User Authentication
| Mandatory Server Settings |
HID_HOST |
<HID Authentication Service Host> (e.g., test123.aaas.hidcloud.com) |
|---|---|---|
|
HID_KONY_APP_KEY |
<App key of the fabric application> (e.g., h728h89031832jdy9292) |
|
|
HID_KONY_APP_SECRET |
<App secret of the fabric application> (e.g., 89bv2894673792003jy2) |
|
| HID_IS_FETCH_USER_ATTRIBUTES |
<Identity provider service value> (e.g., false) Note:
If you set the identity provider service to DbxUserLogin (Custom Identity) instead of customHIDLogin, ensure its value is set to true. The default value is false. |
|
| HID_CIBA_API_PORT |
<Port for the CIBA Callback URL> (e.g., 443) Note:
In cases where the value is different from the usual 443, it is mandatory to add this server property and provide the port value. |
|
| HID_PUSH_LOGON_AUTH_TYPE |
<Push logon authenticator type> (e.g., AT_PASA) |
|
| HID_PUSH_LOG_CHANNEL |
<Channel ID for push> (e.g., CH_PASA) |
|
| HID_REDIRECT_URI |
<Redirect url set for the FIDO tenant> |
|
| HID_AS_CLIENT_ID | <Client Id for the tenant> | |
|
HID_PASSWORD_AUTHTYPE |
<Static Password Authenticator if other than AT_STDPWD> | |
|
HID_OOB_SMS_OTP_AUTHTYPE |
<OOB SMS Authenticator if other than AT_OOBSMS> |
|
|
HID_OOB_EMAIL_OTP_AUTHTYPE |
<OOB Email Authenticator if other than AT_OOBEML> |
|
|
HID_DEVICE_TYPE |
<Device type to be used for Approve if other than DT_TDSV4> | |
|
HID_SECURE_OTP_AUTHTYPE |
<HID Approve OTP Authenticator if other than AT_EMPOTP> |
|
|
HID_HARDWARE_OTP_AUTHTYPE |
<Hardware Token OTP Authenticator if other than AT_OTP> |
|
| HID_IDP_CHANNEL_ID | <End user channel ID> (e.g., CH_EXTRAPP) | |
| HID_API_VERSION |
<This server property defines the API version for the Authentication Service and Appliance, ensuring that updated APIs are used. (The default value is 10 for Authentication Service and 3 for Appliance.)> |
|
| HID_IS_MFA_REQUIRED |
<This setting enables the user to activate/deactivate the Multi-factor authentication (MFA)> (Default: true) |
|
| HID_CACHE_EXPIRY_TIME | 120 (by default) | |
| HID_SMS_MSG_TEMPLATE | <Use # as your OTP for authentication. DO NOT share this OTP with anyone> | |
| HID_IS_GATEWAY_ENABLED |
true: HID generates and sends the OTP. false: HID generates the OTP, but Infinity sends it. |
|
| HID_SMS_DEVICE_TYPE |
<The device type for SMS> Value: DT_OOBSMS (by default) |
|
| HID_EMAIL_DEVICE_TYPE |
<The device type for email> Value : DT_OOBEML (by default) |
Authentication Component Properties
| S.No. | Property Name | Allowed Values | Purpose |
|---|---|---|---|
| 1 | isRMSEnabled | Radio button to select (on/off) | This property determines whether Risk Management Sysytem (RMS) is active or not. |
| 2 | tmCookieTag | <RMS Cookie will have this value> | This property determines the value of RMS cookie for device tag. |
| 3 | tmCookieSid | <RMS Cookie will have this value> | This property determines the value of RMS cookie for session id. |
| 4 | adaptiveAuth | JSON object | This property determines the value as JSON object to choose adaptive auth based on RMS score. |
| 5 | isRMSReadOnly | Radio button to select (on/off) | This property determines whether RMS is read only or not. |
| 6 | FirstFactor | "STATIC_PWD", "SECURE_CODE", "OTP_SMS_PIN", “FIDO” |
This property determines the first authentication factor to be used for the authentication. Currently, the component supports the following factors:
|
|
7 |
Multi-Factor Authentication (MFA) |
"SECURE_CODE" ,"OTP_SMS","OTP_EML","APPROVE", "OTP_HWT", "NO_MFA" |
This property determines the second authentication factor to be used for authentication after the first authentication factor. Currently, the component supports the following factors:
|
-
When we select FirstFactor as FIDO, or USER_ID_LESS, then it is mandatory to select MFA as NO_MFA.
-
OTP_SMS_PIN first factor is not recommended to use.
Authentication Component Functions
No public function is exposed. All the functions are called from the UI provided with the component.
Authentication Component Events
| 1 |
onSuccessCallback |
Callback to be defined for successful login. |
| 2 |
onFailureCallback |
Callback to be defined for failure during login. |
Authentication Component Flow
STATIC_PWD
-
On the login screen, the user must enter their username and password, then click Submit.
-
After successfully validating the user's static password, the component displays the screen to authenticate using the second authentication factor, based on the defined value of the MFA property:
HID Approve
- If the user has more than one registered HID Approve device, the list of devices is displayed.
- If user has only one registered HID Approve device, the user will receive a push notification directly.
- The user can either select a device to which to send Push notification or they can select to authenticate using an HID Approve Secure Code.
- On selecting the device, the user receives a Push notification on the selected device. The user can also select to authenticate using an HID Approve Secure Code.
- After approving the Push notification, user is directed to the next screen confirming that they have been successfully authenticated and can log out if required.
OTP via SMS or Email
User receives an OTP either by SMS or by email based on the MFA selected.
On the next screen, the user enters the received OTP and clicks Confirm to complete the authentication.
After validating the OTP successfully, the user is directed to the next screen confirming that they have been successfully authenticated and can log out if required.
OTP with Hardware token
The user generates an OTP using their hardware token.
- On the next screen, the user enters the OTP and clicks Confirm to complete the authentication.
After validating the OTP successfully, the user is directed to the next screen confirming that they have been successfully authenticated and can log out if required.
SECURE_CODE
-
On the login screen, user must enter their username and Secure Code, then click Submit.
-
After successfully validating the user's Secure Code, the component displays the screen to authenticate using the second authentication factor, based on the defined value of the MFA property.
USER_ID_LESS
-
Onboard a user with any flow which includes registering mobile device. (e.g., SECURE_CODE in web or Mobile onboarding)
-
On the login screen, the User can see a button, click to generate QR code.
-
Scan the QR code with the registered mobile application.
-
Once approved by the user in the mobile application, the user will be logged in to the web application.
FIDO
-
On the login screen, the user must enter their username.
-
Users can authenticate using a FIDO authenticator/passkey through the web authentication platform
-
Once authenticated, the user will be logged in to the web application and redirected to the dashboard.
