Configuring Customer Central for Passkey Management
Customer Central integrates with the following directories:
Integrating with Microsoft Entra ID
Register Customer Central as an Application in Microsoft Entra ID
A Microsoft Azure directory with a valid license for Microsoft Entra ID
A Microsoft Entra ID administrator account with the required role to create an application (for example, Cloud Application Administrator)
The Administrator or Device Service Administrator role, or at least the Create Configuration privilege for Entra ID
Customer Central must be registered as an application with Microsoft Entra ID to be able to connect to Entra ID services.
For details on this procedure, refer to Register an application with the Microsoft identity platform | Microsoft Learn.
When registering your application with Microsoft Entra ID, make sure you set up the following configuration:
-
Log on to the Microsoft Entra admin center (https://entra.microsoft.com/#home) and, if necessary, switch to the required directory.
-
Under Entra ID in the left menu, navigate to App registrations and click New registration.
-
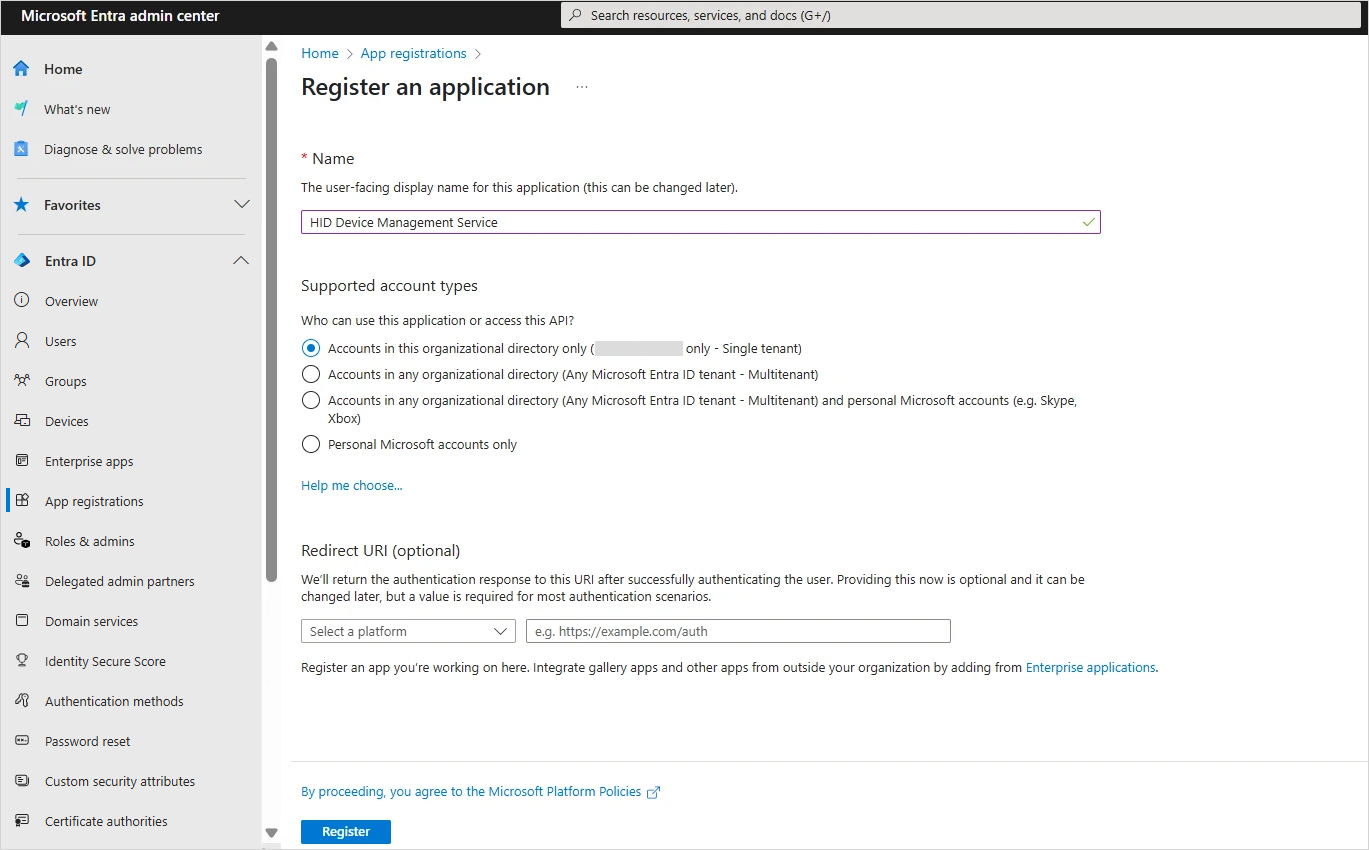
Create the application as follows:
-
Enter a Name for the application.
-
Under Supported account types, select Accounts in this organizational directory only (<your directory> only - Single tenant).
-
Click Register.
-
-
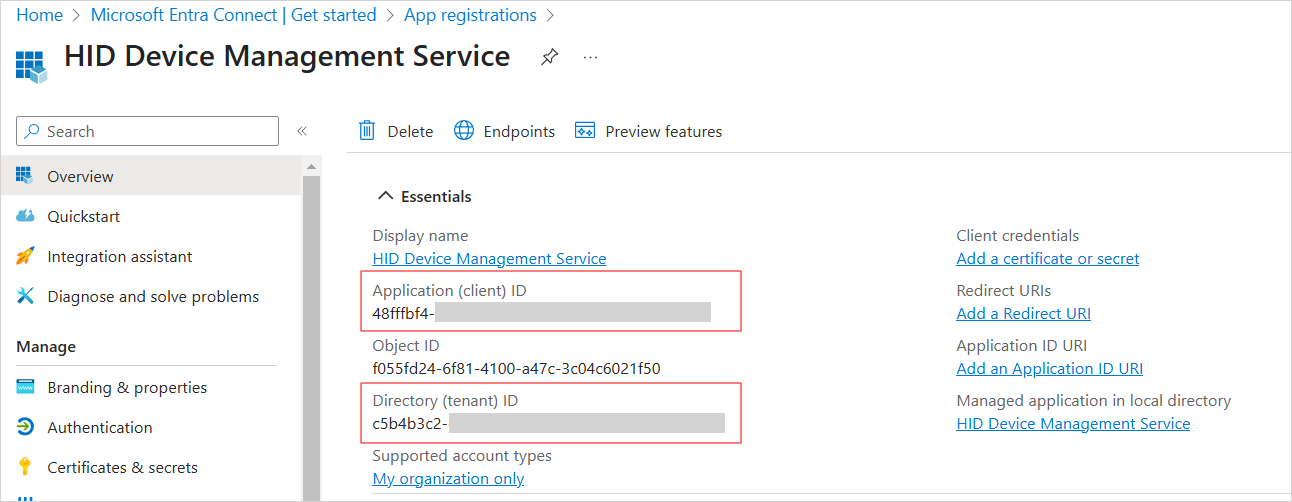
After the initial registration is complete, make a note of the Application (client) ID and the Directory (tenant) ID.
Note: These IDs are required when configuring the connection to Entra ID in Customer Central. -
In the overview page for your application, click the link under Client credentials.
Alternatively, under Manage, select Certificates & secrets.
-
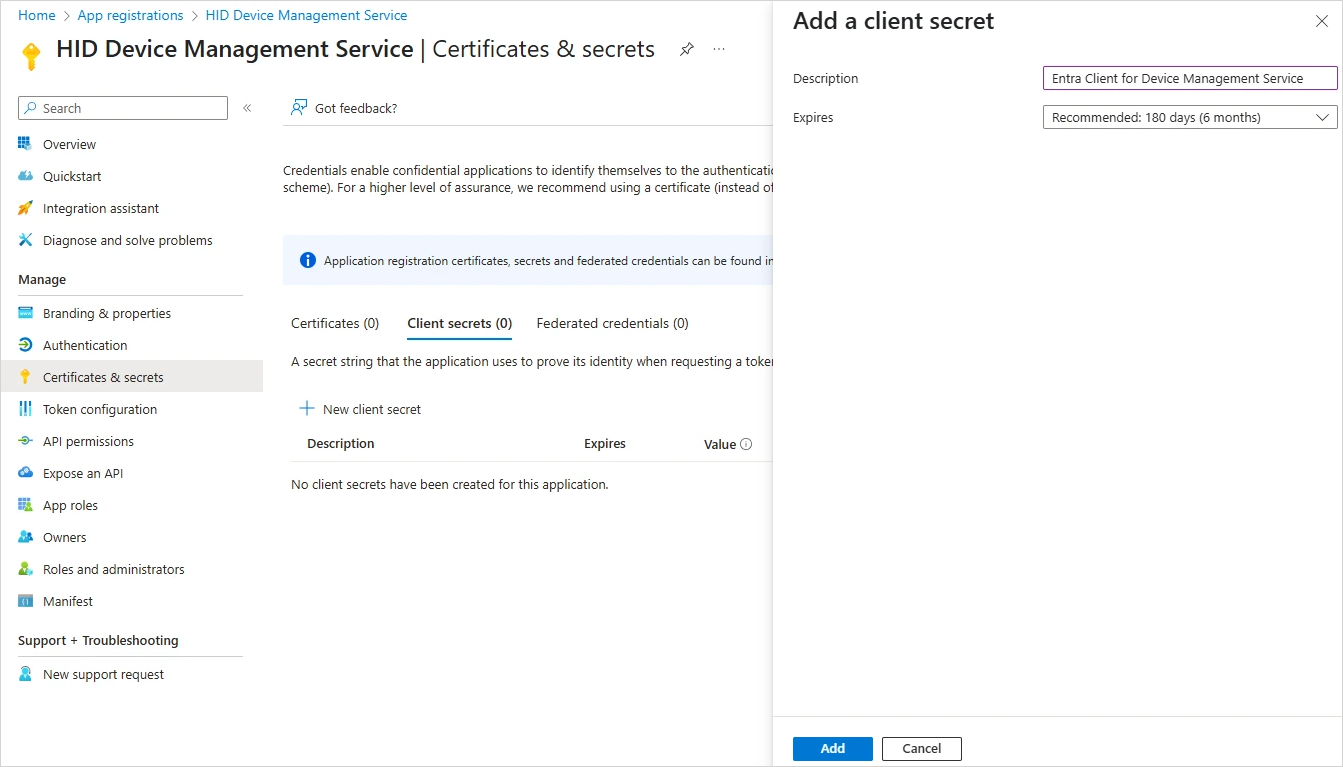
Click New client secret.
-
Add a client secret credential for your application with an identifiable Description and Expires after 180 days as recommended.
-
Click Add.
-
-
Under Manage, click Certificates & secrets.
-
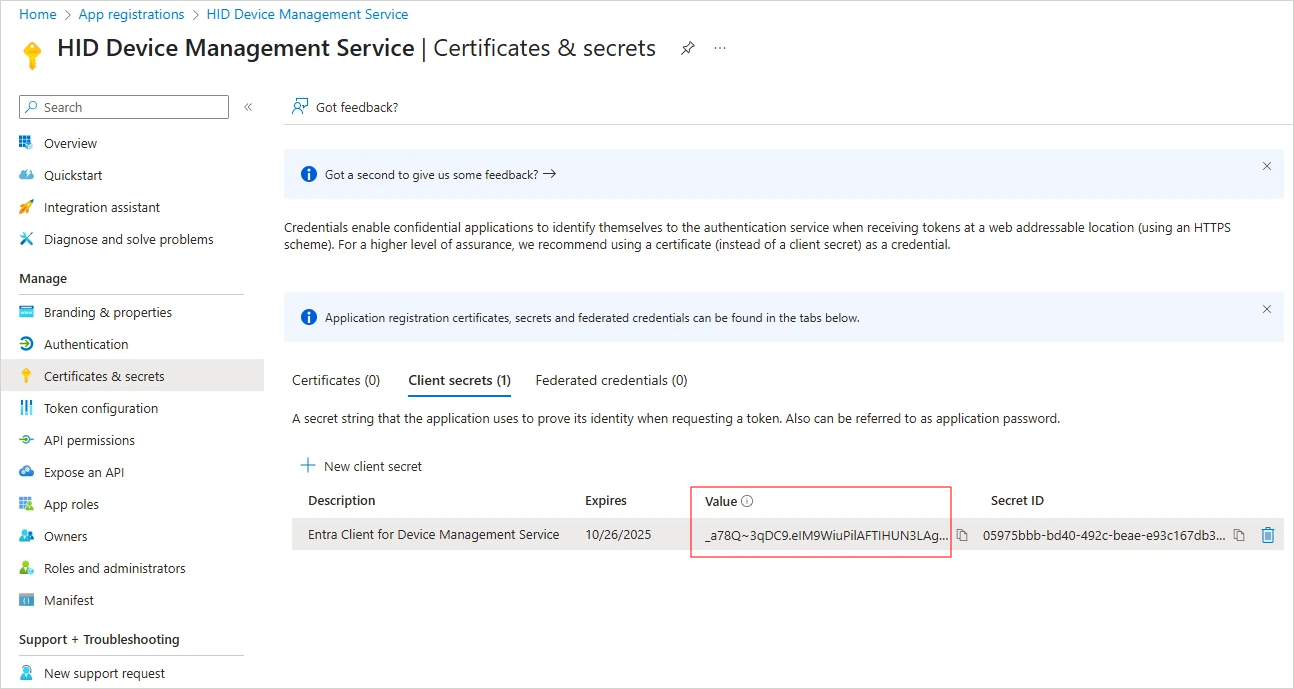
Select the Client secrets tab.
