Mapping User Sources and HID Visitor Manager User Groups
Introduction
As covered in the identity synchronization setup, users from Azure AD can be synced into HID Visitor Manager. We also covered how Azure AD Single Sign-on can be enabled for HID Visitor Manager. In this guide, we will cover how Azure AD user groups can be mapped to HID Visitor Manager user groups so that identities logging into the HID Visitor Manager automatically get assigned the correct roles.This capability will help administrators avoid the step of configuring HID Visitor Manager user groups manually for every identity synced from Azure AD.
Pre-Requisites
The following pre-requisites must be met before proceeding:
-
When using Azure AD user source, identity synchronization setup must be complete. Both identities and user groups must be synchronizing from the Azure AD user source.
-
If the user source is not being used, identities must be manually set up in HID Visitor Manager and manually mapped to Azure AD user groups.
-
HID Visitor Manager SSO using SAML must be completed in both cases.
Steps to Map User Source User Groups with HID Visitor Manager User Groups
When using Azure AD user source:
This option must be used to configure group mapping for Azure AD User Source. Identities that are synced from Azure AD User Source will utilize this configuration to get relevant access to the application.
-
Login to the HID Visitor Manager application and navigate to Admin > User Groups > Mappings tab.
-
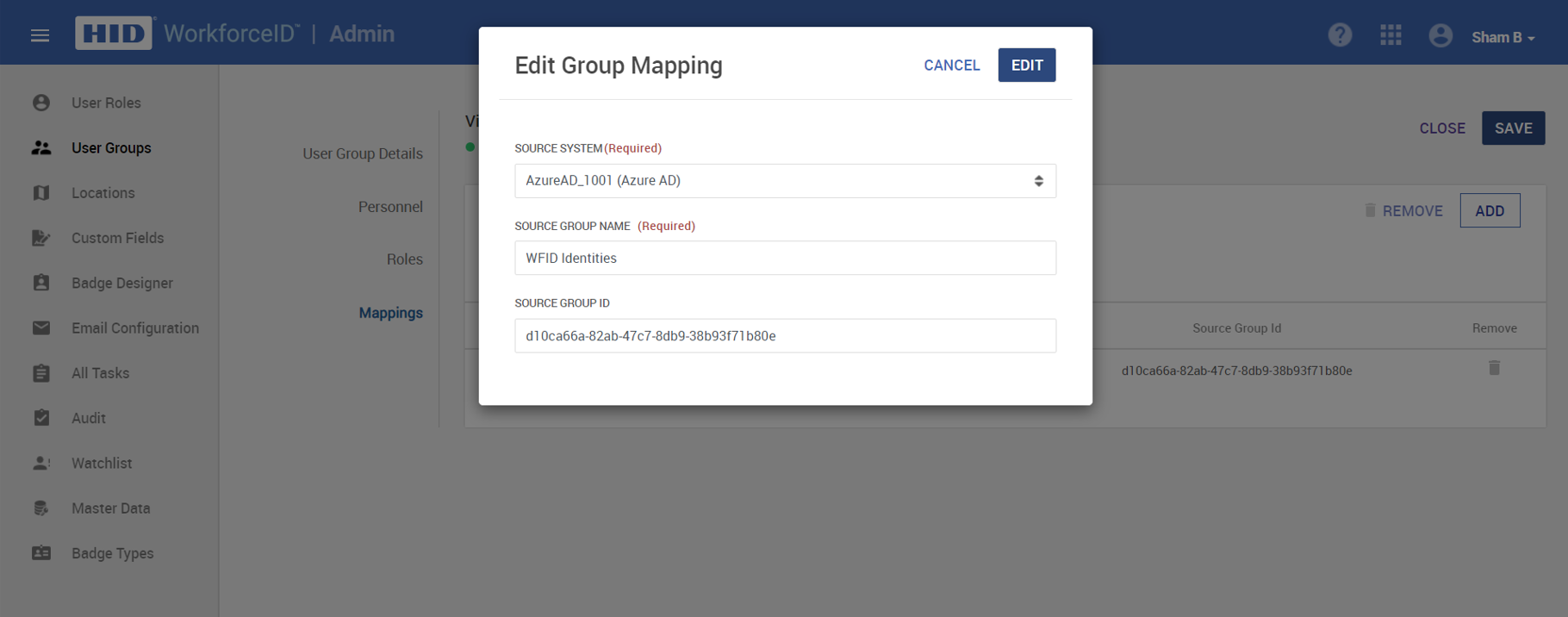
Click ADD and select the Azure AD user source as Source System. Enter the first few characters of the Azure AD group name and it will populate the synced Azure AD User Groups matching with those characters. Once the group name has been selected, the SOURCE GROUP ID (User Group GUID) field is automatically populated from Azure AD. Click on the SAVE to save the mapping.