Authentication Component Services
Object Services
| ServiceName | DataModel | Mapping | Purpose | Input Parameters | Invoking |
|---|---|---|---|---|---|
|
HIDAuthService |
ApproveRequest |
initiate |
Send the Push notification to the HID Approve device. |
Username, deviceId |
HIDApproveInitiation > initiate |
|
HIDAuthService |
ApproveStatus |
poll |
Poll to the ApproveCallback service to fetch the status of user's response to the HID Approve Push notification. |
mfa_key (authRequest Id from the initiate service response) |
HIDPollConsensus > getHIDApprovalStatus |
|
HIDAuthService |
Devices |
searchDevices |
Get the list of devices associated with the user. |
username |
SearchPushDevicesOrch > getDevices |
|
HIDAuthService |
OTPRequest |
sendOTPLogin |
Send the OTP (SMS/Email) to the user. |
userId, AuthenticatorType (AT_OOBSMS/ AT_OOBEML), AuthenticatorValue (OOB Device Type code : DT_OOBSMS/DT_OOBEML) , msgId , password , username |
CustomOTPService > SendOTP |
| HIDAuthService | getScanToApproveQrData | getScanToApproveQrData | It will fetch data to generate QR code for login. | - | GetScanToApproveQrData (1.0).getScanToApproveQrData |
| HIDAuthService | ValidateSecureCode | validateOTPAuth | OTPAuthServices > validateOTPAuth | ||
Fabric Services
| Names | Operation Name | Service Type | Description |
|---|---|---|---|
|
ClientIdentity |
- |
Identity |
Fetches Client Bearer Token |
|
customHIDLogin |
- |
Identity |
End-user authentication with MFA validation |
|
ClientAuthIdentityWrapper |
getClientBearerToken |
Integration |
IntegrationWrapper of ClientIdentity |
|
DependencyManager |
|
Integration |
Resolves the dependencies for HIDProcessor.jar. |
|
HIDApproveInitiation |
Initiate |
Integration |
Sends an HID Approve Push notification to the user's registered device. |
|
HIDPollConsensus |
getHIDApprovalStatus |
Integration |
Java service to fetch the callback response of the HID Approve push notification. |
|
OTPAuthServices |
hardwareOTPAuth |
Integration |
Validates the Hardware token OTP for the user. |
|
OTPAuthServices |
validateOTPAuth |
Integration |
Validates the OOB (SMS/Email) OTP. |
|
PasswordAuthServices |
passwordValidation |
Integration |
Validates the user's static password. |
|
SearchServices |
SearchDeviceAuth |
Integration |
Lists the devices associated with the user. |
|
SearchServices |
SearchUserAuth |
Integration |
Searches for the user. |
| UserIdentityAttributes | getAttributes | Integration | Temenos Digital service to fetch the customer's identity attributes. |
|
SearchPushDevicesOrch |
getDevices |
Orchestration |
Orchestration to fetch the userid and then gets the list of devices associated with the user. |
| OTPServices | sendOOBLogin | Integration | Sends an OOB (SMS/Email) OTP to the user. |
| HIDIdentityService | login | Integration | Identity service endpoint. |
| HIDIdentityService | secondFactorLogin | Integration | Identity service endpoint for MFA |
| GetScanToApproveQrData | getScanToApproveQrData | Integration | It will fetch data to generate QR code for login. |
| FIDO | getTokenUsingAuthorizationCode | Integration | It will generate the token by transferring the generated authorization code. |
| FIDO | getAuthenticationOptions | Integration | It will provide the registered credentials for the client to generate the assertion. |
| FIDO | getAuthorizationCode | Integration | |
| FIDO | authenticate | Integration | It will provide the assertion from the client which will then authenticate user. |
| PushedAuthorizationRequest | PAR | Integration | It will generate the request_uri for subsequent calls. |
| AuthenticatorPolicy | getPasswordPolicy | Integration | Provides the Password policy. |
| CustomOTPService | sendOTP | Integration | Used to send OTP. |
| OTPServiceKMSOrch | addOOBAndSendOTPAuthService, addOOBAndSendOTPAppliance , generateAndSendOTPAppliance, generateAndSendOTPAuthService, sendLoginOTPAppliance, sendLoginOTPAuthService | Orchestration | Used for adding OOB authenticator , generate OTP and sending OTP. |
| HIDSoapServices | indirectPrimaryAuthenticateDevice | Integration (Soap Service) | Generate and Send OTP |
| HIDOTPUtilServices | fetchPhoneNumber | Integration | Used to fetch Phone number of the user. |
| OpenIDConfigService | FetchOpenIDConfig | Integration | Used to fetch the well known openID configurations. |
Java Services
| Service Name | Purpose | Dependencies | Called by (Service Name-Operation) |
|---|---|---|---|
|
HIDPollForConsensus |
Java service which keeps polling for 45 seconds to get the status of the HID Approve Push notification sent to the user. |
HIDPollConsensus-getHIDApprovalStatus |
|
| OTPDeliveryService | Java Service to decide which delivery gateway to use to send SMS | HID_SMS_MSG_TEMPLATE , IS_HID_GATEWAY_ENABLED , HID_OOB_SMS_OTP_AUTHTPYE, HID_OOB_EMAIL_OTP_AUTHTPYE, HID_SMS_DEVICE_TYPE , HID_EMAIL_DEVICE_TYPE | CustomOTPService |
Listener Endpoints (HTTP Servlets)
| Name | URL | Purpose | Dependencies |
|---|---|---|---|
|
ApproveCallBackEndpoint |
https://hidglobal-dev.temenos-cloud.net/services/ApproveCallBackEndpoint |
Listen to the callback response sent by the HID Authentication Service for the user's response to the HID Approve Push notification. |
|
Authentication Pre/Post Processors
| Names | Description | Used by (ServiceName-Operation) |
|---|---|---|
|
GetBearerTokenPostProcessor |
Gets the access token from the result and adds it to the DataControllerRequest. |
ClientAuthIdentityWrapper-getClientBearerToken |
|
GetDevicesOrchPostProcessor |
Processes the output of the get devices orchestration service, adds an error message to the result if any error occurs during the operation. |
SearchPushDevicesOrch-getDevices |
|
HIDApprovePostProcessor |
Inserts the client_notification_token from the service output to the cache for verification during the callback. |