-
Make a note of the Value for the application's secret.
Important: The Value displayed for the client secret credential corresponds to the Secret required when configuring the connection to Entra ID in Customer Central.This Value is only displayed when the secret is generated, so you must make sure to keep a copy of it.
-
-
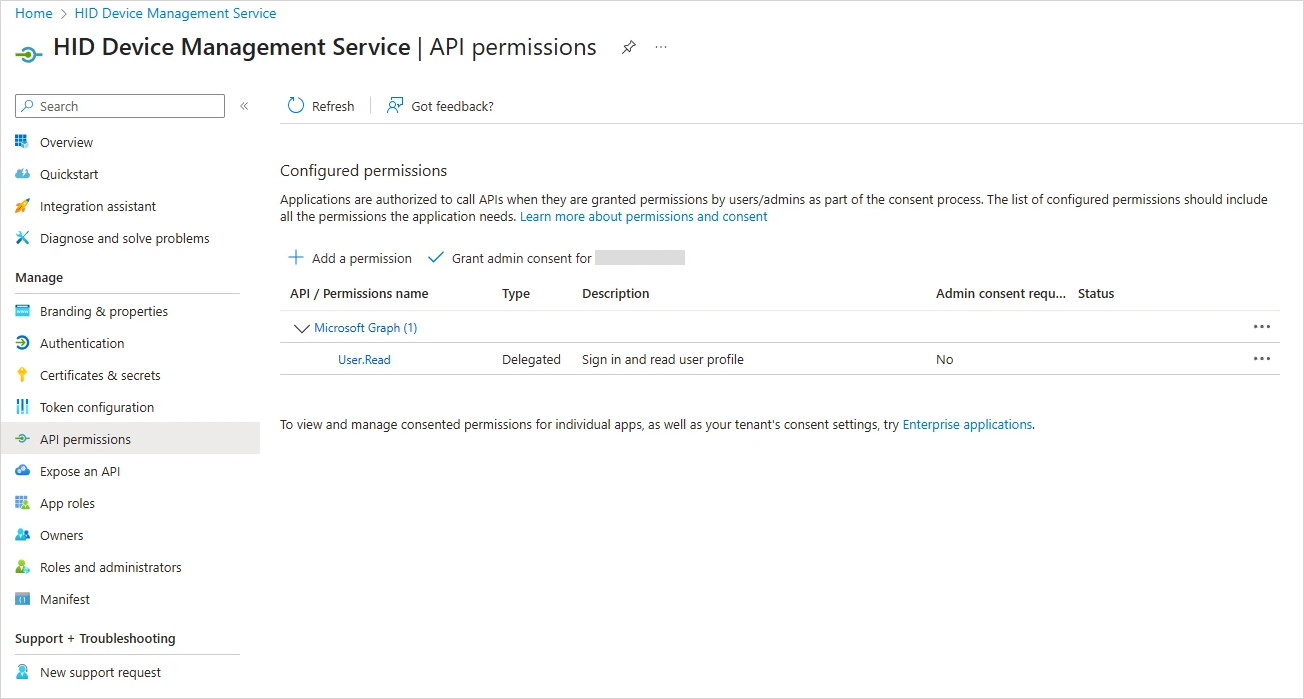
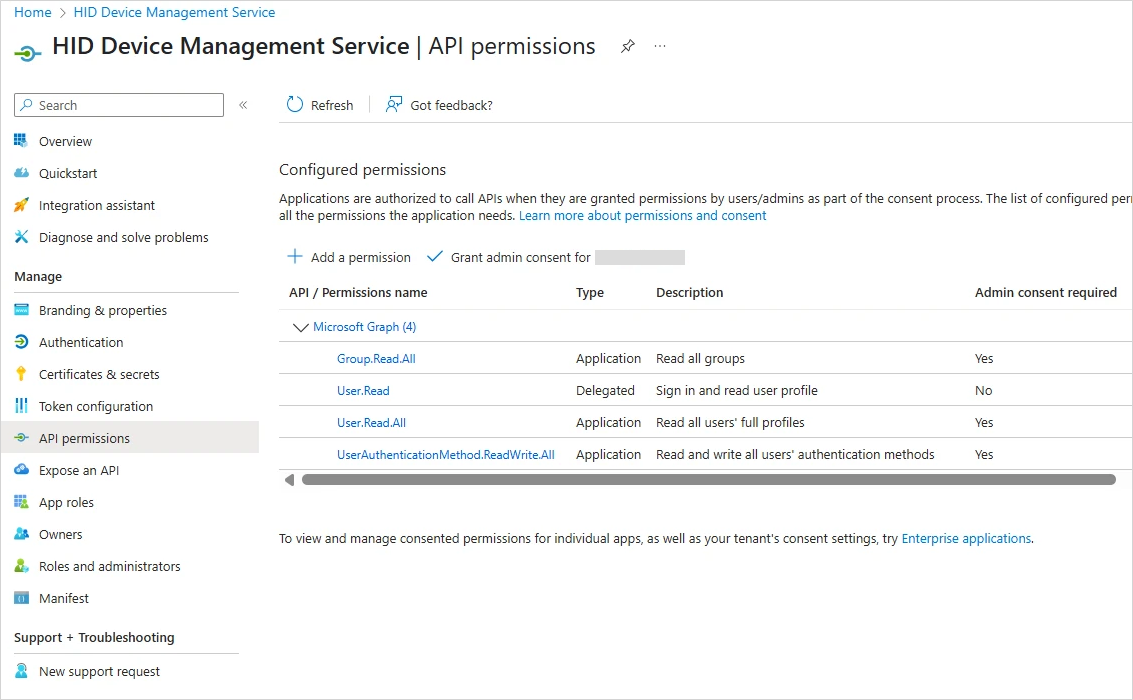
Under Manage, select API Permissions.
Note: Leave the delegated User.Read permission as is.-
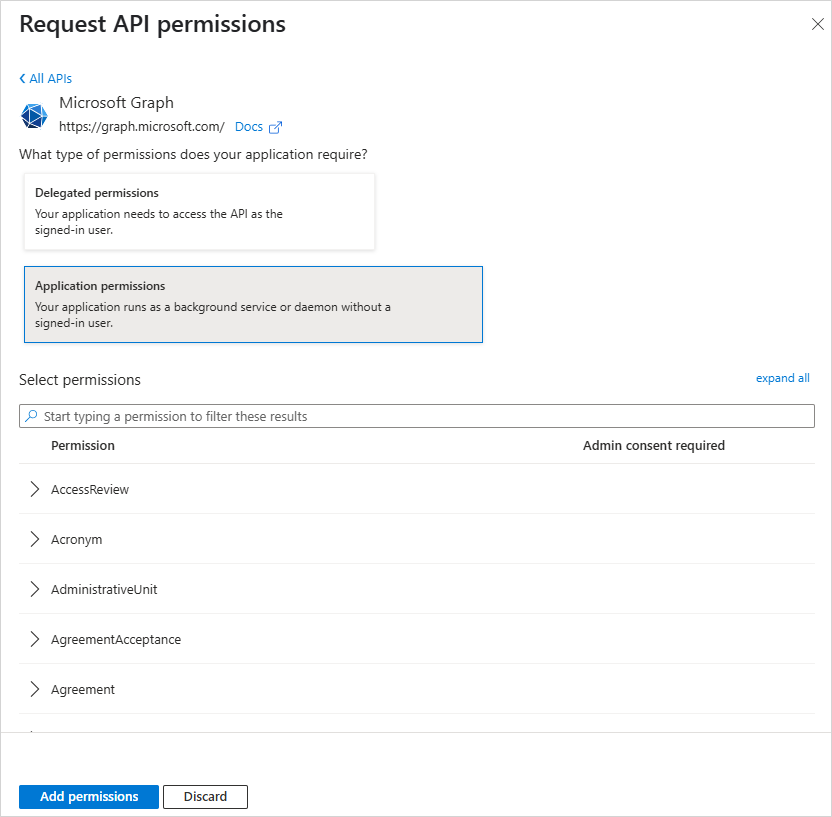
Click Add a permission.
-
Select Microsoft Graph.
-
Select Application Permissions.
-
Add the following permissions:
-
Group.Read.All
-
User.Read.All
-
UserAuthenticationMethod.ReadWrite.All
-
When complete, the Configured permissions should be as follows:
-
-
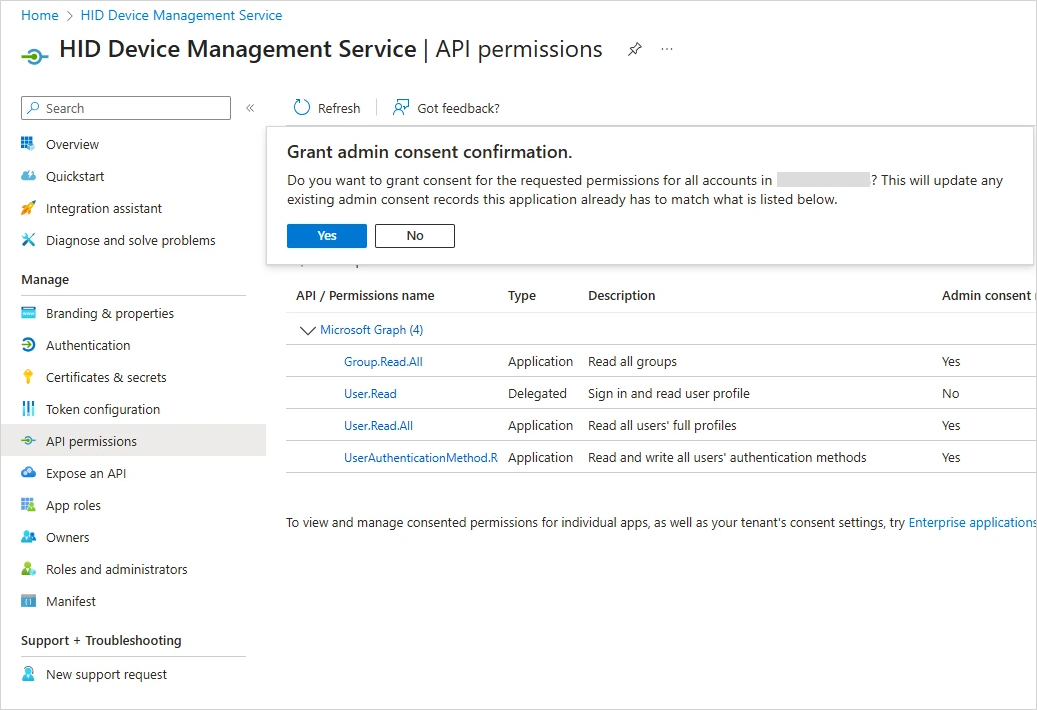
Once these permissions are set, click Grant admin consent for <your directory> and then Yes.
-
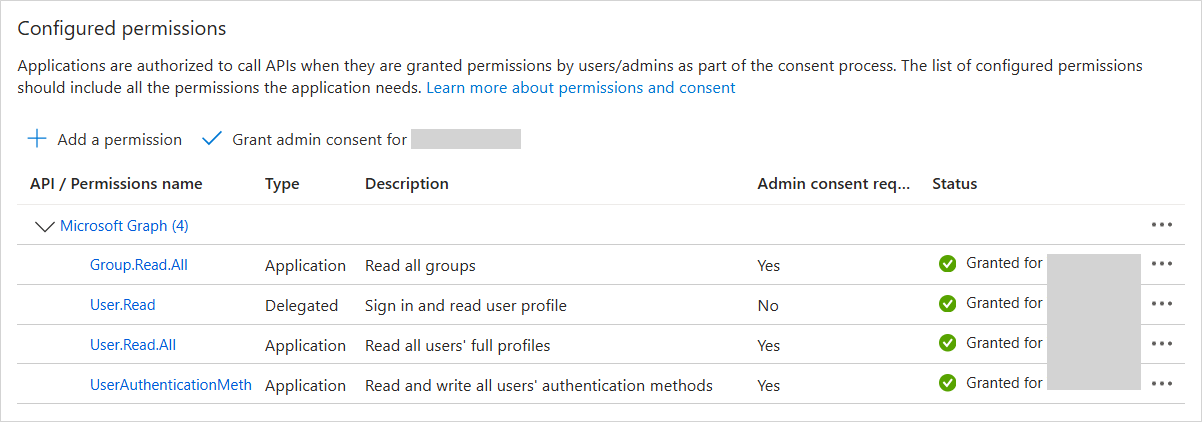
Make sure the status for the permissions is "Granted for <your directory>" with a green checkmark next to each.
Enable FIDO Provisioning
Before users in your organization can register and sign in to their Microsoft Entra account using (FIDO2) passkeys, you must enable the provisioning of the passkeys.
For details on this procedure, refer to Enable passkeys (FIDO2) for your organization | Microsoft Learn.
