This configuration provides Single Sign-on functionality. The user logs on to Windows, and gains access to all security applications without being prompted to authenticate for each application.
-
If not configured, credentials will be controlled by local GPOs. However, credential enrollment will still require authentication.
To edit or delete a credential from the list - click the arrow that appears to the right of the credential.
To add a credential to the list - click Add at the top of the list.
Kiosk Session Authentication Policy
The Kiosk Session Authentication Policy defines the credentials that may be used to access Security applications during a DigitalPersona Kiosk session.
By default, all supported credentials are listed on the tab.
See Primary and Secondary Credentials for details on permitted credential combinations.
-
If enabled, only the specified combination of credentials in the Policy can be used for authentication.
-
If disabled or not configured, credentials will be controlled by local GPOs.
To edit or delete a credential from the list - click the arrow that appears to the right of the credential.
To add a credential to the list - click Add at the top of the list.
Security\Enrollment
Enrollment Policy
The Enrollment Policy specifies the credentials that may be used for enrollment in the User Console, Attended Enrollment and HID DigitalPersona Enrollment applications. By default, all supported credentials are initially listed on this tab.
-
If enabled, only the specified credentials may be enrolled and only those credentials’ tiles are displayed in the UI.
-
If disabled or not configured, any installed and supported credentials may be used, except for Face.
To use the Face credential, the policy must be enabled and the Face credential selected. All other credentials that you want to be available for enrollment must also be selected.
Security\SMS
SMS Configuration
SMS Configuration specifies the API values and Sender Addresses assigned by the Nexmo Gateway and is required for operation of DigitalPersona’s OTP via SMS credential.
-
If enabled, and valid values are entered in the fields provided, SMS authentication will be shown on the logon screen. The API Key assigned by Nexmo is required.
-
If disabled or not configured, SMS authentication is not shown on the logon screen.
| Parameter | Description |
|---|---|
| Nexmo API Key | Enter the API Key assigned by Nexmo. |
| Nexmo API Secret | Enter the API Secret assigned by Nexmo. |
| Nexmo Sender Addresses |
Enter one or more semicolon-delimited alphanumeric strings to be used as Sender Addresses (also called SenderID) by the Nexmo SMS Gateway. There are country specific limitations for sender addresses, for example, alphabetic characters are not allowed in the United States.
|
Security\SMTP
SMTP Configuration
Specify the SMTP server parameters for an account to be used by the password reset and OTP through email features for sending email to the user.
When enabled, the following fields are mandatory:
-
SMTP Server - Hostname only supported
-
Email Address - Used to login to SMTP Server
-
Email Password - Used to login to SMTP Server
To validate the SMTP server parameters entered, enter an Incoming Email Address and click Test Settings. A test email will be sent to the specified address.
-
If enabled and valid SMTP parameters are entered, the specified SMTP server will be used.
-
If disabled or not configured, password reset and OTP through email features will not be successful.
Kiosk Administration
Settings that define DigitalPersona Kiosk policies are stored in the following location:
Computer Configuration\Policies\Software Settings\DigitalPersona Client\Kiosk Administration
Allow automatic logon using Shared Kiosk Account
Determines whether the automatic logon feature is enabled.
-
If enabled, automatic logon uses the Kiosk Shared Account to log users on to the computer when the Windows operating system starts up. The Log On to Windows dialog box is not displayed.
-
If disabled or not configured, the automatic logon is disabled.
Logon/Unlock with Shared Account Credentials
-
If enabled, any user who knows the user name and password for the shared account that Kiosk uses can use those credentials to log on to or unlock the computer.
-
If disabled or not configured, the shared account credentials cannot be used to log on to or unlock the computer.
Prevent users from logging on outside of a Kiosk session
-
If enabled, only those with administrator privileges are able to log on to any Kiosk workstation controlled by the GPO.
-
If disabled or not configured, users can log on to the Kiosk workstations as a local user outside of the Kiosk session.
Kiosk Workstation Shared Account Settings
In order for a DigitalPersona Kiosk workstation to function correctly, this setting must be enabled and the Windows shared account information (user name, domain and password) specified. For further details, see Specifying a Shared Account for the Kiosk.
-
If enabled, you can specify Windows shared account information for the governed kiosks and randomize the Kiosk Shared Account password.
-
If disabled or not configured, Kiosk workstations affected by the GPO will not be operable.
Randomize Kiosk Shared Account password
If the Randomize Shared Account password option is selected, the DigitalPersona Server will randomize it immediately before saving. Then the DigitalPersona Server will automatically re-randomize this password one day before password expiration.
Here is the flow of the password re-randomization process for the Kiosk Shared Account.
-
Once a day the DigitalPersona Server will check the Kiosk Shared Account password expiration time.
-
If the time left before expiration is less than one day, the DigitalPersona Server will re-randomize the Kiosk Shared Account password and store the new password in the DigitalPersona Server database.
This ensures that the Kiosk Shared Account password will never expire and will be changed frequently without requiring administrator involvement.
An Event ID 530 (User password was randomized) is generated on the server whenever the Kiosk shared Account password gets randomized automatically.
Kiosk Unlock Script
Specifies a script file to run whenever a Kiosk session is unlocked by a new user.
By default, the script file should be located in the directory shown below on the Domain Controller or you can specify the full path to a shared folder containing the script file:
%systemroot%\sysvol\sysvol\domain_DNS_name\scripts
DigitalPersona LDS Server
This server setting can be found at the following location:
Computer Configuration\Policies\Software Settings\DigitalPersona Server.
Licenses
This setting provides a way to activate, de-activate and refresh DigitalPersona licenses.
-
To add a license for a DigitalPersona Server, right-click the License node and select Activate.
Follow the instructions provided by the DigitalPersona Activation wizard.
-
To view detailed information about a license, right-click on the license and select Properties.
-
To refresh license information, right-click the License node and select Check for license updates.
Follow the instructions provided by the DigitalPersona Activation wizard.
-
To deactivate a license, right-click the License node and select Deactivate.
Follow the instructions provided by the DigitalPersona Activation wizard.
For complete information on adding and managing your DigitalPersona LDS licenses, see License Activation and Management.