HIDApproveInitiation-initiate |
|
SearchDeviceAuthPostProcessor |
Processes the output of Search devices for user service output to set the friendlyname, start date and expiry date to empty when the particular record in the collection does not have the value. (Post processor to fix the platform issue as collection does not work correctly on the Kony platform.) |
SearchServices-SearchDeviceAuth |
|
SearchUserAuthPostProcessor |
Processes the output of Search user service and sets the value of UserExist to true/false in DataControllerRequest to be used by other services. |
SearchServices-SearchUserAuth |
|
CustomMFAValidation |
Based on the input auth type, invokes the Integration service to authenticate the user for the second authentication factor and validates the MFA. |
CustomMFASelector-validateMFA |
|
CustomValidateAuthentication |
Based on the input auth type, invokes the Integration service to authenticate the user for the first authentication factor and generates the result data set for MFA validation. |
CustomFactorValidation-login |
|
GetBearerTokenPreProcessor |
Sets the value of x-kony-app-key and x-kony-app-secret in request header from the configured server settings KONY_APP_KEY and KONY_APP_SECRET respectively. |
ClientAuthIdentityWrapper-getClientBearerToken |
|
HardwareOTPAuthPreprocessor |
Sets the value of AuthenticationType in the input for the request if configured in the server settings HARDWARE_OTP_AUTHTYPE. If not configured, takes the default value (AT_OTP). |
OTPAuthServices-hardwareOTPAuth |
|
HIDApprovePreprocessor |
Generates the login_hint_token and client_notification_token for the HID Approve Push notification initiate request. |
HIDApproveInitiation-initiate |
|
OTPValidationPreprocessor |
Sets the value of AuthenticationType in the input for the request if configured in the server settings OOB_SMS_OTP_AUTHTYPE, OOB_EMAIL_OTP_AUTHTYPE or SECURE_OTP_AUTHTYPE. If not configured, takes the default value (AT_OOBSMS/AT_OOBEML/AT_EMPOTP). |
OTPAuthServices-validateOTPAuth |
|
PasswordValidationPreprocessor |
Sets the value of AuthenticationType in the input for the request if configured in the server settings PASSWORD_AUTHTYPE. If not configured, takes the default value (AT_STDPWD). |
PasswordAuthServices-passwordValidation |
|
SearchDeviceAuthPreProcessor |
Verifies if the user exists from the Search User service output. If not, then adds the error message to the service output. |
SearchServices-SearchDeviceAuth |
| HIDIdentityServicePreProcessor | To remove the cache value to secure services | HIDIdentityService\ login |
| SendOOBLoginPreprocessor | Sets the value of AuthenticationType in the input for the request if configured in the server settings OOB_SMS_OTP_AUTHTYPE, OOB_EMAIL_OTP_AUTHTYPE or SECURE_OTP_AUTHTYPE. If not configured, takes the default value (AT_OOBSMS/AT_OOBEML/AT_EMPOTP). | OTPServices\ sendOOBLogin |
| OOBAuthenticatorPostProcessor | To remove the cache value to secure services. | OTPServices\ sendOOBLogin |
| GetDevicesOrchPreProcessor | This is to check whether the cache value is present or not and execute the service. | SearchPushDevicesOrch\ getDevices |
| GetDevicesOrchPostProcessor | To remove the cache value to secure services. | SearchPushDevicesOrch\ getDevices |
| GetScanToApproveQrDataPreProcessor | It will Create Payload for the getScanToApproveQrData Service call. | GetScanToApproveQrData\ getScanToApproveQrData |
| GetScanToApproveQrDataPostProcessor | It will process the response from service call. | GetScanToApproveQrData\ getScanToApproveQrData |
| GetAuthCodePostProcessor | It will pass generated code and context to the result of Fabric API. | FIDO\ getAuthorizationCode |
| GetAuthenticatedTokenPreProcessor | It will add csrf token to the request header. | FIDO - getAuthorizationCode |
| GetCredentialOptionsPostProcessor | It will add csrf token to the request for next call. | FIDO - getAuthenticationOptions |
| ClientBasePreProcessor | It will add client auth token to the request. | FIDO - getAuthenticationOptions |
| AuthenticatePostProcessor | It will add csrf token to the request for next call. | FIDO - authenticate |
| FIDOValidationPreProcessor | It will check for authenticator from server settings. | FIDO - authenticate |
| PARPreProcessor | It will read the server property for clientId and request_uri | PushedAuthorizationRequest - PAR |
| PARPostProcessor | It will add request_uri to the request for next call. | PushedAuthorizationRequest - PAR |
| ApplianceOTPGeneratorPreprocessor | Used to generate OTP for Applicance | HIDSoapServices |
| GenerateOTPPreprocessor | Used to generate OTP for Authservice | OTPServices |
| SendOTPPreprocessorKMS | Used to send OTP | OTPServiceKMSOrch |
| FetchUserDetailsPostprocessor | Used to Fetch Phone Number to send OTP | HIDOTPUtilService |
| GenerateOTPPostprocessor | Used to generate OTP for Authservice | OTPServices |
| SendOTPPostprocessorKMS | Used to send OTP | OTPServiceKMSOrch |
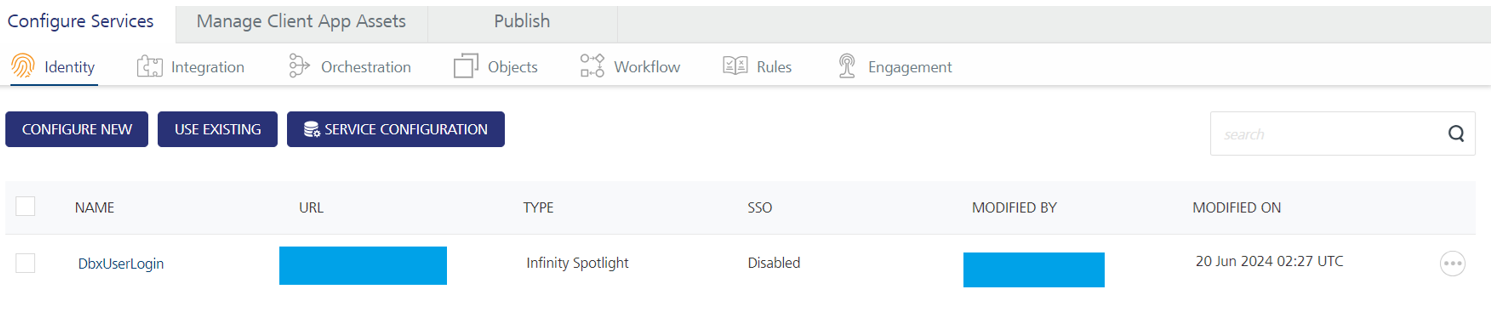
HID Identity Service Configuration
This section describes how to configure the Infinity Identity service (DbxUserLogin) endpoints for the HID identity service (CustomHIDLogin) to perform login validation.
To work with this identity service, you must import the following components in the Quantum visualizer:
-
For web applications: Login component.
-
For mobile applications: MobileApproveSDK component.
Name: HID_IS_FETCH_USER_ATTRIBUTES (Default value: false)
Description: This property controls the behavior of the identity provider service.
-
If the identity provider service is set to DbxUserLogin (Custom Identity): Set this property to true.
-
If the identity provider service is set to customHIDLogin (default): This property can be left as false (default value).