-
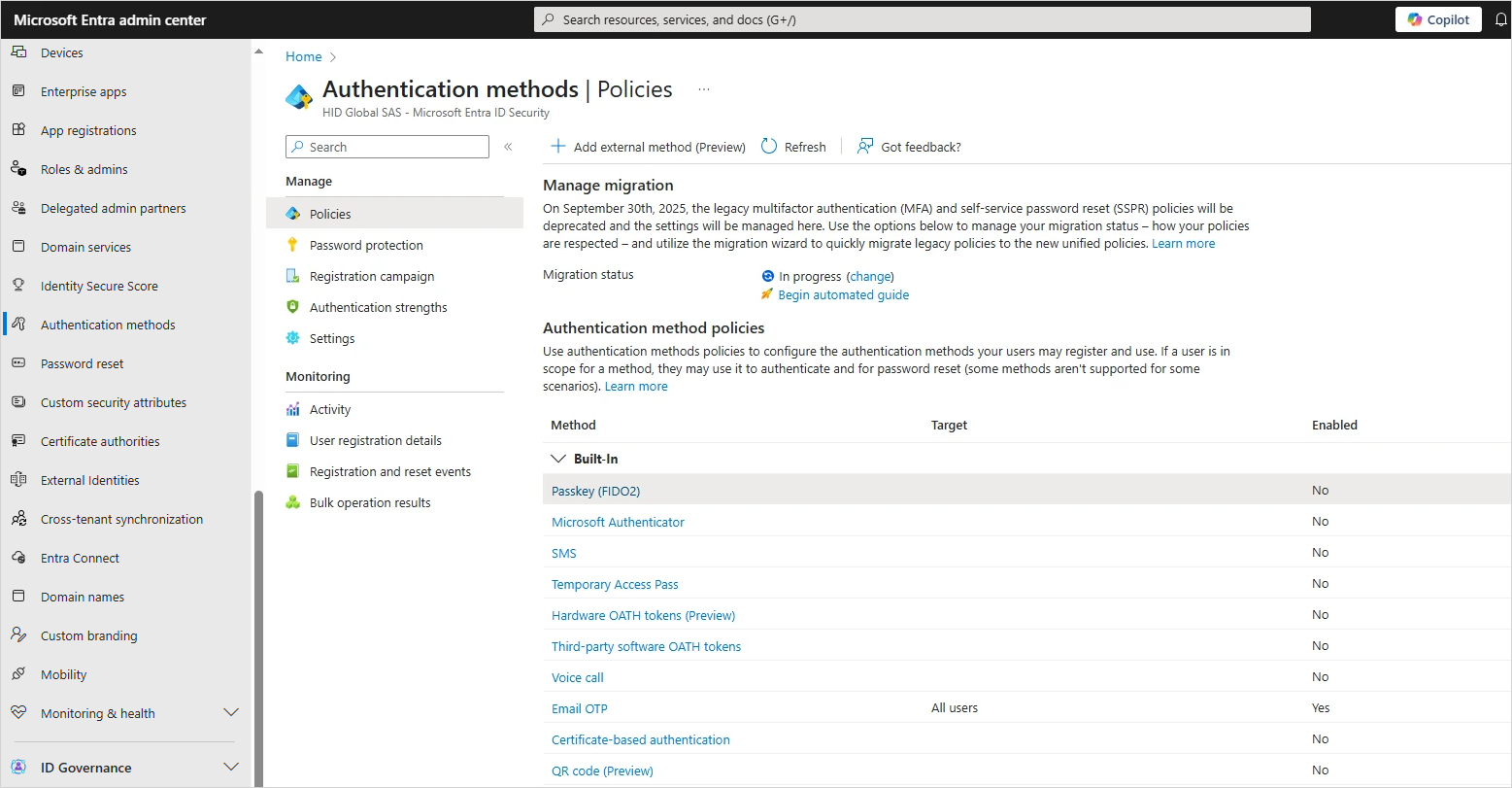
Return to the Microsoft Entra admin center home page and select Authentication Methods in the left menu.
-
Under Manage, select Policies.
-
In the Authentication method policies section, select the Passkey (FIDO2) built-in authentication method.
-
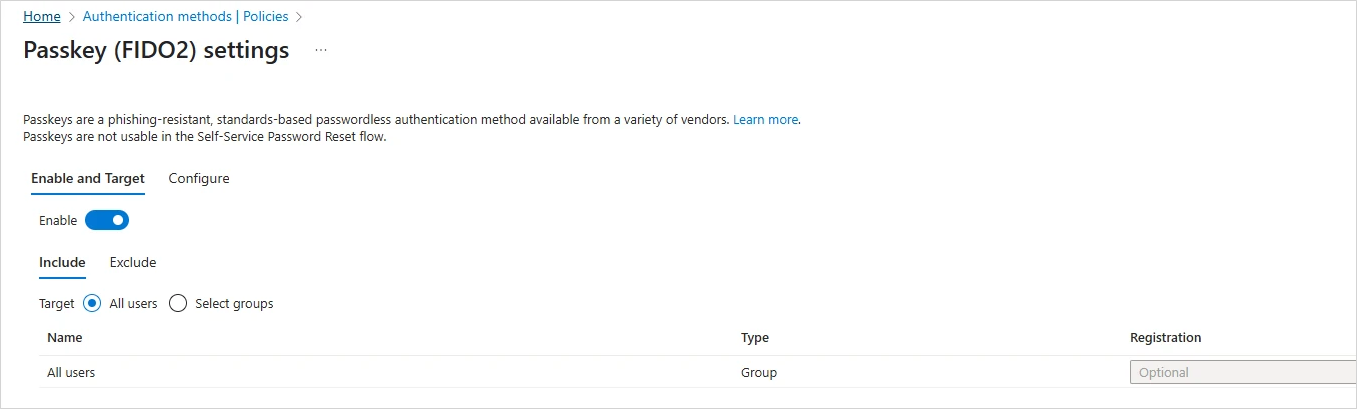
In the Enable and Target tab, toggle the policy to Enable.
-
In the Include tab, select All users or Select groups to define the users allowed to authenticate with this method.
-
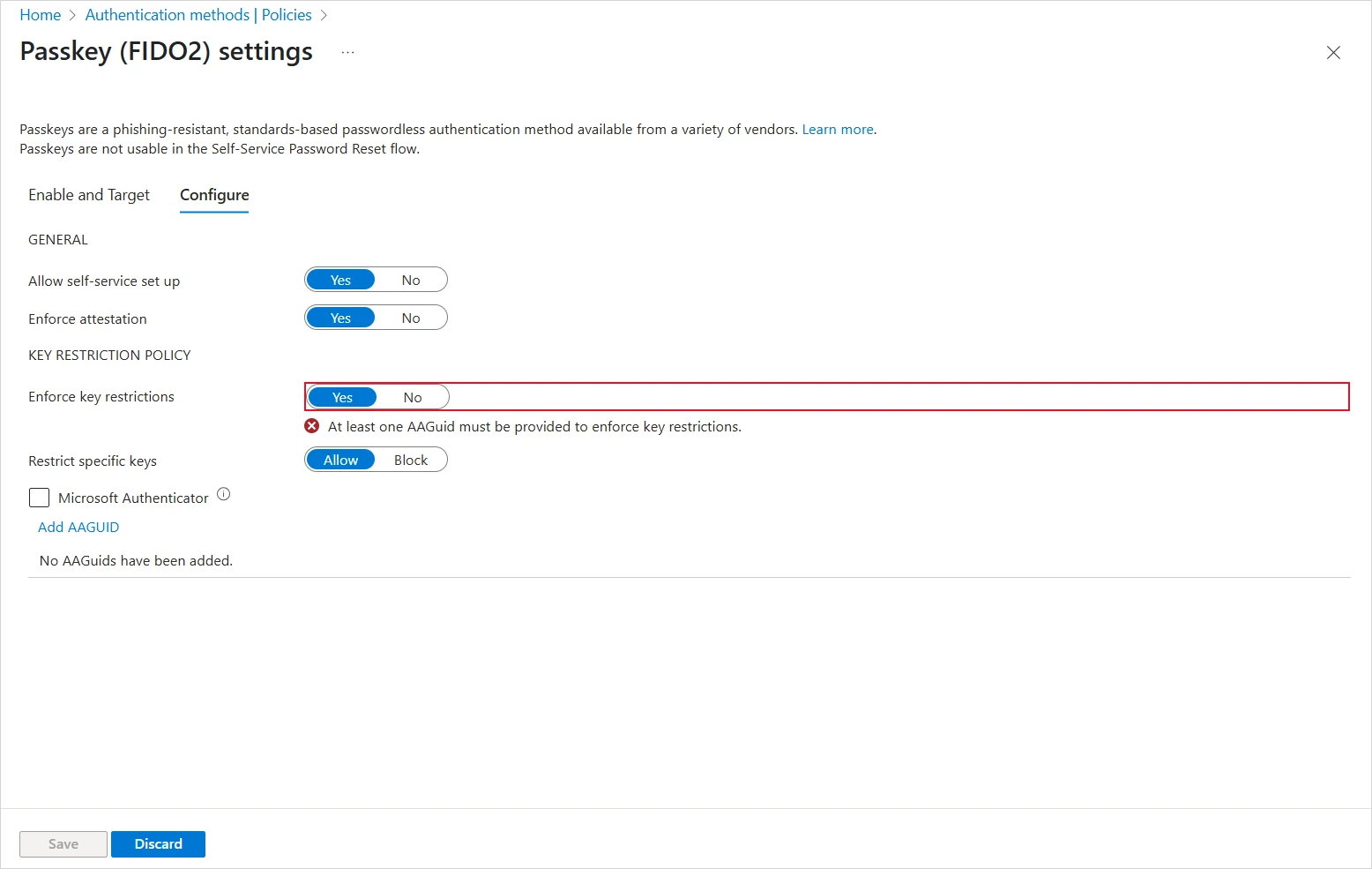
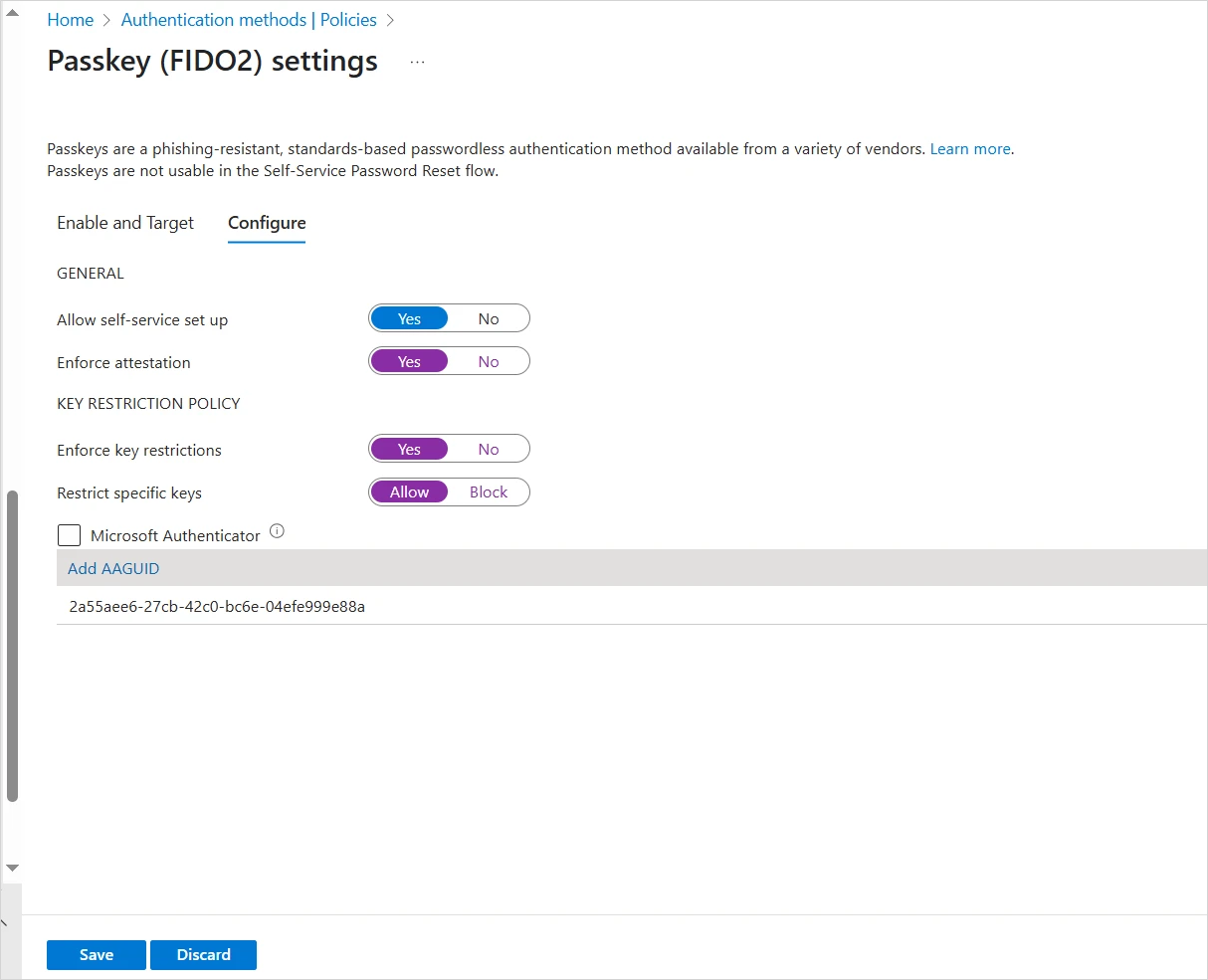
Select the Configure tab and set the following parameters:
Section Setting Description GENERAL Allow self-service set up Set to Yes Enforce attestation Set to Yes if your organization wants to ensure that a FIDO2 security key model or passkey provider is genuine KEY RESTRICTION POLICY Enforce key restrictions Set to Yes only if your organization wants to only allow or disallow certain security key models or passkey providers (identified by their AAGUID) Restrict specific key Set to Allow only if your organization wants to only allow or disallow certain security key models or passkey providers (identified by their AAGUID) Important: If you change key restrictions and remove a previously allowed AAGUID, users who have registered an allowed device will no longer be able use it to sign in. -
Click Add AAGUID and add the AAGUID of your devices (for example, 2a55aee6-27cb-42c0-bc6e-04efe999e88a for the HID Crescendo 4000 device).
