Managing DigitalPersona AD
DigitalPersona provides a full complement of features, tools and utilities to assist the administrator in managing various aspects of the product, as well as expanding the functionality of the product.
Some of these tools and utilities are included in the product packages for either DigitalPersona AD Server or DigitalPersona AD Workstation. Others are available as separate modules, which may be obtained from your HID Global Account Manager or product Reseller.
DigitalPersona Administration Tools
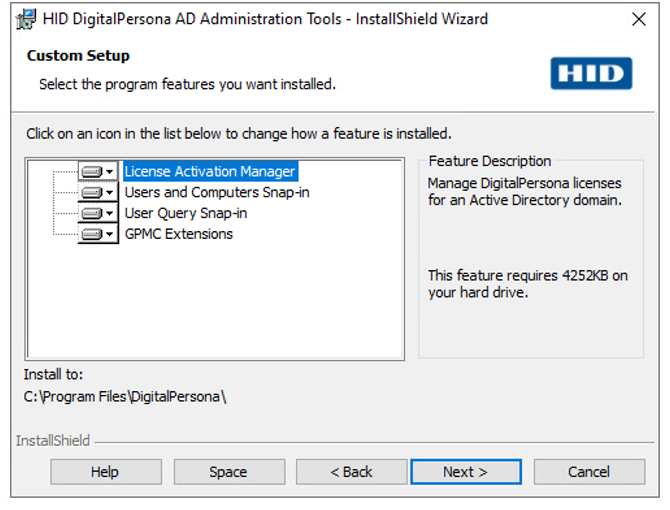
The Administration Tools include the following components and are part of a separate installation package included in the DigitalPersona AD product package.
They are installed by default through the installation wizard and may be deselected during installation by choosing a Custom install:
They can be installed on a single workstation for centralized administration ofDigitalPersona AD, or for larger organizations, each tool may be installed on a separate workstation in order to divide the administration of various features among several people.
Attended Enrollment
DigitalPersona Attended Enrollment is an optional feature of the DigitalPersona client software, DigitalPersona AD Workstation.
It’s installation and features are addressed in Installing DigitalPersona AD Workstation. However, there is a small amount of setup that must be performed in Active Directory by an administrator. Instructions for setup are contained in Setting Up Attended Enrollment.
About GPO Settings
Most of the settings that govern the features and behavior of the DigitalPersona AD solution are controlled through Active Directory GPO settings (see Policies and Settings). Additional settings and behaviors may be configured though Microsoft’s ADSI Editor and through custom VB scripts.
We strongly recommend managing all DigitalPersona policies through a separate GPO linked to an Organizational Unit (OU), and avoiding making any changes to the “Default Domain Policy.”
However, GPO settings that are left “Not Configured” in Active Directory may be configured by the local administrator by installing the GPMC Extensions feature from the Administration Tools component to a computer. Local settings that are configured will then be effective for all users on the specific computer.
Whenever a setting is configured (enabled or disabled) in Active Directory, the local administrator cannot modify the setting for the local computer.
For this reason – especially if the needs specific to your environment require you to provide end users with local administrative privileges – HID Global strongly recommends IT Administrators explicitly configure each desired setting in Active Directory, rather than relying on default behaviors associated with the unconfigured state.
Logon Authentication Policy Resolution Flow
DigitalPersona has three different levels where logon authentication policy can be defined:
-
Computer Level GPO
-
Active Directory group-based Logon Policy set via ADUC
-
User Level Logon Policy set directly to the user via ADUC
The following flow is used to determine the effective logon policy for a given user when authentication policies are set on more than one level:
-
If a user has a Logon Policy set at the individual user level (that is, a User Level Policy via ADUC, then that policy will be applied and DigitalPersona will be used to authenticate the user at Windows logon).
-
If a User Level Logon Policy is not set, then DigitalPersona checks whether the user belongs to an AD Group where a group-based Logon Policy is set.
If so, then the group-based Logon Policy will be applied, and this policy will be used we will use this policy to authenticate the user at Windows logon.
-
If neither of the previously described policies are set, DigitalPersona checks whether a Computer Level GPO is applied on the machine where the user is trying to log on to Windows or unlock the computer.
If this GPO is set, we will use this policy to authenticate the user at Windows logon.
-
If non of the above policies are set, the default DigitalPersona Logon Policy will be used.
This default Logon Policy is defined during installation of the HID DigitalPersona Client and usually contains all primary authentication credentials defined with an "OR" clause.
About Credentials
Passkeys
If passkey (device-bound or synced) credentials will be used with DigitalPersona Web Components (Identity Provider, HID DigitalPersona Administration Console or HID DigitalPersona Enrollment), the Web Management Components module should be installed and configured prior to any user enrolling a passkey credential.
If a passkey credential is enrolled through the DigitalPersona Workstation User Console, prior to the successful configuration of the Web Management Components, the credential will not roam and cannot be managed through HID DigitalPersona Enrollment or used to authenticate to any DigitalPersona web-based component.
Bluetooth Credentials
Enrollment of the Bluetooth credential is not supported in the DigitalPersona Web Enrollment application.
Topics in this section: