Installation Overview
Before you install ActivID CMS, make sure that the following hardware and supported components are installed and configured as indicated. For detailed information about versions supported, refer to ActivID CMS System Environment
ActivID CMS 6.1 is a Windows installer that can also be applied to ActivID CMS 5.10 or higher.
-
If you are installing ActivID CMS for the first time, you can install ActivID CMS 6.1 using the instructions provided in Typical Installation.
-
If you are already using ActivID CMS 5.10 or higher, you can install ActivID CMS 6.1 directly. For details, refer to Upgrading from ActivID CMS 5.10 or Higher.
Installation Prerequisites
-
A machine with at least 80 GB of hard disk space available (required for a full ActivID CMS installation) running a supported Windows operating system and Microsoft Internet Information Services (IIS) Web server.
IIS needs to be installed with the ISAPI (Internet Server Application Programming Interface) Extensions and ISAPI Filters service along with IIS 8.5 Management compatibility roles.
It is recommended to configure ActivID CMS with an NTP (Network Time Protocol) server to avoid time change attacks on the server hosting ActivID CMS.
-
A supported database (installed on the ActivID CMS server machine or a separate machine). Refer to ActivID CMS System Environment for the list of supported databases.
-
If using an Oracle database:
-
Create an Oracle database instance configured with UTF-8 and AL32UTF8 (NOT L16UTF16).
-
Install a supported version of the Oracle Client software (refer to ActivID CMS System Environment). Use a 64-bit client whether the Oracle database server is 32-bit or 64-bit. (Choose Administrator Type for Oracle Client installation, and install all components. For example, management console, management tools, networking services, utilities, and basic software.)
-
In the Oracle client software installed on the ActivID CMS server, declare a TNS (Transparent Network Substrate) name for the targeted Oracle database instance.
-
-
If using Microsoft SQL Server, install the Microsoft OLE DB 18 Driver (see Microsoft OLE DB Driver for SQL Server).
-
An installed Hardware Security Module (HSM) software or libraries on ActivID CMS server.
Important: This version of ActivID CMS supports FIPS 140-2 Level 3 Entrust Datacard® (formerly Thales®) HSMs, which no longer support 2TDEA key generation and thus cannot issue SCP01 profiles.As a result, the default configuration of the HSM directory delivered with this version was updated to be more secure. SCP01 keys were removed and a Legacy subdirectory was added, providing access to definitions of the SCP01 keys (including 2TDEA keys).
For new ActivID CMS installations or upgrades that still require support for SCP01 profiles:
use the LEGACY\Test.cfg and LEGACY\Principal.cfg files (provided in the .zip file) for HSM initialization on an HSM that is not FIPS 140-2 Level 3.
For new ActivID CMS installations or upgrades with support for only SCP03 profiles:
use the main Test.cfg and Principal.cfg files for HSM initialization.
For more information about which devices support SCP01 and SCP03 profiles, refer to Device Profiles and Hardware Devices.
-
An installed and initialized HSM hardware token using the Key Management System with a PIN assigned.
-
An installed LDAP Lightweight Directory Access Protocol v3 directory server.
-
An ActivID CMS Setup and Database Administration accounts.
-
A Domain Name System (DNS) populated with a fully-qualified DNS entry for the ActivID CMS server machine.
-
ActivID CMS automatically installs the following software if it is not installed on the machine:
-
Microsoft Visual C++ 2022 Redistributable Package (x64 and x86)
-
-
ActivID CMS also installs WildFly as a service (named “CMS Server”), using the default ports 8005 for commands, and 8009 for Apache JServ Protocol (AJP).
-
If you are using a Certificate Authority (CA):
-
Make sure the CA is up and running.
-
Optionally, obtain the Web server, Client, and Root CA certificates. For more information, see Required Certificates.
-
-
If you want to issue smart cards via Public Key Cryptography Standards (PKCS#11) (instead of using ActivID CMS secure channel protocol, based on GlobalPlatform), the associated PKCS#11 middleware must be installed on the ActivID CMS server and client issuing station.
Setup Type
During the setup, you are prompted to choose the type of setup. The following table describes your options:
|
Setup Option |
Description |
|---|---|
|
Typical setup (default) |
Installs both the ActivID CMS and the databases. |
|
Custom setup |
Allows you to install the ActivID CMS binaries only, the ActivID CMS databases only, or both. (For instance, if you use an ActivID CMS Peer Server for load balancing.) Note: Generally, the Custom setup is used by organizations where a network or application administrator installs the ActivID CMS server, and a separate database administrator installs the ActivID CMS database.
|
Database Authentication Type
During the setup, you are prompted to choose the database authentication type. The following table describes the methods supported by ActivID CMS.
|
Authentication Method |
Database |
Description |
|---|---|---|
|
SQL authentication |
Microsoft SQL Server |
Generally preferred for deployments because of its domain independence and greater flexibility. |
|
Windows authentication |
Microsoft SQL Server |
Allows the authentication from ActivID CMS to the SQL server to be managed by Windows for organizations that manage their SQL accounts using Active Directory. |
-
If you are installing ActivID CMS in a Windows-only environment, then you can use Windows authentication mode, which uses Windows authentication to log on/connect to the SQL Server. If your environment is not pure Windows (for example, Novell® and Windows), then you must use a mixed authentication mode (either Windows authentication or SQL Server authentication) to connect to the SQL Server.