For the complete list of identifiers for the HID Crescendo FIDO devices, see AAGUID for Crescendo Devices.
-
Click Save.
Assign Users or Groups
Once you have completed the application and passkey configuration, you can now define the user population accessible for Passkey Management in Customer Central.
For details on this procedure, refer to Manage users and groups assignment to an application | Microsoft Learn.
-
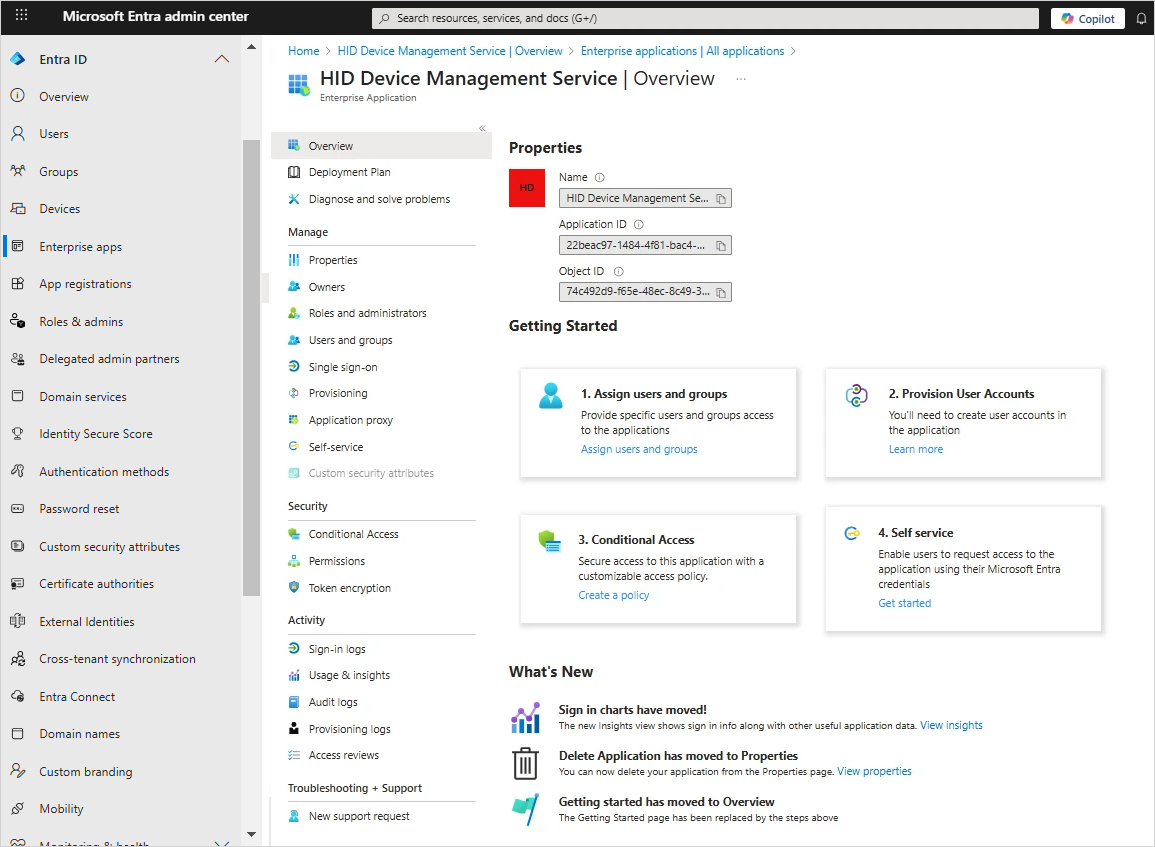
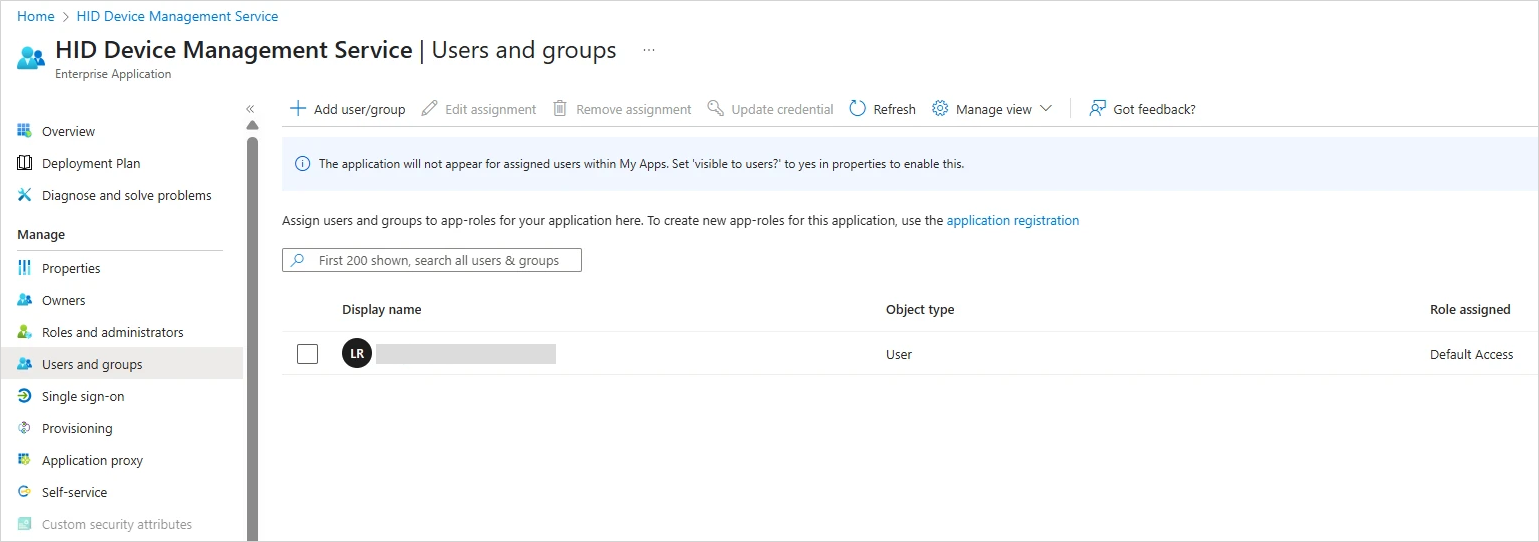
Return to the Microsoft Entra admin center home page, expand Entra ID in the left menu and select Enterprise apps and then your application.
-
In the overview page, under Getting Started, click Assign users and groups.
Alternatively, under Manage, select Users and groups.
-
Click Add user/group.
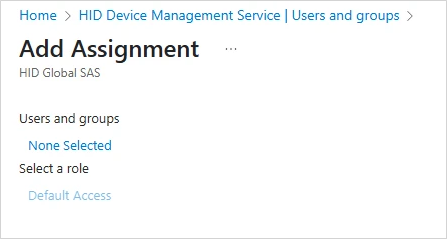
-
Click None Selected.
-
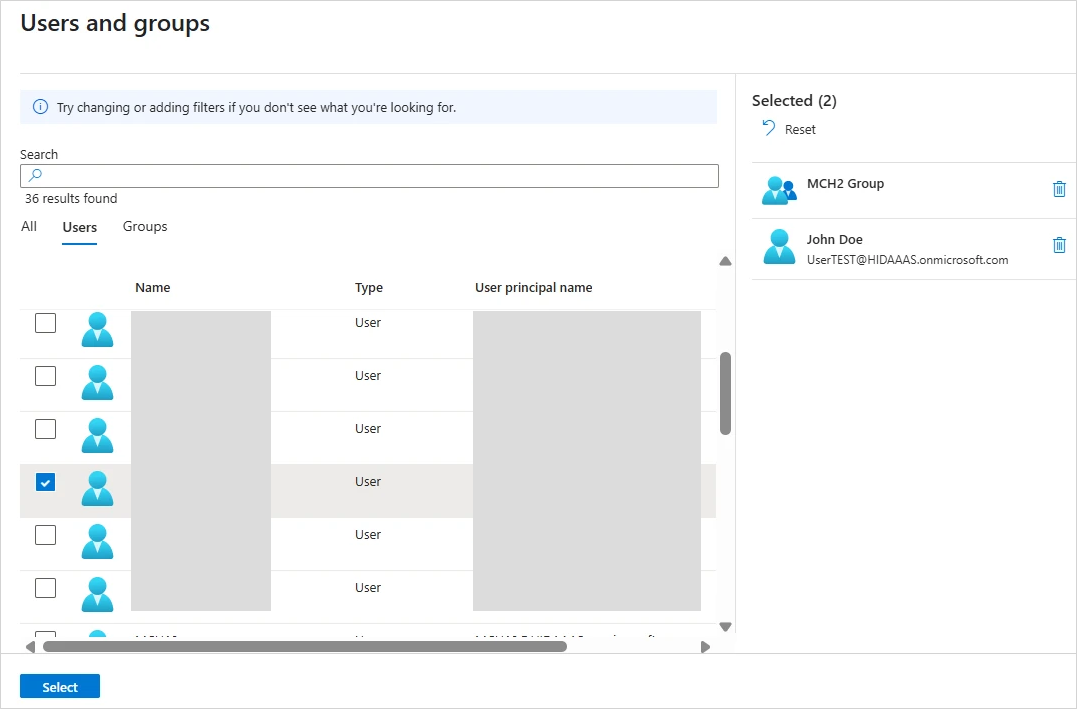
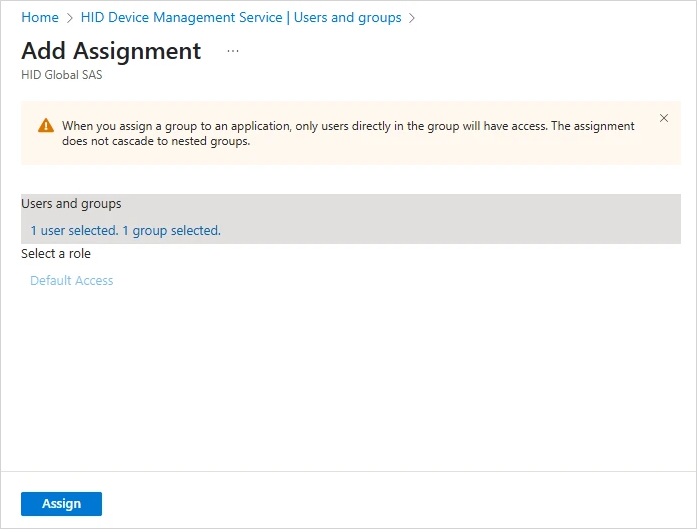
Select the required users or groups you want to assign to the Passkey Management application and click Select.
-
When complete, click Assign.
Configure the Connection to Microsoft Entra ID
Before you can provision and enroll FIDO devices for your users, you must configure the connection between your Microsoft Entra ID application and Customer Central.
A valid license for the FIDO Provisioning service
To purchase new licenses or renew existing ones, contact your HID Account Manager.
The Administrator or Device Service Administrator role, or at least the Create Configuration privilege for Entra ID
Created the application in Microsoft Entra ID and enabled passkey authentication for the service
Assigned the users or groups to the service
The following information that was obtained when you created the application in Microsoft Entra ID:
The Directory (tenant) ID - the unique identifier that represents your organization's Microsoft Entra ID instance
This ID is used to identify which directory your Passkey Management application should communicate with and authenticate against.
The Application (client) ID - the unique identifier that Microsoft Entra ID assigned to your Passkey Management application when you registered it
This ID is used to identify your application when it authenticates with Microsoft Entra ID.
Secret - the Value of the client secret credential used by your Passkey Management application to identify itself when requesting a token
Note: This Value is only displayed when the secret is generated and cannot be displayed again.If you do not know the secret's value, you must generate a new secret.