-
This will map the users belonging to the above Azure AD user group to the HID Visitor Manager user group. When logging into HID Visitor Manager, all the Azure AD users assigned this Azure user group will use the mapped HID Visitor Manager user group.
Please do not update the Source Group ID, as it is synchronized with Azure AD.
Verify group mapping for users synced via Azure AD user source:
-
Create an identity in Azure AD and assign user groups to it. Ensure that the user group is added to the enterprise application in Azure AD where SSO via SAML is configured.
-
Map this user group to the relevant user group in HID Visitor Manager under Admin > User Groups. For example, Administrators to Visitor Administrators, or Operators to VMO, etc.
-
Log in to HID Visitor Manager with a newly added identity. The user gets access to the mapped user groups automatically.
When configuring SSO and user group mapping for default HID Visitor Manager user source:
This option must be used to configure group mappings for HID Visitor Manager User Source - the default user source in HID Visitor Manager. Identities that are manually added to HID Visitor Manager or are part of a bulk import belong to the HID Visitor Manager User Source and will utilize this configuration to get relevant access to the application. SSO must be enabled for HID Visitor Manager in such cases.
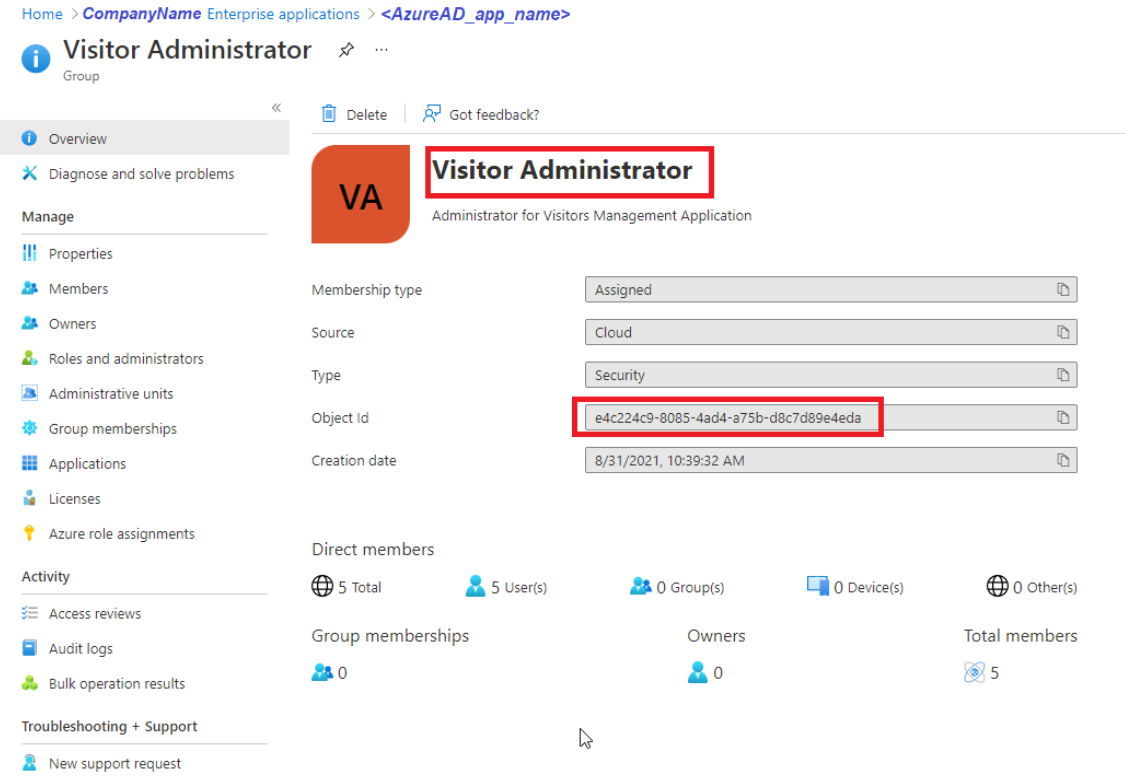
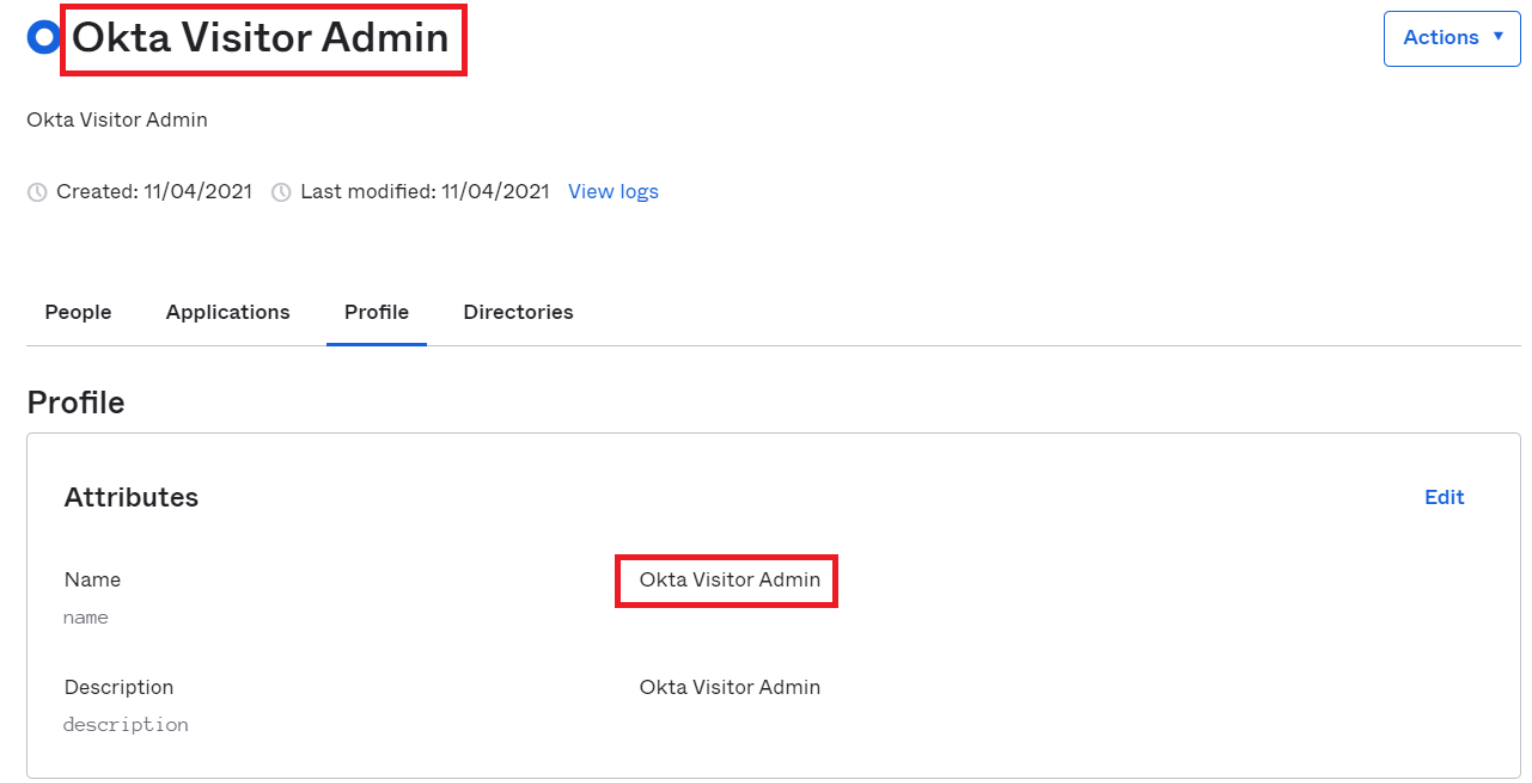
Before proceeding further, copy the Source Group Name and Source Group GUID of the user group from Azure AD. This is the user group that you want to map to the HID Visitor Manager user group
Azure AD
OKTA
-
Login to the HID Visitor Manager application and navigate to Admin > User Groups > Mappings tab for a selected user group, e.g. Visitor Administrator.
-
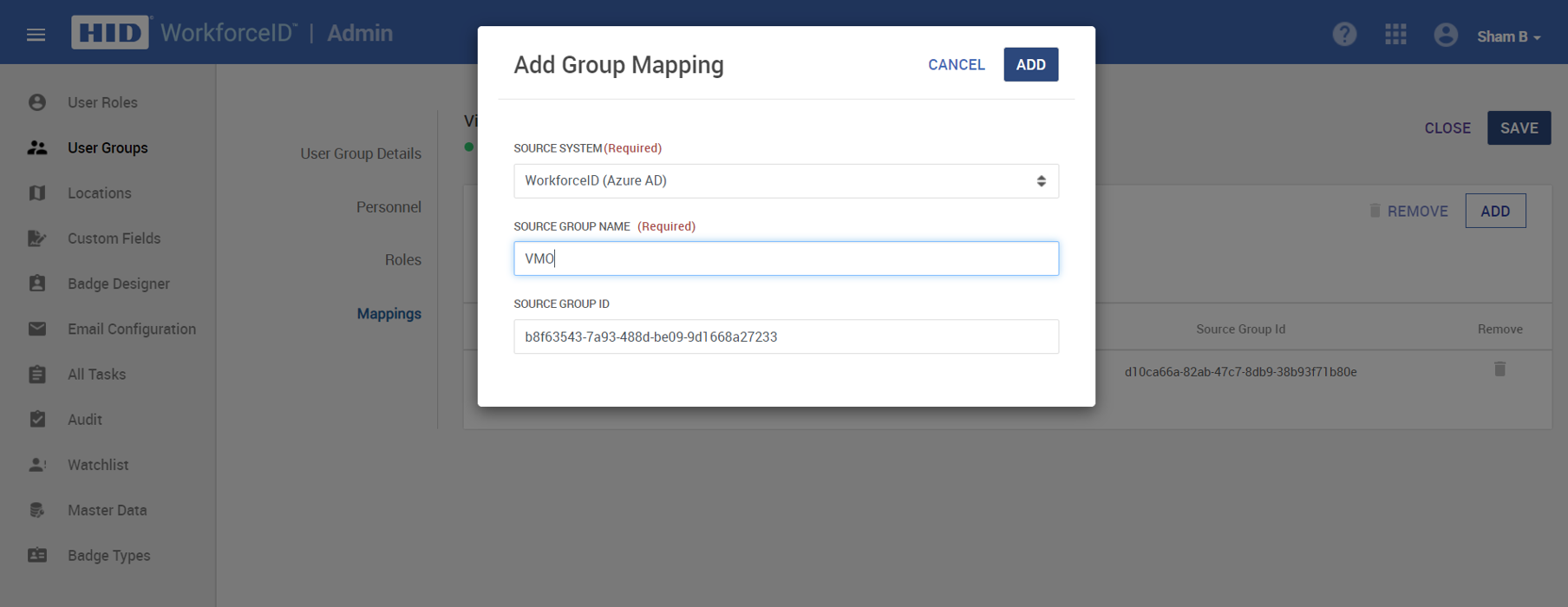
Click Add and select HID Visitor Manager as the Source System. Manually enter the Source Group name and Source Group GUID from the user source, then click ADD. Once all the mappings are added, click Save.