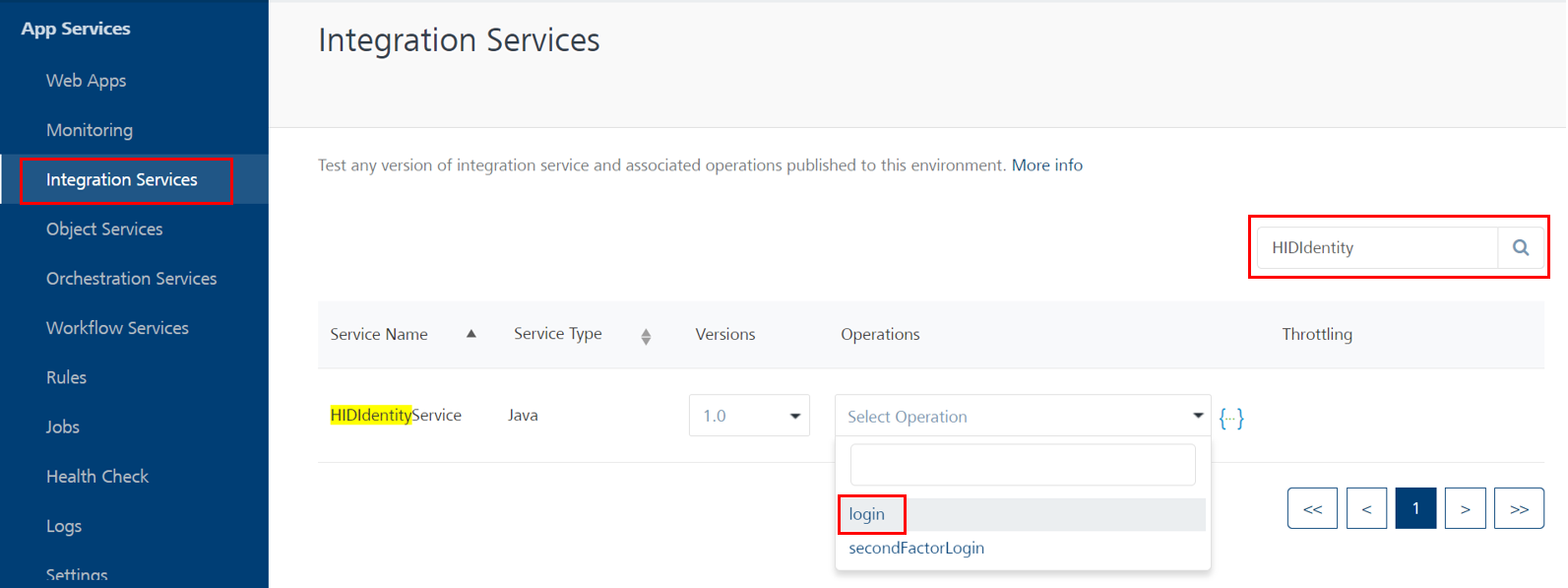
To validate the endpoints, log in to the Fabric Console and execute the HIDIdentityService/login integration service:
-
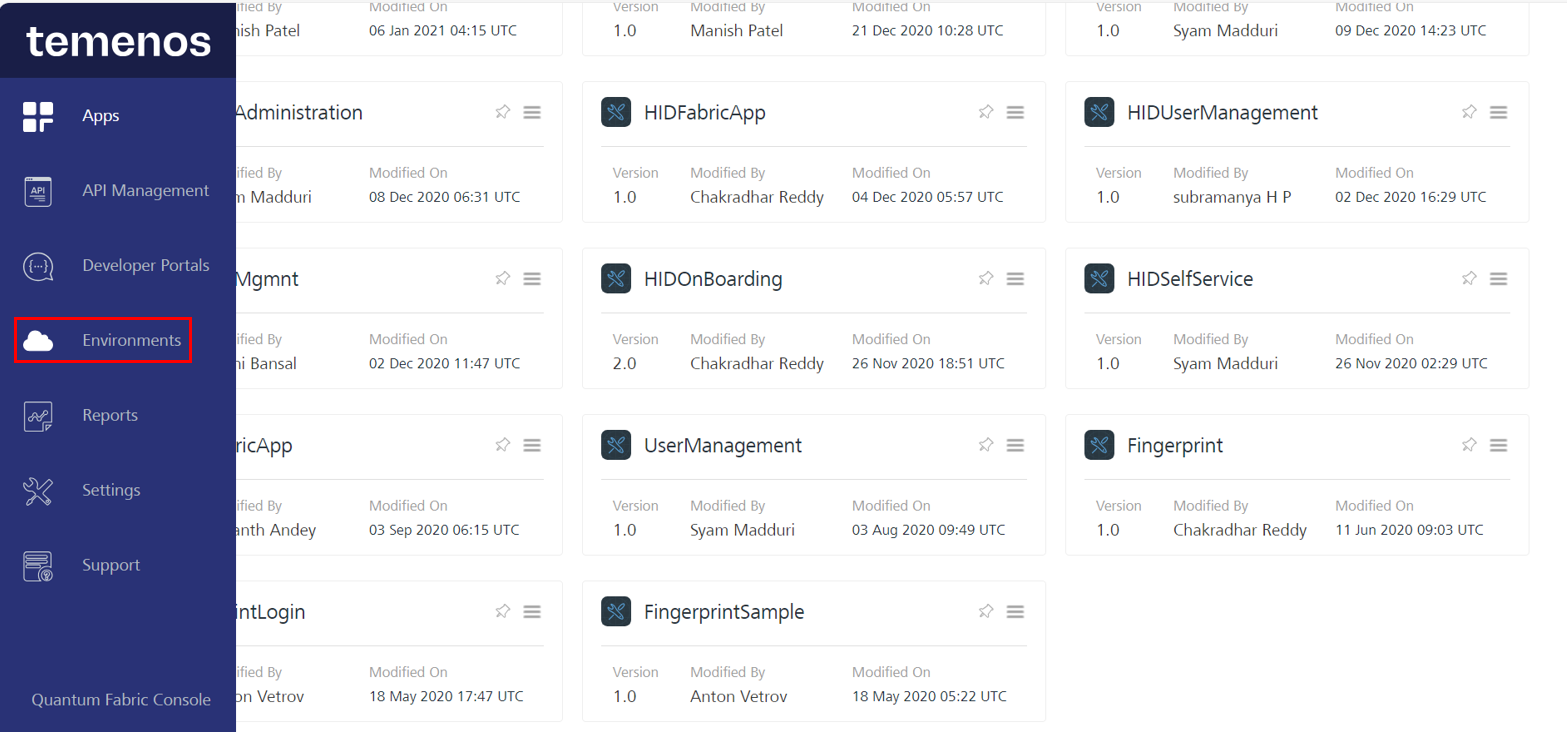
Open Fabric and select the Environments option from the left menu.
-
Select the App Services option.
-
Select Integration Services, search for HIDIdentityService, and select the login operation from the Select Options drop-down menu.