-
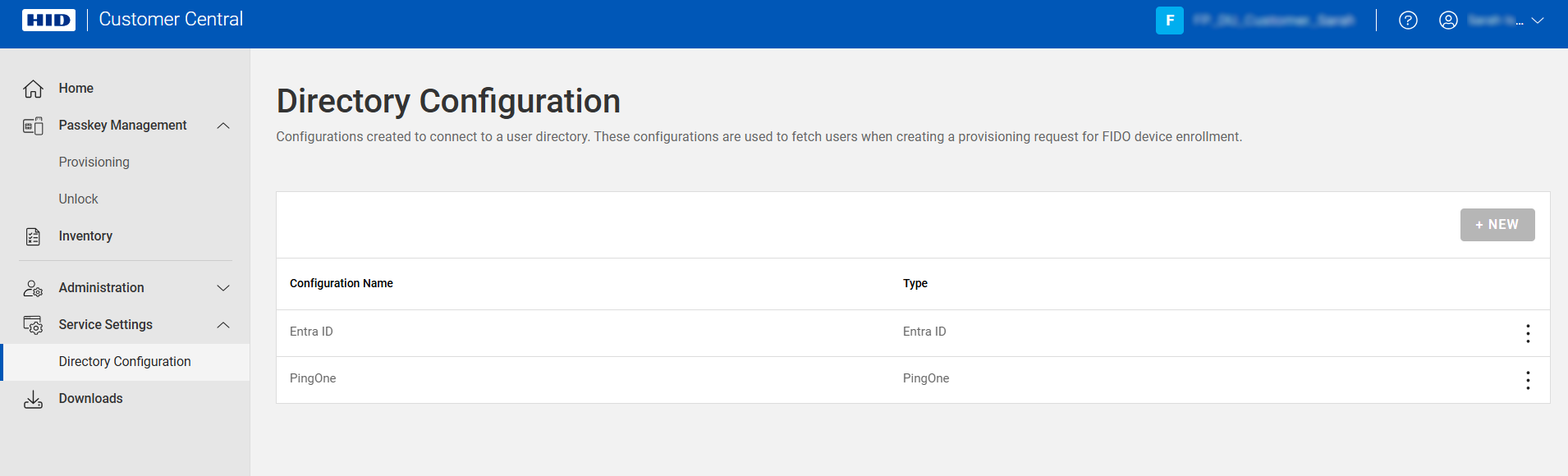
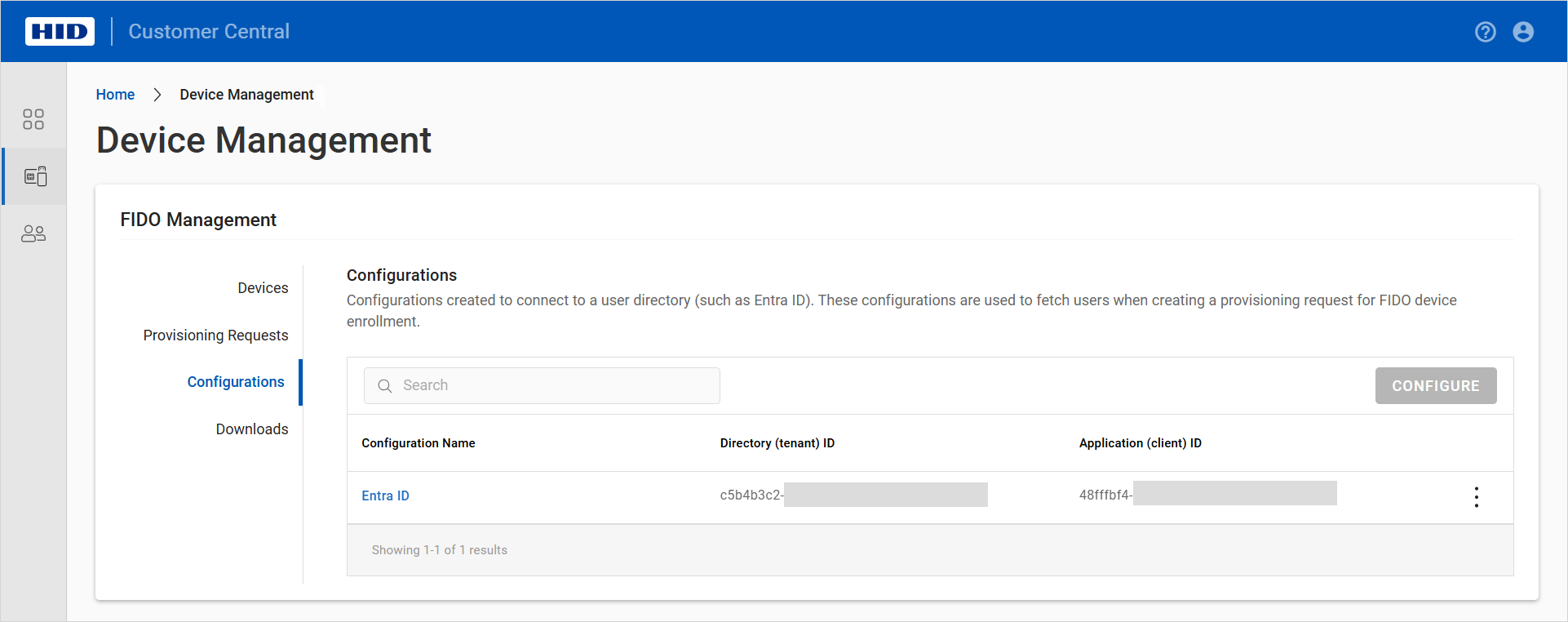
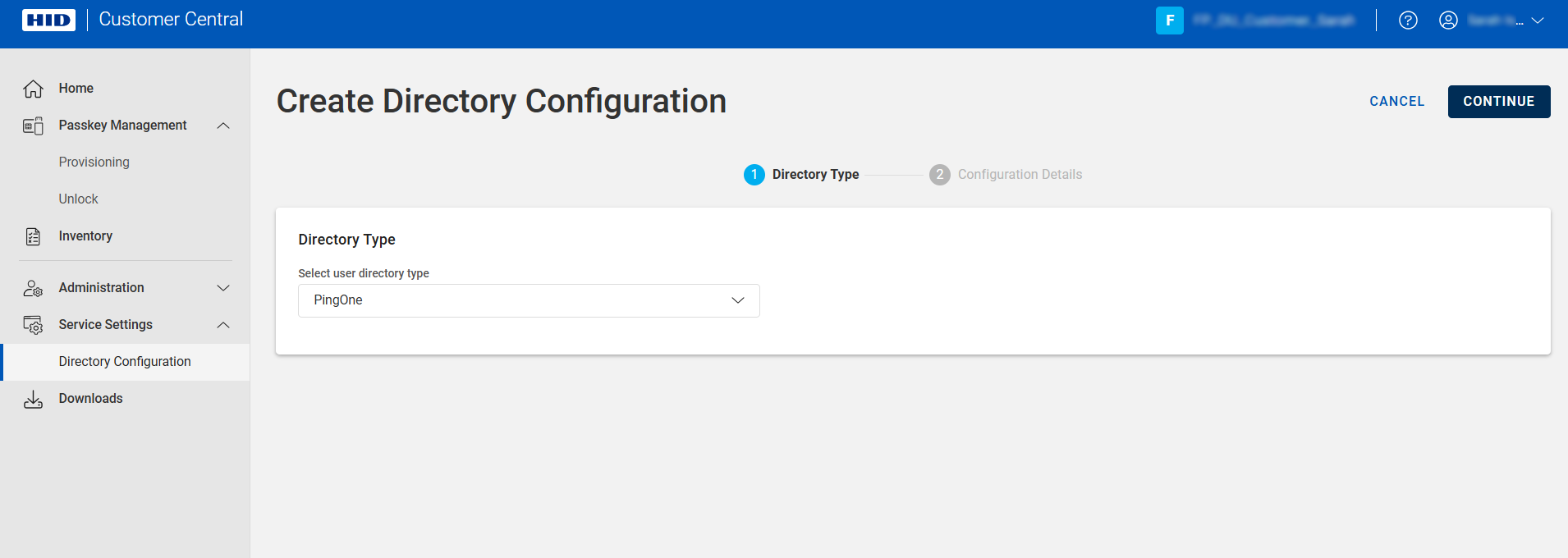
Expand Service Settings
 in the left menu and select Directory Configuration.
in the left menu and select Directory Configuration. -
Click NEW.
-
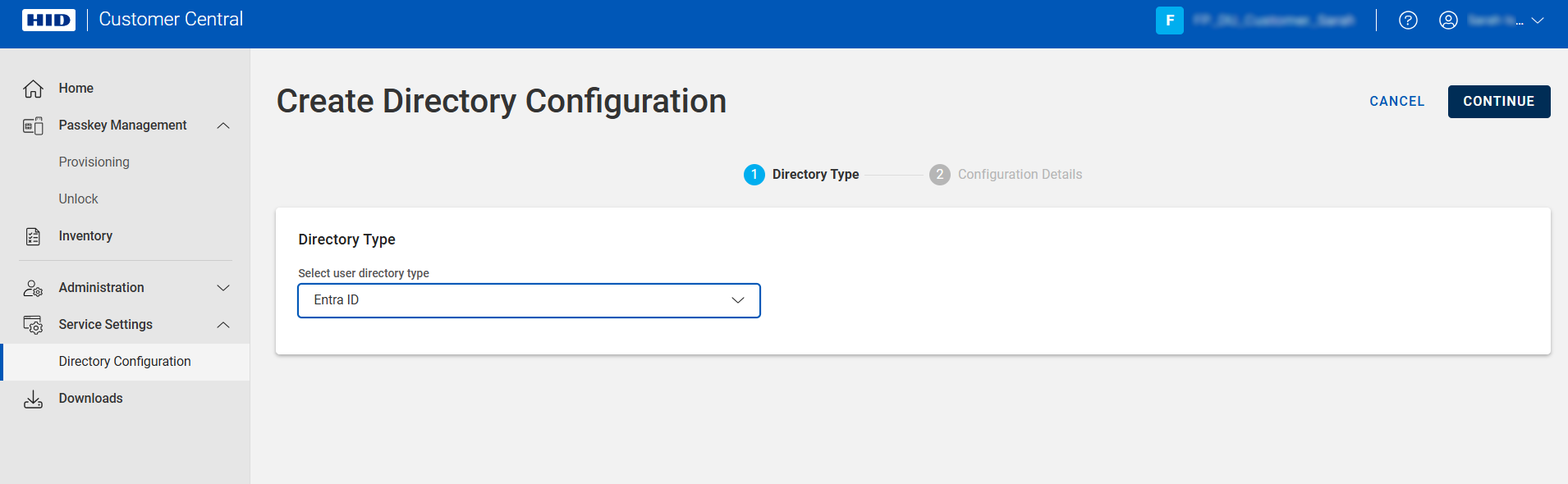
Select the directory type and click CONTINUE.
-
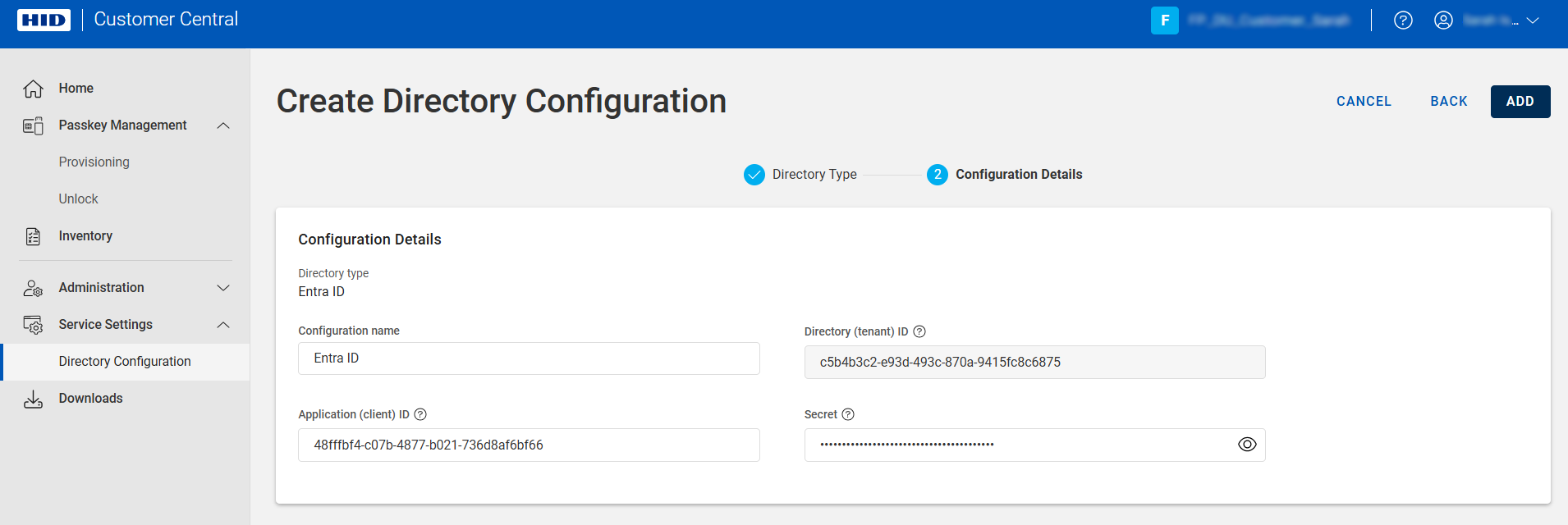
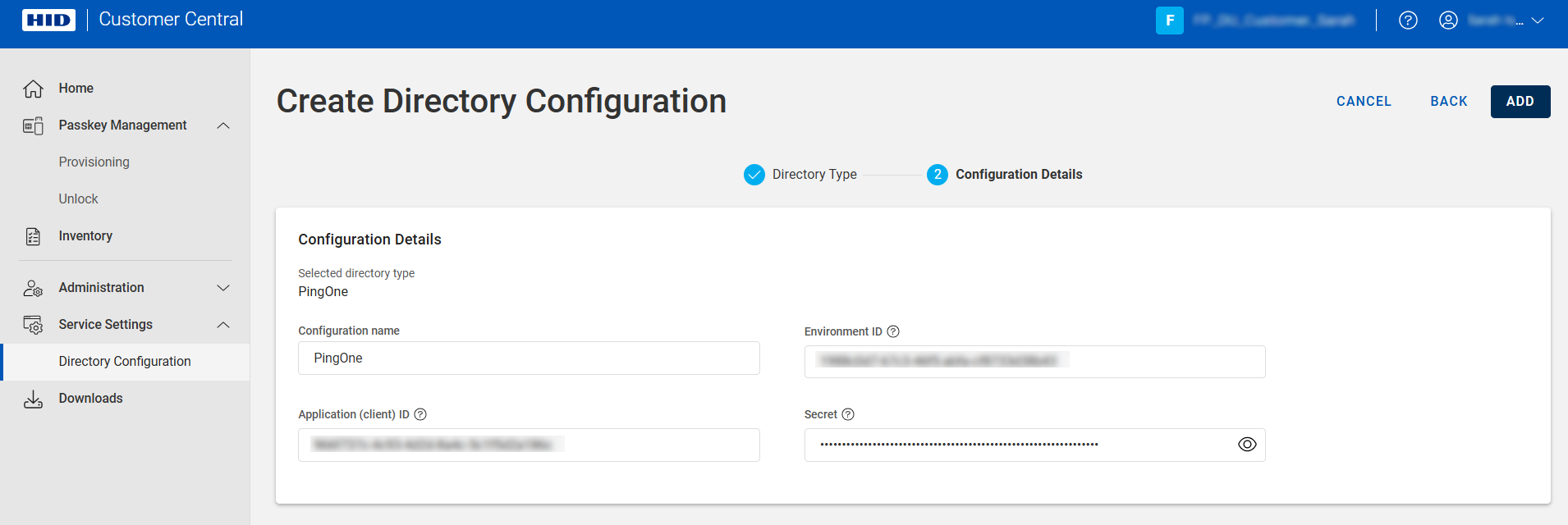
Enter a Configuration name for the configuration.