Azure AD
OKTA
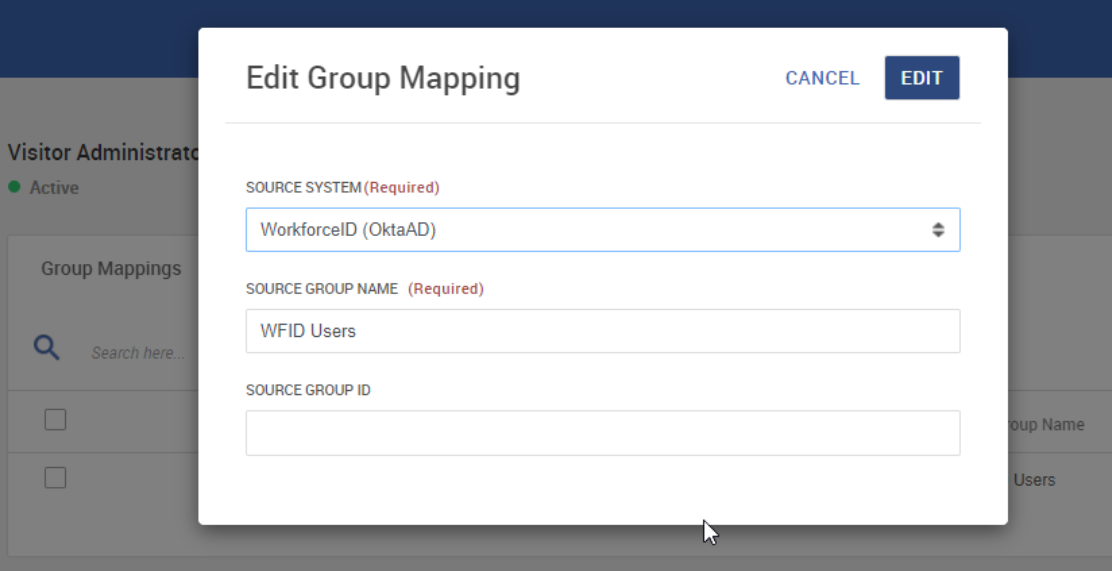
This will map the users belonging to the above Azure AD group to the HID Visitor Manager user group where this mapping is added. When logging into HID Visitor Manager, all the Azure AD users assigned to this Azure user group will use the mapped HID Visitor Manager user group.
Verify group mapping for HID Visitor Manager users:
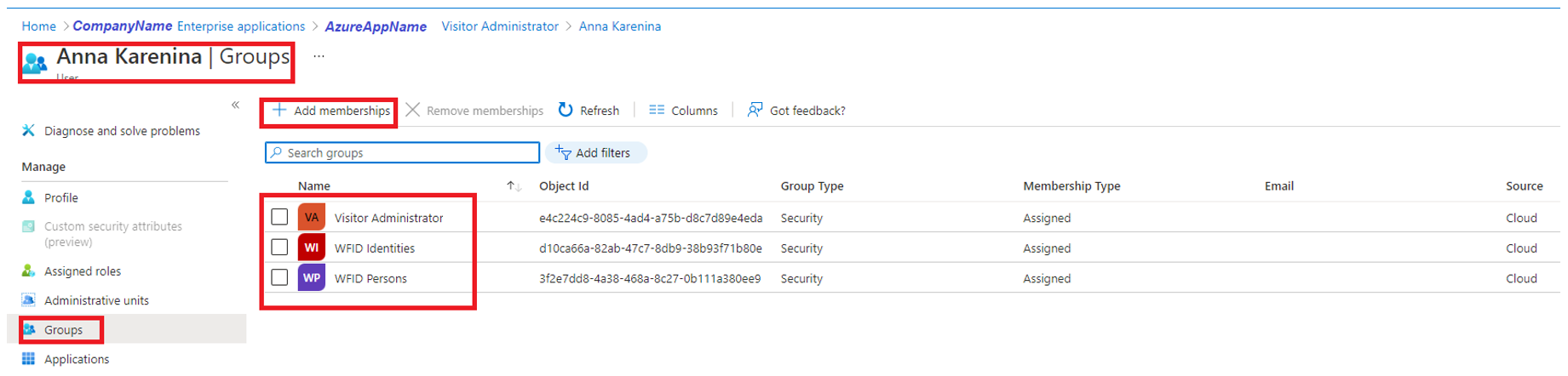
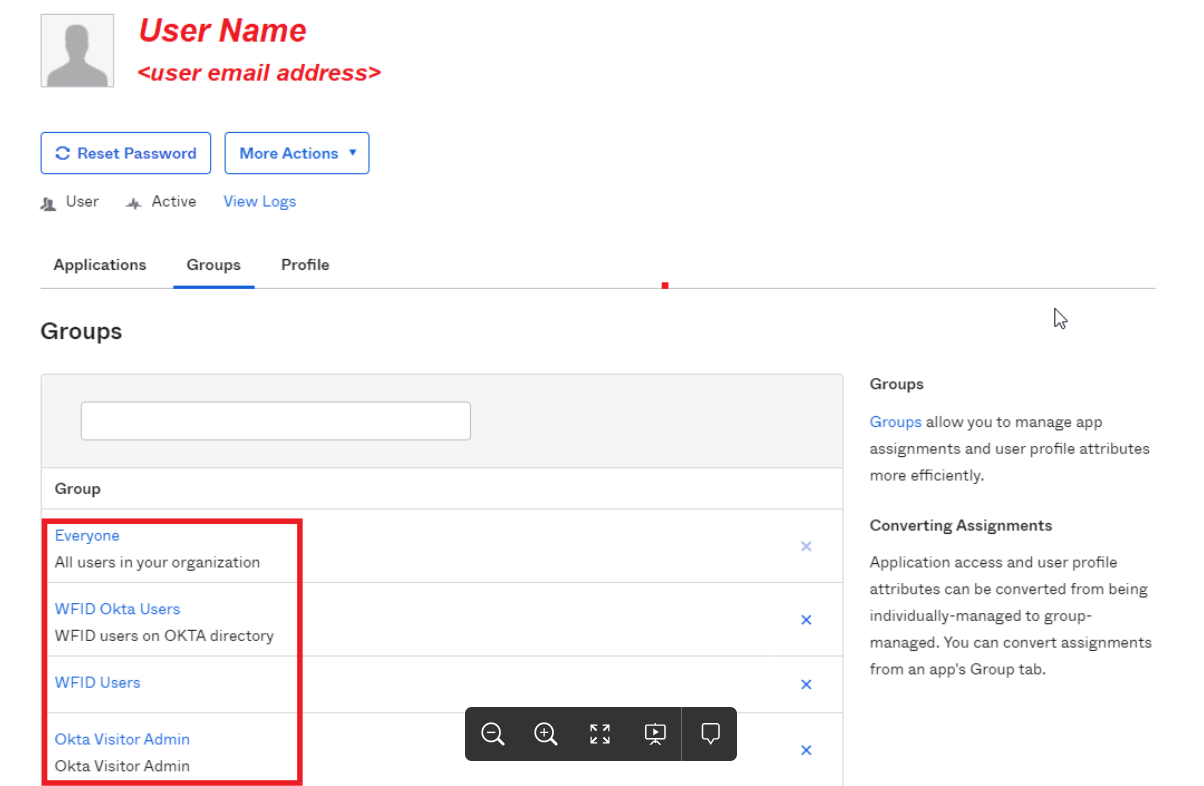
Create an identity in HID Visitor Manager manually and add the same identity in Azure AD. Make sure the login name in HID Visitor Manager is the same as the username in Azure AD. Assign user group to the enterprise application created in Azure AD for the purpose of Single Sign-On.
Azure AD
OKTA
-
Map the user group from Azure AD to the relevant user group in HID Visitor Manager under Admin > User Groups. For example, Administrator to Visitor Administrator, or Operators to VMO.
-
Log in with a newly added identity's username via SSO. The user will automatically get the mapped user groups.