-
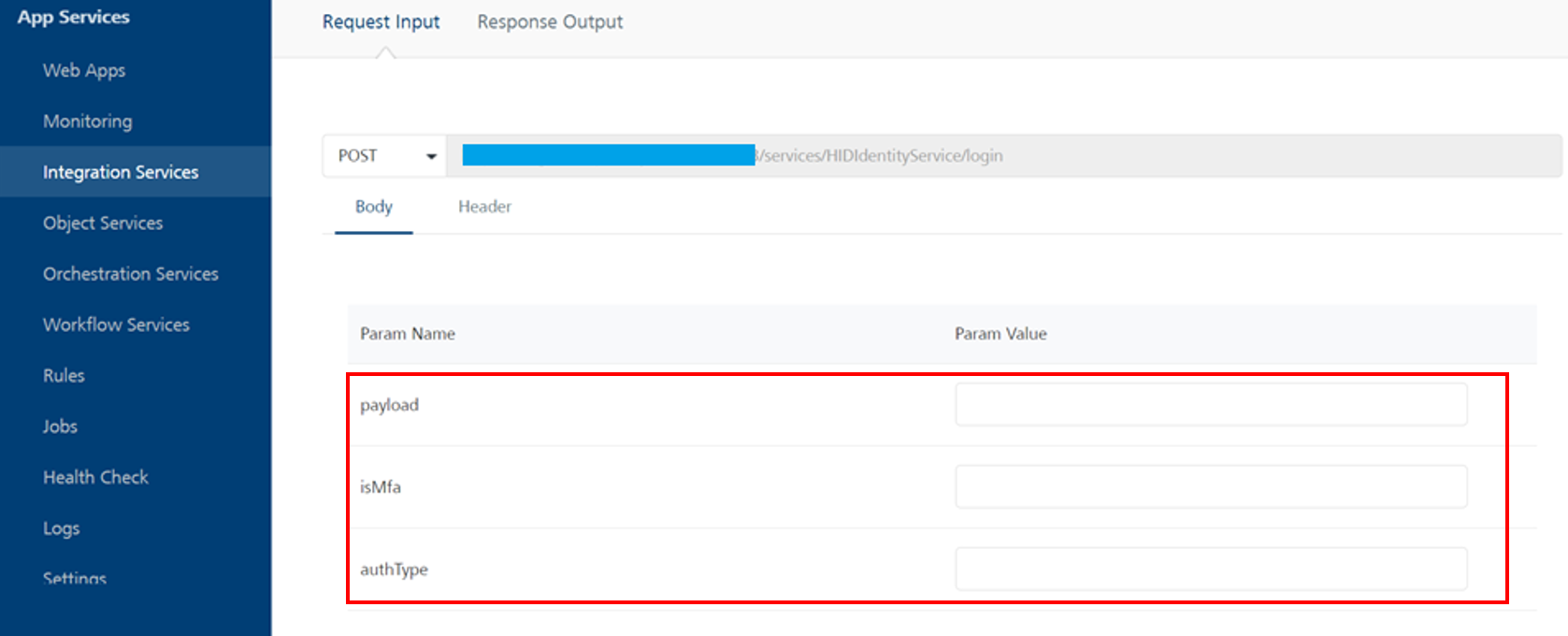
The following page will be displayed, allowing you to enter parameter values and receive a response.
Parameters values to be passed:
-
Payload:
CopyPayload: (update your payloads accordingly){
"Meta": {
"EventType": "urn:com:temenos:security:event:login:v1",
"RiskScore": {
"Required": "0",
"Current": "0"
},
"TransactionId": "9090"
},
"urn:com:temenos:security:event:login:v1": {
"Scope": "LOGIN",
"Name": "Temenos Internet Banking",
"userid": "UpdateUsenameHere",
"password": "UpdatePasswordValueHere"
}
}Note:Update only the userid and password values within the payload.
-
userid: This value is the same as username.
-
password: This value is your password/secure OTP used for first-factor authentication.