-
Enter the following information obtained in Register Customer Central as an Application in Microsoft Entra ID:
-
Directory (tenant) ID - the unique identifier that represents your organization's Microsoft Entra ID instance
-
Application (client) ID - the unique identifier that Microsoft Entra ID assigned to your Passkey Management application when you registered it
-
Secret - the Value of the client secret credential used by your Passkey Management application to identify itself when requesting a token
-
-
Click ADD.
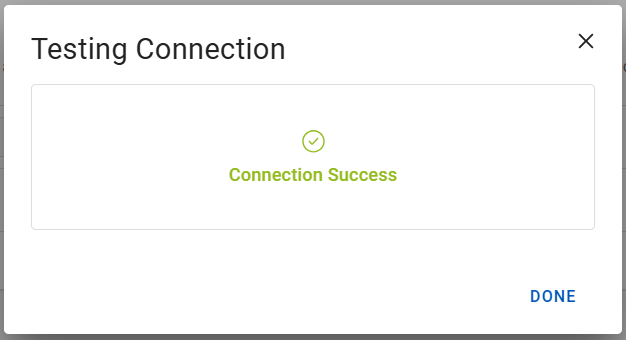
Customer Central verifies that the configuration is correct and displays a success message when complete.
Customer Central is now connected to your Microsoft Entra ID application and your users are available for provisioning.
Integrating with PingOne
A PingOne directory with a valid license for Ping Identity
A PingOne administrator account for your PingOne environment with the required roles to manage applications
The Administrator or Device Service Administrator role, or at least the Create Configuration privilege for PingOne
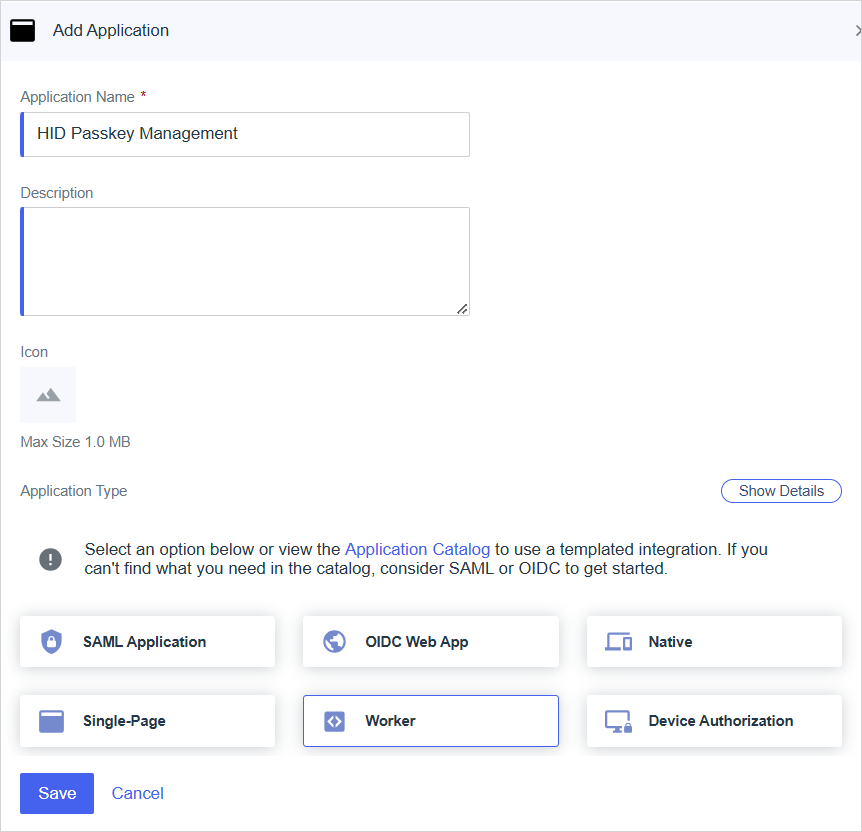
Create an Application
-
Log on to the PingOne admin console as an administrator for your PingOne environment.
-
Expand and select Applications in the left menu and then click + to add an application.
-
Define the application's parameters:
-
Application Name - enter a name for your application
-
Description - enter a brief description for your application (optional)
-
Application Type - select Worker
For further information, go to Applications | PingOne Documentation.
-
-
Click Save.
-
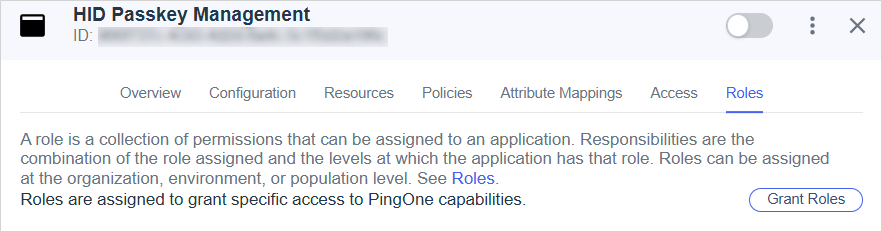
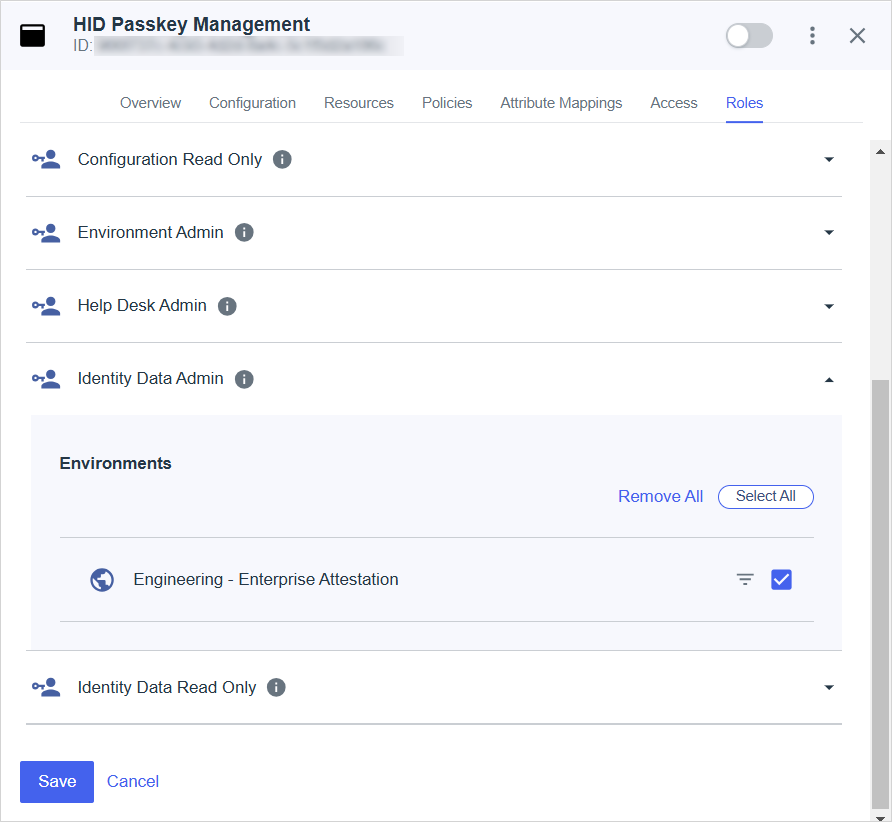
Select Roles in the application's top menu.
-
Click Grant Roles.
-
Add the following roles for your environment:
-
Environment Admin
-
Identify Data Admin
For further information, go to Configuring roles for a worker application | PingOne Documentation.
-
-
Click Save.
-
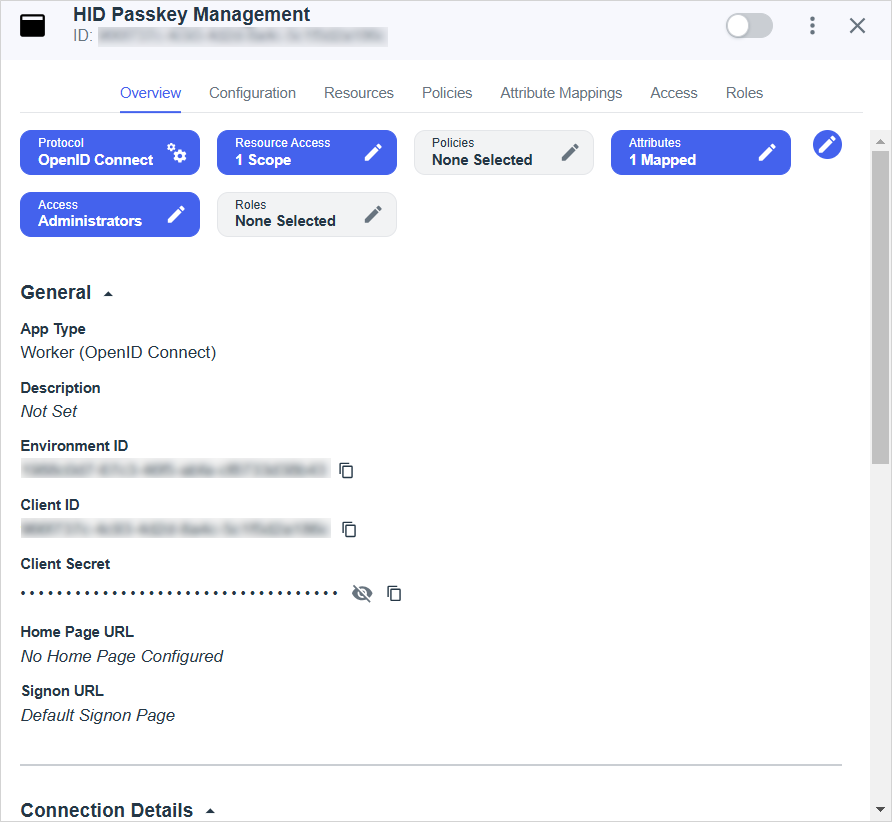
Select Overview in the application's top menu.
-
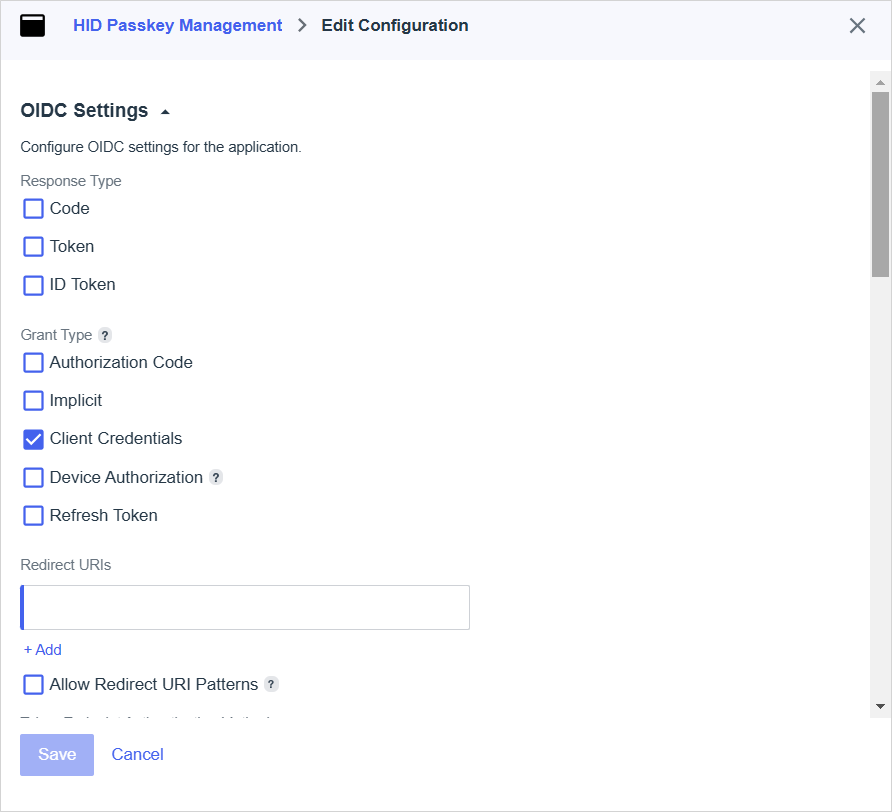
Click Protocol - OpenID Connect.