The logons for the IIS Anonymous access user account and SQL Server NT do not have to be the same.
-
If you are installing ActivID CMS in an Oracle environment, then Oracle allows a single database instance to use any or all authentication methods. Oracle can authenticate users attempting to connect to a database by using information stored in that database.
Attended Startup Mode vs. Unattended Startup Mode
During the setup, you are prompted to choose the ActivID CMS startup mode. The following table describes your options.
|
Startup Mode |
Description |
Pros |
Cons |
|---|---|---|---|
|
Attended |
During Windows logon, the ActivID CMS administrator must enter the Security Key and Database Owner Passwords, and HSM PIN (when an HSM is present) to start ActivID CMS. |
More secure since those passwords are not stored locally. |
Operators must be present when the machine boots and manually provide all credentials. |
|
Unattended |
This mode allows the ActivID CMS server to start automatically without an administrator’s presence at startup time. In this case, the Security Key and Database Owner Passwords, and HSM PIN are all stored obfuscated in a configuration file on the ActivID CMS server. In this case, you must pay particular attention to the Windows access rights for the ActivID CMS configuration file. |
ActivID CMS does not require operators to intervene and restart ActivID CMS after a machine reboots. ActivID CMS starts automatically as soon as IIS and CMS Server services start. |
Security as passwords are stored locally (although obfuscated). |
Modify the Startup Mode
Choose the correct startup mode during setup carefully. It is not easy to modify the startup mode after installation. Refer to Changing the Startup Mode for details.
Obfuscating Passwords
Obfuscating the passwords means that the Security Key Password, HSM Pin, and Database Password are stored in the Secure.data.properties file, obfuscated with a proprietary algorithm. For detailed information about how to obfuscate the passwords, see Advanced Configuration.
Required Account Types and Privileges
There are four types of accounts that you must create before installing ActivID CMS. The following table summarizes these account types and the privileges required for each type of installation.
|
Account Type |
Function |
Minimum Required Privileges |
|---|---|---|
|
ActivID CMS Setup |
ActivID CMS Setup Windows Account: Used to install and operate the ActivID CMS application. Note: The account used to install ActivID CMS can differ from the account used to operate ActivID CMS.
|
Must at least have privileges of a Local Administrator. |
|
ActivID CMS Database Administrator |
ActivID CMS Database Instance Account: Used by the ActivID CMS application to create the six unique ActivID CMS databases (AIMSEE, AIMSAUDIT, AIMSLGI, AIMSCTI, AIMSRQI, and AIMSUSER). Note: Although provided during the setup, this password is not stored anywhere by ActivID CMS.
|
Create database/tables; create Database Owners for ActivID CMS databases. |
|
Database Owner(s) |
ActivID CMS Database Owner Account: Created automatically by ActivID CMS at the time of installation using the ActivID CMS Database Instance Administrator Account. You must create a “password” during setup installation. In unattended installation mode, this password is stored in an ActivID CMS configuration file, obfuscated. In attended mode, the password is not stored, and an operator must provide it at each startup. |
Read/write access to database. |
|
Web server anonymous access user account |
Windows Account: Account under which ActivID CMS operates within IIS and CMS Server services. |
Note: This account does not have to be a Domain Administrator; however, a Local Administrator account is required. There is an exception when using Microsoft CA - in this case, the account needs to be a Domain User, having Local Administrator privileges on the machine where ActivID CMS is installed.
|
ActivID CMS ships with a set of stand-alone database scripts for both Microsoft SQL Server and Oracle, which a qualified database administrator can use to create the ActivID CMS databases independent of the ActivID CMS setup program. For more information about upgrading SQL scripts, see Upgrading from ActivID CMS 5.10 or Higher.
Setting Up “Log On as a Service” Privilege
ActivID CMS runs in a WildFly Windows service (named “CMS Server”) which is started during ActivID CMS startup. This service is using the Web server anonymous access user account. Therefore, the anonymous access user account is required to have the “Log on as a service” privilege.