-
-
isMFA: The value indicates whether your application supports multi-factor authentication (true) or single-factor authentication (false).
-
authType: It is dependent on the first factor of authentication.
-
For static password: STATIC_PWD
-
For secure code: SECURE_CODE
-
For OOB PIN: OTP_SMS_PIN
-
-
-
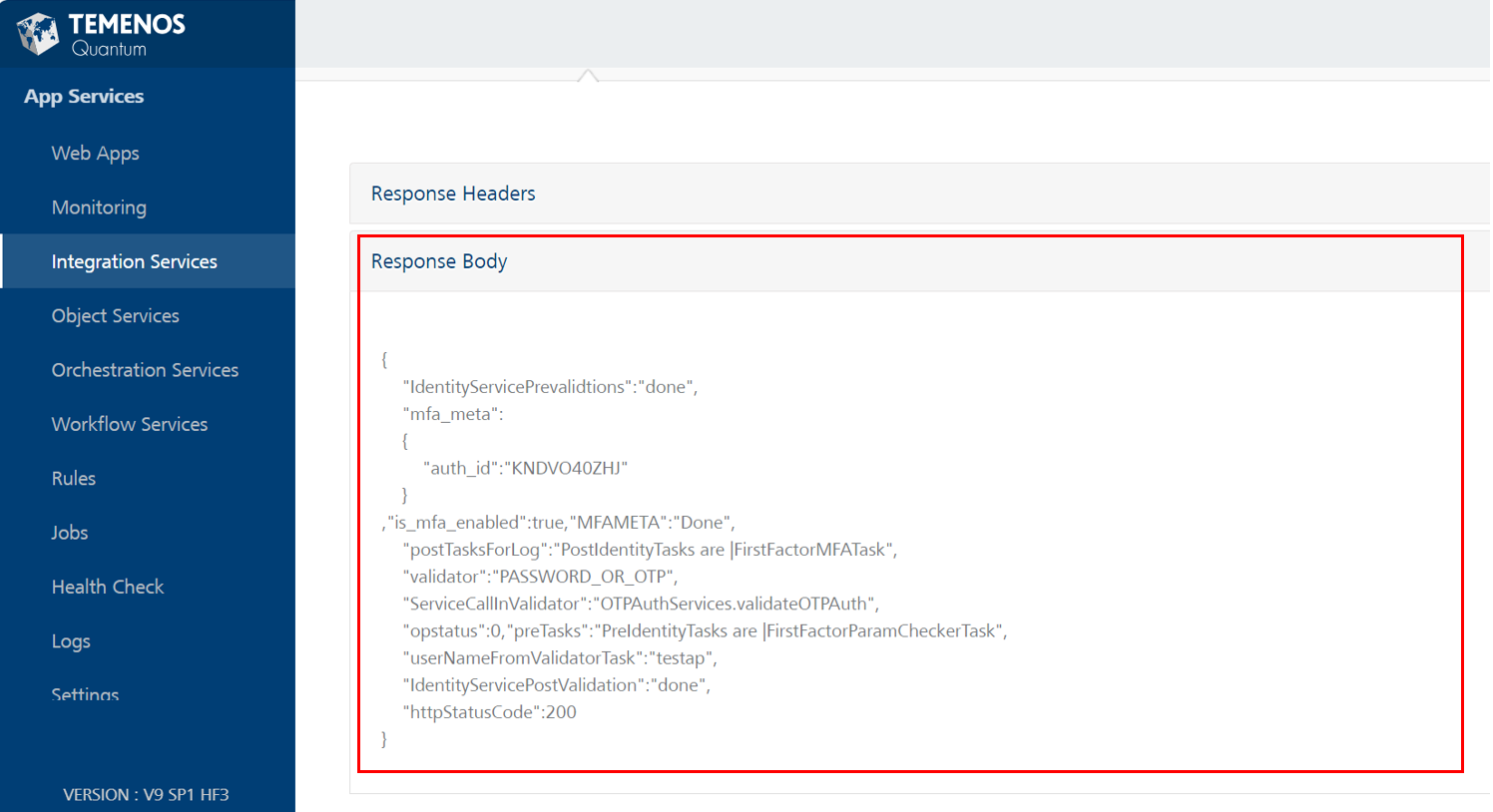
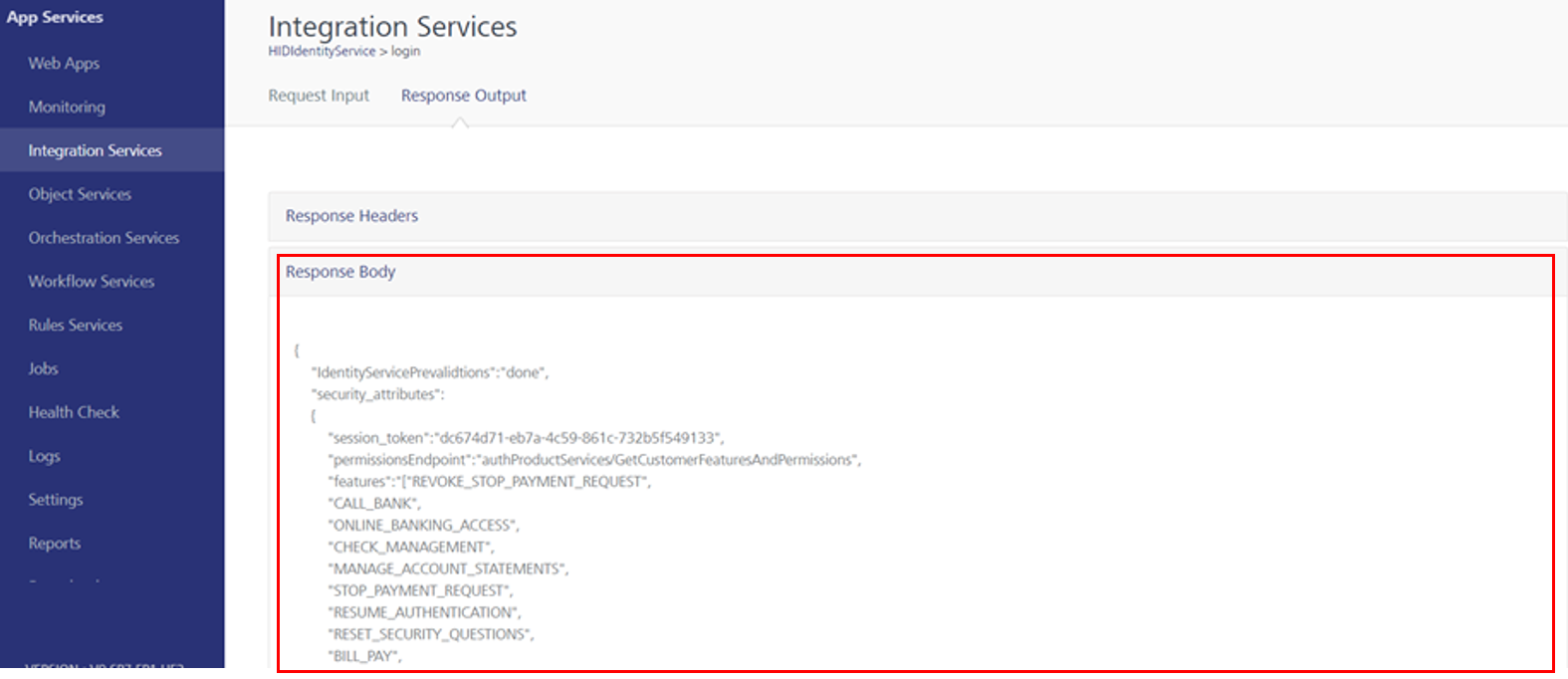
A successful response from the API would look as below with isMFA is set to true.
-
A successful response from the API would look as below with isMFA is set to false.
-
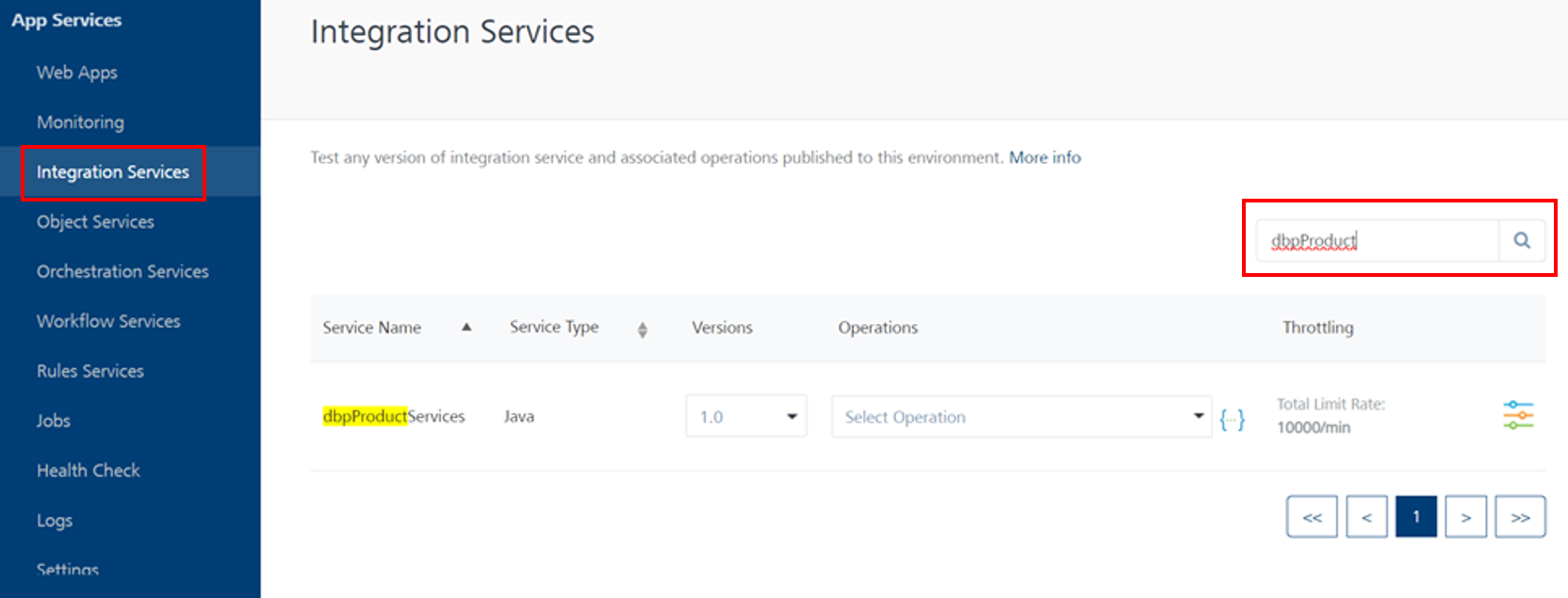
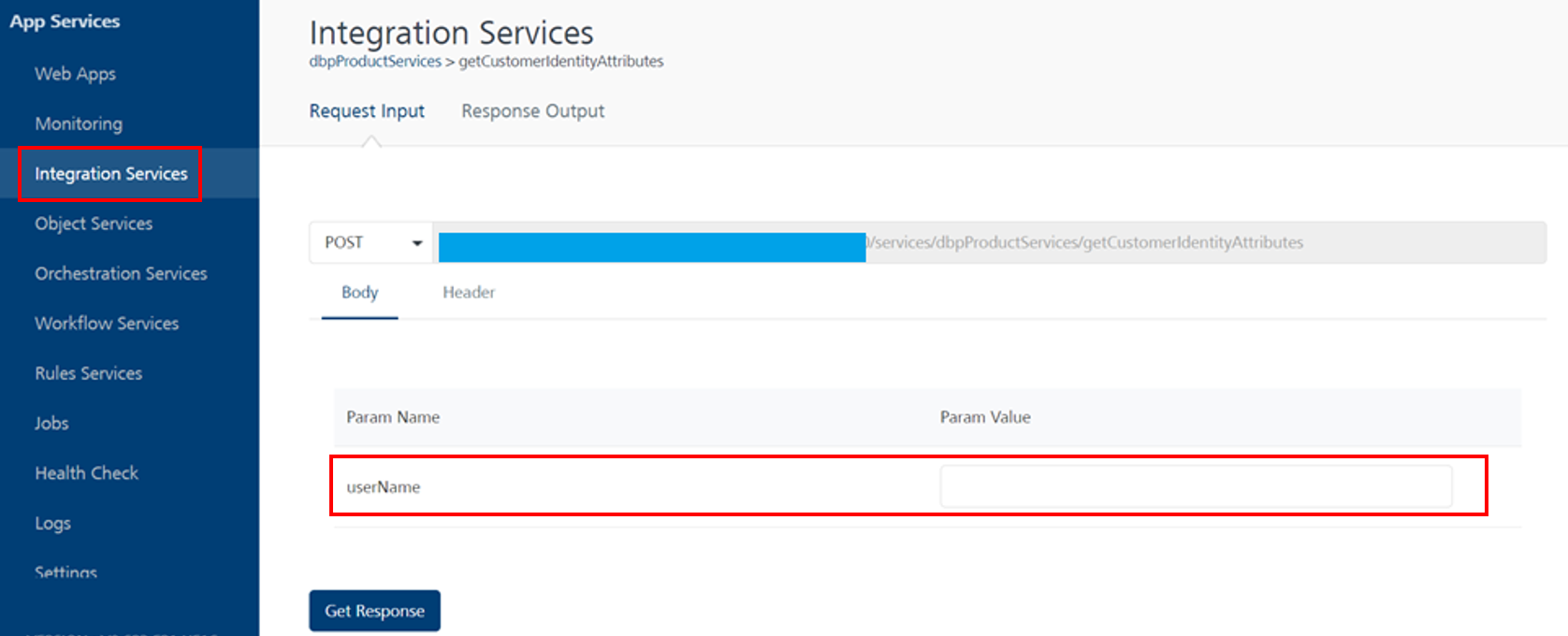
In the Fabric console, navigate to Integration Services and search for the getCustomerIdentityAttributes operation within dbpProductServices.