-
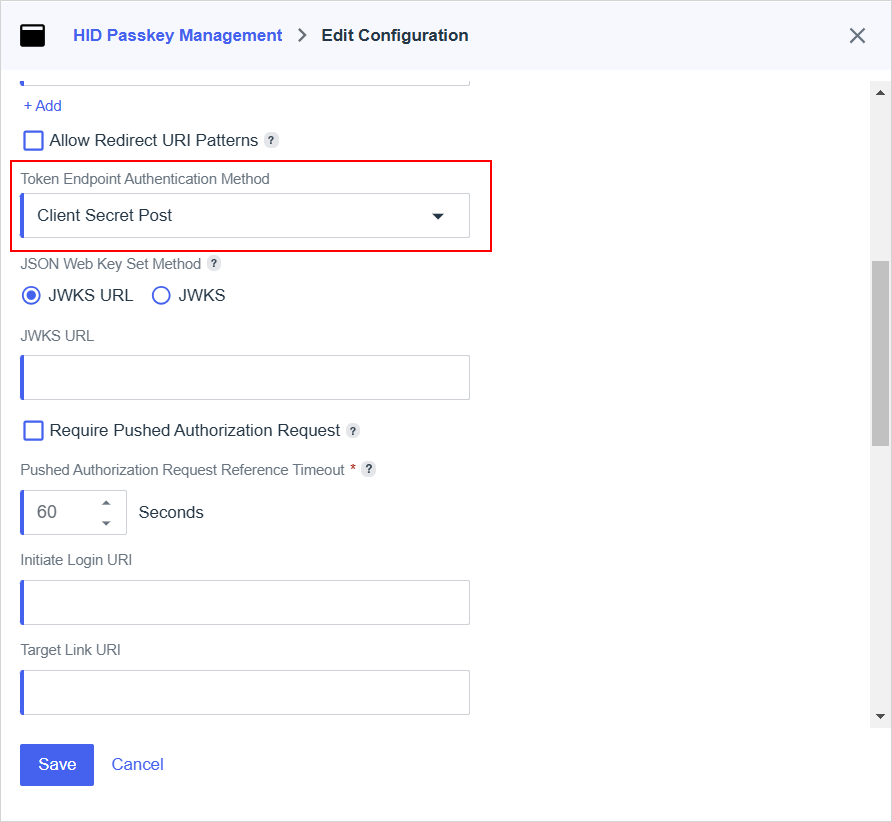
Scroll down to the Token Endpoint Authentication Method section and select Client Secret Post as the method.
For further information, go to Token endpoint authentication methods | PingOne Documentation
-
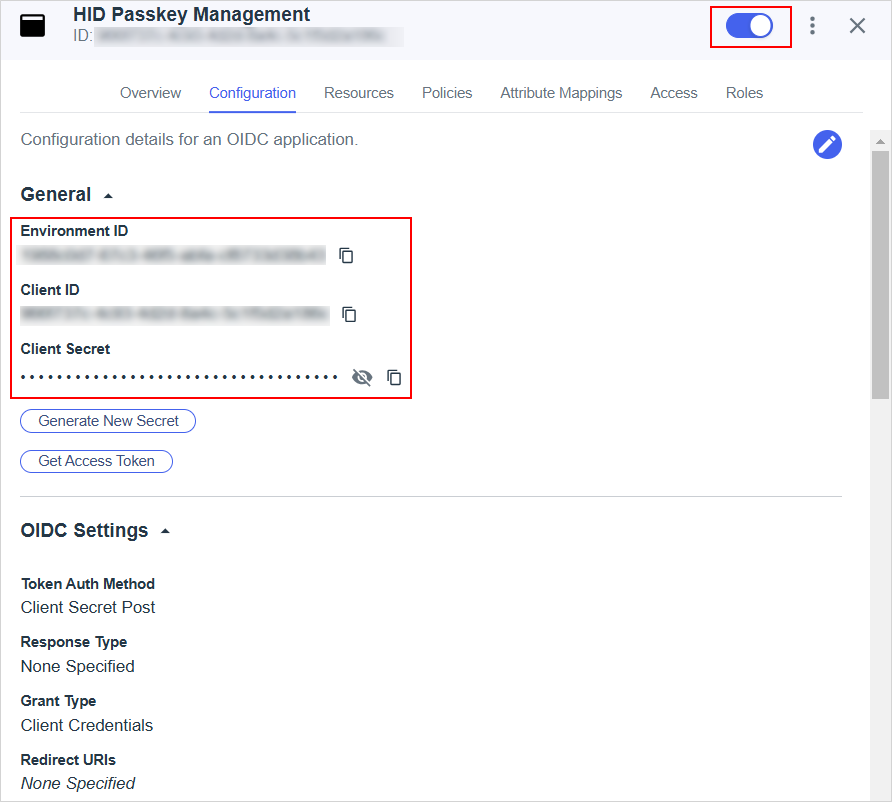
Make a note of the:
-
Environment ID
-
Client ID
-
Client Secret
Note: This information is required when configuring the connection to PingOne in Customer Central. -
-
Enable the application by toggling the button in the application's menu bar.
Define the Authentication Policies
-
Log on to the PingOne admin console as an administrator for your PingOne environment.
-
Expand Authentication in the left menu to display the Policies menu.
-
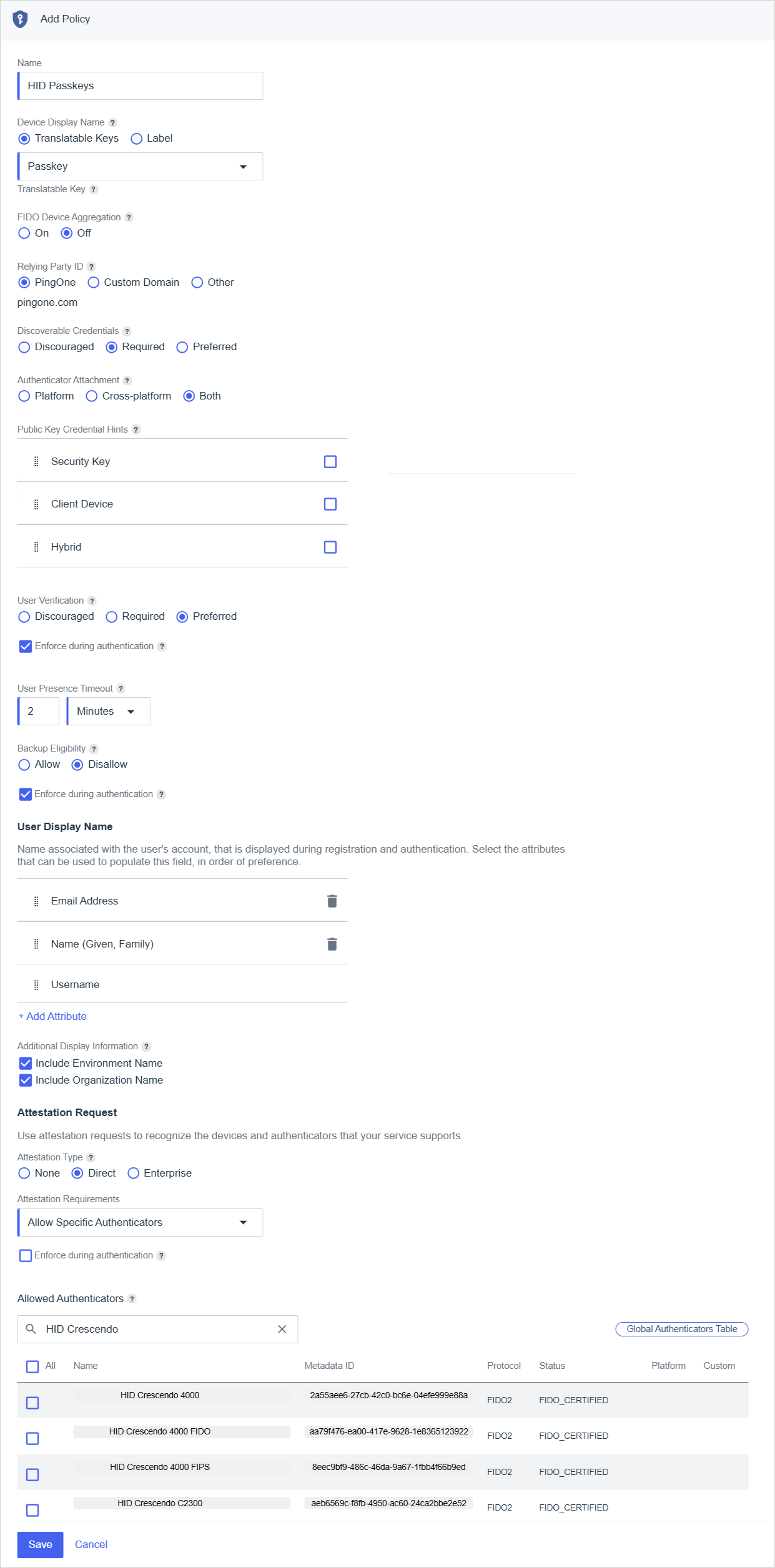
Select FIDO and either select an existing policy or create a new one with the following configuration:
Parameter Value Relying Party ID PingOne Discoverable Credentials Required Authenticator Attachment Both User Verification
-
Preferred
-
Enforce during authentication
Backup Eligibility
-
Disallow
-
Enforce during authentication
User Display Name
-
Attributes:
-
Email Address
-
Name (Given, Family)
-
Username
-
-
Additional Display Information:
-
Include Environment Name
-
Include Organization Name
-
Attestation Request
-
Attestation Type - Direct
-
Attestation Requirements - Allow Specific Authenticators
For further information, go to FIDO policies | PingOne Documentation.
-
-
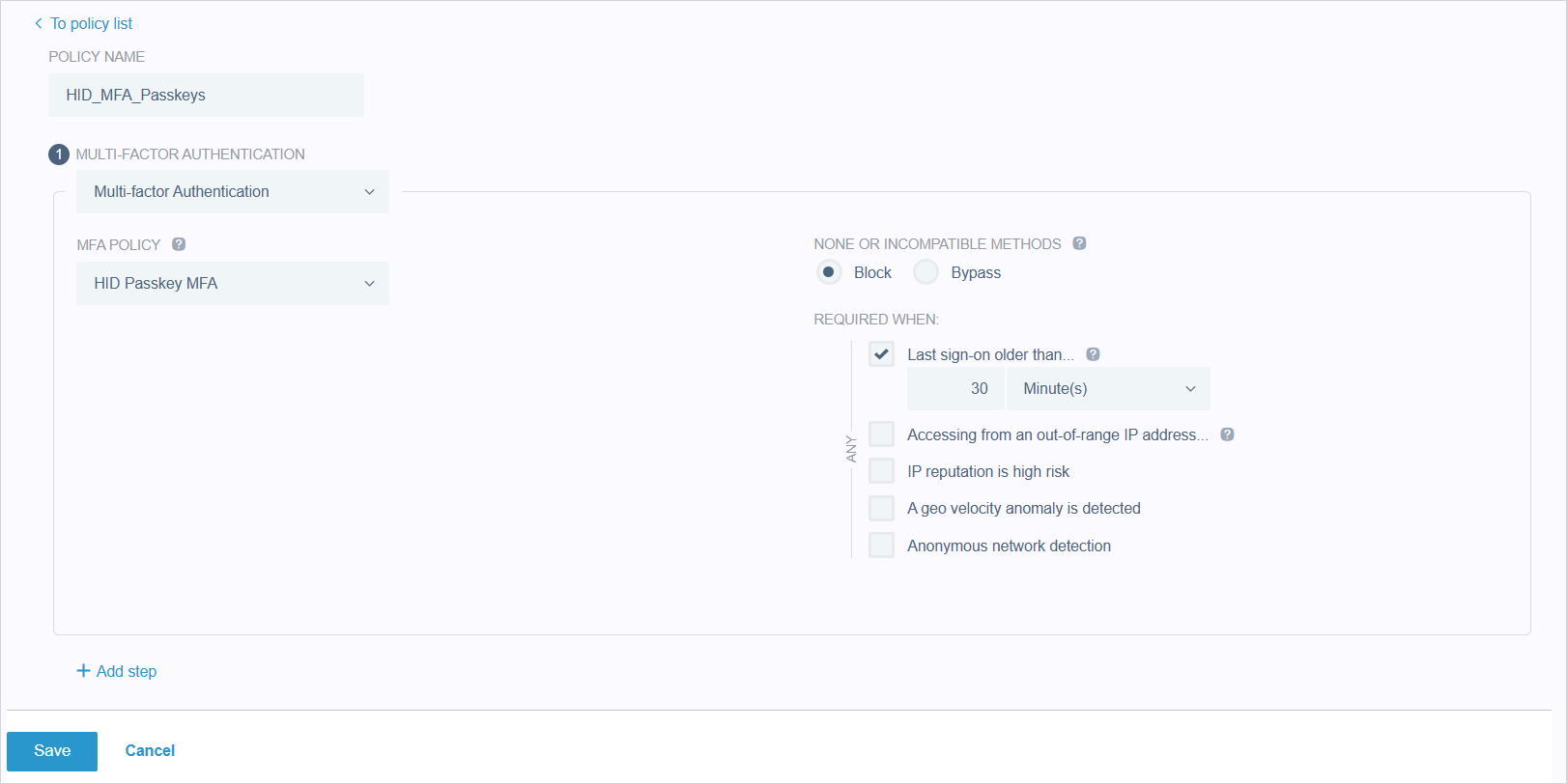
Select MFA and either select an existing policy or create a new one with the following configuration:
Parameter Value Allowed Authentication Methods FIDO2 FIDO Policy The FIDO policy created above Allow Pairing Enabled For further information, go to MFA policies | PingOne Documentation.