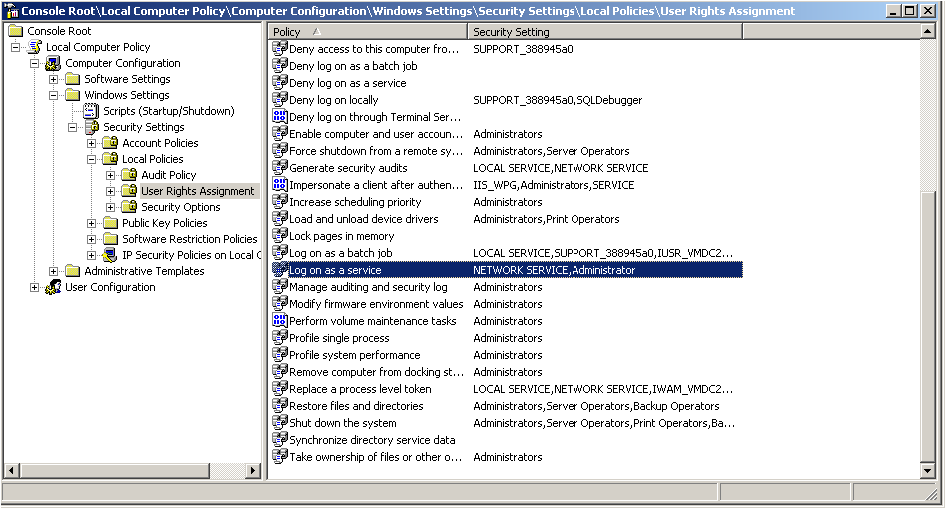
The following screenshot and procedures illustrate how to set this privilege for a Windows account:
-
In the Microsoft Management Console, load the Group Policy Editor snap-in, and select the machine on which ActivID CMS is installed.
-
Go to Local Computer Policy\Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignments.
-
Check if the ActivID CMS website anonymous user account is listed next to Log on as a service policy.
-
If not listed, right-click Log on as a service policy, select Properties, and click Add User or Group. Then, add the user account and click OK.
Required Certificates
There are three certificates required for configuring ActivID CMS. When you install ActivID CMS, you are prompted for the three certificate files.
If you do not have these certificates, (for instance, because you do not have a PKI available), then the ActivID CMS setup creates a self-generated CA for you and provides the certificates. If you choose this option, be sure to replace these self-generated certificates as soon as possible with certificates issued by a trusted CA. The self-generated certificates automatically expire after three years.
For best practice, it is recommended to use certificates generated by a trusted CA instead of the self-generated CA, or to replace the latter as soon as possible. For more information, see Replace a Certificate Generated by Setup by a Trusted CA-Generated Certificate. The following table describes the three required certificates.
|
Certificate Type |
Description |
|---|---|
|
SSL Web server certificate (for example, server.pfx) |
Note: Before you install ActivID CMS, make sure you export the Web server certificate into a PFX file and store it locally. You need it during the installation.
|
|
SSL client certificate (for example, client.pfx) |
The client certificate is used by the first ActivID CMS operator to log on to ActivID CMS. The hard disk-based client certificate allows the first operator to log on to ActivID CMS and configure the system. After smart cards have been issued and assigned to ActivID CMS administrators, we recommend you delete the ActivID CMS administrator using this certificate. Note: You must issue this certificate to any user account that is trusted by the ActivID CMS server machine. You can use any CA to issue an SSL Client certificate.
|
|
Root CA certificate of SSL Web server certificate (for example, root.cer) |
Used to validate the Web server certificate. It must contain the complete chain of trust associated with all CAs ActivID CMS uses. Note: Before you install ActivID CMS, you must export (in a .cer file) the root certificate of the CA that issued the Web Server certificate.
|
About HSMs
It is recommended to use an HSM to securely:
-
Store ActivID CMS and the card vendor’s Master Key (always).
-
Perform the generation of key-pairs for certificates that must be archived (for Microsoft CA).
-
Handle secure communication with CAs.
Deploying ActivID CMS without an HSM is not recommended as it can present security issues. If you choose not to install an HSM, the ActivID CMS and card vendor’s Master Keys are stored on the machine where ActivID CMS is installed. Moreover, in this configuration, ActivID CMS Master Keys are hard-coded and stored in a text file (acvopsm.cfg) in the %PROGRAMDATA%\HID Global\Credential Management System\Shared Files\acvopsm.cfg directory. Any future installations of ActivID CMS would use the same set of Master Keys, thus allowing smart cards to be updated or recycled by other ActivID CMS systems without HSMs.
Furthermore, cards issued without an HSM cannot later be managed by another ActivID CMS using an HSM. Nor can an ActivID CMS installation, which is installed without an HSM originally, be made to work with an HSM in the future.If you choose to install ActivID CMS without an HSM, the following disclaimer message appears during the setup:
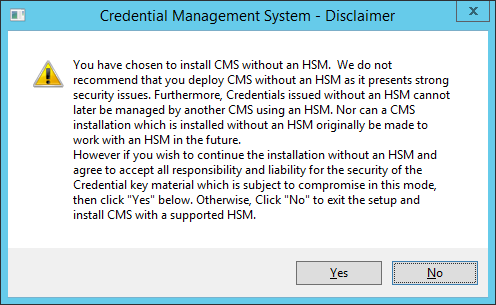
Click Yes if you agree with the terms and want to proceed with the installation. Click No to terminate the installation.