-
You will be able to see the below page where you can add parameter values and get a response.
Note:-
userName must exist in the Infinity database.
-
Since the API uses anonymous app user security, include x-kony-app-key and x-kony-app-secret in the header.
-
Set these keys only if they haven't been set for HID Global services previously.
-
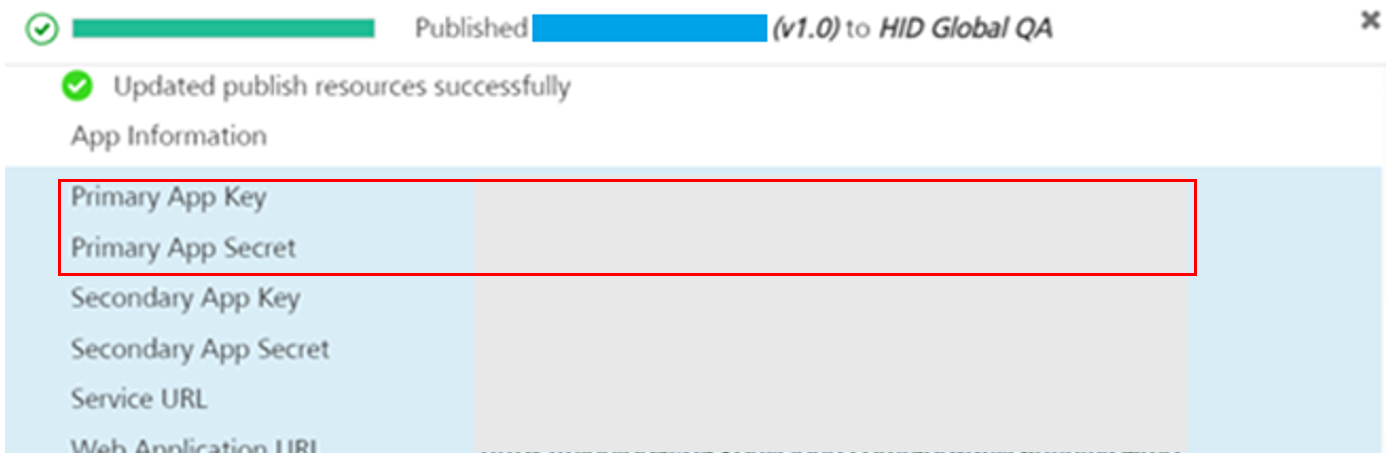
Select the app where you have the HID Global services available, and select the Publish tab.
-
Within the Server properties section, enter the App Key and App Secret values.
Use the Primary App Key and Primary App Secret for this configuration.
-
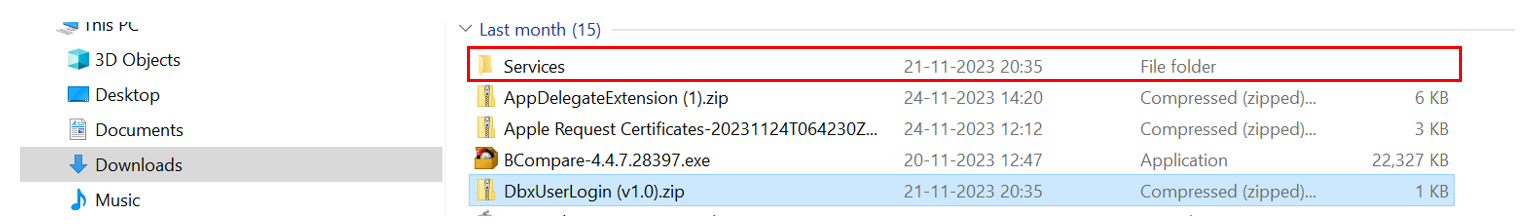
Export the DbxUserLogin identity service from Fabric.
-
Extract the DbxUserLogin(v1.0).zip and you will find the services folder at the top level, as shown in the below image.
-
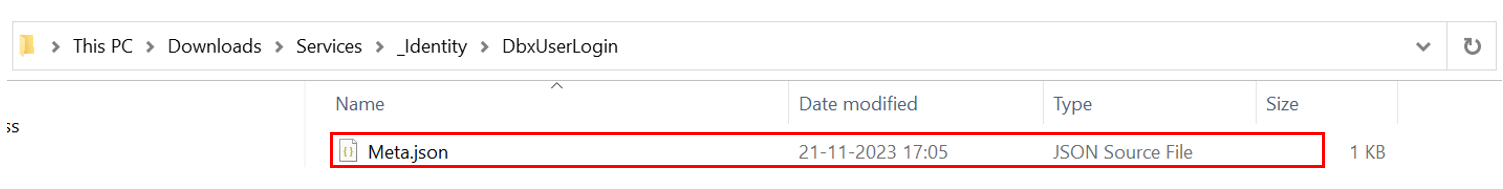
Open the Meta.json file (from location: ../Services/_Identity/DbxUserLogin/Meta.json) in the text editor and remove the subtype key and the corresponding value from the config object.
-
Inside the config object, add a new property named mfa_url.
-
Set the value of mfa_url to the Second-factor endpoint of the CustomHIDLogin identity service.
-
Modify the custom_idp_url property to point to the First-factor endpoint of the CustomHIDLogin identity service.
CopyBefore Changes
{
"name" : "DbxUserLogin",
"displayName" : "DbxUserLogin",
"type" : "custom",
"version" : "1.0",
"metaPreference" : -1,
"config" : "{
\"pre_mfa_token_timeout\":10,
\"header_params\":[\"x-kony-integrity\"],
\"session_restrictions\":{\"session_restriction_type\":\"allow_any_number_of_sessions\"},
\"sub_type\":\"customer360\",
\"is_mfa_enabled\":true,
\"provider_params\":{},
\"body_params\":{},
\"custom_idp_url\":\"https://abc.domain.com /services/DbxCustomerLogin \"
}",
"policyConfig" : "{\"def_user_status\":\"pending\",\"max_login_fail\":5}",
"admissionPolicy" : "no_approval_needed",
"identityMeta" : {
"allow_sso" : false
},
"isIntegrityEnabled" : true,
"ssoenabled" : false,
"empty" : true
}CopyAfter Changes
{
"name" : "DbxUserLogin",
"displayName" : "DbxUserLogin",
"type" : "custom",
"version" : "1.0",
"metaPreference" : -1,
"config" : "{
\"pre_mfa_token_timeout\":10,
\"header_params\":[\"x-kony-integrity\"],
\"mfa_url\":\" https://abc.domain.com/services/HIDIdentityService\SecondFactorlogin",
\"session_restrictions\":{\"session_restriction_type\":\"allow_any_number_of_sessions\"},
\"is_mfa_enabled\":true,
\"tracking_attribute\":\"no_tracking\",
\"provider_params\":{},
\"body_params\":{},
\"custom_idp_url\":\"https://abc.domain.com /services/HIDIdentityService \"
}",
"policyConfig" : "{\"def_user_status\":\"pending\",\"max_login_fail\":5}",
"admissionPolicy" : "no_approval_needed",
"identityMeta" : {
"allow_sso" : false
},
"isIntegrityEnabled" : true,
"ssoenabled" : false,
"empty" : true
} -
Save the changes, zip the Services folder, and rename it as DbxUserLogin(v1.0).zip.
-
Go to API Management in your fabric and import the updated service Zip file.
If you check the DbxUserLogin service after the successful import, you will be able to observe that the type of the service has changed to Custom.
-
Open the Fabric app where DbxUserLogin Identity service is present.
-
Go to Publish Tab.
-
Click the Configure and Publish option below.
-
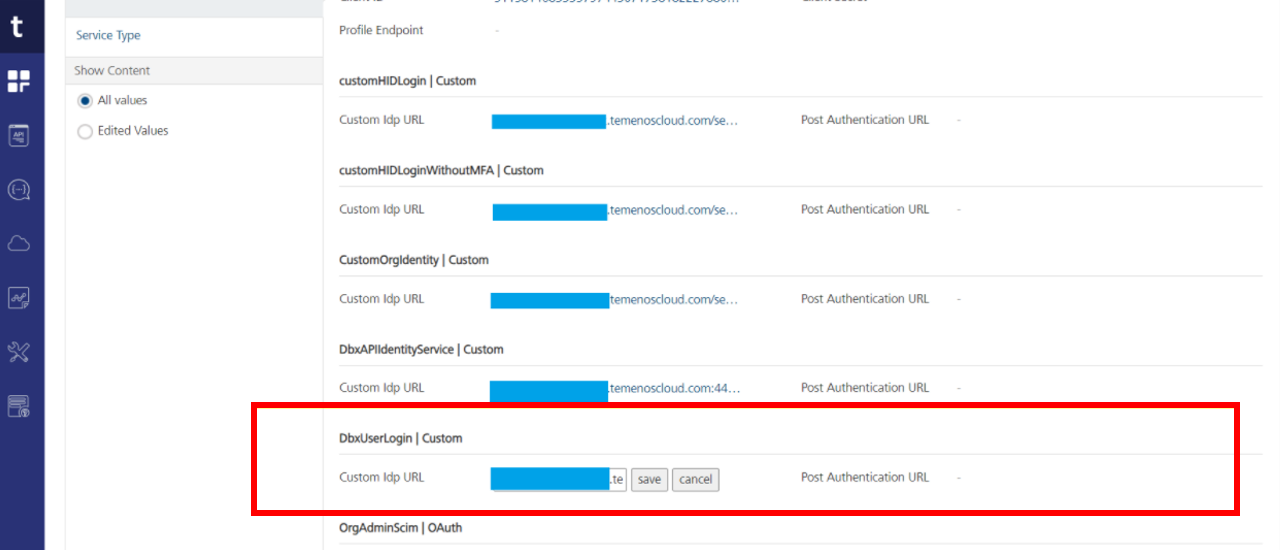
Expand the Service configuration and expand the Identity service configuration.
-
Update the custom idp URL with the First-factor endpoint of the DbxUserLogin.
-
Publish the Fabric application.
Troubleshooting Fabric Services
Refer to troubleshooting the User Authentication Fabric Services.
Risk-based User Authentication
HID Temenos Digital Component additionally supports an adaptive and risk-based authentication. It is optional i.e., You can enable or disable this functionality based on your needs.
HID Risk Management Solution provides this threat detection solution for real time risk-based authentication.
HID Temenos Digital Component enables you to easily integrate with the HID RMS Web component and use the risk-based Login flow as an add-on feature available as part of User Authentication (this section) component.
Refer HID RMS Web component - Login flow for more information.