-
Select Authentication and either select an existing policy or create a new one with the following configuration:
Parameter Value STEP TYPE Multi-factor Authentication MFA Policy The MFA policy created above For further information, go to Adding a multi-factor authentication or PingID step | PingOne Documentation.
-
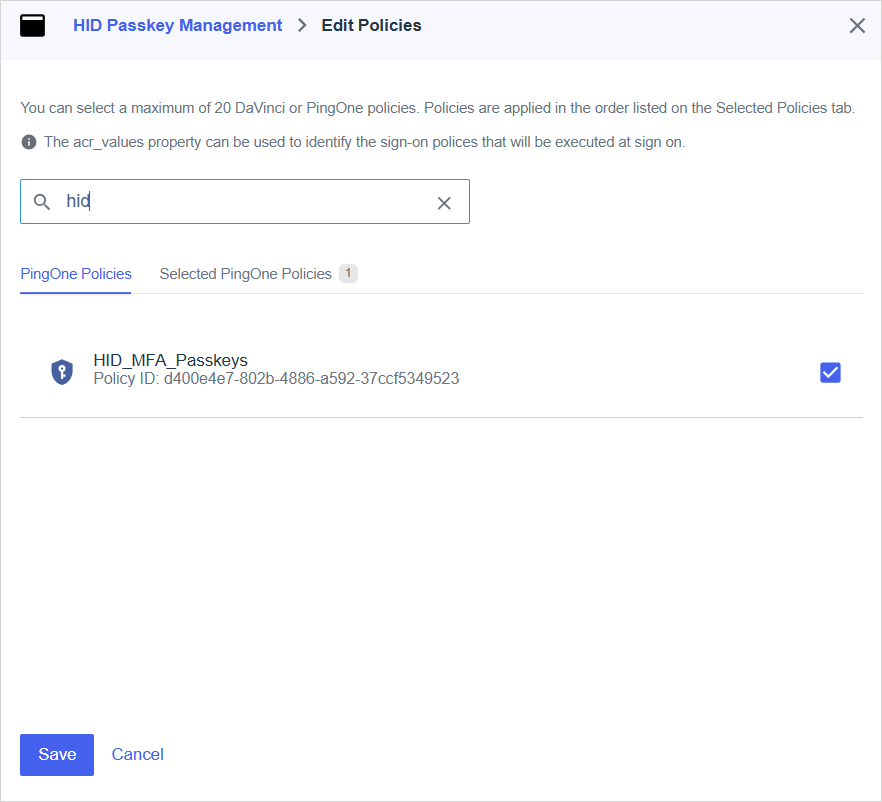
Enable the authentication policy for the application:
Configure the Connection to PingOne
Before you can provision and enroll FIDO devices for your users, you must configure the connection between your PingOne application and Customer Central.
A valid license for the FIDO Provisioning service
To purchase new licenses or renew existing ones, contact your HID Account Manager.
The Administrator or Device Service Administrator role, or at least the Create Configuration privilege for PingOne
Created the application in PingOne and enabled passkey authentication for the service
Assigned the users or groups to the service
The following information that was obtained when you created the application in PingOne:
The Environment ID - the unique identifier that represents your organization's PingOne instance
This ID is used to identify which directory your Passkey Management application should communicate with and authenticate against.
The Client ID - the unique identifier that PingOne assigned to your Passkey Management application when you registered it
This ID is used to identify your application when it authenticates with PingOne.
Secret - the client secret credential used by your Passkey Management application to identify itself when requesting a token
-
Expand Service Settings
 in the left menu and select Directory Configuration.
in the left menu and select Directory Configuration. -
Click NEW.
-
Select the directory type and click CONTINUE.
-
Enter a Configuration name for the configuration.
-
Enter the following information obtained in Create an Application:
-
Environment ID - the unique identifier that represents your organization's PingOne instance
-
Application (client) ID - the unique identifier that PingOne assigned to your Passkey Management application when you registered it
-
Secret - the client secret credential used by your Passkey Management application to identify itself when requesting a token
-
-
Click ADD.
Customer Central verifies that the configuration is correct and displays a success message when complete.
Customer Central is now connected to your PingOne application and your users are available for provisioning.
Test a Connection
-
Expand Service Settings
 in the left menu and select Directory Configuration.
in the left menu and select Directory Configuration. -
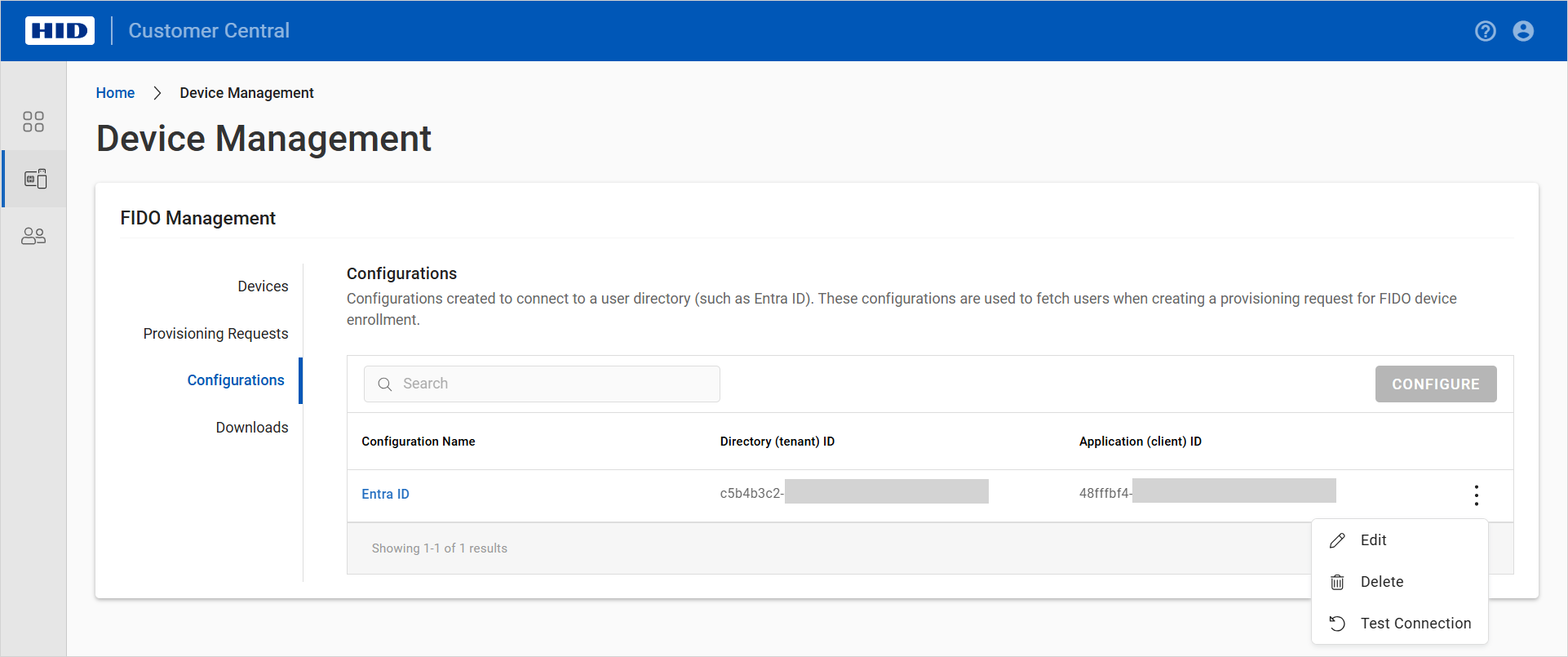
Click the menu icon
 for the configuration and select Test Connection.
for the configuration and select Test Connection.-
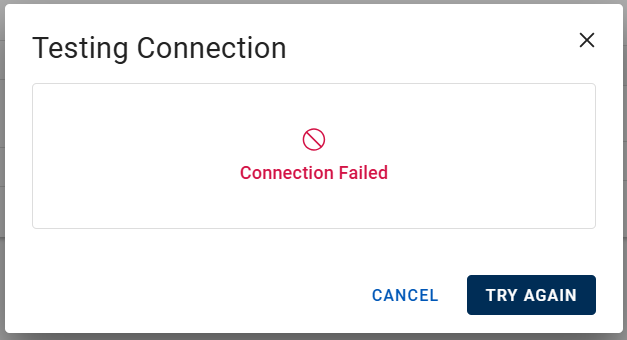
Success:
-
Failure - verify your configuration and try again
-
Edit a Configuration
-
Expand Service Settings
 in the left menu and select Directory Configuration.
in the left menu and select Directory Configuration. -
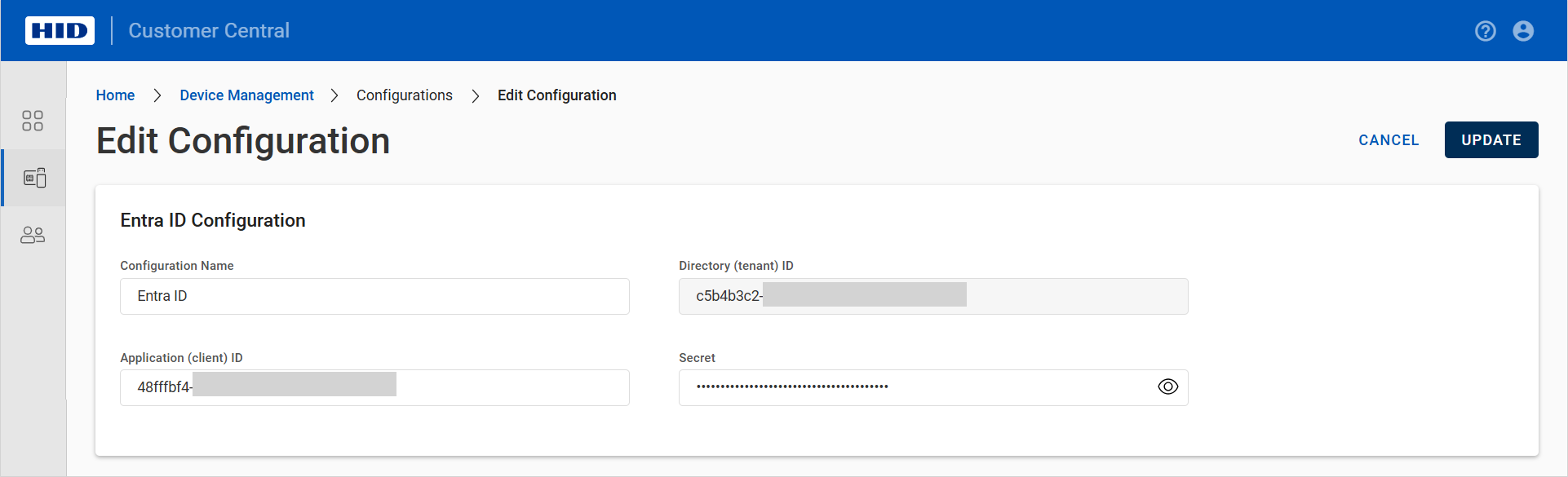
Click the menu icon
 for the configuration and select Edit.Note: The UPDATE button is unavailable until you have entered the required information.
for the configuration and select Edit.Note: The UPDATE button is unavailable until you have entered the required information.You can update the:
-
Configuration Name
-
Application (client) ID - the unique identifier that assigned to your Passkey Management application when you registered it
-
Secret - the client secret credential used by your Passkey Management application to identify itself when requesting a token
Note: For Microsoft Entra ID applications, the secret’s Value is only displayed when the secret is generated and cannot be displayed again.If you do not know the secret's value, you must generate a new secret.
-
-
Edit the configuration as required and click UPDATE.
Delete a Configuration
-
Expand Service Settings
 in the left menu and select Directory Configuration.
in the left menu and select Directory Configuration. -
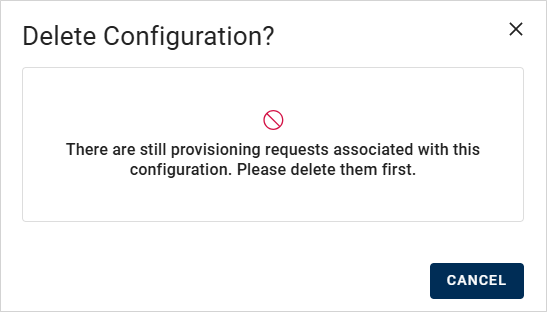
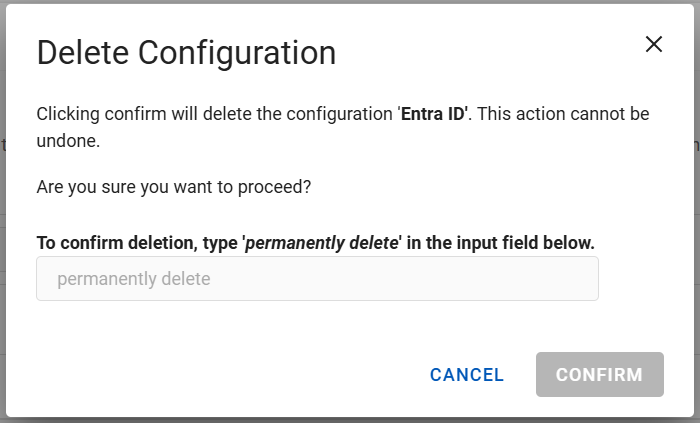
Click the menu icon
 for the configuration and select Delete.
for the configuration and select Delete. -
Enter permanently delete in the field and click CONFIRM.